Thievingfox是一系列爆炸后工具,可从各种密码管理器和Windows实用程序中收集凭据。每个模块都利用一种特定的方法将其注入目标过程,然后挂钩内部功能来收集凭据。
随附的博客文章可以在此处找到
必须安装
安装
Linux
Rustup,请按照: 3https://rustup.rs//
必须安装mingw-w64软件包。在Debian上,可以使用:完成此操作
APT安装mingw-w64 x86和x86_64 Windows目标必须为RUST:安装
rusup target添加x86_64-pc-windows-gnu
还必须安装Rustup Target添加i686-pc-windows-gnu Mono和Nuget,在此处提供说明: 3https://WWW.MONO-PROJEMT.COM/DOWNLOAD/stable/#download/#downloadload-lin
添加单声道存储库后,可以使用APT :安装Nuget
最终,APT安装nuget,必须安装python依赖者:
pip install -r客户端/需求.txt thievingfox与python一起使用=3.11。
必须安装
Windows
Rustup,请按照可用的说明: 3https://rustup.rs//
X86和X86_64必须为RUST:安装Windows目标
rusup target添加x86_64-pc-windows-msvc
还必须安装Rustup Target添加I686-PC-Windows-MSVC .NET开发环境。从Visual Studio,导航到工具获取工具和功能安装“ .NET桌面开发”
最后,必须安装python依赖者:
pip install -r客户端/需求.txt thievingfox与python一起使用=3.11
注意Windows主机上的注释:为了使用keepass模块,必须在路径中可用。这可以通过从Visual Studio开发器PowerShell中运行客户端(工具命令行开发器PowerShell)来实现。
目标
所有模块都已在以下Windows版本上进行了测试:
Windows版本Windows Server 2022 Windows Server 2019 Windows Server 2016 Windows Server 2012R2 Windows 10 Windows 11 [!警告]模块尚未在其他版本上进行测试,并且有望不起作用。
申请注入方法keepAss.exe appDomainManager注入exeAssxc.exe dll proxying logonui.exe(Windows登录屏幕)com hijacking consent.exe(windows uac uac popup)comhijacking mstsc.exe(Windows RDP rdp client) (第三方RDP客户端)COM劫持
用法
[!谨慎],尽管我试图确保这些工具不会影响目标应用程序,内联钩和图书馆注入的稳定性不安全,这可能会导致崩溃,或者应用程序不稳定。如果是这种情况,则使用目标上的清理模块应足以确保下次启动应用程序时,未执行注射/钩。
Thievingfox包含3个主要模块:毒药,清理和收集。
毒药
针对命令行参数中指定的每个应用程序,毒物模块检索将被劫持的原始库(用于劫持和dll代理),编译了与原始dll的属性相匹配的库,将其上传到服务器上,并将其上传到服务器上,并修改了需要进行com if Compor com Jjacking com Jjacking,
为了加快所有库的编译过程,在客户端/缓存/中维护了缓存。
-MSTSC,-RDCMAN和- MOBAXTERM分别具有特定选项-MSTSC-POINS-HKCR,-RDCMAN-POINS-POINS-HKCR和-MOBAXTERM-POINS-POISON-HKCR。如果指定了这些选项之一,则COM劫持将替换HKCR Hive中的注册表密钥,这意味着所有用户都会受到影响。默认情况下,只有当前登录的用户都受到影响(所有具有HKCU Hive的用户)。
- keepass和- keepassXC具有特定的选项, - keepass-path, - keepass-share和- keepassxc-path, - keepassxc-share,以指定安装这些应用程序的位置,如果不是默认的安装路径。由于使用COM劫持,这不是其他应用程序所需的。
Keepass模块需要可视化的C ++重新分布才能安装在目标上。
可以一次指定多个应用程序,也可以使用- 所有标志来针对所有应用程序。
[!
