In the previous article, we talked about the installation of Owasp juice shop. This article will follow my cousin’s footsteps to get through the level! This article mainly talks about the difficulty of one-star pass strategy.
Bonus Payload(Payload)
Description: Use reward payment load in the DOM XSS challenge.
payload: Just copy the code to the search box.
iframe width='100%' height='166' scrolling='no' frameborder='no' allow='autoplay' src='https://w.soundcloud.com/player/?url=https%3A//api.soundcloud.com/tracks/771984076color=%23ff5500auto_play=truehide_related=falseshow_comments=trueshow_user=trueshow_reposts=falseshow_teaser=true'/iframe 
DOM XSS
Description: DOM-based XSS attack
payload:
iframe src='javascript:alert(`xss`)' 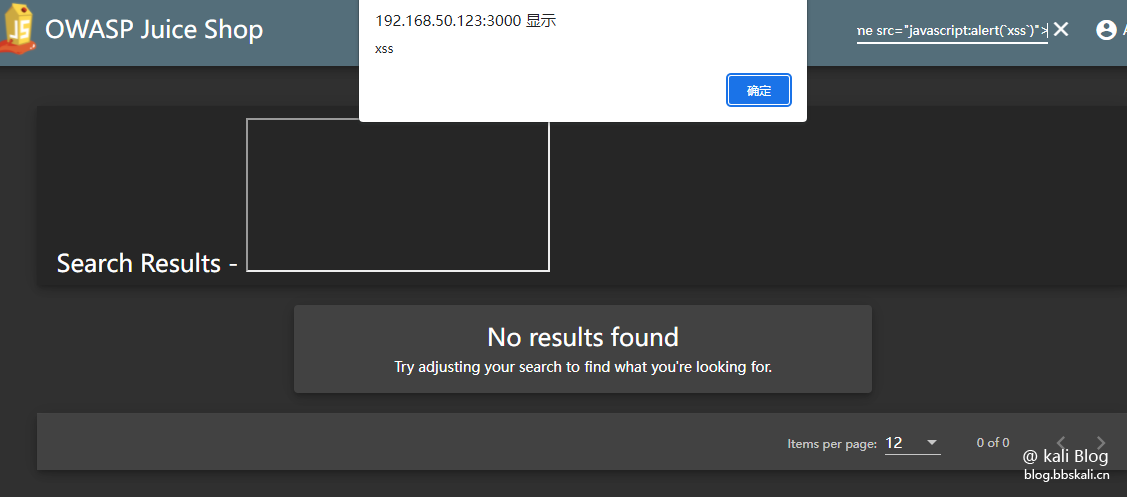
Confidential Files
Description: Check confidential documents
We clicked about us and found a hyperlink. Click on the hyperlink and grab the packet in burp.
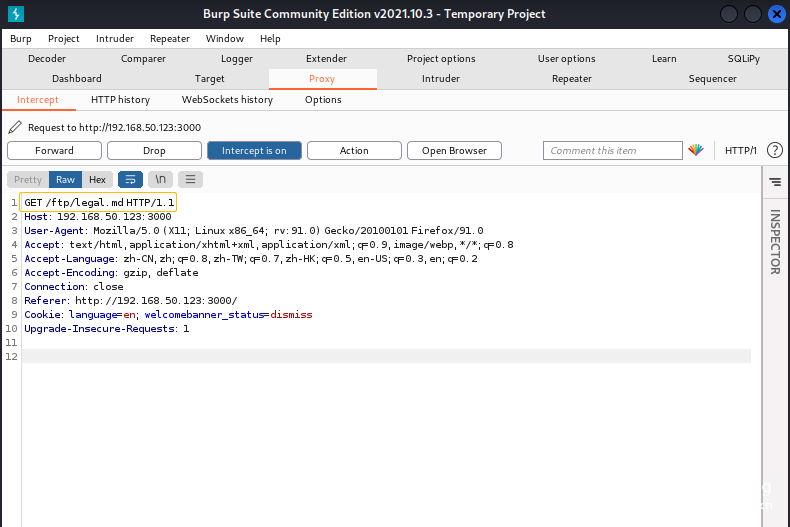
Modify the contents in front of ftp. You can see the following file information.
