In the previous article, we talked about using ipv6 to access the local network without a public IP. However, the IPv6 enablement requires the modification of the configuration of the Lightmao. Without the Lightmao Super Administrator password, I just have the will but lack the ability.
What is hole digging?
Under the NAT1 network, we can expose the local TCP port to the public network through a "hole-punching" method, run HTTP services, etc. Forwarding rules through Natter holes + firewall. We can easily expose intranet devices to the public network.
Experimental Environment
Router (soft router) Centos7 (intranet host)
Examination Network
First use, check the current network NAT situation. We first clone the project to the local environment.
git clone https://github.com/MikeWang000000/Natter.git
cd Natter
# Verify network
python natter.py --check-nat 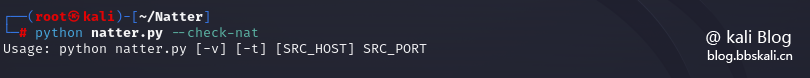
As shown in the picture above, there is no error. Prove that you can have fun.
The reason for the high probability of failure: Your home network is NAT, not NAT1. (Most operator networks are NAT1 at present)
The slight test
Experimental purpose: access my local server (192.168.123.173:5244) alist cloud disk through the external network.
First we use Natter script to dig holes
python3 natter.py -t 5244 -t i.e. tcp protocol.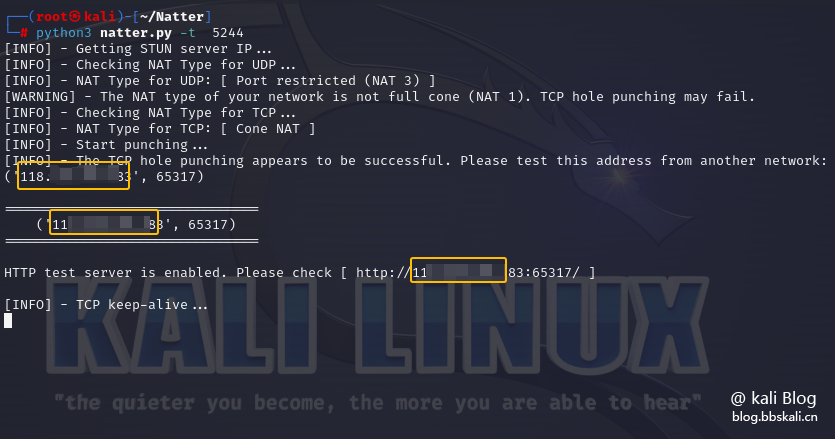
After the previous step is completed, we are still unable to access it. Because there is no IP and port of the intranet device specified. Therefore, we need to do port forwarding in the router.
Port Forwarding
Log in to the router and set the parameters in port forwarding as follows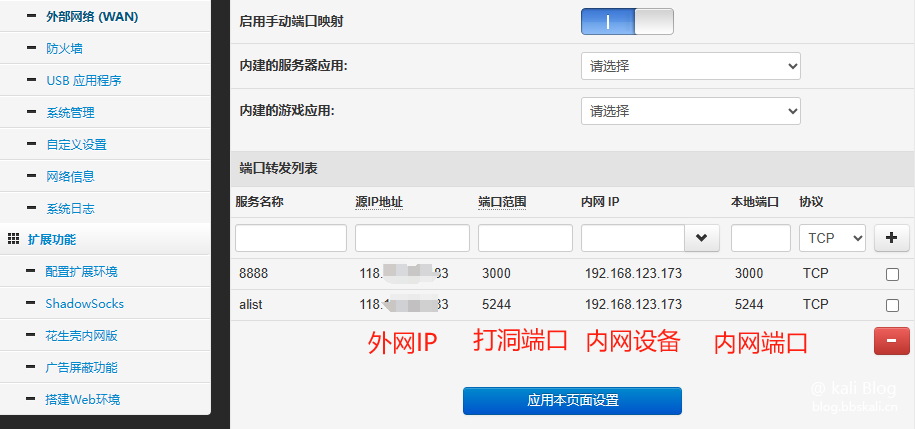
As mentioned above, when we access http://118.xxxx.xxxx.183:65317/, we can access our local port 5244.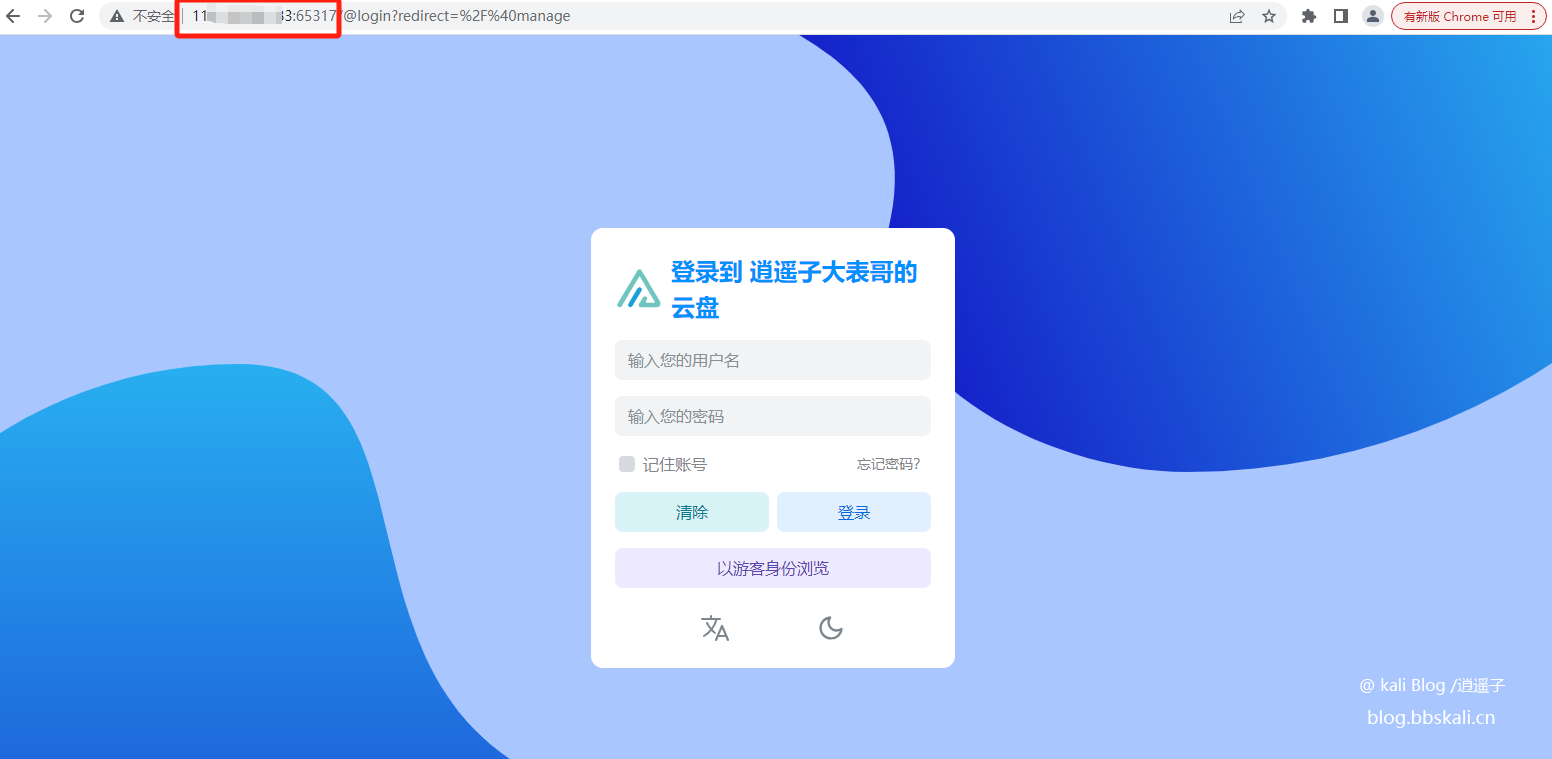
Dig holes on multiple devices
In the above method, we only opened port 5244. What if there are multiple ports and multiple devices? Or what should I do if the router does not have a port forwarding function?