$ python3客户/thievingfox.py毒药-h
usage: thievingfox.py毒药[-h] [-hashes hashes] [-aeskey aeskey]
[ - keepass-share keepass_share] [ - keepAssxc] [ - keepAssxc-path keepAssxc_path] [ - keepAssxc-share keepAssxc_share] [ - mstsc] [ - mstsc-poison-hkcr]
[-consent] [-logonui] [-rdcman] [-rdcman-poison-hkcr] [-mobaxterm] [-mobaxterm-poison-poison-hkcr] [ - all]
目标
位置参数:
目标目标机或范围[域/]用户名[:Password] @IP或fqdn [/cidr]
Options:
-h, - 赫尔普显示此帮助消息和退出
- hashes哈希, - 锤子哈希
LM:NT哈希
-aeskey aeskey,-aeskey aeskey
AES键可用于Kerberos身份验证
-K使用Kerberos身份验证。对于Logonui,MSTSC和同意模块,执行匿名NTLM身份验证,以检索OS版本。
-DC-IP DC_IP,-DC-IP DC_IP
域控制器的IP地址
-No-pass,-no-pass不提示密码
- tempdir tempdir使用用于DLL和输出的临时目录的名称(Default: Thievingfox)
- 维修尝试毒化keepass.exe
- keepass-path keepass_path
安装keetass的路径,没有共享名称(Default:/Program Files/keepass密码安全2/)
- keepass-share keepass_share
安装keepass的份额(Default: C $)
- keepassxc尝试毒化keepAssxc.exe
- keepassxc-path keepAssxc_path
安装keepASSXC的路径,没有共享名称(default:/program Files/keepassxc/)
- ke epassxc-share keepassxc_share
安装keepASSXC的份额(Default: C $)
-MSTSC尝试毒化mstsc.exe
-MSTSC-poison-HKCR而不是毒害目前登录用户的HKCU蜂箱,而是毒害HKCR Hive为MSTSC,这也将适用于目前不适用的用户
登录(default: false)
- 同意尝试毒化同意
- logonui尝试毒化logonui.exe
-RDCMAN尝试毒化rdcman.exe
-RDCMAN-POINS-HKCR而不是毒化目前登录用户的HKCU Hives,毒害HKCR Hive的RDCMAN,这也将适用于目前不做的用户
登录(default: false)
- Mobaxterm尝试毒化mobaxterm.exe
-MobaxTerm-Poison-HKCR
而不是贫穷目前登录用户的HKCU蜂箱,而是毒害HKCR Hive用于MobaxTerm,这也适用于目前不适用的用户
登录(default: false)
- 所有大家都试图毒化所有应用程序
清理
为命令行参数中指定的每个应用程序,清理首先删除迫使目标应用程序加载挂钩库的贫困文物。然后,它试图删除上传到远程主机的库。
对于支持HKCU和HKCR蜂箱贫困的应用,无论如何都可以清理。
可以立即指定多个应用程序,也可以使用- 所有标志可用于清理所有应用程序。
它不会在远程主机上清洁提取的凭据。
[!重要]如果在运行清理模块时正在使用目标应用程序,则无法删除目标上的DLL。但是,清理模块将恢复能够注入的配置,这应确保下次启动应用程序时,未执行注射。记录了无法用Thievingfox删除的文件。
$ python3客户端/thievingfox.py清理-H
usage: thievingfox.py清理[-h] [-hashes hashes] [-aeskey aeskey]
[ - keepiss-path keepass_path] [ - keepissxc] [ - keepissxc-path keepAssxc_path] [ - keepissxc-share keepAssxc_share] [ - mstsc] [ - 同意] [ - logonui]
[ - -RDCMAN] [ - MOBAXTERM] [ - all]
目标
位置参数:
目标目标机或范围[域/]用户名[:Password] @IP或fqdn [/cidr]
Options:
-h, - 赫尔普显示此帮助消息和退出