Click to read in turn and this level will be passed.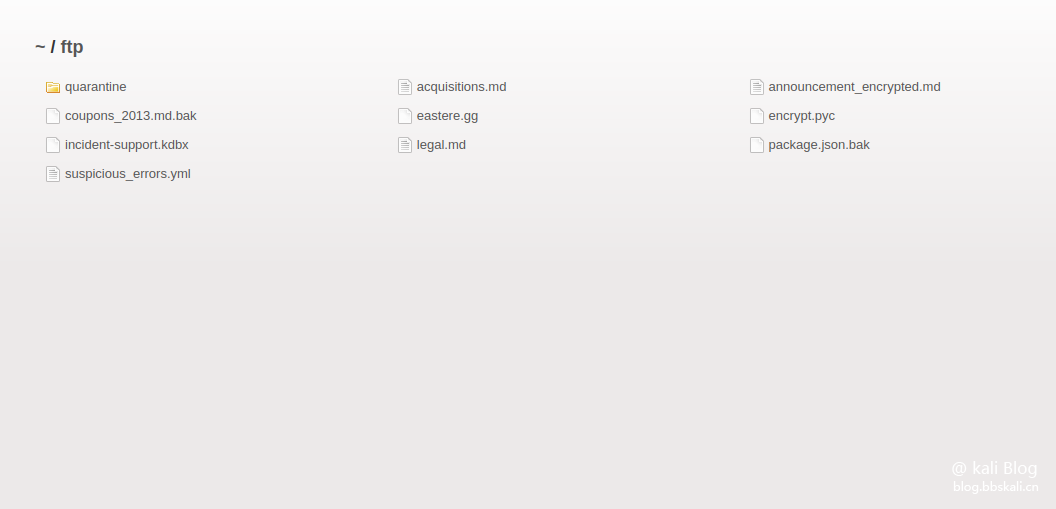
Bully Chatbot
This level is very simple, which means chatting with the robot and obtaining a discount coupon. When the content of the chat post contains a code, the robot will send you a discount coupon.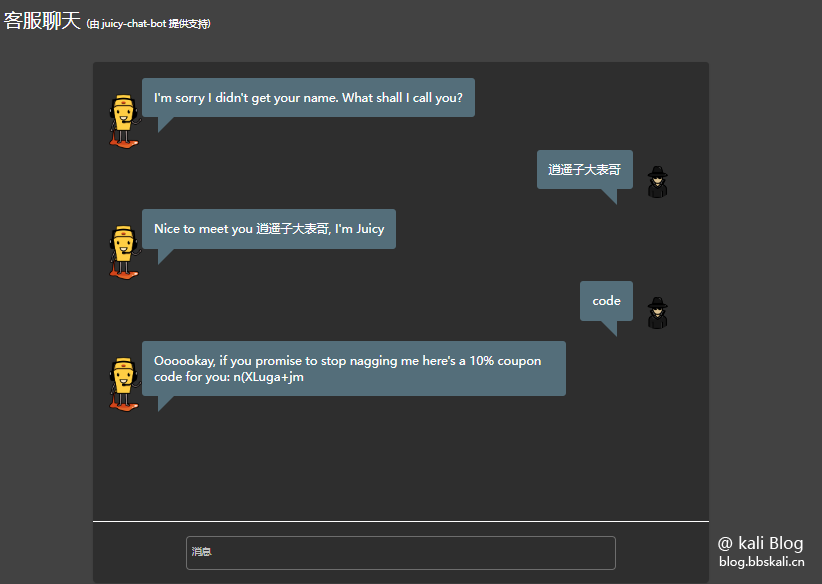
Exposed Metrics
Description: Find out the server data obtained by backend services using common monitoring software
By accessing the documents in the official website, you can check the default backend entry address (localhost:3000/metrics).
