In this article, we will briefly summarize some of the commonly used reverse tools in Android penetration and its basic usage methods.
Apktool
Apktool is the most commonly used Android decompilation tool. It supports multiple platforms, and in Linux we can use the apt command to install it directly.
apt-get install apktool 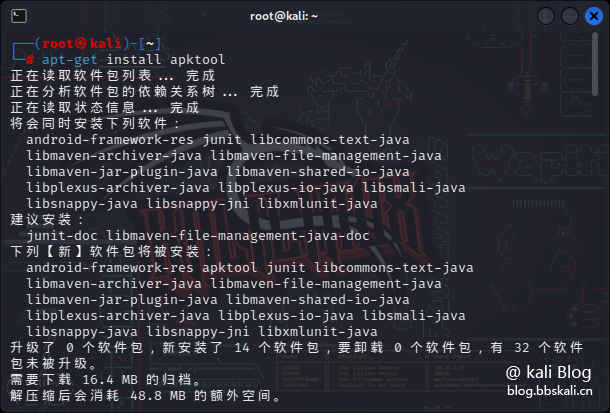
Help command apktool -h 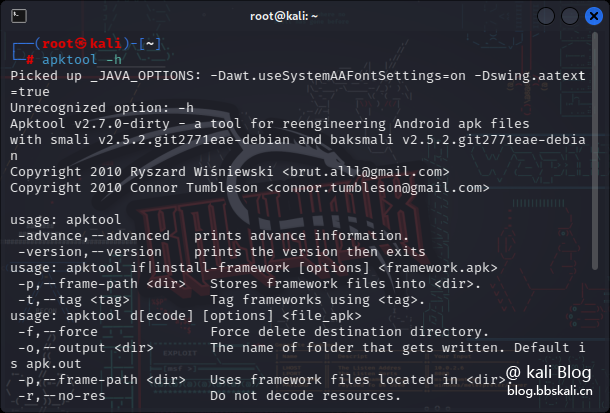
Basic use
Decompile the app, we can decompile the Android apk file with the -d command
apktool d xxxx.apk If you need to compile apk back, you can use the -b command
apktook b xxxx, please do not confuse the two.
dex2jar
dex2jar is used to convert DEX files into JAR files. We need to read the source code of the program and need this tool. Install the source code of dex2jar. The source code compression package can be unzipped from the official website of dex2jar (https://sourceforge.net/projects/dex2jar/). You can use the terminal to enter the decompression directory and execute the following command to compile:
bashCopy code
After the ./gradlew build is compiled, the executable file is located in dex-tools/build/distributions/dex-tools-.zip. Unzip the compressed package and you will get an executable file.
If you don't want to compile, you can download the compiled one directly in the github repository.
JD-GUI
It requires decompiling ordinary Java programs, or simple decompiling and viewing of Android applications, and you can use JD-GUI. If you need to do more in-depth Android application decompilation and analysis, it is recommended to use JADX.
Download address (http://java-decompiler.github.io/) 
Frida
A dynamic code injection tool that can modify and debug Android applications at runtime to install pip3 install frida
sudo pip3 install frida-tools It should be noted that the computer needs a python environment. We will explain the specific use in detail to you in the following article.





Recommended Comments