- hashes哈希, - 锤子哈希
LM:NT哈希
-aeskey aeskey,-aeskey aeskey
AES键可用于Kerberos身份验证
-K使用Kerberos身份验证。对于logonui,mstsc和cons ent模块,执行了匿名的NTLM身份验证,以检索OS版本。
-DC-IP DC_IP,-DC-IP DC_IP
域控制器的IP地址
-No-pass,-no-pass不提示密码
- tempdir tempdir使用用于DLL和输出的临时目录的名称(Default: Thievingfox)
- 维修试图清理所有与keepass.exe相关的毒品
- keepass-share keepass_share
安装keepass的份额(Default: C $)
- keepass-path keepass_path
安装keetass的路径,没有共享名称(Default:/Program Files/keepass密码安全2/)
- keepassxc尝试清理所有与keepAssxc.exe相关的毒物
- keepassxc-path keepAssxc_path
安装keepASSXC的路径,没有共享名称(default:/program Files/keepassxc/)
- keepassxc-share keepassxc_share
安装keepASSXC的份额(Default: C $)
-MSTSC尝试清理所有与mstsc.exe相关的毒物
- 同意尝试清理所有与同意有关的毒物
- logonui尝试清理所有与logonui.exe有关的毒物
- RDCMAN尝试清理所有与rdcman.exe相关的毒物
- Mobaxterm尝试清理所有与Mobaxterm.exe相关的毒物
- 所有大家都尝试清理与所有应用程序
收集
相关的所有贫困工件,为命令行参数指定的每个应用程序,收集模块检索在C: \ Windows \ Windows \ temp \ temp \ tempdir中存储的远程主机上的输出文件,并将其拆除。这些文件从远程主机中删除,并且检索到的数据存储在客户端/ouput/中。
可以立即指定多个应用程序,也可以使用- 所有标志可用于从所有应用程序中收集日志。
$ python3客户端/thievingfox.py收集-H
用法: thievingfox.py collect [-h] [-hashes hashes] [-aeskey aeskey] [-k] [-dc-ip dc_ip] [-no-pass] [-no-pass] [-tempdir tempdir]
[ - -logonui] [ - rdcman] [ - mobaxterm] [ - all]
目标
位置参数:
目标目标机或范围[域/]用户名[:Password] @IP或fqdn [/cidr]
Options:
-h, - 赫尔普显示此帮助消息和退出
- hashes哈希, - 锤子哈希
LM:NT哈希
-aeskey aeskey,-aeskey aeskey
AES键可用于Kerberos身份验证
-K使用Kerberos身份验证。对于Logonui,MSTSC和同意模块,执行匿名NTLM身份验证,以检索OS版本。
-DC-IP DC_IP,-DC-IP DC_IP
域控制器的IP地址
-No-pass,-no-pass不提示密码
- tempdir tempdir使用用于DLL和输出的临时目录的名称(Default: Thievingfox)
- keepass收集keepass.exe日志
- keepassxc收集keepAssxc.exe日志
-MSTSC收集MSTSC.EXE日志
- 一致收集同意。exe日志
-logonui收集logonui.exe日志
-RDCMAN收集rdcman.exe日志
- Mobaxterm收集Mobaxterm.exe日志
- 从所有应用程序中收集日志




.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)

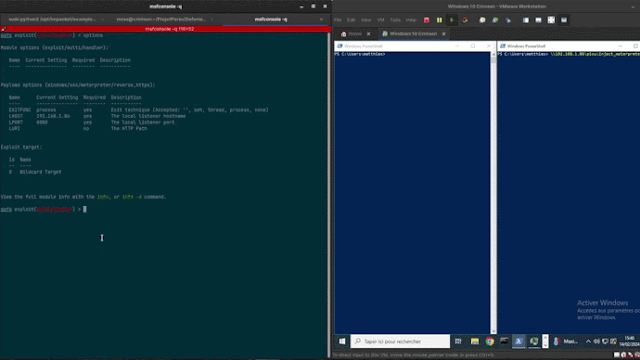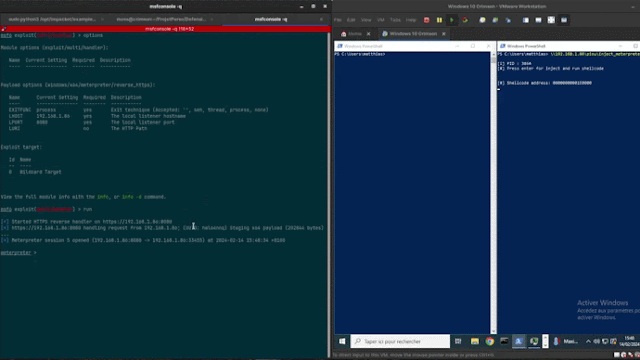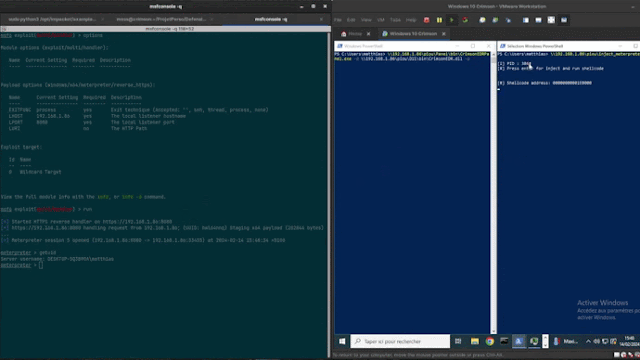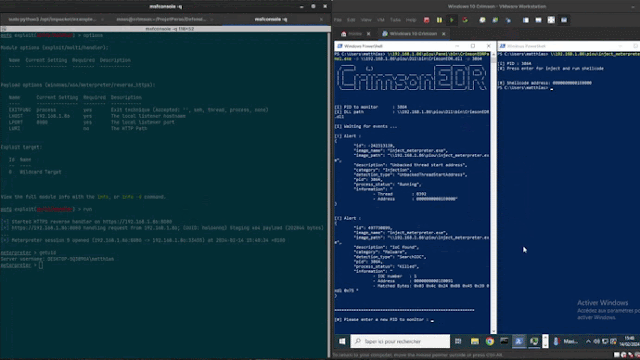



 code is as follows type: picture-elements
code is as follows type: picture-elements
 Next we use Mr. World to create a pdf file.