Missing Encoding
Description: Retrieve photos of Bjoern cat 'Brave Mode'.
Click on the photo wall and found that an image was not loaded. The image review element found that the url of the image is img _ngcontent-utp-c241='' class='image' src='assets/public/images/uploads/-#zatschi-#whoneedsfourlegs-1572600969477.jpg' alt=' #zatschi #whoneedsfourlegs'
The image here has not been parsed because the URL contains special conformity needs and performs a conversion, which will cause some exceptions. Here, change # in the url to %23.
Outdated Allowlist
Search for keyword redirect in js file?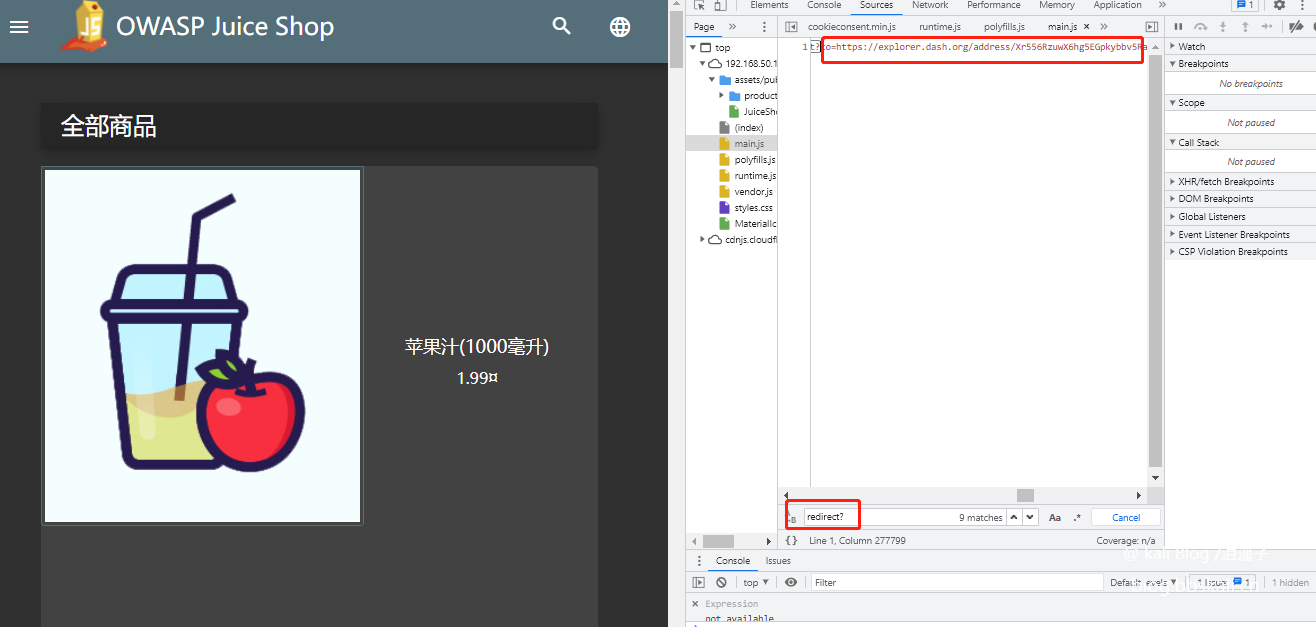
Just visit the url.