We need to create a new json file. The content is as follows
//Note: The JSON configuration file does not support code comments, and here is an explanation of the configuration purpose.
{
'logging': {
'level': 'info', //Log level: optional values: 'debug', 'info', 'warning', 'error'
'log_file': './natter.log' //Export the log to the specified file, please leave it blank if you don't need it: ''
},
'status_report': {
//When the external IP/port changes, the following command will be executed.
//Braces {.} are placeholders, and the command will be replaced by the actual value when executing.
//Please leave blank if you don't need it: ''
'hook': 'bash ./natter-hook.sh '{protocol}' '{inner_ip}' '{inner_port}' '{outer_ip}' '{outer_port}' '{outer_port}',
'status_file': './natter-status.json' //Store the real-time port mapping status to the specified file, please leave it blank if you don't need it: ''
},
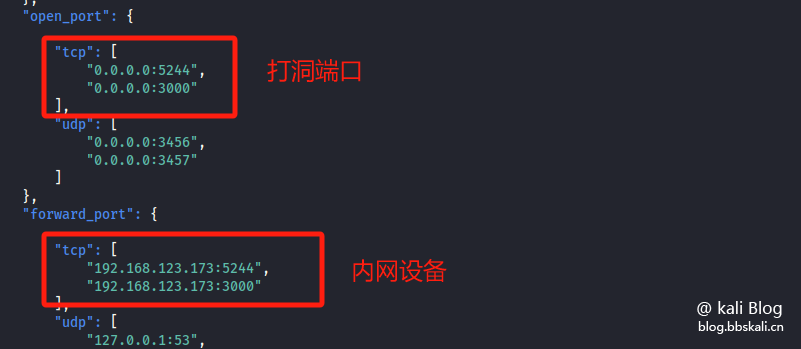
'open_port': {
//Set up Natter hole-punching IP: port here. (Only holes)
//The address here is the address bound (listening) of Natter. Natter only drills holes for these addresses. You need to manually set port forwarding.
//Note: Use default export IP, please use 0.0.0.0 instead of 127.0.0.1 .
'tcp': [
'0.0.0.0:3456',
'0.0.0.0:3457'
],
'udp': [
'0.0.0.0:3456',
'0.0.0.0:3457'
]
},
'forward_port': {
//Here, you need to set up the IP: port that Natter opens to the public network. (Dig hole + built-in forwarding)
//Natter will automatically drill holes and forward them, and you don’t need to intervene.
//Note: Use native IP, use 127.0.0.1 instead of 0.0.0.0.0.
'tcp': [
'127.0.0.1:80',
'192.168.1.100:443'
],
'udp': [
'127.0.0.1:53',
'192.168.1.100:51820'
]
},
'stun_server': {
//Set up a public STUN server here.
//Please make sure that the TCP/3478 port is open and available for the TCP server;
//Please make sure that the UDP/3478 port is open and available for UDP server.
'tcp': [
'stun.stunprotocol.org',
'stun.voip.blackberry.com'
],
'udp': [
'stun.miwifi.com',
'stun.qq.com'
]
},
'keep_alive': 'www.qq.com' //Set up the HTTP Keep-Alive server here. Please make sure that the server is open on port 80 and supports HTTP Keep-Alive.
}  Run python3 natter.py -c ./config.json
Run python3 natter.py -c ./config.json
Summary
Using this tool, we can easily access the intranet devices on the external network. However, when the operator's IP changes, the IP cannot be updated automatically. Therefore, you can refer to the previous article to automatically update the domain name. In addition, there is no need to try not to expose intranet devices to the public network!





Recommended Comments