Next we use Mr. World to create a pdf file.
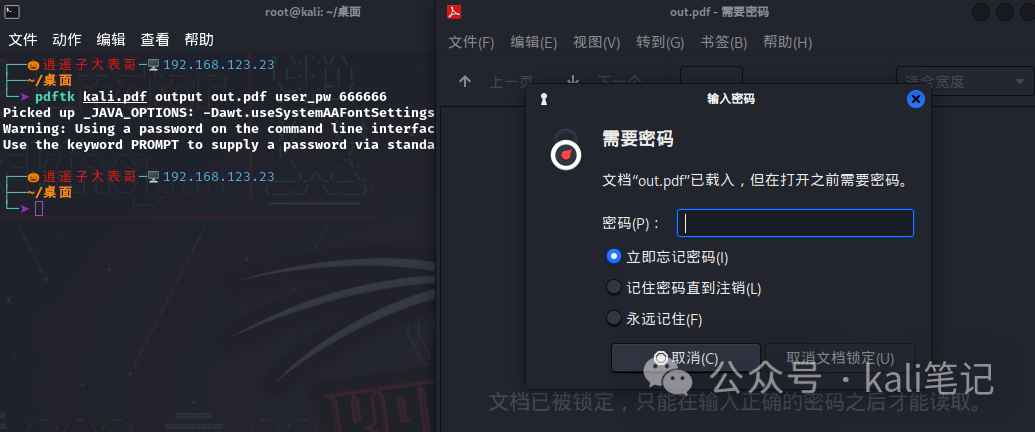
 Next, we add a password to the just generated pdf in Linux. The command is as follows:
Next, we add a password to the just generated pdf in Linux. The command is as follows:
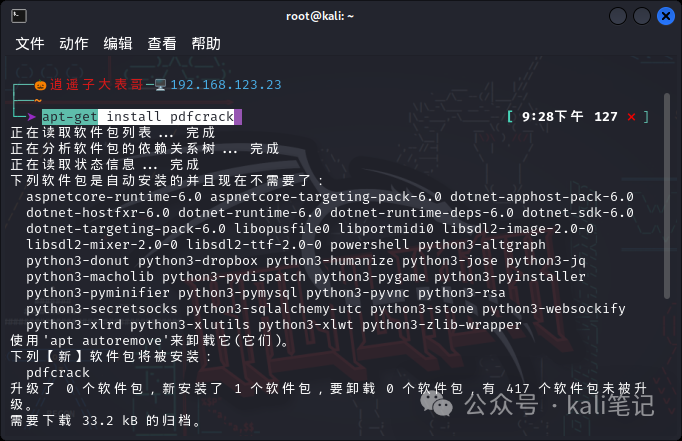
 Now, let’s take a look at how to crack it. First, we install the tool pdfcrack
Now, let’s take a look at how to crack it. First, we install the tool pdfcrack
 Use specified characters to start brute-force cracking pdfcrack-fout.pdf-n6-m8-c0123456789 Parameter Detailed Explanation-f: Select the pdf file to crack
Use specified characters to start brute-force cracking pdfcrack-fout.pdf-n6-m8-c0123456789 Parameter Detailed Explanation-f: Select the pdf file to crack
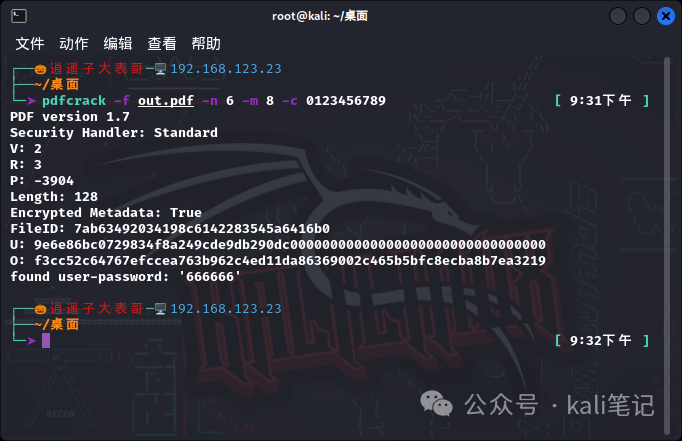 In the column above, my password is only 6 pure numbers. It took less than 30 seconds to crack. Therefore, for important files, you must strengthen the password strength and backup the password to prevent the password from being lost. Of course, in the column above, we only use numbers. What if there are letters? Why not try the universal password below.
In the column above, my password is only 6 pure numbers. It took less than 30 seconds to crack. Therefore, for important files, you must strengthen the password strength and backup the password to prevent the password from being lost. Of course, in the column above, we only use numbers. What if there are letters? Why not try the universal password below.