Repetitive Registration
Click the registration page, review element button, and delete disabled='true'. At this time, we only enter the user name and the others are empty, so we can register directly.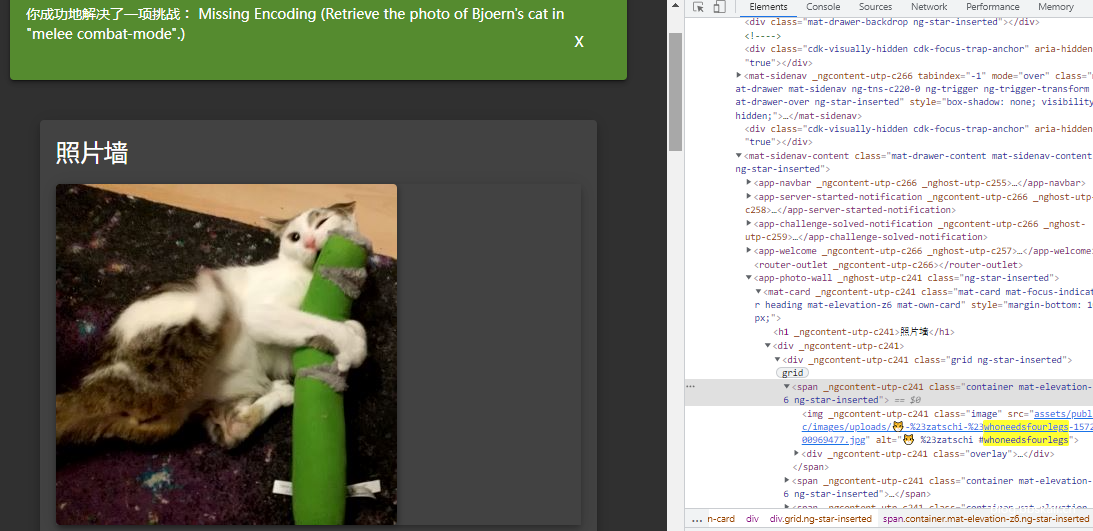
Zero Stars
Click on the customer feedback page to review the elements of the button, remove disabled='true'
At this time, we only need to enter the verification code to submit.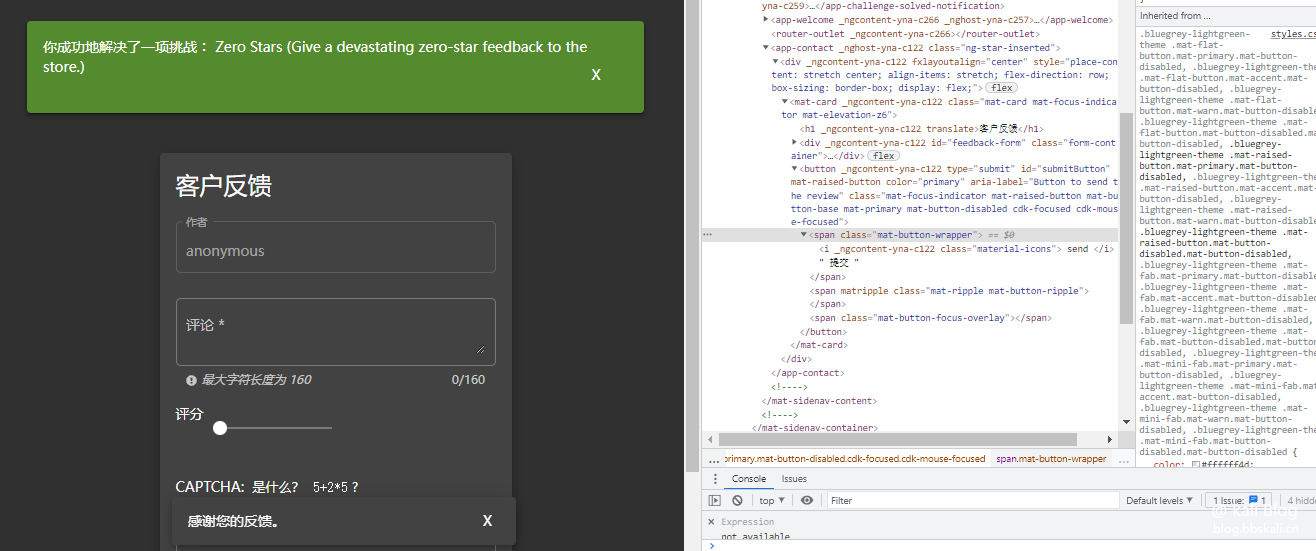





Recommended Comments